Vulnerabilities > CVE-2017-9798 - Use After Free vulnerability in multiple products
Summary
Apache httpd allows remote attackers to read secret data from process memory if the Limit directive can be set in a user's .htaccess file, or if httpd.conf has certain misconfigurations, aka Optionsbleed. This affects the Apache HTTP Server through 2.2.34 and 2.4.x through 2.4.27. The attacker sends an unauthenticated OPTIONS HTTP request when attempting to read secret data. This is a use-after-free issue and thus secret data is not always sent, and the specific data depends on many factors including configuration. Exploitation with .htaccess can be blocked with a patch to the ap_limit_section function in server/core.c.
Vulnerable Configurations
Common Weakness Enumeration (CWE)
Exploit-Db
| description | Apache - HTTP OPTIONS Memory Leak. CVE-2017-9798. Webapps exploit for Linux platform |
| file | exploits/linux/webapps/42745.py |
| id | EDB-ID:42745 |
| last seen | 2017-09-18 |
| modified | 2017-09-18 |
| platform | linux |
| port | |
| published | 2017-09-18 |
| reporter | Exploit-DB |
| source | https://www.exploit-db.com/download/42745/ |
| title | Apache - HTTP OPTIONS Memory Leak |
| type | webapps |
Metasploit
| description | This module scans for the Apache optionsbleed vulnerability where the Allow response header returned from an OPTIONS request may bleed memory if the server has a .htaccess file with an invalid Limit method defined. |
| id | MSF:AUXILIARY/SCANNER/HTTP/APACHE_OPTIONSBLEED |
| last seen | 2020-06-12 |
| modified | 2018-08-27 |
| published | 2017-09-27 |
| references | |
| reporter | Rapid7 |
| source | https://github.com/rapid7/metasploit-framework/blob/master//modules/auxiliary/scanner/http/apache_optionsbleed.rb |
| title | Apache Optionsbleed Scanner |
Nessus
NASL family Red Hat Local Security Checks NASL id REDHAT-RHSA-2017-3113.NASL description An update is now available for Red Hat JBoss Enterprise Web Server 2.1.2 for RHEL 6 and Red Hat JBoss Enterprise Web Server 2.1.2 for RHEL 7. Red Hat Product Security has rated this update as having a security impact of Important. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. The httpd packages provide the Apache HTTP Server, a powerful, efficient, and extensible web server. OpenSSL is a toolkit that implements the Secure Sockets Layer (SSL) and Transport Layer Security (TLS) protocols, as well as a full-strength general-purpose cryptography library. Apache Tomcat is a servlet container for the Java Servlet and JavaServer Pages (JSP) technologies. This release provides an update to httpd, OpenSSL and Tomcat 6/7 for Red Hat JBoss Web Server 2.1.2. The updates are documented in the Release Notes document linked to in the References. This release of Red Hat JBoss Web Server 2.1.2 Service Pack 2 serves as a update for Red Hat JBoss Web Server 2, and includes bug fixes, which are documented in the Release Notes document linked to in the References. Users of Red Hat JBoss Web Server 2 should upgrade to these updated packages, which resolve several security issues. Security Fix(es) : * It was discovered that the httpd last seen 2020-06-01 modified 2020-06-02 plugin id 104456 published 2017-11-08 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/104456 title RHEL 6 / 7 : Red Hat JBoss Web Server (RHSA-2017:3113) (Optionsbleed) code # # (C) Tenable Network Security, Inc. # # The descriptive text and package checks in this plugin were # extracted from Red Hat Security Advisory RHSA-2017:3113. The text # itself is copyright (C) Red Hat, Inc. # include("compat.inc"); if (description) { script_id(104456); script_version("3.15"); script_cvs_date("Date: 2019/10/24 15:35:43"); script_cve_id("CVE-2016-2183", "CVE-2017-12615", "CVE-2017-12617", "CVE-2017-9788", "CVE-2017-9798"); script_xref(name:"RHSA", value:"2017:3113"); script_name(english:"RHEL 6 / 7 : Red Hat JBoss Web Server (RHSA-2017:3113) (Optionsbleed)"); script_summary(english:"Checks the rpm output for the updated packages"); script_set_attribute( attribute:"synopsis", value:"The remote Red Hat host is missing one or more security updates." ); script_set_attribute( attribute:"description", value: "An update is now available for Red Hat JBoss Enterprise Web Server 2.1.2 for RHEL 6 and Red Hat JBoss Enterprise Web Server 2.1.2 for RHEL 7. Red Hat Product Security has rated this update as having a security impact of Important. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. The httpd packages provide the Apache HTTP Server, a powerful, efficient, and extensible web server. OpenSSL is a toolkit that implements the Secure Sockets Layer (SSL) and Transport Layer Security (TLS) protocols, as well as a full-strength general-purpose cryptography library. Apache Tomcat is a servlet container for the Java Servlet and JavaServer Pages (JSP) technologies. This release provides an update to httpd, OpenSSL and Tomcat 6/7 for Red Hat JBoss Web Server 2.1.2. The updates are documented in the Release Notes document linked to in the References. This release of Red Hat JBoss Web Server 2.1.2 Service Pack 2 serves as a update for Red Hat JBoss Web Server 2, and includes bug fixes, which are documented in the Release Notes document linked to in the References. Users of Red Hat JBoss Web Server 2 should upgrade to these updated packages, which resolve several security issues. Security Fix(es) : * It was discovered that the httpd's mod_auth_digest module did not properly initialize memory before using it when processing certain headers related to digest authentication. A remote attacker could possibly use this flaw to disclose potentially sensitive information or cause httpd child process to crash by sending specially crafted requests to a server. (CVE-2017-9788) * A vulnerability was discovered in Tomcat where if a servlet context was configured with readonly=false and HTTP PUT requests were allowed, an attacker could upload a JSP file to that context and achieve code execution. (CVE-2017-12615) * A vulnerability was discovered in Tomcat where if a servlet context was configured with readonly=false and HTTP PUT requests were allowed, an attacker could upload a JSP file to that context and achieve code execution. (CVE-2017-12617) * A flaw was found in the way the DES/3DES cipher was used as part of the TLS /SSL protocol. A man-in-the-middle attacker could use this flaw to recover some plaintext data by capturing large amounts of encrypted traffic between TLS/SSL server and client if the communication used a DES/3DES based ciphersuite. (CVE-2016-2183) * A use-after-free flaw was found in the way httpd handled invalid and previously unregistered HTTP methods specified in the Limit directive used in an .htaccess file. A remote attacker could possibly use this flaw to disclose portions of the server memory, or cause httpd child process to crash. (CVE-2017-9798) Red Hat would like to thank OpenVPN for reporting CVE-2016-2183 and Hanno Bock for reporting CVE-2017-9798. Upstream acknowledges Karthikeyan Bhargavan (Inria) and Gaetan Leurent (Inria) as the original reporters of CVE-2016-2183. Bug Fix(es) : * Corruption in nodestatsmem in multiple core dumps but in different functions of each core dump. (BZ#1338640) * mod_cluster segfaults in process_info() due to wrongly generated assembler instruction movslq (BZ#1448709) * CRL checking of very large CRLs fails with OpenSSL 1.0.2 (BZ#1493075)" ); script_set_attribute( attribute:"see_also", value:"https://access.redhat.com/articles/3227901" ); script_set_attribute( attribute:"see_also", value:"https://access.redhat.com/errata/RHSA-2017:3113" ); script_set_attribute( attribute:"see_also", value:"https://access.redhat.com/security/cve/cve-2016-2183" ); script_set_attribute( attribute:"see_also", value:"https://access.redhat.com/security/cve/cve-2017-12615" ); script_set_attribute( attribute:"see_also", value:"https://access.redhat.com/security/cve/cve-2017-12617" ); script_set_attribute( attribute:"see_also", value:"https://access.redhat.com/security/cve/cve-2017-9788" ); script_set_attribute( attribute:"see_also", value:"https://access.redhat.com/security/cve/cve-2017-9798" ); script_set_attribute(attribute:"solution", value:"Update the affected packages."); script_set_cvss_base_vector("CVSS2#AV:N/AC:M/Au:N/C:P/I:P/A:P"); script_set_cvss_temporal_vector("CVSS2#E:F/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:F/RL:O/RC:C"); script_set_attribute(attribute:"exploitability_ease", value:"Exploits are available"); script_set_attribute(attribute:"exploit_available", value:"true"); script_set_attribute(attribute:"exploit_framework_core", value:"true"); script_set_attribute(attribute:"d2_elliot_name", value:"Apache Tomcat for Windows HTTP PUT Method File Upload"); script_set_attribute(attribute:"exploit_framework_d2_elliot", value:"true"); script_set_attribute(attribute:"metasploit_name", value:'Tomcat RCE via JSP Upload