Vulnerabilities > CVE-2015-7547 - Improper Restriction of Operations within the Bounds of a Memory Buffer vulnerability in multiple products
Attack vector
NETWORK Attack complexity
HIGH Privileges required
NONE Confidentiality impact
HIGH Integrity impact
HIGH Availability impact
HIGH Summary
Multiple stack-based buffer overflows in the (1) send_dg and (2) send_vc functions in the libresolv library in the GNU C Library (aka glibc or libc6) before 2.23 allow remote attackers to cause a denial of service (crash) or possibly execute arbitrary code via a crafted DNS response that triggers a call to the getaddrinfo function with the AF_UNSPEC or AF_INET6 address family, related to performing "dual A/AAAA DNS queries" and the libnss_dns.so.2 NSS module.
Vulnerable Configurations
| Part | Description | Count |
|---|---|---|
| OS | 1 | |
| OS | 3 | |
| OS | 14 | |
| OS | 1 | |
| OS | 1 | |
| OS | 7 | |
| Application | 4 | |
| Application | 2 | |
| Application | 3 | |
| Application | 2 | |
| Application | F5
| 9 |
| Application | Gnu
| 21 |
Common Weakness Enumeration (CWE)
Common Attack Pattern Enumeration and Classification (CAPEC)
- Buffer Overflow via Environment Variables This attack pattern involves causing a buffer overflow through manipulation of environment variables. Once the attacker finds that they can modify an environment variable, they may try to overflow associated buffers. This attack leverages implicit trust often placed in environment variables.
- Overflow Buffers Buffer Overflow attacks target improper or missing bounds checking on buffer operations, typically triggered by input injected by an attacker. As a consequence, an attacker is able to write past the boundaries of allocated buffer regions in memory, causing a program crash or potentially redirection of execution as per the attackers' choice.
- Client-side Injection-induced Buffer Overflow This type of attack exploits a buffer overflow vulnerability in targeted client software through injection of malicious content from a custom-built hostile service.
- Filter Failure through Buffer Overflow In this attack, the idea is to cause an active filter to fail by causing an oversized transaction. An attacker may try to feed overly long input strings to the program in an attempt to overwhelm the filter (by causing a buffer overflow) and hoping that the filter does not fail securely (i.e. the user input is let into the system unfiltered).
- MIME Conversion An attacker exploits a weakness in the MIME conversion routine to cause a buffer overflow and gain control over the mail server machine. The MIME system is designed to allow various different information formats to be interpreted and sent via e-mail. Attack points exist when data are converted to MIME compatible format and back.
Exploit-Db
description glibc - getaddrinfo Stack Based Buffer Overflow. CVE-2015-7547. Remote exploit for Linux platform file exploits/linux/remote/40339.py id EDB-ID:40339 last seen 2016-09-06 modified 2016-09-06 platform linux port published 2016-09-06 reporter SpeeDr00t source https://www.exploit-db.com/download/40339/ title glibc - getaddrinfo Stack Based Buffer Overflow type remote description glibc - getaddrinfo Stack-Based Buffer Overflow. CVE-2015-7547. Dos exploit for linux platform file exploits/linux/dos/39454.txt id EDB-ID:39454 last seen 2016-02-21 modified 2016-02-16 platform linux port published 2016-02-16 reporter Google Security Research source https://www.exploit-db.com/download/39454/ title glibc - getaddrinfo Stack-Based Buffer Overflow type dos
Nessus
NASL family Slackware Local Security Checks NASL id SLACKWARE_SSA_2016-054-02.NASL description New glibc packages are available for Slackware 14.1 and -current to fix security issues. last seen 2020-06-01 modified 2020-06-02 plugin id 88910 published 2016-02-24 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/88910 title Slackware 14.1 / current : glibc (SSA:2016-054-02) code # # (C) Tenable Network Security, Inc. # # The descriptive text and package checks in this plugin were # extracted from Slackware Security Advisory 2016-054-02. The text # itself is copyright (C) Slackware Linux, Inc. # include("compat.inc"); if (description) { script_id(88910); script_version("2.10"); script_cvs_date("Date: 2019/04/11 17:23:07"); script_cve_id("CVE-2015-7547"); script_xref(name:"SSA", value:"2016-054-02"); script_xref(name:"IAVA", value:"2016-A-0053"); script_xref(name:"TRA", value:"TRA-2017-08"); script_name(english:"Slackware 14.1 / current : glibc (SSA:2016-054-02)"); script_summary(english:"Checks for updated packages in /var/log/packages"); script_set_attribute( attribute:"synopsis", value:"The remote Slackware host is missing a security update." ); script_set_attribute( attribute:"description", value: "New glibc packages are available for Slackware 14.1 and -current to fix security issues." ); # http://www.slackware.com/security/viewer.php?l=slackware-security&y=2016&m=slackware-security.569827 script_set_attribute( attribute:"see_also", value:"http://www.nessus.org/u?5b214cba" ); script_set_attribute( attribute:"see_also", value:"https://www.tenable.com/security/research/tra-2017-08" ); script_set_attribute(attribute:"solution", value:"Update the affected packages."); script_set_cvss_base_vector("CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:C"); script_set_cvss_temporal_vector("CVSS2#E:POC/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:P/RL:O/RC:C"); script_set_attribute(attribute:"exploitability_ease", value:"Exploits are available"); script_set_attribute(attribute:"exploit_available", value:"true"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:slackware:slackware_linux:glibc"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:slackware:slackware_linux:glibc-i18n"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:slackware:slackware_linux:glibc-profile"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:slackware:slackware_linux:glibc-solibs"); script_set_attribute(attribute:"cpe", value:"cpe:/o:slackware:slackware_linux"); script_set_attribute(attribute:"cpe", value:"cpe:/o:slackware:slackware_linux:14.1"); script_set_attribute(attribute:"patch_publication_date", value:"2016/02/23"); script_set_attribute(attribute:"in_the_news", value:"true"); script_set_attribute(attribute:"plugin_publication_date", value:"2016/02/24"); script_set_attribute(attribute:"stig_severity", value:"I"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_copyright(english:"This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof."); script_family(english:"Slackware Local Security Checks"); script_dependencies("ssh_get_info.nasl"); script_require_keys("Host/local_checks_enabled", "Host/Slackware/release", "Host/Slackware/packages"); exit(0); } include("audit.inc"); include("global_settings.inc"); include("slackware.inc"); if (!get_kb_item("Host/local_checks_enabled")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); if (!get_kb_item("Host/Slackware/release")) audit(AUDIT_OS_NOT, "Slackware"); if (!get_kb_item("Host/Slackware/packages")) audit(AUDIT_PACKAGE_LIST_MISSING); cpu = get_kb_item("Host/cpu"); if (isnull(cpu)) audit(AUDIT_UNKNOWN_ARCH); if ("x86_64" >!< cpu && cpu !~ "^i[3-6]86$") audit(AUDIT_LOCAL_CHECKS_NOT_IMPLEMENTED, "Slackware", cpu); flag = 0; if (slackware_check(osver:"14.1", pkgname:"glibc", pkgver:"2.17", pkgarch:"i486", pkgnum:"11_slack14.1")) flag++; if (slackware_check(osver:"14.1", pkgname:"glibc-i18n", pkgver:"2.17", pkgarch:"i486", pkgnum:"11_slack14.1")) flag++; if (slackware_check(osver:"14.1", pkgname:"glibc-profile", pkgver:"2.17", pkgarch:"i486", pkgnum:"11_slack14.1")) flag++; if (slackware_check(osver:"14.1", pkgname:"glibc-solibs", pkgver:"2.17", pkgarch:"i486", pkgnum:"11_slack14.1")) flag++; if (slackware_check(osver:"14.1", arch:"x86_64", pkgname:"glibc", pkgver:"2.17", pkgarch:"x86_64", pkgnum:"11_slack14.1")) flag++; if (slackware_check(osver:"14.1", arch:"x86_64", pkgname:"glibc-i18n", pkgver:"2.17", pkgarch:"x86_64", pkgnum:"11_slack14.1")) flag++; if (slackware_check(osver:"14.1", arch:"x86_64", pkgname:"glibc-profile", pkgver:"2.17", pkgarch:"x86_64", pkgnum:"11_slack14.1")) flag++; if (slackware_check(osver:"14.1", arch:"x86_64", pkgname:"glibc-solibs", pkgver:"2.17", pkgarch:"x86_64", pkgnum:"11_slack14.1")) flag++; if (slackware_check(osver:"current", pkgname:"glibc", pkgver:"2.23", pkgarch:"i586", pkgnum:"1")) flag++; if (slackware_check(osver:"current", pkgname:"glibc-i18n", pkgver:"2.23", pkgarch:"i586", pkgnum:"1")) flag++; if (slackware_check(osver:"current", pkgname:"glibc-profile", pkgver:"2.23", pkgarch:"i586", pkgnum:"1")) flag++; if (slackware_check(osver:"current", pkgname:"glibc-solibs", pkgver:"2.23", pkgarch:"i586", pkgnum:"1")) flag++; if (slackware_check(osver:"current", arch:"x86_64", pkgname:"glibc", pkgver:"2.23", pkgarch:"x86_64", pkgnum:"1")) flag++; if (slackware_check(osver:"current", arch:"x86_64", pkgname:"glibc-i18n", pkgver:"2.23", pkgarch:"x86_64", pkgnum:"1")) flag++; if (slackware_check(osver:"current", arch:"x86_64", pkgname:"glibc-profile", pkgver:"2.23", pkgarch:"x86_64", pkgnum:"1")) flag++; if (slackware_check(osver:"current", arch:"x86_64", pkgname:"glibc-solibs", pkgver:"2.23", pkgarch:"x86_64", pkgnum:"1")) flag++; if (flag) { if (report_verbosity > 0) security_hole(port:0, extra:slackware_report_get()); else security_hole(0); exit(0); } else audit(AUDIT_HOST_NOT, "affected");NASL family Misc. NASL id VMWARE_VMSA-2016-0002_REMOTE.NASL description The remote VMware ESXi host is 5.5 prior to build 3568722 or 6.0 prior to build 3568940. It is, therefore, affected by a stack-based buffer overflow condition in the GNU C Library (glibc) DNS client-side resolver due to improper validation of user-supplied input when looking up names via the getaddrinfo() function. An attacker can exploit this to execute arbitrary code by using an attacker-controlled domain name, an attacker-controlled DNS server, or through a man-in-the-middle attack. last seen 2020-06-01 modified 2020-06-02 plugin id 88906 published 2016-02-23 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/88906 title ESXi 5.5 < Build 3568722 / 6.0 < Build 3568940 glibc DNS Resolver RCE (VMSA-2016-0002) (remote check) code # # (C) Tenable Network Security, Inc. # include("compat.inc"); if (description) { script_id(88906); script_version("1.15"); script_cvs_date("Date: 2019/11/20"); script_cve_id("CVE-2015-7547"); script_bugtraq_id(83265); script_xref(name:"VMSA", value:"2016-0002"); script_xref(name:"CERT", value:"457759"); script_xref(name:"EDB-ID", value:"39454"); script_name(english:"ESXi 5.5 < Build 3568722 / 6.0 < Build 3568940 glibc DNS Resolver RCE (VMSA-2016-0002) (remote check)"); script_summary(english:"Checks the ESXi version and build number."); script_set_attribute(attribute:"synopsis", value: "The remote VMware ESXi host is affected by a remote code execution vulnerability."); script_set_attribute(attribute:"description", value: "The remote VMware ESXi host is 5.5 prior to build 3568722 or 6.0 prior to build 3568940. It is, therefore, affected by a stack-based buffer overflow condition in the GNU C Library (glibc) DNS client-side resolver due to improper validation of user-supplied input when looking up names via the getaddrinfo() function. An attacker can exploit this to execute arbitrary code by using an attacker-controlled domain name, an attacker-controlled DNS server, or through a man-in-the-middle attack."); script_set_attribute(attribute:"see_also", value:"http://www.vmware.com/security/advisories/VMSA-2016-0002.html"); script_set_attribute(attribute:"see_also", value:"http://kb.vmware.com/kb/2144353"); script_set_attribute(attribute:"see_also", value:"http://kb.vmware.com/kb/2144357"); script_set_attribute(attribute:"see_also", value:"http://kb.vmware.com/kb/2144057"); script_set_attribute(attribute:"see_also", value:"http://kb.vmware.com/kb/2144054"); # https://googleonlinesecurity.blogspot.com/2016/02/cve-2015-7547-glibc-getaddrinfo-stack.html script_set_attribute(attribute:"see_also", value:"http://www.nessus.org/u?8bdae0a0"); script_set_attribute(attribute:"see_also", value:"https://sourceware.org/bugzilla/show_bug.cgi?id=18665"); script_set_attribute(attribute:"solution", value: "Apply the appropriate patch as referenced in the vendor advisory."); script_set_cvss_base_vector("CVSS2#AV:N/AC:M/Au:N/C:P/I:P/A:P"); script_set_cvss_temporal_vector("CVSS2#E:POC/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:P/RL:O/RC:C"); script_set_attribute(attribute:"cvss_score_source", value:"CVE-2015-7547"); script_set_attribute(attribute:"exploitability_ease", value:"Exploits are available"); script_set_attribute(attribute:"exploit_available", value:"true"); script_set_attribute(attribute:"in_the_news", value:"true"); script_set_attribute(attribute:"vuln_publication_date", value:"2015/07/14"); script_set_attribute(attribute:"patch_publication_date", value:"2016/02/21"); script_set_attribute(attribute:"plugin_publication_date", value:"2016/02/23"); script_set_attribute(attribute:"plugin_type", value:"remote"); script_set_attribute(attribute:"cpe", value:"cpe:/o:vmware:esxi"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_family(english:"Misc."); script_copyright(english:"This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof."); script_dependencies("vmware_vsphere_detect.nbin"); script_require_keys("Host/VMware/version", "Host/VMware/release"); exit(0); } include("audit.inc"); include("global_settings.inc"); include("misc_func.inc"); fixes = make_array( '5.5', '3568722', '6.0', '3568940' ); rel = get_kb_item_or_exit("Host/VMware/release"); if ("ESXi" >!