Security News > 2023 > April > FIN7 and Ex-Conti Cybercrime Gangs Join Forces in Domino Malware Attacks
A new strain of malware developed by threat actors likely affiliated with the FIN7 cybercrime group has been put to use by the members of the now-defunct Conti ransomware gang, indicating collaboration between the two crews.
The latest intrusion wave, spotted by IBM Security X-Force two months ago, involves the use of Dave Loader, a crypter previously attributed to the Conti group, to deploy the Domino backdoor.
Domino's potential connections to FIN7 comes from source code overlaps with DICELOADER, a time-tested malware family attributed to the group.
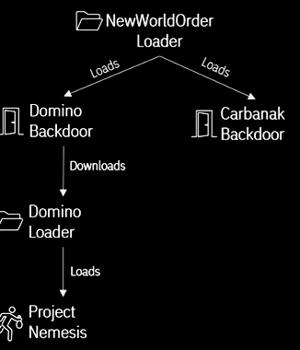
Another crucial link bridging Domino to FIN7 comes from December 2022 that leveraged another loader called NewWorldOrder Loader to deliver both the Domino and Carbanak backdoors.
In November 2022, Microsoft revealed intrusions mounted by a threat actor known as DEV-0569 that leveraged BATLOADER malware to deliver Vidar and Cobalt Strike, the latter of which eventually facilitated human-operated ransomware attacks distributing Royal ransomware.
"The use of malware with ties to multiple groups in a single campaign - such as Dave Loader, Domino Backdoor and Project Nemesis Infostealer - highlights the complexity involved in tracking threat actors but also provides insight into how and with whom they operate," Hammond concluded.
News URL
https://thehackernews.com/2023/04/fin7-and-ex-conti-cybercrime-gangs-join.html
Related news
- New TCESB Malware Found in Active Attacks Exploiting ESET Security Scanner (source)
- Multi-Stage Malware Attack Uses .JSE and PowerShell to Deploy Agent Tesla and XLoader (source)
- New Android malware steals your credit cards for NFC relay attacks (source)
- Hackers Abuse Russian Bulletproof Host Proton66 for Global Attacks and Malware Delivery (source)
- SuperCard X Android Malware Enables Contactless ATM and PoS Fraud via NFC Relay Attacks (source)
- SK Telecom warns customer USIM data exposed in malware attack (source)
- DslogdRAT Malware Deployed via Ivanti ICS Zero-Day CVE-2025-0282 in Japan Attacks (source)
- Malware Attack Targets World Uyghur Congress Leaders via Trojanized UyghurEdit++ Tool (source)
- Nebulous Mantis Targets NATO-Linked Entities with Multi-Stage Malware Attacks (source)
- Disney Slack attack wasn't Russian protesters, just a Cali dude with malware (source)