Vulnerabilities > CVE-2015-7504 - Out-of-bounds Write vulnerability in multiple products
Attack vector
LOCAL Attack complexity
LOW Privileges required
LOW Confidentiality impact
HIGH Integrity impact
HIGH Availability impact
HIGH Summary
Heap-based buffer overflow in the pcnet_receive function in hw/net/pcnet.c in QEMU allows guest OS administrators to cause a denial of service (instance crash) or possibly execute arbitrary code via a series of packets in loopback mode.
Vulnerable Configurations
Common Weakness Enumeration (CWE)
Nessus
NASL family SuSE Local Security Checks NASL id SUSE_SU-2016-0658-1.NASL description Xen was updated to fix the following vulnerabilities : CVE-2014-0222: Qcow1 L2 table size integer overflows (bsc#877642) CVE-2015-4037: Insecure temporary file use in /net/slirp.c (bsc#932267) CVE-2015-5239: Integer overflow in vnc_client_read() and protocol_client_msg() (bsc#944463) CVE-2015-7504: Heap buffer overflow vulnerability in pcnet emulator (XSA-162, bsc#956411) CVE-2015-7971: Some pmu and profiling hypercalls log without rate limiting (XSA-152, bsc#950706) CVE-2015-8104: Guest to host DoS by triggering an infinite loop in microcode via #DB exception (bsc#954405) CVE-2015-5307: Guest to host DOS by intercepting #AC (XSA-156, bsc#953527) CVE-2015-8339: XENMEM_exchange error handling issues (XSA-159, bsc#956408) CVE-2015-8340: XENMEM_exchange error handling issues (XSA-159, bsc#956408) CVE-2015-7512: Buffer overflow in pcnet last seen 2020-06-01 modified 2020-06-02 plugin id 89723 published 2016-03-07 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/89723 title SUSE SLES10 Security Update : Xen (SUSE-SU-2016:0658-1) NASL family Debian Local Security Checks NASL id DEBIAN_DSA-3470.NASL description Several vulnerabilities were discovered in qemu-kvm, a full virtualization solution on x86 hardware. - CVE-2015-7295 Jason Wang of Red Hat Inc. discovered that the Virtual Network Device support is vulnerable to denial-of-service (via resource exhaustion), that could occur when receiving large packets. - CVE-2015-7504 Qinghao Tang of Qihoo 360 Inc. and Ling Liu of Qihoo 360 Inc. discovered that the PC-Net II ethernet controller is vulnerable to a heap-based buffer overflow that could result in denial-of-service (via application crash) or arbitrary code execution. - CVE-2015-7512 Ling Liu of Qihoo 360 Inc. and Jason Wang of Red Hat Inc. discovered that the PC-Net II ethernet controller is vulnerable to a buffer overflow that could result in denial-of-service (via application crash) or arbitrary code execution. - CVE-2015-8345 Qinghao Tang of Qihoo 360 Inc. discovered that the eepro100 emulator contains a flaw that could lead to an infinite loop when processing Command Blocks, eventually resulting in denial-of-service (via application crash). - CVE-2015-8504 Lian Yihan of Qihoo 360 Inc. discovered that the VNC display driver support is vulnerable to an arithmetic exception flaw that could lead to denial-of-service (via application crash). - CVE-2015-8558 Qinghao Tang of Qihoo 360 Inc. discovered that the USB EHCI emulation support contains a flaw that could lead to an infinite loop during communication between the host controller and a device driver. This could lead to denial-of-service (via resource exhaustion). - CVE-2015-8743 Ling Liu of Qihoo 360 Inc. discovered that the NE2000 emulator is vulnerable to an out-of-bound read/write access issue, potentially resulting in information leak or memory corruption. - CVE-2016-1568 Qinghao Tang of Qihoo 360 Inc. discovered that the IDE AHCI emulation support is vulnerable to a use-after-free issue, that could lead to denial-of-service (via application crash) or arbitrary code execution. - CVE-2016-1714 Donghai Zhu of Alibaba discovered that the Firmware Configuration emulation support is vulnerable to an out-of-bound read/write access issue, that could lead to denial-of-service (via application crash) or arbitrary code execution. - CVE-2016-1922 Ling Liu of Qihoo 360 Inc. discovered that 32-bit Windows guests support is vulnerable to a NULL pointer dereference issue, that could lead to denial-of-service (via application crash). last seen 2020-06-01 modified 2020-06-02 plugin id 88629 published 2016-02-09 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/88629 title Debian DSA-3470-1 : qemu-kvm - security update NASL family OracleVM Local Security Checks NASL id ORACLEVM_OVMSA-2016-0081.NASL description The remote OracleVM system is missing necessary patches to address critical security updates : please see Oracle VM Security Advisory OVMSA-2016-0081 for details. last seen 2020-06-01 modified 2020-06-02 plugin id 91756 published 2016-06-22 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/91756 title OracleVM 3.2 : xen (OVMSA-2016-0081) NASL family SuSE Local Security Checks NASL id OPENSUSE-2016-36.NASL description This update for xen fixes the following issues : - CVE-2015-8567,CVE-2015-8568: xen: qemu: net: vmxnet3: host memory leakage (boo#959387) - CVE-2015-8550: xen: paravirtualized drivers incautious about shared memory contents (XSA-155, boo#957988) - CVE-2015-8558: xen: qemu: usb: infinite loop in ehci_advance_state results in DoS (boo#959006) - CVE-2015-7549: xen: qemu pci: NULL pointer dereference issue (boo#958918) - CVE-2015-8504: xen: qemu: ui: vnc: avoid floating point exception (boo#958493) - CVE-2015-8554: xen: qemu-dm buffer overrun in MSI-X handling (XSA-164, boo#958007) - CVE-2015-8555: xen: information leak in legacy x86 FPU/XMM initialization (XSA-165, boo#958009) - boo#958523: xen: ioreq handling possibly susceptible to multiple read issue (XSA-166) - CVE-2015-8345: xen: qemu: net: eepro100: infinite loop in processing command block list (boo#956832) - CVE-2015-5307: xen: x86: CPU lockup during fault delivery (XSA-156, boo#954018) - boo#956592: xen: virtual PMU is unsupported (XSA-163) - CVE-2015-8339, CVE-2015-8340: xen: XENMEM_exchange error handling issues (XSA-159, boo#956408) - CVE-2015-8341: xen: libxl leak of pv kernel and initrd on error (XSA-160, boo#956409) - CVE-2015-7504: xen: heap buffer overflow vulnerability in pcnet emulator (XSA-162, boo#956411) last seen 2020-06-05 modified 2016-01-25 plugin id 88126 published 2016-01-25 reporter This script is Copyright (C) 2016-2020 Tenable Network Security, Inc. source https://www.tenable.com/plugins/nessus/88126 title openSUSE Security Update : xen (openSUSE-2016-36) NASL family Oracle Linux Local Security Checks NASL id ORACLELINUX_ELSA-2015-2694.NASL description From Red Hat Security Advisory 2015:2694 : Updated qemu-kvm packages that fix two security issues are now available for Red Hat Enterprise Linux 6. Red Hat Product Security has rated this update as having Important security impact. Common Vulnerability Scoring System (CVSS) base scores, which give detailed severity ratings, are available for each vulnerability from the CVE links in the References section. KVM (Kernel-based Virtual Machine) is a full virtualization solution for Linux on AMD64 and Intel 64 systems. The qemu-kvm package provides the user-space component for running virtual machines using KVM. A heap-based buffer overflow flaw was discovered in the way QEMU last seen 2020-06-01 modified 2020-06-02 plugin id 87636 published 2015-12-29 reporter This script is Copyright (C) 2015-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/87636 title Oracle Linux 6 : qemu-kvm (ELSA-2015-2694) NASL family Debian Local Security Checks NASL id DEBIAN_DSA-3471.NASL description Several vulnerabilities were discovered in qemu, a full virtualization solution on x86 hardware. - CVE-2015-7295 Jason Wang of Red Hat Inc. discovered that the Virtual Network Device support is vulnerable to denial-of-service, that could occur when receiving large packets. - CVE-2015-7504 Qinghao Tang of Qihoo 360 Inc. and Ling Liu of Qihoo 360 Inc. discovered that the PC-Net II ethernet controller is vulnerable to a heap-based buffer overflow that could result in denial-of-service (via application crash) or arbitrary code execution. - CVE-2015-7512 Ling Liu of Qihoo 360 Inc. and Jason Wang of Red Hat Inc. discovered that the PC-Net II ethernet controller is vulnerable to a buffer overflow that could result in denial-of-service (via application crash) or arbitrary code execution. - CVE-2015-7549 Qinghao Tang of Qihoo 360 Inc. and Ling Liu of Qihoo 360 Inc. discovered that the PCI MSI-X emulator is vulnerable to a NULL pointer dereference issue, that could lead to denial-of-service (via application crash). - CVE-2015-8345 Qinghao Tang of Qihoo 360 Inc. discovered that the eepro100 emulator contains a flaw that could lead to an infinite loop when processing Command Blocks, eventually resulting in denial-of-service (via application crash). - CVE-2015-8504 Lian Yihan of Qihoo 360 Inc. discovered that the VNC display driver support is vulnerable to an arithmetic exception flaw that could lead to denial-of-service (via application crash). - CVE-2015-8550 Felix Wilhelm of ERNW Research discovered that the PV backend drivers are vulnerable to double fetch vulnerabilities, possibly resulting in arbitrary code execution. - CVE-2015-8558 Qinghao Tang of Qihoo 360 Inc. discovered that the USB EHCI emulation support contains a flaw that could lead to an infinite loop during communication between the host controller and a device driver. This could lead to denial-of-service (via resource exhaustion). - CVE-2015-8567 CVE-2015-8568 Qinghao Tang of Qihoo 360 Inc. discovered that the vmxnet3 device emulator could be used to intentionally leak host memory, thus resulting in denial-of-service. - CVE-2015-8613 Qinghao Tang of Qihoo 360 Inc. discovered that the SCSI MegaRAID SAS HBA emulation support is vulnerable to a stack-based buffer overflow issue, that could lead to denial-of-service (via application crash). - CVE-2015-8619 Ling Liu of Qihoo 360 Inc. discovered that the Human Monitor Interface support is vulnerable to an out-of-bound write access issue that could result in denial-of-service (via