< rel) audit(AUDIT_OS_NOT, "ESXi"); ver = get_kb_item_or_exit("Host/VMware/version"); # Lets extract the ESXi version ver = ereg_replace(pattern:"^ESXi? ([0-9]+\.[0-9]+).*$", replace:"\1", string:ver); if ( ver !~ '^5\\.5($|[^0-9])' && ver !~ '^6\\.0($|[^0-9])' ) audit(AUDIT_OS_NOT, "ESXi 5.5 / 6.0"); fixed_build = fixes[ver]; # We should never ever trigger this if (empty_or_null(fixed_build)) audit(AUDIT_VER_FORMAT, ver); match = eregmatch(pattern:'^VMware ESXi.*build-([0-9]+)$', string:rel); if (isnull(match)) audit(AUDIT_UNKNOWN_BUILD, "VMware ESXi", "5.5 / 6.0"); build = int(match[1]); if (build < fixed_build) { report = '\n ESXi version : ' + ver + '\n Installed build : ' + build + '\n Fixed build : ' + fixed_build + '\n'; security_report_v4(port:0, severity:SECURITY_WARNING, extra:report); } else audit(AUDIT_INST_VER_NOT_VULN, "VMware ESXi ", ver + " build " + build);NASL family OracleVM Local Security Checks NASL id ORACLEVM_OVMSA-2017-0051.NASL description The remote OracleVM system is missing necessary patches to address critical security updates : - Update newmode size to fix a possible corruption - Fix AF_INET6 getaddrinfo with nscd (#1416496) - Update tests for struct sockaddr_storage changes (#1338673) - Use FL_CLOEXEC in internal calls to fopen (#1012343). - Fix CVE-2015-8779 glibc: Unbounded stack allocation in catopen function (#1358015). - Make padding in struct sockaddr_storage explicit (#1338673) - Fix detection of Intel FMA hardware (#1384281). - Add support for, ur_IN, and wal_ET locales (#1101858). - Change malloc/tst-malloc-thread-exit.c to use fewer threads and avoid timeout (#1318380). - df can fail on some systems (#1307029). - Log uname, cpuinfo, meminfo during build (#1307029). - Draw graphs for heap and stack only if MAXSIZE_HEAP and MAXSIZE_STACK are non-zero (#1331304). - Avoid unneeded calls to __check_pf in getadddrinfo (#1270950) - Fix CVE-2015-8778 glibc: Integer overflow in hcreate and hcreate_r (#1358013). - Fix CVE-2015-8776 glibc: Segmentation fault caused by passing out-of-range data to strftime (#1358011). - tzdata-update: Ignore umask setting (#1373646) - CVE-2014-9761: Fix unbounded stack allocation in nan* (#1358014) - Avoid using uninitialized data in getaddrinfo (#1223095) - Update fix for CVE-2015-7547 (#1296029). - Create helper threads with enough stack for POSIX AIO and timers (#1299319). - Fix CVE-2015-7547: getaddrinfo stack-based buffer overflow (#1296029). - Update malloc free_list cyclic fix (#1264189). - Update tzdata-update changes (#1200555). - Avoid redundant shift character in iconv output at block boundary (#1293914). - Clean up testsuite results when testing with newer kernels (#1293464). - Do not rewrite /etc/localtime if it is a symbolic link. (#1200555) - Support long lines in /etc/hosts (#1020263). - Avoid aliasing warning in tst-rec-dlopen (#1291444) - Don last seen 2020-06-01 modified 2020-06-02 plugin id 99078 published 2017-03-30 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/99078 title OracleVM 3.3 / 3.4 : glibc (OVMSA-2017-0051) NASL family F5 Networks Local Security Checks NASL id F5_BIGIP_SOL47098834.NASL description Multiple stack-based buffer overflows in the (1) send_dg and (2) send_vc functions in the libresolv library in the GNU C Library (aka glibc or libc6) before 2.23 allow remote attackers to cause a denial of service (crash) or possibly execute arbitrary code via a crafted DNS response that triggers a call to the getaddrinfo function with the AF_UNSPEC or AF_INET6 address family, related to performing last seen 2020-06-01 modified 2020-06-02 plugin id 88769 published 2016-02-17 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/88769 title F5 Networks BIG-IP : glibc vulnerability (K47098834) NASL family SuSE Local Security Checks NASL id OPENSUSE-2016-233.NASL description This update for glibc fixes the following issues : - errorcheck-mutex-no-elision.patch: Don last seen 2020-06-05 modified 2016-02-19 plugin id 88855 published 2016-02-19 reporter This script is Copyright (C) 2016-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/88855 title openSUSE Security Update : glibc (openSUSE-2016-233) NASL family SuSE Local Security Checks NASL id OPENSUSE-2016-234.NASL description This update for glibc fixes the following security issues : - fix stack overflow in the glibc libresolv DNS resolver function getaddrinfo(), known as CVE-2015-7547. It is a client side networked/remote vulnerability. last seen 2020-06-05 modified 2016-02-22 plugin id 88878 published 2016-02-22 reporter This script is Copyright (C) 2016-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/88878 title openSUSE Security Update : glibc (openSUSE-2016-234) NASL family Oracle Linux Local Security Checks NASL id ORACLELINUX_ELSA-2016-0176.NASL description From Red Hat Security Advisory 2016:0176 : Updated glibc packages that fix two security issues and two bugs are now available for Red Hat Enterprise Linux 7. Red Hat Product Security has rated this update as having Critical security impact. Common Vulnerability Scoring System (CVSS) base scores, which give detailed severity ratings, are available for each vulnerability from the CVE links in the References section. The glibc packages provide the standard C libraries (libc), POSIX thread libraries (libpthread), standard math libraries (libm), and the name service cache daemon (nscd) used by multiple programs on the system. Without these libraries, the Linux system cannot function correctly. A stack-based buffer overflow was found in the way the libresolv library performed dual A/AAAA DNS queries. A remote attacker could create a specially crafted DNS response which could cause libresolv to crash or, potentially, execute code with the permissions of the user running the library. Note: this issue is only exposed when libresolv is called from the nss_dns NSS service module. (CVE-2015-7547) It was discovered that the calloc implementation in glibc could return memory areas which contain non-zero bytes. This could result in unexpected application behavior such as hangs or crashes. (CVE-2015-5229) The CVE-2015-7547 issue was discovered by the Google Security Team and Red Hat. Red Hat would like to thank Jeff Layton for reporting the CVE-2015-5229 issue. This update also fixes the following bugs : * The existing implementation of the last seen 2020-06-01 modified 2020-06-02 plugin id 88777 published 2016-02-17 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/88777 title Oracle Linux 7 : glibc (ELSA-2016-0176) NASL family Debian Local Security Checks NASL id DEBIAN_DSA-3481.NASL description Several vulnerabilities have been fixed in the GNU C Library, glibc. The first vulnerability listed below is considered to have critical impact. - CVE-2015-7547 The Google Security Team and Red Hat discovered that the glibc host name resolver function, getaddrinfo, when processing AF_UNSPEC queries (for dual A/AAAA lookups), could mismanage its internal buffers, leading to a stack-based buffer overflow and arbitrary code execution. This vulnerability affects most applications which perform host name resolution using getaddrinfo, including system services. - CVE-2015-8776 Adam Nielsen discovered that if an invalid separated time value is passed to strftime, the strftime function could crash or leak information. Applications normally pass only valid time information to strftime; no affected applications are known. - CVE-2015-8778 Szabolcs Nagy reported that the rarely-used hcreate and hcreate_r functions did not check the size argument properly, leading to a crash (denial of service) for certain arguments. No impacted applications are known at this time. - CVE-2015-8779 The catopen function contains several unbound stack allocations (stack overflows), causing it the crash the process (denial of service). No applications where this issue has a security impact are currently known. While it is only necessary to ensure that all processes are not using the old glibc anymore, it is recommended to reboot the machines after applying the security upgrade. last seen 2020-06-01 modified 2020-06-02 plugin id 88768 published 2016-02-17 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/88768 title Debian DSA-3481-1 : glibc - security update NASL family Fedora Local Security Checks NASL id FEDORA_2016-0480DEFC94.NASL description This updates addresses a critical security vulnerability in the DNS resolver related to `AF_UNSPEC` queries with `getaddrinfo` (CVE-2015-7547). It also includes security fixes for CVE-2015-8777 and CVE-2015-1781. It improves `malloc` scalability for applications which start and terminate many threads. The output of `locale -a` is now ASCII-only (previously, it contained ISO-8859-1 characters). Note that Tenable Network Security has extracted the preceding description block directly from the Fedora security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-05 modified 2016-03-04 plugin id 89473 published 2016-03-04 reporter This script is Copyright (C) 2016-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/89473 title Fedora 22 : glibc-2.21-11.fc22 (2016-0480defc94) NASL family VMware ESX Local Security Checks NASL id VMWARE_VMSA-2016-0002.NASL description a. glibc update for multiple products. The glibc library has been updated in multiple products to resolve a stack-based buffer overflow present in the glibc getaddrinfo function. The Common Vulnerabilities and Exposures project (cve.mitre.org) has assigned the identifier CVE-2015-7547. VMware products have been grouped into the following four categories : I) ESXi and ESX Hypervisor Versions of ESXi and ESX prior to 5.5 are not affected because they do not ship with a vulnerable version of glibc. ESXi 5.5 and ESXi 6.0 ship with a vulnerable version of glibc and are affected. See table 1 for remediation for ESXi 5.5 and ESXi 6.0. II) Windows-based products Windows-based products, including all versions of vCenter Server running on Windows, are not affected. III) VMware virtual appliances VMware virtual appliances ship with a vulnerable version of glibc and are affected. See table 2 for remediation for appliances. IV) Products that run on Linux VMware products that run on Linux (excluding virtual appliances) might use a vulnerable version of glibc as part of the base operating system. If the operating system has a vulnerable version of glibc, VMware recommends that customers contact their operating system vendor for resolution. WORKAROUND Workarounds are available for several virtual appliances. These are documented in VMware KB article 2144032. RECOMMENDATIONS VMware recommends customers evaluate and deploy patches for affected products in Table 1 and 2 below as these patches become available. In case patches are not available, customers are advised to deploy the workaround. Column 4 of the following tables lists the action required to remediate the vulnerability in each release, if a solution is available. Table 1 - ESXi ============== last seen 2020-06-01 modified 2020-06-02 plugin id 88954 published 2016-02-25 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/88954 title VMSA-2016-0002 : VMware product updates address a critical glibc security vulnerability NASL family Red Hat Local Security Checks NASL id REDHAT-RHSA-2016-0225.NASL description Updated glibc packages that fix one security issue are now available for Red Hat Enterprise Linux 6.2, 6.4, and 6.5 Advanced Update Support, and Red Hat Enterprise Linux 6.6 and 7.1 Extended Update Support. Red Hat Product Security has rated this update as having Critical security impact. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available from the CVE link in the References section. The glibc packages provide the standard C libraries (libc), POSIX thread libraries (libpthread), standard math libraries (libm), and the Name Server Caching Daemon (nscd) used by multiple programs on the system. Without these libraries, the Linux system cannot function correctly. A stack-based buffer overflow was found in the way the libresolv library performed dual A/AAAA DNS queries. A remote attacker could create a specially crafted DNS response which could cause libresolv to crash or, potentially, execute code with the permissions of the user running the library. Note: this issue is only exposed when libresolv is called from the nss_dns NSS service module. (CVE-2015-7547) This issue was discovered by the Google Security Team and Red Hat. All glibc users are advised to upgrade to these updated packages, which contain a backported patch to correct this issue. last seen 2020-06-01 modified 2020-06-02 plugin id 88793 published 2016-02-17 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/88793 title RHEL 6 / 7 : glibc (RHSA-2016:0225) NASL family Debian Local Security Checks NASL id DEBIAN_DSA-3480.NASL description Several vulnerabilities have been fixed in the GNU C Library, eglibc. The CVE-2015-7547 vulnerability listed below is considered to have critical impact. - CVE-2014-8121 Robin Hack discovered that the nss_files database did not correctly implement enumeration interleaved with name-based or ID-based lookups. This could cause the enumeration enter an endless loop, leading to a denial of service. - CVE-2015-1781 Arjun Shankar discovered that the _r variants of host name resolution functions (like gethostbyname_r), when performing DNS name resolution, suffered from a buffer overflow if a misaligned buffer was supplied by the applications, leading to a crash or, potentially, arbitrary code execution. Most applications are not affected by this vulnerability because they use aligned buffers. - CVE-2015-7547 The Google Security Team and Red Hat discovered that the eglibc host name resolver function, getaddrinfo, when processing AF_UNSPEC queries (for dual A/AAAA lookups), could mismanage its internal buffers, leading to a stack-based buffer overflow and arbitrary code execution. This vulnerability affects most applications which perform host name resolution using getaddrinfo, including system services. - CVE-2015-8776 Adam Nielsen discovered that if an invalid separated time value is passed to strftime, the strftime function could crash or leak information. Applications normally pass only valid time information to strftime; no affected applications are known. - CVE-2015-8777 Hector Marco-Gisbert reported that LD_POINTER_GUARD was not ignored for SUID programs, enabling an unintended bypass of a security feature. This update causes eglibc to always ignore the LD_POINTER_GUARD environment variable. - CVE-2015-8778 Szabolcs Nagy reported that the rarely-used hcreate and hcreate_r functions did not check the size argument properly, leading to a crash (denial of service) for certain arguments. No impacted applications are known at this time. - CVE-2015-8779 The catopen function contains several unbound stack allocations (stack overflows), causing it the crash the process (denial of service). No applications where this issue has a security impact are currently known. The following fixed vulnerabilities currently lack CVE assignment : - Joseph Myers reported that an integer overflow in the strxfrm can lead to heap-based buffer overflow, possibly allowing arbitrary code execution. In addition, a fallback path in strxfrm uses an unbounded stack allocation (stack overflow), leading to a crash or erroneous application behavior. - Kostya Serebryany reported that the fnmatch function could skip over the terminating NUL character of a malformed pattern, causing an application calling fnmatch to crash (denial of service). - Joseph Myers reported that the IO_wstr_overflow function, internally used by wide-oriented character streams, suffered from an integer overflow, leading to a heap-based buffer overflow. On GNU/Linux systems, wide-oriented character streams are rarely used, and no affected applications are known. - Andreas Schwab reported a memory leak (memory allocation without a matching deallocation) while processing certain DNS answers in getaddrinfo, related to the _nss_dns_gethostbyname4_r function. This vulnerability could lead to a denial of service. While it is only necessary to ensure that all processes are not using the old eglibc anymore, it is recommended to reboot the machines after applying the security upgrade. last seen 2020-06-01 modified 2020-06-02 plugin id 88767 published 2016-02-17 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/88767 title Debian DSA-3480-1 : eglibc - security update NASL family SuSE Local Security Checks NASL id SUSE_SU-2016-0472-1.NASL description This update for glibc fixes the following issues : - CVE-2015-7547: A stack-based buffer overflow in getaddrinfo allowed remote attackers to cause a crash or execute arbitrary code via crafted and timed DNS responses (bsc#961721) - CVE-2015-8777: Insufficient checking of LD_POINTER_GUARD environment variable allowed local attackers to bypass the pointer guarding protection of the dynamic loader on set-user-ID and set-group-ID programs (bsc#950944) - CVE-2015-8776: Out-of-range time values passed to the strftime function may cause it to crash, leading to a denial of service, or potentially disclosure information (bsc#962736) - CVE-2015-8778: Integer overflow in hcreate and hcreate_r could have caused an out-of-bound memory access. leading to application crashes or, potentially, arbitrary code execution (bsc#962737) - CVE-2014-9761: A stack overflow (unbounded alloca) could have caused applications which process long strings with the nan function to crash or, potentially, execute arbitrary code. (bsc#962738) - CVE-2015-8779: A stack overflow (unbounded alloca) in the catopen function could have caused applications which pass long strings to the catopen function to crash or, potentially execute arbitrary code. (bsc#962739) The update package also includes non-security fixes. See advisory for details. Note that Tenable Network Security has extracted the preceding description block directly from the SUSE security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 88833 published 2016-02-18 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/88833 title SUSE SLED11 / SLES11 Security Update : glibc (SUSE-SU-2016:0472-1) NASL family Misc. NASL id ARISTA_EOS_SA0017.NASL description The version of Arista Networks EOS running on the remote device is affected by multiple stack-based buffer overflow conditions in the GNU libresolv library, specifically within the send_dg() and send_vc() functions, when handling DNS responses that trigger a call to the getaddrinfo() function with the AF_UNSPEC or AF_INET6 address family. An unauthenticated, remote attacker can exploit these issues, via a specially crafted DNS response, to cause a denial of service condition or the execution of arbitrary code. last seen 2020-03-17 modified 2018-02-28 plugin id 107059 published 2018-02-28 reporter This script is Copyright (C) 2018-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/107059 title Arista Networks EOS libresolv Overflow RCE (SA0017) NASL family Gentoo Local Security Checks NASL id GENTOO_GLSA-201602-02.NASL description The remote host is affected by the vulnerability described in GLSA-201602-02 (GNU C Library: Multiple vulnerabilities) Multiple vulnerabilities have been discovered in the GNU C Library: The Google Security Team and Red Hat discovered a stack-based buffer overflow in the send_dg() and send_vc() functions due to a buffer mismanagement when getaddrinfo() is called with AF_UNSPEC (CVE-2015-7547). The strftime() function access invalid memory when passed out-of-range data, resulting in a crash (CVE-2015-8776). An integer overflow was found in the __hcreate_r() function (CVE-2015-8778). Multiple unbounded stack allocations were found in the catopen() function (CVE-2015-8779). Please review the CVEs referenced below for additional vulnerabilities that had already been fixed in previous versions of sys-libs/glibc, for which we have not issued a GLSA before. Impact : A remote attacker could exploit any application which performs host name resolution using getaddrinfo() in order to execute arbitrary code or crash the application. The other vulnerabilities can possibly be exploited to cause a Denial of Service or leak information. Workaround : A number of mitigating factors for CVE-2015-7547 have been identified. Please review the upstream advisory and references below. last seen 2020-06-01 modified 2020-06-02 plugin id 88822 published 2016-02-18 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/88822 title GLSA-201602-02 : GNU C Library: Multiple vulnerabilities NASL family Scientific Linux Local Security Checks NASL id SL_20160216_GLIBC_ON_SL7_X.NASL description A stack-based buffer overflow was found in the way the libresolv library performed dual A/AAAA DNS queries. A remote attacker could create a specially crafted DNS response which could cause libresolv to crash or, potentially, execute code with the permissions of the user running the library. Note: this issue is only exposed when libresolv is called from the nss_dns NSS service module. (CVE-2015-7547) It was discovered that the calloc implementation in glibc could return memory areas which contain non-zero bytes. This could result in unexpected application behavior such as hangs or crashes. (CVE-2015-5229) This update also fixes the following bugs : - The existing implementation of the last seen 2020-03-18 modified 2016-02-17 plugin id 88798 published 2016-02-17 reporter This script is Copyright (C) 2016-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/88798 title Scientific Linux Security Update : glibc on SL7.x x86_64 (20160216) NASL family Debian Local Security Checks NASL id DEBIAN_DLA-416.NASL description Several vulnerabilities have been fixed in the Debian GNU C Library, eglibc : CVE-2015-7547 The Google Security Team and Red Hat discovered that the glibc host name resolver function, getaddrinfo, when processing AF_UNSPEC queries (for dual A/AAAA lookups), could mismange its internal buffers, leading to a stack-based buffer overflow and arbitrary code execution. This vulnerability affects most applications which perform host name resolution using getaddrinfo, including system services. The following fixed vulnerabilities currently lack CVE assignment : Andreas Schwab reported a memory leak (memory allocation without a matching deallocation) while processing certain DNS answers in getaddrinfo, related to the _nss_dns_gethostbyname4_r function. This vulnerability could lead to a denial of service. For Debian 6 last seen 2020-03-17 modified 2016-02-17 plugin id 88764 published 2016-02-17 reporter This script is Copyright (C) 2016-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/88764 title Debian DLA-416-1 : eglibc security update NASL family CISCO NASL id CISCO-CSCUY36553-NXOS.NASL description The version of Cisco NX-OS software running on the remote device is affected by a remote code execution vulnerability in the bundled version of the GNU C Library (glibc) due to a stack-based buffer overflow condition in the DNS resolver. An unauthenticated, remote attacker can exploit this, via a crafted DNS response that triggers a call to the getaddrinfo() function, to cause a denial of service condition or the execution of arbitrary code. last seen 2020-06-01 modified 2020-06-02 plugin id 93480 published 2016-09-14 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/93480 title Cisco Nexus 3000 / 9000 Series GNU C Library (glibc) getaddrinfo() RCE (cisco-sa-20160218-glibc) NASL family FreeBSD Local Security Checks NASL id FREEBSD_PKG_2DD7E97ED5E811E5BCBDBC5FF45D0F28.NASL description Fabio Olive Leite reports : A stack-based buffer overflow was found in libresolv when invoked from nss_dns, allowing specially crafted DNS responses to seize control of EIP in the DNS client. The buffer overflow occurs in the functions send_dg (send datagram) and send_vc (send TCP) for the NSS module libnss_dns.so.2 when calling getaddrinfo with AF_UNSPEC family, or in some cases AF_INET6 family. The use of AF_UNSPEC (or AF_INET6 in some cases) triggers the low-level resolver code to send out two parallel queries for A and AAAA. A mismanagement of the buffers used for those queries could result in the response of a query writing beyond the alloca allocated buffer created by __res_nquery. last seen 2020-06-01 modified 2020-06-02 plugin id 88817 published 2016-02-18 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/88817 title FreeBSD : glibc -- getaddrinfo stack-based buffer overflow (2dd7e97e-d5e8-11e5-bcbd-bc5ff45d0f28) NASL family OracleVM Local Security Checks NASL id ORACLEVM_OVMSA-2016-0013.NASL description The remote OracleVM system is missing necessary patches to address critical security updates : - Update fix for CVE-2015-7547 (#1296028). - Create helper threads with enough stack for POSIX AIO and timers (#1301625). - Fix CVE-2015-7547: getaddrinfo stack-based buffer overflow (#1296028). - Support loading more libraries with static TLS (#1291270). - Check for NULL arena pointer in _int_pvalloc (#1256890). - Don last seen 2020-06-01 modified 2020-06-02 plugin id 88783 published 2016-02-17 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/88783 title OracleVM 3.3 : glibc (OVMSA-2016-0013) (GHOST) NASL family SuSE Local Security Checks NASL id SUSE_SU-2016-0470-1.NASL description This update for glibc fixes the following issues : - CVE-2015-7547: A stack-based buffer overflow in getaddrinfo allowed remote attackers to cause a crash or execute arbitrary code via crafted and timed DNS responses (bsc#961721) - CVE-2015-8777: Insufficient checking of LD_POINTER_GUARD environment variable allowed local attackers to bypass the pointer guarding protection of the dynamic loader on set-user-ID and set-group-ID programs (bsc#950944) - CVE-2015-8776: Out-of-range time values passed to the strftime function may cause it to crash, leading to a denial of service, or potentially disclosure information (bsc#962736) - CVE-2015-8778: Integer overflow in hcreate and hcreate_r could have caused an out-of-bound memory access. leading to application crashes or, potentially, arbitrary code execution (bsc#962737) - CVE-2014-9761: A stack overflow (unbounded alloca) could have caused applications which process long strings with the nan function to crash or, potentially, execute arbitrary code. (bsc#962738) - CVE-2015-8779: A stack overflow (unbounded alloca) in the catopen function could have caused applications which pass long strings to the catopen function to crash or, potentially execute arbitrary code. (bsc#962739) - CVE-2013-2207: pt_chown tricked into granting access to another users pseudo-terminal (bsc#830257) - CVE-2013-4458: Stack (frame) overflow in getaddrinfo() when called with AF_INET6 (bsc#847227) - CVE-2014-8121: denial of service issue in the NSS backends (bsc#918187) - bsc#920338: Read past end of pattern in fnmatch - CVE-2015-1781: buffer overflow in nss_dns (bsc#927080) The update package also includes non-security fixes. See advisory for details. Note that Tenable Network Security has extracted the preceding description block directly from the SUSE security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 88831 published 2016-02-18 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/88831 title SUSE SLES11 Security Update : glibc (SUSE-SU-2016:0470-1) NASL family CentOS Local Security Checks NASL id CENTOS_RHSA-2016-0176.NASL description Updated glibc packages that fix two security issues and two bugs are now available for Red Hat Enterprise Linux 7. Red Hat Product Security has rated this update as having Critical security impact. Common Vulnerability Scoring System (CVSS) base scores, which give detailed severity ratings, are available for each vulnerability from the CVE links in the References section. The glibc packages provide the standard C libraries (libc), POSIX thread libraries (libpthread), standard math libraries (libm), and the name service cache daemon (nscd) used by multiple programs on the system. Without these libraries, the Linux system cannot function correctly. A stack-based buffer overflow was found in the way the libresolv library performed dual A/AAAA DNS queries. A remote attacker could create a specially crafted DNS response which could cause libresolv to crash or, potentially, execute code with the permissions of the user running the library. Note: this issue is only exposed when libresolv is called from the nss_dns NSS service module. (CVE-2015-7547) It was discovered that the calloc implementation in glibc could return memory areas which contain non-zero bytes. This could result in unexpected application behavior such as hangs or crashes. (CVE-2015-5229) The CVE-2015-7547 issue was discovered by the Google Security Team and Red Hat. Red Hat would like to thank Jeff Layton for reporting the CVE-2015-5229 issue. This update also fixes the following bugs : * The existing implementation of the last seen 2020-06-01 modified 2020-06-02 plugin id 88758 published 2016-02-17 reporter This script is Copyright (C) 2016-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/88758 title CentOS 7 : glibc (CESA-2016:0176) NASL family SuSE Local Security Checks NASL id SUSE_SU-2016-0471-1.NASL description This update for glibc fixes the following security issues : - CVE-2015-7547: A stack-based buffer overflow in getaddrinfo allowed remote attackers to cause a crash or execute arbitrary code via crafted and timed DNS responses (bsc#961721) - CVE-2015-8777: Insufficient checking of LD_POINTER_GUARD environment variable allowed local attackers to bypass the pointer guarding protection of the dynamic loader on set-user-ID and set-group-ID programs (bsc#950944) - CVE-2015-8776: Out-of-range time values passed to the strftime function may cause it to crash, leading to a denial of service, or potentially disclosure information (bsc#962736) - CVE-2015-8778: Integer overflow in hcreate and hcreate_r could have caused an out-of-bound memory access. leading to application crashes or, potentially, arbitrary code execution (bsc#962737) - CVE-2014-9761: A stack overflow (unbounded alloca) could have caused applications which process long strings with the nan function to crash or, potentially, execute arbitrary code. (bsc#962738) - CVE-2015-8779: A stack overflow (unbounded alloca) in the catopen function could have caused applications which pass long strings to the catopen function to crash or, potentially execute arbitrary code. (bsc#962739) The update package also includes non-security fixes. See advisory for details. Note that Tenable Network Security has extracted the preceding description block directly from the SUSE security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 88832 published 2016-02-18 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/88832 title SUSE SLED12 / SLES12 Security Update : glibc (SUSE-SU-2016:0471-1) NASL family Ubuntu Local Security Checks NASL id UBUNTU_USN-2900-1.NASL description It was discovered that the GNU C Library incorrectly handled receiving responses while performing DNS resolution. A remote attacker could use this issue to cause the GNU C Library to crash, resulting in a denial of service, or possibly execute arbitrary code. Note that Tenable Network Security has extracted the preceding description block directly from the Ubuntu security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 88806 published 2016-02-17 reporter Ubuntu Security Notice (C) 2016-2019 Canonical, Inc. / NASL script (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/88806 title Ubuntu 12.04 LTS / 14.04 LTS / 15.10 : eglibc, glibc vulnerability (USN-2900-1) NASL family Red Hat Local Security Checks NASL id REDHAT-RHSA-2016-0277.NASL description Updated rhev-hypervisor packages that fix one security issue are now available. Red Hat Product Security has rated this update as having Critical security impact. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available from the CVE link in the References section. The rhev-hypervisor package provides a Red Hat Enterprise Virtualization Hypervisor ISO disk image. The Red Hat Enterprise Virtualization Hypervisor is a dedicated Kernel-based Virtual Machine (KVM) hypervisor. It includes everything necessary to run and manage virtual machines: A subset of the Red Hat Enterprise Linux operating environment and the Red Hat Enterprise Virtualization Agent. Note: Red Hat Enterprise Virtualization Hypervisor is only available for the Intel 64 and AMD64 architectures with virtualization extensions. A stack-based buffer overflow was found in the way the libresolv library performed dual A/AAAA DNS queries. A remote attacker could create a specially crafted DNS response which could cause libresolv to crash or, potentially, execute code with the permissions of the user running the library. Note: this issue is only exposed when libresolv is called from the nss_dns NSS service module. (CVE-2015-7547) This issue was discovered by the Google Security Team and Red Hat. Users of Red Hat Enterprise Virtualization Hypervisor are advised to upgrade to these updated packages. last seen 2020-06-01 modified 2020-06-02 plugin id 88889 published 2016-02-23 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/88889 title RHEL 6 : rhev-hypervisor (RHSA-2016:0277) NASL family Oracle Linux Local Security Checks NASL id ORACLELINUX_ELSA-2016-0175.NASL description From Red Hat Security Advisory 2016:0175 : Updated glibc packages that fix one security issue and two bugs are now available for Red Hat Enterprise Linux 6. Red Hat Product Security has rated this update as having Critical security impact. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available from the CVE link in the References section. The glibc packages provide the standard C libraries (libc), POSIX thread libraries (libpthread), standard math libraries (libm), and the Name Server Caching Daemon (nscd) used by multiple programs on the system. Without these libraries, the Linux system cannot function correctly. A stack-based buffer overflow was found in the way the libresolv library performed dual A/AAAA DNS queries. A remote attacker could create a specially crafted DNS response which could cause libresolv to crash or, potentially, execute code with the permissions of the user running the library. Note: this issue is only exposed when libresolv is called from the nss_dns NSS service module. (CVE-2015-7547) This issue was discovered by the Google Security Team and Red Hat. This update also fixes the following bugs : * The dynamic loader has been enhanced to allow the loading of more shared libraries that make use of static thread local storage. While static thread local storage is the fastest access mechanism it may also prevent the shared library from being loaded at all since the static storage space is a limited and shared process-global resource. Applications which would previously fail with last seen 2020-06-01 modified 2020-06-02 plugin id 88776 published 2016-02-17 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/88776 title Oracle Linux 6 : glibc (ELSA-2016-0175) NASL family Red Hat Local Security Checks NASL id REDHAT-RHSA-2016-0175.NASL description Updated glibc packages that fix one security issue and two bugs are now available for Red Hat Enterprise Linux 6. Red Hat Product Security has rated this update as having Critical security impact. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available from the CVE link in the References section. The glibc packages provide the standard C libraries (libc), POSIX thread libraries (libpthread), standard math libraries (libm), and the Name Server Caching Daemon (nscd) used by multiple programs on the system. Without these libraries, the Linux system cannot function correctly. A stack-based buffer overflow was found in the way the libresolv library performed dual A/AAAA DNS queries. A remote attacker could create a specially crafted DNS response which could cause libresolv to crash or, potentially, execute code with the permissions of the user running the library. Note: this issue is only exposed when libresolv is called from the nss_dns NSS service module. (CVE-2015-7547) This issue was discovered by the Google Security Team and Red Hat. This update also fixes the following bugs : * The dynamic loader has been enhanced to allow the loading of more shared libraries that make use of static thread local storage. While static thread local storage is the fastest access mechanism it may also prevent the shared library from being loaded at all since the static storage space is a limited and shared process-global resource. Applications which would previously fail with last seen 2020-06-01 modified 2020-06-02 plugin id 88784 published 2016-02-17 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/88784 title RHEL 6 : glibc (RHSA-2016:0175) NASL family Amazon Linux Local Security Checks NASL id ALA_ALAS-2016-653.NASL description A stack-based buffer overflow flaw was found in the send_dg() and send_vc() functions, used by getaddrinfo() and other higher-level interfaces of glibc. A remote attacker able to cause an application to call either of these functions could use this flaw to execute arbitrary code with the permissions of the user running the application. last seen 2020-06-01 modified 2020-06-02 plugin id 88756 published 2016-02-17 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/88756 title Amazon Linux AMI : glibc (ALAS-2016-653) NASL family SuSE Local Security Checks NASL id OPENSUSE-2016-224.NASL description This update for glibc fixes the following security issues : - CVE-2015-7547: A stack-based buffer overflow in getaddrinfo allowed remote attackers to cause a crash or execute arbitrary code via crafted and timed DNS responses (bsc#961721) - CVE-2015-8777: Insufficient checking of LD_POINTER_GUARD environment variable allowed local attackers to bypass the pointer guarding protection of the dynamic loader on set-user-ID and set-group-ID programs (bsc#950944) - CVE-2015-8776: Out-of-range time values passed to the strftime function may cause it to crash, leading to a denial of service, or potentially disclosure information (bsc#962736) - CVE-2015-8778: Integer overflow in hcreate and hcreate_r could have caused an out-of-bound memory access. leading to application crashes or, potentially, arbitrary code execution (bsc#962737) - CVE-2014-9761: A stack overflow (unbounded alloca) could have caused applications which process long strings with the nan function to crash or, potentially, execute arbitrary code. (bsc#962738) - CVE-2015-8779: A stack overflow (unbounded alloca) in the catopen function could have caused applications which pass long strings to the catopen function to crash or, potentially execute arbitrary code. (bsc#962739) The following non-security bugs were fixed : - bsc#955647: Resource leak in resolver - bsc#956716: Don last seen 2020-06-05 modified 2016-02-18 plugin id 88829 published 2016-02-18 reporter This script is Copyright (C) 2016-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/88829 title openSUSE Security Update : glibc (openSUSE-2016-224) NASL family Scientific Linux Local Security Checks NASL id SL_20160216_GLIBC_ON_SL6_X.NASL description A stack-based buffer overflow was found in the way the libresolv library performed dual A/AAAA DNS queries. A remote attacker could create a specially crafted DNS response which could cause libresolv to crash or, potentially, execute code with the permissions of the user running the library. Note: this issue is only exposed when libresolv is called from the nss_dns NSS service module. (CVE-2015-7547) This update also fixes the following bugs : - The dynamic loader has been enhanced to allow the loading of more shared libraries that make use of static thread local storage. While static thread local storage is the fastest access mechanism it may also prevent the shared library from being loaded at all since the static storage space is a limited and shared process-global resource. Applications which would previously fail with last seen 2020-03-18 modified 2016-02-17 plugin id 88797 published 2016-02-17 reporter This script is Copyright (C) 2016-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/88797 title Scientific Linux Security Update : glibc on SL6.x i386/x86_64 (20160216) NASL family CentOS Local Security Checks NASL id CENTOS_RHSA-2016-0175.NASL description Updated glibc packages that fix one security issue and two bugs are now available for Red Hat Enterprise Linux 6. Red Hat Product Security has rated this update as having Critical security impact. