Vulnerabilities > CVE-2016-0728
Attack vector
LOCAL Attack complexity
LOW Privileges required
LOW Confidentiality impact
HIGH Integrity impact
HIGH Availability impact
HIGH Summary
The join_session_keyring function in security/keys/process_keys.c in the Linux kernel before 4.4.1 mishandles object references in a certain error case, which allows local users to gain privileges or cause a denial of service (integer overflow and use-after-free) via crafted keyctl commands.
Vulnerable Configurations
Exploit-Db
description Linux Kernel <= 4.4.1 - REFCOUNT Overflow/Use-After-Free in Keyrings Local Root (2). CVE-2016-0728. Local exploit for linux platform id EDB-ID:40003 last seen 2016-06-22 modified 2016-01-19 published 2016-01-19 reporter Federico Bento source https://www.exploit-db.com/download/40003/ title Linux Kernel <= 4.4.1 - REFCOUNT Overflow/Use-After-Free in Keyrings Local Root 2 description Linux Kernel REFCOUNT Overflow/Use-After-Free in Keyrings. CVE-2016-0728. Local exploit for linux platform file exploits/linux/local/39277.c id EDB-ID:39277 last seen 2016-02-04 modified 2016-01-19 platform linux port published 2016-01-19 reporter Perception Point Team source https://www.exploit-db.com/download/39277/ title Linux Kernel REFCOUNT Overflow/Use-After-Free in Keyrings type local
Nessus
NASL family SuSE Local Security Checks NASL id SUSE_SU-2016-0205-1.NASL description The SUSE Linux Enterprise 12 kernel was updated to receive a security fix. Following security bug was fixed : - A reference leak in keyring handling with join_session_keyring() could lead to local attackers gain root privileges. (bsc#962075, CVE-2016-0728). Note that Tenable Network Security has extracted the preceding description block directly from the SUSE security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 88144 published 2016-01-25 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/88144 title SUSE SLED12 / SLES12 Security Update : kernel (SUSE-SU-2016:0205-1) code # # (C) Tenable Network Security, Inc. # # The descriptive text and package checks in this plugin were # extracted from SUSE update advisory SUSE-SU-2016:0205-1. # The text itself is copyright (C) SUSE. # include("compat.inc"); if (description) { script_id(88144); script_version("2.12"); script_cvs_date("Date: 2019/09/11 11:22:13"); script_cve_id("CVE-2016-0728"); script_name(english:"SUSE SLED12 / SLES12 Security Update : kernel (SUSE-SU-2016:0205-1)"); script_summary(english:"Checks rpm output for the updated packages."); script_set_attribute( attribute:"synopsis", value:"The remote SUSE host is missing one or more security updates." ); script_set_attribute( attribute:"description", value: "The SUSE Linux Enterprise 12 kernel was updated to receive a security fix. Following security bug was fixed : - A reference leak in keyring handling with join_session_keyring() could lead to local attackers gain root privileges. (bsc#962075, CVE-2016-0728). Note that Tenable Network Security has extracted the preceding description block directly from the SUSE security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues." ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.suse.com/show_bug.cgi?id=962075" ); script_set_attribute( attribute:"see_also", value:"https://www.suse.com/security/cve/CVE-2016-0728/" ); # https://www.suse.com/support/update/announcement/2016/suse-su-20160205-1/ script_set_attribute( attribute:"see_also", value:"http://www.nessus.org/u?3fd53631" ); script_set_attribute( attribute:"solution", value: "To install this SUSE Security Update use YaST online_update. Alternatively you can run the command listed for your product : SUSE Linux Enterprise Workstation Extension 12 : zypper in -t patch SUSE-SLE-WE-12-2016-137=1 SUSE Linux Enterprise Software Development Kit 12 : zypper in -t patch SUSE-SLE-SDK-12-2016-137=1 SUSE Linux Enterprise Server 12 : zypper in -t patch SUSE-SLE-SERVER-12-2016-137=1 SUSE Linux Enterprise Module for Public Cloud 12 : zypper in -t patch SUSE-SLE-Module-Public-Cloud-12-2016-137=1 SUSE Linux Enterprise Live Patching 12 : zypper in -t patch SUSE-SLE-Live-Patching-12-2016-137=1 SUSE Linux Enterprise Desktop 12 : zypper in -t patch SUSE-SLE-DESKTOP-12-2016-137=1 To bring your system up-to-date, use 'zypper patch'." ); script_set_cvss_base_vector("CVSS2#AV:L/AC:L/Au:N/C:C/I:C/A:C"); script_set_cvss_temporal_vector("CVSS2#E:H/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:H/RL:O/RC:C"); script_set_attribute(attribute:"exploitability_ease", value:"Exploits are available"); script_set_attribute(attribute:"exploit_available", value:"true"); script_set_attribute(attribute:"exploit_framework_core", value:"true"); script_set_attribute(attribute:"exploited_by_malware", value:"true"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:suse_linux:kernel-default"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:suse_linux:kernel-default-base"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:suse_linux:kernel-default-base-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:suse_linux:kernel-default-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:suse_linux:kernel-default-debugsource"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:suse_linux:kernel-default-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:suse_linux:kernel-default-extra"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:suse_linux:kernel-default-extra-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:suse_linux:kernel-default-man"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:suse_linux:kernel-syms"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:suse_linux:kernel-xen"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:suse_linux:kernel-xen-base"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:suse_linux:kernel-xen-base-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:suse_linux:kernel-xen-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:suse_linux:kernel-xen-debugsource"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:suse_linux:kernel-xen-devel"); script_set_attribute(attribute:"cpe", value:"cpe:/o:novell:suse_linux:12"); script_set_attribute(attribute:"vuln_publication_date", value:"2016/02/08"); script_set_attribute(attribute:"patch_publication_date", value:"2016/01/22"); script_set_attribute(attribute:"plugin_publication_date", value:"2016/01/25"); script_set_attribute(attribute:"generated_plugin", value:"current"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_copyright(english:"This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof."); script_family(english:"SuSE Local Security Checks"); script_dependencies("ssh_get_info.nasl"); script_require_keys("Host/local_checks_enabled", "Host/cpu", "Host/SuSE/release", "Host/SuSE/rpm-list"); exit(0); } include("audit.inc"); include("global_settings.inc"); include("rpm.inc"); if (!get_kb_item("Host/local_checks_enabled")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); release = get_kb_item("Host/SuSE/release"); if (isnull(release) || release !~ "^(SLED|SLES)") audit(AUDIT_OS_NOT, "SUSE"); os_ver = pregmatch(pattern: "^(SLE(S|D)\d+)", string:release); if (isnull(os_ver)) audit(AUDIT_UNKNOWN_APP_VER, "SUSE"); os_ver = os_ver[1]; if (! preg(pattern:"^(SLED12|SLES12)$", string:os_ver)) audit(AUDIT_OS_NOT, "SUSE SLED12 / SLES12", "SUSE " + os_ver); if (!get_kb_item("Host/SuSE/rpm-list")) audit(AUDIT_PACKAGE_LIST_MISSING); cpu = get_kb_item("Host/cpu"); if (isnull(cpu)) audit(AUDIT_UNKNOWN_ARCH); if (cpu !~ "^i[3-6]86$" && "x86_64" >!< cpu && "s390x" >!< cpu) audit(AUDIT_LOCAL_CHECKS_NOT_IMPLEMENTED, "SUSE " + os_ver, cpu); sp = get_kb_item("Host/SuSE/patchlevel"); if (isnull(sp)) sp = "0"; if (os_ver == "SLES12" && (! preg(pattern:"^(0)$", string:sp))) audit(AUDIT_OS_NOT, "SLES12 SP0", os_ver + " SP" + sp); if (os_ver == "SLED12" && (! preg(pattern:"^(0)$", string:sp))) audit(AUDIT_OS_NOT, "SLED12 SP0", os_ver + " SP" + sp); flag = 0; if (rpm_check(release:"SLES12", sp:"0", cpu:"x86_64", reference:"kernel-xen-3.12.51-52.39.1")) flag++; if (rpm_check(release:"SLES12", sp:"0", cpu:"x86_64", reference:"kernel-xen-base-3.12.51-52.39.1")) flag++; if (rpm_check(release:"SLES12", sp:"0", cpu:"x86_64", reference:"kernel-xen-base-debuginfo-3.12.51-52.39.1")) flag++; if (rpm_check(release:"SLES12", sp:"0", cpu:"x86_64", reference:"kernel-xen-debuginfo-3.12.51-52.39.1")) flag++; if (rpm_check(release:"SLES12", sp:"0", cpu:"x86_64", reference:"kernel-xen-debugsource-3.12.51-52.39.1")) flag++; if (rpm_check(release:"SLES12", sp:"0", cpu:"x86_64", reference:"kernel-xen-devel-3.12.51-52.39.1")) flag++; if (rpm_check(release:"SLES12", sp:"0", cpu:"s390x", reference:"kernel-default-man-3.12.51-52.39.1")) flag++; if (rpm_check(release:"SLES12", sp:"0", reference:"kernel-default-3.12.51-52.39.1")) flag++; if (rpm_check(release:"SLES12", sp:"0", reference:"kernel-default-base-3.12.51-52.39.1")) flag++; if (rpm_check(release:"SLES12", sp:"0", reference:"kernel-default-base-debuginfo-3.12.51-52.39.1")) flag++; if (rpm_check(release:"SLES12", sp:"0", reference:"kernel-default-debuginfo-3.12.51-52.39.1")) flag++; if (rpm_check(release:"SLES12", sp:"0", reference:"kernel-default-debugsource-3.12.51-52.39.1")) flag++; if (rpm_check(release:"SLES12", sp:"0", reference:"kernel-default-devel-3.12.51-52.39.1")) flag++; if (rpm_check(release:"SLES12", sp:"0", reference:"kernel-syms-3.12.51-52.39.1")) flag++; if (rpm_check(release:"SLED12", sp:"0", cpu:"x86_64", reference:"kernel-default-3.12.51-52.39.1")) flag++; if (rpm_check(release:"SLED12", sp:"0", cpu:"x86_64", reference:"kernel-default-debuginfo-3.12.51-52.39.1")) flag++; if (rpm_check(release:"SLED12", sp:"0", cpu:"x86_64", reference:"kernel-default-debugsource-3.12.51-52.39.1")) flag++; if (rpm_check(release:"SLED12", sp:"0", cpu:"x86_64", reference:"kernel-default-devel-3.12.51-52.39.1")) flag++; if (rpm_check(release:"SLED12", sp:"0", cpu:"x86_64", reference:"kernel-default-extra-3.12.51-52.39.1")) flag++; if (rpm_check(release:"SLED12", sp:"0", cpu:"x86_64", reference:"kernel-default-extra-debuginfo-3.12.51-52.39.1")) flag++; if (rpm_check(release:"SLED12", sp:"0", cpu:"x86_64", reference:"kernel-syms-3.12.51-52.39.1")) flag++; if (rpm_check(release:"SLED12", sp:"0", cpu:"x86_64", reference:"kernel-xen-3.12.51-52.39.1")) flag++; if (rpm_check(release:"SLED12", sp:"0", cpu:"x86_64", reference:"kernel-xen-debuginfo-3.12.51-52.39.1")) flag++; if (rpm_check(release:"SLED12", sp:"0", cpu:"x86_64", reference:"kernel-xen-debugsource-3.12.51-52.39.1")) flag++; if (rpm_check(release:"SLED12", sp:"0", cpu:"x86_64", reference:"kernel-xen-devel-3.12.51-52.39.1")) flag++; if (flag) { if (report_verbosity > 0) security_hole(port:0, extra:rpm_report_get()); else security_hole(0); exit(0); } else { tested = pkg_tests_get(); if (tested) audit(AUDIT_PACKAGE_NOT_AFFECTED, tested); else audit(AUDIT_PACKAGE_NOT_INSTALLED, "kernel"); }NASL family Ubuntu Local Security Checks NASL id UBUNTU_USN-2871-2.NASL description Yevgeny Pats discovered that the session keyring implementation in the Linux kernel did not properly reference count when joining an existing session keyring. A local attacker could use this to cause a denial of service (system crash) or possibly execute arbitrary code with administrative privileges. Note that Tenable Network Security has extracted the preceding description block directly from the Ubuntu security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 88013 published 2016-01-20 reporter Ubuntu Security Notice (C) 2016-2019 Canonical, Inc. / NASL script (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/88013 title Ubuntu 14.04 LTS : linux-lts-vivid vulnerability (USN-2871-2) code # # (C) Tenable Network Security, Inc. # # The descriptive text and package checks in this plugin were # extracted from Ubuntu Security Notice USN-2871-2. The text # itself is copyright (C) Canonical, Inc. See # <http://www.ubuntu.com/usn/>. Ubuntu(R) is a registered # trademark of Canonical, Inc. # include("compat.inc"); if (description) { script_id(88013); script_version("2.13"); script_cvs_date("Date: 2019/09/18 12:31:45"); script_cve_id("CVE-2016-0728"); script_xref(name:"USN", value:"2871-2"); script_name(english:"Ubuntu 14.04 LTS : linux-lts-vivid vulnerability (USN-2871-2)"); script_summary(english:"Checks dpkg output for updated packages."); script_set_attribute( attribute:"synopsis", value: "The remote Ubuntu host is missing one or more security-related patches." ); script_set_attribute( attribute:"description", value: "Yevgeny Pats discovered that the session keyring implementation in the Linux kernel did not properly reference count when joining an existing session keyring. A local attacker could use this to cause a denial of service (system crash) or possibly execute arbitrary code with administrative privileges. Note that Tenable Network Security has extracted the preceding description block directly from the Ubuntu security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues." ); script_set_attribute( attribute:"see_also", value:"https://usn.ubuntu.com/2871-2/" ); script_set_attribute( attribute:"solution", value: "Update the affected linux-image-3.19-generic, linux-image-3.19-generic-lpae and / or linux-image-3.19-lowlatency packages." ); script_set_cvss_base_vector("CVSS2#AV:L/AC:L/Au:N/C:C/I:C/A:C"); script_set_cvss_temporal_vector("CVSS2#E:H/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:H/RL:O/RC:C"); script_set_attribute(attribute:"exploitability_ease", value:"Exploits are available"); script_set_attribute(attribute:"exploit_available", value:"true"); script_set_attribute(attribute:"exploit_framework_core", value:"true"); script_set_attribute(attribute:"exploited_by_malware", value:"true"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:canonical:ubuntu_linux:linux-image-3.19-generic"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:canonical:ubuntu_linux:linux-image-3.19-generic-lpae"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:canonical:ubuntu_linux:linux-image-3.19-lowlatency"); script_set_attribute(attribute:"cpe", value:"cpe:/o:canonical:ubuntu_linux:14.04"); script_set_attribute(attribute:"vuln_publication_date", value:"2016/02/08"); script_set_attribute(attribute:"patch_publication_date", value:"2016/01/19"); script_set_attribute(attribute:"plugin_publication_date", value:"2016/01/20"); script_set_attribute(attribute:"generated_plugin", value:"current"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_copyright(english:"Ubuntu Security Notice (C) 2016-2019 Canonical, Inc. / NASL script (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof."); script_family(english:"Ubuntu Local Security Checks"); script_dependencies("ssh_get_info.nasl", "linux_alt_patch_detect.nasl"); script_require_keys("Host/cpu", "Host/Ubuntu", "Host/Ubuntu/release", "Host/Debian/dpkg-l"); exit(0); } include("audit.inc"); include("ubuntu.inc"); include("ksplice.inc"); if ( ! get_kb_item("Host/local_checks_enabled") ) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); release = get_kb_item("Host/Ubuntu/release"); if ( isnull(release) ) audit(AUDIT_OS_NOT, "Ubuntu"); release = chomp(release); if (! preg(pattern:"^(14\.04)$", string:release)) audit(AUDIT_OS_NOT, "Ubuntu 14.04", "Ubuntu " + release); if ( ! get_kb_item("Host/Debian/dpkg-l") ) audit(AUDIT_PACKAGE_LIST_MISSING); cpu = get_kb_item("Host/cpu"); if (isnull(cpu)) audit(AUDIT_UNKNOWN_ARCH); if ("x86_64" >!< cpu && cpu !~ "^i[3-6]86$") audit(AUDIT_LOCAL_CHECKS_NOT_IMPLEMENTED, "Ubuntu", cpu); if (get_one_kb_item("Host/ksplice/kernel-cves")) { rm_kb_item(name:"Host/uptrack-uname-r"); cve_list = make_list("CVE-2016-0728"); if (ksplice_cves_check(cve_list)) { audit(AUDIT_PATCH_INSTALLED, "KSplice hotfix for USN-2871-2"); } else { _ubuntu_report = ksplice_reporting_text(); } } flag = 0; if (ubuntu_check(osver:"14.04", pkgname:"linux-image-3.19.0-47-generic", pkgver:"3.19.0-47.53~14.04.1")) flag++; if (ubuntu_check(osver:"14.04", pkgname:"linux-image-3.19.0-47-generic-lpae", pkgver:"3.19.0-47.53~14.04.1")) flag++; if (ubuntu_check(osver:"14.04", pkgname:"linux-image-3.19.0-47-lowlatency", pkgver:"3.19.0-47.53~14.04.1")) flag++; if (flag) { security_report_v4( port : 0, severity : SECURITY_HOLE, extra : ubuntu_report_get() ); exit(0); } else { tested = ubuntu_pkg_tests_get(); if (tested) audit(AUDIT_PACKAGE_NOT_AFFECTED, tested); else audit(AUDIT_PACKAGE_NOT_INSTALLED, "linux-image-3.19-generic / linux-image-3.19-generic-lpae / etc"); }NASL family Fedora Local Security Checks NASL id FEDORA_2016-B59FD603BE.NASL description Backported i915, networking, and nouveau fixes tagged for stable from 4.4 upstream. Assorted fixes elsewhere. ---- A few bug fixes and backports of all the i915 patches queued for stable from 4.4. ---- A number of fixes across the tree Note that Tenable Network Security has extracted the preceding description block directly from the Fedora security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-05 modified 2016-03-04 plugin id 89600 published 2016-03-04 reporter This script is Copyright (C) 2016-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/89600 title Fedora 23 : kernel-4.3.3-303.fc23 (2016-b59fd603be) code #%NASL_MIN_LEVEL 80502 # # (C) Tenable Network Security, Inc. # # The descriptive text and package checks in this plugin were # extracted from Fedora Security Advisory 2016-b59fd603be. # include("compat.inc"); if (description) { script_id(89600); script_version("1.6"); script_set_attribute(attribute:"plugin_modification_date", value:"2020/06/04"); script_cve_id("CVE-2015-7513", "CVE-2015-7566", "CVE-2016-0728"); script_xref(name:"FEDORA", value:"2016-b59fd603be"); script_name(english:"Fedora 23 : kernel-4.3.3-303.fc23 (2016-b59fd603be)"); script_summary(english:"Checks rpm output for the updated package."); script_set_attribute( attribute:"synopsis", value:"The remote Fedora host is missing a security update." ); script_set_attribute( attribute:"description", value: "Backported i915, networking, and nouveau fixes tagged for stable from 4.4 upstream. Assorted fixes elsewhere. ---- A few bug fixes and backports of all the i915 patches queued for stable from 4.4. ---- A number of fixes across the tree Note that Tenable Network Security has extracted the preceding description block directly from the Fedora security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues." ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.redhat.com/show_bug.cgi?id=1284847" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.redhat.com/show_bug.cgi?id=1296466" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.redhat.com/show_bug.cgi?id=1297475" ); # https://lists.fedoraproject.org/pipermail/package-announce/2016-January/176194.html script_set_attribute( attribute:"see_also", value:"http://www.nessus.org/u?6c84e8fb" ); script_set_attribute( attribute:"solution", value:"Update the affected kernel package." ); script_set_cvss_base_vector("CVSS2#AV:L/AC:L/Au:N/C:C/I:C/A:C"); script_set_cvss_temporal_vector("CVSS2#E:H/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:H/RL:O/RC:C"); script_set_attribute(attribute:"exploitability_ease", value:"Exploits are available"); script_set_attribute(attribute:"exploit_available", value:"true"); script_set_attribute(attribute:"exploit_framework_core", value:"true"); script_set_attribute(attribute:"exploited_by_malware", value:"true"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:fedoraproject:fedora:kernel"); script_set_attribute(attribute:"cpe", value:"cpe:/o:fedoraproject:fedora:23"); script_set_attribute(attribute:"patch_publication_date", value:"2016/01/26"); script_set_attribute(attribute:"plugin_publication_date", value:"2016/03/04"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_copyright(english:"This script is Copyright (C) 2016-2020 and is owned by Tenable, Inc. or an Affiliate thereof."); script_family(english:"Fedora Local Security Checks"); script_dependencies("ssh_get_info.nasl"); script_require_keys("Host/local_checks_enabled", "Host/RedHat/release", "Host/RedHat/rpm-list"); exit(0); } include("audit.inc"); include("global_settings.inc"); include("rpm.inc"); if (!get_kb_item("Host/local_checks_enabled")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); release = get_kb_item("Host/RedHat/release"); if (isnull(release) || "Fedora" >!< release) audit(AUDIT_OS_NOT, "Fedora"); os_ver = eregmatch(pattern: "Fedora.*release ([0-9]+)", string:release); if (isnull(os_ver)) audit(AUDIT_UNKNOWN_APP_VER, "Fedora"); os_ver = os_ver[1]; if (! ereg(pattern:"^23([^0-9]|$)", string:os_ver)) audit(AUDIT_OS_NOT, "Fedora 23.x", "Fedora " + os_ver); if (!get_kb_item("Host/RedHat/rpm-list")) audit(AUDIT_PACKAGE_LIST_MISSING); cpu = get_kb_item("Host/cpu"); if (isnull(cpu)) audit(AUDIT_UNKNOWN_ARCH); if ("x86_64" >!< cpu && cpu !~ "^i[3-6]86$") audit(AUDIT_LOCAL_CHECKS_NOT_IMPLEMENTED, "Fedora", cpu); flag = 0; if (rpm_check(release:"FC23", reference:"kernel-4.3.3-303.fc23")) flag++; if (flag) { if (report_verbosity > 0) security_hole(port:0, extra:rpm_report_get()); else security_hole(0); exit(0); } else { tested = pkg_tests_get(); if (tested) audit(AUDIT_PACKAGE_NOT_AFFECTED, tested); else audit(AUDIT_PACKAGE_NOT_INSTALLED, "kernel"); }NASL family Huawei Local Security Checks NASL id EULEROS_SA-2019-1491.NASL description According to the versions of the kernel packages installed, the EulerOS Virtualization installation on the remote host is affected by the following vulnerabilities : - A use-after-free flaw was found in the way the Linux kernel last seen 2020-03-19 modified 2019-05-13 plugin id 124815 published 2019-05-13 reporter This script is Copyright (C) 2019-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/124815 title EulerOS Virtualization 3.0.1.0 : kernel (EulerOS-SA-2019-1491) code # # (C) Tenable Network Security, Inc. # include("compat.inc"); if (description) { script_id(124815); script_version("1.5"); script_set_attribute(attribute:"plugin_modification_date", value:"2020/03/19"); script_cve_id( "CVE-2016-0728", "CVE-2016-0758", "CVE-2016-0821", "CVE-2016-0823", "CVE-2016-10044", "CVE-2016-10088", "CVE-2016-10200", "CVE-2016-10208", "CVE-2016-10229", "CVE-2016-1575", "CVE-2016-1576", "CVE-2016-2053", "CVE-2016-2069", "CVE-2016-2070", "CVE-2016-2117", "CVE-2016-2184", "CVE-2016-2185", "CVE-2016-2186", "CVE-2016-2187", "CVE-2016-2188", "CVE-2016-2384", "CVE-2016-2543", "CVE-2016-2544" ); script_name(english:"EulerOS Virtualization 3.0.1.0 : kernel (EulerOS-SA-2019-1491)"); script_summary(english:"Checks the rpm output for the updated packages."); script_set_attribute(attribute:"synopsis", value: "The remote EulerOS Virtualization host is missing multiple security updates."); script_set_attribute(attribute:"description", value: "According to the versions of the kernel packages installed, the EulerOS Virtualization installation on the remote host is affected by the following vulnerabilities : - A use-after-free flaw was found in the way the Linux kernel's key management subsystem handled keyring object reference counting in certain error path of the join_session_keyring() function. A local, unprivileged user could use this flaw to escalate their privileges on the system.(CVE-2016-0728) - A flaw was found in the way the Linux kernel's ASN.1 DER decoder processed certain certificate files with tags of indefinite length. A local, unprivileged user could use a specially crafted X.509 certificate DER file to crash the system or, potentially, escalate their privileges on the system.(CVE-2016-0758) - The LIST_POISON feature in include/linux/poison.h in the Linux kernel before 4.3, as used in Android 6.0.1 before 2016-03-01, does not properly consider the relationship to the mmap_min_addr value, which makes it easier for attackers to bypass a poison-pointer protection mechanism by triggering the use of an uninitialized list entry, aka Android internal bug 26186802, a different vulnerability than CVE-2015-3636.(CVE-2016-0821) - The pagemap_open function in fs/proc/task_mmu.c in the Linux kernel before 3.19.3, as used in Android 6.0.1 before 2016-03-01, allows local users to obtain sensitive physical-address information by reading a pagemap file, aka Android internal bug 25739721.(CVE-2016-0823) - The aio_mount function in fs/aio.c in the Linux kernel does not properly restrict execute access, which makes it easier for local users to bypass intended SELinux W^X policy restrictions.(CVE-2016-10044) - It was found that the fix for CVE-2016-9576 was incomplete: the Linux kernel's sg implementation did not properly restrict write operations in situations where the KERNEL_DS option is set. A local attacker to read or write to arbitrary kernel memory locations or cause a denial of service (use-after-free) by leveraging write access to a /dev/sg device.(CVE-2016-10088) - A use-after-free flaw was found in the Linux kernel which enables a race condition in the L2TPv3 IP Encapsulation feature. A local user could use this flaw to escalate their privileges or crash the system.(CVE-2016-10200) - Mounting a crafted EXT4 image read-only leads to an attacker controlled memory corruption and SLAB-Out-of-Bounds reads.(CVE-2016-10208) - The Linux kernel allows remote attackers to execute arbitrary code via UDP traffic that triggers an unsafe second checksum calculation during execution of a recv system call with the MSG_PEEK flag. This may create a kernel panic or memory corruption leading to privilege escalation.(CVE-2016-10229) - The overlayfs implementation in the Linux kernel through 4.5.2 does not properly maintain POSIX ACL xattr data, which allows local users to gain privileges by leveraging a group-writable setgid directory.(CVE-2016-1575) - The overlayfs implementation in the Linux kernel through 4.5.2 does not properly restrict the mount namespace, which allows local users to gain privileges by mounting an overlayfs filesystem on top of a FUSE filesystem, and then executing a crafted setuid program.(CVE-2016-1576) - A syntax vulnerability was discovered in the kernel's ASN1.1 DER decoder, which could lead to memory corruption or a complete local denial of service through x509 certificate DER files. A local system user could use a specially created key file to trigger BUG_ON() in the public_key_verify_signature() function (crypto/asymmetric_keys/public_key.c), to cause a kernel panic and crash the system.(CVE-2016-2053) - A flaw was discovered in the way the Linux kernel dealt with paging structures. When the kernel invalidated a paging structure that was not in use locally, it could, in principle, race against another CPU that is switching to a process that uses the paging structure in question. A local user could use a thread running with a stale cached virtual-i1/4zphysical translation to potentially escalate their privileges if the translation in question were writable and the physical page got reused for something critical (for example, a page table).(CVE-2016-2069) - A divide-by-zero vulnerability was found in a way the kernel processes TCP connections. The error can occur if a connection starts another cwnd reduction phase by setting tp-i1/4zprior_cwnd to the current cwnd (0) in tcp_init_cwnd_reduction(). A remote, unauthenticated attacker could use this flaw to crash the kernel (denial of service).(CVE-2016-2070) - It was discovered that the atl2_probe() function in the Atheros L2 Ethernet driver in the Linux kernel incorrectly enabled scatter/gather I/O. A remote attacker could use this flaw to obtain potentially sensitive information from the kernel memory.(CVE-2016-2117) - The create_fixed_stream_quirk function in sound/usb/quirks.c in the snd-usb-audio driver in the Linux kernel before 4.5.1 allows physically proximate attackers to cause a denial of service (NULL pointer dereference or double free, and system crash) via a crafted endpoints value in a USB device descriptor.(CVE-2016-2184) - The ati_remote2_probe function in drivers/input/misc/ati_remote2.c in the Linux kernel before 4.5.1 allows physically proximate attackers to cause a denial of service (NULL pointer dereference and system crash) via a crafted endpoints value in a USB device descriptor.(CVE-2016-2185) - The powermate_probe function in drivers/input/misc/powermate.c in the Linux kernel before 4.5.1 allows physically proximate attackers to cause a denial of service (NULL pointer dereference and system crash) via a crafted endpoints value in a USB device descriptor.(CVE-2016-2186) - The gtco_probe function in drivers/input/tablet/gtco.c in the Linux kernel through 4.5.2 allows physically proximate attackers to cause a denial of service (NULL pointer dereference and system crash) via a crafted endpoints value in a USB device descriptor.(CVE-2016-2187) - The iowarrior_probe function in drivers/usb/misc/iowarrior.c in the Linux kernel before 4.5.1 allows physically proximate attackers to cause a denial of service (NULL pointer dereference and system crash) via a crafted endpoints value in a USB device descriptor.(CVE-2016-2188) - A flaw was found in the USB-MIDI Linux kernel driver: a double-free error could be triggered for the 'umidi' object. An attacker with physical access to the system could use this flaw to escalate their privileges.(CVE-2016-2384) - The snd_seq_ioctl_remove_events function in sound/core/seq/seq_clientmgr.c in the Linux kernel before 4.4.1 does not verify FIFO assignment before proceeding with FIFO clearing, which allows local users to cause a denial of service (NULL pointer dereference and OOPS) via a crafted ioctl call.(CVE-2016-2543) - Race condition in the queue_delete function in sound/core/seq/seq_queue.c in the Linux kernel before 4.4.1 allows local users to cause a denial of service (use-after-free and system crash) by making an ioctl call at a certain time.(CVE-2016-2544) Note that Tenable Network Security has extracted the preceding description block directly from the EulerOS security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues."); # https://developer.huaweicloud.com/ict/en/site-euleros/euleros/security-advisories/EulerOS-SA-2019-1491 script_set_attribute(attribute:"see_also", value:"http://www.nessus.org/u?2d818220"); script_set_attribute(attribute:"solution", value: "Update the affected kernel packages."); script_set_cvss_base_vector("CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:C"); script_set_cvss_temporal_vector("CVSS2#E:H/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:H/RL:O/RC:C"); script_set_attribute(attribute:"exploitability_ease", value:"Exploits are available"); script_set_attribute(attribute:"exploit_available", value:"true"); script_set_attribute(attribute:"exploit_framework_core", value:"true"); script_set_attribute(attribute:"exploited_by_malware", value:"true"); script_set_attribute(attribute:"patch_publication_date", value:"2019/05/09"); script_set_attribute(attribute:"plugin_publication_date", value:"2019/05/13"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:huawei:euleros:kernel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:huawei:euleros:kernel-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:huawei:euleros:kernel-headers"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:huawei:euleros:kernel-tools"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:huawei:euleros:kernel-tools-libs"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:huawei:euleros:kernel-tools-libs-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:huawei:euleros:perf"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:huawei:euleros:python-perf"); script_set_attribute(attribute:"cpe", value:"cpe:/o:huawei:euleros:uvp:3.0.1.0"); script_set_attribute(attribute:"generated_plugin", value:"current"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_family(english:"Huawei Local Security Checks"); script_copyright(english:"This script is Copyright (C) 2019-2020 and is owned by Tenable, Inc. or an Affiliate thereof."); script_dependencies("ssh_get_info.nasl"); script_require_keys("Host/local_checks_enabled", "Host/cpu", "Host/EulerOS/release", "Host/EulerOS/rpm-list", "Host/EulerOS/uvp_version"); exit(0); } include("audit.inc"); include("global_settings.inc"); include("rpm.inc"); if (!get_kb_item("Host/local_checks_enabled")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); release = get_kb_item("Host/EulerOS/release"); if (isnull(release) || release !