Vulnerabilities > CVE-2016-10229 - Improperly Implemented Security Check for Standard vulnerability in multiple products
Attack vector
NETWORK Attack complexity
LOW Privileges required
NONE Confidentiality impact
HIGH Integrity impact
HIGH Availability impact
HIGH Summary
udp.c in the Linux kernel before 4.5 allows remote attackers to execute arbitrary code via UDP traffic that triggers an unsafe second checksum calculation during execution of a recv system call with the MSG_PEEK flag.
Vulnerable Configurations
Common Weakness Enumeration (CWE)
Nessus
NASL family Oracle Linux Local Security Checks NASL id ORACLELINUX_ELSA-2017-3565.NASL description Description of changes: kernel-uek [4.1.12-94.3.4.el7uek] - ipv6: catch a null skb before using it in a DTRACE (Shannon Nelson) [Orabug: 26075879] - sparc64: Do not retain old VM_SPARC_ADI flag when protection changes on page (Khalid Aziz) [Orabug: 26038830] [4.1.12-94.3.3.el7uek] - nfsd: stricter decoding of write-like NFSv2/v3 ops (J. Bruce Fields) [Orabug: 25986971] {CVE-2017-7895} [4.1.12-94.3.2.el7uek] - sparc64: Detect DAX ra+pgsz when hvapi minor doesn last seen 2020-06-01 modified 2020-06-02 plugin id 100233 published 2017-05-17 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/100233 title Oracle Linux 6 / 7 : Unbreakable Enterprise kernel (ELSA-2017-3565) code # # (C) Tenable Network Security, Inc. # # The descriptive text and package checks in this plugin were # extracted from Oracle Linux Security Advisory ELSA-2017-3565. # include("compat.inc"); if (description) { script_id(100233); script_version("3.10"); script_cvs_date("Date: 2019/09/27 13:00:38"); script_cve_id("CVE-2016-10229", "CVE-2017-7895"); script_name(english:"Oracle Linux 6 / 7 : Unbreakable Enterprise kernel (ELSA-2017-3565)"); script_summary(english:"Checks rpm output for the updated packages"); script_set_attribute( attribute:"synopsis", value:"The remote Oracle Linux host is missing one or more security updates." ); script_set_attribute( attribute:"description", value: "Description of changes: kernel-uek [4.1.12-94.3.4.el7uek] - ipv6: catch a null skb before using it in a DTRACE (Shannon Nelson) [Orabug: 26075879] - sparc64: Do not retain old VM_SPARC_ADI flag when protection changes on page (Khalid Aziz) [Orabug: 26038830] [4.1.12-94.3.3.el7uek] - nfsd: stricter decoding of write-like NFSv2/v3 ops (J. Bruce Fields) [Orabug: 25986971] {CVE-2017-7895} [4.1.12-94.3.2.el7uek] - sparc64: Detect DAX ra+pgsz when hvapi minor doesn't indicate it (Rob Gardner) [Orabug: 25997533] - sparc64: DAX memory will use RA+PGSZ feature in HV (Rob Gardner) [Orabug: 25997533] [Orabug: 25931417] - sparc64: Disable DAX flow control (Rob Gardner) [Orabug: 25997226] - sparc64: DAX memory needs persistent mappings (Rob Gardner) [Orabug: 25997137] - sparc64: Fix incorrect error print in DAX driver when validating ccb (Sanath Kumar) [Orabug: 25996975] - sparc64: DAX request for non 4MB memory should return with unique errno (Sanath Kumar) [Orabug: 25996823] - sparc64: DAX request to mmap non 4MB memory should fail with a debug print (Sanath Kumar) [Orabug: 25996823] - sparc64: DAX request for non 4MB memory should return with unique errno (Sanath Kumar) [Orabug: 25996823] - sparc64: Incorrect print by DAX driver when old driver API is used (Sanath Kumar) [Orabug: 25996790] - sparc64: DAX request to dequeue half of a long CCB should not succeed (Sanath Kumar) [Orabug: 25996747] - sparc64: dax_overflow_check