Security News > 2023 > March > KamiKakaBot Malware Used in Latest Dark Pink APT Attacks on Southeast Asian Targets
The Dark Pink advanced persistent threat actor has been linked to a fresh set of attacks targeting government and military entities in Southeast Asian countries with a malware called KamiKakaBot.
Dark Pink, also called Saaiwc, was first profiled by Group-IB earlier this year, describing its use of custom tools such as TelePowerBot and KamiKakaBot to run arbitrary commands and exfiltrate sensitive information.
"The latest attacks, which took place in February 2023, were almost identical to previous attacks," Dutch cybersecurity company EclecticIQ disclosed in a new report published last week.
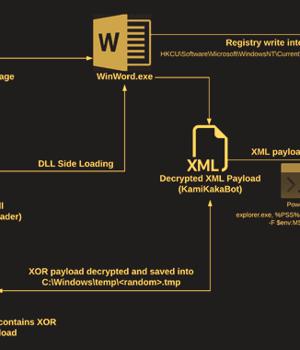
The attacks play out in the form of social engineering lures that contain ISO image file attachments in email messages to deliver the malware.
The ISO image includes an executable, a loader, and a decoy Microsoft Word document, the latter of which comes embedded with the KamiKakaBot payload. The loader, for its part, is designed to load the KamiKakaBot malware by leveraging the DLL side-loading method to evade security protections and load it into the memory of the Winword.
"The Dark Pink APT group is very likely a cyber espionage-motivated threat actor that specifically exploits relations between ASEAN and European nations to create phishing lures during the February 2023 campaign."
News URL
https://thehackernews.com/2023/03/kamikakabot-malware-used-in-latest-dark.html
Related news
- New TCESB Malware Found in Active Attacks Exploiting ESET Security Scanner (source)
- Multi-Stage Malware Attack Uses .JSE and PowerShell to Deploy Agent Tesla and XLoader (source)
- New Android malware steals your credit cards for NFC relay attacks (source)
- Hackers Abuse Russian Bulletproof Host Proton66 for Global Attacks and Malware Delivery (source)
- SuperCard X Android Malware Enables Contactless ATM and PoS Fraud via NFC Relay Attacks (source)
- SK Telecom warns customer USIM data exposed in malware attack (source)
- DslogdRAT Malware Deployed via Ivanti ICS Zero-Day CVE-2025-0282 in Japan Attacks (source)
- Malware Attack Targets World Uyghur Congress Leaders via Trojanized UyghurEdit++ Tool (source)
- Nebulous Mantis Targets NATO-Linked Entities with Multi-Stage Malware Attacks (source)
- Disney Slack attack wasn't Russian protesters, just a Cali dude with malware (source)