Security News > 2023 > March > Serious Security: TPM 2.0 vulns – is your super-secure data at risk?
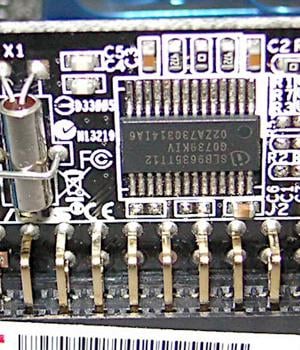
TPMs are sometimes implemented as a miniature plug-in board that plugs into a designated TPM socket on your computer's motherboard.
Hardware TPMs of this sort contain a tiny, dedicated coprocessor with its own secure storage that provides a range of security-related functionality, including hardware random number generation, trusted creation of crytographic keys, and secure digital signatures.
A software TPM can only be activated once your operating system has loaded, so you can't use this solution to install Windows 11 on a computer without a hardware-level or firmware-level TPM. Windows 11 insists that you have a TPM ready and active before Windows itself starts up.
One reason for forcing users to have a TPM is to secure the bootup process to stop attackers tampering with your BIOS or computer firmware and installing malware that loads before the operating system itself even gets going.
Who can be affected? Large Tech vendors[, and] organisations using Enterprise PCs, many servers and embedded systems that include a TPM. In fact, the official TPM Library 2.0 "Errata" bulletin lists numerous other bugs along with these two, but as far as we know, the vulnerabilities reported by Quarklab are the only two that received official CVE designation: CVE-2023-1017 and CVE-2023-1018.
Lenovo, for example, has already provided some information about products that include TPM code based on the reference implementation, and where to look for security bulletins to quantify your risk.
News URL
Related Vulnerability
| DATE | CVE | VULNERABILITY TITLE | RISK |
|---|---|---|---|
| 2023-02-28 | CVE-2023-1017 | Out-of-bounds Write vulnerability in multiple products An out-of-bounds write vulnerability exists in TPM2.0's Module Library allowing writing of a 2-byte data past the end of TPM2.0 command in the CryptParameterDecryption routine. | 7.8 |
| 2023-02-28 | CVE-2023-1018 | Out-of-bounds Read vulnerability in multiple products An out-of-bounds read vulnerability exists in TPM2.0's Module Library allowing a 2-byte read past the end of a TPM2.0 command in the CryptParameterDecryption routine. | 5.5 |