application crash). - CVE-2015-8743 Ling Liu of Qihoo 360 Inc. discovered that the NE2000 emulator is vulnerable to an out-of-bound read/write access issue, potentially resulting in information leak or memory corruption. - CVE-2015-8744 The vmxnet3 driver incorrectly processes small packets, which could result in denial-of-service (via application crash). - CVE-2015-8745 The vmxnet3 driver incorrectly processes Interrupt Mask Registers, which could result in denial-of-service (via application crash). - CVE-2016-1568 Qinghao Tang of Qihoo 360 Inc. discovered that the IDE AHCI emulation support is vulnerable to a use-after-free issue, that could lead to denial-of-service (via application crash) or arbitrary code execution. - CVE-2016-1714 Donghai Zhu of Alibaba discovered that the Firmware Configuration emulation support is vulnerable to an out-of-bound read/write access issue, that could lead to denial-of-service (via application crash) or arbitrary code execution. - CVE-2016-1922 Ling Liu of Qihoo 360 Inc. discovered that 32-bit Windows guests support is vulnerable to a NULL pointer dereference issue, that could lead to denial-of-service (via application crash). - CVE-2016-1981 The e1000 driver is vulnerable to an infinite loop issue that could lead to denial-of-service (via application crash). last seen 2020-06-01 modified 2020-06-02 plugin id 88630 published 2016-02-09 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/88630 title Debian DSA-3471-1 : qemu - security update NASL family Fedora Local Security Checks NASL id FEDORA_2015-12A089920E.NASL description eepro100: Prevent two endless loops [CVE-2015-8345], pcnet: fix rx buffer overflow [CVE-2015-7512], ui: vnc: avoid floating point exception [CVE-2015-8504], additional patch for [XSA-158, CVE-2015-8338] long running memory operations on ARM [XSA-158, CVE-2015-8338] XENMEM_exchange error handling issues [XSA-159, CVE-2015-8339, CVE-2015-8340] libxl leak of pv kernel and initrd on error [XSA-160, CVE-2015-8341] ---- heap buffer overflow vulnerability in pcnet emulator [XSA-162, CVE-2015-7504], virtual PMU is unsupported [XSA-163] Note that Tenable Network Security has extracted the preceding description block directly from the Fedora security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-05 modified 2016-03-04 plugin id 89151 published 2016-03-04 reporter This script is Copyright (C) 2016-2020 Tenable Network Security, Inc. source https://www.tenable.com/plugins/nessus/89151 title Fedora 23 : xen-4.5.2-5.fc23 (2015-12a089920e) NASL family Scientific Linux Local Security Checks NASL id SL_20151222_QEMU_KVM_ON_SL6_X.NASL description A heap-based buffer overflow flaw was discovered in the way QEMU last seen 2020-03-18 modified 2015-12-29 plugin id 87639 published 2015-12-29 reporter This script is Copyright (C) 2015-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/87639 title Scientific Linux Security Update : qemu-kvm on SL6.x i386/x86_64 (20151222) NASL family Ubuntu Local Security Checks NASL id UBUNTU_USN-2828-1.NASL description Jason Wang discovered that QEMU incorrectly handled the virtio-net device. A remote attacker could use this issue to cause guest network consumption, resulting in a denial of service. (CVE-2015-7295) Qinghao Tang and Ling Liu discovered that QEMU incorrectly handled the pcnet driver when used in loopback mode. A malicious guest could use this issue to cause a denial of service, or possibly execute arbitrary code on the host as the user running the QEMU process. In the default installation, when QEMU is used with libvirt, attackers would be isolated by the libvirt AppArmor profile. (CVE-2015-7504) Ling Liu and Jason Wang discovered that QEMU incorrectly handled the pcnet driver. A remote attacker could use this issue to cause a denial of service, or possibly execute arbitrary code on the host as the user running the QEMU process. In the default installation, when QEMU is used with libvirt, attackers would be isolated by the libvirt AppArmor profile. (CVE-2015-7512) Qinghao Tang discovered that QEMU incorrectly handled the eepro100 driver. A malicious guest could use this issue to cause an infinite loop, leading to a denial of service. (CVE-2015-8345). Note that Tenable Network Security has extracted the preceding description block directly from the Ubuntu security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 87205 published 2015-12-04 reporter Ubuntu Security Notice (C) 2015-2019 Canonical, Inc. / NASL script (C) 2015-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/87205 title Ubuntu 12.04 LTS / 14.04 LTS / 15.04 / 15.10 : qemu, qemu-kvm vulnerabilities (USN-2828-1) NASL family SuSE Local Security Checks NASL id SUSE_SU-2015-2338-1.NASL description This update fixes the following security issues : - bsc#955399 - Fix xm migrate --log_progress. Due to logic error progress was not logged when requested. - bsc#956832 - CVE-2015-8345: xen: qemu: net: eepro100: infinite loop in processing command block list - bsc#956592 - xen: virtual