reports incorrect data (Sanath Kumar) [Orabug: 25996655] - sparc64: Ignored DAX ref count causes lockup (Rob Gardner) [Orabug: 25996628] - sparc64: disable dax page range checking on RA (Rob Gardner) [Orabug: 25996546] - sparc64: Oracle Data Analytics Accelerator (DAX) driver (Sanath Kumar) [Orabug: 25996522] - sparc64: Add DAX hypervisor services (Allen Pais) [Orabug: 25996475] - sparc64: create/destroy cpu sysfs dynamically (Atish Patra) [Orabug: 21775890] [Orabug: 25216469] - megaraid: Fix unaligned warning (Allen Pais) [Orabug: 24817799] [4.1.12-94.3.1.el7uek] - Re-enable SDP for uek-nano kernel (Ashok Vairavan) [Orabug: 25968572] - xsigo: Compute node crash on FC failover (Pradeep Gopanapalli) [Orabug: 25946533] - NVMe: Set affinity after allocating request queues (Keith Busch) [Orabug: 25945973] - nvme: use an integer value to Linux errno values (Christoph Hellwig) [Orabug: 25945973] - blk-mq: fix racy updates of rq->errors (Christoph Hellwig) [Orabug: 25945973] - x86/apic: Handle zero vector gracefully in clear_vector_irq() (Keith Busch) [Orabug: 24515998] - PCI: Prevent VPD access for QLogic ISP2722 (Ethan Zhao) [Orabug: 24819170] - PCI: Prevent VPD access for buggy devices (Babu Moger) [Orabug: 24819170] - ipv6: Skip XFRM lookup if dst_entry in socket cache is valid (Jakub Sitnicki) [Orabug: 25525433] - Btrfs: don't BUG_ON() in btrfs_orphan_add (Josef Bacik) [Orabug: 25534945] - Btrfs: clarify do_chunk_alloc()'s return value (Liu Bo) [Orabug: 25534945] - btrfs: flush_space: treat return value of do_chunk_alloc properly (Alex Lyakas) [Orabug: 25534945] - Revert '[SCSI] libiscsi: Reduce locking contention in fast path' (Ashish Samant) [Orabug: 25721518] - qla2xxx: Allow vref count to timeout on vport delete. (Joe Carnuccio) [Orabug: 25862953] - Drivers: hv: kvp: fix IP Failover (Vitaly Kuznetsov) [Orabug: 25866691] - Drivers: hv: util: Pass the channel information during the init call (K. Y. Srinivasan) [Orabug: 25866691] - Drivers: hv: utils: run polling callback always in interrupt context (Olaf Hering) [Orabug: 25866691] - Drivers: hv: util: Increase the timeout for util services (K. Y. Srinivasan) [Orabug: 25866691] - Drivers: hv: kvp: check kzalloc return value (Vitaly Kuznetsov) [Orabug: 25866691] - Drivers: hv: fcopy: dynamically allocate smsg_out in fcopy_send_data() (Vitaly Kuznetsov) - Drivers: hv: vss: full handshake support (Vitaly Kuznetsov) [Orabug: 25866691] - xen: Make VPMU init message look less scary (Juergen Gross) [Orabug: 25873416] - udp: properly support MSG_PEEK with truncated buffers (Eric Dumazet) [Orabug: 25876652] {CVE-2016-10229}" ); script_set_attribute( attribute:"see_also", value:"https://oss.oracle.com/pipermail/el-errata/2017-May/006909.html" ); script_set_attribute( attribute:"see_also", value:"https://oss.oracle.com/pipermail/el-errata/2017-May/006910.html" ); script_set_attribute( attribute:"solution", value:"Update the affected unbreakable enterprise kernel packages." ); script_set_cvss_base_vector("CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:C"); script_set_cvss_temporal_vector("CVSS2#E:U/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:U/RL:O/RC:C"); script_set_attribute(attribute:"exploitability_ease", value:"No known exploits are