Security News > 2023 > May > North Korea's ScarCruft Deploys RokRAT Malware via LNK File Infection Chains
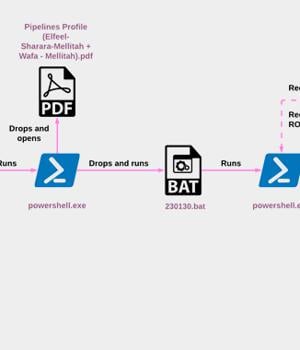
The North Korean threat actor known as ScarCruft began experimenting with oversized LNK files as a delivery route for RokRAT malware as early as July 2022, the same month Microsoft began blocking macros across Office documents by default.
Other bespoke malware used by the group include, but not limited to, Chinotto, BLUELIGHT, GOLDBACKDOOR, Dolphin, and, most recently, M2RAT. It's also known to use commodity malware such as Amadey, a downloader that can receive commands from the attacker to download additional malware, in a bid to confuse attribution.
The use of LNK files as decoys to activate the infection sequences was also highlighted by the AhnLab Security Emergency Response Center last week, with the files containing PowerShell commands that deploy the RokRAT malware.
Another attack wave observed at the beginning of November 2022, according to the Israeli cybersecurity company, employed ZIP archives incorporating LNK files to deploy the Amadey malware.
"APT37 continues to pose a considerable threat, launching multiple campaigns across the platforms and significantly improving its malware delivery methods."
The findings come as Kaspersky disclosed a new Go-based malware developed by ScarCruft codenamed SidLevel that utilizes the cloud messaging service Ably as a C2 mechanism for the first time and comes with "Extensive capabilities to steal sensitive information from victims."
News URL
https://thehackernews.com/2023/05/north-koreas-scarcruft-deploys-rokrat.html