Bypass'); script_set_attribute(attribute:"exploit_framework_metasploit", value:"true"); script_set_attribute(attribute:"exploit_framework_canvas", value:"true"); script_set_attribute(attribute:"canvas_package", value:'CANVAS'); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:httpd"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:httpd-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:httpd-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:httpd-manual"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:httpd-tools"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:httpd22"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:httpd22-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:httpd22-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:httpd22-manual"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:httpd22-tools"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:jbcs-httpd24-openssl"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:jbcs-httpd24-openssl-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:jbcs-httpd24-openssl-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:jbcs-httpd24-openssl-libs"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:jbcs-httpd24-openssl-perl"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:jbcs-httpd24-openssl-static"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:mod_cluster-native"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:mod_cluster-native-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:mod_ldap"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:mod_ldap22"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:mod_ssl"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:mod_ssl22"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:tomcat6"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:tomcat6-admin-webapps"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:tomcat6-docs-webapp"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:tomcat6-el-2.1-api"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:tomcat6-javadoc"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:tomcat6-jsp-2.1-api"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:tomcat6-lib"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:tomcat6-log4j"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:tomcat6-maven-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:tomcat6-servlet-2.5-api"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:tomcat6-webapps"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:tomcat7"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:tomcat7-admin-webapps"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:tomcat7-docs-webapp"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:tomcat7-el-2.2-api"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:tomcat7-javadoc"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:tomcat7-jsp-2.2-api"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:tomcat7-lib"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:tomcat7-log4j"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:tomcat7-maven-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:tomcat7-servlet-3.0-api"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:redhat:enterprise_linux:tomcat7-webapps"); script_set_attribute(attribute:"cpe", value:"cpe:/o:redhat:enterprise_linux:6"); script_set_attribute(attribute:"cpe", value:"cpe:/o:redhat:enterprise_linux:7"); script_set_attribute(attribute:"vuln_publication_date", value:"2016/09/01"); script_set_attribute(attribute:"patch_publication_date", value:"2017/11/02"); script_set_attribute(attribute:"plugin_publication_date", value:"2017/11/08"); script_set_attribute(attribute:"in_the_news", value:"true"); script_set_attribute(attribute:"generated_plugin", value:"current"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_copyright(english:"This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof."); script_family(english:"Red Hat Local Security Checks"); script_dependencies("ssh_get_info.nasl"); script_require_keys("Host/local_checks_enabled", "Host/RedHat/release", "Host/RedHat/rpm-list", "Host/cpu"); exit(0); } include("audit.inc"); include("global_settings.inc"); include("misc_func.inc"); include("rpm.inc"); if (!get_kb_item("Host/local_checks_enabled")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); release = get_kb_item("Host/RedHat/release"); if (isnull(release) || "Red Hat" >!< release) audit(AUDIT_OS_NOT, "Red Hat"); os_ver = pregmatch(pattern: "Red Hat Enterprise Linux.*release ([0-9]+(\.[0-9]+)?)", string:release); if (isnull(os_ver)) audit(AUDIT_UNKNOWN_APP_VER, "Red Hat"); os_ver = os_ver[1]; if (! preg(pattern:"^(6|7)([^0-9]|$)", string:os_ver)) audit(AUDIT_OS_NOT, "Red Hat 6.x / 7.x", "Red Hat " + os_ver); if (!get_kb_item("Host/RedHat/rpm-list")) audit(AUDIT_PACKAGE_LIST_MISSING); cpu = get_kb_item("Host/cpu"); if (isnull(cpu)) audit(AUDIT_UNKNOWN_ARCH); if ("x86_64" >!< cpu && cpu !~ "^i[3-6]86$" && "s390" >!< cpu) audit(AUDIT_LOCAL_CHECKS_NOT_IMPLEMENTED, "Red Hat", cpu); yum_updateinfo = get_kb_item("Host/RedHat/yum-updateinfo"); if (!empty_or_null(yum_updateinfo)) { rhsa = "RHSA-2017:3113"; yum_report = redhat_generate_yum_updateinfo_report(rhsa:rhsa); if (!empty_or_null(yum_report)) { security_report_v4( port : 0, severity : SECURITY_WARNING, extra : yum_report ); exit(0); } else { audit_message = "affected by Red Hat security advisory " + rhsa; audit(AUDIT_OS_NOT, audit_message); } } else { flag = 0; if (! (rpm_exists(release:"RHEL6", rpm:"jws-2") || rpm_exists(release:"RHEL7", rpm:"jws-2"))) audit(AUDIT_PACKAGE_NOT_INSTALLED, "JBoss Web Server"); if (rpm_check(release:"RHEL6", cpu:"i386", reference:"httpd-2.2.26-57.ep6.el6")) flag++; if (rpm_check(release:"RHEL6", cpu:"x86_64", reference:"httpd-2.2.26-57.ep6.el6")) flag++; if (rpm_check(release:"RHEL6", cpu:"i386", reference:"httpd-debuginfo-2.2.26-57.ep6.el6")) flag++; if (rpm_check(release:"RHEL6", cpu:"x86_64", reference:"httpd-debuginfo-2.2.26-57.ep6.el6")) flag++; if (rpm_check(release:"RHEL6", cpu:"i386", reference:"httpd-devel-2.2.26-57.ep6.el6")) flag++; if (rpm_check(release:"RHEL6", cpu:"x86_64", reference:"httpd-devel-2.2.26-57.ep6.el6")) flag++; if (rpm_check(release:"RHEL6", cpu:"i386", reference:"httpd-manual-2.2.26-57.ep6.el6")) flag++; if (rpm_check(release:"RHEL6", cpu:"x86_64", reference:"httpd-manual-2.2.26-57.ep6.el6")) flag++; if (rpm_check(release:"RHEL6", cpu:"i386", reference:"httpd-tools-2.2.26-57.ep6.el6")) flag++; if (rpm_check(release:"RHEL6", cpu:"x86_64", reference:"httpd-tools-2.2.26-57.ep6.el6")) flag++; if (rpm_check(release:"RHEL6", cpu:"i686", reference:"jbcs-httpd24-openssl-1.0.2h-14.jbcs.el6")) flag++; if (rpm_check(release:"RHEL6", cpu:"x86_64", reference:"jbcs-httpd24-openssl-1.0.2h-14.jbcs.el6")) flag++; if (rpm_check(release:"RHEL6", cpu:"i686", reference:"jbcs-httpd24-openssl-debuginfo-1.0.2h-14.jbcs.el6")) flag++; if (rpm_check(release:"RHEL6", cpu:"x86_64", reference:"jbcs-httpd24-openssl-debuginfo-1.0.2h-14.jbcs.el6")) flag++; if (rpm_check(release:"RHEL6", cpu:"i686", reference:"jbcs-httpd24-openssl-devel-1.0.2h-14.jbcs.el6")) flag++; if (rpm_check(release:"RHEL6", cpu:"x86_64", reference:"jbcs-httpd24-openssl-devel-1.0.2h-14.jbcs.el6")) flag++; if (rpm_check(release:"RHEL6", cpu:"i686", reference:"jbcs-httpd24-openssl-libs-1.0.2h-14.jbcs.el6")) flag++; if (rpm_check(release:"RHEL6", cpu:"x86_64", reference:"jbcs-httpd24-openssl-libs-1.0.2h-14.jbcs.el6")) flag++; if (rpm_check(release:"RHEL6", cpu:"i686", reference:"jbcs-httpd24-openssl-perl-1.0.2h-14.jbcs.el6")) flag++; if (rpm_check(release:"RHEL6", cpu:"x86_64", reference:"jbcs-httpd24-openssl-perl-1.0.2h-14.jbcs.el6")) flag++; if (rpm_check(release:"RHEL6", cpu:"i686", reference:"jbcs-httpd24-openssl-static-1.0.2h-14.jbcs.el6")) flag++; if (rpm_check(release:"RHEL6", cpu:"x86_64", reference:"jbcs-httpd24-openssl-static-1.0.2h-14.jbcs.el6")) flag++; if (rpm_check(release:"RHEL6", cpu:"i386", reference:"mod_cluster-native-1.2.13-9.Final_redhat_2.ep6.el6")) flag++; if (rpm_check(release:"RHEL6", cpu:"x86_64", reference:"mod_cluster-native-1.2.13-9.Final_redhat_2.ep6.el6")) flag++; if (rpm_check(release:"RHEL6", cpu:"i386", reference:"mod_cluster-native-debuginfo-1.2.13-9.Final_redhat_2.ep6.el6")) flag++; if (rpm_check(release:"RHEL6", cpu:"x86_64", reference:"mod_cluster-native-debuginfo-1.2.13-9.Final_redhat_2.ep6.el6")) flag++; if (rpm_check(release:"RHEL6", cpu:"i386", reference:"mod_ldap-2.2.26-57.ep6.el6")) flag++; if (rpm_check(release:"RHEL6", cpu:"x86_64", reference:"mod_ldap-2.2.26-57.ep6.el6")) flag++; if (rpm_check(release:"RHEL6", cpu:"i386", reference:"mod_ssl-2.2.26-57.ep6.el6")) flag++; if (rpm_check(release:"RHEL6", cpu:"x86_64", reference:"mod_ssl-2.2.26-57.ep6.el6")) flag++; if (rpm_check(release:"RHEL6", reference:"tomcat6-6.0.41-19_patch_04.ep6.el6")) flag++; if (rpm_check(release:"RHEL6", reference:"tomcat6-admin-webapps-6.0.41-19_patch_04.ep6.el6")) flag++; if (rpm_check(release:"RHEL6", reference:"tomcat6-docs-webapp-6.0.41-19_patch_04.ep6.el6")) flag++; if (rpm_check(release:"RHEL6", reference:"tomcat6-el-2.1-api-6.0.41-19_patch_04.ep6.el6")) flag++; if (rpm_check(release:"RHEL6", reference:"tomcat6-javadoc-6.0.41-19_patch_04.ep6.el6")) flag++; if (rpm_check(release:"RHEL6", reference:"tomcat6-jsp-2.1-api-6.0.41-19_patch_04.ep6.el6")) flag++; if (rpm_check(release:"RHEL6", reference:"tomcat6-lib-6.0.41-19_patch_04.ep6.el6")) flag++; if (rpm_check(release:"RHEL6", reference:"tomcat6-log4j-6.0.41-19_patch_04.ep6.el6")) flag++; if (rpm_check(release:"RHEL6", reference:"tomcat6-maven-devel-6.0.41-19_patch_04.ep6.el6")) flag++; if (rpm_check(release:"RHEL6", reference:"tomcat6-servlet-2.5-api-6.0.41-19_patch_04.ep6.el6")) flag++; if (rpm_check(release:"RHEL6", reference:"tomcat6-webapps-6.0.41-19_patch_04.ep6.el6")) flag++; if (rpm_check(release:"RHEL6", reference:"tomcat7-7.0.54-28_patch_05.ep6.el6")) flag++; if (rpm_check(release:"RHEL6", reference:"tomcat7-admin-webapps-7.0.54-28_patch_05.ep6.el6")) flag++; if (rpm_check(release:"RHEL6", reference:"tomcat7-docs-webapp-7.0.54-28_patch_05.ep6.el6")) flag++; if (rpm_check(release:"RHEL6", reference:"tomcat7-el-2.2-api-7.0.54-28_patch_05.ep6.el6")) flag++; if (rpm_check(release:"RHEL6", reference:"tomcat7-javadoc-7.0.54-28_patch_05.ep6.el6")) flag++; if (rpm_check(release:"RHEL6", reference:"tomcat7-jsp-2.2-api-7.0.54-28_patch_05.ep6.el6")) flag++; if (rpm_check(release:"RHEL6", reference:"tomcat7-lib-7.0.54-28_patch_05.ep6.el6")) flag++; if (rpm_check(release:"RHEL6", reference:"tomcat7-log4j-7.0.54-28_patch_05.ep6.el6")) flag++; if (rpm_check(release:"RHEL6", reference:"tomcat7-maven-devel-7.0.54-28_patch_05.ep6.el6")) flag++; if (rpm_check(release:"RHEL6", reference:"tomcat7-servlet-3.0-api-7.0.54-28_patch_05.ep6.el6")) flag++; if (rpm_check(release:"RHEL6", reference:"tomcat7-webapps-7.0.54-28_patch_05.ep6.el6")) flag++; if (rpm_check(release:"RHEL7", cpu:"x86_64", reference:"httpd22-2.2.26-58.ep6.el7")) flag++; if (rpm_check(release:"RHEL7", cpu:"x86_64", reference:"httpd22-debuginfo-2.2.26-58.ep6.el7")) flag++; if (rpm_check(release:"RHEL7", cpu:"x86_64", reference:"httpd22-devel-2.2.26-58.ep6.el7")) flag++; if (rpm_check(release:"RHEL7", cpu:"x86_64", reference:"httpd22-manual-2.2.26-58.ep6.el7")) flag++; if (rpm_check(release:"RHEL7", cpu:"x86_64", reference:"httpd22-tools-2.2.26-58.ep6.el7")) flag++; if (rpm_check(release:"RHEL7", cpu:"x86_64", reference:"jbcs-httpd24-openssl-1.0.2h-14.jbcs.el7")) flag++; if (rpm_check(release:"RHEL7", cpu:"x86_64", reference:"jbcs-httpd24-openssl-debuginfo-1.0.2h-14.jbcs.el7")) flag++; if (rpm_check(release:"RHEL7", cpu:"x86_64", reference:"jbcs-httpd24-openssl-devel-1.0.2h-14.jbcs.el7")) flag++; if (rpm_check(release:"RHEL7", cpu:"x86_64", reference:"jbcs-httpd24-openssl-libs-1.0.2h-14.jbcs.el7")) flag++; if (rpm_check(release:"RHEL7", cpu:"x86_64", reference:"jbcs-httpd24-openssl-perl-1.0.2h-14.jbcs.el7")) flag++; if (rpm_check(release:"RHEL7", cpu:"x86_64", reference:"jbcs-httpd24-openssl-static-1.0.2h-14.jbcs.el7")) flag++; if (rpm_check(release:"RHEL7", cpu:"x86_64", reference:"mod_cluster-native-1.2.13-9.Final_redhat_2.ep6.el7")) flag++; if (rpm_check(release:"RHEL7", cpu:"x86_64", reference:"mod_cluster-native-debuginfo-1.2.13-9.Final_redhat_2.ep6.el7")) flag++; if (rpm_check(release:"RHEL7", cpu:"x86_64", reference:"mod_ldap22-2.2.26-58.ep6.el7")) flag++; if (rpm_check(release:"RHEL7", cpu:"x86_64", reference:"mod_ssl22-2.2.26-58.ep6.el7")) flag++; if (rpm_check(release:"RHEL7", reference:"tomcat6-6.0.41-19_patch_04.ep6.el7")) flag++; if (rpm_check(release:"RHEL7", reference:"tomcat6-admin-webapps-6.0.41-19_patch_04.ep6.el7")) flag++; if (rpm_check(release:"RHEL7", reference:"tomcat6-docs-webapp-6.0.41-19_patch_04.ep6.el7")) flag++; if (rpm_check(release:"RHEL7", reference:"tomcat6-el-2.1-api-6.0.41-19_patch_04.ep6.el7")) flag++; if (rpm_check(release:"RHEL7", reference:"tomcat6-javadoc-6.0.41-19_patch_04.ep6.el7")) flag++; if (rpm_check(release:"RHEL7", reference:"tomcat6-jsp-2.1-api-6.0.41-19_patch_04.ep6.el7")) flag++; if (rpm_check(release:"RHEL7", reference:"tomcat6-lib-6.0.41-19_patch_04.ep6.el7")) flag++; if (rpm_check(release:"RHEL7", reference:"tomcat6-log4j-6.0.41-19_patch_04.ep6.el7")) flag++; if (rpm_check(release:"RHEL7", reference:"tomcat6-maven-devel-6.0.41-19_patch_04.ep6.el7")) flag++; if (rpm_check(release:"RHEL7", reference:"tomcat6-servlet-2.5-api-6.0.41-19_patch_04.ep6.el7")) flag++; if (rpm_check(release:"RHEL7", reference:"tomcat6-webapps-6.0.41-19_patch_04.ep6.el7")) flag++; if (rpm_check(release:"RHEL7", reference:"tomcat7-7.0.54-28_patch_05.ep6.el7")) flag++; if (rpm_check(release:"RHEL7", reference:"tomcat7-admin-webapps-7.0.54-28_patch_05.ep6.el7")) flag++; if (rpm_check(release:"RHEL7", reference:"tomcat7-docs-webapp-7.0.54-28_patch_05.ep6.el7")) flag++; if (rpm_check(release:"RHEL7", reference:"tomcat7-el-2.2-api-7.0.54-28_patch_05.ep6.el7")) flag++; if (rpm_check(release:"RHEL7", reference:"tomcat7-javadoc-7.0.54-28_patch_05.ep6.el7")) flag++; if (rpm_check(release:"RHEL7", reference:"tomcat7-jsp-2.2-api-7.0.54-28_patch_05.ep6.el7")) flag++; if (rpm_check(release:"RHEL7", reference:"tomcat7-lib-7.0.54-28_patch_05.ep6.el7")) flag++; if (rpm_check(release:"RHEL7", reference:"tomcat7-log4j-7.0.54-28_patch_05.ep6.el7")) flag++; if (rpm_check(release:"RHEL7", reference:"tomcat7-maven-devel-7.0.54-28_patch_05.ep6.el7")) flag++; if (rpm_check(release:"RHEL7", reference:"tomcat7-servlet-3.0-api-7.0.54-28_patch_05.ep6.el7")) flag++; if (rpm_check(release:"RHEL7", reference:"tomcat7-webapps-7.0.54-28_patch_05.ep6.el7")) flag++; if (flag) { security_report_v4( port : 0, severity : SECURITY_WARNING, extra : rpm_report_get() + redhat_report_package_caveat() ); exit(0); } else { tested = pkg_tests_get(); if (tested) audit(AUDIT_PACKAGE_NOT_AFFECTED, tested); else audit(AUDIT_PACKAGE_NOT_INSTALLED, "httpd / httpd-debuginfo / httpd-devel / httpd-manual / httpd-tools / etc"); } }NASL family CentOS Local Security Checks NASL id CENTOS_RHSA-2017-2882.NASL description An update for httpd is now available for Red Hat Enterprise Linux 7. Red Hat Product Security has rated this update as having a security impact of Moderate. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. The httpd packages provide the Apache HTTP Server, a powerful, efficient, and extensible web server. Security Fix(es) : * A use-after-free flaw was found in the way httpd handled invalid and previously unregistered HTTP methods specified in the Limit directive used in an .htaccess file. A remote attacker could possibly use this flaw to disclose portions of the server memory, or cause httpd child process to crash. (CVE-2017-9798) Red Hat would like to thank Hanno Bock for reporting this issue. last seen 2020-06-01 modified 2020-06-02 plugin id 103790 published 2017-10-12 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/103790 title CentOS 7 : httpd (CESA-2017:2882) (Optionsbleed) NASL family Red Hat Local Security Checks NASL id REDHAT-RHSA-2017-3195.NASL description An update for httpd is now available for Red Hat Enterprise Linux 6.7 Extended Update Support. Red Hat Product Security has rated this update as having a security impact of Important. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. The httpd packages provide the Apache HTTP Server, a powerful, efficient, and extensible web server. Security Fix(es) : * It was discovered that the httpd last seen 2020-06-01 modified 2020-06-02 plugin id 104541 published 2017-11-14 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/104541 title RHEL 6 : httpd (RHSA-2017:3195) (Optionsbleed) NASL family MacOS X Local Security Checks NASL id MACOS_10_13_2.NASL description The remote host is running a version of Mac OS X that is 10.13.x prior to 10.13.2. It is, therefore, affected by multiple vulnerabilities in the following components : - apache - curl - Directory Utility - IOAcceleratorFamily - IOKit - Intel Graphics Driver - Kernel - Mail - Mail Drafts - OpenSSL - Screen Sharing Server Note that successful exploitation of the most serious issues can result in arbitrary code execution. last seen 2020-06-01 modified 2020-06-02 plugin id 105080 published 2017-12-07 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/105080 title macOS 10.13.x < 10.13.2 Multiple Vulnerabilities (Meltdown) NASL family Junos Local Security Checks NASL id JUNIPER_SPACE_JSA_10838.NASL description According to its self-reported version number, the remote Junos Space version is prior to 17.2R1. It is, therefore, affected by multiple vulnerabilities. last seen 2020-06-01 modified 2020-06-02 plugin id 108520 published 2018-03-21 reporter This script is Copyright (C) 2018-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/108520 title Juniper Junos Space < 17.2R1 Multiple Vulnerabilities (JSA10838) NASL family Red Hat Local Security Checks NASL id REDHAT-RHSA-2017-2972.NASL description An update for httpd is now available for Red Hat Enterprise Linux 6. Red Hat Product Security has rated this update as having a security impact of Moderate. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. The httpd packages provide the Apache HTTP Server, a powerful, efficient, and extensible web server. Security Fix(es) : * A use-after-free flaw was found in the way httpd handled invalid and previously unregistered HTTP methods specified in the Limit directive used in an .htaccess file. A remote attacker could possibly use this flaw to disclose portions of the server memory, or cause httpd child process to crash. (CVE-2017-9798) * A regression was found in the Red Hat Enterprise Linux 6.9 version of httpd, causing comments in the last seen 2020-06-01 modified 2020-06-02 plugin id 104006 published 2017-10-20 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/104006 title RHEL 6 : httpd (RHSA-2017:2972) (Optionsbleed) NASL family CGI abuses NASL id ORACLE_PRIMAVERA_UNIFIER_CPU_APR_2019.NASL description According to its self-reported version number, the Oracle Primavera Unifier installation running on the remote web server is 16.x prior to 16.2.15.7 or 17.7.x prior to 17.12.10 or 18.x prior to 18.8.6. It is, therefore, affected by multiple vulnerabilities: - A deserialization vulnerability in Apache Commons FileUpload allows for remote code execution. (CVE-2016-1000031) - A denial of service (DoS) vulnerability exists in Apache HTTP Server 2.4.17 to 2.4.34, due to a design error. An unauthenticated, remote attacker can exploit this issue by sending continuous, large SETTINGS frames to cause a client to occupy a connection, server thread and CPU time without any connection timeout coming to effect. This affects only HTTP/2 connections. A possible mitigation is to not enable the h2 protocol. (CVE-2018-11763). - A deserialization vulnerability in jackson-databind, a fast and powerful JSON library for Java, allows an unauthenticated user to perform code execution. The issue was resolved by extending the blacklist and blocking more classes from polymorphic deserialization. (CVE-2018-19362) Note that Nessus has not tested for these issues but has instead relied only on the application last seen 2020-06-01 modified 2020-06-02 plugin id 124170 published 2019-04-19 reporter This script is Copyright (C) 2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/124170 title Oracle Primavera Unifier Multiple Vulnerabilities (Apr 2019 