available"); script_set_attribute(attribute:"exploit_available", value:"false"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:oracle:linux:dtrace-modules-4.1.12-94.3.4.el6uek"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:oracle:linux:dtrace-modules-4.1.12-94.3.4.el7uek"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:oracle:linux:kernel-uek"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:oracle:linux:kernel-uek-debug"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:oracle:linux:kernel-uek-debug-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:oracle:linux:kernel-uek-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:oracle:linux:kernel-uek-doc"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:oracle:linux:kernel-uek-firmware"); script_set_attribute(attribute:"cpe", value:"cpe:/o:oracle:linux:6"); script_set_attribute(attribute:"cpe", value:"cpe:/o:oracle:linux:7"); script_set_attribute(attribute:"vuln_publication_date", value:"2017/04/04"); script_set_attribute(attribute:"patch_publication_date", value:"2017/05/16"); script_set_attribute(attribute:"plugin_publication_date", value:"2017/05/17"); script_set_attribute(attribute:"generated_plugin", value:"current"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_copyright(english:"This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof."); script_family(english:"Oracle Linux Local Security Checks"); script_dependencies("ssh_get_info.nasl", "linux_alt_patch_detect.nasl"); script_require_keys("Host/local_checks_enabled", "Host/OracleLinux", "Host/RedHat/release", "Host/RedHat/rpm-list"); exit(0); } include("audit.inc"); include("global_settings.inc"); include("rpm.inc"); include("ksplice.inc"); if (!get_kb_item("Host/local_checks_enabled")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); if (!get_kb_item("Host/OracleLinux")) audit(AUDIT_OS_NOT, "Oracle Linux"); release = get_kb_item("Host/RedHat/release"); if (isnull(release) || !pregmatch(pattern: "Oracle (?:Linux Server|Enterprise Linux)", string:release)) audit(AUDIT_OS_NOT, "Oracle Linux"); os_ver = pregmatch(pattern: "Oracle (?:Linux Server|Enterprise Linux) .*release ([0-9]+(\.[0-9]+)?)", string:release); if (isnull(os_ver)) audit(AUDIT_UNKNOWN_APP_VER, "Oracle Linux"); os_ver = os_ver[1]; if (! preg(pattern:"^(6|7)([^0-9]|$)", string:os_ver)) audit(AUDIT_OS_NOT, "Oracle Linux 6 / 7", "Oracle Linux " + os_ver); if (!get_kb_item("Host/RedHat/rpm-list")) audit(AUDIT_PACKAGE_LIST_MISSING); cpu = get_kb_item("Host/cpu"); if (isnull(cpu)) audit(AUDIT_UNKNOWN_ARCH); if ("x86_64" >!< cpu && cpu !~ "^i[3-6]86$") audit(AUDIT_LOCAL_CHECKS_NOT_IMPLEMENTED, "Oracle Linux", cpu); if ("x86_64" >!< cpu) audit(AUDIT_ARCH_NOT, "x86_64", cpu); if (get_one_kb_item("Host/ksplice/kernel-cves")) { rm_kb_item(name:"Host/uptrack-uname-r"); cve_list = make_list("CVE-2016-10229", "CVE-2017-7895"); if (ksplice_cves_check(cve_list)) { audit(AUDIT_PATCH_INSTALLED, "KSplice hotfix for ELSA-2017-3565"); } else { __rpm_report = ksplice_reporting_text(); } } kernel_major_minor = get_kb_item("Host/uname/major_minor"); if (empty_or_null(kernel_major_minor)) exit(1, "Unable to determine kernel major-minor level."); expected_kernel_major_minor = "4.1"; if (kernel_major_minor != expected_kernel_major_minor) audit(AUDIT_OS_NOT, "running kernel level " + expected_kernel_major_minor + ", it is running kernel level " + kernel_major_minor); flag = 0; if (rpm_check(release:"EL6", cpu:"x86_64", reference:"dtrace-modules-4.1.12-94.3.4.el6uek-0.6.0-4.el6")) flag++; if (rpm_exists(release:"EL6", rpm:"kernel-uek-4.1.12") && rpm_check(release:"EL6", cpu:"x86_64", reference:"kernel-uek-4.1.12-94.3.4.el6uek")) flag++; if (rpm_exists(release:"EL6", rpm:"kernel-uek-debug-4.1.12") && rpm_check(release:"EL6", cpu:"x86_64", reference:"kernel-uek-debug-4.1.12-94.3.4.el6uek")) flag++; if (rpm_exists(release:"EL6", rpm:"kernel-uek-debug-devel-4.1.12") && rpm_check(release:"EL6", cpu:"x86_64", reference:"kernel-uek-debug-devel-4.1.12-94.3.4.el6uek")) flag++; if (rpm_exists(release:"EL6", rpm:"kernel-uek-devel-4.1.12") && rpm_check(release:"EL6", cpu:"x86_64", reference:"kernel-uek-devel-4.1.12-94.3.4.el6uek")) flag++; if (rpm_exists(release:"EL6", rpm:"kernel-uek-doc-4.1.12") && rpm_check(release:"EL6", cpu:"x86_64", reference:"kernel-uek-doc-4.1.12-94.3.4.el6uek")) flag++; if (rpm_exists(release:"EL6", rpm:"kernel-uek-firmware-4.1.12") && rpm_check(release:"EL6", cpu:"x86_64", reference:"kernel-uek-firmware-4.1.12-94.3.4.el6uek")) flag++; if (rpm_check(release:"EL7", cpu:"x86_64", reference:"dtrace-modules-4.1.12-94.3.4.el7uek-0.6.0-4.el7")) flag++; if (rpm_exists(release:"EL7", rpm:"kernel-uek-4.1.12") && rpm_check(release:"EL7", cpu:"x86_64", reference:"kernel-uek-4.1.12-94.3.4.el7uek")) flag++; if (rpm_exists(release:"EL7", rpm:"kernel-uek-debug-4.1.12") && rpm_check(release:"EL7", cpu:"x86_64", reference:"kernel-uek-debug-4.1.12-94.3.4.el7uek")) flag++; if (rpm_exists(release:"EL7", rpm:"kernel-uek-debug-devel-4.1.12") && rpm_check(release:"EL7", cpu:"x86_64", reference:"kernel-uek-debug-devel-4.1.12-94.3.4.el7uek")) flag++; if (rpm_exists(release:"EL7", rpm:"kernel-uek-devel-4.1.12") && rpm_check(release:"EL7", cpu:"x86_64", reference:"kernel-uek-devel-4.1.12-94.3.4.el7uek")) flag++; if (rpm_exists(release:"EL7", rpm:"kernel-uek-doc-4.1.12") && rpm_check(release:"EL7", cpu:"x86_64", reference:"kernel-uek-doc-4.1.12-94.3.4.el7uek")) flag++; if (rpm_exists(release:"EL7", rpm:"kernel-uek-firmware-4.1.12") && rpm_check(release:"EL7", cpu:"x86_64", reference:"kernel-uek-firmware-4.1.12-94.3.4.el7uek")) flag++; if (flag) { if (report_verbosity > 0) security_hole(port:0, extra:rpm_report_get()); else security_hole(0); exit(0); } else { tested = pkg_tests_get(); if (tested) audit(AUDIT_PACKAGE_NOT_AFFECTED, tested); else audit(AUDIT_PACKAGE_NOT_INSTALLED, "affected kernel"); }NASL family Oracle Linux Local Security Checks NASL id ORACLELINUX_ELSA-2017-3566.NASL description Description of changes: kernel-uek [3.8.13-118.18.2.el7uek] - nfsd: stricter decoding of write-like NFSv2/v3 ops (J. Bruce Fields) [Orabug: 25986990] {CVE-2017-7895} [3.8.13-118.18.1.el7uek] - fnic: Update fnic driver version to 1.6.0.24 (John Sobecki) [Orabug: 24448585] - xen-netfront: Rework the fix for Rx stall during OOM and network stress (Dongli Zhang) [Orabug: 25450703] - xen-netfront: Fix Rx stall during network stress and OOM (Dongli Zhang) [Orabug: 25450703] - ipv6: Skip XFRM lookup if dst_entry in socket cache is valid (Jakub Sitnicki) - uek-rpm: enable CONFIG_KSPLICE. (Jamie Iles) [Orabug: 25549809] - ksplice: add sysctls for determining Ksplice features. (Jamie Iles) [Orabug: 25549809] - signal: protect SIGNAL_UNKILLABLE from unintentional clearing. (Jamie Iles) [Orabug: 25549809] - VSOCK: Fix lockdep issue. (Dongli Zhang) [Orabug: 25559937] - VSOCK: sock_put wasn last seen 2020-06-01 modified 2020-06-02 plugin id 100234 published 2017-05-17 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/100234 title Oracle Linux 6 / 7 : Unbreakable Enterprise kernel (ELSA-2017-3566) code # # (C) Tenable Network Security, Inc. # # The