PMU is unsupported (XSA-163) - bsc#956408 - CVE-2015-8339, CVE-2015-8340: xen: XENMEM_exchange error handling issues (XSA-159) - bsc#956409 - CVE-2015-8341: xen: libxl leak of pv kernel and initrd on error (XSA-160) - bsc#956411 - CVE-2015-7504: xen: heap buffer overflow vulnerability in pcnet emulator (XSA-162) - bsc#947165 - CVE-2015-7311: xen: libxl fails to honour readonly flag on disks with qemu-xen (xsa-142) - bsc#955399 - Fix xm migrate --live. The options were not passed due to a merge error. As a result the migration was not live, instead the suspended guest was migrated. - bsc#954405 - CVE-2015-8104: Xen: guest to host DoS by triggering an infinite loop in microcode via #DB exception - bsc#954018 - CVE-2015-5307: xen: x86: CPU lockup during fault delivery (XSA-156) - bsc#950704 - CVE-2015-7970: xen: x86: Long latency populate-on-demand operation is not preemptible (XSA-150) - bsc#951845 - CVE-2015-7972: xen: x86: populate-on-demand balloon size inaccuracy can crash guests (XSA-153) - Drop 5604f239-x86-PV-properly-populate-descriptor-tables.patc h - bsc#950703 - CVE-2015-7969: xen: leak of main per-domain vcpu pointer array (DoS) (XSA-149) - bsc#950705 - CVE-2015-7969: xen: x86: leak of per-domain profiling-related vcpu pointer array (DoS) (XSA-151) - bsc#950706 - CVE-2015-7971: xen: x86: some pmu and profiling hypercalls log without rate limiting (XSA-152) Note that Tenable Network Security has extracted the preceding description block directly from the SUSE security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 87650 published 2015-12-29 reporter This script is Copyright (C) 2015-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/87650 title SUSE SLED11 / SLES11 Security Update : xen (SUSE-SU-2015:2338-1) NASL family SuSE Local Security Checks NASL id SUSE_SU-2015-2324-1.NASL description This update fixes the following security issues : - bsc#956832 - CVE-2015-8345: xen: qemu: net: eepro100: infinite loop in processing command block list - Revert x86/IO-APIC: don last seen 2020-06-01 modified 2020-06-02 plugin id 87588 published 2015-12-22 reporter This script is Copyright (C) 2015-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/87588 title SUSE SLED12 / SLES12 Security Update : xen (SUSE-SU-2015:2324-1) NASL family F5 Networks Local Security Checks NASL id F5_BIGIP_SOL63519101.NASL description CVE-2014-8106 Heap-based buffer overflow in the Cirrus VGA emulator (hw/display/cirrus_vga.c) in QEMU before 2.2.0 allows local guest users to execute arbitrary code via vectors related to blit regions. NOTE: this vulnerability exists because an incomplete fix for CVE-2007-1320. CVE-2015-3209 Heap-based buffer overflow in the PCNET controller in QEMU allows remote attackers to execute arbitrary code by sending a packet with TXSTATUS_STARTPACKET set and then a crafted packet with TXSTATUS_DEVICEOWNS set. CVE-2015-5165 The C+ mode offload emulation in the RTL8139 network card device model in QEMU, as used in Xen 4.5.x and earlier, allows remote attackers to read process heap memory via unspecified vectors. CVE-2015-5279 Heap-based buffer overflow in the ne2000_receive function in hw/net/ne2000.c in QEMU before 2.4.0.1 allows guest OS users to cause a denial of service (instance crash) or possibly execute arbitrary code via vectors related to receiving packets. CVE-2015-7504 Heap-based buffer overflow in the pcnet_receive function in hw/net/pcnet.c in QEMU allows guest OS administrators to cause a denial of service (instance crash) or possibly execute arbitrary code via a series of packets in loopback mode. CVE-2015-7512 Buffer overflow in the pcnet_receive function in hw/net/pcnet.c in QEMU, when a guest NIC has a larger MTU, allows remote attackers to cause a denial of service (guest OS crash) or execute arbitrary code via a large packet. Impact An attacker may be able to cause a denial of service (DoS) or execute arbitrary code if using the virtual drivers specified in these CVE descriptions. last seen 2020-03-17 modified 2016-02-17 plugin id 88770 published 2016-02-17 reporter This script is Copyright (C) 2016-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/88770 title F5 Networks BIG-IP : Multiple QEMU vulnerabilities (K63519101) NASL family Fedora Local Security Checks NASL id FEDORA_2015-08E4AF5A20.NASL description eepro100: Prevent two endless loops [CVE-2015-8345] (#1285215), pcnet: fix rx buffer overflow [CVE-2015-7512], ui: vnc: avoid floating point exception [CVE-2015-8504], additional patch for [XSA-158, CVE-2015-8338] long running memory operations on ARM [XSA-158, CVE-2015-8338] XENMEM_exchange error handling issues [XSA-159, CVE-2015-8339, CVE-2015-8340] libxl leak of pv kernel and initrd on error [XSA-160, CVE-2015-8341] ---- heap buffer overflow vulnerability in pcnet emulator [XSA-162, CVE-2015-7504], virtual PMU is unsupported [XSA-163] Note that Tenable Network Security has extracted the preceding description block directly from the Fedora security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-05 