CPU) NASL family SuSE Local Security Checks NASL id OPENSUSE-2017-1083.NASL description This update for apache2 fixes the following security issue : - CVE-2017-9798: Prevent use-after-free use of memory that allowed for an information leak via OPTIONS (bsc#1058058). This update was imported from the SUSE:SLE-12-SP2:Update update project. last seen 2020-06-05 modified 2017-09-22 plugin id 103399 published 2017-09-22 reporter This script is Copyright (C) 2017-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/103399 title openSUSE Security Update : apache2 (openSUSE-2017-1083) (Optionsbleed) NASL family Misc. NASL id ORACLE_ENTERPRISE_MANAGER_OPS_CENTER_APR_2019_CPU.NASL description The version of Oracle Enterprise Manager Cloud Control installed on the remote host is affected by multiple vulnerabilities in Enterprise Manager Base Platform component: - A deserialization vulnerability in Apache Commons FileUpload allows for remote code execution. (CVE-2016-1000031) - An information disclosure vulnerability exists in OpenSSL due to the potential for a side-channel timing attack. An unauthenticated attacker can exploit this to disclose potentially sensitive information. (CVE-2018-0734) - A denial of service (DoS) vulnerability exists in Apache HTTP Server 2.4.17 to 2.4.34, due to a design error. An unauthenticated, remote attacker can exploit this issue by sending continuous, large SETTINGS frames to cause a client to occupy a connection, server thread and CPU time without any connection timeout coming to effect. This affects only HTTP/2 connections. A possible mitigation is to not enable the h2 protocol. (CVE-2018-11763). - Networking component of Enterprise Manager Base Platform (Spring Framework) is easily exploited and may allow an unauthenticated, remote attacker to takeover the Enterprise Manager Base Platform. (CVE-2018-1258) last seen 2020-06-01 modified 2020-06-02 plugin id 125147 published 2019-05-15 reporter This script is Copyright (C) 2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/125147 title Oracle Enterprise Manager Ops Center (Apr 2019 CPU) NASL family Misc. NASL id ORACLE_ENTERPRISE_MANAGER_JUL_2018_CPU.NASL description The version of Oracle Enterprise Manager Cloud Control installed on the remote host is affected by multiple vulnerabilities in the Enterprise Manager Base Platform component. last seen 2020-06-01 modified 2020-06-02 plugin id 111152 published 2018-07-20 reporter This script is Copyright (C) 2018-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/111152 title Oracle Enterprise Manager Cloud Control Multiple Vulnerabilities (July 2018 CPU) NASL family Amazon Linux Local Security Checks NASL id ALA_ALAS-2017-896.NASL description Apache httpd allows remote attackers to read secret data from process memory if the Limit directive can be set in a user last seen 2020-06-01 modified 2020-06-02 plugin id 103309 published 2017-09-19 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/103309 title Amazon Linux AMI : httpd24 / httpd (ALAS-2017-896) (Optionsbleed) NASL family Gentoo Local Security Checks NASL id GENTOO_GLSA-201710-32.NASL description The remote host is affected by the vulnerability described in GLSA-201710-32 (Apache: Multiple vulnerabilities) Multiple vulnerabilities have been discovered in Apache. Please review the referenced CVE identifiers for details. Impact : The Optionsbleed vulnerability can leak arbitrary memory from the server process that may contain secrets. Additionally attackers may cause a Denial of Service condition, bypass authentication, or cause information loss. Workaround : There is no known workaround at this time. last seen 2020-06-01 modified 2020-06-02 plugin id 104233 published 2017-10-30 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/104233 title GLSA-201710-32 : Apache: Multiple vulnerabilities (Optionsbleed) NASL family Virtuozzo Local Security Checks NASL id VIRTUOZZO_VZLSA-2017-2972.NASL description An update for httpd is now available for Red Hat Enterprise Linux 6. Red Hat Product Security has rated this update as having a security impact of Moderate. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. The httpd packages provide the Apache HTTP Server, a powerful, efficient, and extensible web server. Security Fix(es) : * A use-after-free flaw was found in the way httpd handled invalid and previously unregistered HTTP methods specified in the Limit directive used in an .htaccess file. A remote attacker could possibly use this flaw to disclose portions of the server memory, or cause httpd child process to crash. (CVE-2017-9798) * A regression was found in the Red Hat Enterprise Linux 6.9 version of httpd, causing comments in the last seen 2020-06-01 modified 2020-06-02 plugin id 119234 published 2018-11-27 reporter This script is Copyright (C) 2018-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/119234 title Virtuozzo 6 : httpd / httpd-devel / httpd-manual / httpd-tools / etc (VZLSA-2017-2972) NASL family Huawei Local Security Checks NASL id EULEROS_SA-2019-1389.NASL description According to the versions of the httpd packages installed, the EulerOS Virtualization for ARM 64 installation on the remote host is affected by the following vulnerabilities : - In Apache HTTP Server 2.4 release 2.4.37 and prior, mod_session checks the session expiry time before decoding the session. This causes session expiry time to be ignored for mod_session_cookie sessions since the expiry time is loaded when the session is decoded.(CVE-2018-17199) - It was discovered that the use of httpd last seen 2020-06-01 modified 2020-06-02 plugin id 124892 published 2019-05-14 reporter This script is Copyright (C) 2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/124892 title EulerOS Virtualization for ARM 64 3.0.1.0 : httpd (EulerOS-SA-2019-1389) NASL family Web Servers NASL id APACHE_2_4_28.NASL description According to its banner, the version of Apache running on the remote host is 2.4.x prior to 2.4.28. It is, therefore, affected by an HTTP vulnerability related to the <Limit {method}> directive in an .htaccess file. Note that Nessus has not tested for these issues but has instead relied only on the application last seen 2020-06-01 modified 2020-06-02 plugin id 103838 published 2017-10-13 reporter This script is Copyright (C) 2018 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/103838 title Apache 2.4.x < 2.4.28 HTTP Vulnerability (OptionsBleed) NASL family Misc. NASL id ORACLE_SECURE_GLOBAL_DESKTOP_APR_2018_CPU.NASL description The version of Oracle Secure Global Desktop installed on the remote host is 5.3 and is missing a security patch from the April 2018 Critical Patch Update (CPU). It is, therefore, affected by multiple vulnerabilities. last seen 2020-06-01 modified 2020-06-02 plugin id 109165 published 2018-04-19 reporter This script is Copyright (C) 2018 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/109165 title Oracle Secure Global Desktop Multiple Vulnerabilities (April 2018 CPU) NASL family Oracle Linux Local Security Checks NASL id ORACLELINUX_ELSA-2017-2882.NASL description From Red Hat Security Advisory 2017:2882 : An update for httpd is now available for Red Hat Enterprise Linux 7. Red Hat Product Security has rated this update as having a security impact of Moderate. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. The httpd packages provide the Apache HTTP Server, a powerful, efficient, and extensible web server. Security Fix(es) : * A use-after-free flaw was found in the way httpd handled invalid and previously unregistered HTTP methods specified in the Limit directive used in an .htaccess file. A remote attacker could possibly use this flaw to disclose portions of the server memory, or cause httpd child process to crash. (CVE-2017-9798) Red Hat would like to thank Hanno Bock for reporting this issue. last seen 2020-06-01 modified 2020-06-02 plugin id 103803 published 2017-10-12 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/103803 title Oracle Linux 7 : httpd (ELSA-2017-2882) (Optionsbleed) NASL family Red Hat Local Security Checks NASL id REDHAT-RHSA-2017-3193.NASL description An update for httpd is now available for Red Hat Enterprise Linux 7.2 Extended Update Support. Red Hat Product Security has rated this update as having a security impact of Important. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. The httpd packages provide the Apache HTTP Server, a powerful, efficient, and extensible web server. Security Fix(es) : * It was discovered that the httpd last seen 2020-06-01 modified 2020-06-02 plugin id 104539 published 2017-11-14 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/104539 title RHEL 7 : httpd (RHSA-2017:3193) (Optionsbleed) NASL family Fedora Local Security Checks NASL id FEDORA_2017-A52F252521.NASL description This is a release fixing a security fix applied upstream, known as last seen 2020-06-05 modified 2017-09-25 plugin id 103438 published 2017-09-25 reporter This script is Copyright (C) 2017-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/103438 title Fedora 26 : httpd (2017-a52f252521) (Optionsbleed) NASL family Scientific Linux Local Security Checks NASL id SL_20171011_HTTPD_ON_SL7_X.NASL description Security Fix(es) : - A use-after-free flaw was found in the way httpd handled invalid and previously unregistered HTTP methods specified in the Limit directive used in an .htaccess file. A remote attacker could possibly use this flaw to disclose portions of the server memory, or cause httpd child process to crash. (CVE-2017-9798) last seen 2020-03-18 modified 2017-10-12 plugin id 103806 published 2017-10-12 reporter This script is Copyright (C) 2017-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/103806 title Scientific Linux Security Update : httpd on SL7.x x86_64 (20171011) (Optionsbleed) NASL family Red Hat Local Security Checks NASL id REDHAT-RHSA-2017-3240.NASL description An update is now available for Red Hat JBoss Enterprise Application Platform 6.4 for RHEL 6 and Red Hat JBoss Enterprise Application Platform 6.4 for RHEL 7. Red Hat Product Security has rated this update as having a security impact of Important. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. [Updated 21st November 2017] Previously, this erratum was marked as a replacement of the JBoss Enterprise Application Platform 6.4.16 Natives. This was incorrect; the erratum is an update, not a replacement. The erratum text has been modified to reflect this. Red Hat JBoss Enterprise Application Platform is a platform for Java applications based on the JBoss Application Server. This release provides an update to httpd and OpenSSL. The updates are documented in the Release Notes document linked to in the References. The httpd packages provide the Apache HTTP Server, a powerful, efficient, and extensible web server. OpenSSL is a toolkit that implements the Secure Sockets Layer (SSL) and Transport Layer Security (TLS) protocols, as well as a full-strength general-purpose cryptography library. This release of JBoss Enterprise Application Platform 6.4.18 Natives serves as an update to the JBoss Enterprise Application Platform 6.4.16 Natives and includes bug fixes which are documented in the Release Notes document linked to in the References. All users of Red Hat JBoss Enterprise Application Platform 6.4 Natives are advised to upgrade to these updated packages. Security Fix(es) : * It was discovered that the httpd last seen 2020-06-01 modified 2020-06-02 plugin id 104699 published 2017-11-20 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/104699 title RHEL 6 / 7 : JBoss EAP (RHSA-2017:3240) (Optionsbleed) NASL family NewStart CGSL Local Security Checks NASL id NEWSTART_CGSL_NS-SA-2019-0118_HTTPD.NASL description The remote NewStart CGSL host, running version MAIN 4.05, has httpd packages installed that are affected by multiple vulnerabilities: - Off-by-one error in the mod_ssl Certificate Revocation List (CRL) verification callback in Apache, when configured to use a CRL, allows remote attackers to cause a denial of service (child process crash) via a CRL that causes a buffer overflow of one null byte. (CVE-2005-1268) - The Apache HTTP server before 1.3.34, and 2.0.x before 2.0.55, when acting as an HTTP proxy, allows remote attackers to poison the web cache, bypass web application firewall protection, and conduct XSS attacks via an HTTP request with both a Transfer-Encoding: chunked header and a Content-Length header, which causes Apache to incorrectly handle and forward the body of the request in a way that causes the receiving server to process it as a separate HTTP request, aka HTTP Request Smuggling. (CVE-2005-2088) - ssl_engine_kernel.c in mod_ssl before 2.8.24, when using SSLVerifyClient optional in the global virtual host configuration, does not properly enforce SSLVerifyClient require in a per-location context, which allows remote attackers to bypass intended access restrictions. (CVE-2005-2700) - The byte-range filter in Apache 2.0 before 2.0.54 allows remote attackers to cause a denial of service (memory consumption) via an HTTP header with a large Range field. (CVE-2005-2728) - Cross-site scripting (XSS) vulnerability in the mod_imap module of Apache httpd before 1.3.35-dev and Apache httpd 2.0.x before 2.0.56-dev allows remote attackers to inject arbitrary web script or HTML via the Referer when using image maps. (CVE-2005-3352) - mod_ssl in Apache 2.0 up to 2.0.55, when configured with an SSL vhost with access control and a custom error 400 error page, allows remote attackers to cause a denial of service (application crash) via a non-SSL request to an SSL port, which triggers a NULL pointer dereference. (CVE-2005-3357) - The TLS protocol, and the SSL protocol 3.0 and possibly earlier, as used in Microsoft Internet Information Services (IIS) 7.0, mod_ssl in the Apache HTTP Server 2.2.14 and earlier, OpenSSL before 0.9.8l, GnuTLS 2.8.5 and earlier, Mozilla Network Security Services (NSS) 3.12.4 and earlier, multiple Cisco products, and other products, does not properly associate renegotiation handshakes with an existing connection, which allows man-in-the-middle attackers to insert data into HTTPS sessions, and possibly other types of sessions protected by TLS or SSL, by sending an unauthenticated request that is processed retroactively by a server in a post- renegotiation context, related to a plaintext injection attack, aka the Project Mogul issue. (CVE-2009-3555) - The (1) mod_cache and (2) mod_dav modules in the Apache HTTP Server 2.2.x before 2.2.16 allow remote attackers to cause a denial of service (process crash) via a request that lacks a path. (CVE-2010-1452) - fs/ext4/extents.c in the Linux kernel before 3.0 does not mark a modified extent as dirty in certain cases of extent splitting, which allows local users to cause a denial of service (system crash) via vectors involving ext4 umount and mount operations. (CVE-2011-3638) - It was discovered that the HTTP parser in httpd incorrectly allowed certain characters not permitted by the HTTP protocol specification to appear unencoded in HTTP request headers. If httpd was used in conjunction with a proxy or backend server that interpreted those characters differently, a remote attacker could possibly use this flaw to inject data into HTTP responses, resulting in proxy cache poisoning. (CVE-2016-8743) - It was discovered that the use of httpd last seen 2020-06-01 modified 2020-06-02 plugin id 127360 published 2019-08-12 reporter This script is Copyright (C) 2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/127360 title NewStart CGSL MAIN 4.05 : httpd Multiple Vulnerabilities (NS-SA-2019-0118) NASL family CentOS Local Security Checks NASL id CENTOS_RHSA-2017-2972.NASL description An update for httpd is now available for Red Hat Enterprise Linux 6. Red Hat Product Security has rated this update as having a security impact of Moderate. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. The httpd packages provide the Apache HTTP Server, a powerful, efficient, and extensible web server. Security Fix(es) : * A use-after-free flaw was found in the way httpd handled invalid and previously unregistered HTTP methods specified in the Limit directive used in an .htaccess file. A remote attacker could possibly use this flaw to disclose portions of the server memory, or cause httpd child process to crash. (CVE-2017-9798) * A regression was found in the Red Hat Enterprise Linux 6.9 version of httpd, causing comments in the last seen 2020-06-01 modified 2020-06-02 plugin id 104053 published 2017-10-23 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/104053 title CentOS 6 : httpd (CESA-2017:2972) (Optionsbleed) NASL family Slackware Local Security Checks NASL id SLACKWARE_SSA_2017-261-01.NASL description New httpd packages are available for Slackware 13.0, 13.1, 13.37, 14.0, 14.1, 14.2, and -current to fix a security issue. last seen 2020-06-01 modified 2020-06-02 plugin id 103306 published 2017-09-19 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/103306 title Slackware 13.0 / 13.1 / 13.37 / 14.0 / 14.1 / 14.2 / current : httpd (SSA:2017-261-01) (Optionsbleed) NASL family Red Hat Local Security Checks NASL id REDHAT-RHSA-2017-3476.NASL description An update is now available for JBoss Core Services on RHEL 7. Red Hat Product Security has rated this update as having a security impact of Important. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. Red Hat JBoss Core Services is a set of supplementary software for Red Hat JBoss middleware products. This software, such as Apache HTTP Server, is common to multiple JBoss middleware products, and is packaged under Red Hat JBoss Core Services to allow for faster distribution of updates, and for a more consistent update experience. This release of Red Hat JBoss Core Services Apache HTTP Server 2.4.23 Service Pack 3 serves as an update to Red Hat JBoss Core Services Apache HTTP Server 2.4.23 Service Pack 2, and includes bug fixes, which are documented in the Release Notes document linked to in the References. Security Fix(es) : * An out-of-bounds array dereference was found in apr_time_exp_get(). An attacker could abuse an unvalidated usage of this function to cause a denial of service or potentially lead to data leak. (CVE-2017-12613) * It was discovered that the use of httpd last seen 2020-06-01 modified 2020-06-02 plugin id 105368 published 2017-12-19 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/105368 title RHEL 7 : Red Hat JBoss Core Services Apache HTTP Server 2.4.23 (RHSA-2017:3476) (Optionsbleed) NASL family MacOS X Local Security Checks NASL id MACOSX_SECUPD2017-005.NASL description The remote host is running Mac OS X 10.11.6 or Mac OS X 10.12.6 and is missing a security update. It is therefore, affected by multiple vulnerabilities affecting the following components : - apache - curl - IOAcceleratorFamily - IOKit - Kernel - OpenSSL - Screen Sharing Server last seen 2020-06-01 modified 2020-06-02 plugin id 105081 published 2017-12-07 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/105081 title macOS and Mac OS X Multiple Vulnerabilities (Security Update 2017-002 and 2017-005) NASL family Fedora Local Security Checks NASL id FEDORA_2017-FDD3A98E8F.NASL description This is a release fixing a security fix applied upstream, known as last seen 2020-06-05 modified 2018-01-15 plugin id 106018 published 2018-01-15 reporter This script is Copyright (C) 2018-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/106018 title Fedora 27 : httpd (2017-fdd3a98e8f) (Optionsbleed) NASL family FreeBSD Local Security Checks NASL id FREEBSD_PKG_76B085E29D3311E79260000C292EE6B8.NASL description The Fuzzing Project reports : Apache httpd allows remote attackers to read secret data from process memory if the Limit directive can be set in a user last seen 2020-06-01 modified 2020-06-02 plugin id 103344 published 2017-09-20 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/103344 title FreeBSD : Apache -- HTTP OPTIONS method can leak server memory (76b085e2-9d33-11e7-9260-000c292ee6b8) (Optionsbleed) NASL family Red Hat Local Security Checks NASL id REDHAT-RHSA-2017-3477.NASL description An update is now available for JBoss Core Services on RHEL 6. Red Hat Product Security has rated this update as having a security impact of Important. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. Red Hat JBoss Core Services is a set of supplementary software for Red Hat JBoss middleware products. This software, such as Apache HTTP Server, is common to multiple JBoss middleware products, and is packaged under Red Hat JBoss Core Services to allow for faster distribution of updates, and for a more consistent update experience. This release of Red Hat JBoss Core Services Apache HTTP Server 2.4.23 Service Pack 3 serves as an update to Red Hat JBoss Core Services Apache HTTP Server 2.4.23 Service Pack 2, and includes bug fixes, which are documented in the Release Notes document linked to in the References. Security Fix(es) : * An out-of-bounds array dereference was found in apr_time_exp_get(). An attacker could abuse an unvalidated usage of this function to cause a denial of service or potentially lead to data leak. (CVE-2017-12613) * It was discovered that the use of httpd last seen 2020-06-01 modified 2020-06-02 plugin id 105369 published 2017-12-19 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/105369 title RHEL 6 : Red Hat JBoss Core Services Apache HTTP Server 2.4.23 (RHSA-2017:3477) (Optionsbleed) NASL family Debian Local Security Checks NASL id DEBIAN_DLA-1102.NASL description Hanno Boeck discovered that incorrect parsing of Limit directives of .htaccess files by the Apache HTTP Server could result in memory disclosure. For Debian 7 last seen 2020-03-17 modified 2017-09-22 plugin id 103389 published 2017-09-22 reporter This script is Copyright (C) 2017-2020 Tenable Network Security, Inc. source https://www.tenable.com/plugins/nessus/103389 title Debian DLA-1102-1 : apache2 security update (Optionsbleed) NASL family Red Hat Local Security Checks NASL id REDHAT-RHSA-2017-3194.NASL description An update for httpd is now available for Red Hat Enterprise Linux 7.3 Extended Update Support. Red Hat Product Security has rated this update as having a security impact of Important. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. The httpd packages provide the Apache HTTP Server, a powerful, efficient, and extensible web server. Security Fix(es) : * It was discovered that the httpd last seen 2020-06-01 modified 2020-06-02 plugin id 104540 published 2017-11-14 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/104540 title RHEL 7 : httpd (RHSA-2017:3194) (Optionsbleed) NASL family SuSE Local Security Checks NASL id OPENSUSE-2018-389.NASL description This update for VirtualBox to version 5.1.36 fixes multiple issues : Security issues fixed : - CVE-2018-0739: Unauthorized remote attacker may have caused a hang or frequently repeatable crash (complete DOS) - CVE-2018-2830: Attacker with host login may have compromised Virtualbox or further system services after interaction with a third user - CVE-2018-2831: Attacker with host login may have compromised VirtualBox or further system services, allowing read access to some data - CVE-2018-2835: Attacker with host login may have gained control over VirtualBox and possibly further system services after interacting with a third user - CVE-2018-2836: Attacker with host login may have gained control over VirtualBox and possibly further system services after interacting with a third user - CVE-2018-2837: Attacker with host login may have gained control over VirtualBox and possibly further system services after interacting with a third user - CVE-2018-2842: Attacker with host login may have gained control over VirtualBox and possibly further system services after interacting with a third user - CVE-2018-2843: Attacker with host login may have gained control over VirtualBox and possibly further system services after interacting with a third user - CVE-2018-2844: Attacker with host login may have gained control over VirtualBox and possibly further system services after interacting with a third user - CVE-2018-2845: Attacker with host login may have caused a hang or frequently repeatable crash (complete DOS), and perform unauthorized read and write operation to some VirtualBox accessible data - CVE-2018-2860: Privileged attacker may have gained control over VirtualBox and possibly further system services http://www.oracle.com/technetwork/security-advisory/cpuapr2018verbose- 3678108.html http://www.oracle.com/technetwork/security-advisory/cpuapr2018-3678067 .html#AppendixOVIR This update also contains all upstream fixes and improvements in the stable 5.1.36 release. last seen 2020-06-05 modified 2018-04-24 plugin id 109294 published 2018-04-24 reporter This script is Copyright (C) 2018-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/109294 title openSUSE Security Update : virtualbox (openSUSE-2018-389) (Optionsbleed) NASL family Oracle Linux Local Security Checks NASL id ORACLELINUX_ELSA-2017-2972.NASL description From Red Hat Security Advisory 2017:2972 : An update for httpd is now available for Red Hat Enterprise Linux 6. Red Hat Product Security has rated this update as having a security impact of Moderate. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. The httpd packages provide the Apache HTTP Server, a powerful, efficient, and extensible web server. Security Fix(es) : * A use-after-free flaw was found in the way httpd handled invalid and previously unregistered HTTP methods specified in the Limit directive used in an .htaccess file. A remote attacker could possibly use this flaw to disclose portions of the server memory, or cause httpd child process to crash. (CVE-2017-9798) * A regression was found in the Red Hat Enterprise Linux 6.9 version of httpd, causing comments in the last seen 2020-06-01 modified 2020-06-02 plugin id 104002 published 2017-10-20 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/104002 title Oracle Linux 6 : httpd (ELSA-2017-2972) (Optionsbleed) NASL family Huawei Local Security Checks NASL id EULEROS_SA-2019-1419.NASL description According to the versions of the httpd packages installed, the EulerOS Virtualization installation on the remote host is affected by the following vulnerabilities : - The log_cookie function in mod_log_config.c in the mod_log_config module in the Apache HTTP Server before 2.4.8 allows remote attackers to cause a denial of service (segmentation fault and daemon crash) via a crafted cookie that is not properly handled during truncation.(CVE-2014-0098) - A race condition flaw, leading to heap-based buffer overflows, was found in the mod_status httpd module. A remote attacker able to access a status page served by mod_status on a server using a threaded Multi-Processing Module (MPM) could send a specially crafted request that would cause the httpd child process to crash or, possibly, allow the attacker to execute arbitrary code with the privileges of the last seen 2020-06-01 modified 2020-06-02 plugin id 124922 published 2019-05-14 reporter This script is Copyright (C) 2019-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/124922 title EulerOS Virtualization 3.0.1.0 : httpd (EulerOS-SA-2019-1419) NASL family Web Servers NASL id SUN_JAVA_WEB_SERVER_7_0_27.NASL description According to its self-reported version, the Oracle iPlanet Web Server (formerly known as Sun Java System Web Server) running on the remote host is 7.0.x prior to 7.0.27 Patch 26834070. It is, therefore, affected by an unspecified vulnerability in the Network Security Services (NSS) library with unknown impact. last seen 2020-06-01 modified 2020-06-02 plugin id 106349 published 2018-01-25 reporter This script is Copyright (C) 2018-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/106349 title Oracle iPlanet Web Server 7.0.x < 7.0.27 NSS Unspecified Vulnerability (January 2018 CPU) NASL family Ubuntu Local Security Checks NASL id UBUNTU_USN-3425-1.NASL description Hanno Bock discovered that the Apache HTTP Server incorrectly handled Limit directives in .htaccess files. In certain configurations, a remote attacker could possibly use this issue to read arbitrary server memory, including sensitive information. This issue is known as Optionsbleed. Note that Tenable Network Security has extracted the preceding description block directly from the Ubuntu security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 103356 published 2017-09-20 reporter Ubuntu Security Notice (C) 2017-2019 Canonical, Inc. / NASL script (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/103356 title Ubuntu 14.04 LTS / 16.04 LTS / 17.04 : apache2 vulnerability (USN-3425-1) (Optionsbleed) NASL family Huawei Local Security Checks NASL id EULEROS_SA-2017-1253.NASL description According to the version of the httpd packages installed, the EulerOS installation on the remote host is affected by the following vulnerability : - A use-after-free flaw was found in the way httpd handled invalid and previously unregistered HTTP methods specified in the Limit directive used in an .htaccess file. A remote attacker could possibly use this flaw to disclose portions of the server memory, or cause httpd child process to crash. (CVE-2017-9798) Note that Tenable Network Security has extracted the preceding