descriptive text and package checks in this plugin were # extracted from Oracle Linux Security Advisory ELSA-2017-3566. # include("compat.inc"); if (description) { script_id(100234); script_version("3.11"); script_cvs_date("Date: 2019/09/27 13:00:38"); script_cve_id("CVE-2015-5257", "CVE-2015-6252", "CVE-2015-9731", "CVE-2016-10088", "CVE-2016-10142", "CVE-2016-10208", "CVE-2016-10229", "CVE-2016-2782", "CVE-2016-7910", "CVE-2016-8399", "CVE-2016-9644", "CVE-2017-2583", "CVE-2017-2647", "CVE-2017-5669", "CVE-2017-5986", "CVE-2017-6214", "CVE-2017-7184", "CVE-2017-7187", "CVE-2017-7895"); script_name(english:"Oracle Linux 6 / 7 : Unbreakable Enterprise kernel (ELSA-2017-3566)"); script_summary(english:"Checks rpm output for the updated packages"); script_set_attribute( attribute:"synopsis", value:"The remote Oracle Linux host is missing one or more security updates." ); script_set_attribute( attribute:"description", value: "Description of changes: kernel-uek [3.8.13-118.18.2.el7uek] - nfsd: stricter decoding of write-like NFSv2/v3 ops (J. Bruce Fields) [Orabug: 25986990] {CVE-2017-7895} [3.8.13-118.18.1.el7uek] - fnic: Update fnic driver version to 1.6.0.24 (John Sobecki) [Orabug: 24448585] - xen-netfront: Rework the fix for Rx stall during OOM and network stress (Dongli Zhang) [Orabug: 25450703] - xen-netfront: Fix Rx stall during network stress and OOM (Dongli Zhang) [Orabug: 25450703] - ipv6: Skip XFRM lookup if dst_entry in socket cache is valid (Jakub Sitnicki) - uek-rpm: enable CONFIG_KSPLICE. (Jamie Iles) [Orabug: 25549809] - ksplice: add sysctls for determining Ksplice features. (Jamie Iles) [Orabug: 25549809] - signal: protect SIGNAL_UNKILLABLE from unintentional clearing. (Jamie Iles) [Orabug: 25549809] - VSOCK: Fix lockdep issue. (Dongli Zhang) [Orabug: 25559937] - VSOCK: sock_put wasn't safe to call in interrupt context (Dongli Zhang) [Orabug: 25559937] - IB/CORE: sync the resouce access in fmr_pool (Wengang Wang) [Orabug: 25677469] - KVM: x86: fix emulation of 'MOV SS, null selector' (Paolo Bonzini) [Orabug: 25719675] {CVE-2017-2583} {CVE-2017-2583} - ext4: validate s_first_meta_bg at mount time (Eryu Guan) [Orabug: 25719738] {CVE-2016-10208} - sctp: avoid BUG_ON on sctp_wait_for_sndbuf (Marcelo Ricardo Leitner) [Orabug: 25719810] {CVE-2017-5986} - tcp: avoid infinite loop in tcp_splice_read() (Eric Dumazet) [Orabug: 25720813] {CVE-2017-6214} - lpfc cannot establish connection with targets that send PRLI under P2P mode (Joe Jin) [Orabug: 25759083] - USB: visor: fix null-deref at probe (Johan Hovold) [Orabug: 25796594] {CVE-2016-2782} - ipc/shm: Fix shmat mmap nil-page protection (Davidlohr Bueso) [Orabug: 25797012] {CVE-2017-5669} - vhost: actually track log eventfd file (Marc-André Lureau) [Orabug: 25797052] {CVE-2015-6252} - xfrm_user: validate XFRM_MSG_NEWAE incoming ESN size harder (Andy Whitcroft) [Orabug: 25814663] {CVE-2017-7184} - xfrm_user: validate XFRM_MSG_NEWAE XFRMA_REPLAY_ESN_VAL replay_window (Andy Whitcroft) [Orabug: 25814663] {CVE-2017-7184} - KEYS: Remove key_type::match in favour of overriding default by match_preparse (Aniket Alshi) [Orabug: 25823962] {CVE-2017-2647} {CVE-2017-2647} - USB: whiteheat: fix potential null-deref at probe (Johan Hovold) [Orabug: 25825105] {CVE-2015-5257} {CVE-2015-5257} - udf: Check path length when reading symlink (Jan Kara) [Orabug: 25871102] {CVE-2015-9731} - udp: properly support MSG_PEEK with truncated buffers (Eric Dumazet) [Orabug: 