~ "^EulerOS") audit(AUDIT_OS_NOT, "EulerOS"); uvp = get_kb_item("Host/EulerOS/uvp_version"); if (uvp != "3.0.1.0") audit(AUDIT_OS_NOT, "EulerOS Virtualization 3.0.1.0"); if (!get_kb_item("Host/EulerOS/rpm-list")) audit(AUDIT_PACKAGE_LIST_MISSING); cpu = get_kb_item("Host/cpu"); if (isnull(cpu)) audit(AUDIT_UNKNOWN_ARCH); if ("x86_64" >!< cpu && cpu !~ "^i[3-6]86$" && "aarch64" >!< cpu) audit(AUDIT_LOCAL_CHECKS_NOT_IMPLEMENTED, "EulerOS", cpu); if ("x86_64" >!< cpu && cpu !~ "^i[3-6]86$") audit(AUDIT_ARCH_NOT, "i686 / x86_64", cpu); flag = 0; pkgs = ["kernel-3.10.0-862.14.1.6_42", "kernel-devel-3.10.0-862.14.1.6_42", "kernel-headers-3.10.0-862.14.1.6_42", "kernel-tools-3.10.0-862.14.1.6_42", "kernel-tools-libs-3.10.0-862.14.1.6_42", "kernel-tools-libs-devel-3.10.0-862.14.1.6_42", "perf-3.10.0-862.14.1.6_42", "python-perf-3.10.0-862.14.1.6_42"]; foreach (pkg in pkgs) if (rpm_check(release:"EulerOS-2.0", reference:pkg)) flag++; if (flag) { security_report_v4( port : 0, severity : SECURITY_HOLE, extra : rpm_report_get() ); exit(0); } else { tested = pkg_tests_get(); if (tested) audit(AUDIT_PACKAGE_NOT_AFFECTED, tested); else audit(AUDIT_PACKAGE_NOT_INSTALLED, "kernel"); }NASL family Red Hat Local Security Checks NASL id REDHAT-RHSA-2016-0064.NASL description Updated kernel packages that fix one security issue are now available for Red Hat Enterprise Linux 7. Red Hat Product Security has rated this update as having Important security impact. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available from the CVE link in the References section. The kernel packages contain the Linux kernel, the core of any Linux operating system. * A use-after-free flaw was found in the way the Linux kernel last seen 2020-06-01 modified 2020-06-02 plugin id 88173 published 2016-01-26 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/88173 title RHEL 7 : kernel (RHSA-2016:0064) code # # (C) Tenable Network Security, Inc. # # The descriptive text and package checks in this plugin were # extracted from Red Hat Security Advisory RHSA-2016:0064. The text # itself is copyright (C) Red Hat, Inc. # include("compat.inc"); if (description) { script_id(88173); script_version("2.16"); script_cvs_date("Date: 2019/10/24 15:35:41"); script_cve_id("CVE-2016-0728"); script_xref(name:"RHSA", value:"2016:0064"); script_name(english:"RHEL 7 : kernel (RHSA-2016:0064)"); script_summary(english:"Checks the rpm output for the updated packages"); script_set_attribute( attribute:"synopsis", value:"The remote Red Hat host is missing one or more security updates." ); script_set_attribute( attribute:"description", value: "Updated kernel packages that fix one security issue are now available for Red Hat Enterprise Linux 7. Red Hat Product Security has rated this update as having Important security impact. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available from the CVE link in the References section. The kernel packages contain the Linux kernel, the core of any Linux operating system. * A use-after-free flaw was found in the way the Linux kernel's key management subsystem handled keyring object reference counting in certain error path of the join_session_keyring() function. A local, unprivileged user could use this flaw to escalate their privileges on the system. (CVE-2016-0728, Important) Red Hat would like to thank the Perception Point research team for reporting this issue. All kernel users are advised to upgrade to these updated packages, which contain a backported patch to correct this issue. The system must be rebooted for this update to take effect." ); script_set_attribute( attribute:"see_also", value:"https://access.redhat.com/errata/RHSA-2016:0064" ); script_set_attribute( attribute:"see_also", value:"https://access.redhat.com/security/cve/cve-2016-0728" ); script_set_attribute(attribute:"solution", value:"Update the affected packages."); script_set_cvss_base_vector("CVSS2#AV:L/AC:L/Au:N/C:C/I:C/A:C"); script_set_cvss_temporal_vector("CVSS2#E:H/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:H/RL:O/RC:C"); script_set_attribute(attribute:"exploitability_ease", value:"Exploits are available"); script_set_attribute(attribute:"exploit_available", value:"true"); script_set_attribute(attribute:"exploit_framework_core", value:"true"); script_set_attribute(attribute:"exploited_by_malware", value:"true"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:kernel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:kernel-abi-whitelists"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:kernel-debug"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:kernel-debug-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:kernel-debug-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:kernel-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:kernel-debuginfo-common-s390x"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:kernel-debuginfo-common-x86_64"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:kernel-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:kernel-doc"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:kernel-headers"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:kernel-kdump"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:kernel-kdump-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:kernel-kdump-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:kernel-tools"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:kernel-tools-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:kernel-tools-libs"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:kernel-tools-libs-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:perf"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:perf-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:python-perf"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:python-perf-debuginfo"); script_set_attribute(attribute:"cpe", value:"cpe:/o:redhat:enterprise_linux:7"); script_set_attribute(attribute:"cpe", value:"cpe:/o:redhat:enterprise_linux:7.2"); script_set_attribute(attribute:"cpe", value:"cpe:/o:redhat:enterprise_linux:7.3"); script_set_attribute(attribute:"cpe", value:"cpe:/o:redhat:enterprise_linux:7.4"); script_set_attribute(attribute:"cpe", value:"cpe:/o:redhat:enterprise_linux:7.5"); script_set_attribute(attribute:"cpe", value:"cpe:/o:redhat:enterprise_linux:7.6"); script_set_attribute(attribute:"cpe", value:"cpe:/o:redhat:enterprise_linux:7.7"); script_set_attribute(attribute:"vuln_publication_date", value:"2016/02/08"); script_set_attribute(attribute:"patch_publication_date", value:"2016/01/25"); script_set_attribute(attribute:"plugin_publication_date", value:"2016/01/26"); script_set_attribute(attribute:"generated_plugin", value:"current"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_copyright(english:"This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof."); script_family(english:"Red Hat Local Security Checks"); script_dependencies("ssh_get_info.nasl", "linux_alt_patch_detect.nasl"); script_require_keys("Host/local_checks_enabled", "Host/RedHat/release", "Host/RedHat/rpm-list", "Host/cpu"); exit(0); } include("audit.inc"); include("global_settings.inc"); include("misc_func.inc"); include("rpm.inc"); include("ksplice.inc"); if (!get_kb_item("Host/local_checks_enabled")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); release = get_kb_item("Host/RedHat/release"); if (isnull(release) || "Red Hat" >!< release) audit(AUDIT_OS_NOT, "Red Hat"); os_ver = pregmatch(pattern: "Red Hat Enterprise Linux.*release ([0-9]+(\.[0-9]+)?)", string:release); if (isnull(os_ver)) audit(AUDIT_UNKNOWN_APP_VER, "Red Hat"); os_ver = os_ver[1]; if (! preg(pattern:"^7([^0-9]|$)", string:os_ver)) audit(AUDIT_OS_NOT, "Red Hat 7.x", "Red Hat " + os_ver); if (!get_kb_item("Host/RedHat/rpm-list")) audit(AUDIT_PACKAGE_LIST_MISSING); cpu = get_kb_item("Host/cpu"); if (isnull(cpu)) audit(AUDIT_UNKNOWN_ARCH); if ("x86_64" >!< cpu && cpu !~ "^i[3-6]86$" && "s390" >!< cpu) audit(AUDIT_LOCAL_CHECKS_NOT_IMPLEMENTED, "Red Hat", cpu); if (get_one_kb_item("Host/ksplice/kernel-cves")) { rm_kb_item(name:"Host/uptrack-uname-r"); cve_list = make_list("CVE-2016-0728"); if (ksplice_cves_check(cve_list)) { audit(AUDIT_PATCH_INSTALLED, "KSplice hotfix for RHSA-2016:0064"); } else { __rpm_report = ksplice_reporting_text(); } } yum_updateinfo = get_kb_item("Host/RedHat/yum-updateinfo"); if (!empty_or_null(yum_updateinfo)) { rhsa = "RHSA-2016:0064"; yum_report = redhat_generate_yum_updateinfo_report(rhsa:rhsa); if (!empty_or_null(yum_report)) { security_report_v4( port : 0, severity : SECURITY_HOLE, extra : yum_report ); exit(0); } else { audit_message = "affected by Red Hat security advisory " + rhsa; audit(AUDIT_OS_NOT, audit_message); } } else { flag = 0; if (rpm_check(release:"RHEL7", cpu:"s390x", reference:"kernel-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"RHEL7", cpu:"x86_64", reference:"kernel-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"RHEL7", reference:"kernel-abi-whitelists-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"RHEL7", cpu:"s390x", reference:"kernel-debug-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"RHEL7", cpu:"x86_64", reference:"kernel-debug-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"RHEL7", cpu:"s390x", reference:"kernel-debug-debuginfo-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"RHEL7", cpu:"x86_64", reference:"kernel-debug-debuginfo-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"RHEL7", cpu:"s390x", reference:"kernel-debug-devel-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"RHEL7", cpu:"x86_64", reference:"kernel-debug-devel-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"RHEL7", cpu:"s390x", reference:"kernel-debuginfo-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"RHEL7", cpu:"x86_64", reference:"kernel-debuginfo-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"RHEL7", cpu:"s390x", reference:"kernel-debuginfo-common-s390x-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"RHEL7", cpu:"x86_64", reference:"kernel-debuginfo-common-x86_64-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"RHEL7", cpu:"s390x", reference:"kernel-devel-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"RHEL7", cpu:"x86_64", reference:"kernel-devel-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"RHEL7", reference:"kernel-doc-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"RHEL7", cpu:"s390x", reference:"kernel-headers-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"RHEL7", cpu:"x86_64", reference:"kernel-headers-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"RHEL7", cpu:"s390x", reference:"kernel-kdump-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"RHEL7", cpu:"s390x", reference:"kernel-kdump-debuginfo-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"RHEL7", cpu:"s390x", reference:"kernel-kdump-devel-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"RHEL7", cpu:"x86_64", reference:"kernel-tools-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"RHEL7", cpu:"x86_64", reference:"kernel-tools-debuginfo-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"RHEL7", cpu:"x86_64", reference:"kernel-tools-libs-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"RHEL7", cpu:"x86_64", reference:"kernel-tools-libs-devel-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"RHEL7", cpu:"s390x", reference:"perf-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"RHEL7", cpu:"x86_64", reference:"perf-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"RHEL7", cpu:"s390x", reference:"perf-debuginfo-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"RHEL7", cpu:"x86_64", reference:"perf-debuginfo-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"RHEL7", cpu:"s390x", reference:"python-perf-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"RHEL7", cpu:"x86_64", reference:"python-perf-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"RHEL7", cpu:"s390x", reference:"python-perf-debuginfo-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"RHEL7", cpu:"x86_64", reference:"python-perf-debuginfo-3.10.0-327.4.5.el7")) flag++; if (flag) { security_report_v4( port : 0, severity : SECURITY_HOLE, extra : rpm_report_get() + redhat_report_package_caveat() ); exit(0); } else { tested = pkg_tests_get(); if (tested) audit(AUDIT_PACKAGE_NOT_AFFECTED, tested); else audit(AUDIT_PACKAGE_NOT_INSTALLED, "kernel / kernel-abi-whitelists / kernel-debug / etc"); } }NASL family Ubuntu Local Security Checks NASL id UBUNTU_USN-2870-2.NASL description Yevgeny Pats discovered that the session keyring implementation in the Linux kernel did not properly reference count when joining an existing session keyring. A local attacker could use this to cause a denial of service (system crash) or possibly execute arbitrary code with administrative privileges. Note that Tenable Network Security has extracted the preceding description block directly from the Ubuntu security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 88011 published 2016-01-20 reporter Ubuntu Security Notice (C) 2016-2019 Canonical, Inc. / NASL script (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/88011 title Ubuntu 12.04 LTS : linux-lts-trusty vulnerability (USN-2870-2) code # # (C) Tenable Network Security, Inc. # # The descriptive text and package checks in this plugin were # extracted from Ubuntu Security Notice USN-2870-2. The text # itself is copyright (C) Canonical, Inc. See # <http://www.ubuntu.com/usn/>. Ubuntu(R) is a registered # trademark of Canonical, Inc. # include("compat.inc"); if (description) { script_id(88011); script_version("2.13"); script_cvs_date("Date: 2019/09/18 12:31:45"); script_cve_id("CVE-2016-0728"); script_xref(name:"USN", value:"2870-2"); script_name(english:"Ubuntu 12.04 LTS : linux-lts-trusty vulnerability (USN-2870-2)"); script_summary(english:"Checks dpkg output for updated packages."); script_set_attribute( attribute:"synopsis", value: "The remote Ubuntu host is missing one or more security-related patches." ); script_set_attribute( attribute:"description", value: "Yevgeny Pats discovered that the session keyring implementation in the Linux kernel did not properly reference count when joining an existing session keyring. A local attacker could use this to cause a denial of service (system crash) or possibly execute arbitrary code with administrative privileges. Note that Tenable Network Security has extracted the preceding description block directly from the Ubuntu security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues." ); script_set_attribute( attribute:"see_also", value:"https://usn.ubuntu.com/2870-2/" ); script_set_attribute( attribute:"solution", value: "Update the affected linux-image-3.13-generic and / or linux-image-3.13-generic-lpae packages." ); script_set_cvss_base_vector("CVSS2#AV:L/AC:L/Au:N/C:C/I:C/A:C"); script_set_cvss_temporal_vector("CVSS2#E:H/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:H/RL:O/RC:C"); script_set_attribute(attribute:"exploitability_ease", value:"Exploits are available"); script_set_attribute(attribute:"exploit_available", value:"true"); script_set_attribute(attribute:"exploit_framework_core", value:"true"); script_set_attribute(attribute:"exploited_by_malware", value:"true"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:canonical:ubuntu_linux:linux-image-3.13-generic"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:canonical:ubuntu_linux:linux-image-3.13-generic-lpae"); script_set_attribute(attribute:"cpe", value:"cpe:/o:canonical:ubuntu_linux:12.04:-:lts"); script_set_attribute(attribute:"vuln_publication_date", value:"2016/02/08"); script_set_attribute(attribute:"patch_publication_date", value:"2016/01/19"); script_set_attribute(attribute:"plugin_publication_date", value:"2016/01/20"); script_set_attribute(attribute:"generated_plugin", value:"current"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_copyright(english:"Ubuntu Security Notice (C) 2016-2019 Canonical, Inc. / NASL script (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof."); script_family(english:"Ubuntu Local Security Checks"); script_dependencies("ssh_get_info.nasl", "linux_alt_patch_detect.nasl"); script_require_keys("Host/cpu", "Host/Ubuntu", "Host/Ubuntu/release", "Host/Debian/dpkg-l"); exit(0); } include("audit.inc"); include("ubuntu.inc"); include("ksplice.inc"); if ( ! get_kb_item("Host/local_checks_enabled") ) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); release = get_kb_item("Host/Ubuntu/release"); if ( isnull(release) ) audit(AUDIT_OS_NOT, "Ubuntu"); release = chomp(release); if (! preg(pattern:"^(12\.04)$", string:release)) audit(AUDIT_OS_NOT, "Ubuntu 12.04", "Ubuntu " + release); if ( ! get_kb_item("Host/Debian/dpkg-l") ) audit(AUDIT_PACKAGE_LIST_MISSING); cpu = get_kb_item("Host/cpu"); if (isnull(cpu)) audit(AUDIT_UNKNOWN_ARCH); if ("x86_64" >!< cpu && cpu !~ "^i[3-6]86$") audit(AUDIT_LOCAL_CHECKS_NOT_IMPLEMENTED, "Ubuntu", cpu); if (get_one_kb_item("Host/ksplice/kernel-cves")) { rm_kb_item(name:"Host/uptrack-uname-r"); cve_list = make_list("CVE-2016-0728"); if (ksplice_cves_check(cve_list)) { audit(AUDIT_PATCH_INSTALLED, "KSplice hotfix for USN-2870-2"); } else { _ubuntu_report = ksplice_reporting_text(); } } flag = 0; if (ubuntu_check(osver:"12.04", pkgname:"linux-image-3.13.0-76-generic", pkgver:"3.13.0-76.120~precise1")) flag++; if (ubuntu_check(osver:"12.04", pkgname:"linux-image-3.13.0-76-generic-lpae", pkgver:"3.13.0-76.120~precise1")) flag++; if (flag) { security_report_v4( port : 0, severity : SECURITY_HOLE, extra : ubuntu_report_get() ); exit(0); } else { tested = ubuntu_pkg_tests_get(); if (tested) audit(AUDIT_PACKAGE_NOT_AFFECTED, tested); else audit(AUDIT_PACKAGE_NOT_INSTALLED, "linux-image-3.13-generic / linux-image-3.13-generic-lpae"); }NASL family SuSE Local Security Checks NASL id OPENSUSE-2016-116.NASL description The Linux kernel for openSUSE Leap 42.1 was updated to the 4.1.15 stable release, and also includes security and bugfixes. Following security bugs were fixed : - CVE-2016-0728: A reference leak in keyring handling with join_session_keyring() could lead to local attackers gain root privileges. (bsc#962075). - CVE-2015-7550: A local user could have triggered a race between read and revoke in keyctl (bnc#958951). - CVE-2015-8767: A case can occur when sctp_accept() is called by the user during a heartbeat timeout event after the 4-way handshake. Since sctp_assoc_migrate() changes both assoc->base.sk and assoc->ep, the bh_sock_lock in sctp_generate_heartbeat_event() will be taken with the listening socket but released with the new association socket. The result is a deadlock on any future attempts to take the listening socket lock. (bsc#961509) - CVE-2015-8539: A negatively instantiated user key could have been used by a local user to leverage privileges (bnc#958463). - CVE-2015-8569: The (1) pptp_bind and (2) pptp_connect functions in drivers/net/ppp/pptp.c in the Linux kernel did not verify an address length, which allowed local users to obtain sensitive information from kernel memory and bypass the KASLR protection mechanism via a crafted application (bnc#959190). - CVE-2015-8543: The networking implementation in the Linux kernel did not validate protocol identifiers for certain protocol families, which allowed local users to cause a denial of service (NULL function pointer dereference and system crash) or possibly gain privileges by leveraging CLONE_NEWUSER support to execute a crafted SOCK_RAW application (bnc#958886). - CVE-2015-8575: Validate socket address length in sco_sock_bind() to prevent information leak (bsc#959399). - CVE-2015-8551, CVE-2015-8552: xen/pciback: For XEN_PCI_OP_disable_msi[|x] only disable if device has MSI(X) enabled (bsc#957990). - CVE-2015-8550: Compiler optimizations in the XEN PV backend drivers could have lead to double fetch vulnerabilities, causing denial of service or arbitrary code execution (depending on the configuration) (bsc#957988). The following non-security bugs were fixed : - ALSA: hda - Add a fixup for Thinkpad X1 Carbon 2nd (bsc#958439). - ALSA: hda - Apply click noise workaround for Thinkpads generically (bsc#958439). - ALSA: hda - Fix noise problems on Thinkpad T440s (boo#958504). - ALSA: hda - Flush the pending probe work at remove (boo#960710). - ALSA: hda - Set codec to D3 at reboot/shutdown on Thinkpads (bsc#958439). - Add Cavium Thunderx network enhancements - Add RHEL to kernel-obs-build - Backport amd xgbe fixes and features - Backport arm64 patches from SLE12-SP1-ARM. - Btrfs: fix the number of transaction units needed to remove a block group (bsc#950178). - Btrfs: use global reserve when deleting unused block group after ENOSPC (bsc#950178). - Documentation: nousb is a module parameter (bnc#954324). - Driver for IBM System i/p VNIC protocol. - Enable CONFIG_PINCTRL_CHERRYVIEW (boo#954532) Needed for recent tablets/laptops. CONFIG_PINCTRL_BAYTRAIL is still disabled as it can last seen 2020-06-05 modified 2016-02-03 plugin id 88542 published 2016-02-03 reporter This script is Copyright (C) 2016-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/88542 title openSUSE Security Update : the Linux Kernel (openSUSE-2016-116) code #%NASL_MIN_LEVEL 80502 # # (C) Tenable Network Security, Inc. # # The descriptive text and package checks in this plugin were # extracted from openSUSE Security Update openSUSE-2016-116. # # The text description of this plugin is (C) SUSE LLC. # include("compat.inc"); if (description) { script_id(88542); script_version("2.7"); script_set_attribute(attribute:"plugin_modification_date", value:"2020/06/04"); script_cve_id("CVE-2015-7550", "CVE-2015-8539", "CVE-2015-8543", "CVE-2015-8550", "CVE-2015-8551", "CVE-2015-8552", "CVE-2015-8569", "CVE-2015-8575", "CVE-2015-8767", "CVE-2016-0728"); script_name(english:"openSUSE Security Update : the Linux Kernel (openSUSE-2016-116)"); script_summary(english:"Check for the openSUSE-2016-116 patch"); script_set_attribute( attribute:"synopsis", value:"The remote openSUSE host is missing a security update." ); script_set_attribute( attribute:"description", value: "The Linux kernel for openSUSE Leap 42.1 was updated to the 4.1.15 stable release, and also includes security and bugfixes. Following security bugs were fixed : - CVE-2016-0728: A reference leak in keyring handling with join_session_keyring() could lead to local attackers gain root privileges. (bsc#962075). - CVE-2015-7550: A local user could have triggered a race between read and revoke in keyctl (bnc#958951). - CVE-2015-8767: A case can occur when sctp_accept() is called by the user during a heartbeat timeout event after the 4-way handshake. Since sctp_assoc_migrate() changes both assoc->base.sk and assoc->ep, the bh_sock_lock in sctp_generate_heartbeat_event() will be taken with the listening socket but released with the new association socket. The result is a deadlock on any future attempts to take the listening socket lock. (bsc#961509) - CVE-2015-8539: A negatively instantiated user key could have been used by a local user to leverage privileges (bnc#958463). - CVE-2015-8569: The (1) pptp_bind and (2) pptp_connect functions in drivers/net/ppp/pptp.c in the Linux kernel did not verify an address length, which allowed local users to obtain sensitive information from kernel memory and bypass the KASLR protection mechanism via a crafted application (bnc#959190). - CVE-2015-8543: The networking implementation in the Linux kernel did not validate protocol identifiers for certain protocol families, which allowed local users to cause a denial of service (NULL function pointer dereference and system crash) or possibly gain privileges by leveraging CLONE_NEWUSER support to execute a crafted SOCK_RAW application (bnc#958886). - CVE-2015-8575: Validate socket address length in sco_sock_bind() to prevent information leak (bsc#959399). - CVE-2015-8551, CVE-2015-8552: xen/pciback: For XEN_PCI_OP_disable_msi[|x] only disable if device has MSI(X) enabled (bsc#957990). - CVE-2015-8550: Compiler optimizations in the XEN PV backend drivers could have lead to double fetch vulnerabilities, causing denial of service or arbitrary code execution (depending on the configuration) (bsc#957988). The following non-security bugs were fixed : - ALSA: hda - Add a fixup for Thinkpad X1 Carbon 2nd (bsc#958439). - ALSA: hda - Apply click noise workaround for Thinkpads generically (bsc#958439). - ALSA: hda - Fix noise problems on Thinkpad T440s (boo#958504). - ALSA: hda - Flush the pending probe work at remove (boo#960710). - ALSA: hda - Set codec to D3 at reboot/shutdown on Thinkpads (bsc#958439). - Add Cavium Thunderx network enhancements - Add RHEL to kernel-obs-build - Backport amd xgbe fixes and features - Backport arm64 patches from SLE12-SP1-ARM. - Btrfs: fix the number of transaction units needed to remove a block group (bsc#950178). - Btrfs: use global reserve when deleting unused block group after ENOSPC (bsc#950178). - Documentation: nousb is a module parameter (bnc#954324). - Driver for IBM System i/p VNIC protocol. - Enable CONFIG_PINCTRL_CHERRYVIEW (boo#954532) Needed for recent tablets/laptops. CONFIG_PINCTRL_BAYTRAIL is still disabled as it can't be built as a module. - Fix PCI generic host controller - Fix kABI breakage for max_dev_sectors addition to queue_limits (boo#961263). - HID: multitouch: Fetch feature reports on demand for Win8 devices (boo#954532). - HID: multitouch: fix input mode switching on some Elan panels (boo#954532). - Implement enable/disable for Display C6 state (boo#960021). - Input: aiptek - fix crash on detecting device without endpoints (bnc#956708). - Linux 4.1.15 (boo#954647 bsc#955422). - Move kabi patch to patches.kabi directory - Obsolete compat-wireless, rts5229 and rts_pstor KMPs These are found in SLE11-SP3, now replaced with the upstream drivers. - PCI: generic: Pass starting bus number to pci_scan_root_bus(). - Revert 'block: remove artifical max_hw_sectors cap' (boo#961263). - Set system time through RTC device - Update arm64 config files. Enabled DRM_AST in the vanilla kernel since it is now enabled in the default kernel. - Update config files: CONFIG_IBMVNIC=m - block/sd: Fix device-imposed transfer length limits (boo#961263). - block: bump BLK_DEF_MAX_SECTORS to 2560 (boo#961263). - drm/i915/skl: Add DC5 Trigger Sequence (boo#960021). - drm/i915/skl: Add DC6 Trigger sequence (boo#960021). - drm/i915/skl: Add support to load SKL CSR firmware (boo#960021). - drm/i915/skl: Add the INIT power domain to the MISC I/O power well (boo#960021). - drm/i915/skl: Deinit/init the display at suspend/resume (boo#960021). - drm/i915/skl: Fix DMC API version in firmware file name (boo#960021). - drm/i915/skl: Fix WaDisableChickenBitTSGBarrierAckForFFSliceCS (boo#960021). - drm/i915/skl: Fix stepping check for a couple of W/As (boo#960021). - drm/i915/skl: Fix the CTRL typo in the DPLL_CRTL1 defines (boo#960021). - drm/i915/skl: Implement WaDisableVFUnitClockGating (boo#960021). - drm/i915/skl: Implement enable/disable for Display C5 state (boo#960021). - drm/i915/skl: Make the Misc I/O power well part of the PLLS domain (boo#960021). - drm/i915/skl: add F0 stepping ID (boo#960021). - drm/i915/skl: enable WaForceContextSaveRestoreNonCoherent (boo#960021). - drm/i915: Clear crtc atomic flags at beginning of transaction (boo#960021). - drm/i915: Fix CSR MMIO address check (boo#960021). - drm/i915: Switch to full atomic helpers for plane updates/disable, take two (boo#960021). - drm/i915: set CDCLK if DPLL0 enabled during resuming from S3 (boo#960021). - ethernet/atheros/alx: sanitize buffer sizing and padding (boo#952621). - genksyms: Handle string literals with spaces in reference files (bsc#958510). - group-source-files: mark module.lds as devel file ld: cannot open linker script file /usr/src/linux-4.2.5-1/arch/arm/kernel/module.lds: No such file or directory - hwrng: core - sleep interruptible in read (bnc#962597). - ipv6: distinguish frag queues by device for multicast and link-local packets (bsc#955422). - kABI fixes for linux-4.1.15. - rpm/compute-PATCHVERSION.sh: Skip stale directories in the package dir - rpm/constraints.in: Bump disk space requirements up a bit Require 10GB on s390x, 20GB elsewhere. - rpm/constraints.in: Require 14GB worth of disk space on POWER The builds started to fail randomly due to ENOSPC errors. - rpm/kernel-binary.spec.in: Do not explicitly set DEBUG_SECTION_MISMATCH CONFIG_DEBUG_SECTION_MISMATCH is a selectable Kconfig option since 2.6.39 and is enabled in our configs. - rpm/kernel-binary.spec.in: Do not obsolete ocfs2-kmp (bnc#865259)865259 - rpm/kernel-binary.spec.in: Fix build if no UEFI certs are installed - rpm/kernel-binary.spec.in: Install libopenssl-devel for newer sign-file - rpm/kernel-binary.spec.in: No scriptlets in kernel-zfcpdump The kernel should not be added to the bootloader nor are there any KMPs. - rpm/kernel-binary.spec.in: Obsolete the -base package from SLE11 (bnc#865096) - rpm/kernel-binary.spec.in: Use parallel make in all invocations Also, remove the lengthy comment, since we are using a standard rpm macro now. - thinkpad_acpi: Do not yell on unsupported brightness interfaces (boo#957152). - usb: make 'nousb' a clear module parameter (bnc#954324). - usbvision fix overflow of interfaces array (bnc#950998). - x86/microcode/amd: Do not overwrite final patch levels (bsc#913996). - x86/microcode/amd: Extract current patch level read to a function (bsc#913996). - xen/pciback: Do not allow MSI-X ops if PCI_COMMAND_MEMORY is not set (bsc#957990 XSA-157). - xhci: refuse loading if nousb is used (bnc#954324)." ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=865096" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=865259" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=913996" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=950178" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=950998" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=952621" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=954324" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=954532" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=954647" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=955422" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=956708" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=957152" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=957988" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=957990" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=958439" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=958463" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=958504" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=958510" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=958886" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=958951" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=959190" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=959399" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=960021" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=960710" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=961263" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=961509" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=962075" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=962597" ); script_set_attribute( attribute:"solution", value:"Update the affected the Linux Kernel packages." ); script_set_cvss_base_vector("CVSS2#AV:L/AC:L/Au:N/C:C/I:C/A:C"); script_set_cvss_temporal_vector("CVSS2#E:H/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:L/AC:L/PR:H/UI:N/S:C/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:H/RL:O/RC:C"); script_set_attribute(attribute:"exploitability_ease", value:"Exploits are available"); script_set_attribute(attribute:"exploit_available", value:"true"); script_set_attribute(attribute:"exploit_framework_core", value:"true"); script_set_attribute(attribute:"exploited_by_malware", value:"true"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-debug"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-debug-base"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-debug-base-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-debug-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-debug-debugsource"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-debug-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-debug-devel-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-default"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-default-base"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-default-base-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-default-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-default-debugsource"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-default-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-docs-html"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-docs-pdf"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-ec2"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-ec2-base"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-ec2-base-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-ec2-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-ec2-debugsource"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-ec2-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-macros"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-obs-build"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-obs-build-debugsource"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-obs-qa"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-obs-qa-xen"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-pae"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-pae-base"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-pae-base-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-pae-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-pae-debugsource"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-pae-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-pv"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-pv-base"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-pv-base-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-pv-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-pv-debugsource"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-pv-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-source"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-source-vanilla"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-syms"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-vanilla"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-vanilla-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-vanilla-debugsource"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-vanilla-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-xen"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-xen-base"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-xen-base-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-xen-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-xen-debugsource"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-xen-devel"); script_set_attribute(attribute:"cpe", value:"cpe:/o:novell:opensuse:42.1"); script_set_attribute(attribute:"patch_publication_date", value:"2016/01/29"); script_set_attribute(attribute:"plugin_publication_date", value:"2016/02/03"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_copyright(english:"This script is Copyright (C) 2016-2020 and is owned by Tenable, Inc. or an Affiliate thereof."); script_family(english:"SuSE Local Security Checks"); script_dependencies("ssh_get_info.nasl"); script_require_keys("Host/local_checks_enabled", "Host/SuSE/release", "Host/SuSE/rpm-list", "Host/cpu"); exit(0); } include("audit.inc"); include("global_settings.inc"); include("rpm.inc"); if (!get_kb_item("Host/local_checks_enabled")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); release = get_kb_item("Host/SuSE/release"); if (isnull(release) || release =~ "^(SLED|SLES)") audit(AUDIT_OS_NOT, "openSUSE"); if (release !~ "^(SUSE42\.1)$") audit(AUDIT_OS_RELEASE_NOT, "openSUSE", "42.1", release); if (!get_kb_item("Host/SuSE/rpm-list")) audit(AUDIT_PACKAGE_LIST_MISSING); ourarch = get_kb_item("Host/cpu"); if (!ourarch) audit(AUDIT_UNKNOWN_ARCH); if (ourarch !~ "^(i586|i686|x86_64)$") audit(AUDIT_ARCH_NOT, "i586 / i686 / x86_64", ourarch); flag = 0; if ( rpm_check(release:"SUSE42.1", reference:"kernel-default-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", reference:"kernel-default-base-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", reference:"kernel-default-base-debuginfo-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", reference:"kernel-default-debuginfo-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", reference:"kernel-default-debugsource-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", reference:"kernel-default-devel-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", reference:"kernel-devel-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", reference:"kernel-docs-html-4.1.15-8.3") ) flag++; if ( rpm_check(release:"SUSE42.1", reference:"kernel-docs-pdf-4.1.15-8.3") ) flag++; if ( rpm_check(release:"SUSE42.1", reference:"kernel-macros-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", reference:"kernel-obs-build-4.1.15-8.2") ) flag++; if ( rpm_check(release:"SUSE42.1", reference:"kernel-obs-build-debugsource-4.1.15-8.2") ) flag++; if ( rpm_check(release:"SUSE42.1", reference:"kernel-obs-qa-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", reference:"kernel-obs-qa-xen-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", reference:"kernel-source-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", reference:"kernel-source-vanilla-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", reference:"kernel-syms-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"i686", reference:"kernel-debug-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"i686", reference:"kernel-debug-base-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"i686", reference:"kernel-debug-base-debuginfo-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"i686", reference:"kernel-debug-debuginfo-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"i686", reference:"kernel-debug-debugsource-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"i686", reference:"kernel-debug-devel-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"i686", reference:"kernel-debug-devel-debuginfo-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"i686", reference:"kernel-ec2-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"i686", reference:"kernel-ec2-base-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"i686", reference:"kernel-ec2-base-debuginfo-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"i686", reference:"kernel-ec2-debuginfo-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"i686", reference:"kernel-ec2-debugsource-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"i686", reference:"kernel-ec2-devel-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"i686", reference:"kernel-pae-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"i686", reference:"kernel-pae-base-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"i686", reference:"kernel-pae-base-debuginfo-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"i686", reference:"kernel-pae-debuginfo-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"i686", reference:"kernel-pae-debugsource-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"i686", reference:"kernel-pae-devel-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"i686", reference:"kernel-pv-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"i686", reference:"kernel-pv-base-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"i686", reference:"kernel-pv-base-debuginfo-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"i686", reference:"kernel-pv-debuginfo-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"i686", reference:"kernel-pv-debugsource-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"i686", reference:"kernel-pv-devel-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"i686", reference:"kernel-vanilla-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"i686", reference:"kernel-vanilla-debuginfo-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"i686", reference:"kernel-vanilla-debugsource-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"i686", reference:"kernel-vanilla-devel-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"i686", reference:"kernel-xen-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"i686", reference:"kernel-xen-base-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"i686", reference:"kernel-xen-base-debuginfo-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"i686", reference:"kernel-xen-debuginfo-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"i686", reference:"kernel-xen-debugsource-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"i686", reference:"kernel-xen-devel-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"x86_64", reference:"kernel-debug-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"x86_64", reference:"kernel-debug-base-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"x86_64", reference:"kernel-debug-base-debuginfo-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"x86_64", reference:"kernel-debug-debuginfo-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"x86_64", reference:"kernel-debug-debugsource-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"x86_64", reference:"kernel-debug-devel-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"x86_64", reference:"kernel-debug-devel-debuginfo-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"x86_64", reference:"kernel-ec2-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"x86_64", reference:"kernel-ec2-base-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"x86_64", reference:"kernel-ec2-base-debuginfo-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"x86_64", reference:"kernel-ec2-debuginfo-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"x86_64", reference:"kernel-ec2-debugsource-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"x86_64", reference:"kernel-ec2-devel-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"x86_64", reference:"kernel-pae-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"x86_64", reference:"kernel-pae-base-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"x86_64", reference:"kernel-pae-base-debuginfo-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"x86_64", reference:"kernel-pae-debuginfo-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"x86_64", reference:"kernel-pae-debugsource-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"x86_64", reference:"kernel-pae-devel-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"x86_64", reference:"kernel-pv-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"x86_64", reference:"kernel-pv-base-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"x86_64", reference:"kernel-pv-base-debuginfo-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"x86_64", reference:"kernel-pv-debuginfo-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"x86_64", reference:"kernel-pv-debugsource-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"x86_64", reference:"kernel-pv-devel-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"x86_64", reference:"kernel-vanilla-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"x86_64", reference:"kernel-vanilla-debuginfo-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"x86_64", reference:"kernel-vanilla-debugsource-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"x86_64", reference:"kernel-vanilla-devel-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"x86_64", reference:"kernel-xen-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"x86_64", reference:"kernel-xen-base-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"x86_64", reference:"kernel-xen-base-debuginfo-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"x86_64", reference:"kernel-xen-debuginfo-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"x86_64", reference:"kernel-xen-debugsource-4.1.15-8.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"x86_64", reference:"kernel-xen-devel-4.1.15-8.1") ) flag++; if (flag) { if (report_verbosity > 0) security_hole(port:0, extra:rpm_report_get()); else security_hole(0); exit(0); } else { tested = pkg_tests_get(); if (tested) audit(AUDIT_PACKAGE_NOT_AFFECTED, tested); else audit(AUDIT_PACKAGE_NOT_INSTALLED, "kernel-debug / kernel-debug-base / kernel-debug-base-debuginfo / etc"); }NASL family Debian Local Security Checks NASL id DEBIAN_DSA-3448.NASL description Several vulnerabilities have been discovered in the Linux kernel that may lead to a privilege escalation or denial-of-service. - CVE-2013-4312 Tetsuo Handa discovered that it is possible for a process to open far more files than the process last seen 2020-06-01 modified 2020-06-02 plugin id 87995 published 2016-01-20 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/87995 title Debian DSA-3448-1 : linux - security update code # # (C) Tenable Network Security, Inc. # # The descriptive text and package checks in this plugin were # extracted from Debian Security Advisory DSA-3448. The text # itself is copyright (C) Software in the Public Interest, Inc. # include("compat.inc"); if (description) { script_id(87995); script_version("2.11"); script_cvs_date("Date: 2019/07/15 14:20:29"); script_cve_id("CVE-2013-4312", "CVE-2015-7566", "CVE-2015-8767", "CVE-2016-0723", "CVE-2016-0728"); script_xref(name:"DSA", value:"3448"); script_name(english:"Debian DSA-3448-1 : linux - security update"); script_summary(english:"Checks dpkg output for the updated package"); script_set_attribute( attribute:"synopsis", value:"The remote Debian host is missing a security-related update." ); script_set_attribute( attribute:"description", value: "Several vulnerabilities have been discovered in the Linux kernel that may lead to a privilege escalation or denial-of-service. - CVE-2013-4312 Tetsuo Handa discovered that it is possible for a process to open far more files than the process' limit leading to denial-of-service conditions. - CVE-2015-7566 Ralf Spenneberg of OpenSource Security reported that the visor driver crashes when a specially crafted USB device without bulk-out endpoint is detected. - CVE-2015-8767 An SCTP denial-of-service was discovered which can be triggered by a local attacker during a heartbeat timeout event after the 4-way handshake. - CVE-2016-0723 A use-after-free vulnerability was discovered in the TIOCGETD ioctl. A local attacker could use this flaw for denial-of-service. - CVE-2016-0728 The Perception Point research team discovered a use-after-free vulnerability in the keyring facility, possibly leading to local privilege escalation." ); script_set_attribute( attribute:"see_also", value:"https://security-tracker.debian.org/tracker/CVE-2013-4312" ); script_set_attribute( attribute:"see_also", value:"https://security-tracker.debian.org/tracker/CVE-2015-7566" ); script_set_attribute( attribute:"see_also", value:"https://security-tracker.debian.org/tracker/CVE-2015-8767" ); script_set_attribute( attribute:"see_also", value:"https://security-tracker.debian.org/tracker/CVE-2016-0723" ); script_set_attribute( attribute:"see_also", value:"https://security-tracker.debian.org/tracker/CVE-2016-0728" ); script_set_attribute( attribute:"see_also", value:"https://packages.debian.org/source/jessie/linux" ); script_set_attribute( attribute:"see_also", value:"https://www.debian.org/security/2016/dsa-3448" ); script_set_attribute( attribute:"solution", value: "Upgrade the linux packages. For the stable distribution (jessie), these problems have been fixed in version 3.16.7-ckt20-1+deb8u3." ); script_set_cvss_base_vector("CVSS2#AV:L/AC:L/Au:N/C:C/I:C/A:C"); script_set_cvss_temporal_vector("CVSS2#E:H/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:H/RL:O/RC:C"); script_set_attribute(attribute:"exploitability_ease", value:"Exploits are available"); script_set_attribute(attribute:"exploit_available", value:"true"); script_set_attribute(attribute:"exploit_framework_core", value:"true"); script_set_attribute(attribute:"exploited_by_malware", value:"true"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:debian:debian_linux:linux"); script_set_attribute(attribute:"cpe", value:"cpe:/o:debian:debian_linux:8.0"); script_set_attribute(attribute:"vuln_publication_date", value:"2016/02/08"); script_set_attribute(attribute:"patch_publication_date", value:"2016/01/19"); script_set_attribute(attribute:"plugin_publication_date", value:"2016/01/20"); script_set_attribute(attribute:"generated_plugin", value:"current"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_copyright(english:"This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof."); script_family(english:"Debian Local Security Checks"); script_dependencies("ssh_get_info.nasl"); script_require_keys("Host/local_checks_enabled", "Host/Debian/release", "Host/Debian/dpkg-l"); exit(0); } include("audit.inc"); include("debian_package.inc"); if (!get_kb_item("Host/local_checks_enabled")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); if (!get_kb_item("Host/Debian/release")) audit(AUDIT_OS_NOT, "Debian"); if (!get_kb_item("Host/Debian/dpkg-l")) audit(AUDIT_PACKAGE_LIST_MISSING); flag = 0; if (deb_check(release:"8.0", prefix:"linux-compiler-gcc-4.8-arm", reference:"3.16.7-ckt20-1+deb8u3")) flag++; if (deb_check(release:"8.0", prefix:"linux-compiler-gcc-4.8-x86", reference:"3.16.7-ckt20-1+deb8u3")) flag++; if (deb_check(release:"8.0", prefix:"linux-compiler-gcc-4.9-x86", reference:"3.16.7-ckt20-1+deb8u3")) flag++; if (deb_check(release:"8.0", prefix:"linux-doc-3.16", reference:"3.16.7-ckt20-1+deb8u3")) flag++; if (deb_check(release:"8.0", prefix:"linux-headers-3.16.0-9-586", reference:"3.16.7-ckt20-1+deb8u3")) flag++; if (deb_check(release:"8.0", prefix:"linux-headers-3.16.0-9-686-pae", reference:"3.16.7-ckt20-1+deb8u3")) flag++; if (deb_check(release:"8.0", prefix:"linux-headers-3.16.0-9-all", reference:"3.16.7-ckt20-1+deb8u3")) flag++; if (deb_check(release:"8.0", prefix:"linux-headers-3.16.0-9-all-amd64", reference:"3.16.7-ckt20-1+deb8u3")) flag++; if (deb_check(release:"8.0", prefix:"linux-headers-3.16.0-9-all-armel", reference:"3.16.7-ckt20-1+deb8u3")) flag++; if (deb_check(release:"8.0", prefix:"linux-headers-3.16.0-9-all-armhf", reference:"3.16.7-ckt20-1+deb8u3")) flag++; if (deb_check(release:"8.0", prefix:"linux-headers-3.16.0-9-all-i386", reference:"3.16.7-ckt20-1+deb8u3")) flag++; if (deb_check(release:"8.0", prefix:"linux-headers-3.16.0-9-amd64", reference:"3.16.7-ckt20-1+deb8u3")) flag++; if (deb_check(release:"8.0", prefix:"linux-headers-3.16.0-9-armmp", reference:"3.16.7-ckt20-1+deb8u3")) flag++; if (deb_check(release:"8.0", prefix:"linux-headers-3.16.0-9-armmp-lpae", reference:"3.16.7-ckt20-1+deb8u3")) flag++; if (deb_check(release:"8.0", prefix:"linux-headers-3.16.0-9-common", reference:"3.16.7-ckt20-1+deb8u3")) flag++; if (deb_check(release:"8.0", prefix:"linux-headers-3.16.0-9-ixp4xx", reference:"3.16.7-ckt20-1+deb8u3")) flag++; if (deb_check(release:"8.0", prefix:"linux-headers-3.16.0-9-kirkwood", reference:"3.16.7-ckt20-1+deb8u3")) flag++; if (deb_check(release:"8.0", prefix:"linux-headers-3.16.0-9-orion5x", reference:"3.16.7-ckt20-1+deb8u3")) flag++; if (deb_check(release:"8.0", prefix:"linux-headers-3.16.0-9-versatile", reference:"3.16.7-ckt20-1+deb8u3")) flag++; if (deb_check(release:"8.0", prefix:"linux-image-3.16.0-9-586", reference:"3.16.7-ckt20-1+deb8u3")) flag++; if (deb_check(release:"8.0", prefix:"linux-image-3.16.0-9-686-pae", reference:"3.16.7-ckt20-1+deb8u3")) flag++; if (deb_check(release:"8.0", prefix:"linux-image-3.16.0-9-686-pae-dbg", reference:"3.16.7-ckt20-1+deb8u3")) flag++; if (deb_check(release:"8.0", prefix:"linux-image-3.16.0-9-amd64", reference:"3.16.7-ckt20-1+deb8u3")) flag++; if (deb_check(release:"8.0", prefix:"linux-image-3.16.0-9-amd64-dbg", reference:"3.16.7-ckt20-1+deb8u3")) flag++; if (deb_check(release:"8.0", prefix:"linux-image-3.16.0-9-armmp", reference:"3.16.7-ckt20-1+deb8u3")) flag++; if (deb_check(release:"8.0", prefix:"linux-image-3.16.0-9-armmp-lpae", reference:"3.16.7-ckt20-1+deb8u3")) flag++; if (deb_check(release:"8.0", prefix:"linux-image-3.16.0-9-ixp4xx", reference:"3.16.7-ckt20-1+deb8u3")) flag++; if (deb_check(release:"8.0", prefix:"linux-image-3.16.0-9-kirkwood", reference:"3.16.7-ckt20-1+deb8u3")) flag++; if (deb_check(release:"8.0", prefix:"linux-image-3.16.0-9-orion5x", reference:"3.16.7-ckt20-1+deb8u3")) flag++; if (deb_check(release:"8.0", prefix:"linux-image-3.16.0-9-versatile", reference:"3.16.7-ckt20-1+deb8u3")) flag++; if (deb_check(release:"8.0", prefix:"linux-libc-dev", reference:"3.16.7-ckt20-1+deb8u3")) flag++; if (deb_check(release:"8.0", prefix:"linux-manual-3.16", reference:"3.16.7-ckt20-1+deb8u3")) flag++; if (deb_check(release:"8.0", prefix:"linux-source-3.16", reference:"3.16.7-ckt20-1+deb8u3")) flag++; if (deb_check(release:"8.0", prefix:"linux-support-3.16.0-9", reference:"3.16.7-ckt20-1+deb8u3")) flag++; if (deb_check(release:"8.0", prefix:"xen-linux-system-3.16.0-9-amd64", reference:"3.16.7-ckt20-1+deb8u3")) flag++; if (flag) { if (report_verbosity > 0) security_hole(port:0, extra:deb_report_get()); else security_hole(0); exit(0); } else audit(AUDIT_HOST_NOT, "affected");NASL family Scientific Linux Local Security Checks NASL id SL_20160125_KERNEL_ON_SL7_X.NASL description * A use-after-free flaw was found in the way the Linux kernel last seen 2020-03-18 modified 2016-01-26 plugin id 88174 published 2016-01-26 reporter This script is Copyright (C) 2016-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/88174 title Scientific Linux Security Update : kernel on SL7.x x86_64 (20160125) code # # (C) Tenable Network Security, Inc. # # The descriptive text is (C) Scientific Linux. # include("compat.inc"); if (description) { script_id(88174); script_version("2.8"); script_set_attribute(attribute:"plugin_modification_date", value:"2020/02/25"); script_cve_id("CVE-2016-0728"); script_name(english:"Scientific Linux Security Update : kernel on SL7.x x86_64 (20160125)"); script_summary(english:"Checks rpm output for the updated packages"); script_set_attribute( attribute:"synopsis", value: "The remote Scientific Linux host is missing one or more security updates." ); script_set_attribute( attribute:"description", value: "* A use-after-free flaw was found in the way the Linux kernel's key management subsystem handled keyring object reference counting in certain error path of the join_session_keyring() function. A local, unprivileged user could use this flaw to escalate their privileges on the system. (CVE-2016-0728, Important) The system must be rebooted for this update to take effect." ); # https://listserv.fnal.gov/scripts/wa.exe?A2=ind1601&L=scientific-linux-errata&F=&S=&P=11419 script_set_attribute( attribute:"see_also", value:"http://www.nessus.org/u?3869eafb" ); script_set_attribute(attribute:"solution", value:"Update the affected packages."); script_set_cvss_base_vector("CVSS2#AV:L/AC:L/Au:N/C:C/I:C/A:C"); script_set_cvss_temporal_vector("CVSS2#E:H/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:H/RL:O/RC:C"); script_set_attribute(attribute:"exploitability_ease", value:"Exploits are available"); script_set_attribute(attribute:"exploit_available", value:"true"); script_set_attribute(attribute:"exploit_framework_core", value:"true"); script_set_attribute(attribute:"exploited_by_malware", value:"true"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:fermilab:scientific_linux:kernel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:fermilab:scientific_linux:kernel-abi-whitelists"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:fermilab:scientific_linux:kernel-debug"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:fermilab:scientific_linux:kernel-debug-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:fermilab:scientific_linux:kernel-debug-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:fermilab:scientific_linux:kernel-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:fermilab:scientific_linux:kernel-debuginfo-common-x86_64"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:fermilab:scientific_linux:kernel-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:fermilab:scientific_linux:kernel-doc"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:fermilab:scientific_linux:kernel-headers"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:fermilab:scientific_linux:kernel-tools"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:fermilab:scientific_linux:kernel-tools-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:fermilab:scientific_linux:kernel-tools-libs"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:fermilab:scientific_linux:kernel-tools-libs-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:fermilab:scientific_linux:perf"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:fermilab:scientific_linux:perf-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:fermilab:scientific_linux:python-perf"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:fermilab:scientific_linux:python-perf-debuginfo"); script_set_attribute(attribute:"cpe", value:"x-cpe:/o:fermilab:scientific_linux"); script_set_attribute(attribute:"vuln_publication_date", value:"2016/02/08"); script_set_attribute(attribute:"patch_publication_date", value:"2016/01/25"); script_set_attribute(attribute:"plugin_publication_date", value:"2016/01/26"); script_set_attribute(attribute:"generated_plugin", value:"current"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_copyright(english:"This script is Copyright (C) 2016-2020 and is owned by Tenable, Inc. or an Affiliate thereof."); script_family(english:"Scientific Linux Local Security Checks"); script_dependencies("ssh_get_info.nasl"); script_require_keys("Host/local_checks_enabled", "Host/cpu", "Host/RedHat/release", "Host/RedHat/rpm-list"); exit(0); } include("audit.inc"); include("global_settings.inc"); include("misc_func.inc"); include("rpm.inc"); if (!get_kb_item("Host/local_checks_enabled")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); release = get_kb_item("Host/RedHat/release"); if (isnull(release) || "Scientific Linux " >!< release) audit(AUDIT_HOST_NOT, "running Scientific Linux"); os_ver = pregmatch(pattern: "Scientific Linux.*release ([0-9]+(\.[0-9]+)?)", string:release); if (isnull(os_ver)) audit(AUDIT_UNKNOWN_APP_VER, "Scientific Linux"); os_ver = os_ver[1]; if (! preg(pattern:"^7([^0-9]|$)", string:os_ver)) audit(AUDIT_OS_NOT, "Scientific Linux 7.x", "Scientific Linux " + os_ver); if (!get_kb_item("Host/RedHat/rpm-list")) audit(AUDIT_PACKAGE_LIST_MISSING); cpu = get_kb_item("Host/cpu"); if (isnull(cpu)) audit(AUDIT_UNKNOWN_ARCH); if (cpu >!< "x86_64" && cpu !~ "^i[3-6]86$") audit(AUDIT_LOCAL_CHECKS_NOT_IMPLEMENTED, "Scientific Linux", cpu); flag = 0; if (rpm_check(release:"SL7", cpu:"x86_64", reference:"kernel-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"SL7", reference:"kernel-abi-whitelists-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"SL7", cpu:"x86_64", reference:"kernel-debug-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"SL7", cpu:"x86_64", reference:"kernel-debug-debuginfo-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"SL7", cpu:"x86_64", reference:"kernel-debug-devel-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"SL7", cpu:"x86_64", reference:"kernel-debuginfo-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"SL7", cpu:"x86_64", reference:"kernel-debuginfo-common-x86_64-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"SL7", cpu:"x86_64", reference:"kernel-devel-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"SL7", reference:"kernel-doc-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"SL7", cpu:"x86_64", reference:"kernel-headers-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"SL7", cpu:"x86_64", reference:"kernel-tools-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"SL7", cpu:"x86_64", reference:"kernel-tools-debuginfo-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"SL7", cpu:"x86_64", reference:"kernel-tools-libs-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"SL7", cpu:"x86_64", reference:"kernel-tools-libs-devel-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"SL7", cpu:"x86_64", reference:"perf-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"SL7", cpu:"x86_64", reference:"perf-debuginfo-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"SL7", cpu:"x86_64", reference:"python-perf-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"SL7", cpu:"x86_64", reference:"python-perf-debuginfo-3.10.0-327.4.5.el7")) flag++; if (flag) { security_report_v4( port : 0, severity : SECURITY_HOLE, extra : rpm_report_get() ); exit(0); } else { tested = pkg_tests_get(); if (tested) audit(AUDIT_PACKAGE_NOT_AFFECTED, tested); else audit(AUDIT_PACKAGE_NOT_INSTALLED, "kernel / kernel-abi-whitelists / kernel-debug / etc"); }NASL family CentOS Local Security Checks NASL id CENTOS_RHSA-2016-0064.NASL description Updated kernel packages that fix one security issue are now available for Red Hat Enterprise Linux 7. Red Hat Product Security has rated this update as having Important security impact. