Security News > 2021 > December > New Payment Data Stealing Malware Hides in Nginx Process on Linux Servers
E-commerce platforms in the U.S., Germany, and France have come under attack from a new form of malware that targets Nginx servers in an attempt to masquerade its presence and slip past detection by security solutions.
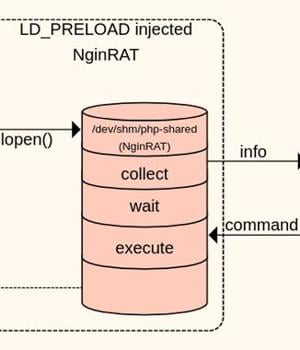
"This novel code injects itself into a host Nginx application and is nearly invisible," Sansec Threat Research team said in a new report.
NginRAT, as the advanced malware is called, works by hijacking a host Nginx application to embed itself into the webserver process.
Both CronRAT and NginRAT are designed to provide a remote way into the compromised servers, and the goal of the intrusions is to make server-side modifications to the compromised e-commerce websites in a manner that enable the adversaries to exfiltrate data by skimming online payment forms.
The attacks, collectively known as Magecart or web skimming, are the work of a cybercrime syndicate comprised of dozens of subgroups that are involved in digital credit card theft by exploiting software vulnerabilities to gain access to an online portal's source code and insert malicious JavaScript code that siphons the data shoppers enter into checkout pages.
"The latest techniques include compromising vulnerable versions of e-commerce platforms, hosting skimmer scripts on CDNs and cloud services, and using newly registered domains lexically close to any legitimate web service or specific e-commerce store to host malicious skimmer scripts."
News URL
https://thehackernews.com/2021/12/new-payment-data-sealing-malware-hides.html
Related news
- Outlaw Group Uses SSH Brute-Force to Deploy Cryptojacking Malware on Linux Servers (source)
- OPSEC Failure Exposes Coquettte’s Malware Campaigns on Bulletproof Hosting Servers (source)
- Police detains Smokeloader malware customers, seizes servers (source)
- Chinese Hackers Target Linux Systems Using SNOWLIGHT Malware and VShell Tool (source)
- New BPFDoor Controller Enables Stealthy Lateral Movement in Linux Server Attacks (source)
- Experts Uncover New XorDDoS Controller, Infrastructure as Malware Expands to Docker, Linux, IoT (source)
- Watch out for any Linux malware sneakily evading syscall-watching antivirus (source)
- Malicious Go Modules Deliver Disk-Wiping Linux Malware in Advanced Supply Chain Attack (source)
- Linux wiper malware hidden in malicious Go modules on GitHub (source)
- Go-Based Malware Deploys XMRig Miner on Linux Hosts via Redis Configuration Abuse (source)