25876655] {CVE-2016-10229} - block: fix use-after-free in seq file (Vegard Nossum) [Orabug: 25877530] {CVE-2016-7910} - Revert 'fix minor infoleak in get_user_ex()' (Brian Maly) [Orabug: 25790392] {CVE-2016-9644} - net: ping: check minimum size on ICMP header length (Kees Cook) [Orabug: 25766911] {CVE-2016-8399} - ipv6: stop sending PTB packets for MTU < 1280 (Hagen Paul Pfeifer) [Orabug: 25765776] {CVE-2016-10142} - sg_write()/bsg_write() is not fit to be called under KERNEL_DS (Al Viro) [Orabug: 25765445] {CVE-2016-10088} - scsi: sg: check length passed to SG_NEXT_CMD_LEN (peter chang) [Orabug: 25751996] {CVE-2017-7187}" ); script_set_attribute( attribute:"see_also", value:"https://oss.oracle.com/pipermail/el-errata/2017-May/006911.html" ); script_set_attribute( attribute:"see_also", value:"https://oss.oracle.com/pipermail/el-errata/2017-May/006912.html" ); script_set_attribute( attribute:"solution", value:"Update the affected unbreakable enterprise kernel packages." ); script_set_cvss_base_vector("CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:C"); script_set_cvss_temporal_vector("CVSS2#E:POC/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:P/RL:O/RC:C"); script_set_attribute(attribute:"exploitability_ease", value:"Exploits are available"); script_set_attribute(attribute:"exploit_available", value:"true"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:oracle:linux:dtrace-modules-3.8.13-118.18.2.el6uek"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:oracle:linux:dtrace-modules-3.8.13-118.18.2.el7uek"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:oracle:linux:kernel-uek"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:oracle:linux:kernel-uek-debug"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:oracle:linux:kernel-uek-debug-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:oracle:linux:kernel-uek-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:oracle:linux:kernel-uek-doc"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:oracle:linux:kernel-uek-firmware"); script_set_attribute(attribute:"cpe", value:"cpe:/o:oracle:linux:6"); script_set_attribute(attribute:"cpe", value:"cpe:/o:oracle:linux:7"); script_set_attribute(attribute:"vuln_publication_date", value:"2015/10/19"); script_set_attribute(attribute:"patch_publication_date", value:"2017/05/16"); script_set_attribute(attribute:"plugin_publication_date", value:"2017/05/17"); script_set_attribute(attribute:"generated_plugin", value:"current"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_copyright(english:"This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof."); script_family(english:"Oracle Linux Local Security Checks"); script_dependencies("ssh_get_info.nasl", "linux_alt_patch_detect.nasl"); script_require_keys("Host/local_checks_enabled", "Host/OracleLinux", "Host/RedHat/release", "Host/RedHat/rpm-list"); exit(0); } include("audit.inc"); include("global_settings.inc"); include("rpm.inc"); include("ksplice.inc"); if (!get_kb_item("Host/local_checks_enabled")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); if (!get_kb_item("Host/OracleLinux")) audit(AUDIT_OS_NOT, "Oracle Linux"); release = get_kb_item("Host/RedHat/release"); if (isnull(release) || !pregmatch(pattern: "Oracle (?:Linux Server|Enterprise Linux)", string:release)) audit(AUDIT_OS_NOT, "Oracle Linux"); os_ver = pregmatch(pattern: "Oracle (?:Linux Server|Enterprise Linux) .*release ([0-9]+(\.