description block directly from the EulerOS security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-05-06 modified 2017-11-01 plugin id 104278 published 2017-11-01 reporter This script is Copyright (C) 2017-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/104278 title EulerOS 2.0 SP2 : httpd (EulerOS-SA-2017-1253) NASL family SuSE Local Security Checks NASL id SUSE_SU-2017-2907-1.NASL description This update for apache2 fixes the following issues : - Allow disabling SNI on proxy connections using last seen 2020-06-01 modified 2020-06-02 plugin id 104270 published 2017-10-31 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/104270 title SUSE SLES11 Security Update : apache2 (SUSE-SU-2017:2907-1) (Optionsbleed) NASL family CGI abuses NASL id ORACLE_PRIMAVERA_P6_EPPM_CPU_APR_2019.NASL description According to its self-reported version number, the Oracle Primavera P6 Enterprise Project Portfolio Management (EPPM) installation running on the remote web server is 8.4 prior to 8.4.15.10, 15.x prior to 15.2.18.4, 16.x prior to 16.2.17.2, 17.x prior to 17.12.12.0, or 18.x prior to 18.8.8.0. It is, therefore, affected by multiple vulnerabilities: - A deserialization vulnerability in Apache Commons FileUpload allows for remote code execution. (CVE-2016-1000031) - A denial of service vulnerability in the bundled third-party component OpenSSL library last seen 2020-06-01 modified 2020-06-02 plugin id 124169 published 2019-04-19 reporter This script is Copyright (C) 2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/124169 title Oracle Primavera P6 Enterprise Project Portfolio Management (EPPM) Multiple Vulnerabilities (Apr 2019 CPU) NASL family SuSE Local Security Checks NASL id SUSE_SU-2017-2756-1.NASL description This update for apache2 fixes several issues. These security issues were fixed : - CVE-2017-9798: Prevent use-after-free use of memory that allowed for an information leak via OPTIONS (bsc#1058058) - CVE-2017-9788: Uninitialized memory reflection in mod_auth_digest could have lead to leakage of potentially confidential information, and a segfault in other cases resulting in DoS (bsc#1048576). - CVE-2017-7679: mod_mime could have read one byte past the end of a buffer when sending a malicious Content-Type response header (bsc#1045060). - CVE-2017-3169: mod_ssl may dereferenced a NULL pointer when third-party modules call ap_hook_process_connection() during an HTTP request to an HTTPS port allowing for DoS (bsc#1045062). - CVE-2017-3167: Use of the ap_get_basic_auth_pw() by third-party modules outside of the authentication phase may have lead to authentication requirements being bypassed (bsc#1045065). The update package also includes non-security fixes. See advisory for details. Note that Tenable Network Security has extracted the preceding description block directly from the SUSE security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 103961 published 2017-10-19 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/103961 title SUSE SLES12 Security Update : apache2 (SUSE-SU-2017:2756-1) (Optionsbleed) NASL family Scientific Linux Local Security Checks NASL id SL_20171019_HTTPD_ON_SL6_X.NASL description Security Fix(es) : - A use-after-free flaw was found in the way httpd handled invalid and previously unregistered HTTP methods specified in the Limit directive used in an .htaccess file. A remote attacker could possibly use this flaw to disclose portions of the server memory, or cause httpd child process to crash. (CVE-2017-9798) - A regression was found in the Scientific Linux 6.9 version of httpd, causing comments in the last seen 2020-03-18 modified 2017-10-20 plugin id 104007 published 2017-10-20 reporter This script is Copyright (C) 2017-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/104007 title Scientific Linux Security Update : httpd on SL6.x i386/x86_64 (20171019) (Optionsbleed) NASL family Web Servers NASL id ORACLE_HTTP_SERVER_CPU_JAN_2018.NASL description The version of Oracle HTTP Server installed on the remote host is affected by multiple vulnerabilities as noted in the January 2018 CPU advisory. last seen 2020-03-18 modified 2018-01-24 plugin id 106299 published 2018-01-24 reporter This script is Copyright (C) 2018-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/106299 title Oracle Fusion Middleware Oracle HTTP Server Multiple Vulnerabilities (January 2018 CPU) NASL family Red Hat Local Security Checks NASL id REDHAT-RHSA-2017-2882.NASL description An update for httpd is now available for Red Hat Enterprise Linux 7. Red Hat Product Security has rated this update as having a security impact of Moderate. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. The httpd packages provide the Apache HTTP Server, a powerful, efficient, and extensible web server. Security Fix(es) : * A use-after-free flaw was found in the way httpd handled invalid and previously unregistered HTTP methods specified in the Limit directive used in an .htaccess file. A remote attacker could possibly use this flaw to disclose portions of the server memory, or cause httpd child process to crash. (CVE-2017-9798) Red Hat would like to thank Hanno Bock for reporting this issue. last seen 2020-06-01 modified 2020-06-02 plugin id 103804 published 2017-10-12 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/103804 title RHEL 7 : httpd (RHSA-2017:2882) (Optionsbleed) NASL family Debian Local Security Checks NASL id DEBIAN_DSA-3980.NASL description Hanno Boeck discovered that incorrect parsing of Limit directives of .htaccess files by the Apache HTTP Server could result in memory disclosure. last seen 2020-06-01 modified 2020-06-02 plugin id 103364 published 2017-09-21 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/103364 title Debian DSA-3980-1 : apache2 - security update (Optionsbleed) NASL family SuSE Local Security Checks NASL id SUSE_SU-2017-2542-1.NASL description This update for apache2 fixes the following security issue : - CVE-2017-9798: Prevent use-after-free use of memory that allowed for an information leak via OPTIONS (bsc#1058058). Note that Tenable Network Security has extracted the preceding description block directly from the SUSE security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 103413 published 2017-09-22 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/103413 title SUSE SLES12 Security Update : apache2 (SUSE-SU-2017:2542-1) (Optionsbleed) NASL family SuSE Local Security Checks NASL id SUSE_SU-2017-2718-1.NASL description This update for apache2 fixes one issues. This security issue was fixed : - CVE-2017-9798: Prevent use-after-free use of memory that allowed for an information leak via OPTIONS (bsc#1058058) Note that Tenable Network Security has extracted the preceding description block directly from the SUSE security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 103833 published 2017-10-13 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/103833 title SUSE SLES12 Security Update : apache2 (SUSE-SU-2017:2718-1) (Optionsbleed) NASL family Huawei Local Security Checks NASL id EULEROS_SA-2017-1252.NASL description According to the version of the httpd packages installed, the EulerOS installation on the remote host is affected by the following vulnerability : - A use-after-free flaw was found in the way httpd handled invalid and previously unregistered HTTP methods specified in the Limit directive used in an .htaccess file. A remote attacker could possibly use this flaw to disclose portions of the server memory, or cause httpd child process to crash. (CVE-2017-9798) Note that Tenable Network Security has extracted the preceding description block directly from the EulerOS security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-05-06 modified 2017-11-01 plugin id 104277 published 2017-11-01 reporter This script is Copyright (C) 2017-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/104277 title EulerOS 2.0 SP1 : httpd (EulerOS-SA-2017-1252)
Redhat
| advisories |
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| rpms |
|
Seebug
| bulletinFamily | exploit |
| description | If you're using the HTTP protocol in everday Internet use you are usually only using two of its methods: GET and POST. However HTTP has a number of other methods, so I wondered what you can do with them and if there are any vulnerabilities. One HTTP method is called OPTIONS. It simply allows asking a server which other HTTP methods it supports. The server answers with the "Allow" header and gives us a comma separated list of supported methods. A scan of the Alexa Top 1 Million revealed something strange: Plenty of servers sent out an "Allow" header with what looked like corrupted data. Some examples: ``` Allow: ,GET,,,POST,OPTIONS,HEAD,, Allow: POST,OPTIONS,,HEAD,:09:44 GMT Allow: GET,HEAD,OPTIONS,,HEAD,,HEAD,,HEAD,, HEAD,,HEAD,,HEAD,,HEAD,POST,,HEAD,, HEAD,!