modified 2016-03-04 plugin id 89135 published 2016-03-04 reporter This script is Copyright (C) 2016-2020 Tenable Network Security, Inc. source https://www.tenable.com/plugins/nessus/89135 title Fedora 22 : xen-4.5.2-5.fc22 (2015-08e4af5a20) NASL family SuSE Local Security Checks NASL id OPENSUSE-2016-34.NASL description This update for xen fixes the following security issues : - CVE-2015-8550: paravirtualized drivers incautious about shared memory contents (XSA-155, boo#957988) - CVE-2015-8558: qemu: usb: infinite loop in ehci_advance_state results in DoS (boo#959006) - CVE-2015-7549: qemu pci: NULL pointer dereference issue (boo#958918) - CVE-2015-8504: qemu: ui: vnc: avoid floating point exception (boo#958493) - CVE-2015-8554: qemu-dm buffer overrun in MSI-X handling (XSA-164, boo#958007) - CVE-2015-8555: information leak in legacy x86 FPU/XMM initialization (XSA-165, boo#958009) - boo#958523 xen: ioreq handling possibly susceptible to multiple read issue (XSA-166) - CVE-2015-8345: xen: qemu: net: eepro100: infinite loop in processing command block list (boo#956832) - boo#956592: xen: virtual PMU is unsupported (XSA-163) - CVE-2015-8339, CVE-2015-8340: xen: XENMEM_exchange error handling issues (XSA-159, boo#956408) - CVE-2015-8341: xen: libxl leak of pv kernel and initrd on error (XSA-160, boo#956409) - CVE-2015-7504: xen: heap buffer overflow vulnerability in pcnet emulator (XSA-162, boo#956411) - CVE-2015-7311: xen: libxl fails to honour readonly flag on disks with qemu-xen (xsa-142, boo#947165) - CVE-2015-8104: Xen: guest to host DoS by triggering an infinite loop in microcode via #DB exception (boo#954405) - CVE-2015-5307: xen: x86: CPU lockup during fault delivery (XSA-156, boo#954018) - CVE-2015-7970: xen: x86: Long latency populate-on-demand operation is not preemptible (XSA-150, boo#950704) last seen 2020-06-05 modified 2016-01-25 plugin id 88124 published 2016-01-25 reporter This script is Copyright (C) 2016-2020 Tenable Network Security, Inc. source https://www.tenable.com/plugins/nessus/88124 title openSUSE Security Update : xen (openSUSE-2016-34) NASL family Gentoo Local Security Checks NASL id GENTOO_GLSA-201602-01.NASL description The remote host is affected by the vulnerability described in GLSA-201602-01 (QEMU: Multiple vulnerabilities) Multiple vulnerabilities have been discovered in QEMU. Please review the CVE identifiers referenced below for details. Impact : A remote attacker might cause a Denial of Service or gain escalated privileges from a guest VM. Workaround : There is no known workaround at this time. last seen 2020-06-01 modified 2020-06-02 plugin id 88587 published 2016-02-05 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/88587 title GLSA-201602-01 : QEMU: Multiple vulnerabilities (Venom) NASL family FreeBSD Local Security Checks NASL id FREEBSD_PKG_405446F4B1B311E59728002590263BF5.NASL description Prasad J Pandit, Red Hat Product Security Team, reports : Qemu emulator built with the AMD PC-Net II Ethernet Controller support is vulnerable to a heap buffer overflow flaw. While receiving packets in the loopback mode, it appends CRC code to the receive buffer. If the data size given is same as the receive buffer size, the appended CRC code overwrites 4 bytes beyond this last seen 2020-06-01 modified 2020-06-02 plugin id 87691 published 2016-01-04 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/87691 title FreeBSD : qemu and xen-tools -- denial of service vulnerabilities in AMD PC-Net II NIC support (405446f4-b1b3-11e5-9728-002590263bf5) NASL family Red Hat Local Security Checks NASL id REDHAT-RHSA-2015-2694.NASL description Updated qemu-kvm packages that fix two security issues are now available for Red Hat Enterprise Linux 6. Red Hat Product Security has rated this update as having Important security impact. Common Vulnerability Scoring System (CVSS) base scores, which give detailed severity ratings, are available for each vulnerability from the CVE links in the References section. KVM (Kernel-based Virtual Machine) is a full virtualization solution for Linux on AMD64 and Intel 64 systems. The qemu-kvm package provides the user-space component for running virtual machines using KVM. A heap-based buffer overflow flaw was discovered in the way QEMU last seen 2020-06-01 modified 2020-06-02 plugin id 87637 published 2015-12-29 reporter This script is Copyright (C) 2015-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/87637 title RHEL 6 : qemu-kvm (RHSA-2015:2694) NASL family Gentoo Local Security Checks NASL id GENTOO_GLSA-201604-03.NASL description The remote host is affected by the vulnerability described in GLSA-201604-03 (Xen: Multiple vulnerabilities) Multiple vulnerabilities have been discovered in Xen. Please review the CVE identifiers referenced below for details. Impact : A local attacker could possibly cause a Denial of Service condition or obtain sensitive information. Workaround : There is no known workaround at this time. last seen 2020-06-01 modified 2020-06-02 plugin