Security News > 2024 > July > APT41 Infiltrates Networks in Italy, Spain, Taiwan, Turkey, and the U.K.
"APT41 successfully infiltrated and maintained prolonged, unauthorized access to numerous victims' networks since 2023, enabling them to extract sensitive data over an extended period," Google-owned Mandiant said in a new report published Thursday.
Attack chains involve the use of web shells, custom droppers, and publicly available tools to achieve persistence, deliver additional payloads, and exfiltrate data of interest.
The web shells act as a conduit to download the DUSTPAN dropper that's responsible for loading Cobalt Strike Beacon for command-and-control communication, followed by the deployment of the DUSTTRAP dropper post lateral movement.
The intrusions are also characterized by the use of SQLULDR2 to export data from Oracle Databases to a local text-based file and PINEGROVE to transmit large volumes of sensitive data from compromised networks by abusing Microsoft OneDrive as an exfiltration vector.
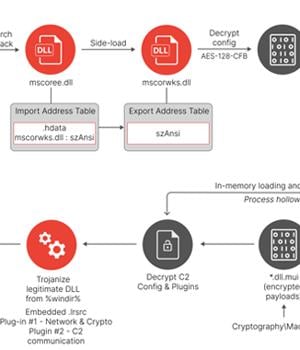
"DUSTTRAP is a multi-stage plugin framework with multiple components," Mandiant researchers said, adding it identified at least 15 plugins that are capable of executing shell commands, carrying out file system operations, enumerating and terminating processes, capturing keystrokes and screenshots, gathering system information, and modifying Windows Registry.
"The DUSTTRAP malware and its associated components that were observed during the intrusion were code signed with presumably stolen code signing certificates," the company said.
News URL
https://thehackernews.com/2024/07/apt41-infiltrates-networks-in-italy.html