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd" Allow: GET,HEAD,OPTIONS,=write HTTP/1.0,HEAD,,HEAD,POST,,HEAD,TRACE ``` 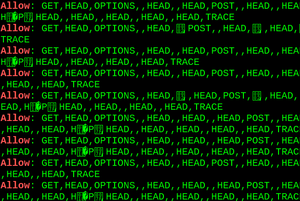 That clearly looked interesting - and dangerous. It suspiciously looked like a "bleed"-style bug, which has become a name for bugs where arbitrary pieces of memory are leaked to a potential attacker. However these were random servers on the Internet, so at first I didn't know what software was causing this. Sometimes HTTP servers send a "Server" header telling the software. However one needs to be aware that the "Server" header can lie. It's quite common to have one HTTP server proxying another. I got all kinds of different "Server" headers back, but I very much suspected that these were all from the same bug. I tried to contact the affected server operators, but only one of them answered, and he was extremely reluctant to tell me anything about his setup, so that wasn't very helpful either. However I got one clue: Some of the corrupted headers contained strings that were clearly configuration options from Apache. It seemed quite unlikely that those would show up in the memory of other server software. But I was unable to reproduce anything alike on my own Apache servers. I also tried reading the code that put together the Allow header to see if I can find any clues, but with no success. So without knowing any details I contacted the Apache security team. Fortunately Apache developer Jacob Champion digged into it and figured out what was going on: Apache supports a configuration directive Limit that allows restricting access to certain HTTP methods to a specific user. And if one sets the [Limit](https://httpd.apache.org/docs/2.4/mod/core.html#limit) directive in an .htaccess file for an HTTP method that's not globally registered in the server then the corruption happens. After that I was able to reproduce it myself. Setting a Limit directive for any invalid HTTP method in an .htaccess file caused a use after free error in the construction of the Allow header which was also [detectable with Address Sanitizer](https://blog.fuzzing-project.org/uploads/optionsbleed-asan.txt). (However ASAN doesn't work reliable due to the memory allocation abstraction done by APR.) ### FAQ #### What's Optionsbleed? Optionsbleed is a use after free error in Apache HTTP that causes a corrupted Allow header to be constructed in response to HTTP OPTIONS requests. This can leak pieces of arbitrary memory from the server process that may contain secrets. The memory pieces change after multiple requests, so for a vulnerable host an arbitrary number of memory chunks can be leaked. The bug appears if a webmaster tries to use the "Limit" directive with an invalid HTTP method. Example `.htaccess`: ``` <Limit abcxyz> </Limit> ``` #### How prevalent is it? Scanning the Alexa Top 1 Million revealed 466 hosts with corrupted Allow headers. In theory it's possible that other server software has similar bugs. On the other hand this bug is nondeterministic, so not all vulnerable hosts may have been catched. #### So it only happens if you set a quite unusual configuration option? There's an additional risk in shared hosting environments. The corruption is not limited to a single virtual host. One customer of a shared hosting provider could deliberately create an .htaccess file causing this corruption hoping to be able to extract secret data from other hosts on the same system. #### I can't reproduce it! Due to its nature the bug doesn't appear deterministically. It only seems to appear on busy servers. Sometimes it only appears after multiple requests. #### Does it have a CVE? [CVE-2017-9798](https://nvd.nist.gov/vuln/detail/CVE-2017-9798). #### I'm seeing Allow headers containing HEAD multiple times! This is actually a different Apache bug ([#61207](https://bz.apache.org/bugzilla/show_bug.cgi?id=61207)) that I found during this investigation. It causes HEAD to appear three times instead of once. However it's harmless and not a security bug. Launchpad also has [a harmless bug that produces a malformed Allow header](https://bugs.launchpad.net/launchpad/+bug/1717682), using a space-separated list instead of a comma-separated one. #### How can I test it? A simple way is to use Curl in a loop and send OPTIONS requests: ``` for i in {1..100}; do curl -sI -X OPTIONS https://www.google.com/|grep -i "allow:"; done ``` Depending on the server configuration it may not answer to OPTIONS requests on some URLs. Try different paths, HTTP versus HTTPS hosts, non-www versus www etc. may lead to different results. Please note that this bug does not show up with the "*" OPTIONS target, you need a specific path. Here's a [python proof of concept script](https://github.com/hannob/optionsbleed). #### What shall I do? If you run an Apache web server you should update. Most distributions should have updated packages by now or very soon. A patch can [be found here](https://svn.apache.org/viewvc/httpd/httpd/branches/2.4.x/server/core.c?r1=1805223&r2=1807754&pathrev=1807754&view=patch). A patch for Apache 2.2 is [available here](https://blog.fuzzing-project.org/uploads/apache-2.2-optionsbleed-backport.patch) (thanks to Thomas Deutschmann for backporting it). Unfortunately the communication with the Apache security team wasn't ideal. They were unable to provide a timeline for a coordinated release with a fix, so I decided to define a disclosure date on my own without an upstream fix. If you run an Apache web server in a shared hosting environment that allows users to create .htaccess files you should drop everything you do right now, update immediately and make sure you restart the server afterwards. #### Is this as bad as Heartbleed? No. Although similar in nature, this bug leaks only small chunks of memory and more importantly only affects a small number of hosts by default. It's still a pretty bad bug, particularly for shared hosting environments. |
| id | SSV:96537 |
| last seen | 2017-11-19 |
| modified | 2017-09-19 |
| published | 2017-09-19 |
| reporter | Root |
| source | https://www.seebug.org/vuldb/ssvid-96537 |
| title | HTTP OPTIONS method can leak Apache's server memory(CVE-2017-9798) (Optionsbleed) |
References
- https://security-tracker.debian.org/tracker/CVE-2017-9798
- https://github.com/hannob/optionsbleed
- https://blog.fuzzing-project.org/uploads/apache-2.2-optionsbleed-backport.patch
- https://blog.fuzzing-project.org/60-Optionsbleed-HTTP-OPTIONS-method-can-leak-Apaches-server-memory.html
- http://openwall.com/lists/oss-security/2017/09/18/2
- https://svn.apache.org/viewvc/httpd/httpd/branches/2.4.x/server/core.c?r1=1805223&r2=1807754&pathrev=1807754&view=patch
- https://www.exploit-db.com/exploits/42745/
- http://www.securitytracker.com/id/1039387
- http://www.securityfocus.com/bid/100872
- https://security.gentoo.org/glsa/201710-32
- http://www.debian.org/security/2017/dsa-3980
- https://access.redhat.com/errata/RHSA-2017:3240
- https://access.redhat.com/errata/RHSA-2017:3239
- https://access.redhat.com/errata/RHSA-2017:3195
- https://access.redhat.com/errata/RHSA-2017:3194
- https://access.redhat.com/errata/RHSA-2017:3193
- https://access.redhat.com/errata/RHSA-2017:3114
- https://access.redhat.com/errata/RHSA-2017:3113
- https://access.redhat.com/errata/RHSA-2017:3018
- https://access.redhat.com/errata/RHSA-2017:2972
- https://access.redhat.com/errata/RHSA-2017:2882
- https://access.redhat.com/errata/RHSA-2017:3477
- https://access.redhat.com/errata/RHSA-2017:3476
- https://access.redhat.com/errata/RHSA-2017:3475
- https://support.apple.com/HT208331
- http://www.oracle.com/technetwork/security-advisory/cpujan2018-3236628.html
- http://www.oracle.com/technetwork/security-advisory/cpuapr2018-3678067.html
- https://security.netapp.com/advisory/ntap-20180601-0003/
- http://www.oracle.com/technetwork/security-advisory/cpujul2018-4258247.html
- http://www.oracle.com/technetwork/security-advisory/cpuoct2018-4428296.html
- http://www.securityfocus.com/bid/105598
- https://www.oracle.com/technetwork/security-advisory/cpujan2019-5072801.html
- https://support.hpe.com/hpsc/doc/public/display?docLocale=en_US&docId=emr_na-hpesbux03909en_us
- https://httpd.apache.org/security/vulnerabilities_24.html#CVE-2017-9798
- https://www.oracle.com/technetwork/security-advisory/cpuapr2019-5072813.html
- https://www.tenable.com/security/tns-2019-09
- https://github.com/apache/httpd/commit/4cc27823899e070268b906ca677ee838d07cf67a
- https://lists.apache.org/thread.html/56c2e7cc9deb1c12a843d0dc251ea7fd3e7e80293cde02fcd65286ba%40%3Ccvs.httpd.apache.org%3E
- https://lists.apache.org/thread.html/84a3714f0878781f6ed84473d1a503d2cc382277e100450209231830%40%3Ccvs.httpd.apache.org%3E
- https://lists.apache.org/thread.html/8d63cb8e9100f28a99429b4328e4e7cebce861d5772ac9863ba2ae6f%40%3Ccvs.httpd.apache.org%3E
- https://lists.apache.org/thread.html/f7f95ac1cd9895db2714fa3ebaa0b94d0c6df360f742a40951384a53%40%3Ccvs.httpd.apache.org%3E
- https://lists.apache.org/thread.html/r57608dc51b79102f3952ae06f54d5277b649c86d6533dcd6a7d201f7%40%3Ccvs.httpd.apache.org%3E
- https://lists.apache.org/thread.html/rd18c3c43602e66f9cdcf09f1de233804975b9572b0456cc582390b6f%40%3Ccvs.httpd.apache.org%3E
- https://lists.apache.org/thread.html/re3d27b6250aa8548b8845d314bb8a350b3df326cacbbfdfe4d455234%40%3Ccvs.httpd.apache.org%3E
- https://lists.apache.org/thread.html/rfbaf647d52c1cb843e726a0933f156366a806cead84fbd430951591b%40%3Ccvs.httpd.apache.org%3E
- https://lists.apache.org/thread.html/rf6449464fd8b7437704c55f88361b66f12d5b5f90bcce66af4be4ba9%40%3Ccvs.httpd.apache.org%3E
- https://lists.apache.org/thread.html/r9ea3538f229874c80a10af473856a81fbf5f694cd7f471cc679ba70b%40%3Ccvs.httpd.apache.org%3E
- https://lists.apache.org/thread.html/rc998b18880df98bafaade071346690c2bc1444adaa1a1ea464b93f0a%40%3Ccvs.httpd.apache.org%3E
- https://lists.apache.org/thread.html/r15f9aa4427581a1aecb4063f1b4b983511ae1c9935e2a0a6876dad3c%40%3Ccvs.httpd.apache.org%3E
- https://lists.apache.org/thread.html/rfcf929bd33a6833e3f0c35eebdad70d5060665f9c4e17ea467c66770%40%3Ccvs.httpd.apache.org%3E
- https://lists.apache.org/thread.html/rdca61ae990660bacb682295f2a09d34612b7bb5f457577fe17f4d064%40%3Ccvs.httpd.apache.org%3E
- https://lists.apache.org/thread.html/r9f93cf6dde308d42a9c807784e8102600d0397f5f834890708bf6920%40%3Ccvs.httpd.apache.org%3E
- https://lists.apache.org/thread.html/r6521a7f62276340eabdb3339b2aa9a38c5f59d978497a1f794af53be%40%3Ccvs.httpd.apache.org%3E
- https://lists.apache.org/thread.html/rcc44594d4d6579b90deccd4536b5d31f099ef563df39b094be286b9e%40%3Ccvs.httpd.apache.org%3E
- https://lists.apache.org/thread.html/r75cbe9ea3e2114e4271bbeca7aff96117b50c1b6eb7c4772b0337c1f%40%3Ccvs.httpd.apache.org%3E