Security News > 2024 > July > Alert: HotPage Adware Disguised as Ad Blocker Installs Malicious Kernel Driver
Cybersecurity researchers have shed light on an adware module that purports to block ads and malicious websites, while stealthily offloading a kernel driver component that grants attackers the ability to run arbitrary code with elevated permissions on Windows hosts.
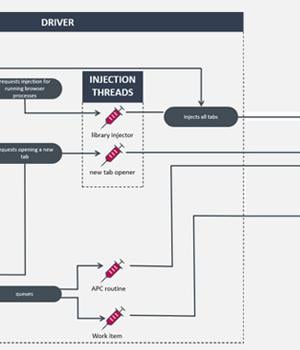
The malware, dubbed HotPage, gets its name from the eponymous installer, according to new findings from ESET. The installer "Deploys a driver capable of injecting code into remote processes, and two libraries capable of intercepting and tampering with browsers' network traffic," ESET researcher Romain Dumont said in a technical analysis published today.
The absence of any access control lists for the driver meant that an attacker with a non-privileged account could leverage it to obtain elevated privileges and run code as the NT AUTHORITYSystem account.
The embedded driver is notable for the fact that it's signed by Microsoft.
The Chinese company is believed to have gone through Microsoft's driver code signing requirements and managed to obtain an Extended Verification certificate.
Kernel-mode drivers have been required to be digitally signed to be loaded by the Windows operating system, an important layer of defense erected by Microsoft to protect against malicious drivers that could be weaponized to subvert security controls and interfere with system processes.
News URL
https://thehackernews.com/2024/07/alert-hotpage-adware-disguised-as-ad.html