Security News > 2024 > July > FakeBat Loader Malware Spreads Widely Through Drive-by Download Attacks
2024-07-03 07:05
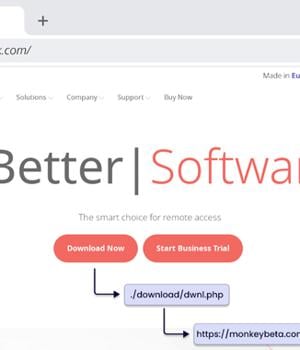
The loader-as-a-service (LaaS) known as FakeBat has become one of the most widespread loader malware families distributed using the drive-by download technique this year, findings from Sekoia reveal. "FakeBat primarily aims to download and execute the next-stage payload, such as IcedID, Lumma, RedLine, SmokeLoader, SectopRAT, and Ursnif," the company said in a Tuesday analysis. Drive-by attacks
News URL
https://thehackernews.com/2024/07/fakebat-loader-malware-spreads-widely.html
Related news
- ⚡ THN Weekly Recap: GitHub Supply Chain Attack, AI Malware, BYOVD Tactics, and More (source)
- Chinese FamousSparrow hackers deploy upgraded malware in attacks (source)
- Open-source malware doubles, data exfiltration attacks dominate (source)
- Microsoft Warns of Tax-Themed Email Attacks Using PDFs and QR Codes to Deliver Malware (source)
- New TCESB Malware Found in Active Attacks Exploiting ESET Security Scanner (source)
- Multi-Stage Malware Attack Uses .JSE and PowerShell to Deploy Agent Tesla and XLoader (source)
- New Android malware steals your credit cards for NFC relay attacks (source)
- Hackers Abuse Russian Bulletproof Host Proton66 for Global Attacks and Malware Delivery (source)
- SuperCard X Android Malware Enables Contactless ATM and PoS Fraud via NFC Relay Attacks (source)
- SK Telecom warns customer USIM data exposed in malware attack (source)