Security News > 2023 > August > Understanding Active Directory Attack Paths to Improve Security
In 2022, our in-house research found that 73% of the top attack techniques used in the compromising of critical assets involved mismanaged or stolen credentials - and more than half of the attacks in organizations include some element of Active Directory compromise.
So now let's take a look into the anatomy of 3 actual Active Directory attack paths and see how attackers made their way through this environment.
Once they saw this, they finally understood their Active Directory security approach needed to level-up so they locked down and hardened their security practices.
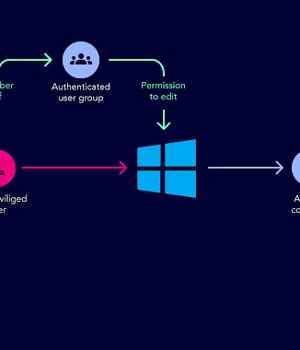
The attacker then had the permissions to add themselves to a group so they could add the compromised Active Directory user to an Active Directory helpdesk group.
By understanding these actual real-world attack paths, organizations can start to see what their Active Directory and AD Azure environments look like from the attacker's point of view.
By getting a comprehensive view of the attack paths that exist in Active Directory across on-prem and cloud environments, organizations can learn how attackers move laterally with a context-based understanding of their environment - giving them visibility into how issues can combine to facilitate attacks and impersonate users, escalate privileges, and gain access to cloud environments.
News URL
https://thehackernews.com/2023/08/understanding-active-directory-attack.html