Security News > 2021 > January > A Set of Severe Flaws Affect Popular DNSMasq DNS Forwarder
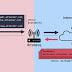
Dnsmasq, short for DNS masquerade, is a lightweight software with DNS forwarding capabilities used for locally caching DNS records, thus reducing the load on upstream nameservers and improving performance.
If the malicious answer with the right transaction ID from the attacker arrives before the response from the authoritative server, then the DNS cache would be effectively poisoned, returning the attacker's chosen IP address instead of the legitimate address for as long as the DNS response was valid.
The attacks - named "SAD DNS" or Side-channel AttackeD DNS - involves sending a burst of spoofed UDP packets to a DNS resolver, each sent over a different port, and subsequently using ICMP "Port Unreachable" messages as an indicator to discern if the rate limit has been met and eventually narrow down the exact source port from which the request originated.
Interestingly, the DNS cache poisoning attacks detailed by JSOF bear similarities to SAD DNS in that the three vulnerabilities aim to reduce the entropy of the Transaction IDs and source port that are required for a response to be accepted.
Even worse, these weaknesses can be chained with other network attacks such as SAD DNS and NAT Slipstreaming to mount multi-staged attacks against Dnsmasq resolvers listening on port 53.
"This highlight[s] the importance of DNS security in general and the security of DNS forwarders in particular. It also highlights the need to expedite the deployment of DNS security measures such as DNSSEC, DNS transport security, and DNS cookies."