Security News > 2024 > August > Multi-Stage ValleyRAT Targets Chinese Users with Advanced Tactics
Chinese-speaking users are the target of an ongoing campaign that distributes malware known as ValleyRAT. "ValleyRAT is a multi-stage malware that utilizes diverse techniques to monitor and control its victims and deploy arbitrary plugins to cause further damage," Fortinet FortiGuard Labs researchers Eduardo Altares and Joie Salvio said.
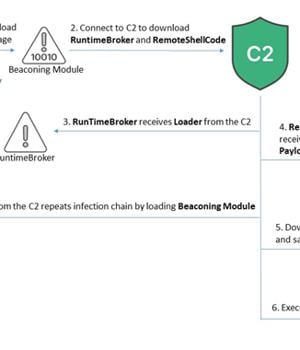
The attack sequence is a multi-stage process that starts with a first-stage loader that impersonates legitimate applications like Microsoft Office to make them appear harmless.
Launching the executable causes the decoy document to be dropped and the shellcode to be loaded for advancing to the next phase of the attack.
The second method used for privilege escalation concerns the abuse of the CMSTPLUA COM interface, a technique previously adopted by threat actors connected to the Avaddon ransomware and also observed in recent Hijack Loader campaigns.
RuntimeBroker's primary task is to retrieve from the C2 server a component named Loader, which functions the same way as the first-stage loader and executes the beaconing module to repeat the infection process.
The Loader payload also exhibits some distinct characteristics, including carrying out checks to see if it's running in a sandbox and scanning the Windows Registry for keys related to apps like Tencent WeChat and Alibaba DingTalk, reinforcing the hypothesis that the malware exclusively targets Chinese systems.
News URL
https://thehackernews.com/2024/08/multi-stage-valleyrat-targets-chinese.html