id 90380 published 2016-04-07 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/90380 title GLSA-201604-03 : Xen: Multiple vulnerabilities (Venom) NASL family SuSE Local Security Checks NASL id SUSE_SU-2015-2306-1.NASL description This update fixes the following security issues : - bsc#956832 - CVE-2015-8345: xen: qemu: net: eepro100: infinite loop in processing command block list - bsc#956408 - CVE-2015-8339, CVE-2015-8340: xen: XENMEM_exchange error handling issues (XSA-159) xsa159.patch - bsc#956411 - CVE-2015-7504: xen: heap buffer overflow vulnerability in pcnet emulator (XSA-162) - bsc#954405 - CVE-2015-8104: Xen: guest to host DoS by triggering an infinite loop in microcode via #DB exception - bsc#953527 - CVE-2015-5307: kernel: kvm/xen: x86: avoid guest->host DOS by intercepting #AC (XSA-156) - bsc#950704 - CVE-2015-7970: xen: x86: Long latency populate-on-demand operation is not preemptible (XSA-150) - bsc#951845 - CVE-2015-7972: xen: x86: populate-on-demand balloon size inaccuracy can crash guests (XSA-153) - bsc#950703 - CVE-2015-7969: xen: leak of main per-domain vcpu pointer array (DoS) (XSA-149) - bsc#950705 - CVE-2015-7969: xen: x86: leak of per-domain profiling-related vcpu pointer array (DoS) (XSA-151) - bsc#950706 - CVE-2015-7971: xen: x86: some pmu and profiling hypercalls log without rate limiting (XSA-152) Note that Tenable Network Security has extracted the preceding description block directly from the SUSE security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 87528 published 2015-12-21 reporter This script is Copyright (C) 2015-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/87528 title SUSE SLES11 Security Update : xen (SUSE-SU-2015:2306-1) NASL family Debian Local Security Checks NASL id DEBIAN_DSA-3469.NASL description Several vulnerabilities were discovered in qemu, a full virtualization solution on x86 hardware. - CVE-2015-7295 Jason Wang of Red Hat Inc. discovered that the Virtual Network Device support is vulnerable to denial-of-service (via resource exhaustion), that could occur when receiving large packets. - CVE-2015-7504 Qinghao Tang of Qihoo 360 Inc. and Ling Liu of Qihoo 360 Inc. discovered that the PC-Net II ethernet controller is vulnerable to a heap-based buffer overflow that could result in denial-of-service (via application crash) or arbitrary code execution. - CVE-2015-7512 Ling Liu of Qihoo 360 Inc. and Jason Wang of Red Hat Inc. discovered that the PC-Net II ethernet controller is vulnerable to a buffer overflow that could result in denial-of-service (via application crash) or arbitrary code execution. - CVE-2015-8345 Qinghao Tang of Qihoo 360 Inc. discovered that the eepro100 emulator contains a flaw that could lead to an infinite loop when processing Command Blocks, eventually resulting in denial-of-service (via application crash). - CVE-2015-8504 Lian Yihan of Qihoo 360 Inc. discovered that the VNC display driver support is vulnerable to an arithmetic exception flaw that could lead to denial-of-service (via application crash). - CVE-2015-8558 Qinghao Tang of Qihoo 360 Inc. discovered that the USB EHCI emulation support contains a flaw that could lead to an infinite loop during communication between the host controller and a device driver. This could lead to denial-of-service (via resource exhaustion). - CVE-2015-8743 Ling Liu of Qihoo 360 Inc. discovered that the NE2000 emulator is vulnerable to an out-of-bound read/write access issue, potentially resulting in information leak or memory corruption. - CVE-2016-1568 Qinghao Tang of Qihoo 360 Inc. discovered that the IDE AHCI emulation support is vulnerable to a use-after-free issue, that could lead to denial-of-service (via application crash) or arbitrary code execution. - CVE-2016-1714 Donghai Zhu of Alibaba discovered that the Firmware Configuration emulation support is vulnerable to an out-of-bound read/write access issue, that could lead to denial-of-service (via application crash) or arbitrary code execution. - CVE-2016-1922 Ling Liu of Qihoo 360 Inc. discovered that 32-bit Windows guests support is vulnerable to a NULL pointer dereference issue, that could lead to denial-of-service (via application crash). last seen 2020-06-01 modified 2020-06-02 plugin id 88628 published 2016-02-09 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/88628 title Debian DSA-3469-1 : qemu - security update NASL family CentOS Local Security Checks NASL id CENTOS_RHSA-2015-2694.NASL description Updated qemu-kvm packages that fix two security issues are now available for Red Hat Enterprise Linux 6. Red Hat Product Security has rated this update as having Important security impact. Common Vulnerability Scoring System (CVSS) base scores, which give detailed severity ratings, are available for each vulnerability from the CVE links in the References section. KVM (Kernel-based Virtual Machine) is a full virtualization solution for Linux on AMD64 and Intel 64 systems. The qemu-kvm package provides the user-space component for running virtual