Security News > 2023 > January > Serious Security: The Samba logon bug caused by outdated crypto
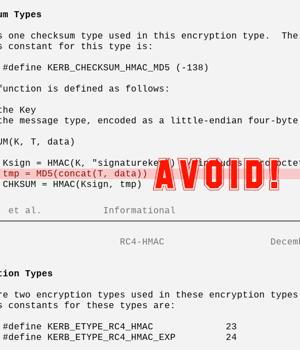
Astonishingly, the CVE-2022-38023 vulnerability existed in the first place because both Windows and Samba still supported a style of integrity protection based on the long-deprecated hashing algorithm MD5. Simply put, network authentication using Microsoft's version of the Kerberos protocol still allowed data to be integrity-protected using flawed cryptography.
Assuming a reliable algorithm, with no exploitable weaknesses, you'd expect that a hash with X bits of output would need about 2X-1 tries to find a second input that collided with the hash of an existing file.
If there are 2X different possible hash outputs, you'd hope to hit a 50:50 chance of finding an input with a specific, pre-determined hash after about half as many tries, and 2X/2 = 2X-1.
You can't easily go backwards from an MD5 hash to uncover anything about the specific input that produced it, which is another cryptographic promise that a reliable hash needs to keep.
Once the first hash is calculated, the key has a different set of bits flipped, gets prepended to that first hash value, and this new input data is hashed a second time.
Instead, the heart of the bug is line 11, where the data you're trying to hash so it can be authenticated is compressed into a fixed-length string.
News URL
Related news
Related Vulnerability
| DATE | CVE | VULNERABILITY TITLE | RISK |
|---|---|---|---|
| 2022-11-09 | CVE-2022-38023 | Netlogon RPC Elevation of Privilege Vulnerability | 0.0 |