Security News > 2021 > September > A New Jupyter Malware Version is Being Distributed via MSI Installers
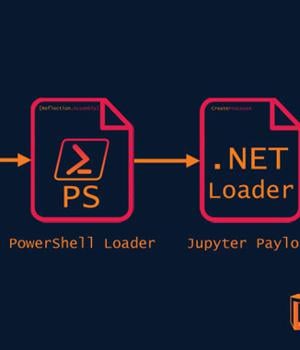
The new delivery chain, spotted by Morphisec on September 8, underscores that the malware has not just continued to remain active but also showcases "How threat actors continue to develop their attacks to become more efficient and evasive." The Israeli company said it's currently investigating the scale and scope of the attacks.
First documented in November 2020, Jupyter is likely Russian in origin and primarily targets Chromium, Firefox, and Chrome browser data, with additional capabilities that allow for full backdoor functionality, including features to siphon information and upload the details to a remote server and download and execute further payloads.
Forensic evidence gathered by Morphisec shows that multiple versions of Jupyter began emerging starting May 2020.
The attacks start with a deployment of an MSI installer payload that's over 100MB in size, allowing them to bypass anti-malware engines, and obfuscated using a third-party application packaging wizard called Advanced Installer.
The loader, in the final-stage, decodes and runs the in-memory Jupyter.
"The evolution of the Jupyter infostealer/backdoor from when we first identified it in 2020 proves the truth of the statement that threat actors are always innovating," Morphisec researcher Nadav Lorber said.