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available from the CVE link in the References section. The kernel packages contain the Linux kernel, the core of any Linux operating system. * A use-after-free flaw was found in the way the Linux kernel last seen 2020-06-01 modified 2020-06-02 plugin id 88148 published 2016-01-26 reporter This script is Copyright (C) 2016-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/88148 title CentOS 7 : kernel (CESA-2016:0064) code # # (C) Tenable Network Security, Inc. # # The descriptive text and package checks in this plugin were # extracted from Red Hat Security Advisory RHSA-2016:0064 and # CentOS Errata and Security Advisory 2016:0064 respectively. # include("compat.inc"); if (description) { script_id(88148); script_version("2.10"); script_cvs_date("Date: 2020/01/02"); script_cve_id("CVE-2016-0728"); script_xref(name:"RHSA", value:"2016:0064"); script_name(english:"CentOS 7 : kernel (CESA-2016:0064)"); script_summary(english:"Checks rpm output for the updated packages"); script_set_attribute( attribute:"synopsis", value:"The remote CentOS host is missing one or more security updates." ); script_set_attribute( attribute:"description", value: "Updated kernel packages that fix one security issue are now available for Red Hat Enterprise Linux 7. Red Hat Product Security has rated this update as having Important security impact. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available from the CVE link in the References section. The kernel packages contain the Linux kernel, the core of any Linux operating system. * A use-after-free flaw was found in the way the Linux kernel's key management subsystem handled keyring object reference counting in certain error path of the join_session_keyring() function. A local, unprivileged user could use this flaw to escalate their privileges on the system. (CVE-2016-0728, Important) Red Hat would like to thank the Perception Point research team for reporting this issue. All kernel users are advised to upgrade to these updated packages, which contain a backported patch to correct this issue. The system must be rebooted for this update to take effect." ); # https://lists.centos.org/pipermail/centos-announce/2016-January/021625.html script_set_attribute( attribute:"see_also", value:"http://www.nessus.org/u?5252ffe4" ); script_set_attribute( attribute:"solution", value:"Update the affected kernel packages." ); script_set_cvss_base_vector("CVSS2#AV:L/AC:L/Au:N/C:C/I:C/A:C"); script_set_cvss_temporal_vector("CVSS2#E:H/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:H/RL:O/RC:C"); script_set_attribute(attribute:"cvss_score_source", value:"CVE-2016-0728"); script_set_attribute(attribute:"exploitability_ease", value:"Exploits are available"); script_set_attribute(attribute:"exploit_available", value:"true"); script_set_attribute(attribute:"exploit_framework_core", value:"true"); script_set_attribute(attribute:"exploited_by_malware", value:"true"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:centos:centos:kernel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:centos:centos:kernel-abi-whitelists"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:centos:centos:kernel-debug"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:centos:centos:kernel-debug-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:centos:centos:kernel-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:centos:centos:kernel-doc"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:centos:centos:kernel-headers"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:centos:centos:kernel-tools"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:centos:centos:kernel-tools-libs"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:centos:centos:kernel-tools-libs-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:centos:centos:perf"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:centos:centos:python-perf"); script_set_attribute(attribute:"cpe", value:"cpe:/o:centos:centos:7"); script_set_attribute(attribute:"vuln_publication_date", value:"2016/02/08"); script_set_attribute(attribute:"patch_publication_date", value:"2016/01/25"); script_set_attribute(attribute:"plugin_publication_date", value:"2016/01/26"); script_set_attribute(attribute:"generated_plugin", value:"current"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_copyright(english:"This script is Copyright (C) 2016-2020 and is owned by Tenable, Inc. or an Affiliate thereof."); script_family(english:"CentOS Local Security Checks"); script_dependencies("ssh_get_info.nasl"); script_require_keys("Host/local_checks_enabled", "Host/CentOS/release", "Host/CentOS/rpm-list"); exit(0); } include("audit.inc"); include("global_settings.inc"); include("rpm.inc"); if (!get_kb_item("Host/local_checks_enabled")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); release = get_kb_item("Host/CentOS/release"); if (isnull(release) || "CentOS" >!< release) audit(AUDIT_OS_NOT, "CentOS"); os_ver = pregmatch(pattern: "CentOS(?: Linux)? release ([0-9]+)", string:release); if (isnull(os_ver)) audit(AUDIT_UNKNOWN_APP_VER, "CentOS"); os_ver = os_ver[1]; if (! preg(pattern:"^7([^0-9]|$)", string:os_ver)) audit(AUDIT_OS_NOT, "CentOS 7.x", "CentOS " + os_ver); if (!get_kb_item("Host/CentOS/rpm-list")) audit(AUDIT_PACKAGE_LIST_MISSING); cpu = get_kb_item("Host/cpu"); if (isnull(cpu)) audit(AUDIT_UNKNOWN_ARCH); if ("x86_64" >!< cpu && cpu !~ "^i[3-6]86$") audit(AUDIT_LOCAL_CHECKS_NOT_IMPLEMENTED, "CentOS", cpu); flag = 0; if (rpm_check(release:"CentOS-7", cpu:"x86_64", reference:"kernel-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"CentOS-7", cpu:"x86_64", reference:"kernel-abi-whitelists-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"CentOS-7", cpu:"x86_64", reference:"kernel-debug-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"CentOS-7", cpu:"x86_64", reference:"kernel-debug-devel-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"CentOS-7", cpu:"x86_64", reference:"kernel-devel-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"CentOS-7", cpu:"x86_64", reference:"kernel-doc-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"CentOS-7", cpu:"x86_64", reference:"kernel-headers-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"CentOS-7", cpu:"x86_64", reference:"kernel-tools-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"CentOS-7", cpu:"x86_64", reference:"kernel-tools-libs-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"CentOS-7", cpu:"x86_64", reference:"kernel-tools-libs-devel-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"CentOS-7", cpu:"x86_64", reference:"perf-3.10.0-327.4.5.el7")) flag++; if (rpm_check(release:"CentOS-7", cpu:"x86_64", reference:"python-perf-3.10.0-327.4.5.el7")) flag++; if (flag) { security_report_v4( port : 0, severity : SECURITY_HOLE, extra : rpm_report_get() ); exit(0); } else { tested = pkg_tests_get(); if (tested) audit(AUDIT_PACKAGE_NOT_AFFECTED, tested); else audit(AUDIT_PACKAGE_NOT_INSTALLED, "kernel / kernel-abi-whitelists / kernel-debug / kernel-debug-devel / etc"); }NASL family OracleVM Local Security Checks NASL id ORACLEVM_OVMSA-2016-0005.NASL description The remote OracleVM system is missing necessary patches to address critical security updates : - KEYS: Fix keyring ref leak in join_session_keyring (Yevgeny Pats) [Orabug: 22563965] (CVE-2016-0728) - KEYS: Don last seen 2020-06-01 modified 2020-06-02 plugin id 88034 published 2016-01-21 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/88034 title OracleVM 3.3 : kernel-uek (OVMSA-2016-0005) code # # (C) Tenable Network Security, Inc. # # The package checks in this plugin were extracted from OracleVM # Security Advisory OVMSA-2016-0005. # include("compat.inc"); if (description) { script_id(88034); script_version("2.10"); script_cvs_date("Date: 2019/09/27 13:00:34"); script_cve_id("CVE-2015-7872", "CVE-2016-0728"); script_name(english:"OracleVM 3.3 : kernel-uek (OVMSA-2016-0005)"); script_summary(english:"Checks the RPM output for the updated packages."); script_set_attribute( attribute:"synopsis", value:"The remote OracleVM host is missing one or more security updates." ); script_set_attribute( attribute:"description", value: "The remote OracleVM system is missing necessary patches to address critical security updates : - KEYS: Fix keyring ref leak in join_session_keyring (Yevgeny Pats) [Orabug: 22563965] (CVE-2016-0728) - KEYS: Don't permit request_key to construct a new keyring (David Howells) [Orabug: 22373442] (CVE-2015-7872) - dcache: Handle escaped paths in prepend_path (Eric W. Biederman) - vfs: Test for and handle paths that are unreachable from their mnt_root (Eric W. Biederman) [Orabug: 22249875] - KEYS: Fix crash when attempt to garbage collect an uninstantiated keyring (David Howells) [Orabug: 22373442] (CVE-2015-7872) - KEYS: Fix race between key destruction and finding a keyring by name (David Howells) [Orabug: 22373442]" ); # https://oss.oracle.com/pipermail/oraclevm-errata/2016-January/000409.html script_set_attribute( attribute:"see_also", value:"http://www.nessus.org/u?b266b603" ); script_set_attribute( attribute:"solution", value:"Update the affected kernel-uek / kernel-uek-firmware packages." ); script_set_cvss_base_vector("CVSS2#AV:L/AC:L/Au:N/C:C/I:C/A:C"); script_set_cvss_temporal_vector("CVSS2#E:H/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:H/RL:O/RC:C"); script_set_attribute(attribute:"exploitability_ease", value:"Exploits are available"); script_set_attribute(attribute:"exploit_available", value:"true"); script_set_attribute(attribute:"exploit_framework_core", value:"true"); script_set_attribute(attribute:"exploited_by_malware", value:"true"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:oracle:vm:kernel-uek"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:oracle:vm:kernel-uek-firmware"); script_set_attribute(attribute:"cpe", value:"cpe:/o:oracle:vm_server:3.3"); script_set_attribute(attribute:"vuln_publication_date", value:"2015/11/16"); script_set_attribute(attribute:"patch_publication_date", value:"2016/01/20"); script_set_attribute(attribute:"plugin_publication_date", value:"2016/01/21"); script_set_attribute(attribute:"generated_plugin", value:"current"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_copyright(english:"This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof."); script_family(english:"OracleVM Local Security Checks"); script_dependencies("ssh_get_info.nasl"); script_require_keys("Host/local_checks_enabled", "Host/OracleVM/release", "Host/OracleVM/rpm-list"); exit(0); } include("audit.inc"); include("global_settings.inc"); include("rpm.inc"); if (!get_kb_item("Host/local_checks_enabled")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); release = get_kb_item("Host/OracleVM/release"); if (isnull(release) || "OVS" >!< release) audit(AUDIT_OS_NOT, "OracleVM"); if (! preg(pattern:"^OVS" + "3\.3" + "(\.[0-9]|$)", string:release)) audit(AUDIT_OS_NOT, "OracleVM 3.3", "OracleVM " + release); if (!get_kb_item("Host/OracleVM/rpm-list")) audit(AUDIT_PACKAGE_LIST_MISSING); cpu = get_kb_item("Host/cpu"); if (isnull(cpu)) audit(AUDIT_UNKNOWN_ARCH); if ("x86_64" >!< cpu && cpu !~ "^i[3-6]86$") audit(AUDIT_LOCAL_CHECKS_NOT_IMPLEMENTED, "OracleVM", cpu); if ("x86_64" >!< cpu) audit(AUDIT_ARCH_NOT, "x86_64", cpu); flag = 0; if (rpm_check(release:"OVS3.3", reference:"kernel-uek-3.8.13-118.2.5.el6uek")) flag++; if (rpm_check(release:"OVS3.3", reference:"kernel-uek-firmware-3.8.13-118.2.5.el6uek")) flag++; if (flag) { if (report_verbosity > 0) security_hole(port:0, extra:rpm_report_get()); else security_hole(0); exit(0); } else { tested = pkg_tests_get(); if (tested) audit(AUDIT_PACKAGE_NOT_AFFECTED, tested); else audit(AUDIT_PACKAGE_NOT_INSTALLED, "kernel-uek / kernel-uek-firmware"); }NASL family Red Hat Local Security Checks NASL id REDHAT-RHSA-2016-0103.NASL description Updated kernel packages that fix three security issues, multiple bugs, and one enhancement are now available for Red Hat Enterprise Linux 7.1 Extended Update Support. Red Hat Product Security has rated this update as having Important security impact. Common Vulnerability Scoring System (CVSS) base scores, which give detailed severity ratings, are available for each vulnerability from the CVE links in the References section. The kernel packages contain the Linux kernel, the core of any Linux operating system. * It was found that the x86 ISA (Instruction Set Architecture) is prone to a denial of service attack inside a virtualized environment in the form of an infinite loop in the microcode due to the way (sequential) delivering of benign exceptions such as #DB (debug exception) is handled. A privileged user inside a guest could use this flaw to create denial of service conditions on the host kernel. (CVE-2015-8104, Important) * A use-after-free flaw was found in the way the Linux kernel last seen 2020-06-01 modified 2020-06-02 plugin id 88558 published 2016-02-03 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/88558 title RHEL 7 : kernel (RHSA-2016:0103) code # # (C) Tenable Network Security, Inc. # # The descriptive text and package checks in this plugin were # extracted from Red Hat Security Advisory RHSA-2016:0103. The text # itself is copyright (C) Red Hat, Inc. # include("compat.inc"); if (description) { script_id(88558); script_version("2.13"); script_cvs_date("Date: 2019/10/24 15:35:41"); script_cve_id("CVE-2015-8104", "CVE-2016-0728", "CVE-2016-0774"); script_xref(name:"RHSA", value:"2016:0103"); script_name(english:"RHEL 7 : kernel (RHSA-2016:0103)"); script_summary(english:"Checks the rpm output for the updated packages"); script_set_attribute( attribute:"synopsis", value:"The remote Red Hat host is missing one or more security updates." ); script_set_attribute( attribute:"description", value: "Updated kernel packages that fix three security issues, multiple bugs, and one enhancement are now available for Red Hat Enterprise Linux 7.1 Extended Update Support. Red Hat Product Security has rated this update as having Important security impact. Common Vulnerability Scoring System (CVSS) base scores, which give detailed severity ratings, are available for each vulnerability from the CVE links in the References section. The kernel packages contain the Linux kernel, the core of any Linux operating system. * It was found that the x86 ISA (Instruction Set Architecture) is prone to a denial of service attack inside a virtualized environment in the form of an infinite loop in the microcode due to the way (sequential) delivering of benign exceptions such as #DB (debug exception) is handled. A privileged user inside a guest could use this flaw to create denial of service conditions on the host kernel. (CVE-2015-8104, Important) * A use-after-free flaw was found in the way the Linux kernel's key management subsystem handled keyring object reference counting in certain error path of the join_session_keyring() function. A local, unprivileged user could use this flaw to escalate their privileges on the system. (CVE-2016-0728, Important) * It was found that the fix for CVE-2015-1805 incorrectly kept buffer offset and buffer length in sync on a failed atomic read, potentially resulting in a pipe buffer state corruption. A local, unprivileged user could use this flaw to crash the system or leak kernel memory to user space. (CVE-2016-0774, Moderate) Red Hat would like to thank the Perception Point research team for reporting the CVE-2016-0728 issue. The security impact of the CVE-2016-0774 issue was discovered by Red Hat. Bug fixes : * NMI watchdog of guests using legacy LVT0-based NMI delivery did not work with APICv. Now, NMI works with LVT0 regardless of APICv. (BZ#1244726) * Parallel file-extending direct I/O writes could previously race to update the size of the file. If they executed out-of-order, the file size could move backwards and push a previously completed write beyond the end of the file, causing it to be lost. (BZ#1258942) * The GHES NMI handler had a global spin lock that significantly increased the latency of each perf sample collection. This update simplifies locking inside the handler. (BZ#1280200) * Sometimes, iptables rules are updated along with ip rules, and routes are reloaded. Previously, skb->sk was mistakenly attached to some IPv6 forwarding traffic packets, which could cause kernel panic. Now, such packets are checked and not processed. (BZ#1281700) * The NUMA node was not reported for PCI adapters, which affected every POWER system deployed with Red Hat Enterprise Linux 7 and caused significant decrease in the system performance. (BZ#1283525) * Processing packets with a lot of different IPv6 source addresses caused the kernel to return warnings concerning soft-lockups due to high lock contention and latency increase. (BZ#1285369) * Running edge triggered interrupts with an ack notifier when simultaneously reconfiguring the Intel I/O IOAPIC did not work correctly, so EOI in the interrupt did not cause a VM to exit if APICv was enabled. Consequently, the VM sometimes became unresponsive. (BZ#1287001) * Block device readahead was artificially limited, so the read performance was poor, especially on RAID devices. Now, per-device readahead limits are used for each device, which has improved read performance. (BZ#1287548) * Identical expectations could not be tracked simultaneously even if they resided in different connection tracking zones. Now, an expectation insert attempt is rejected only if the zone is also identical. (BZ#1290093) * The storvsc kernel driver for Microsoft Hyper-V storage was setting incorrect SRB flags, and Red Hat Enterprise Linux 7 guests running on Microsoft Hyper-V were experiencing slow I/O as well as I/O failures when they were connected to a virtual SAN. Now, SRB flags are set correctly. (BZ#1290095) * When a NUMA system with no memory in node 0 was used, the system terminated unexpectedly during boot or when using OpenVSwitch. Now, the kernel tries to allocate memory from other nodes when node 0 is not present. (BZ#1300950) Enhancement : * IPsec has been updated to provide many fixes and some enhancements. Of particular note is the ability to match on outgoing interfaces. (BZ#1287407)" ); script_set_attribute( attribute:"see_also", value:"https://access.redhat.com/errata/RHSA-2016:0103" ); script_set_attribute( attribute:"see_also", value:"https://access.redhat.com/security/cve/cve-2015-8104" ); script_set_attribute( attribute:"see_also", value:"https://access.redhat.com/security/cve/cve-2016-0728" ); script_set_attribute( attribute:"see_also", value:"https://access.redhat.com/security/cve/cve-2016-0774" ); script_set_attribute(attribute:"solution", value:"Update the affected packages."); script_set_cvss_base_vector("CVSS2#AV:L/AC:L/Au:N/C:C/I:C/A:C"); script_set_cvss_temporal_vector("CVSS2#E:H/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:H/RL:O/RC:C"); script_set_attribute(attribute:"exploitability_ease", value:"Exploits are available"); script_set_attribute(attribute:"exploit_available", value:"true"); script_set_attribute(attribute:"exploit_framework_core", value:"true"); script_set_attribute(attribute:"exploited_by_malware", value:"true"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:kernel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:kernel-abi-whitelists"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:kernel-debug"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:kernel-debug-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:kernel-debug-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:kernel-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:kernel-debuginfo-common-s390x"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:kernel-debuginfo-common-x86_64"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:kernel-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:kernel-doc"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:kernel-headers"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:kernel-kdump"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:kernel-kdump-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:kernel-kdump-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:kernel-tools"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:kernel-tools-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:kernel-tools-libs"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:kernel-tools-libs-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:perf"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:perf-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:python-perf"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:python-perf-debuginfo"); script_set_attribute(attribute:"cpe", value:"cpe:/o:redhat:enterprise_linux:7.1"); script_set_attribute(attribute:"vuln_publication_date", value:"2015/11/16"); script_set_attribute(attribute:"patch_publication_date", value:"2016/02/02"); script_set_attribute(attribute:"plugin_publication_date", value:"2016/02/03"); script_set_attribute(attribute:"generated_plugin", value:"current"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_copyright(english:"This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof."); script_family(english:"Red Hat Local Security Checks"); script_dependencies("ssh_get_info.nasl", "linux_alt_patch_detect.nasl"); script_require_keys("Host/local_checks_enabled", "Host/RedHat/release", "Host/RedHat/rpm-list", "Host/cpu"); exit(0); } include("audit.inc"); include("global_settings.inc"); include("misc_func.inc"); include("rpm.inc"); include("ksplice.inc"); if (!get_kb_item("Host/local_checks_enabled")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); release = get_kb_item("Host/RedHat/release"); if (isnull(release) || "Red Hat" >!< release) audit(AUDIT_OS_NOT, "Red Hat"); os_ver = pregmatch(pattern: "Red Hat Enterprise Linux.*release ([0-9]+(\.[0-9]+)?)", string:release); if (isnull(os_ver)) audit(AUDIT_UNKNOWN_APP_VER, "Red Hat"); os_ver = os_ver[1]; if (! preg(pattern:"^7\.1([^0-9]|$)", string:os_ver)) audit(AUDIT_OS_NOT, "Red Hat 7.1", "Red Hat " + os_ver); if (!get_kb_item("Host/RedHat/rpm-list")) audit(AUDIT_PACKAGE_LIST_MISSING); cpu = get_kb_item("Host/cpu"); if (isnull(cpu)) audit(AUDIT_UNKNOWN_ARCH); if ("x86_64" >!< cpu && cpu !~ "^i[3-6]86$" && "s390" >!< cpu) audit(AUDIT_LOCAL_CHECKS_NOT_IMPLEMENTED, "Red Hat", cpu); if (get_one_kb_item("Host/ksplice/kernel-cves")) { rm_kb_item(name:"Host/uptrack-uname-r"); cve_list = make_list("CVE-2015-8104", "CVE-2016-0728", "CVE-2016-0774"); if (ksplice_cves_check(cve_list)) { audit(AUDIT_PATCH_INSTALLED, "KSplice hotfix for RHSA-2016:0103"); } else { __rpm_report = ksplice_reporting_text(); } } yum_updateinfo = get_kb_item("Host/RedHat/yum-updateinfo"); if (!empty_or_null(yum_updateinfo)) { rhsa = "RHSA-2016:0103"; yum_report = redhat_generate_yum_updateinfo_report(rhsa:rhsa); if (!empty_or_null(yum_report)) { security_report_v4( port : 0, severity : SECURITY_HOLE, extra : yum_report ); exit(0); } else { audit_message = "affected by Red Hat security advisory " + rhsa; audit(AUDIT_OS_NOT, audit_message); } } else { flag = 0; if (rpm_check(release:"RHEL7", sp:"1", cpu:"s390x", reference:"kernel-3.10.0-229.26.2.el7")) flag++; if (rpm_check(release:"RHEL7", sp:"1", cpu:"x86_64", reference:"kernel-3.10.0-229.26.2.el7")) flag++; if (rpm_check(release:"RHEL7", sp:"1", reference:"kernel-abi-whitelists-3.10.0-229.26.2.el7")) flag++; if (rpm_check(release:"RHEL7", sp:"1", cpu:"s390x", reference:"kernel-debug-3.10.0-229.26.2.el7")) flag++; if (rpm_check(release:"RHEL7", sp:"1", cpu:"x86_64", reference:"kernel-debug-3.10.0-229.26.2.el7")) flag++; if (rpm_check(release:"RHEL7", sp:"1", cpu:"s390x", reference:"kernel-debug-debuginfo-3.10.0-229.26.2.el7")) flag++; if (rpm_check(release:"RHEL7", sp:"1", cpu:"x86_64", reference:"kernel-debug-debuginfo-3.10.0-229.26.2.el7")) flag++; if (rpm_check(release:"RHEL7", sp:"1", cpu:"s390x", reference:"kernel-debug-devel-3.10.0-229.26.2.el7")) flag++; if (rpm_check(release:"RHEL7", sp:"1", cpu:"x86_64", reference:"kernel-debug-devel-3.10.0-229.26.2.el7")) flag++; if (rpm_check(release:"RHEL7", sp:"1", cpu:"s390x", reference:"kernel-debuginfo-3.10.0-229.26.2.el7")) flag++; if (rpm_check(release:"RHEL7", sp:"1", cpu:"x86_64", reference:"kernel-debuginfo-3.10.0-229.26.2.el7")) flag++; if (rpm_check(release:"RHEL7", sp:"1", cpu:"s390x", reference:"kernel-debuginfo-common-s390x-3.10.0-229.26.2.el7")) flag++; if (rpm_check(release:"RHEL7", sp:"1", cpu:"x86_64", reference:"kernel-debuginfo-common-x86_64-3.10.0-229.26.2.el7")) flag++; if (rpm_check(release:"RHEL7", sp:"1", cpu:"s390x", reference:"kernel-devel-3.10.0-229.26.2.el7")) flag++; if (rpm_check(release:"RHEL7", sp:"1", cpu:"x86_64", reference:"kernel-devel-3.10.0-229.26.2.el7")) flag++; if (rpm_check(release:"RHEL7", sp:"1", reference:"kernel-doc-3.10.0-229.26.2.el7")) flag++; if (rpm_check(release:"RHEL7", sp:"1", cpu:"s390x", reference:"kernel-headers-3.10.0-229.26.2.el7")) flag++; if (rpm_check(release:"RHEL7", sp:"1", cpu:"x86_64", reference:"kernel-headers-3.10.0-229.26.2.el7")) flag++; if (rpm_check(release:"RHEL7", sp:"1", cpu:"s390x", reference:"kernel-kdump-3.10.0-229.26.2.el7")) flag++; if (rpm_check(release:"RHEL7", sp:"1", cpu:"s390x", reference:"kernel-kdump-debuginfo-3.10.0-229.26.2.el7")) flag++; if (rpm_check(release:"RHEL7", sp:"1", cpu:"s390x", reference:"kernel-kdump-devel-3.10.0-229.26.2.el7")) flag++; if (rpm_check(release:"RHEL7", sp:"1", cpu:"x86_64", reference:"kernel-tools-3.10.0-229.26.2.el7")) flag++; if (rpm_check(release:"RHEL7", sp:"1", cpu:"x86_64", reference:"kernel-tools-debuginfo-3.10.0-229.26.2.el7")) flag++; if (rpm_check(release:"RHEL7", sp:"1", cpu:"x86_64", reference:"kernel-tools-libs-3.10.0-229.26.2.el7")) flag++; if (rpm_check(release:"RHEL7", sp:"1", cpu:"x86_64", reference:"kernel-tools-libs-devel-3.10.0-229.26.2.el7")) flag++; if (rpm_check(release:"RHEL7", sp:"1", cpu:"s390x", reference:"perf-3.10.0-229.26.2.el7")) flag++; if (rpm_check(release:"RHEL7", sp:"1", cpu:"x86_64", reference:"perf-3.10.0-229.26.2.el7")) flag++; if (rpm_check(release:"RHEL7", sp:"1", cpu:"s390x", reference:"perf-debuginfo-3.10.0-229.26.2.el7")) flag++; if (rpm_check(release:"RHEL7", sp:"1", cpu:"x86_64", reference:"perf-debuginfo-3.10.0-229.26.2.el7")) flag++; if (rpm_check(release:"RHEL7", sp:"1", cpu:"s390x", reference:"python-perf-3.10.0-229.26.2.el7")) flag++; if (rpm_check(release:"RHEL7", sp:"1", cpu:"x86_64", reference:"python-perf-3.10.0-229.26.2.el7")) flag++; if (rpm_check(release:"RHEL7", sp:"1", cpu:"s390x", reference:"python-perf-debuginfo-3.10.0-229.26.2.el7")) flag++; if (rpm_check(release:"RHEL7", sp:"1", cpu:"x86_64", reference:"python-perf-debuginfo-3.10.0-229.26.2.el7")) flag++; if (flag) { security_report_v4( port : 0, severity : SECURITY_HOLE, extra : rpm_report_get() + redhat_report_package_caveat() ); exit(0); } else { tested = pkg_tests_get(); if (tested) audit(AUDIT_PACKAGE_NOT_AFFECTED, tested); else audit(AUDIT_PACKAGE_NOT_INSTALLED, "kernel / kernel-abi-whitelists / kernel-debug / etc"); } }NASL family SuSE Local Security Checks NASL id OPENSUSE-2016-124.NASL description The openSUSE 13.1 kernel was updated to receive various security and bugfixes. Following security bugs were fixed : - CVE-2016-0728: A reference leak in keyring handling with join_session_keyring() could lead to local attackers gain root privileges. (bsc#962075). - CVE-2015-7550: A local user could have triggered a race between read and revoke in keyctl (bnc#958951). - CVE-2015-8569: The (1) pptp_bind and (2) pptp_connect functions in drivers/net/ppp/pptp.c in the Linux kernel did not verify an address length, which allowed local users to obtain sensitive information from kernel memory and bypass the KASLR protection mechanism via a crafted application (bnc#959190). - CVE-2015-8543: The networking implementation in the Linux kernel did not validate protocol identifiers for certain protocol families, which allowed local users to cause a denial of service (NULL function pointer dereference and system crash) or possibly gain privileges by leveraging CLONE_NEWUSER support to execute a crafted SOCK_RAW application (bnc#958886). - CVE-2014-8989: The Linux kernel did not properly restrict dropping of supplemental group memberships in certain namespace scenarios, which allowed local users to bypass intended file permissions by leveraging a POSIX ACL containing an entry for the group category that is more restrictive than the entry for the other category, aka a last seen 2020-06-05 modified 2016-02-03 plugin id 88545 published 2016-02-03 reporter This script is Copyright (C) 2016-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/88545 title openSUSE Security Update : the Linux Kernel (openSUSE-2016-124) code #%NASL_MIN_LEVEL 80502 # # (C) Tenable Network Security, Inc. # # The descriptive text and package checks in this plugin were # extracted from openSUSE Security Update openSUSE-2016-124. # # The text description of this plugin is (C) SUSE LLC. # include("compat.inc"); if (description) { script_id(88545); script_version("2.7"); script_set_attribute(attribute:"plugin_modification_date", value:"2020/06/04"); script_cve_id("CVE-2014-2568", "CVE-2014-8133", "CVE-2014-8989", "CVE-2014-9090", "CVE-2014-9419", "CVE-2014-9529", "CVE-2014-9683", "CVE-2014-9715", "CVE-2014-9728", "CVE-2014-9729", "CVE-2014-9730", "CVE-2014-9731", "CVE-2015-0272", "CVE-2015-0777", "CVE-2015-1420", "CVE-2015-1421", "CVE-2015-2041", "CVE-2015-2042", "CVE-2015-2150", "CVE-2015-2666", "CVE-2015-2830", "CVE-2015-2922", "CVE-2015-2925", "CVE-2015-3212", "CVE-2015-3339", "CVE-2015-3636", "CVE-2015-4001", "CVE-2015-4002", "CVE-2015-4003", "CVE-2015-4004", "CVE-2015-4036", "CVE-2015-4167", "CVE-2015-4692", "CVE-2015-4700", "CVE-2015-5157", "CVE-2015-5283", "CVE-2015-5307", "CVE-2015-5364", "CVE-2015-5366", "CVE-2015-5707", "CVE-2015-6937", "CVE-2015-7550", "CVE-2015-7799", "CVE-2015-7833", "CVE-2015-7872", "CVE-2015-7885", "CVE-2015-7990", "CVE-2015-8104", "CVE-2015-8215", "CVE-2015-8543", "CVE-2015-8550", "CVE-2015-8551", "CVE-2015-8552", "CVE-2015-8569", "CVE-2015-8575", "CVE-2015-8767", "CVE-2016-0728"); script_name(english:"openSUSE Security Update : the Linux Kernel (openSUSE-2016-124)"); script_summary(english:"Check for the openSUSE-2016-124 patch"); script_set_attribute( attribute:"synopsis", value:"The remote openSUSE host is missing a security update." ); script_set_attribute( attribute:"description", value: "The openSUSE 13.1 kernel was updated to receive various security and bugfixes. Following security bugs were fixed : - CVE-2016-0728: A reference leak in keyring handling with join_session_keyring() could lead to local attackers gain root privileges. (bsc#962075). - CVE-2015-7550: A local user could have triggered a race between read and revoke in keyctl (bnc#958951). - CVE-2015-8569: The (1) pptp_bind and (2) pptp_connect functions in drivers/net/ppp/pptp.c in the Linux kernel did not verify an address length, which allowed local users to obtain sensitive information from kernel memory and bypass the KASLR protection mechanism via a crafted application (bnc#959190). - CVE-2015-8543: The networking implementation in the Linux kernel did not validate protocol identifiers for certain protocol families, which allowed local users to cause a denial of service (NULL function pointer dereference and system crash) or possibly gain privileges by leveraging CLONE_NEWUSER support to execute a crafted SOCK_RAW application (bnc#958886). - CVE-2014-8989: The Linux kernel did not properly restrict dropping of supplemental group memberships in certain namespace