Security News > 2023 > July > New SOHO Router Botnet AVrecon Spreads to 70,000 Devices Across 20 Countries
A new malware strain has been found covertly targeting small office/home office routers for more than two years, infiltrating over 70,000 devices and creating a botnet with 40,000 nodes spanning 20 countries.
Lumen Black Lotus Labs has dubbed the malware AVrecon, making it the third such strain to focus on SOHO routers after ZuoRAT and HiatusRAT over the past year.
"This makes AVrecon one of the largest SOHO router-targeting botnets ever seen," the company said.
AVrecon was first highlighted by Kaspersky senior security researcher Ye Jin in May 2021, indicating that the malware has managed to avoid detection until now.
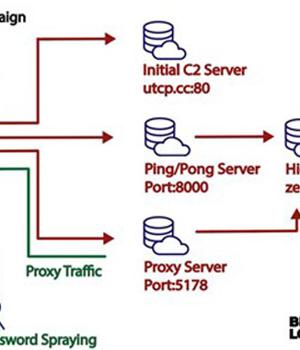
In the attack chain detailed by Lumen, a successful infection is followed by enumerating the victim's SOHO router and exfiltrating that information back to an embedded command-and-control server.
AVrecon is written in the C programming language, making it easy to port the malware for different architectures.
News URL
https://thehackernews.com/2023/07/new-soho-router-botnet-avrecon-spreads.html