Security News > 2024 > July > China-linked APT17 Targets Italian Companies with 9002 RAT Malware
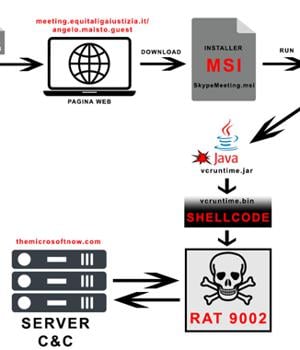
A China-linked threat actor called APT17 has been observed targeting Italian companies and government entities using a variant of a known malware referred to as 9002 RAT. The two targeted attacks took place on June 24 and July 2, 2024, Italian cybersecurity company TG Soft said in an analysis published last week.
"The first campaign on June 24, 2024 used an Office document, while the second campaign contained a link," the company noted.
"Both campaigns invited the victim to install a Skype for Business package from a link of an Italian government-like domain to convey a variant of 9002 RAT.".
APT17 was first documented by Google-owned Mandiant in 2013 as part of cyber espionage operations called DeputyDog and Ephemeral Hydra that leveraged zero-day flaws in Microsoft's Internet Explorer to breach targets of interest.
9002 RAT, aka Hydraq and McRAT, achieved notoriety as the cyber weapon of choice in Operation Aurora that singled out Google and other large companies in 2009.
The Java application, in turn, decrypts and executes the shellcode responsible for launching 9002 RAT. A modular trojan, 9002 RAT comes with features to monitor network traffic, capture screenshots, enumerate files, manage processes, and run additional commands received from a remote server to facilitate network discovery, among others.
News URL
https://thehackernews.com/2024/07/china-linked-apt17-targets-italian.html