scenarios, which allowed local users to bypass intended file permissions by leveraging a POSIX ACL containing an entry for the group category that is more restrictive than the entry for the other category, aka a 'negative groups' issue, related to kernel/groups.c, kernel/uid16.c, and kernel/user_namespace.c (bnc#906545). - CVE-2015-5157: arch/x86/entry/entry_64.S in the Linux kernel on the x86_64 platform mishandles IRET faults in processing NMIs that occurred during userspace execution, which might allow local users to gain privileges by triggering an NMI (bnc#937969). - CVE-2015-7799: The slhc_init function in drivers/net/slip/slhc.c in the Linux kernel through 4.2.3 did not ensure that certain slot numbers are valid, which allowed local users to cause a denial of service (NULL pointer dereference and system crash) via a crafted PPPIOCSMAXCID ioctl call (bnc#949936). - CVE-2015-8104: The KVM subsystem in the Linux kernel through 4.2.6, and Xen 4.3.x through 4.6.x, allowed guest OS users to cause a denial of service (host OS panic or hang) by triggering many #DB (aka Debug) exceptions, related to svm.c (bnc#954404). - CVE-2015-5307: The KVM subsystem in the Linux kernel through 4.2.6, and Xen 4.3.x through 4.6.x, allowed guest OS users to cause a denial of service (host OS panic or hang) by triggering many #AC (aka Alignment Check) exceptions, related to svm.c and vmx.c (bnc#953527). - CVE-2014-9529: Race condition in the key_gc_unused_keys function in security/keys/gc.c in the Linux kernel allowed local users to cause a denial of service (memory corruption or panic) or possibly have unspecified other impact via keyctl commands that trigger access to a key structure member during garbage collection of a key (bnc#912202). - CVE-2015-7990: Race condition in the rds_sendmsg function in net/rds/sendmsg.c in the Linux kernel allowed local users to cause a denial of service (NULL pointer dereference and system crash) or possibly have unspecified other impact by using a socket that was not properly bound. NOTE: this vulnerability exists because of an incomplete fix for CVE-2015-6937 (bnc#952384 953052). - CVE-2015-6937: The __rds_conn_create function in net/rds/connection.c in the Linux kernel allowed local users to cause a denial of service (NULL pointer dereference and system crash) or possibly have unspecified other impact by using a socket that was not properly bound (bnc#945825). - CVE-2015-7885: The dgnc_mgmt_ioctl function in drivers/staging/dgnc/dgnc_mgmt.c in the Linux kernel through 4.3.3 did not initialize a certain structure member, which allowed local users to obtain sensitive information from kernel memory via a crafted application (bnc#951627). - CVE-2015-8215: net/ipv6/addrconf.c in the IPv6 stack in the Linux kernel did not validate attempted changes to the MTU value, which allowed context-dependent attackers to cause a denial of service (packet loss) via a value that is (1) smaller than the minimum compliant value or (2) larger than the MTU of an interface, as demonstrated by a Router Advertisement (RA) message that is not validated by a daemon, a different vulnerability than CVE-2015-0272. NOTE: the scope of CVE-2015-0272 is limited to the NetworkManager product (bnc#955354). - CVE-2015-8767: A case can occur when sctp_accept() is called by the user during a heartbeat timeout event after the 4-way handshake. Since sctp_assoc_migrate() changes both assoc->base.sk and assoc->ep, the bh_sock_lock in sctp_generate_heartbeat_event() will be taken with the listening socket but released with the new association socket. The result is a deadlock on any future attempts to take the listening socket lock. (bsc#961509) - CVE-2015-8575: Validate socket address length in sco_sock_bind() to prevent information leak (bsc#959399). - CVE-2015-8551, CVE-2015-8552: xen/pciback: For XEN_PCI_OP_disable_msi[|x] only disable if device has MSI(X) enabled (bsc#957990). - CVE-2015-8550: Compiler optimizations in the XEN PV backend drivers could have lead to double fetch vulnerabilities, causing denial of service or arbitrary code execution (depending on the configuration) (bsc#957988). The following non-security bugs were fixed : - ALSA: hda - Disable 64bit address for Creative HDA controllers (bnc#814440). - ALSA: hda - Fix noise problems on Thinkpad T440s (boo#958504). - Input: aiptek - fix crash on detecting device without endpoints (bnc#956708). - KEYS: Make /proc/keys unconditional if CONFIG_KEYS=y (boo#956934). - KVM: x86: update masterclock values on TSC writes (bsc#961739). - NFS: Fix a NULL pointer dereference of migration recovery ops for v4.2 client (bsc#960839). - apparmor: allow SYS_CAP_RESOURCE to be sufficient to prlimit another task (bsc#921949). - blktap: also call blkif_disconnect() when frontend switched to closed (bsc#952976). - blktap: refine mm tracking (bsc#952976). - cdrom: Random writing support for BD-RE media (bnc#959568). - genksyms: Handle string literals with spaces in reference files (bsc#958510). - ipv4: Do not increase PMTU with Datagram Too Big message (bsc#955224). - ipv6: distinguish frag queues by device for multicast and link-local packets (bsc#955422). - ipv6: fix tunnel error handling (bsc#952579). - route: Use ipv4_mtu instead of raw rt_pmtu (bsc#955224). - uas: Add response iu handling (bnc#954138). - usbvision fix overflow of interfaces array (bnc#950998). - x86/evtchn: make use of PHYSDEVOP_map_pirq. - xen/pciback: Do not allow MSI-X ops if PCI_COMMAND_MEMORY is not set (bsc#957990 XSA-157)." ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=814440" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=851610" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=869564" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=873385" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=906545" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=907818" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=909077" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=909477" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=911326" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=912202" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=915517" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=915577" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=917830" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=918333" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=919007" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=919018" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=919463" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=919596" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=921313" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=921949" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=922583" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=922936" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=922944" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=926238" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=926240" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=927780" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=927786" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=928130" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=929525" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=930399" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=931988" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=932348" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=933896" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=933904" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=933907" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=933934" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=935542" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=935705" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=936502" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=936831" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=937032" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=937033" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=937969" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=938706" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=940338" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=944296" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=945825" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=947155" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=949936" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=950998" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=951194" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=951440" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=951627" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=952384" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=952579" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=952976" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=953052" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=953527" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=954138" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=954404" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=955224" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=955354" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=955422" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=956708" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=956934" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=957988" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=957990" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=958504" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=958510" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=958886" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=958951" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=959190" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=959399" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=959568" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=960839" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=961509" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=961739" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=962075" ); script_set_attribute( attribute:"solution", value:"Update the affected the Linux Kernel packages." ); script_set_cvss_base_vector("CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:C"); script_set_cvss_temporal_vector("CVSS2#E:H/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:L/AC:L/PR:H/UI:N/S:C/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:H/RL:O/RC:C"); script_set_attribute(attribute:"exploitability_ease", value:"Exploits are available"); script_set_attribute(attribute:"exploit_available", value:"true"); script_set_attribute(attribute:"exploit_framework_core", value:"true"); script_set_attribute(attribute:"exploited_by_malware", value:"true"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:cloop"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:cloop-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:cloop-debugsource"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:cloop-kmp-default"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:cloop-kmp-default-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:cloop-kmp-desktop"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:cloop-kmp-desktop-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:cloop-kmp-pae"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:cloop-kmp-pae-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:cloop-kmp-xen"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:cloop-kmp-xen-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:crash"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:crash-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:crash-debugsource"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:crash-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:crash-eppic"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:crash-eppic-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:crash-gcore"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:crash-gcore-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:crash-kmp-default"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:crash-kmp-default-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:crash-kmp-desktop"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:crash-kmp-desktop-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:crash-kmp-pae"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:crash-kmp-pae-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:crash-kmp-xen"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:crash-kmp-xen-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:hdjmod-debugsource"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:hdjmod-kmp-default"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:hdjmod-kmp-default-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:hdjmod-kmp-desktop"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:hdjmod-kmp-desktop-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:hdjmod-kmp-pae"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:hdjmod-kmp-pae-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:hdjmod-kmp-xen"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:hdjmod-kmp-xen-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:ipset"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:ipset-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:ipset-debugsource"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:ipset-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:ipset-kmp-default"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:ipset-kmp-default-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:ipset-kmp-desktop"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:ipset-kmp-desktop-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:ipset-kmp-pae"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:ipset-kmp-pae-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:ipset-kmp-xen"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:ipset-kmp-xen-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:iscsitarget"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:iscsitarget-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:iscsitarget-debugsource"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:iscsitarget-kmp-default"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:iscsitarget-kmp-default-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:iscsitarget-kmp-desktop"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:iscsitarget-kmp-desktop-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:iscsitarget-kmp-pae"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:iscsitarget-kmp-pae-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:iscsitarget-kmp-xen"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:iscsitarget-kmp-xen-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-debug"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-debug-base"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-debug-base-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-debug-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-debug-debugsource"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-debug-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-debug-devel-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-default"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-default-base"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-default-base-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-default-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-default-debugsource"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-default-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-default-devel-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-desktop"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-desktop-base"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-desktop-base-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-desktop-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-desktop-debugsource"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-desktop-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-desktop-devel-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-ec2"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-ec2-base"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-ec2-base-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-ec2-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-ec2-debugsource"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-ec2-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-ec2-devel-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-pae"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-pae-base"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-pae-base-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-pae-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-pae-debugsource"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-pae-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-pae-devel-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-source"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-source-vanilla"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-syms"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-trace"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-trace-base"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-trace-base-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-trace-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-trace-debugsource"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-trace-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-trace-devel-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-vanilla"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-vanilla-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-vanilla-debugsource"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-vanilla-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-vanilla-devel-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-xen"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-xen-base"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-xen-base-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-xen-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-xen-debugsource"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-xen-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-xen-devel-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:libipset3"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:libipset3-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:ndiswrapper"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:ndiswrapper-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:ndiswrapper-debugsource"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:ndiswrapper-kmp-default"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:ndiswrapper-kmp-default-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:ndiswrapper-kmp-desktop"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:ndiswrapper-kmp-desktop-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:ndiswrapper-kmp-pae"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:ndiswrapper-kmp-pae-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:pcfclock"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:pcfclock-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:pcfclock-debugsource"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:pcfclock-kmp-default"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:pcfclock-kmp-default-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:pcfclock-kmp-desktop"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:pcfclock-kmp-desktop-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:pcfclock-kmp-pae"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:pcfclock-kmp-pae-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:python-virtualbox"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:python-virtualbox-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:vhba-kmp-debugsource"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:vhba-kmp-default"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:vhba-kmp-default-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:vhba-kmp-desktop"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:vhba-kmp-desktop-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:vhba-kmp-pae"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:vhba-kmp-pae-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:vhba-kmp-xen"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:vhba-kmp-xen-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:virtualbox"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:virtualbox-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:virtualbox-debugsource"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:virtualbox-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:virtualbox-guest-kmp-default"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:virtualbox-guest-kmp-default-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:virtualbox-guest-kmp-desktop"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:virtualbox-guest-kmp-desktop-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:virtualbox-guest-kmp-pae"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:virtualbox-guest-kmp-pae-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:virtualbox-guest-tools"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:virtualbox-guest-tools-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:virtualbox-guest-x11"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:virtualbox-guest-x11-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:virtualbox-host-kmp-default"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:virtualbox-host-kmp-default-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:virtualbox-host-kmp-desktop"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:virtualbox-host-kmp-desktop-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:virtualbox-host-kmp-pae"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:virtualbox-host-kmp-pae-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:virtualbox-host-source"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:virtualbox-qt"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:virtualbox-qt-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:virtualbox-websrv"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:virtualbox-websrv-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xen"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xen-debugsource"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xen-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xen-doc-html"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xen-kmp-default"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xen-kmp-default-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xen-kmp-desktop"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xen-kmp-desktop-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xen-kmp-pae"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xen-kmp-pae-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xen-libs"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xen-libs-32bit"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xen-libs-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xen-libs-debuginfo-32bit"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xen-tools"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xen-tools-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xen-tools-domU"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xen-tools-domU-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xen-xend-tools"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xen-xend-tools-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xtables-addons"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xtables-addons-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xtables-addons-debugsource"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xtables-addons-kmp-default"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xtables-addons-kmp-default-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xtables-addons-kmp-desktop"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xtables-addons-kmp-desktop-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xtables-addons-kmp-pae"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xtables-addons-kmp-pae-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xtables-addons-kmp-xen"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xtables-addons-kmp-xen-debuginfo"); script_set_attribute(attribute:"cpe", value:"cpe:/o:novell:opensuse:13.1"); script_set_attribute(attribute:"patch_publication_date", value:"2016/02/08"); script_set_attribute(attribute:"plugin_publication_date", value:"2016/02/03"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_copyright(english:"This script is Copyright (C) 2016-2020 and is owned by Tenable, Inc. or an Affiliate thereof."); script_family(english:"SuSE Local Security Checks"); script_dependencies("ssh_get_info.nasl"); script_require_keys("Host/local_checks_enabled", "Host/SuSE/release", "Host/SuSE/rpm-list", "Host/cpu"); exit(0); } include("audit.inc"); include("global_settings.inc"); include("rpm.inc"); if (!get_kb_item("Host/local_checks_enabled")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); release = get_kb_item("Host/SuSE/release"); if (isnull(release) || release =~ "^(SLED|SLES)") audit(AUDIT_OS_NOT, "openSUSE"); if (release !~ "^(SUSE13\.1)$") audit(AUDIT_OS_RELEASE_NOT, "openSUSE", "13.1", release); if (!get_kb_item("Host/SuSE/rpm-list")) audit(AUDIT_PACKAGE_LIST_MISSING); ourarch = get_kb_item("Host/cpu"); if (!ourarch) audit(AUDIT_UNKNOWN_ARCH); if (ourarch !~ "^(i586|i686|x86_64)$") audit(AUDIT_ARCH_NOT, "i586 / i686 / x86_64", ourarch); flag = 0; if ( rpm_check(release:"SUSE13.1", reference:"cloop-2.639-11.23.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"cloop-debuginfo-2.639-11.23.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"cloop-debugsource-2.639-11.23.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"cloop-kmp-default-2.639_k3.11.10_34-11.23.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"cloop-kmp-default-debuginfo-2.639_k3.11.10_34-11.23.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"cloop-kmp-desktop-2.639_k3.11.10_34-11.23.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"cloop-kmp-desktop-debuginfo-2.639_k3.11.10_34-11.23.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"cloop-kmp-pae-2.639_k3.11.10_34-11.23.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"cloop-kmp-pae-debuginfo-2.639_k3.11.10_34-11.23.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"cloop-kmp-xen-2.639_k3.11.10_34-11.23.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"cloop-kmp-xen-debuginfo-2.639_k3.11.10_34-11.23.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"crash-7.0.2-2.23.7") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"crash-debuginfo-7.0.2-2.23.7") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"crash-debugsource-7.0.2-2.23.7") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"crash-devel-7.0.2-2.23.7") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"crash-eppic-7.0.2-2.23.7") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"crash-eppic-debuginfo-7.0.2-2.23.7") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"crash-gcore-7.0.2-2.23.7") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"crash-gcore-debuginfo-7.0.2-2.23.7") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"crash-kmp-default-7.0.2_k3.11.10_34-2.23.7") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"crash-kmp-default-debuginfo-7.0.2_k3.11.10_34-2.23.7") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"crash-kmp-desktop-7.0.2_k3.11.10_34-2.23.7") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"crash-kmp-desktop-debuginfo-7.0.2_k3.11.10_34-2.23.7") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"crash-kmp-pae-7.0.2_k3.11.10_34-2.23.7") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"crash-kmp-pae-debuginfo-7.0.2_k3.11.10_34-2.23.7") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"crash-kmp-xen-7.0.2_k3.11.10_34-2.23.7") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"crash-kmp-xen-debuginfo-7.0.2_k3.11.10_34-2.23.7") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"hdjmod-debugsource-1.28-16.23.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"hdjmod-kmp-default-1.28_k3.11.10_34-16.23.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"hdjmod-kmp-default-debuginfo-1.28_k3.11.10_34-16.23.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"hdjmod-kmp-desktop-1.28_k3.11.10_34-16.23.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"hdjmod-kmp-desktop-debuginfo-1.28_k3.11.10_34-16.23.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"hdjmod-kmp-pae-1.28_k3.11.10_34-16.23.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"hdjmod-kmp-pae-debuginfo-1.28_k3.11.10_34-16.23.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"hdjmod-kmp-xen-1.28_k3.11.10_34-16.23.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"hdjmod-kmp-xen-debuginfo-1.28_k3.11.10_34-16.23.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"ipset-6.21.1-2.27.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"ipset-debuginfo-6.21.1-2.27.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"ipset-debugsource-6.21.1-2.27.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"ipset-devel-6.21.1-2.27.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"ipset-kmp-default-6.21.1_k3.11.10_34-2.27.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"ipset-kmp-default-debuginfo-6.21.1_k3.11.10_34-2.27.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"ipset-kmp-desktop-6.21.1_k3.11.10_34-2.27.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"ipset-kmp-desktop-debuginfo-6.21.1_k3.11.10_34-2.27.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"ipset-kmp-pae-6.21.1_k3.11.10_34-2.27.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"ipset-kmp-pae-debuginfo-6.21.1_k3.11.10_34-2.27.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"ipset-kmp-xen-6.21.1_k3.11.10_34-2.27.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"ipset-kmp-xen-debuginfo-6.21.1_k3.11.10_34-2.27.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"iscsitarget-1.4.20.3-13.23.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"iscsitarget-debuginfo-1.4.20.3-13.23.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"iscsitarget-debugsource-1.4.20.3-13.23.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"iscsitarget-kmp-default-1.4.20.3_k3.11.10_34-13.23.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"iscsitarget-kmp-default-debuginfo-1.4.20.3_k3.11.10_34-13.23.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"iscsitarget-kmp-desktop-1.4.20.3_k3.11.10_34-13.23.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"iscsitarget-kmp-desktop-debuginfo-1.4.20.3_k3.11.10_34-13.23.