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available from the CVE link in the References section. The glibc packages provide the standard C libraries (libc), POSIX thread libraries (libpthread), standard math libraries (libm), and the Name Server Caching Daemon (nscd) used by multiple programs on the system. Without these libraries, the Linux system cannot function correctly. A stack-based buffer overflow was found in the way the libresolv library performed dual A/AAAA DNS queries. A remote attacker could create a specially crafted DNS response which could cause libresolv to crash or, potentially, execute code with the permissions of the user running the library. Note: this issue is only exposed when libresolv is called from the nss_dns NSS service module. (CVE-2015-7547) This issue was discovered by the Google Security Team and Red Hat. This update also fixes the following bugs : * The dynamic loader has been enhanced to allow the loading of more shared libraries that make use of static thread local storage. While static thread local storage is the fastest access mechanism it may also prevent the shared library from being loaded at all since the static storage space is a limited and shared process-global resource. Applications which would previously fail with last seen 2020-06-01 modified 2020-06-02 plugin id 88757 published 2016-02-17 reporter This script is Copyright (C) 2016-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/88757 title CentOS 6 : glibc (CESA-2016:0175) NASL family Red Hat Local Security Checks NASL id REDHAT-RHSA-2016-0176.NASL description Updated glibc packages that fix two security issues and two bugs are now available for Red Hat Enterprise Linux 7. Red Hat Product Security has rated this update as having Critical security impact. Common Vulnerability Scoring System (CVSS) base scores, which give detailed severity ratings, are available for each vulnerability from the CVE links in the References section. The glibc packages provide the standard C libraries (libc), POSIX thread libraries (libpthread), standard math libraries (libm), and the name service cache daemon (nscd) used by multiple programs on the system. Without these libraries, the Linux system cannot function correctly. A stack-based buffer overflow was found in the way the libresolv library performed dual A/AAAA DNS queries. A remote attacker could create a specially crafted DNS response which could cause libresolv to crash or, potentially, execute code with the permissions of the user running the library. Note: this issue is only exposed when libresolv is called from the nss_dns NSS service module. (CVE-2015-7547) It was discovered that the calloc implementation in glibc could return memory areas which contain non-zero bytes. This could result in unexpected application behavior such as hangs or crashes. (CVE-2015-5229) The CVE-2015-7547 issue was discovered by the Google Security Team and Red Hat. Red Hat would like to thank Jeff Layton for reporting the CVE-2015-5229 issue. This update also fixes the following bugs : * The existing implementation of the last seen 2020-06-01 modified 2020-06-02 plugin id 88785 published 2016-02-17 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/88785 title RHEL 7 : glibc (RHSA-2016:0176) NASL family Fedora Local Security Checks NASL id FEDORA_2016-0F9E9A34CE.NASL description This updates addresses a critical security vulnerability in the DNS resolver related to `AF_UNSPEC` queries with `getaddrinfo` (CVE-2015-7547). In addition, a bug that causes Hesiod lookups to fail with a crash is fixed. Note that Tenable Network Security has extracted the preceding description block directly from the Fedora security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-05 modified 2016-03-04 plugin id 89476 published 2016-03-04 reporter This script is Copyright (C) 2016-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/89476 title Fedora 23 : glibc-2.22-9.fc23 (2016-0f9e9a34ce) NASL family Huawei Local Security Checks NASL id EULEROS_SA-2019-1551.NASL description According to the versions of the glibc packages installed, the EulerOS Virtualization installation on the remote host is affected by the following vulnerabilities : - stdlib/canonicalize.c in the GNU C Library (aka glibc or libc6) 2.27 and earlier, when processing very long pathname arguments to the realpath function, could encounter an integer overflow on 32-bit architectures, leading to a stack-based buffer overflow and, potentially, arbitrary code execution.(CVE-2018-11236) - An integer overflow vulnerability was found in hcreate() and hcreate_r() functions which could result in an out-of-bounds memory access. This could lead to application crash or, potentially, arbitrary code execution.(CVE-2015-8778) - A stack-based buffer overflow was found in the way the libresolv library performed dual A/AAAA DNS queries. A remote attacker could create a specially crafted DNS response which could cause libresolv to crash or, potentially, execute code with the permissions of the user running the library. Note: this issue is only exposed when libresolv is called from the nss_dns NSS service module.(CVE-2015-7547) - A flaw was found in the regular expression matching routines that process multibyte character input. If an application utilized the glibc regular expression matching mechanism, an attacker could provide specially-crafted input that, when processed, would cause the application to crash.(CVE-2013-0242) - A flaw was found in the way memory was being allocated on the stack for user space binaries. If heap (or different memory region) and stack memory regions were adjacent to each other, an attacker could use this flaw to jump over the stack guard gap, cause controlled memory corruption on process stack or the adjacent memory region, and thus increase their privileges on the system. This is glibc-side mitigation which blocks processing of LD_LIBRARY_PATH for programs running in secure-execution mode and reduces the number of allocations performed by the processing of LD_AUDIT, LD_PRELOAD, and LD_HWCAP_MASK, making successful exploitation of this issue more difficult.(CVE-2017-1000366) - The DNS stub resolver in the GNU C Library (aka glibc or libc6) before version 2.26, when EDNS support is enabled, will solicit large UDP responses from name servers, potentially simplifying off-path DNS spoofing attacks due to IP fragmentation.(CVE-2017-12132) - It was found that the files back end of Name Service Switch (NSS) did not isolate iteration over an entire database from key-based look-up API calls. An application performing look-ups on a database while iterating over it could enter an infinite loop, leading to a denial of service.(CVE-2014-8121) - Stack-based buffer overflow in the getaddrinfo function in sysdeps/posix/getaddrinfo.c in the GNU C Library (aka glibc or libc6) allows remote attackers to cause a denial of service (crash) via vectors involving hostent conversion. NOTE: this vulnerability exists because of an incomplete fix for CVE-2013-4458.(CVE-2016-3706) - In glibc 2.26 and earlier there is confusion in the usage of getcwd() by realpath() which can be used to write before the destination buffer leading to a buffer underflow and potential code execution.(CVE-2018-1000001) - Stack-based buffer overflow in string/strcoll_l.c in the GNU C Library (aka glibc or libc6) 2.17 and earlier allows context-dependent attackers to cause a denial of service (crash) or possibly execute arbitrary code via a long string that triggers a malloc failure and use of the alloca function.(CVE-2012-4424) - It was found that the dynamic loader did not sanitize the LD_POINTER_GUARD environment variable. An attacker could use this flaw to bypass the pointer guarding protection on set-user-ID or set-group-ID programs to execute arbitrary code with the permissions of the user running the application.(CVE-2015-8777) - The glob function in glob.c in the GNU C Library (aka glibc or libc6) before 2.27 contains a buffer overflow during unescaping of user names with the ~ operator.(CVE-2017-15804) - res_query in libresolv in glibc before 2.25 allows remote attackers to cause a denial of service (NULL pointer dereference and process crash).(CVE-2015-5180) - pt_chown in GNU C Library (aka glibc or libc6) before 2.18 does not properly check permissions for tty files, which allows local users to change the permission on the files and obtain access to arbitrary pseudo-terminals by leveraging a FUSE file system.(CVE-2013-2207) - A stack overflow flaw was found in glibc last seen 2020-03-17 modified 2019-05-14 plugin id 125004 published 2019-05-14 reporter This script is Copyright (C) 2019-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/125004 title EulerOS Virtualization 3.0.1.0 : glibc (EulerOS-SA-2019-1551)
Packetstorm
data source https://packetstormsecurity.com/files/download/138601/glibcgetaddrinfo-overflow.txt id PACKETSTORM:138601 last seen 2016-12-05 published 2016-09-06 reporter jang kyoungchip source https://packetstormsecurity.com/files/138601/glibc-getaddrinfo-Stack-Buffer-Overflow.html title glibc getaddrinfo Stack Buffer Overflow data source https://packetstormsecurity.com/files/download/154361/SA-20190904-0.txt id PACKETSTORM:154361 last seen 2019-09-05 published 2019-09-04 reporter T. Weber source https://packetstormsecurity.com/files/154361/Cisco-Device-Hardcoded-Credentials-GNU-glibc-BusyBox.html title Cisco Device Hardcoded Credentials / GNU glibc / BusyBox
Redhat
| advisories |
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| rpms |
|
Seebug
| bulletinFamily | exploit |
| description | ### 1. 漏洞概要 Glibc是GNU发布的LIBC库的C运行库,Glibc是Linux系统中最底层的API,基本其它任何运行库都会依赖于Glibc。Glibc除了封装Linux操作系统所提供的系统服务外,还提供了其它的必要服务的实现。由于 Glibc 几乎包含所有的 UNIX 通行的标准,可以说是操作系统重要支撑库。  Glibc中的 DNS 解析器中存在基于栈的缓冲区溢出漏洞,当在程序中调用`Getaddrinfo`函数时,攻击者自定义域名或是通过中间人攻击利用该漏洞控制用户系统。比如攻击者向用户发送带有指向恶意域名的链接的邮件,一旦用户点击该链接,攻击者构造合法的DNS请求时、以过大的DNS数据回应便会形成堆栈缓存区溢出并执行远程代码,达到完全控制用户操作系统。 > 该漏洞影响Glibc 2.9以后的所有版本,虽然可以进行远程执行攻击,攻击者还需要解决绕过ASLR系统安全机制。 ### 2. 漏洞复现 Google提供的POC由两部分组成: * 执行`CVE-2015-7547-POC.py`作为一个伪造的DNS服务器,会向DNS客户端发送构造的验证数据,包含超长字符串。 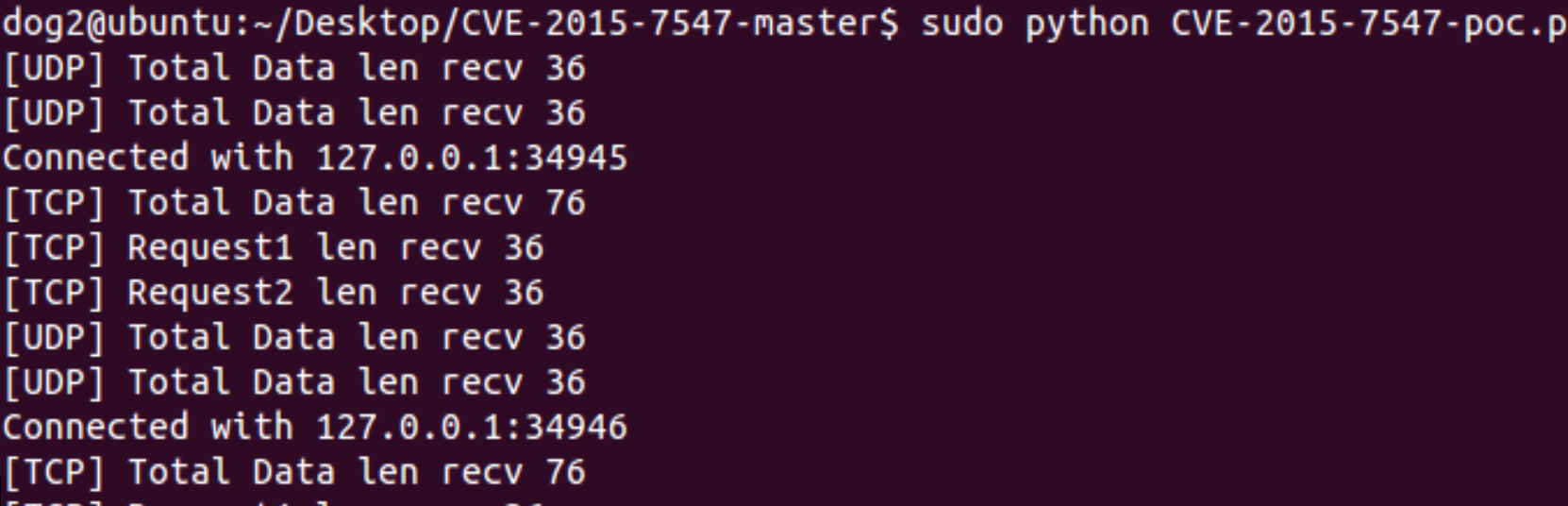 * 执行编译好的`CVE-2015-7547-CLIENT.c`作为客户端,向此DNS服务器进行查询,会在收到数据后导致程序崩溃。实测其它调用Glibc的程序也会因查询域名导致崩溃。 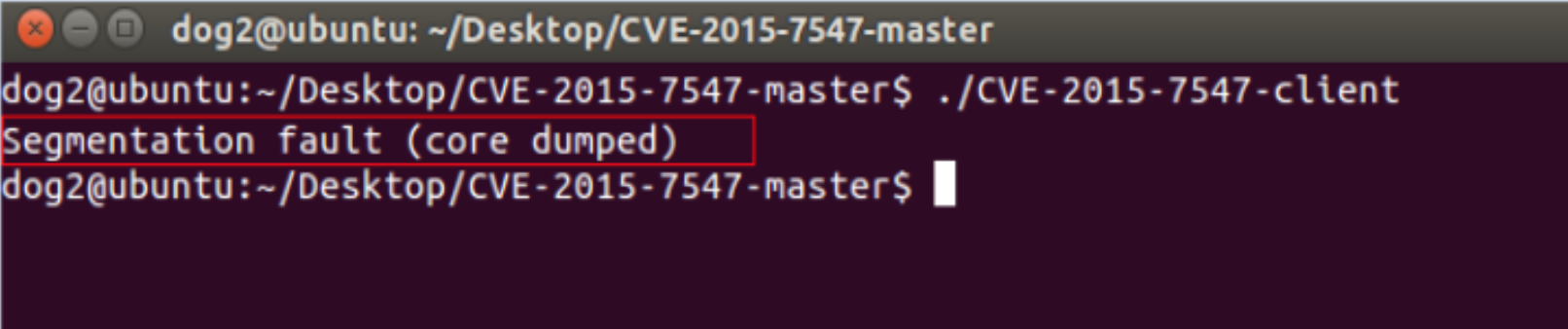 实测其它调用Glibc的程序也会因查询域名导致崩溃。伪造DNS服务器发出的POC数据,在TCP DNS数据中包含了大量字符“B”,如下 : 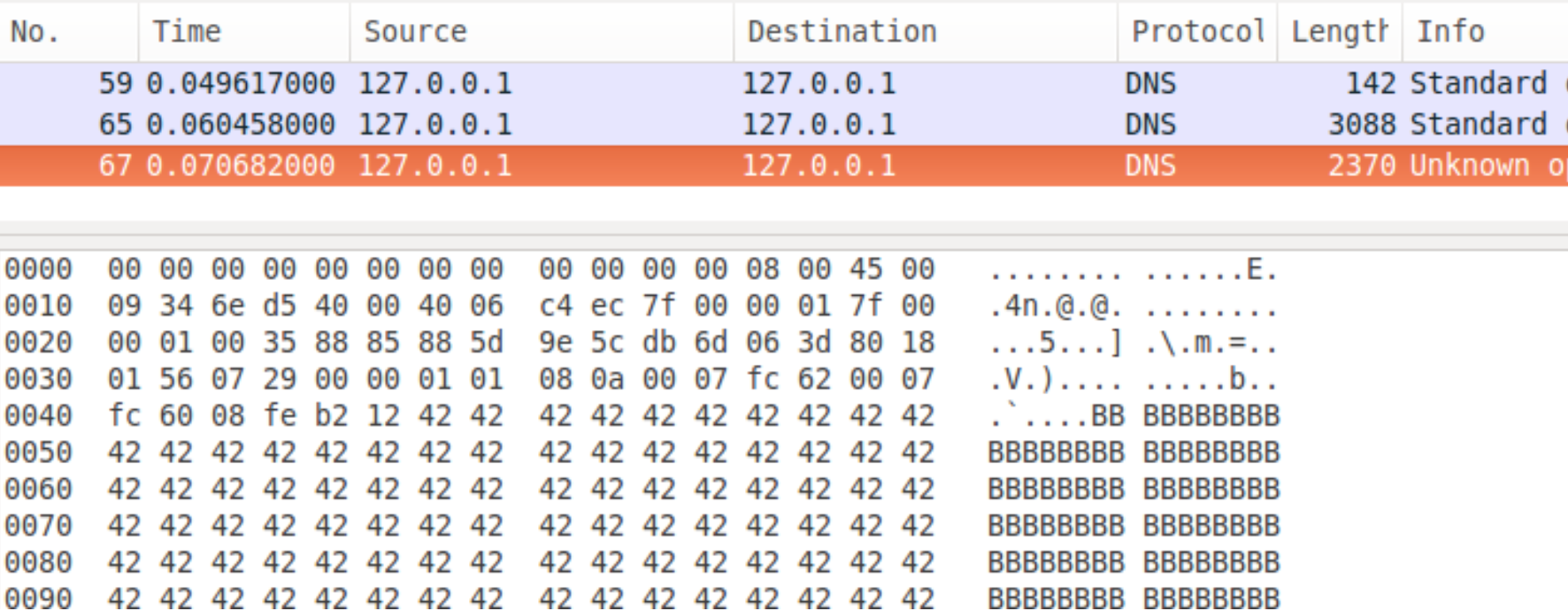 使用IDA远程调试 Debian 系统上的CVE-2015-7547-CLIENT,在调用Glibc的 `Getaddrinfo` 函数时出现崩溃,崩溃现场的状态如下:  由于产生溢出覆盖,`EDX`寄存器的值被控制为`0x42424242`,处在未使用的地址段,导致在对`[EDX+3]`进行寻址访问时造成异常。此时函数调用栈如下: 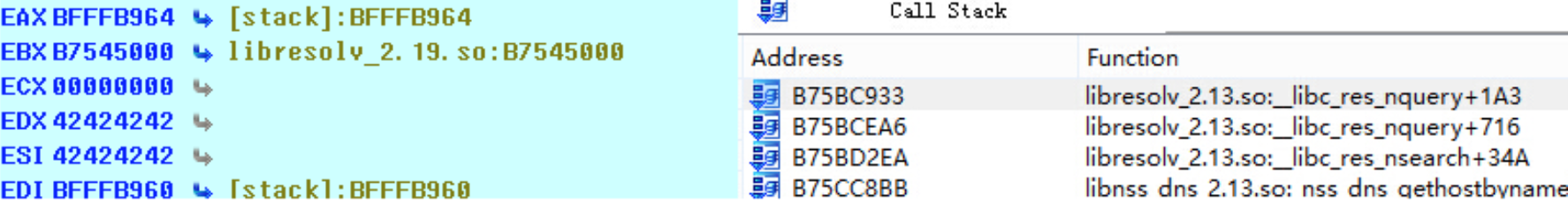 栈空间中被覆盖的数据如下:  ### 3.漏洞原因和利用 Glibc中导致此漏洞的函数调用顺序如下: ``` getaddrinfo (getaddrinfo.c) -> _nss_dns_gethostbyname4_r (dns-host.c) -> __libc_res_nsearch (res_query.c) -> __libc_res_nquery (res_query.c) -> __libc_res_nsend (res_send.c) -> send_vc (res_send.c) ``` 存在溢出漏洞的缓冲区是在_nss_dns_gethostbyname4_r函数中申请的。 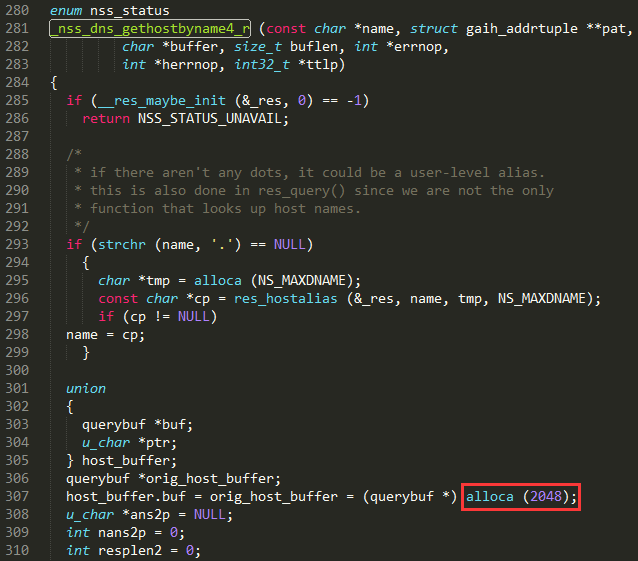 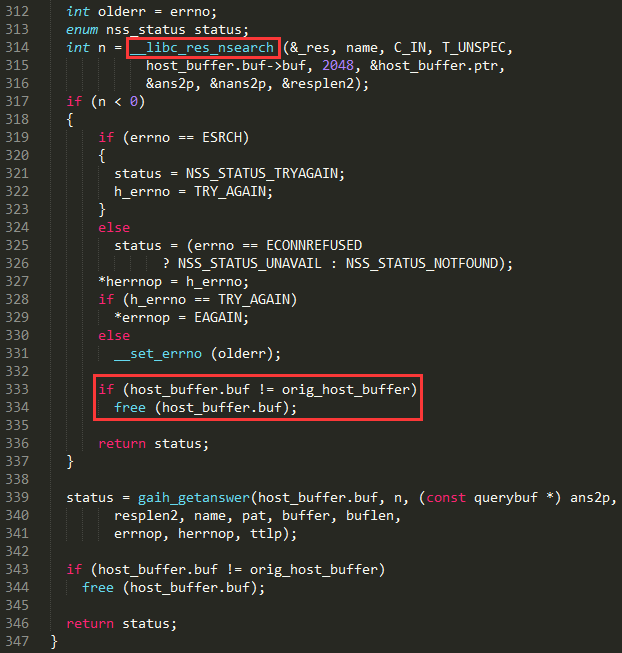 可以看到在_nss_dns_gethostbyname4_r函数中,使用alloca函数申请了2048字节的内存空间。alloca函数的功能是动态开辟栈地址空间,但如果参数是个固定大小的值,汇编代码就生成为把ESP减去固定值。调试分析栈的布局可以发现,host_buffer等局部变量是处在栈的高地址,alloca分配的内存是处在栈的低地址,这2048字节被溢出之后会覆盖掉host_buffer等变量。 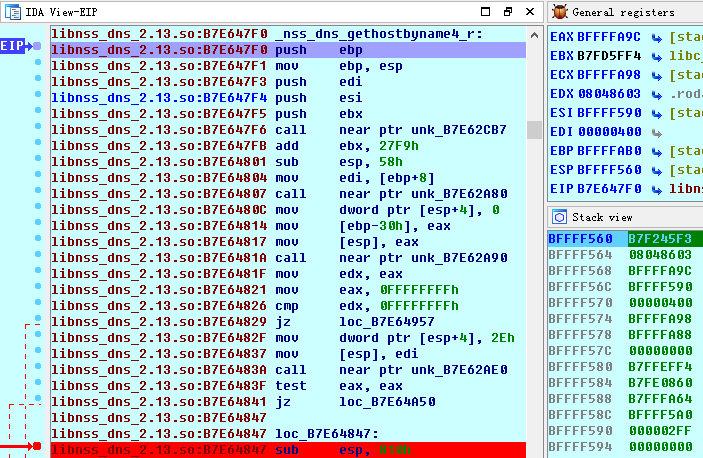 从以上两图可以看出,进入_nss_dns_gethostbyname4_r函数时,返回地址所在栈中的位置是0xBFFFF560。而当完成溢出覆盖导致访问异常时,此返回地址处的值已经被改写为0x42424242。 _nss_dns_gethostbyname4_r函数中调用了__libc_res_nsearch函数进行实际域名查询,把局部变量host_buffer的栈地址作为参数传递进去,用于保存DNS服务器数据的实际存储地址。最终会调用到send_vc函数,在接收大于2048字节的数据之前,本应该在判断缓冲区大小不够时去分配更大的堆内存,但由于存在一段不太成熟的测试代码结果造成了逻辑错误,使得判断缓冲区过小的条件永远不成立,这样就不会去分配大内存,导致数据保存到alloca分配的栈内存中,造成缓冲区溢出。在最新发布的glibc 2.23版补丁中,这段不成熟的代码已被删掉,解决了此漏洞。 POC导致程序崩溃的原因,是由于出现缓冲区溢出后,在__libc_res_nquery函数中会访问host_buffer指针所指向的地址,但此值已经被覆盖为0x42424242,是不可访问的地址,需要把这个值覆盖为一个可访问地址。 为了实现漏洞利用,要覆盖_nss_dns_gethostbyname4_r函数的返回地址。但是在此函数返回之前,还要进行一次free的操作。会判断host_buffer指针是否还是alloca分配的栈地址,如果被改变了,就说明又重新分配了堆内存,需要进行内存释放。但如果此变量被溢出覆盖成其它值了,就会导致释放这个非堆内存地址时,出现程序异常,不能继续加载返回地址。所以解决的办法是,在溢出覆盖后要么不改变这个指针的栈地址值,要么修改为一个有效的堆块起始地址。Glibc模块在函数代码中没有进行栈溢出检查,之后即可在函数返回时控制程序流程。 但是在开启地址随机化的情况下,如果没有办法泄露内存地址布局,单独靠这一漏洞是无法成功利用的。 ### 4. 