Security News > 2023 > May > Netgear Routers' Flaws Expose Users to Malware, Remote Attacks, and Surveillance
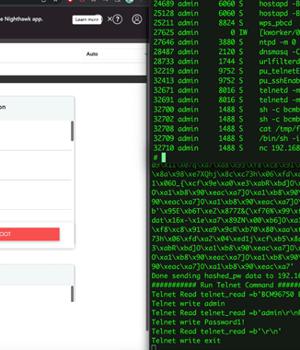
As many as five security flaws have been disclosed in Netgear RAX30 routers that could be chained to bypass authentication and achieve remote code execution.
"Successful exploits could allow attackers to monitor users' internet activity, hijack internet connections, and redirect traffic to malicious websites or inject malware into network traffic," Claroty security researcher Uri Katz said in a report.
A network-adjacent threat actor could also weaponize the flaws to access and control networked smart devices like security cameras, thermostats, smart locks; tamper with router settings, and even use a compromised network to launch attacks against other devices or networks.
A proof-of-concept exploit chain illustrated by the industrial cybersecurity firm shows that it's possible to string the flaws - CVE-2023-27357, CVE-2023-27369, CVE-2023-27368, CVE-2023-27370, and CVE-2023-27367 - to extract the device serial number and ultimately obtain root access to it.
"These five CVEs can be chained together to compromise affected RAX30 routers, the most severe of which enable pre-authentication remote code execution on the device," Katz noted.
Users of Netgear RAX30 routers are advised to update to firmware version 1.0.10.94 released by the networking company on April 7, 2023, to address the flaws and mitigate potential risks.
News URL
https://thehackernews.com/2023/05/netgear-routers-flaws-expose-users-to.html
Related news
- Netgear warns users to patch critical WiFi router vulnerabilities (source)
- Swap EOL Zyxel routers, upgrade Netgear ones! (source)
- New “whoAMI” Attack Exploits AWS AMI Name Confusion for Remote Code Execution (source)
- New Linux Malware ‘Auto-Color’ Grants Hackers Full Remote Access to Compromised Systems (source)
- Silver Fox APT Uses Winos 4.0 Malware in Cyber Attacks Against Taiwanese Organizations (source)
- ⚡ THN Weekly Recap: Router Hacks, PyPI Attacks, New Ransomware Decryptor, and More (source)
- ⚡ THN Weekly Recap: GitHub Supply Chain Attack, AI Malware, BYOVD Tactics, and More (source)
- Chinese FamousSparrow hackers deploy upgraded malware in attacks (source)
Related Vulnerability
| DATE | CVE | VULNERABILITY TITLE | RISK |
|---|---|---|---|
| 2024-05-03 | CVE-2023-27370 | Cleartext Storage of Sensitive Information vulnerability in Netgear Rax30 Firmware NETGEAR RAX30 Device Configuration Cleartext Storage Information Disclosure Vulnerability. | 5.7 |
| 2024-05-03 | CVE-2023-27369 | Out-of-bounds Write vulnerability in Netgear Rax30 Firmware NETGEAR RAX30 soap_serverd Stack-based Buffer Overflow Authentication Bypass Vulnerability. | 8.8 |
| 2024-05-03 | CVE-2023-27368 | Out-of-bounds Write vulnerability in Netgear Rax30 Firmware NETGEAR RAX30 soap_serverd Stack-based Buffer Overflow Authentication Bypass Vulnerability. | 8.8 |
| 2024-05-03 | CVE-2023-27367 | OS Command Injection vulnerability in Netgear Rax30 Firmware NETGEAR RAX30 libcms_cli Command Injection Remote Code Execution Vulnerability. | 8.0 |
| 2024-05-03 | CVE-2023-27357 | Missing Authentication for Critical Function vulnerability in Netgear Rax30 Firmware NETGEAR RAX30 GetInfo Missing Authentication Information Disclosure Vulnerability. | 6.5 |