machines using KVM. A heap-based buffer overflow flaw was discovered in the way QEMU last seen 2020-06-01 modified 2020-06-02 plugin id 87604 published 2015-12-29 reporter This script is Copyright (C) 2015-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/87604 title CentOS 6 : qemu-kvm (CESA-2015:2694) NASL family Fedora Local Security Checks NASL id FEDORA_2015-2773B85B49.NASL description - Fix SSE4 emulation with accel=tcg (bz #1270703) * CVE-2015-8345: Fix infinite loop in eepro100 (bz #1285214) * CVE-2015-7504: Fix heap overflow in pcnet (bz #1286543) * CVE-2015-7512: Fix buffer overflow in pcnet (bz #1286549) Note that Tenable Network Security has extracted the preceding description block directly from the Fedora security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-05 modified 2016-03-04 plugin id 89181 published 2016-03-04 reporter This script is Copyright (C) 2016-2020 Tenable Network Security, Inc. source https://www.tenable.com/plugins/nessus/89181 title Fedora 23 : qemu-2.4.1-2.fc23 (2015-2773b85b49) NASL family Red Hat Local Security Checks NASL id REDHAT-RHSA-2015-2696.NASL description Updated qemu-kvm-rhev packages that fix two security issues are now available for Red Hat Enterprise Virtualization. Red Hat Product Security has rated this update as having Important security impact. Common Vulnerability Scoring System (CVSS) base scores, which give detailed severity ratings, are available for each vulnerability from the CVE links in the References section. KVM (Kernel-based Virtual Machine) is a full virtualization solution for Linux on AMD64 and Intel 64 systems. The qemu-kvm-rhev package provides the user-space component for running virtual machines using KVM. A heap-based buffer overflow flaw was discovered in the way QEMU last seen 2020-06-01 modified 2020-06-02 plugin id 87664 published 2015-12-30 reporter This script is Copyright (C) 2015-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/87664 title RHEL 6 : qemu-kvm-rhev (RHSA-2015:2696) NASL family SuSE Local Security Checks NASL id SUSE_SU-2015-2326-1.NASL description This update fixes the following security issues : - bsc#956832 - CVE-2015-8345: xen: qemu: net: eepro100: infinite loop in processing command block list - bsc#956592 - xen: virtual PMU is unsupported (XSA-163) - bsc#956408 - CVE-2015-8339, CVE-2015-8340: xen: XENMEM_exchange error handling issues (XSA-159) - bsc#956409 - CVE-2015-8341: xen: libxl leak of pv kernel and initrd on error (XSA-160) - bsc#956411 - CVE-2015-7504: xen: heap buffer overflow vulnerability in pcnet emulator (XSA-162) - bsc#947165 - CVE-2015-7311: xen: libxl fails to honour readonly flag on disks with qemu-xen (xsa-142) - bsc#954405 - CVE-2015-8104: Xen: guest to host DoS by triggering an infinite loop in microcode via #DB exception - bsc#954018 - CVE-2015-5307: xen: x86: CPU lockup during fault delivery (XSA-156) - bsc#950704 - CVE-2015-7970: xen: x86: Long latency populate-on-demand operation is not preemptible (XSA-150) - bsc#951845 - CVE-2015-7972: xen: x86: populate-on-demand balloon size inaccuracy can crash guests (XSA-153) - bsc#950703 - CVE-2015-7969: xen: leak of main per-domain vcpu pointer array (DoS) (XSA-149) - bsc#950705 - CVE-2015-7969: xen: x86: leak of per-domain profiling-related vcpu pointer array (DoS) (XSA-151) - bsc#950706 - CVE-2015-7971: xen: x86: some pmu and profiling hypercalls log without rate limiting (XSA-152) Note that Tenable Network Security has extracted the preceding description block directly from the SUSE security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 87590 published 2015-12-22 reporter This script is Copyright (C) 2015-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/87590 title SUSE SLED11 / SLES11 Security Update : xen (SUSE-SU-2015:2326-1) NASL family SuSE Local Security Checks NASL id OPENSUSE-2016-35.NASL description This update for xen fixes the following security issues : - CVE-2015-8568 CVE-2015-8567: xen: qemu: net: vmxnet3: host memory leakage (boo#959387) - CVE-2015-8550: xen: paravirtualized drivers incautious about shared memory contents (XSA-155, boo#957988) - CVE-2015-8558: xen: qemu: usb: infinite loop in ehci_advance_state results in DoS (boo#959006) - CVE-2015-7549: xen: qemu pci: NULL pointer dereference issue (boo#958918) - CVE-2015-8504: xen: qemu: ui: vnc: avoid floating point exception (boo#958493) - CVE-2015-8554: xen: qemu-dm buffer overrun in MSI-X handling (XSA-164, boo#958007) - CVE-2015-8555: xen: information leak in legacy x86 FPU/XMM initialization (XSA-165, boo#958009) - boo#958523: xen: ioreq handling possibly susceptible to multiple read issue (XSA-166) - CVE-2015-5307: xen: x86: CPU lockup during fault delivery (XSA-156, boo#954018) - CVE-2015-8345: xen: qemu: net: eepro100: infinite loop in processing command block list (boo#956832) - boo#956592: xen: virtual PMU is unsupported (XSA-163) - CVE-2015-8339, CVE-2015-8340: xen: XENMEM_exchange error handling issues (XSA-159, boo#956408) - CVE-2015-8341: xen: libxl leak