漏洞分析(该部分内容来自用户k0sh1) 在回溯过程中,我们需要着重观察的是,究竟是何时栈中被畸形字符串覆盖,又是在何处,导致畸形字符串的读取。 首先我们就从离崩溃现场已知最远端入手,进行分析。根据bt回溯的信息,我们可以看到nss_dns_gethostbyname4_r是nss_dns/dns-host.c中的函数,这个.c文件对应的动态链接库是libnss_dns.so.2,那么我们需要在加载动态链接库后对这个函数下断点,我们使用gdb中的catch load libnss_dns.so.2对动态链接库加载进行跟踪。 ``` gdb-peda$ catch load libnss_dns.so.2 Catchpoint 1 (load) gdb-peda$ run Starting program: /root/Desktop/CVE-2015-7547-master/CVE-2015-7547-master/gclient [----------------------------------registers-----------------------------------] EAX: 0xbfffe98c --> 0xbfffeb50 ("libnss_dns.so.2") EBX: 0xb7fff000 --> 0x22f0c ECX: 0x4 EDX: 0x9 ('\t') ESI: 0x0 EDI: 0x4 EBP: 0xbfffe868 --> 0xbfffe9c8 --> 0xbfffeb88 --> 0xbfffebb8 --> 0xbffff0e8 --> 0xbffff218 --> 0xbffff268 --> 0x0 ESP: 0xbfffe800 --> 0x804bff0 --> 0xb7e04000 --> 0x464c457f EIP: 0xb7fef15a (<dl_open_worker+970>: nop) EFLAGS: 0x202 (carry parity adjust zero sign trap INTERRUPT direction overflow) [-------------------------------------code-------------------------------------] 0xb7fef153 <dl_open_worker+963>: test eax,eax 0xb7fef155 <dl_open_worker+965>: je 0xb7fef15b <dl_open_worker+971> 0xb7fef157 <dl_open_worker+967>: mov eax,DWORD PTR [ebp+0x8] => 0xb7fef15a <dl_open_worker+970>: nop 0xb7fef15b <dl_open_worker+971>: mov eax,DWORD PTR [ebp+0x8] 0xb7fef15e <dl_open_worker+974>: sub esp,0xc 0xb7fef161 <dl_open_worker+977>: mov ecx,DWORD PTR [eax+0x1c] 0xb7fef164 <dl_open_worker+980>: mov edx,DWORD PTR [eax+0x18] [------------------------------------stack-------------------------------------] [------------------------------------------------------------------------------] Legend: code, data, rodata, value Catchpoint 1 Inferior loaded /lib/i386-linux-gnu/libnss_dns.so.2 /lib/i386-linux-gnu/libresolv.so.2 0xb7fef15a in dl_open_worker (a=0xbfffe98c) at dl-open.c:572 572 dl-open.c: No such file or directory. ``` 程序中断后,说明动态链接库已经被加载,这时,我们就可以给_nss_dns_gethostbyname4_r下断点了。 ``` gdb-peda$ delete gdb-peda$ b _nss_dns_gethostbyname4_r Breakpoint 2 at 0xb7e064d0: file nss_dns/dns-host.c, line 284. gdb-peda$ run Starting program: /root/Desktop/CVE-2015-7547-master/CVE-2015-7547-master/gclient [----------------------------------registers-----------------------------------] EAX: 0xbffff0c4 --> 0x0 EBX: 0xb7fd3000 --> 0x19cd64 ECX: 0xbfffeb27 --> 0x0 EDX: 0xb7e064d0 (<_nss_dns_gethostbyname4_r>: push ebp) ESI: 0xb7e064d0 (<_nss_dns_gethostbyname4_r>: push ebp) EDI: 0x420 EBP: 0xbffff0e8 --> 0xbffff218 --> 0xbffff268 --> 0x0 ESP: 0xbfffebac --> 0xb7efddbc (<gaih_inet+3495>: add esp,0x20) EIP: 0xb7e064d0 (<_nss_dns_gethostbyname4_r>: push ebp) EFLAGS: 0x286 (carry PARITY adjust zero SIGN trap INTERRUPT direction overflow) [-------------------------------------code-------------------------------------] 0xb7e064c8 <_nss_dns_gethostbyname_r+136>: pop ebx 0xb7e064c9 <_nss_dns_gethostbyname_r+137>: ret 0xb7e064ca: lea esi,[esi+0x0] => 0xb7e064d0 <_nss_dns_gethostbyname4_r>: push ebp 0xb7e064d1 <_nss_dns_gethostbyname4_r+1>: mov ebp,esp 0xb7e064d3 <_nss_dns_gethostbyname4_r+3>: push edi 0xb7e064d4 <_nss_dns_gethostbyname4_r+4>: push esi 0xb7e064d5 <_nss_dns_gethostbyname4_r+5>: push ebx [------------------------------------stack-------------------------------------] [------------------------------------------------------------------------------] Legend: code, data, rodata, value Breakpoint 2, _nss_dns_gethostbyname4_r (name=0x8048653 "foo.bar.google.com", pat=0xbffff0c8, buffer=0xbfffebd0 "\377\002", buflen=0x420, errnop=0xbffff0c4, herrnop=0xbffff0b0, ttlp=0x0) at nss_dns/dns-host.c:284 284 nss_dns/dns-host.c: No such file or directory. ``` 顺利在入口处断了下来,这时我们继续按c,进行continue操作发现直接到达漏洞现场,这个过程就不展示了,可以在跟踪调试时进行,这说明进入此函数是漏洞触发前唯一一次调用到_nss_dns_gethostbyname4_r函数的位置,我们通过bt来观察一下。 ``` gdb-peda$ bt #0 _nss_dns_gethostbyname4_r (name=0x8048653 "foo.bar.google.com", pat=0xbffff0c8, buffer=0xbfffebd0 "\377\002", buflen=0x420, errnop=0xbffff0c4, herrnop=0xbffff0b0, ttlp=0x0) at nss_dns/dns-host.c:284 #1 0xb7efddbc in gaih_inet (name=<optimized out>, name@entry=0x8048653 "foo.bar.google.com", service=<optimized out>, req=0xbffff23c, pai=0xbffff1fc, naddrs=0xbffff1c4) at ../sysdeps/posix/getaddrinfo.c:862 #2 0xb7f0023e in __GI_getaddrinfo (name=<optimized out>, service=0x8048650 "22", hints=0xbffff23c, pai=0xbffff234) at ../sysdeps/posix/getaddrinfo.c:2417 #3 0x08048588 in main () #4 0xb7e4d5cb in __libc_start_main (main=0x804853b <main>, argc=0x1, argv=0xbffff314, init=0x80485d0 <__libc_csu_init>, fini=0x8048630 <__libc_csu_fini>, rtld_fini=0xb7feb210 <_dl_fini>, stack_end=0xbffff30c) at libc-start.c:289 #5 0x08048461 in _start () ``` 整个过程调用非常清晰,#3位置在主函数里,紧接着#2调用了我们的漏洞函数getaddrinfo,调用后某个位置我们调用了nss_dns_gethostbyname4_r函数,在到达此函数时,我们在poc端进行观察,发现poc并没有发送畸形字符串,在此函数入口,我们通过参数观察,也没有看到有畸形字符串加载进来。 这一点说明在getaddrinfo函数到nss_dns_gethostbyname之间没有涉及到畸形字符串获取,也就是说和漏洞无关,那么我们可以跳过这段调试,直接从_nss_gethostbyname4_r入手继续寻找。 接下来,我们通过最开始的bt堆栈调用,对后面几个函数进行分析,如果想在之后的调用位置下断点,需要继续对libresolv.so.2的加载进行跟踪,那么接下来,为了能够快速定位,我们就利用最开始回溯堆栈调用给予的信息,对#0,#1,#2三处下断点,首先利用catch load libresolv.so.2对动态链接库下断点,中断后,我们首先来到第一个#2位置。 ``` gdb-peda$ b __libc_res_nsearch Breakpoint 4 at 0xb7df5240: file res_query.c, line 342. gdb-peda$ run Starting program: /opt/gclient [----------------------------------registers-----------------------------------] EAX: 0xffffffb8 EBX: 0xb7e0d000 --> 0x5ec8 ECX: 0xbfffe200 --> 0x0 EDX: 0x0 ESI: 0xb7e35940 (0xb7e35940) EDI: 0x8048653 ("foo.bar.google.com") EBP: 0xbfffea68 --> 0xbfffefa8 --> 0xbffff0d8 --> 0xbffff128 --> 0x0 ESP: 0xbfffe1cc --> 0xb7e09590 (<_nss_dns_gethostbyname4_r+192>: add esp,0x30) EIP: 0xb7df5240 (<__GI___libc_res_nsearch>: push ebp) EFLAGS: 0x292 (carry parity ADJUST zero SIGN trap INTERRUPT direction overflow) [-------------------------------------code-------------------------------------] 0xb7df5238 <__GI___res_hostalias+440>: ret 0xb7df5239 <__GI___res_hostalias+441>: call 0xb7dfca50 <__stack_chk_fail_local> 0xb7df523e: xchg ax,ax => 0xb7df5240 <__GI___libc_res_nsearch>: push ebp 0xb7df5241 <__GI___libc_res_nsearch+1>: push edi 0xb7df5242 <__GI___libc_res_nsearch+2>: push esi 0xb7df5243 <__GI___libc_res_nsearch+3>: push ebx 0xb7df5244 <__GI___libc_res_nsearch+4>: call 0xb7df06e0 <__x86.get_pc_thunk.bx> [------------------------------------------------------------------------------] Legend: code, data, rodata, value Breakpoint 4, __GI___libc_res_nsearch (statp=0xb7fd6340 <_res@GLIBC_2.0>, name=0x8048653 "foo.bar.google.com", class=0x1, type=0xf371, answer=0xbfffe200 "", anslen=0x800, answerp=0xbfffea2c, answerp2=0xbfffea30, nanswerp2=0xbfffea34, resplen2=0xbfffea38, answerp2_malloced=0xbfffea3c) at res_query.c:342 342 res_query.c: No such file or directory. ``` 可以看到,此函数调用时,还是我们程序对应的地址内容,那么接下来,到达#1位置。 ``` gdb-peda$ b __libc_res_nquerydomain Breakpoint 5 at 0xb7df4eb0: file res_query.c, line 563. gdb-peda$ run Starting program: /opt/gclient [----------------------------------registers-----------------------------------] EAX: 0xb7fd6340 --> 0x5 EBX: 0xb7e04000 --> 0x14ed4 ECX: 0xbfffea2c --> 0xbfffe200 --> 0x0 EDX: 0x8048653 ("foo.bar.google.com") ESI: 0x3 EDI: 0xb7fd6340 --> 0x5 EBP: 0xbfffea30 --> 0x0 ESP: 0xbfffdd2c --> 0xb7df54cb (<__GI___libc_res_nsearch+651>: add esp,0x30) EIP: 0xb7df4eb0 (<__libc_res_nquerydomain>: push ebp) EFLAGS: 0x292 (carry parity ADJUST zero SIGN trap INTERRUPT direction overflow) [-------------------------------------code-------------------------------------] 0xb7df4ea4 <__GI___libc_res_nquery+1716>: push eax 0xb7df4ea5 <__GI___libc_res_nquery+1717>: call 0xb7df0680 <__assert_fail@plt> 0xb7df4eaa: lea esi,[esi+0x0] => 0xb7df4eb0 <__libc_res_nquerydomain>: push ebp 0xb7df4eb1 <__libc_res_nquerydomain+1>: push edi 0xb7df4eb2 <__libc_res_nquerydomain+2>: mov edi,eax 0xb7df4eb4 <__libc_res_nquerydomain+4>: push esi 0xb7df4eb5 <__libc_res_nquerydomain+5>: push ebx [------------------------------------------------------------------------------] Legend: code, data, rodata, value Breakpoint 5, __libc_res_nquerydomain ( statp=statp@entry=0xb7fd6340 <_res@GLIBC_2.0>, name=name@entry=0x8048653 "foo.bar.google.com", domain=0x0, class=0x1, type=0xf371, answer=0xbfffe200 "", anslen=0x800, answerp=0xbfffea2c, answerp2=0xbfffea30, nanswerp2=0xbfffea34, resplen2=0xbfffea38, answerp2_malloced=0xbfffea3c) at res_query.c:563 563 res_query.c: No such file or directory. ``` 可以看到,此时还是正常,接下来来到#0位置。 ``` gdb-peda$ b __libc_res_nquery Breakpoint 6 at 0xb7df47f0: file res_query.c, line 124. gdb-peda$ run Starting program: /opt/gclient [----------------------------------registers-----------------------------------] EAX: 0x11 EBX: 0xb7e04000 --> 0x14ed4 ECX: 0x13 EDX: 0x5 ESI: 0x8048653 ("foo.bar.google.com") EDI: 0xb7fd6340 --> 0x5 EBP: 0x0 ESP: 0xbfffd8ac --> 0xb7df4fa1 (<__libc_res_nquerydomain+241>: add esp,0x30) EIP: 0xb7df47f0 (<__GI___libc_res_nquery>: push ebp) EFLAGS: 0x292 (carry parity ADJUST zero SIGN trap INTERRUPT direction overflow) [-------------------------------------code-------------------------------------] 0xb7df47eb: xchg ax,ax 0xb7df47ed: xchg ax,ax 0xb7df47ef: nop => 0xb7df47f0 <__GI___libc_res_nquery>: push ebp 0xb7df47f1 <__GI___libc_res_nquery+1>: mov edx,0x220 0xb7df47f6 <__GI___libc_res_nquery+6>: mov ebp,esp 0xb7df47f8 <__GI___libc_res_nquery+8>: push edi 0xb7df47f9 <__GI___libc_res_nquery+9>: push esi [------------------------------------------------------------------------------] Legend: code, data, rodata, value Breakpoint 6, __GI___libc_res_nquery (statp=0xb7fd6340 <_res@GLIBC_2.0>, name=0x8048653 "foo.bar.google.com", class=0x1, type=0xf371, answer=0xbfffe200 "", anslen=0x800, answerp=0xbfffea2c, answerp2=0xbfffea30, nanswerp2=0xbfffea34, resplen2=0xbfffea38, answerp2_malloced=0xbfffea3c) at res_query.c:124 124 res_query.c: No such file or directory. ``` 可以看到此时依然正常,这说明漏洞位置就出现在libc_res_nquery函数中,那么我们接下来,在对此函数进行跟踪分析之前,我们来通过源码来总结一下之前的调用过程。 ``` _nss_dns_gethostbyname4_r (const char *name, struct gaih_addrtuple **pat, char *buffer, size_t buflen, int *errnop, int *herrnop, int32_t *ttlp) { …… //省略过程 …… host_buffer.buf = orig_host_buffer = (querybuf *) alloca (2048);//开辟2048空间,重要! u_char *ans2p = NULL; int nans2p = 0; int resplen2 = 0; int ans2p_malloced = 0; int olderr = errno; enum nss_status status; //调用__libc_res_nsearch int n = __libc_res_nsearch (&_res, name, C_IN, T_UNSPEC, host_buffer.buf->buf, 2048, &host_buffer.ptr, &ans2p, &nans2p, &resplen2, &ans2p_malloced); ``` 可以看到这里为host_buffer作为querybuf开辟了2048字节的缓冲区,这也是后面漏洞在res_nquery形成的关键点。我将几次函数调用写在一起,省略了部分过程(毕竟不重要),这里我们还观察一下libc_res_nsearch调用的第五个参数,也就是2048空间对应的地址位置,接下来。 ``` int __libc_res_nsearch(res_state statp, const char *name, /* domain name */ int class, int type, /* class and type of query */ u_char *answer, /* buffer to put answer */ int anslen, /* size of answer */ u_char **answerp, u_char **answerp2, int *nanswerp2, int *resplen2, int *answerp2_malloced) { …… 省略过程 …… //调用_libc_res_nquerydomain ret = __libc_res_nquerydomain(statp, name, NULL, class, type, answer, anslen, answerp, answerp2, nanswerp2, resplen2, answerp2_malloced); ``` 还记得刚才我们提到的第五个参数吗,就是现在的*answerp,紧接着继续调用到最后的处理函数。 ``` static int __libc_res_nquerydomain(res_state statp, const char *name, const char *domain, int class, int type, /* class and type of query */ u_char *answer, /* buffer to put answer */ int anslen, /* size of answer */ u_char **answerp, u_char **answerp2, int *nanswerp2, int *resplen2, int *answerp2_malloced) { …… 省略过程 …… //调用libc_res_nquery return (__libc_res_nquery(statp, longname, class, type, answer, anslen, answerp, answerp2, nanswerp2, resplen2, answerp2_malloced)); } ``` 还是answer变量值得关注,接下来的分析中会提到这一点,这个answer函数对应的位置就是已经分配的2048空间,而在函数进行read操作时,并没有对DNS返回的字符串畸形检查,而直接拷贝字符串了到数组空间了! 那么进入到res_nquery之后,我们需要对这个函数进行单步跟踪分析,因为一直到这个函数前,PoC端都没有反应,可见此时还是在本机进行了一些读取操作,后面查询操作时,才涉及到和DNS交互。单步跟踪,在某函数位置发现了问题。 ``` gdb-peda$ run Starting program: /root/Desktop/CVE-2015-7547-master/CVE-2015-7547-master/gclient [----------------------------------registers-----------------------------------] EAX: 0x804c728 --> 0x35000002 EBX: 0xb7e01000 --> 0x14ed4 ECX: 0x0 EDX: 0xb7fd6340 --> 0x5 ESI: 0x0 EDI: 0xb7fd6514 --> 0xffffffff EBP: 0xb7fd6340 --> 0x5 ESP: 0xbfffd5d0 --> 0xbfffd764 --> 0x1006d EIP: 0xb7df3702 (<__libc_res_nsend+354>: mov eax,DWORD PTR [esp+0x158]) EFLAGS: 0x246 (carry PARITY adjust ZERO sign trap INTERRUPT direction overflow) [-------------------------------------code-------------------------------------] 0xb7df36f6 <__libc_res_nsend+342>: mov esi,DWORD PTR [esp+0x1c] 0xb7df36fa <__libc_res_nsend+346>: test esi,esi 0xb7df36fc <__libc_res_nsend+348>: jne 0xb7df4145 <__libc_res_nsend+2981> => 0xb7df3702 <__libc_res_nsend+354>: mov eax,DWORD PTR [esp+0x158] 0xb7df3709 <__libc_res_nsend+361>: mov esi,DWORD PTR [ebp+0x0] 0xb7df370c <__libc_res_nsend+364>: mov DWORD PTR [esp+0x9c],0x0 0xb7df3717 <__libc_res_nsend+375>: mov DWORD PTR [esp+0x74],eax 0xb7df371b <__libc_res_nsend+379>: mov eax,DWORD PTR [esp+0x4] [------------------------------------------------------------------------------] Legend: code, data, rodata, value Breakpoint 2, __libc_res_nsend (statp=0xb7fd6340 <_res@GLIBC_2.0>, buf=0xbfffd740 "\362 \001", buflen=0x24, buf2=0xbfffd764 "m", buflen2=0x24, ans=0xbfffe340 "", anssiz=0x800, ansp=0xbfffeb6c, ansp2=0xbfffeb70, nansp2=0xbfffeb74, resplen2=0xbfffeb78, ansp2_malloced=0xbfffeb7c) at res_send.c:564 564 res_send.c: No such file or directory. ``` 我们进入到一处res_nsend函数,在进入前一切还正常,我们直接通过finish来执行到函数返回位置。 ``` gdb-peda$ finish Run till exit from #0 __libc_res_nsend (statp=0xb7fd6340 <_res@GLIBC_2.0>, buf=0xbfffd740 "\362 \001", buflen=0x24, buf2=0xbfffd764 "m", buflen2=0x24, ans=0xbfffe340 "", anssiz=0x800, ansp=0xbfffeb6c, ansp2=0xbfffeb70, nansp2=0xbfffeb74, resplen2=0xbfffeb78, ansp2_malloced=0xbfffeb7c) at res_send.c:564 [----------------------------------registers-----------------------------------] EAX: 0xbcc EBX: 0xb7e01000 --> 0x14ed4 ECX: 0x1 EDX: 0xffffffff ESI: 0xb7fd6340 --> 0x5 EDI: 0xbfffe340 --> 0x4242006d ('m') EBP: 0xbfffd9e8 --> 0x0 ESP: 0xbfffd710 --> 0xb7fd6340 --> 0x5 EIP: 0xb7df191b (<__GI___libc_res_nquery+299>: mov DWORD PTR [ebp-0x30],eax) EFLAGS: 0x286 (carry PARITY adjust zero SIGN trap INTERRUPT direction overflow) [-------------------------------------code-------------------------------------] 0xb7df1912 <__GI___libc_res_nquery+290>: push DWORD PTR [ebp-0x30] 0xb7df1915 <__GI___libc_res_nquery+293>: push esi 0xb7df1916 <__GI___libc_res_nquery+294>: call 0xb7df35a0 <__libc_res_nsend> => 0xb7df191b <__GI___libc_res_nquery+299>: mov DWORD PTR [ebp-0x30],eax 0xb7df191e <__GI___libc_res_nquery+302>: mov eax,DWORD PTR [ebp-0x40] 0xb7df1921 <__GI___libc_res_nquery+305>: add esp,0x30 0xb7df1924 <__GI___libc_res_nquery+308>: test eax,eax 0xb7df1926 <__GI___libc_res_nquery+310>: jne 0xb7df1b50 <__GI___libc_res_nquery+864> [------------------------------------stack-------------------------------------] 0000| 0xbfffd710 --> 0xb7fd6340 --> 0x5 0004| 0xbfffd714 --> 0xbfffd740 --> 0x120f2 0008| 0xbfffd718 --> 0x24 ('$') 0012| 0xbfffd71c --> 0xbfffd764 --> 0x1006d 0016| 0xbfffd720 --> 0x24 ('$') 0020| 0xbfffd724 --> 0xbfffe340 --> 0x4242006d ('m') 0024| 0xbfffd728 --> 0x10000 0028| 0xbfffd72c --> 0xbfffeb6c ('B' <repeats 200 times>...) [------------------------------------------------------------------------------] Legend: code, data, rodata, value 0xb7df191b in __GI___libc_res_nquery (statp=0xb7fd6340 <_res@GLIBC_2.0>, name=0x8048653 "foo.bar.google.com", class=0x1, type=0xf371, answer=0xbfffe340 "m", anslen=0x800, answerp=0xbfffeb6c, answerp2=0xbfffeb70, nanswerp2=0xbfffeb74, resplen2=0xbfffeb78, answerp2_malloced=0xbfffeb7c) at res_query.c:227 227 res_query.c: No such file or directory. ``` 在代码区,我们可以看到现在所处的位置是0xb7df191b的位置,而在这个位置上面的地址,执行了call __libc_res_nsend函数,当函数返回后,我们发现在栈中bfffeb6c的位置,出现了我们的畸形字符串B,而PoC端此时也执行了发送操作。我们来看一下bfffeb6c此时的值。 ``` 0xbfffeb9c: 0x42 0x42 0x42 0x42 0x42 0x42 0x42 0x42 0xbfffeba4: 0x42 0x42 0x42 0x42 0x42 0x42 0x42 0x42 0xbfffebac: 0x42 0x42 0x42 0x42 0x42 0x42 0x42 0x42 0xbfffebb4: 0x42 0x42 0x42 0x42 0x42 0x42 0x42 0x42 0xbfffebbc: 0x42 0x42 0x42 0x42 0x42 0x42 0x42 0x42 0xbfffebc4: 0x42 0x42 0x42 0x42 0x42 0x42 0x42 0x42 0xbfffebcc: 0x42 0x42 0x42 0x42 ``` 已经覆盖了大量的42424242,那么我们可以定位出现问题的地方在__libc_res_nsend中。在res_query.c中,我们可以看到res_nquery函数对res_nsend的调用。而且也只有这一处调用了res_nsend。 ``` int __libc_res_nquery(res_state statp, const char *name, /* domain name */ int class, int type, /* class and type of query */ u_char *answer, /* buffer to put answer */ int anslen, /* size of answer buffer */ u_char **answerp, /* if buffer needs to be enlarged */ u_char **answerp2, int *nanswerp2, int *resplen2, int *answerp2_malloced) { HEADER *hp = (HEADER *) answer; HEADER *hp2; int n, use_malloc = 0; u_int oflags = statp->_flags; …… 省略过程 …… assert (answerp == NULL || (void *) *answerp == (void *) answer); //漏洞触发函数 n = __libc_res_nsend(statp, query1, nquery1, query2, nquery2, answer, anslen, answerp, answerp2, nanswerp2, resplen2, answerp2_malloced); if (use_malloc) free (buf); ``` 接下来,我们要着重关注一下libc_res_nsend函数,首先我们跟踪调试时发现程序会进入一处if语句判断,进入send_vc和send_dg函数,在send_vc函数中发现了socket和connect连接语句,在连接语句执行结束时,poc端提示connect 127.0.0.1,也就是执行了连接操作。 ``` gdb-peda$ n [----------------------------------registers-----------------------------------] EAX: 0x3 EBX: 0xb7e01000 --> 0x14ed4 ECX: 0xbfffd2e0 --> 0x2 EDX: 0xb7e01000 --> 0x14ed4 ESI: 0xbfffeb78 --> 0x0 EDI: 0xb7fd6514 --> 0xffffffff EBP: 0xb7fd6340 --> 0x5 ESP: 0xbfffd2e0 --> 0x2 EIP: 0xb7df2b64 (<send_vc+244>: add esp,0x10) EFLAGS: 0x203 (CARRY parity adjust zero sign trap INTERRUPT direction overflow) [-------------------------------------code-------------------------------------] 0xb7df2b5b <send_vc+235>: movzx eax,WORD PTR [eax] 0xb7df2b5e <send_vc+238>: push eax 0xb7df2b5f <send_vc+239>: call 0xb7ded620 <socket@plt> => 0xb7df2b64 <send_vc+244>: add esp,0x10 0xb7df2b67 <send_vc+247>: test eax,eax 0xb7df2b69 <send_vc+249>: mov DWORD PTR [ebp+0x1c4],eax 0xb7df2b6f <send_vc+255>: js 0xb7df312a <send_vc+1722> 0xb7df2b75 <send_vc+261>: mov edi,DWORD PTR [esp+0x48] [------------------------------------stack-------------------------------------] 0000| 0xbfffd2e0 --> 0x2 0004| 0xbfffd2e4 --> 0x1 0008| 0xbfffd2e8 --> 0x0 0012| 0xbfffd2ec --> 0xb7e433e8 --> 0x72647800 ('') 0016| 0xbfffd2f0 --> 0xb7fd8900 --> 0xb7e36000 --> 0x464c457f 0020| 0xbfffd2f4 --> 0xbfffeb74 --> 0x0 0024| 0xbfffd2f8 --> 0xbfffeb6c --> 0x804c748 --> 0x8083ab32 0028| 0xbfffd2fc --> 0xbfffd728 --> 0x10000 [------------------------------------------------------------------------------] Legend: code, data, rodata, value 725 in res_send.c Breakpoint 2, send_vc (statp=0xb7fd6340 <_res@GLIBC_2.0>, buf=0xbfffd740 "B6\001", buflen=0x24, buf2=0xbfffd764 "\t\374\001", buflen2=0x24, ansp=0xbfffd65c, anssizp=0xbfffd728, terrno=0xbfffd668, ns=0x0, anscp=0xbfffeb6c, ansp2=0xbfffeb70, anssizp2=0xbfffeb74, resplen2=0xbfffeb78, ansp2_malloced=0xbfffeb7c) at res_send.c:669 669 res_send.c: No such file or directory. ``` 连接后,我们继续单步跟进,poc端收到了tcp的请求,同时,glibc接收到了畸形字符串,通过read函数读取,我们可以来观察一下读取前后的情况,在此之前,我们通过bt观察一下某个之前提到的重点变量,就是保存了2048缓冲区的重点变量。 ``` gdb-peda$ bt #0 send_vc (statp=0xb7fd6340 <_res@GLIBC_2.0>, buf=0xbfffd740 "\274\206\001", buflen=0x24, buf2=0xbfffd764 "\264\316\001", buflen2=0x24, ansp=0xbfffd65c, anssizp=0xbfffd728, terrno=0xbfffd668, ns=0x0, anscp=0xbfffeb6c, ansp2=0xbfffeb70, anssizp2=0xbfffeb74, resplen2=0xbfffeb78, ansp2_malloced=0xbfffeb7c) at res_send.c:669 #1 0xb7df3c4e in __libc_res_nsend (statp=0xb7fd6340 <_res@GLIBC_2.0>, buf=0xbfffd740 "\274\206\001", buflen=0x24, buf2=0xbfffd764 "\264\316\001", buflen2=0x24, ans=0xbfffe340 "", anssiz=0x10000, ansp=0xbfffeb6c, ansp2=0xbfffeb70, nansp2=0xbfffeb74, resplen2=0xbfffeb78, ansp2_malloced=0xbfffeb7c) at res_send.c:554 #2 0xb7df191b in __GI___libc_res_nquery (statp=0xb7fd6340 <_res@GLIBC_2.0>, name=0x8048653 "foo.bar.google.com", class=0x1, type=0xf371, answer=0xbfffe340 "", anslen=0x800, answerp=0xbfffeb6c, answerp2=0xbfffeb70, nanswerp2=0xbfffeb74, resplen2=0xbfffeb78, answerp2_malloced=0xbfffeb7c) at res_query.c:227 #3 0xb7df1fa1 in __libc_res_nquerydomain ( statp=statp@entry=0xb7fd6340 <_res@GLIBC_2.0>, name=name@entry=0x8048653 "foo.bar.google.com", domain=0x0, class=0x1, type=0xf371, answer=0xbfffe340 "", anslen=0x800, answerp=0xbfffeb6c, answerp2=0xbfffeb70, nanswerp2=0xbfffeb74, resplen2=0xbfffeb78, answerp2_malloced=0xbfffeb7c) at res_query.c:594 #4 0xb7df24cb in __GI___libc_res_nsearch (statp=0xb7fd6340 <_res@GLIBC_2.0>, name=0x8048653 "foo.bar.google.com", class=0x1, type=0xf371, answer=0xbfffe340 "", anslen=0x800, answerp=0xbfffeb6c, answerp2=0xbfffeb70, nanswerp2=0xbfffeb74, resplen2=0xbfffeb78, answerp2_malloced=0xbfffeb7c) at res_query.c:381 ``` 这里我们要好好分析一下,首先是#4处的answer,地址是0xbfffe340,之前我们提到过,这里时开辟的2048长度地址的缓冲区,后面的anslen=0x800也是长度,2048,接下来在#3中,answer地址没有变化继续传递,接下来在res_nquery中,依然没有变化,最后到达关键函数send_vc的时候,我们可以看到ansp=0xbfffd65c,这个地址非常有意思,首先在函数入口处,我们可以看一下这个地址的中存放的值。 ``` gdb-peda$ x/10x 0xbfffd65c 0xbfffd65c: 0xbfffe340 0xbfffd764 0xbfffd770 0x0000006e 0xbfffd66c: 0x000009e8 0x56cd507c 0x1d20b5f8 0x00000003 0xbfffd67c: 0x00010001 0xbfffd740 ``` 还是0xbfffe340,那么这个地址很有可能是地址指针的指针,也就是类似于**ansp这样的形式!接下来这个值是如何传递的呢,我们可以分析一下。请注意我单行的注释。 ``` static int send_vc(res_state statp, const u_char *buf, int buflen, const u_char *buf2, int buflen2, u_char **ansp, int *anssizp,//ansp是2048缓冲区对应地址 int *terrno, int ns, u_char **anscp, u_char **ansp2, int *anssizp2, int *resplen2, int *ansp2_malloced) { const HEADER *hp = (HEADER *) buf; const HEADER *hp2 = (HEADER *) buf2; u_char *ans = *ansp;//对应地址的传递 int orig_anssizp = *anssizp; // XXX REMOVE // int anssiz = *anssizp; HEADER *anhp = (HEADER *) ans; …… …… if (statp->_vcsock < 0 || (statp->_flags & RES_F_VC) == 0) { if (statp->_vcsock >= 0) __res_iclose(statp, false); //这里建立socket连接 statp->_vcsock = socket(nsap->sin6_family, SOCK_STREAM, 0); if (statp->_vcsock < 0) { *terrno = errno; Perror(statp, stderr, "socket(vc)", errno); return (-1); } __set_errno (0); //connect操作,客户端会提示connect 127.0.0.1 if (connect(statp->_vcsock, (struct sockaddr *)nsap, nsap->sin6_family == AF_INET ? sizeof (struct sockaddr_in) : sizeof (struct sockaddr_in6)) < 0) { *terrno = errno; Aerror(statp, stderr, "connect/vc", errno, (struct sockaddr *) nsap); __res_iclose(statp, false); return (0); } statp->_flags |= RES_F_VC; } /*发送部分,无关紧要 * Send length & message */ …… /*接收部分 * Receive length & response */ int recvresp1 = 0; int recvresp2 = buf2 == NULL; uint16_t rlen16; read_len: cp = (u_char *)&rlen16; len = sizeof(rlen16); while ((n = TEMP_FAILURE_RETRY (read(statp->_vcsock, cp, (int)len))) > 0) { cp += n; if ((len -= n) <= 0) break; } if (n <= 0) { *terrno = errno; Perror(statp, stderr, "read failed", errno); __res_iclose(statp, false); /* * A long running process might get its TCP * connection reset if the remote server was * restarted. Requery the server instead of * trying a new one. When there is only one * server, this means that a query might work * instead of failing. We only allow one reset * per query to prevent looping. */ if (*terrno == ECONNRESET && !connreset) { connreset = 1; goto same_ns; } return (0); } int rlen = ntohs (rlen16); int *thisanssizp; u_char **thisansp; int *thisresplenp; if ((recvresp1 | recvresp2) == 0 || buf2 == NULL) { ……//第一次收到,无关紧要,第二次收到将进入下面的else部分 } else { if (*anssizp != MAXPACKET) { …… } else { /* The first reply did not fit into the user-provided buffer. Maybe the second answer will. */ *anssizp2 = orig_anssizp; *ansp2 = *ansp; } thisanssizp = anssizp2; thisansp = ansp2; //此时ansp2会赋值给thisansp,而此时thisansp的值是ansp thisresplenp = resplen2; } …… //此时cp的地址是bfffe340,也就是2048字节缓冲区 cp = *thisansp; 接着read参数会读取这个接收到的参数,第二次接收到时,是长度为超长的字符串,而此时,没有对这个字符串长度进行任何判断! while (len != 0 && (n = read(statp->_vcsock, (char *)cp, (int)len)) > 0){ cp += n; len -= n; } ``` 看到这里,我们基本可以分析出来为什么PoC要发送两次,而在第二次中,加上了2300个'B',也就是说在第二次接收时,2048缓冲区对应的变量会赋值给即将接收字符串的缓冲区,而此时,没有对这个缓冲区要接收内容的长度进行处理,从而导致了超长串覆盖,函数返回后,某个地址被覆盖导致dns请求崩溃。 接下来我们可以看一下read前后,缓冲区的变化。 ``` gdb-peda$ n [----------------------------------registers-----------------------------------] EAX: 0x8fe EBX: 0xb7e01000 --> 0x14ed4 ECX: 0xbfffd65c --> 0xbfffe340 --> 0x0 EDX: 0x10000 ESI: 0xbfffe340 --> 0x0 EDI: 0xbfffeb70 --> 0xbfffe340 --> 0x0 EBP: 0xb7fd6340 --> 0x5 ESP: 0xbfffd2f0 --> 0xb7fd8900 --> 0xb7e36000 --> 0x464c457f EIP: 0xb7df2eba (<send_vc+1098>: mov edi,DWORD PTR [edi]) EFLAGS: 0x206 (carry PARITY adjust zero sign trap INTERRUPT direction overflow) [-------------------------------------code-------------------------------------] 0xb7df2eab <send_vc+1083>: mov WORD PTR [esp+0x5e],ax 0xb7df2eb0 <send_vc+1088>: cmp ax,0xb 0xb7df2eb4 <send_vc+1092>: jbe 0xb7df2fbd <send_vc+1357> => 0xb7df2eba <send_vc+1098>: mov edi,DWORD PTR [edi] 0xb7df2ebc <send_vc+1100>: jmp 0xb7df2ed6 <send_vc+1126> 0xb7df2ebe <send_vc+1102>: xchg ax,ax 0xb7df2ec0 <send_vc+1104>: movzx edx,WORD PTR [esp+0x5e] 0xb7df2ec5 <send_vc+1109>: add edi,eax [------------------------------------stack-------------------------------------] 0000| 0xbfffd2f0 --> 0xb7fd8900 --> 0xb7e36000 --> 0x464c457f 0004| 0xbfffd2f4 --> 0xbfffeb74 --> 0x10000 0008| 0xbfffd2f8 --> 0xbfffeb6c --> 0x804c748 --> 0x80818bf5 0012| 0xbfffd2fc --> 0xbfffd728 --> 0x10000 0016| 0xbfffd300 --> 0xbfffeb70 --> 0xbfffe340 --> 0x0 0020| 0xbfffd304 --> 0x0 0024| 0xbfffd308 --> 0xbfffeb74 --> 0x10000 0028| 0xbfffd30c --> 0x1 [------------------------------------------------------------------------------] Legend: code, data, rodata, value 883 in res_send.c gdb-peda$ n [----------------------------------registers-----------------------------------] EAX: 0x8fe EBX: 0xb7e01000 --> 0x14ed4 ECX: 0xbfffe340 --> 0x4242bb5e EDX: 0x8fe ESI: 0xbfffe340 --> 0x4242bb5e EDI: 0xbfffe340 --> 0x4242bb5e EBP: 0xb7fd6340 --> 0x5 ESP: 0xbfffd2f0 --> 0xb7fd8900 --> 0xb7e36000 --> 0x464c457f EIP: 0xb7df2ec0 (<send_vc+1104>: movzx edx,WORD PTR [esp+0x5e]) EFLAGS: 0x202 (carry parity adjust zero sign trap INTERRUPT direction overflow) [-------------------------------------code-------------------------------------] 0xb7df2eba <send_vc+1098>: mov edi,DWORD PTR [edi] 0xb7df2ebc <send_vc+1100>: jmp 0xb7df2ed6 <send_vc+1126> 0xb7df2ebe <send_vc+1102>: xchg ax,ax => 0xb7df2ec0 <send_vc+1104>: movzx edx,WORD PTR [esp+0x5e] 0xb7df2ec5 <send_vc+1109>: add edi,eax 0xb7df2ec7 <send_vc+1111>: sub edx,eax 0xb7df2ec9 <send_vc+1113>: movzx eax,dx 0xb7df2ecc <send_vc+1116>: test ax,ax [------------------------------------stack-------------------------------------] 0000| 0xbfffd2f0 --> 0xb7fd8900 --> 0xb7e36000 --> 0x464c457f 0004| 0xbfffd2f4 --> 0xbfffeb74 ('B' <repeats 200 times>...) 0008| 0xbfffd2f8 --> 0xbfffeb6c ('B' <repeats 200 times>...) 