Security News > 2023 > April > Google Uncovers APT41's Use of Open Source GC2 Tool to Target Media and Job Sites
A Chinese nation-state group targeted an unnamed Taiwanese media organization to deliver an open source red teaming tool known as Google Command and Control amid broader abuse of Google's infrastructure for malicious ends.
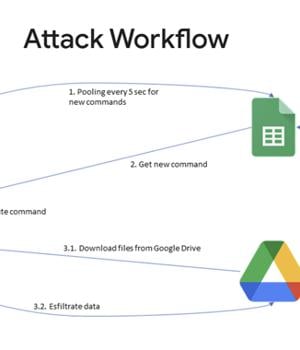
The starting point of the attack is a phishing email that contains links to a password-protected file hosted on Google Drive, which, in turn, incorporates the GC2 tool to read commands from Google Sheets and exfiltrate data using the cloud storage service.
"After installation on the victim machine, the malware queries Google Sheets to obtain attacker commands," Google's cloud division said in its sixth Threat Horizons Report.
Google said the threat actor previously utilized the same malware in July 2022 to target an Italian job search website.
Google further cautioned that the "Undeniable value of cloud services" have made them a lucrative target for cybercriminals and government-backed actors alike, "Either as hosts for malware or providing the infrastructure for command-and-control."
The findings come three months after Google Cloud detailed APT10's targeting of cloud infrastructure and VPN technologies to breach enterprise environments and exfiltrate data of interest.
News URL
https://thehackernews.com/2023/04/google-uncovers-apt41s-use-of-open.html