of pv kernel and initrd on error (XSA-160, boo#956409) - CVE-2015-7504: xen: heap buffer overflow vulnerability in pcnet emulator (XSA-162, boo#956411) last seen 2020-06-05 modified 2016-01-25 plugin id 88125 published 2016-01-25 reporter This script is Copyright (C) 2016-2020 Tenable Network Security, Inc. source https://www.tenable.com/plugins/nessus/88125 title openSUSE Security Update : xen (openSUSE-2016-35) NASL family SuSE Local Security Checks NASL id SUSE_SU-2015-2328-1.NASL description This update fixes the following security issues : - bsc#956832 - CVE-2015-8345: xen: qemu: net: eepro100: infinite loop in processing command block list - bsc#956592 - xen: virtual PMU is unsupported (XSA-163) - bsc#956408 - CVE-2015-8339, CVE-2015-8340: xen: XENMEM_exchange error handling issues (XSA-159) - bsc#956409 - CVE-2015-8341: xen: libxl leak of pv kernel and initrd on error (XSA-160) - bsc#956411 - CVE-2015-7504: xen: heap buffer overflow vulnerability in pcnet emulator (XSA-162) - bsc#947165 - CVE-2015-7311: xen: libxl fails to honour readonly flag on disks with qemu-xen (xsa-142) - bsc#954405 - CVE-2015-8104: Xen: guest to host DoS by triggering an infinite loop in microcode via #DB exception - bsc#954018 - CVE-2015-5307: xen: x86: CPU lockup during fault delivery (XSA-156) CVE-2015-5307-xsa156.patch - bsc#950704 - CVE-2015-7970: xen: x86: Long latency populate-on-demand operation is not preemptible (XSA-150) 563212c9-x86-PoD-Eager-sweep-for-zeroed-pages.patch - bsc#951845 - CVE-2015-7972: xen: x86: populate-on-demand balloon size inaccuracy can crash guests (XSA-153) xsa153-libxl.patch xend-xsa153.patch - Drop 5604f239-x86-PV-properly-populate-descriptor-tables.patc h - bsc#950703 - CVE-2015-7969: xen: leak of main per-domain vcpu pointer array (DoS) (XSA-149) - bsc#950705 - CVE-2015-7969: xen: x86: leak of per-domain profiling-related vcpu pointer array (DoS) (XSA-151) - bsc#950706 - CVE-2015-7971: xen: x86: some pmu and profiling hypercalls log without rate limiting (XSA-152) Note that Tenable Network Security has extracted the preceding description block directly from the SUSE security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 87591 published 2015-12-22 reporter This script is Copyright (C) 2015-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/87591 title SUSE SLED12 / SLES12 Security Update : xen (SUSE-SU-2015:2328-1)
Redhat
| advisories |
| ||||||||||||
| rpms |
|
Seebug
| bulletinFamily | exploit |
| description | 目前厂商已经发布了升级补丁以修复这个安全问题,请到厂商的主页下载: https://lists.gnu.org/archive/html/qemu-devel/2015-11/msg06342.html pcnet是虚拟化软件QEMU中实现AMD PCNET网卡功能模拟的组件,相关的代码实现位于/hw/net/pcnet.c中。 在qemu软件中使用pcnet网卡,需要如下的命令行进行配置: ``` qemu-system-x86_64 centos-6.5-x64.img -m 1024 - net nic,model=pcnet -net user ``` 该漏洞发生在pcnet网卡模块的接收数据包的过程中,相关函数pcnet_receive的执行逻辑:首先检测CSR_DRX(s),CSR_STOP(s),CSR_SPND(s),size,CSR_LOOP(s),s->looptest这些值是否符合边界要求,确定函数是否继续处理。并且如果buf太小,则把它扩充到MIN_BUF_SIZE,之后检测是否要接受此包。最终把数据拷到rmd中物理地址中。相关代码截图如下: 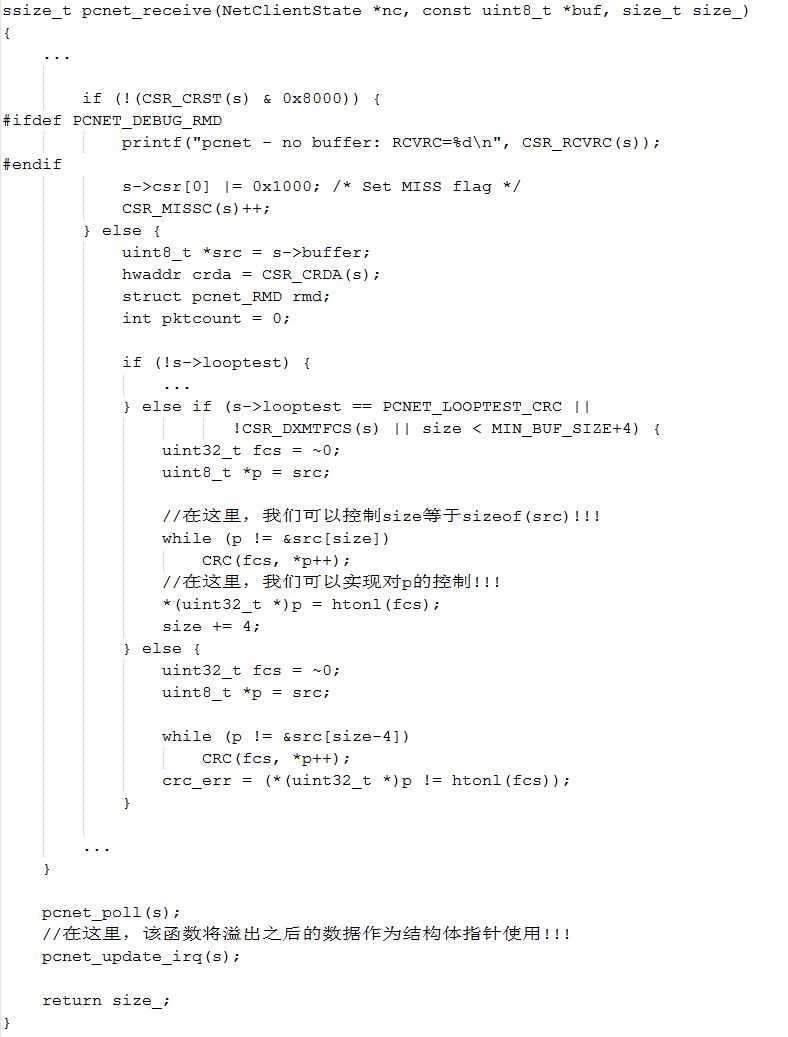 在上述代码中,我们可以看到,在实现数据包buffer操作的逻辑时,程序员出现了一个明显的错误:未判断数据包的长度是否已经等于buffer长度。另外,在pcnet.c的另一个函数pcnet_transmit中也有对缓冲区位置和数据包长度的处理,截图如下: 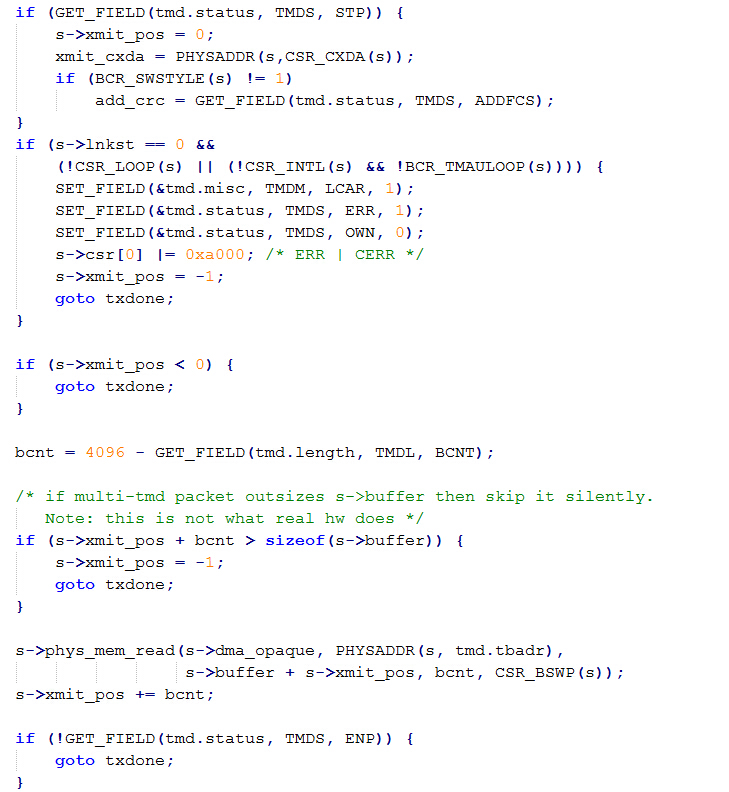 如果数据包长度临近缓冲区长度(4096)时,由于代码逻辑会自动添加4个字节的crc值,因此就会发生缓冲区溢出。 巧合的是溢出了buffer之后的四个字节恰好会覆盖一个结构体指针。如图所示: 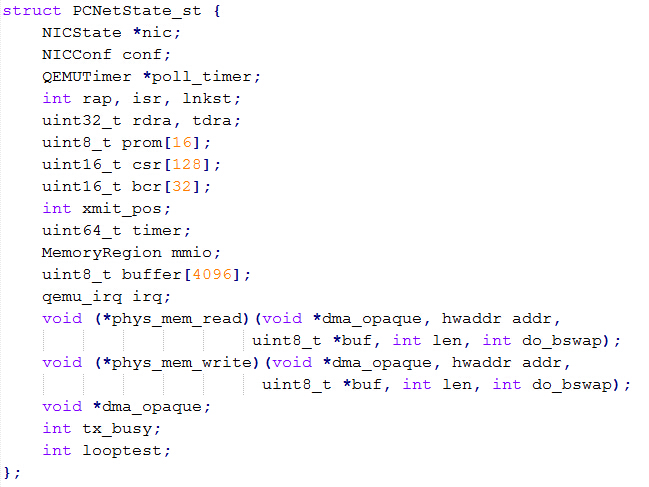 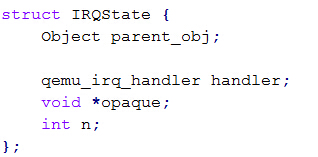 在溢出发生之后,代码流程进入pcnet_update_irq函数中,该函数经过层层调用,最终使用了irq->handler作为函数指针!!!而该irq的结构体指针我们可以对其进行控制,因此就完成了对代码逻辑的劫持。 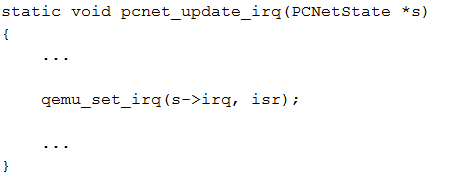 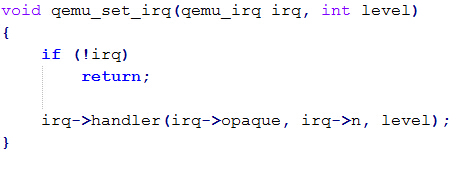 |
| id | SSV:90067 |
| last seen | 2017-11-19 |
| modified | 2015-12-10 |
| published | 2015-12-10 |
| reporter | Root |
| title | QEMU pcnet_receive 堆缓冲区溢出漏洞(CVE-2015-7504) |
References
- http://rhn.redhat.com/errata/RHSA-2015-2694.html
- http://rhn.redhat.com/errata/RHSA-2015-2694.html
- http://rhn.redhat.com/errata/RHSA-2015-2695.html
- http://rhn.redhat.com/errata/RHSA-2015-2695.html
- http://rhn.redhat.com/errata/RHSA-2015-2696.html
- http://rhn.redhat.com/errata/RHSA-2015-2696.html
- http://www.debian.org/security/2016/dsa-3469
- http://www.debian.org/security/2016/dsa-3469
- http://www.debian.org/security/2016/dsa-3470
- http://www.debian.org/security/2016/dsa-3470
- http://www.debian.org/security/2016/dsa-3471
- http://www.debian.org/security/2016/dsa-3471
- http://www.openwall.com/lists/oss-security/2015/11/30/2
- http://www.openwall.com/lists/oss-security/2015/11/30/2
- http://www.securityfocus.com/bid/78227
- http://www.securityfocus.com/bid/78227
- http://www.securitytracker.com/id/1034268
- http://www.securitytracker.com/id/1034268
- http://xenbits.xen.org/xsa/advisory-162.html
- http://xenbits.xen.org/xsa/advisory-162.html
- https://lists.gnu.org/archive/html/qemu-devel/2015-11/msg06342.html
- https://lists.gnu.org/archive/html/qemu-devel/2015-11/msg06342.html
- https://security.gentoo.org/glsa/201602-01
- https://security.gentoo.org/glsa/201602-01
- https://security.gentoo.org/glsa/201604-03
- https://security.gentoo.org/glsa/201604-03