0012| 0xbfffd2fc --> 0xbfffd728 --> 0x10000 0016| 0xbfffd300 --> 0xbfffeb70 ('B' <repeats 200 times>...) 0020| 0xbfffd304 --> 0x0 0024| 0xbfffd308 --> 0xbfffeb74 ('B' <repeats 200 times>...) 0028| 0xbfffd30c --> 0x1 [------------------------------------------------------------------------------] Legend: code, data, rodata, value 886 in res_send.c ``` 最后我们可以来看一下补丁后的对比 ``` *thisresplenp = rlen; /* Is the answer buffer too small? */ if (*thisanssizp < rlen) { /* If the current buffer is not the the static user-supplied buffer then we can reallocate it. */ if (thisansp != NULL && thisansp != ansp) { /* Always allocate MAXPACKET, callers expect this specific size. */ u_char *newp = malloc (MAXPACKET); if (newp == NULL) { *terrno = ENOMEM; __res_iclose(statp, false); return (0); } *thisanssizp = MAXPACKET; *thisansp = newp; if (thisansp == ansp2) *ansp2_malloced = 1; ``` 可以看到,在官方修复的2.23版本说明中,这里将不再采用静态缓冲区2048,而是会根据用户申请缓冲区的大小来重新分配缓冲区。 ### 5. 漏洞检测 由于glibc 2.9 是在2008年发行的,所以大量Linux 系统都会受到该漏洞影响。若一旦绕过内存防护技术,则该漏洞可以成为一大杀器。被劫持的DNS server进行中间人攻击,可直接批量获取大量主机权限。 利用ldd 命令查看C 库函数版本如下:  > 有趣的是,早在去年的7月份,就有研究人员公布了有关这一漏洞的信息,但当时 此漏洞并没有得到重视。 根据目前的调查情况我们认为此漏洞的级别该视为高危漏洞,Glibc应用于众多Linux发行版本中,所以此类漏洞影响范围十分广泛。该漏洞影响Glibc 2.9以后的所有版本。 ### 6. 漏洞修复 建议广大用户尽快给操作系统打补丁,该漏洞存在于resolv/res_send.c文件中,当getaddrinfo()函数被调用时会触发该漏洞。技术人员可以限制TCP DNS响应包字节的大小,并丢弃超过512字节的UDP DNS数据包来缓解该问题。 有趣的是,早在去年的7月份,就有研究人员公布了有关这一漏洞的信息,但当时 此漏洞并没有得到重视。根据目前的调查情况我们认为此漏洞的级别该视为高危漏洞,glibc应用于众多Linux发行版本中,所以此类漏洞影响范围十分广泛。该漏洞影响glibc 2.9到2.22的所有版本。 ### 7. 相关链接 1. [CVE-2015-7547: glibc getaddrinfo stack-based buffer overflow](https://googleonlinesecurity.blogspot.jp/2016/02/cve-2015-7547-glibc-getaddrinfo-stack.html) 2. [CVE-2015-7547 补丁](https://sourceware.org/ml/libc-alpha/2016-02/msg00416.html) 3. [紧急!Linux 底层函数库“glibc”再现重大安全漏洞!多个 Linux 发行版受影响](https://mp.weixin.qq.com/s?__biz=MzIwMTQ2NzY4NA==&mid=403076844&idx=1&sn=657ee0d88806c2f1b1c9d8d687aae77a&scene=0&key=710a5d99946419d9b1d0d10b2383538792cf67e29692e00185ec90053e80301f92a83b3ad88bfff9b2ce8b9254db3498&ascene=0&uin=NjY5NjY5MDgw&version=11020201&pass_ticket=SxQNHpTQu%2BemqqSwok9Ncxcx7i7ras3ry108ltQKsj6oDLTthSm%2B6IOpHAad0BG%2B) 4. [Linux Glibc 函数库漏洞分析(CVE-2015-7547)](http://blog.knownsec.com/2016/02/linux-glibc-cve-2015-7547-analysis/) |
| id | SSV:90749 |
| last seen | 2017-11-19 |
| modified | 2016-02-17 |
| published | 2016-02-17 |
| reporter | Root |
| source | https://www.seebug.org/vuldb/ssvid-90749 |
| title | glibc getaddrinfo 栈缓冲区溢出漏洞(CVE-2015-7547) |
The Hacker News
| id | THN:ACBFC80659E47A5B7C81B99570749679 |
| last seen | 2018-01-27 |
| modified | 2016-02-17 |
| published | 2016-02-16 |
| reporter | Swati Khandelwal |
| source | https://thehackernews.com/2016/02/glibc-linux-flaw.html |
| title | Critical glibc Flaw Puts Linux Machines and Apps at Risk (Patch Immediately) |
References
- http://fortiguard.com/advisory/glibc-getaddrinfo-stack-overflow
- http://fortiguard.com/advisory/glibc-getaddrinfo-stack-overflow
- http://lists.fedoraproject.org/pipermail/package-announce/2016-February/177404.html
- http://lists.fedoraproject.org/pipermail/package-announce/2016-February/177404.html
- http://lists.fedoraproject.org/pipermail/package-announce/2016-February/177412.html
- http://lists.fedoraproject.org/pipermail/package-announce/2016-February/177412.html
- http://lists.opensuse.org/opensuse-security-announce/2016-02/msg00036.html
- http://lists.opensuse.org/opensuse-security-announce/2016-02/msg00036.html
- http://lists.opensuse.org/opensuse-security-announce/2016-02/msg00037.html
- http://lists.opensuse.org/opensuse-security-announce/2016-02/msg00037.html
- http://lists.opensuse.org/opensuse-security-announce/2016-02/msg00038.html
- http://lists.opensuse.org/opensuse-security-announce/2016-02/msg00038.html
- http://lists.opensuse.org/opensuse-security-announce/2016-02/msg00039.html
- http://lists.opensuse.org/opensuse-security-announce/2016-02/msg00039.html
- http://lists.opensuse.org/opensuse-security-announce/2016-02/msg00042.html
- http://lists.opensuse.org/opensuse-security-announce/2016-02/msg00042.html
- http://lists.opensuse.org/opensuse-security-announce/2016-02/msg00043.html
- http://lists.opensuse.org/opensuse-security-announce/2016-02/msg00043.html
- http://lists.opensuse.org/opensuse-security-announce/2016-02/msg00044.html
- http://lists.opensuse.org/opensuse-security-announce/2016-02/msg00044.html
- http://marc.info/?l=bugtraq&m=145596041017029&w=2
- http://marc.info/?l=bugtraq&m=145596041017029&w=2
- http://marc.info/?l=bugtraq&m=145672440608228&w=2
- http://marc.info/?l=bugtraq&m=145672440608228&w=2
- http://marc.info/?l=bugtraq&m=145690841819314&w=2
- http://marc.info/?l=bugtraq&m=145690841819314&w=2
- http://marc.info/?l=bugtraq&m=145857691004892&w=2
- http://marc.info/?l=bugtraq&m=145857691004892&w=2
- http://marc.info/?l=bugtraq&m=146161017210491&w=2
- http://marc.info/?l=bugtraq&m=146161017210491&w=2
- http://packetstormsecurity.com/files/135802/glibc-getaddrinfo-Stack-Based-Buffer-Overflow.html
- http://packetstormsecurity.com/files/135802/glibc-getaddrinfo-Stack-Based-Buffer-Overflow.html
- http://packetstormsecurity.com/files/154361/Cisco-Device-Hardcoded-Credentials-GNU-glibc-BusyBox.html
- http://packetstormsecurity.com/files/154361/Cisco-Device-Hardcoded-Credentials-GNU-glibc-BusyBox.html
- http://packetstormsecurity.com/files/164014/Moxa-Command-Injection-Cross-Site-Scripting-Vulnerable-Software.html
- http://packetstormsecurity.com/files/164014/Moxa-Command-Injection-Cross-Site-Scripting-Vulnerable-Software.html
- http://packetstormsecurity.com/files/167552/Nexans-FTTO-GigaSwitch-Outdated-Components-Hardcoded-Backdoor.html
- http://packetstormsecurity.com/files/167552/Nexans-FTTO-GigaSwitch-Outdated-Components-Hardcoded-Backdoor.html
- http://rhn.redhat.com/errata/RHSA-2016-0175.html
- http://rhn.redhat.com/errata/RHSA-2016-0175.html
- http://rhn.redhat.com/errata/RHSA-2016-0176.html
- http://rhn.redhat.com/errata/RHSA-2016-0176.html
- http://rhn.redhat.com/errata/RHSA-2016-0225.html
- http://rhn.redhat.com/errata/RHSA-2016-0225.html
- http://rhn.redhat.com/errata/RHSA-2016-0277.html
- http://rhn.redhat.com/errata/RHSA-2016-0277.html
- http://seclists.org/fulldisclosure/2019/Sep/7
- http://seclists.org/fulldisclosure/2019/Sep/7
- http://seclists.org/fulldisclosure/2021/Sep/0
- http://seclists.org/fulldisclosure/2021/Sep/0
- http://seclists.org/fulldisclosure/2022/Jun/36
- http://seclists.org/fulldisclosure/2022/Jun/36
- http://support.citrix.com/article/CTX206991
- http://support.citrix.com/article/CTX206991
- http://ubuntu.com/usn/usn-2900-1
- http://ubuntu.com/usn/usn-2900-1
- http://www.debian.org/security/2016/dsa-3480
- http://www.debian.org/security/2016/dsa-3480
- http://www.debian.org/security/2016/dsa-3481
- http://www.debian.org/security/2016/dsa-3481
- http://www.fortiguard.com/advisory/glibc-getaddrinfo-stack-overflow
- http://www.fortiguard.com/advisory/glibc-getaddrinfo-stack-overflow
- http://www.huawei.com/en/psirt/security-advisories/huawei-sa-20160304-01-glibc-en
- http://www.huawei.com/en/psirt/security-advisories/huawei-sa-20160304-01-glibc-en
- http://www.oracle.com/technetwork/security-advisory/cpuapr2016v3-2985753.html
- http://www.oracle.com/technetwork/security-advisory/cpuapr2016v3-2985753.html
- http://www.oracle.com/technetwork/security-advisory/cpujan2018-3236628.html
- http://www.oracle.com/technetwork/security-advisory/cpujan2018-3236628.html
- http://www.oracle.com/technetwork/topics/security/linuxbulletinjan2016-2867209.html
- http://www.oracle.com/technetwork/topics/security/linuxbulletinjan2016-2867209.html
- http://www.securityfocus.com/bid/83265
- http://www.securityfocus.com/bid/83265
- http://www.securitytracker.com/id/1035020
- http://www.securitytracker.com/id/1035020
- http://www.vmware.com/security/advisories/VMSA-2016-0002.html
- http://www.vmware.com/security/advisories/VMSA-2016-0002.html
- https://access.redhat.com/articles/2161461
- https://access.redhat.com/articles/2161461
- https://blogs.sophos.com/2016/02/24/utm-up2date-9-355-released/
- https://blogs.sophos.com/2016/02/24/utm-up2date-9-355-released/
- https://blogs.sophos.com/2016/02/29/utm-up2date-9-319-released/
- https://blogs.sophos.com/2016/02/29/utm-up2date-9-319-released/
- https://bto.bluecoat.com/security-advisory/sa114
- https://bto.bluecoat.com/security-advisory/sa114
- https://bugzilla.redhat.com/show_bug.cgi?id=1293532
- https://bugzilla.redhat.com/show_bug.cgi?id=1293532
- https://googleonlinesecurity.blogspot.com/2016/02/cve-2015-7547-glibc-getaddrinfo-stack.html
- https://googleonlinesecurity.blogspot.com/2016/02/cve-2015-7547-glibc-getaddrinfo-stack.html
- https://h20566.www2.hpe.com/hpsc/doc/public/display?docId=emr_na-c05028479
- https://h20566.www2.hpe.com/hpsc/doc/public/display?docId=emr_na-c05028479
- https://h20566.www2.hpe.com/portal/site/hpsc/public/kb/docDisplay?docId=emr_na-c04989404
- https://h20566.www2.hpe.com/portal/site/hpsc/public/kb/docDisplay?docId=emr_na-c04989404
- https://h20566.www2.hpe.com/portal/site/hpsc/public/kb/docDisplay?docId=emr_na-c05008367
- https://h20566.www2.hpe.com/portal/site/hpsc/public/kb/docDisplay?docId=emr_na-c05008367
- https://h20566.www2.hpe.com/portal/site/hpsc/public/kb/docDisplay?docId=emr_na-c05053211
- https://h20566.www2.hpe.com/portal/site/hpsc/public/kb/docDisplay?docId=emr_na-c05053211
- https://h20566.www2.hpe.com/portal/site/hpsc/public/kb/docDisplay?docId=emr_na-c05073516
- https://h20566.www2.hpe.com/portal/site/hpsc/public/kb/docDisplay?docId=emr_na-c05073516
- https://h20566.www2.hpe.com/portal/site/hpsc/public/kb/docDisplay?docId=emr_na-c05098877
- https://h20566.www2.hpe.com/portal/site/hpsc/public/kb/docDisplay?docId=emr_na-c05098877
- https://h20566.www2.hpe.com/portal/site/hpsc/public/kb/docDisplay?docId=emr_na-c05125672
- https://h20566.www2.hpe.com/portal/site/hpsc/public/kb/docDisplay?docId=emr_na-c05125672
- https://h20566.www2.hpe.com/portal/site/hpsc/public/kb/docDisplay?docId=emr_na-c05128937
- https://h20566.www2.hpe.com/portal/site/hpsc/public/kb/docDisplay?docId=emr_na-c05128937
- https://h20566.www2.hpe.com/portal/site/hpsc/public/kb/docDisplay?docId=emr_na-c05130958
- https://h20566.www2.hpe.com/portal/site/hpsc/public/kb/docDisplay?docId=emr_na-c05130958
- https://h20566.www2.hpe.com/portal/site/hpsc/public/kb/docDisplay?docId=emr_na-c05140858
- https://h20566.www2.hpe.com/portal/site/hpsc/public/kb/docDisplay?docId=emr_na-c05140858
- https://h20566.www2.hpe.com/portal/site/hpsc/public/kb/docDisplay?docId=emr_na-c05158380
- https://h20566.www2.hpe.com/portal/site/hpsc/public/kb/docDisplay?docId=emr_na-c05158380
- https://h20566.www2.hpe.com/portal/site/hpsc/public/kb/docDisplay?docId=emr_na-c05176716
- https://h20566.www2.hpe.com/portal/site/hpsc/public/kb/docDisplay?docId=emr_na-c05176716
- https://h20566.www2.hpe.com/portal/site/hpsc/public/kb/docDisplay?docId=emr_na-c05212266
- https://h20566.www2.hpe.com/portal/site/hpsc/public/kb/docDisplay?docId=emr_na-c05212266
- https://h20566.www2.hpe.com/portal/site/hpsc/public/kb/docDisplay?docId=emr_na-c05376917
- https://h20566.www2.hpe.com/portal/site/hpsc/public/kb/docDisplay?docId=emr_na-c05376917
- https://h20566.www2.hpe.com/portal/site/hpsc/public/kb/docDisplay?docId=emr_na-c05390722
- https://h20566.www2.hpe.com/portal/site/hpsc/public/kb/docDisplay?docId=emr_na-c05390722
- https://help.ecostruxureit.com/display/public/UADCO8x/StruxureWare+Data+Center+Operation+Software+Vulnerability+Fixes
- https://help.ecostruxureit.com/display/public/UADCO8x/StruxureWare+Data+Center+Operation+Software+Vulnerability+Fixes
- https://ics-cert.us-cert.gov/advisories/ICSA-16-103-01
- https://ics-cert.us-cert.gov/advisories/ICSA-16-103-01
- https://kb.pulsesecure.net/articles/Pulse_Security_Advisories/SA40161
- https://kb.pulsesecure.net/articles/Pulse_Security_Advisories/SA40161
- https://kc.mcafee.com/corporate/index?page=content&id=SB10150
- https://kc.mcafee.com/corporate/index?page=content&id=SB10150
- https://seclists.org/bugtraq/2019/Sep/7
- https://seclists.org/bugtraq/2019/Sep/7
- https://security.gentoo.org/glsa/201602-02
- https://security.gentoo.org/glsa/201602-02
- https://security.netapp.com/advisory/ntap-20160217-0002/
- https://security.netapp.com/advisory/ntap-20160217-0002/
- https://sourceware.org/bugzilla/show_bug.cgi?id=18665
- https://sourceware.org/bugzilla/show_bug.cgi?id=18665
- https://sourceware.org/ml/libc-alpha/2016-02/msg00416.html
- https://sourceware.org/ml/libc-alpha/2016-02/msg00416.html
- https://support.f5.com/kb/en-us/solutions/public/k/47/sol47098834.html
- https://support.f5.com/kb/en-us/solutions/public/k/47/sol47098834.html
- https://support.lenovo.com/us/en/product_security/len_5450
- https://support.lenovo.com/us/en/product_security/len_5450
- https://www.arista.com/en/support/advisories-notices/security-advisories/1255-security-advisory-17
- https://www.arista.com/en/support/advisories-notices/security-advisories/1255-security-advisory-17
- https://www.exploit-db.com/exploits/39454/
- https://www.exploit-db.com/exploits/39454/
- https://www.exploit-db.com/exploits/40339/
- https://www.exploit-db.com/exploits/40339/
- https://www.kb.cert.org/vuls/id/457759
- https://www.kb.cert.org/vuls/id/457759
- https://www.tenable.com/security/research/tra-2017-08
- https://www.tenable.com/security/research/tra-2017-08