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"iscsitarget-kmp-pae-1.4.20.3_k3.11.10_34-13.23.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"iscsitarget-kmp-pae-debuginfo-1.4.20.3_k3.11.10_34-13.23.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"iscsitarget-kmp-xen-1.4.20.3_k3.11.10_34-13.23.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"iscsitarget-kmp-xen-debuginfo-1.4.20.3_k3.11.10_34-13.23.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"kernel-default-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"kernel-default-base-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"kernel-default-base-debuginfo-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"kernel-default-debuginfo-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"kernel-default-debugsource-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"kernel-default-devel-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"kernel-default-devel-debuginfo-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"kernel-devel-3.11.10-34.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"kernel-source-3.11.10-34.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"kernel-source-vanilla-3.11.10-34.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"kernel-syms-3.11.10-34.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"libipset3-6.21.1-2.27.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"libipset3-debuginfo-6.21.1-2.27.2") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"ndiswrapper-1.58-23.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"ndiswrapper-debuginfo-1.58-23.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"ndiswrapper-debugsource-1.58-23.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"ndiswrapper-kmp-default-1.58_k3.11.10_34-23.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"ndiswrapper-kmp-default-debuginfo-1.58_k3.11.10_34-23.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"ndiswrapper-kmp-desktop-1.58_k3.11.10_34-23.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"ndiswrapper-kmp-desktop-debuginfo-1.58_k3.11.10_34-23.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"ndiswrapper-kmp-pae-1.58_k3.11.10_34-23.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"ndiswrapper-kmp-pae-debuginfo-1.58_k3.11.10_34-23.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"pcfclock-0.44-258.23.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"pcfclock-debuginfo-0.44-258.23.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"pcfclock-debugsource-0.44-258.23.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"pcfclock-kmp-default-0.44_k3.11.10_34-258.23.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"pcfclock-kmp-default-debuginfo-0.44_k3.11.10_34-258.23.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"pcfclock-kmp-desktop-0.44_k3.11.10_34-258.23.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"pcfclock-kmp-desktop-debuginfo-0.44_k3.11.10_34-258.23.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"pcfclock-kmp-pae-0.44_k3.11.10_34-258.23.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"pcfclock-kmp-pae-debuginfo-0.44_k3.11.10_34-258.23.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"python-virtualbox-4.2.36-2.56.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"python-virtualbox-debuginfo-4.2.36-2.56.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"vhba-kmp-debugsource-20130607-2.24.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"vhba-kmp-default-20130607_k3.11.10_34-2.24.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"vhba-kmp-default-debuginfo-20130607_k3.11.10_34-2.24.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"vhba-kmp-desktop-20130607_k3.11.10_34-2.24.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"vhba-kmp-desktop-debuginfo-20130607_k3.11.10_34-2.24.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"vhba-kmp-pae-20130607_k3.11.10_34-2.24.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"vhba-kmp-pae-debuginfo-20130607_k3.11.10_34-2.24.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"vhba-kmp-xen-20130607_k3.11.10_34-2.24.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"vhba-kmp-xen-debuginfo-20130607_k3.11.10_34-2.24.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"virtualbox-4.2.36-2.56.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"virtualbox-debuginfo-4.2.36-2.56.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"virtualbox-debugsource-4.2.36-2.56.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"virtualbox-devel-4.2.36-2.56.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"virtualbox-guest-kmp-default-4.2.36_k3.11.10_34-2.56.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"virtualbox-guest-kmp-default-debuginfo-4.2.36_k3.11.10_34-2.56.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"virtualbox-guest-kmp-desktop-4.2.36_k3.11.10_34-2.56.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"virtualbox-guest-kmp-desktop-debuginfo-4.2.36_k3.11.10_34-2.56.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"virtualbox-guest-kmp-pae-4.2.36_k3.11.10_34-2.56.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"virtualbox-guest-kmp-pae-debuginfo-4.2.36_k3.11.10_34-2.56.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"virtualbox-guest-tools-4.2.36-2.56.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"virtualbox-guest-tools-debuginfo-4.2.36-2.56.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"virtualbox-guest-x11-4.2.36-2.56.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"virtualbox-guest-x11-debuginfo-4.2.36-2.56.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"virtualbox-host-kmp-default-4.2.36_k3.11.10_34-2.56.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"virtualbox-host-kmp-default-debuginfo-4.2.36_k3.11.10_34-2.56.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"virtualbox-host-kmp-desktop-4.2.36_k3.11.10_34-2.56.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"virtualbox-host-kmp-desktop-debuginfo-4.2.36_k3.11.10_34-2.56.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"virtualbox-host-kmp-pae-4.2.36_k3.11.10_34-2.56.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"virtualbox-host-kmp-pae-debuginfo-4.2.36_k3.11.10_34-2.56.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"virtualbox-host-source-4.2.36-2.56.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"virtualbox-qt-4.2.36-2.56.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"virtualbox-qt-debuginfo-4.2.36-2.56.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"virtualbox-websrv-4.2.36-2.56.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"virtualbox-websrv-debuginfo-4.2.36-2.56.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"xen-debugsource-4.3.4_10-57.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"xen-devel-4.3.4_10-57.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"xen-kmp-default-4.3.4_10_k3.11.10_34-57.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"xen-kmp-default-debuginfo-4.3.4_10_k3.11.10_34-57.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"xen-kmp-desktop-4.3.4_10_k3.11.10_34-57.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"xen-kmp-desktop-debuginfo-4.3.4_10_k3.11.10_34-57.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"xen-kmp-pae-4.3.4_10_k3.11.10_34-57.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"xen-kmp-pae-debuginfo-4.3.4_10_k3.11.10_34-57.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"xen-libs-4.3.4_10-57.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"xen-libs-debuginfo-4.3.4_10-57.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"xen-tools-domU-4.3.4_10-57.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"xen-tools-domU-debuginfo-4.3.4_10-57.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"xtables-addons-2.3-2.23.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"xtables-addons-debuginfo-2.3-2.23.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"xtables-addons-debugsource-2.3-2.23.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"xtables-addons-kmp-default-2.3_k3.11.10_34-2.23.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"xtables-addons-kmp-default-debuginfo-2.3_k3.11.10_34-2.23.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"xtables-addons-kmp-desktop-2.3_k3.11.10_34-2.23.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"xtables-addons-kmp-desktop-debuginfo-2.3_k3.11.10_34-2.23.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"xtables-addons-kmp-pae-2.3_k3.11.10_34-2.23.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"xtables-addons-kmp-pae-debuginfo-2.3_k3.11.10_34-2.23.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"xtables-addons-kmp-xen-2.3_k3.11.10_34-2.23.1") ) flag++; if ( rpm_check(release:"SUSE13.1", reference:"xtables-addons-kmp-xen-debuginfo-2.3_k3.11.10_34-2.23.1") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"i686", reference:"kernel-debug-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"i686", reference:"kernel-debug-base-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"i686", reference:"kernel-debug-base-debuginfo-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"i686", reference:"kernel-debug-debuginfo-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"i686", reference:"kernel-debug-debugsource-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"i686", reference:"kernel-debug-devel-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"i686", reference:"kernel-debug-devel-debuginfo-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"i686", reference:"kernel-desktop-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"i686", reference:"kernel-desktop-base-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"i686", reference:"kernel-desktop-base-debuginfo-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"i686", reference:"kernel-desktop-debuginfo-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"i686", reference:"kernel-desktop-debugsource-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"i686", reference:"kernel-desktop-devel-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"i686", reference:"kernel-desktop-devel-debuginfo-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"i686", reference:"kernel-ec2-3.11.10-34.1") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"i686", reference:"kernel-ec2-base-3.11.10-34.1") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"i686", reference:"kernel-ec2-base-debuginfo-3.11.10-34.1") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"i686", reference:"kernel-ec2-debuginfo-3.11.10-34.1") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"i686", reference:"kernel-ec2-debugsource-3.11.10-34.1") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"i686", reference:"kernel-ec2-devel-3.11.10-34.1") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"i686", reference:"kernel-ec2-devel-debuginfo-3.11.10-34.1") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"i686", reference:"kernel-pae-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"i686", reference:"kernel-pae-base-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"i686", reference:"kernel-pae-base-debuginfo-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"i686", reference:"kernel-pae-debuginfo-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"i686", reference:"kernel-pae-debugsource-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"i686", reference:"kernel-pae-devel-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"i686", reference:"kernel-pae-devel-debuginfo-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"i686", reference:"kernel-trace-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"i686", reference:"kernel-trace-base-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"i686", reference:"kernel-trace-base-debuginfo-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"i686", reference:"kernel-trace-debuginfo-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"i686", reference:"kernel-trace-debugsource-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"i686", reference:"kernel-trace-devel-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"i686", reference:"kernel-trace-devel-debuginfo-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"i686", reference:"kernel-vanilla-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"i686", reference:"kernel-vanilla-debuginfo-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"i686", reference:"kernel-vanilla-debugsource-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"i686", reference:"kernel-vanilla-devel-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"i686", reference:"kernel-vanilla-devel-debuginfo-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"i686", reference:"kernel-xen-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"i686", reference:"kernel-xen-base-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"i686", reference:"kernel-xen-base-debuginfo-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"i686", reference:"kernel-xen-debuginfo-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"i686", reference:"kernel-xen-debugsource-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"i686", reference:"kernel-xen-devel-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"i686", reference:"kernel-xen-devel-debuginfo-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"x86_64", reference:"kernel-debug-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"x86_64", reference:"kernel-debug-base-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"x86_64", reference:"kernel-debug-base-debuginfo-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"x86_64", reference:"kernel-debug-debuginfo-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"x86_64", reference:"kernel-debug-debugsource-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"x86_64", reference:"kernel-debug-devel-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"x86_64", reference:"kernel-debug-devel-debuginfo-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"x86_64", reference:"kernel-desktop-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"x86_64", reference:"kernel-desktop-base-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"x86_64", reference:"kernel-desktop-base-debuginfo-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"x86_64", reference:"kernel-desktop-debuginfo-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"x86_64", reference:"kernel-desktop-debugsource-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"x86_64", reference:"kernel-desktop-devel-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"x86_64", reference:"kernel-desktop-devel-debuginfo-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"x86_64", reference:"kernel-ec2-3.11.10-34.1") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"x86_64", reference:"kernel-ec2-base-3.11.10-34.1") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"x86_64", reference:"kernel-ec2-base-debuginfo-3.11.10-34.1") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"x86_64", reference:"kernel-ec2-debuginfo-3.11.10-34.1") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"x86_64", reference:"kernel-ec2-debugsource-3.11.10-34.1") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"x86_64", reference:"kernel-ec2-devel-3.11.10-34.1") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"x86_64", reference:"kernel-ec2-devel-debuginfo-3.11.10-34.1") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"x86_64", reference:"kernel-pae-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"x86_64", reference:"kernel-pae-base-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"x86_64", reference:"kernel-pae-base-debuginfo-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"x86_64", reference:"kernel-pae-debuginfo-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"x86_64", reference:"kernel-pae-debugsource-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"x86_64", reference:"kernel-pae-devel-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"x86_64", reference:"kernel-pae-devel-debuginfo-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"x86_64", reference:"kernel-trace-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"x86_64", reference:"kernel-trace-base-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"x86_64", reference:"kernel-trace-base-debuginfo-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"x86_64", reference:"kernel-trace-debuginfo-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"x86_64", reference:"kernel-trace-debugsource-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"x86_64", reference:"kernel-trace-devel-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"x86_64", reference:"kernel-trace-devel-debuginfo-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"x86_64", reference:"kernel-vanilla-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"x86_64", reference:"kernel-vanilla-debuginfo-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"x86_64", reference:"kernel-vanilla-debugsource-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"x86_64", reference:"kernel-vanilla-devel-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"x86_64", reference:"kernel-vanilla-devel-debuginfo-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"x86_64", reference:"kernel-xen-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"x86_64", reference:"kernel-xen-base-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"x86_64", reference:"kernel-xen-base-debuginfo-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"x86_64", reference:"kernel-xen-debuginfo-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"x86_64", reference:"kernel-xen-debugsource-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"x86_64", reference:"kernel-xen-devel-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"x86_64", reference:"kernel-xen-devel-debuginfo-3.11.10-34.2") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"x86_64", reference:"xen-4.3.4_10-57.1") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"x86_64", reference:"xen-doc-html-4.3.4_10-57.1") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"x86_64", reference:"xen-libs-32bit-4.3.4_10-57.1") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"x86_64", reference:"xen-libs-debuginfo-32bit-4.3.4_10-57.1") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"x86_64", reference:"xen-tools-4.3.4_10-57.1") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"x86_64", reference:"xen-tools-debuginfo-4.3.4_10-57.1") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"x86_64", reference:"xen-xend-tools-4.3.4_10-57.1") ) flag++; if ( rpm_check(release:"SUSE13.1", cpu:"x86_64", reference:"xen-xend-tools-debuginfo-4.3.4_10-57.1") ) flag++; if (flag) { if (report_verbosity > 0) security_hole(port:0, extra:rpm_report_get()); else security_hole(0); exit(0); } else { tested = pkg_tests_get(); if (tested) audit(AUDIT_PACKAGE_NOT_AFFECTED, tested); else audit(AUDIT_PACKAGE_NOT_INSTALLED, "cloop / cloop-debuginfo / cloop-debugsource / cloop-kmp-default / etc"); }NASL family SuSE Local Security Checks NASL id OPENSUSE-2016-136.NASL description The openSUSE 13.2 kernel was updated to receive various security and bugfixes. Following security bugs were fixed : - CVE-2016-0728: A reference leak in keyring handling with join_session_keyring() could lead to local attackers gain root privileges. (bsc#962075). - CVE-2015-7550: A local user could have triggered a race between read and revoke in keyctl (bnc#958951). - CVE-2015-8569: The (1) pptp_bind and (2) pptp_connect functions in drivers/net/ppp/pptp.c in the Linux kernel did not verify an address length, which allowed local users to obtain sensitive information from kernel memory and bypass the KASLR protection mechanism via a crafted application (bnc#959190). - CVE-2015-8543: The networking implementation in the Linux kernel did not validate protocol identifiers for certain protocol families, which allowed local users to cause a denial of service (NULL function pointer dereference and system crash) or possibly gain privileges by leveraging CLONE_NEWUSER support to execute a crafted SOCK_RAW application (bnc#958886). - CVE-2014-8989: The Linux kernel did not properly restrict dropping of supplemental group memberships in certain namespace scenarios, which allowed local users to bypass intended file permissions by leveraging a POSIX ACL containing an entry for the group category that is more restrictive than the entry for the other category, aka a last seen 2020-06-05 modified 2016-02-08 plugin id 88605 published 2016-02-08 reporter This script is Copyright (C) 2016-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/88605 title openSUSE Security Update : the Linux Kernel (openSUSE-2016-136) code #%NASL_MIN_LEVEL 80502 # # (C) Tenable Network Security, Inc. # # The descriptive text and package checks in this plugin were # extracted from openSUSE Security Update openSUSE-2016-136. # # The text description of this plugin is (C) SUSE LLC. # include("compat.inc"); if (description) { script_id(88605); script_version("2.7"); script_set_attribute(attribute:"plugin_modification_date", value:"2020/06/04"); script_cve_id("CVE-2014-8989", "CVE-2014-9529", "CVE-2015-0272", "CVE-2015-5157", "CVE-2015-5307", "CVE-2015-6937", "CVE-2015-7550", "CVE-2015-7799", "CVE-2015-7885", "CVE-2015-7990", "CVE-2015-8104", "CVE-2015-8215", "CVE-2015-8543", "CVE-2015-8550", "CVE-2015-8551", "CVE-2015-8552", "CVE-2015-8569", "CVE-2015-8575", "CVE-2015-8767", "CVE-2016-0728"); script_name(english:"openSUSE Security Update : the Linux Kernel (openSUSE-2016-136)"); script_summary(english:"Check for the openSUSE-2016-136 patch"); script_set_attribute( attribute:"synopsis", value:"The remote openSUSE host is missing a security update." ); script_set_attribute( attribute:"description", value: "The openSUSE 13.2 kernel was updated to receive various security and bugfixes. Following security bugs were fixed : - CVE-2016-0728: A reference leak in keyring handling with join_session_keyring() could lead to local attackers gain root privileges. (bsc#962075). - CVE-2015-7550: A local user could have triggered a race between read and revoke in keyctl (bnc#958951). - CVE-2015-8569: The (1) pptp_bind and (2) pptp_connect functions in drivers/net/ppp/pptp.c in the Linux kernel did not verify an address length, which allowed local users to obtain sensitive information from kernel memory and bypass the KASLR protection mechanism via a crafted application (bnc#959190). - CVE-2015-8543: The networking implementation in the Linux kernel did not validate protocol identifiers for certain protocol families, which allowed local users to cause a denial of service (NULL function pointer dereference and system crash) or possibly gain privileges by leveraging CLONE_NEWUSER support to execute a crafted SOCK_RAW application (bnc#958886). - CVE-2014-8989: The Linux kernel did not properly restrict dropping of supplemental group memberships in certain namespace scenarios, which allowed local users to bypass intended file permissions by leveraging a POSIX ACL containing an entry for the group category that is more restrictive than the entry for the other category, aka a 'negative groups' issue, related to kernel/groups.c, kernel/uid16.c, and kernel/user_namespace.c (bnc#906545). - CVE-2015-5157: arch/x86/entry/entry_64.S in the Linux kernel on the x86_64 platform mishandles IRET faults in processing NMIs that occurred during userspace execution, which might allow local users to gain privileges by triggering an NMI (bnc#937969). - CVE-2015-7799: The slhc_init function in drivers/net/slip/slhc.c in the Linux kernel through 4.2.3 did not ensure that certain slot numbers are valid, which allowed local users to cause a denial of service (NULL pointer dereference and system crash) via a crafted PPPIOCSMAXCID ioctl call (bnc#949936). - CVE-2015-8104: The KVM subsystem in the Linux kernel through 4.2.6, and Xen 4.3.x through 4.6.x, allowed guest OS users to cause a denial of service (host OS panic or hang) by triggering many #DB (aka Debug) exceptions, related to svm.c (bnc#954404). - CVE-2015-5307: The KVM subsystem in the Linux kernel through 4.2.6, and Xen 4.3.x through 4.6.x, allowed guest OS users to cause a denial of service (host OS panic or hang) by triggering many #AC (aka Alignment Check) exceptions, related to svm.c and vmx.c (bnc#953527). - CVE-2014-9529: Race condition in the key_gc_unused_keys function in security/keys/gc.c in the Linux kernel allowed local users to cause a denial of service (memory corruption or panic) or possibly have unspecified other impact via keyctl commands that trigger access to a key structure member during garbage collection of a key (bnc#912202). - CVE-2015-7990: Race condition in the rds_sendmsg function in net/rds/sendmsg.c in the Linux kernel allowed local users to cause a denial of service (NULL pointer dereference and system crash) or possibly have unspecified other impact by using a socket that was not properly bound. NOTE: this vulnerability exists because of an incomplete fix for CVE-2015-6937 (bnc#952384 953052). - CVE-2015-6937: The __rds_conn_create function in net/rds/connection.c in the Linux kernel allowed local users to cause a denial of service (NULL pointer dereference and system crash) or possibly have unspecified other impact by using a socket that was not properly bound (bnc#945825). - CVE-2015-7885: The dgnc_mgmt_ioctl function in drivers/staging/dgnc/dgnc_mgmt.c in the Linux kernel through 4.3.3 did not initialize a certain structure member, which allowed local users to obtain sensitive information from kernel memory via a crafted application (bnc#951627). - CVE-2015-8215: net/ipv6/addrconf.c in the IPv6 stack in the Linux kernel did not validate attempted changes to the MTU value, which allowed context-dependent attackers to cause a denial of service (packet loss) via a value that is (1) smaller than the minimum compliant value or (2) larger than the MTU of an interface, as demonstrated by a Router Advertisement (RA) message that is not validated by a daemon, a different vulnerability than CVE-2015-0272. NOTE: the scope of CVE-2015-0272 is limited to the NetworkManager product (bnc#955354). - CVE-2015-8767: A case can occur when sctp_accept() is called by the user during a heartbeat timeout event after the 4-way handshake. Since sctp_assoc_migrate() changes both assoc->base.sk and assoc->ep, the bh_sock_lock in sctp_generate_heartbeat_event() will be taken with the listening socket but released with the new association socket. The result is a deadlock on any future attempts to take the listening socket lock. (bsc#961509) - CVE-2015-8575: Validate socket address length in sco_sock_bind() to prevent information leak (bsc#959399). - CVE-2015-8551, CVE-2015-8552: xen/pciback: For XEN_PCI_OP_disable_msi[|x] only disable if device has MSI(X) enabled (bsc#957990). - CVE-2015-8550: Compiler optimizations in the XEN PV backend drivers could have lead to double fetch vulnerabilities, causing denial of service or arbitrary code execution (depending on the configuration) (bsc#957988). The following non-security bugs were fixed : - ALSA: hda - Disable 64bit address for Creative HDA controllers (bnc#814440). - ALSA: hda - Fix noise problems on Thinkpad T440s (boo#958504). - Input: aiptek - fix crash on detecting device without endpoints (bnc#956708). - KEYS: Make /proc/keys unconditional if CONFIG_KEYS=y (boo#956934). - KVM: x86: update masterclock values on TSC writes (bsc#961739). - NFS: Fix a NULL pointer dereference of migration recovery ops for v4.2 client (bsc#960839). - apparmor: allow SYS_CAP_RESOURCE to be sufficient to prlimit another task (bsc#921949). - blktap: also call blkif_disconnect() when frontend switched to closed (bsc#952976). - blktap: refine mm tracking (bsc#952976). - cdrom: Random writing support for BD-RE media (bnc#959568). - genksyms: Handle string literals with spaces in reference files (bsc#958510). - ipv4: Do not increase PMTU with Datagram Too Big message (bsc#955224). - ipv6: distinguish frag queues by device for multicast and link-local packets (bsc#955422). - ipv6: fix tunnel error handling (bsc#952579). - route: Use ipv4_mtu instead of raw rt_pmtu (bsc#955224). - uas: Add response iu handling (bnc#954138). - usbvision fix overflow of interfaces array (bnc#950998). - x86/evtchn: make use of PHYSDEVOP_map_pirq. - xen/pciback: Do not allow MSI-X ops if PCI_COMMAND_MEMORY is not set (bsc#957990 XSA-157)." ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=814440" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=906545" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=912202" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=921949" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=937969" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=937970" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=938706" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=944296" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=945825" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=949936" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=950998" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=951627" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=951638" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=952384" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=952579" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=952976" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=953527" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=954138" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=954404" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=955224" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=955354" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=955422" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=956708" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=956934" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=957988" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=957990" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=958504" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=958510" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=958886" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=958951" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=959190" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=959399" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=959568" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=960839" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=961509" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=961739" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=962075" ); script_set_attribute( attribute:"solution", value:"Update the affected the Linux Kernel packages." ); script_set_cvss_base_vector("CVSS2#AV:L/AC:L/Au:N/C:C/I:C/A:C"); script_set_cvss_temporal_vector("CVSS2#E:H/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:L/AC:L/PR:H/UI:N/S:C/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:H/RL:O/RC:C"); script_set_attribute(attribute:"exploitability_ease", value:"Exploits are available"); script_set_attribute(attribute:"exploit_available", value:"true"); script_set_attribute(attribute:"exploit_framework_core", value:"true"); script_set_attribute(attribute:"exploited_by_malware", value:"true"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:bbswitch"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:bbswitch-debugsource"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:bbswitch-kmp-default"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:bbswitch-kmp-default-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:bbswitch-kmp-desktop"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:bbswitch-kmp-desktop-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:bbswitch-kmp-pae"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:bbswitch-kmp-pae-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:bbswitch-kmp-xen"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:bbswitch-kmp-xen-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:cloop"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:cloop-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:cloop-debugsource"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:cloop-kmp-default"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:cloop-kmp-default-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:cloop-kmp-desktop"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:cloop-kmp-desktop-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:cloop-kmp-pae"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:cloop-kmp-pae-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:cloop-kmp-xen"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:cloop-kmp-xen-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:crash"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:crash-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:crash-debugsource"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:crash-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:crash-eppic"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:crash-eppic-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:crash-gcore"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:crash-gcore-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:crash-kmp-default"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:crash-kmp-default-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:crash-kmp-desktop"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:crash-kmp-desktop-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:crash-kmp-pae"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:crash-kmp-pae-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:crash-kmp-xen"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:crash-kmp-xen-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:hdjmod-debugsource"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:hdjmod-kmp-default"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:hdjmod-kmp-default-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:hdjmod-kmp-desktop"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:hdjmod-kmp-desktop-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:hdjmod-kmp-pae"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:hdjmod-kmp-pae-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:hdjmod-kmp-xen"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:hdjmod-kmp-xen-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:ipset"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:ipset-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:ipset-debugsource"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:ipset-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:ipset-kmp-default"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:ipset-kmp-default-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:ipset-kmp-desktop"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:ipset-kmp-desktop-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:ipset-kmp-pae"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:ipset-kmp-pae-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:ipset-kmp-xen"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:ipset-kmp-xen-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-debug"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-debug-base"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-debug-base-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-debug-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-debug-debugsource"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-debug-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-debug-devel-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-default"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-default-base"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-default-base-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-default-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-default-debugsource"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-default-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-desktop"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-desktop-base"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-desktop-base-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-desktop-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-desktop-debugsource"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-desktop-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-ec2"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-ec2-base"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-ec2-base-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-ec2-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-ec2-debugsource"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-ec2-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-macros"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-obs-build"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-obs-build-debugsource"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-obs-qa"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-obs-qa-xen"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-pae"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-pae-base"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-pae-base-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-pae-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-pae-debugsource"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-pae-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-source"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-source-vanilla"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-syms"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-vanilla"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-vanilla-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-vanilla-debugsource"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-vanilla-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-xen"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-xen-base"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-xen-base-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-xen-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-xen-debugsource"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:kernel-xen-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:libipset3"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:libipset3-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:pcfclock"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:pcfclock-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:pcfclock-debugsource"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:pcfclock-kmp-default"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:pcfclock-kmp-default-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:pcfclock-kmp-desktop"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:pcfclock-kmp-desktop-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:pcfclock-kmp-pae"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:pcfclock-kmp-pae-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:python-virtualbox"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:python-virtualbox-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:vhba-kmp-debugsource"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:vhba-kmp-default"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:vhba-kmp-default-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:vhba-kmp-desktop"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:vhba-kmp-desktop-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:vhba-kmp-pae"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:vhba-kmp-pae-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:vhba-kmp-xen"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:vhba-kmp-xen-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:virtualbox"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:virtualbox-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:virtualbox-debugsource"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:virtualbox-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:virtualbox-guest-desktop-icons"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:virtualbox-guest-kmp-default"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:virtualbox-guest-kmp-default-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:virtualbox-guest-kmp-desktop"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:virtualbox-guest-kmp-desktop-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:virtualbox-guest-kmp-pae"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:virtualbox-guest-kmp-pae-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:virtualbox-guest-tools"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:virtualbox-guest-tools-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:virtualbox-guest-x11"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:virtualbox-guest-x11-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:virtualbox-host-kmp-default"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:virtualbox-host-kmp-default-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:virtualbox-host-kmp-desktop"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:virtualbox-host-kmp-desktop-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:virtualbox-host-kmp-pae"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:virtualbox-host-kmp-pae-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:virtualbox-host-source"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:virtualbox-qt"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:virtualbox-qt-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:virtualbox-websrv"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:virtualbox-websrv-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xen"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xen-debugsource"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xen-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xen-doc-html"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xen-kmp-default"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xen-kmp-default-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xen-kmp-desktop"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xen-kmp-desktop-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xen-libs"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xen-libs-32bit"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xen-libs-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xen-libs-debuginfo-32bit"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xen-tools"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xen-tools-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xen-tools-domU"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xen-tools-domU-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xtables-addons"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xtables-addons-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xtables-addons-debugsource"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xtables-addons-kmp-default"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xtables-addons-kmp-default-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xtables-addons-kmp-desktop"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xtables-addons-kmp-desktop-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xtables-addons-kmp-pae"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xtables-addons-kmp-pae-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xtables-addons-kmp-xen"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:xtables-addons-kmp-xen-debuginfo"); script_set_attribute(attribute:"cpe", value:"cpe:/o:novell:opensuse:13.2"); script_set_attribute(attribute:"patch_publication_date", value:"2016/02/03"); script_set_attribute(attribute:"plugin_publication_date", value:"2016/02/08"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_copyright(english:"This script is Copyright (C) 2016-2020 and is owned by Tenable, Inc. or an Affiliate thereof."); script_family(english:"SuSE Local Security Checks"); script_dependencies("ssh_get_info.nasl"); script_require_keys("Host/local_checks_enabled", "Host/SuSE/release", "Host/SuSE/rpm-list", "Host/cpu"); exit(0); } include("audit.inc"); include("global_settings.inc"); include("rpm.inc"); if (!get_kb_item("Host/local_checks_enabled")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); release = get_kb_item("Host/SuSE/release"); if (isnull(release) || release =~ "^(SLED|SLES)") audit(AUDIT_OS_NOT, "openSUSE"); if (release !~ "^(SUSE13\.2)$") audit(AUDIT_OS_RELEASE_NOT, "openSUSE", "13.2", release); if (!get_kb_item("Host/SuSE/rpm-list")) audit(AUDIT_PACKAGE_LIST_MISSING); ourarch = get_kb_item("Host/cpu"); if (!ourarch) audit(AUDIT_UNKNOWN_ARCH); if (ourarch !~ "^(i586|i686|x86_64)$") audit(AUDIT_ARCH_NOT, "i586 / i686 / x86_64", ourarch); flag = 0; if ( rpm_check(release:"SUSE13.2", reference:"bbswitch-0.8-3.15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"bbswitch-debugsource-0.8-3.15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"bbswitch-kmp-default-0.8_k3.16.7_32-3.15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"bbswitch-kmp-default-debuginfo-0.8_k3.16.7_32-3.15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"bbswitch-kmp-desktop-0.8_k3.16.7_32-3.15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"bbswitch-kmp-desktop-debuginfo-0.8_k3.16.7_32-3.15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"bbswitch-kmp-pae-0.8_k3.16.7_32-3.15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"bbswitch-kmp-pae-debuginfo-0.8_k3.16.7_32-3.15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"bbswitch-kmp-xen-0.8_k3.16.7_32-3.15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"bbswitch-kmp-xen-debuginfo-0.8_k3.16.7_32-3.15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"cloop-2.639-14.15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"cloop-debuginfo-2.639-14.15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"cloop-debugsource-2.639-14.15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"cloop-kmp-default-2.639_k3.16.7_32-14.15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"cloop-kmp-default-debuginfo-2.639_k3.16.7_32-14.15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"cloop-kmp-desktop-2.639_k3.16.7_32-14.15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"cloop-kmp-desktop-debuginfo-2.639_k3.16.7_32-14.15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"cloop-kmp-pae-2.639_k3.16.7_32-14.15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"cloop-kmp-pae-debuginfo-2.639_k3.16.7_32-14.15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"cloop-kmp-xen-2.639_k3.16.7_32-14.15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"cloop-kmp-xen-debuginfo-2.639_k3.16.7_32-14.15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"crash-7.0.8-15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"crash-debuginfo-7.0.8-15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"crash-debugsource-7.0.8-15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"crash-devel-7.0.8-15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"crash-eppic-7.0.8-15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"crash-eppic-debuginfo-7.0.8-15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"crash-gcore-7.0.8-15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"crash-gcore-debuginfo-7.0.8-15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"crash-kmp-default-7.0.8_k3.16.7_32-15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"crash-kmp-default-debuginfo-7.0.8_k3.16.7_32-15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"crash-kmp-desktop-7.0.8_k3.16.7_32-15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"crash-kmp-desktop-debuginfo-7.0.8_k3.16.7_32-15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"crash-kmp-pae-7.0.8_k3.16.7_32-15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"crash-kmp-pae-debuginfo-7.0.8_k3.16.7_32-15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"crash-kmp-xen-7.0.8_k3.16.7_32-15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"crash-kmp-xen-debuginfo-7.0.8_k3.16.7_32-15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"hdjmod-debugsource-1.28-18.16.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"hdjmod-kmp-default-1.28_k3.16.7_32-18.16.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"hdjmod-kmp-default-debuginfo-1.28_k3.16.7_32-18.16.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"hdjmod-kmp-desktop-1.28_k3.16.7_32-18.16.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"hdjmod-kmp-desktop-debuginfo-1.28_k3.16.7_32-18.16.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"hdjmod-kmp-pae-1.28_k3.16.7_32-18.16.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"hdjmod-kmp-pae-debuginfo-1.28_k3.16.7_32-18.16.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"hdjmod-kmp-xen-1.28_k3.16.7_32-18.16.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"hdjmod-kmp-xen-debuginfo-1.28_k3.16.7_32-18.16.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"ipset-6.23-15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"ipset-debuginfo-6.23-15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"ipset-debugsource-6.23-15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"ipset-devel-6.23-15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"ipset-kmp-default-6.23_k3.16.7_32-15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"ipset-kmp-default-debuginfo-6.23_k3.16.7_32-15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"ipset-kmp-desktop-6.23_k3.16.7_32-15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"ipset-kmp-desktop-debuginfo-6.23_k3.16.7_32-15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"ipset-kmp-pae-6.23_k3.16.7_32-15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"ipset-kmp-pae-debuginfo-6.23_k3.16.7_32-15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"ipset-kmp-xen-6.23_k3.16.7_32-15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"ipset-kmp-xen-debuginfo-6.23_k3.16.7_32-15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"kernel-default-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"kernel-default-base-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"kernel-default-base-debuginfo-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"kernel-default-debuginfo-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"kernel-default-debugsource-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"kernel-default-devel-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"kernel-devel-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"kernel-ec2-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"kernel-ec2-base-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"kernel-ec2-devel-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"kernel-macros-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"kernel-obs-build-3.16.7-32.2") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"kernel-obs-build-debugsource-3.16.7-32.2") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"kernel-obs-qa-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"kernel-obs-qa-xen-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"kernel-source-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"kernel-source-vanilla-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"kernel-syms-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"libipset3-6.23-15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"libipset3-debuginfo-6.23-15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"pcfclock-0.44-260.15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"pcfclock-debuginfo-0.44-260.15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"pcfclock-debugsource-0.44-260.15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"pcfclock-kmp-default-0.44_k3.16.7_32-260.15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"pcfclock-kmp-default-debuginfo-0.44_k3.16.7_32-260.15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"pcfclock-kmp-desktop-0.44_k3.16.7_32-260.15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"pcfclock-kmp-desktop-debuginfo-0.44_k3.16.7_32-260.15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"pcfclock-kmp-pae-0.44_k3.16.7_32-260.15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"pcfclock-kmp-pae-debuginfo-0.44_k3.16.7_32-260.15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"python-virtualbox-4.3.34-37.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"python-virtualbox-debuginfo-4.3.34-37.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"vhba-kmp-debugsource-20140629-2.15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"vhba-kmp-default-20140629_k3.16.7_32-2.15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"vhba-kmp-default-debuginfo-20140629_k3.16.7_32-2.15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"vhba-kmp-desktop-20140629_k3.16.7_32-2.15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"vhba-kmp-desktop-debuginfo-20140629_k3.16.7_32-2.15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"vhba-kmp-pae-20140629_k3.16.7_32-2.15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"vhba-kmp-pae-debuginfo-20140629_k3.16.7_32-2.15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"vhba-kmp-xen-20140629_k3.16.7_32-2.15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"vhba-kmp-xen-debuginfo-20140629_k3.16.7_32-2.15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"virtualbox-4.3.34-37.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"virtualbox-debuginfo-4.3.34-37.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"virtualbox-debugsource-4.3.34-37.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"virtualbox-devel-4.3.34-37.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"virtualbox-guest-desktop-icons-4.3.34-37.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"virtualbox-guest-kmp-default-4.3.34_k3.16.7_32-37.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"virtualbox-guest-kmp-default-debuginfo-4.3.34_k3.16.7_32-37.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"virtualbox-guest-kmp-desktop-4.3.34_k3.16.7_32-37.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"virtualbox-guest-kmp-desktop-debuginfo-4.3.34_k3.16.7_32-37.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"virtualbox-guest-kmp-pae-4.3.34_k3.16.7_32-37.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"virtualbox-guest-kmp-pae-debuginfo-4.3.34_k3.16.7_32-37.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"virtualbox-guest-tools-4.3.34-37.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"virtualbox-guest-tools-debuginfo-4.3.34-37.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"virtualbox-guest-x11-4.3.34-37.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"virtualbox-guest-x11-debuginfo-4.3.34-37.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"virtualbox-host-kmp-default-4.3.34_k3.16.7_32-37.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"virtualbox-host-kmp-default-debuginfo-4.3.34_k3.16.7_32-37.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"virtualbox-host-kmp-desktop-4.3.34_k3.16.7_32-37.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"virtualbox-host-kmp-desktop-debuginfo-4.3.34_k3.16.7_32-37.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"virtualbox-host-kmp-pae-4.3.34_k3.16.7_32-37.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"virtualbox-host-kmp-pae-debuginfo-4.3.34_k3.16.7_32-37.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"virtualbox-host-source-4.3.34-37.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"virtualbox-qt-4.3.34-37.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"virtualbox-qt-debuginfo-4.3.34-37.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"virtualbox-websrv-4.3.34-37.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"virtualbox-websrv-debuginfo-4.3.34-37.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"xen-debugsource-4.4.3_08-38.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"xen-devel-4.4.3_08-38.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"xen-libs-4.4.3_08-38.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"xen-libs-debuginfo-4.4.3_08-38.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"xen-tools-domU-4.4.3_08-38.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"xen-tools-domU-debuginfo-4.4.3_08-38.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"xtables-addons-2.6-15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"xtables-addons-debuginfo-2.6-15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"xtables-addons-debugsource-2.6-15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"xtables-addons-kmp-default-2.6_k3.16.7_32-15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"xtables-addons-kmp-default-debuginfo-2.6_k3.16.7_32-15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"xtables-addons-kmp-desktop-2.6_k3.16.7_32-15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"xtables-addons-kmp-desktop-debuginfo-2.6_k3.16.7_32-15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"xtables-addons-kmp-pae-2.6_k3.16.7_32-15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"xtables-addons-kmp-pae-debuginfo-2.6_k3.16.7_32-15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"xtables-addons-kmp-xen-2.6_k3.16.7_32-15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"xtables-addons-kmp-xen-debuginfo-2.6_k3.16.7_32-15.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"i686", reference:"kernel-debug-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"i686", reference:"kernel-debug-base-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"i686", reference:"kernel-debug-base-debuginfo-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"i686", reference:"kernel-debug-debuginfo-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"i686", reference:"kernel-debug-debugsource-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"i686", reference:"kernel-debug-devel-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"i686", reference:"kernel-debug-devel-debuginfo-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"i686", reference:"kernel-desktop-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"i686", reference:"kernel-desktop-base-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"i686", reference:"kernel-desktop-base-debuginfo-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"i686", reference:"kernel-desktop-debuginfo-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"i686", reference:"kernel-desktop-debugsource-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"i686", reference:"kernel-desktop-devel-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"i686", reference:"kernel-ec2-base-debuginfo-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"i686", reference:"kernel-ec2-debuginfo-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"i686", reference:"kernel-ec2-debugsource-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"i686", reference:"kernel-pae-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"i686", reference:"kernel-pae-base-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"i686", reference:"kernel-pae-base-debuginfo-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"i686", reference:"kernel-pae-debuginfo-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"i686", reference:"kernel-pae-debugsource-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"i686", reference:"kernel-pae-devel-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"i686", reference:"kernel-vanilla-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"i686", reference:"kernel-vanilla-debuginfo-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"i686", reference:"kernel-vanilla-debugsource-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"i686", reference:"kernel-vanilla-devel-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"i686", reference:"kernel-xen-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"i686", reference:"kernel-xen-base-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"i686", reference:"kernel-xen-base-debuginfo-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"i686", reference:"kernel-xen-debuginfo-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"i686", reference:"kernel-xen-debugsource-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"i686", reference:"kernel-xen-devel-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"x86_64", reference:"kernel-debug-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"x86_64", reference:"kernel-debug-base-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"x86_64", reference:"kernel-debug-base-debuginfo-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"x86_64", reference:"kernel-debug-debuginfo-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"x86_64", reference:"kernel-debug-debugsource-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"x86_64", reference:"kernel-debug-devel-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"x86_64", reference:"kernel-debug-devel-debuginfo-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"x86_64", reference:"kernel-desktop-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"x86_64", reference:"kernel-desktop-base-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"x86_64", reference:"kernel-desktop-base-debuginfo-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"x86_64", reference:"kernel-desktop-debuginfo-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"x86_64", reference:"kernel-desktop-debugsource-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"x86_64", reference:"kernel-desktop-devel-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"x86_64", reference:"kernel-ec2-base-debuginfo-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"x86_64", reference:"kernel-ec2-debuginfo-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"x86_64", reference:"kernel-ec2-debugsource-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"x86_64", reference:"kernel-pae-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"x86_64", reference:"kernel-pae-base-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"x86_64", reference:"kernel-pae-base-debuginfo-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"x86_64", reference:"kernel-pae-debuginfo-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"x86_64", reference:"kernel-pae-debugsource-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"x86_64", reference:"kernel-pae-devel-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"x86_64", reference:"kernel-vanilla-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"x86_64", reference:"kernel-vanilla-debuginfo-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"x86_64", reference:"kernel-vanilla-debugsource-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"x86_64", reference:"kernel-vanilla-devel-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"x86_64", reference:"kernel-xen-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"x86_64", reference:"kernel-xen-base-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"x86_64", reference:"kernel-xen-base-debuginfo-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"x86_64", reference:"kernel-xen-debuginfo-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"x86_64", reference:"kernel-xen-debugsource-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"x86_64", reference:"kernel-xen-devel-3.16.7-32.