Security News

The botnet behind the largest HTTPS distributed denial-of-service attack in June 2022 has been linked to a spate of attacks aimed at nearly 1,000 Cloudflare customers. Calling the powerful botnet Mantis, the web performance and security company attributed it to more than 3,000 HTTP DDoS attacks against its users.

The botnet behind the largest-ever HTTPS-based distributed-denial-of-service attack is now named after a tiny shrimp. While Mantis initially launched its network-flooding-traffic attack over HTTPS, in the month since its discovery, Mantis has launched more than 3,000 HTTP DDoS attacks against the firm's customers, Yoachimik added.
The record-breaking distributed denial-of-service attack that Cloudflare mitigated last month originated from a new botnet called Mantis, which is currently described as "The most powerful botnet to date." The previous record was held by Mēris botnet, which launched an attack that spiked at 21.8 million requests per second.

Norway's National Security Authority published a statement yesterday warning that some of the country's most important websites and online services are being rendered inaccessible due to distributed denial of service attacks. DDoS attacks are a special type of cyberattack that causes internet servers to be overwhelmed by many requests and garbage traffic, rendering the hosted sites and services inaccessible for legitimate visitors and users.

Russia-linked cyber collective Killnet has claimed responsibility for DDoS attacks Monday on the Lithuanian government and other entities in the Baltic country over closure of transit routes within the Russian exclave of Kaliningrad, according to researchers. On Monday, Lithuania's National Cyber Security Center under the Ministry of National Defense warned of intense and ongoing DDoS attacks against Lithuania's Secure National Data Transfer Network as well as other governmental institutions and private companies in the country.

The National Cyber Security Center of Lithuania has issued a public warning about a steep increase in distributed denial of service attacks directed against public authorities in the country. DDoS is a special type of cyberattack that causes internet servers to be overwhelmed by a large number of requests and garbage traffic, rendering the hosted sites and services inaccessible for legitimate visitors and users.

Cloudflare said it this month staved off another record-breaking HTTPS-based distributed denial-of-service attack, this one significantly larger than the previous largest DDoS attack that occurred only two months ago. In April, the biz said it mitigated an HTTPS DDoS attack that reached a peak of 15.3 million requests-per-second.
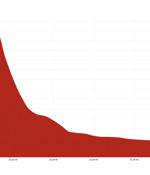
Cloudflare on Tuesday disclosed that it had acted to prevent a record-setting 26 million request per second distributed denial-of-service attack last week, making it the largest HTTPS DDoS attack detected to date. The web performance and security company said the attack was directed against an unnamed customer website using its Free plan and emanated from a "Powerful" botnet of 5,067 devices, with each node generating approximately 5,200 RPS at peak.

A 33-year-old Illinois man has been sentenced to two years in prison for running websites that paying customers used to launch more than 200,000 distributed denial-of-services attacks. Gatrel, was convicted of owning and operating two websites - DownThem.org and AmpNode.com - that sold DDoS attacks.

An Illinois man was sentenced to two years in prison for operating a distributed denial of service platform that allowed threat actors to conduct over 200,000 attacks. The sentenced man, Matthew Gatrel, 33, had created and operated the websites "Downthem.org" and "Ampnode.com." The former sold subscriptions to a powerful DDoS arsenal, and the latter was a bulletproof hosting service that also aided customers in launching their own DDoS attacks.