Security News > 2023 > April > Tonto Team Uses Anti-Malware File to Launch Attacks on South Korean Institutions
Construction, diplomatic, and political institutions are at the receiving end of new attacks perpetrated by a China-aligned threat actor known as the Tonto Team.
"Recent cases have revealed that the group is using a file related to anti-malware products to ultimately execute their malicious attacks," the AhnLab Security Emergency Response Center said in a report published this week.
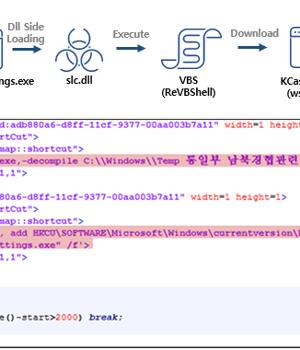
Earlier this year, the group was attributed to an unsuccessful phishing attack on cybersecurity company Group-IB. The attack sequence discovered by ASEC starts with a Microsoft Compiled HTML Help file that executes a binary file to side-load a malicious DLL file and launch ReVBShell, an open source VBScript backdoor also put to use by another Chinese threat actor called Tick.
"The Tonto Team is constantly evolving through various means such as using normal software for more elaborate attacks," ASEC said.
The use of CHM files as a distribution vector for malware is not limited to Chinese threat actors alone.
Similar attack chains have been adopted by a North Korean nation-state group known as ScarCruft in attacks aimed at its southern counterpart to backdoor targeted hosts.
News URL
https://thehackernews.com/2023/04/tonto-team-uses-anti-malware-file-to.html
Related news
- ⚡ THN Weekly Recap: GitHub Supply Chain Attack, AI Malware, BYOVD Tactics, and More (source)
- Chinese FamousSparrow hackers deploy upgraded malware in attacks (source)
- Open-source malware doubles, data exfiltration attacks dominate (source)
- Microsoft Warns of Tax-Themed Email Attacks Using PDFs and QR Codes to Deliver Malware (source)
- New TCESB Malware Found in Active Attacks Exploiting ESET Security Scanner (source)
- Multi-Stage Malware Attack Uses .JSE and PowerShell to Deploy Agent Tesla and XLoader (source)
- New Android malware steals your credit cards for NFC relay attacks (source)
- Hackers Abuse Russian Bulletproof Host Proton66 for Global Attacks and Malware Delivery (source)
- SuperCard X Android Malware Enables Contactless ATM and PoS Fraud via NFC Relay Attacks (source)
- SK Telecom warns customer USIM data exposed in malware attack (source)