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"x86_64", reference:"xen-4.4.3_08-38.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"x86_64", reference:"xen-doc-html-4.4.3_08-38.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"x86_64", reference:"xen-kmp-default-4.4.3_08_k3.16.7_32-38.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"x86_64", reference:"xen-kmp-default-debuginfo-4.4.3_08_k3.16.7_32-38.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"x86_64", reference:"xen-kmp-desktop-4.4.3_08_k3.16.7_32-38.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"x86_64", reference:"xen-kmp-desktop-debuginfo-4.4.3_08_k3.16.7_32-38.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"x86_64", reference:"xen-libs-32bit-4.4.3_08-38.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"x86_64", reference:"xen-libs-debuginfo-32bit-4.4.3_08-38.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"x86_64", reference:"xen-tools-4.4.3_08-38.1") ) flag++; if ( rpm_check(release:"SUSE13.2", cpu:"x86_64", reference:"xen-tools-debuginfo-4.4.3_08-38.1") ) flag++; if (flag) { if (report_verbosity > 0) security_hole(port:0, extra:rpm_report_get()); else security_hole(0); exit(0); } else { tested = pkg_tests_get(); if (tested) audit(AUDIT_PACKAGE_NOT_AFFECTED, tested); else audit(AUDIT_PACKAGE_NOT_INSTALLED, "bbswitch / bbswitch-debugsource / bbswitch-kmp-default / etc"); }NASL family Ubuntu Local Security Checks NASL id UBUNTU_USN-2872-2.NASL description Yevgeny Pats discovered that the session keyring implementation in the Linux kernel did not properly reference count when joining an existing session keyring. A local attacker could use this to cause a denial of service (system crash) or possibly execute arbitrary code with administrative privileges. Note that Tenable Network Security has extracted the preceding description block directly from the Ubuntu security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 88015 published 2016-01-20 reporter Ubuntu Security Notice (C) 2016-2019 Canonical, Inc. / NASL script (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/88015 title Ubuntu 14.04 LTS : linux-lts-wily vulnerability (USN-2872-2) NASL family Fedora Local Security Checks NASL id FEDORA_2016-5D43766E33.NASL description Update to latest upstream stable release, Linux v4.3.4. Elan touchpad fixes. ---- Update to 4.3.y stable series. Fixes across the tree. Note that Tenable Network Security has extracted the preceding description block directly from the Fedora security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-05 modified 2016-03-04 plugin id 89554 published 2016-03-04 reporter This script is Copyright (C) 2016-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/89554 title Fedora 22 : kernel-4.3.4-200.fc22 (2016-5d43766e33) NASL family Ubuntu Local Security Checks NASL id UBUNTU_USN-2873-1.NASL description Yevgeny Pats discovered that the session keyring implementation in the Linux kernel did not properly reference count when joining an existing session keyring. A local attacker could use this to cause a denial of service (system crash) or possibly execute arbitrary code with administrative privileges. Note that Tenable Network Security has extracted the preceding description block directly from the Ubuntu security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 88017 published 2016-01-20 reporter Ubuntu Security Notice (C) 2016-2019 Canonical, Inc. / NASL script (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/88017 title Ubuntu 14.04 LTS : linux-lts-utopic vulnerability (USN-2873-1) NASL family OracleVM Local Security Checks NASL id ORACLEVM_OVMSA-2017-0057.NASL description The remote OracleVM system is missing necessary patches to address critical security updates : please see Oracle VM Security Advisory OVMSA-2017-0057 for details. last seen 2020-06-01 modified 2020-06-02 plugin id 99163 published 2017-04-03 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/99163 title OracleVM 3.3 : Unbreakable / etc (OVMSA-2017-0057) (Dirty COW) NASL family Ubuntu Local Security Checks NASL id UBUNTU_USN-2870-1.NASL description Yevgeny Pats discovered that the session keyring implementation in the Linux kernel did not properly reference count when joining an existing session keyring. A local attacker could use this to cause a denial of service (system crash) or possibly execute arbitrary code with administrative privileges. Note that Tenable Network Security has extracted the preceding description block directly from the Ubuntu security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 88010 published 2016-01-20 reporter Ubuntu Security Notice (C) 2016-2019 Canonical, Inc. / NASL script (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/88010 title Ubuntu 14.04 LTS : linux vulnerability (USN-2870-1) NASL family Red Hat Local Security Checks NASL id REDHAT-RHSA-2016-0065.NASL description Updated kernel-rt packages that fix one security issue are now available for Red Hat Enterprise Linux 7. Red Hat Product Security has rated this update as having Important security impact. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available from the CVE link in the References section. The kernel packages contain the Linux kernel, the core of any Linux operating system. * A use-after-free flaw was found in the way the Linux kernel last seen 2020-06-01 modified 2020-06-02 plugin id 88574 published 2016-02-04 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/88574 title RHEL 7 : kernel-rt (RHSA-2016:0065) NASL family Huawei Local Security Checks NASL id EULEROS_SA-2019-1527.NASL description According to the versions of the kernel packages installed, the EulerOS Virtualization for ARM 64 installation on the remote host is affected by the following vulnerabilities : - The Linux kernel, before version 4.14.3, is vulnerable to a denial of service in drivers/md/dm.c:dm_get_from_kobject() which can be caused by local users leveraging a race condition with __dm_destroy() during creation and removal of DM devices. Only privileged local users (with CAP_SYS_ADMIN capability) can directly perform the ioctl operations for dm device creation and removal and this would typically be outside the direct control of the unprivileged attacker.(CVE-2017-18203i1/4%0 - The batadv_frag_merge_packets function in net/batman-adv/fragmentation.c in the B.A.T.M.A.N. implementation in the Linux kernel through 3.18.1 uses an incorrect length field during a calculation of an amount of memory, which allows remote attackers to cause a denial of service (mesh-node system crash) via fragmented packets.(CVE-2014-9428i1/4%0 - The regulator_ena_gpio_free function in drivers/regulator/core.c in the Linux kernel allows local users to gain privileges or cause a denial of service (use-after-free) via a crafted application.(CVE-2014-9940i1/4%0 - The Linux kernel before 3.12, when UDP Fragmentation Offload (UFO) is enabled, does not properly initialize certain data structures, which allows local users to cause a denial of service (memory corruption and system crash) or possibly gain privileges via a crafted application that uses the UDP_CORK option in a setsockopt system call and sends both short and long packets, related to the ip_ufo_append_data function in net/ipv4/ip_output.c and the ip6_ufo_append_data function in net/ipv6/ip6_output.c.(CVE-2013-4470i1/4%0 - A use-after-free flaw was found in the way the Linux kernel last seen 2020-03-19 modified 2019-05-14 plugin id 124980 published 2019-05-14 reporter This script is Copyright (C) 2019-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/124980 title EulerOS Virtualization for ARM 64 3.0.1.0 : kernel (EulerOS-SA-2019-1527) NASL family Ubuntu Local Security Checks NASL id UBUNTU_USN-2872-1.NASL description Yevgeny Pats discovered that the session keyring implementation in the Linux kernel did not properly reference count when joining an existing session keyring. A local attacker could use this to cause a denial of service (system crash) or possibly execute arbitrary code with administrative privileges. Note that Tenable Network Security has extracted the preceding description block directly from the Ubuntu security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 88014 published 2016-01-20 reporter Ubuntu Security Notice (C) 2016-2019 Canonical, Inc. / NASL script (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/88014 title Ubuntu 15.10 : linux vulnerability (USN-2872-1) NASL family Ubuntu Local Security Checks NASL id UBUNTU_USN-2871-1.NASL description Yevgeny Pats discovered that the session keyring implementation in the Linux kernel did not properly reference count when joining an existing session keyring. A local attacker could use this to cause a denial of service (system crash) or possibly execute arbitrary code with administrative privileges. Note that Tenable Network Security has extracted the preceding description block directly from the Ubuntu security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 88012 published 2016-01-20 reporter Ubuntu Security Notice (C) 2016-2019 Canonical, Inc. / NASL script (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/88012 title Ubuntu 15.04 : linux vulnerability (USN-2871-1) NASL family Oracle Linux Local Security Checks NASL id ORACLELINUX_ELSA-2016-3509.NASL description Description of changes: kernel-uek [3.8.13-118.2.5.el7uek] - KEYS: Fix keyring ref leak in join_session_keyring() (Yevgeny Pats) [Orabug: 22563965] {CVE-2016-0728} last seen 2020-06-01 modified 2020-06-02 plugin id 88032 published 2016-01-21 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/88032 title Oracle Linux 6 / 7 : Unbreakable Enterprise kernel (ELSA-2016-3509) NASL family Amazon Linux Local Security Checks NASL id ALA_ALAS-2016-642.NASL description Perception Point Research identified a use-after-free vulnerability, representing a local privilege escalation vulnerability in the Linux kernel. Their post contains a detailed analysis of the bug. kernel-4.1.13-19.30.amzn1 and earlier versions are impacted. last seen 2020-06-01 modified 2020-06-02 plugin id 87991 published 2016-01-20 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/87991 title Amazon Linux AMI : kernel (ALAS-2016-642) NASL family SuSE Local Security Checks NASL id SUSE_SU-2016-0186-1.NASL description The SUSE Linux Enterprise 12 SP1 kernel was updated to receive a security fix. Following security bug was fixed : - A reference leak in keyring handling with join_session_keyring() could lead to local attackers gain root privileges. (bsc#962075, CVE-2016-0728). Note that Tenable Network Security has extracted the preceding description block directly from the SUSE security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 88140 published 2016-01-25 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/88140 title SUSE SLED12 / SLES12 Security Update : kernel (SUSE-SU-2016:0186-1) NASL family Ubuntu Local Security Checks NASL id UBUNTU_USN-2872-3.NASL description Yevgeny Pats discovered that the session keyring implementation in the Linux kernel did not properly reference count when joining an existing session keyring. A local attacker could use this to cause a denial of service (system crash) or possibly execute arbitrary code with administrative privileges. Note that Tenable Network Security has extracted the preceding description block directly from the Ubuntu security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 88016 published 2016-01-20 reporter Ubuntu Security Notice (C) 2016-2019 Canonical, Inc. / NASL script (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/88016 title Ubuntu 15.10 : linux-raspi2 vulnerability (USN-2872-3) NASL family Red Hat Local Security Checks NASL id REDHAT-RHSA-2016-0068.NASL description Updated kernel-rt packages that fix one security issue are now available for Red Hat Enterprise MRG 2. Red Hat Product Security has rated this update as having Important security impact. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available from the CVE link in the References section. The kernel packages contain the Linux kernel, the core of any Linux operating system. * A use-after-free flaw was found in the way the Linux kernel last seen 2020-06-01 modified 2020-06-02 plugin id 88405 published 2016-01-27 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/88405 title RHEL 6 : MRG (RHSA-2016:0068) NASL family Oracle Linux Local Security Checks NASL id ORACLELINUX_ELSA-2016-0064.NASL description From Red Hat Security Advisory 2016:0064 : Updated kernel packages that fix one security issue are now available for Red Hat Enterprise Linux 7. Red Hat Product Security has rated this update as having Important security impact. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available from the CVE link in the References section. The kernel packages contain the Linux kernel, the core of any Linux operating system. * A use-after-free flaw was found in the way the Linux kernel last seen 2020-06-01 modified 2020-06-02 plugin id 88168 published 2016-01-26 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/88168 title Oracle Linux 7 : kernel (ELSA-2016-0064) NASL family Oracle Linux Local Security Checks NASL id ORACLELINUX_ELSA-2016-3510.NASL description Description of changes: kernel-uek [4.1.12-32.1.2.el7uek] - KEYS: Fix keyring ref leak in join_session_keyring() (Yevgeny Pats) [Orabug: 22563965] {CVE-2016-0728} [4.1.12-32.1.1.el7uek] - ocfs2: return non-zero st_blocks for inline data (John Haxby) [Orabug: 22218243] - xen/events/fifo: Consume unprocessed events when a CPU dies (Ross Lagerwall) [Orabug: 22498877] - Revert last seen 2020-06-01 modified 2020-06-02 plugin id 88033 published 2016-01-21 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/88033 title Oracle Linux 6 / 7 : Unbreakable Enterprise kernel (ELSA-2016-3510)
Packetstorm
| data source | https://packetstormsecurity.com/files/download/135330/linuxrefcount-uaf.txt |
| id | PACKETSTORM:135330 |
| last seen | 2016-12-05 |
| published | 2016-01-20 |
| reporter | Perception Point Team |
| source | https://packetstormsecurity.com/files/135330/Linux-Kernel-REFCOUNT-Overflow-Use-After-Free.html |
| title | Linux Kernel REFCOUNT Overflow / Use-After-Free |
Redhat
| advisories |
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| rpms |
|
Seebug
bulletinFamily exploit description ### 漏洞分析 Linux Kernel的这个漏洞会造成两个影响,第一个是造成信息泄露,可以bypass ASLR,另一个是UAF造成代码执行,利用的是KeyRing机制中的两个漏洞,一个是对Keyring操作控制不严谨,另一个是利用对Keyring计数变量控制不严谨,其中代码执行利用条件相对苛刻,下面对此漏洞进行详细分析。 Keyring信息泄露: Keyring和安全密钥有关,进程可以申请自己新的keyring,同时也可以通过申请新的keyring替换老的keyring,其中,调用到join_session_keyring函数。 ``` long join_session_keyring(const char *name) { ... new = prepare_creds(); ... keyring = find_keyring_by_name(name, false); //find_keyring_by_name increments keyring->usage if a keyring was found if (PTR_ERR(keyring) == -ENOKEY) { /* not found - try and create a new one */ keyring = keyring_alloc( name, old->uid, old->gid, old, KEY_POS_ALL | KEY_USR_VIEW | KEY_USR_READ | KEY_USR_LINK, KEY_ALLOC_IN_QUOTA, NULL); if (IS_ERR(keyring)) { ret = PTR_ERR(keyring); goto error2; } ``` 这里会通过find_keyring_by_name,去查看当前请求进程是否已经存在keyring,如果不存在,则会创建一个新的keyring,而当存在时,则会执行下面的函数逻辑。 ``` ret = install_session_keyring_to_cred(new, keyring); if (ret < 0) goto error2; commit_creds(new); mutex_unlock(&key_session_mutex); ret = keyring->serial; key_put(keyring); ``` 会利用新的keyring替换老的keyring,这里都没有问题,但是有另一个函数逻辑是存在问题的地方。 ``` else if (keyring == new->session_keyring) { ret = 0; goto error2; //<-- The bug is here, skips key_put. } ``` 当新申请的keyring和老得keyring相等的时候,则会跳转到error2执行,而在error2里。 ``` error2: mutex_unlock(&key_session_mutex); ``` 会调用mutex_unlock泄露keryring的引用信息,造成信息泄露。 释放后重用漏洞: 这个漏洞发生于keyring的计数中,这个计数存放于一个usage数据域中,当每次申请一次keyring,数据域计数就会加1,这个数据域是atomic_t类型,也就是说存在上限。 而在整个过程中,没有对这个数据域计数的大小进行判断,从而导致不断申请keyring直至超过数据域大小的时候,usage会置0,这个过程会释放keyring,而这个过程会产生一个悬垂指针,在申请keyring的时候,通过精心构造这个过程,可以覆盖这个悬垂指针。 覆盖内容使用内核代码,当再次引用的时候,可以引发代码执行。 id SSV:91603 last seen 2017-11-19 modified 2016-05-20 published 2016-05-20 reporter toT0C source https://www.seebug.org/vuldb/ssvid-91603 title Linux内核 Keyrings 引用计数溢出 UAF 漏洞 bulletinFamily exploit description ## Introduction The Perception Point Research team has identified a 0-day local privilege escalation vulnerability in the Linux kernel. While the vulnerability has existed since 2012, our team discovered the vulnerability only recently, disclosed the details to the Kernel security team, and later developed a proof-of-concept exploit. As of the date of disclosure, this vulnerability has implications for approximately tens of millions of Linux PCs and servers, and 66 percent of all Android devices (phones/tablets). While neither us nor the Kernel security team have observed any exploit targeting this vulnerability in the wild, we recommend that security teams examine potentially affected devices and implement patches as soon as possible. In this write-up, we’ll discuss the technical details of the vulnerability as well as the techniques used to achieve kernel code execution using the vulnerability. Ultimately, the PoC provided successfully escalates privileges from a local user to root. ## The Bug CVE-2016-0728 is caused by a reference leak in the keyrings facility. Before we dive into the details, let’s cover some background required to understand the bug. Quoting directly from its manpage, the keyrings facility is primarily a way for drivers to retain or cache security data, authentication keys, encryption keys and other data in the kernel. System call interfaces – keyctl syscall (there are two other syscalls that are used for handling keys: add_key and request_key. keyctl, however, is definitely the most important one for this write-up.) are provided so that userspace programs can manage those objects and use the facility for their own purposes. Each process can create a keyring for the current session using keyctl(KEYCTL_JOIN_SESSION_KEYRING, name) and can choose to either assign a name to the keyring or not by passing NULL. The keyring object can be shared between processes by referencing the same keyring name. If a process already has a session keyring, this same system call will replace its keyring with a new one. If an object is shared between processes, the object’s internal refcount, stored in a field called usage, is incremented. The leak occurs when a process tries to replace its current session keyring with the very same one. As we see in the next code snippet, taken from kernel version 3.18, the execution jumps to error2 label which skips the call to key_put and leaks the reference that was increased by find_keyring_by_name. Triggering the bug from userspace is fairly straightforward, as we can see in the following code snippet: which results the following output having leaked-keyring 100 references: 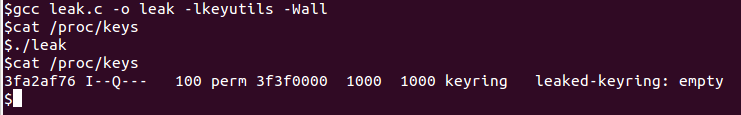 ## Exploiting the Bug Even though the bug itself can directly cause a memory leak, it has far more serious consequences. After a quick examination of the relevant code flow, we found that the usage field used to store the reference count for the object is of type atomic_t, which under the hood, is basically an int – meaning 32-bit on both 32-bit and 64-bit architectures. While every integer is theoretically possible to overflow, this particular observation makes practical exploitation of this bug as a way to overflow the reference count seem feasible. And it turns out no checks are performed to prevent overflowing the usage field from wrapping around to 0. If a process causes the kernel to leak 0x100000000 references to the same object, it can later cause the kernel to think the object is no longer referenced and consequently free the object. If the same process holds another legitimate reference and uses it after the kernel freed the object, it will cause the kernel to reference deallocated, or a reallocated memory. This way, we can achieve a use-after-free, by using the exact same bug from before. A lot has been written on use-after-free vulnerability exploitation in the kernel, so the following steps wouldn’t surprise an experienced vulnerability researcher. The outline of the steps that to be executed by the exploit code is as follows: 1.Hold a (legitimate) reference to a key object 2.Overflow the same object’s usage 3.Get the keyring object freed 4.Allocate a different kernel object from user-space, with a user-controlled content, over the same memory previously used by the freed keyring object 5.Use the reference to the old key object and trigger code execution Step 1 is completely out of the manpage, step 2 was explained earlier. Let’s dive into the technical details of the rest of the steps. ## Overflowing usage Refcount This step is actually an extension of the bug. The usage field is of int type which means it has a max value of 2^32 both on 32-bit and 64-bit architectures. To overflow the usage field we have to loop the snippet above 2^32 times to get usage to zero. ## Freeing keyring object There are a couple of ways to get the keyring object freed while holding a reference to it. One possible way is using one process to overflow the keyring usage field to 0 and getting the object freed by the Garbage Collection algorithm inside the keyring subsystem which frees any keyring object the moment the usage counter is 0. One caveat though, if we look at the join_session_keyring function prepare_creds also increments the current session keyring and abort_creds or commit_creds decrements it respectively. The problem is that abort_creds doesn’t decrement the keyring’s usage field synchronically but it is called later using rcu job, which means we can overflow the usage counter without knowing it was overflowed. It is possible to solve this issue by using sleep(1) after each call to join_session_keyring, of course it is not feasible to sleep(2^32) seconds. A feasible work around will be to use a variation of the divide-and-conquer algorithm and to sleep after 2^31-1 calls, then after 2^30-1 etc… this way we never overflow unintentionally because the maximum value of refcount can be double the value it should be if no jobs where called. ## Allocating and controlling kernel object Having our process point to a freed keyring object, now we need to allocate a kernel object that will override the freed keyring object. That will be easy thanks to how SLAB memory works, allocating many objects of the keyring size just after the object is freed. We choose to use the Linux IPC subsystem to send messages of size 0xb8 – 0x30 when 0xb8 is the size of the keyring object and 0x30 is the size of a message header. This way we control the lower 0x88 bytes of the keyring object. ## Gaining kernel code execution From here it’s pretty easy thanks to the struct key_type inside the keyring object which contains many function pointers. An interesting function pointer is the revoke function pointer which can be invoked using the keyctl(KEY_REVOKE, key_name) syscall. The following is the Linux kernel snippet calling the revoke function: The keyring object should be filled as follows: 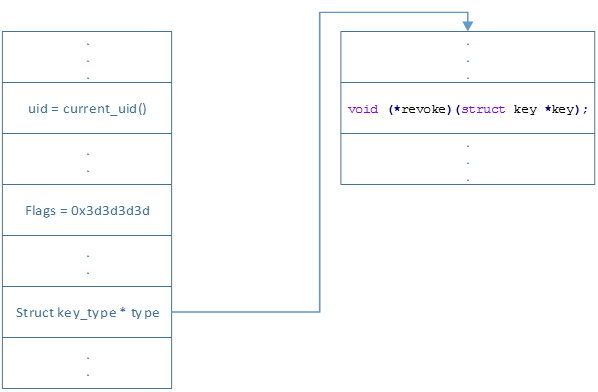 The uid and flags attributes should be filled that way to pass a few control check until the execution gets to key->type->revoke. The type field should point to a user-space struct containing the function pointers with revoke pointing to a function that will be executed with root privileges. Here is a code snippet that demonstrates this. Addresses of commit_creds and prepare_kernel_cred functions are static and can be determined per Linux kernel version/android device. Now the last step is of course: here is a link to the full exploit which runs on kernel 3.18 64-bit, following is the output of running the full exploit which takes about 30 minutes to run on Intel Core i7-5500 CPU (Usually time is not an issue in a privilege escalation exploit): 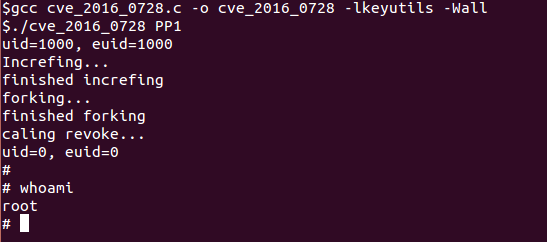 ## Mitigations & Conclusions The vulnerability affects any Linux Kernel version 3.8 and higher. SMEP & SMAP will make it difficult to exploit as well as SELinux on android devices. Maybe we’ll talk about tricks to bypass those mitigation in upcoming blogs, anyway the most important thing for now is to patch it as soon as you can. id SSV:90673 last seen 2017-11-19 modified 2016-01-28 published 2016-01-28 reporter Root title ACTi E31 surveillance Cameras 弱密码漏洞
The Hacker News
| id | THN:2F321B0D3CF635D0F8D272948E9B31C9 |
| last seen | 2018-01-27 |
| modified | 2016-01-22 |
| published | 2016-01-19 |
| reporter | Mohit Kumar |
| source | https://thehackernews.com/2016/01/linux-kernel-hacker.html |
| title | Zero-Day Flaw Found in 'Linux Kernel' leaves Millions Vulnerable |
Related news
References
- http://git.kernel.org/cgit/linux/kernel/git/torvalds/linux.git/commit/?id=23567fd052a9abb6d67fe8e7a9ccdd9800a540f2
- http://git.kernel.org/cgit/linux/kernel/git/torvalds/linux.git/commit/?id=23567fd052a9abb6d67fe8e7a9ccdd9800a540f2
- http://lists.fedoraproject.org/pipermail/package-announce/2016-February/176484.html
- http://lists.fedoraproject.org/pipermail/package-announce/2016-February/176484.html
- http://lists.fedoraproject.org/pipermail/package-announce/2016-January/176194.html
- http://lists.fedoraproject.org/pipermail/package-announce/2016-January/176194.html
- http://lists.opensuse.org/opensuse-security-announce/2016-01/msg00026.html
- http://lists.opensuse.org/opensuse-security-announce/2016-01/msg00026.html
- http://lists.opensuse.org/opensuse-security-announce/2016-02/msg00012.html
- http://lists.opensuse.org/opensuse-security-announce/2016-02/msg00012.html
- http://lists.opensuse.org/opensuse-security-announce/2016-03/msg00033.html
- http://lists.opensuse.org/opensuse-security-announce/2016-03/msg00033.html
- http://lists.opensuse.org/opensuse-security-announce/2016-03/msg00034.html
- http://lists.opensuse.org/opensuse-security-announce/2016-03/msg00034.html
- http://lists.opensuse.org/opensuse-security-announce/2016-03/msg00035.html
- http://lists.opensuse.org/opensuse-security-announce/2016-03/msg00035.html
- http://lists.opensuse.org/opensuse-security-announce/2016-03/msg00038.html
- http://lists.opensuse.org/opensuse-security-announce/2016-03/msg00038.html
- http://lists.opensuse.org/opensuse-security-announce/2016-03/msg00039.html
- http://lists.opensuse.org/opensuse-security-announce/2016-03/msg00039.html
- http://lists.opensuse.org/opensuse-security-announce/2016-03/msg00040.html
- http://lists.opensuse.org/opensuse-security-announce/2016-03/msg00040.html
- http://lists.opensuse.org/opensuse-security-announce/2016-03/msg00041.html
- http://lists.opensuse.org/opensuse-security-announce/2016-03/msg00041.html
- http://lists.opensuse.org/opensuse-security-announce/2016-03/msg00043.html
- http://lists.opensuse.org/opensuse-security-announce/2016-03/msg00043.html
- http://lists.opensuse.org/opensuse-security-announce/2016-03/msg00044.html
- http://lists.opensuse.org/opensuse-security-announce/2016-03/msg00044.html
- http://lists.opensuse.org/opensuse-security-announce/2016-03/msg00045.html
- http://lists.opensuse.org/opensuse-security-announce/2016-03/msg00045.html
- http://perception-point.io/2016/01/14/analysis-and-exploitation-of-a-linux-kernel-vulnerability-cve-2016-0728/
- http://perception-point.io/2016/01/14/analysis-and-exploitation-of-a-linux-kernel-vulnerability-cve-2016-0728/
- http://rhn.redhat.com/errata/RHSA-2016-0064.html
- http://rhn.redhat.com/errata/RHSA-2016-0064.html
- http://rhn.redhat.com/errata/RHSA-2016-0065.html
- http://rhn.redhat.com/errata/RHSA-2016-0065.html
- http://rhn.redhat.com/errata/RHSA-2016-0068.html
- http://rhn.redhat.com/errata/RHSA-2016-0068.html
- http://source.android.com/security/bulletin/2016-03-01.html
- http://source.android.com/security/bulletin/2016-03-01.html
- http://www.debian.org/security/2016/dsa-3448
- http://www.debian.org/security/2016/dsa-3448
- http://www.kernel.org/pub/linux/kernel/v4.x/ChangeLog-4.4.1
- http://www.kernel.org/pub/linux/kernel/v4.x/ChangeLog-4.4.1
- http://www.openwall.com/lists/oss-security/2016/01/19/2
- http://www.openwall.com/lists/oss-security/2016/01/19/2
- http://www.oracle.com/technetwork/topics/security/linuxbulletinjan2016-2867209.html
- http://www.oracle.com/technetwork/topics/security/linuxbulletinjan2016-2867209.html
- http://www.securityfocus.com/bid/81054
- http://www.securityfocus.com/bid/81054
- http://www.securitytracker.com/id/1034701
- http://www.securitytracker.com/id/1034701
- http://www.ubuntu.com/usn/USN-2870-1
- http://www.ubuntu.com/usn/USN-2870-1
- http://www.ubuntu.com/usn/USN-2870-2
- http://www.ubuntu.com/usn/USN-2870-2
- http://www.ubuntu.com/usn/USN-2871-1
- http://www.ubuntu.com/usn/USN-2871-1
- http://www.ubuntu.com/usn/USN-2871-2
- http://www.ubuntu.com/usn/USN-2871-2
- http://www.ubuntu.com/usn/USN-2872-1
- http://www.ubuntu.com/usn/USN-2872-1
- http://www.ubuntu.com/usn/USN-2872-2
- http://www.ubuntu.com/usn/USN-2872-2
- http://www.ubuntu.com/usn/USN-2872-3
- http://www.ubuntu.com/usn/USN-2872-3
- http://www.ubuntu.com/usn/USN-2873-1
- http://www.ubuntu.com/usn/USN-2873-1
- https://bto.bluecoat.com/security-advisory/sa112
- https://bto.bluecoat.com/security-advisory/sa112
- https://bugzilla.redhat.com/show_bug.cgi?id=1297475
- https://bugzilla.redhat.com/show_bug.cgi?id=1297475
- https://github.com/torvalds/linux/commit/23567fd052a9abb6d67fe8e7a9ccdd9800a540f2
- https://github.com/torvalds/linux/commit/23567fd052a9abb6d67fe8e7a9ccdd9800a540f2
- https://h20565.www2.hp.com/portal/site/hpsc/public/kb/docDisplay?docId=emr_na-c05018265
- https://h20565.www2.hp.com/portal/site/hpsc/public/kb/docDisplay?docId=emr_na-c05018265
- https://h20566.www2.hpe.com/portal/site/hpsc/public/kb/docDisplay?docId=emr_na-c05130958
- https://h20566.www2.hpe.com/portal/site/hpsc/public/kb/docDisplay?docId=emr_na-c05130958
- https://h20566.www2.hpe.com/portal/site/hpsc/public/kb/docDisplay?docId=emr_na-c05158380
- https://h20566.www2.hpe.com/portal/site/hpsc/public/kb/docDisplay?docId=emr_na-c05158380
- https://security.netapp.com/advisory/ntap-20160211-0001/
- https://security.netapp.com/advisory/ntap-20160211-0001/
- https://www.exploit-db.com/exploits/39277/
- https://www.exploit-db.com/exploits/39277/