[0-9]+)?)", string:release); if (isnull(os_ver)) audit(AUDIT_UNKNOWN_APP_VER, "Oracle Linux"); os_ver = os_ver[1]; if (! preg(pattern:"^(6|7)([^0-9]|$)", string:os_ver)) audit(AUDIT_OS_NOT, "Oracle Linux 6 / 7", "Oracle Linux " + os_ver); if (!get_kb_item("Host/RedHat/rpm-list")) audit(AUDIT_PACKAGE_LIST_MISSING); cpu = get_kb_item("Host/cpu"); if (isnull(cpu)) audit(AUDIT_UNKNOWN_ARCH); if ("x86_64" >!< cpu && cpu !~ "^i[3-6]86$") audit(AUDIT_LOCAL_CHECKS_NOT_IMPLEMENTED, "Oracle Linux", cpu); if ("x86_64" >!< cpu) audit(AUDIT_ARCH_NOT, "x86_64", cpu); if (get_one_kb_item("Host/ksplice/kernel-cves")) { rm_kb_item(name:"Host/uptrack-uname-r"); cve_list = make_list("CVE-2015-5257", "CVE-2015-6252", "CVE-2015-9731", "CVE-2016-10088", "CVE-2016-10142", "CVE-2016-10208", "CVE-2016-10229", "CVE-2016-2782", "CVE-2016-7910", "CVE-2016-8399", "CVE-2016-9644", "CVE-2017-2583", "CVE-2017-2647", "CVE-2017-5669", "CVE-2017-5986", "CVE-2017-6214", "CVE-2017-7184", "CVE-2017-7187", "CVE-2017-7895"); if (ksplice_cves_check(cve_list)) { audit(AUDIT_PATCH_INSTALLED, "KSplice hotfix for ELSA-2017-3566"); } else { __rpm_report = ksplice_reporting_text(); } } kernel_major_minor = get_kb_item("Host/uname/major_minor"); if (empty_or_null(kernel_major_minor)) exit(1, "Unable to determine kernel major-minor level."); expected_kernel_major_minor = "3.8"; if (kernel_major_minor != expected_kernel_major_minor) audit(AUDIT_OS_NOT, "running kernel level " + expected_kernel_major_minor + ", it is running kernel level " + kernel_major_minor); flag = 0; if (rpm_check(release:"EL6", cpu:"x86_64", reference:"dtrace-modules-3.8.13-118.18.2.el6uek-0.4.5-3.el6")) flag++; if (rpm_exists(release:"EL6", rpm:"kernel-uek-3.8.13") && rpm_check(release:"EL6", cpu:"x86_64", reference:"kernel-uek-3.8.13-118.18.2.el6uek")) flag++; if (rpm_exists(release:"EL6", rpm:"kernel-uek-debug-3.8.13") && rpm_check(release:"EL6", cpu:"x86_64", reference:"kernel-uek-debug-3.8.13-118.18.2.el6uek")) flag++; if (rpm_exists(release:"EL6", rpm:"kernel-uek-debug-devel-3.8.13") && rpm_check(release:"EL6", cpu:"x86_64", reference:"kernel-uek-debug-devel-3.8.13-118.18.2.el6uek")) flag++; if (rpm_exists(release:"EL6", rpm:"kernel-uek-devel-3.8.13") && rpm_check(release:"EL6", cpu:"x86_64", reference:"kernel-uek-devel-3.8.13-118.18.2.el6uek")) flag++; if (rpm_exists(release:"EL6", rpm:"kernel-uek-doc-3.8.13") && rpm_check(release:"EL6", cpu:"x86_64", reference:"kernel-uek-doc-3.8.13-118.18.2.el6uek")) flag++; if (rpm_exists(release:"EL6", rpm:"kernel-uek-firmware-3.8.13") && rpm_check(release:"EL6", cpu:"x86_64", reference:"kernel-uek-firmware-3.8.13-118.18.2.el6uek")) flag++; if (rpm_check(release:"EL7", cpu:"x86_64", reference:"dtrace-modules-3.8.13-118.18.2.el7uek-0.4.5-3.el7")) flag++; if (rpm_exists(release:"EL7", rpm:"kernel-uek-3.8.13") && rpm_check(release:"EL7", cpu:"x86_64", reference:"kernel-uek-3.8.13-118.18.2.el7uek")) flag++; if (rpm_exists(release:"EL7", rpm:"kernel-uek-debug-3.8.13") && rpm_check(release:"EL7", cpu:"x86_64", reference:"kernel-uek-debug-3.8.13-118.18.2.el7uek")) flag++; if (rpm_exists(release:"EL7", rpm:"kernel-uek-debug-devel-3.8.13") && rpm_check(release:"EL7", cpu:"x86_64", reference:"kernel-uek-debug-devel-3.8.13-118.18.2.el7uek")) flag++; if (rpm_exists(release:"EL7", rpm:"kernel-uek-devel-3.8.13") && rpm_check(release:"EL7", cpu:"x86_64", reference:"kernel-uek-devel-3.8.13-118.18.2.el7uek")) flag++; if (rpm_exists(release:"EL7", rpm:"kernel-uek-doc-3.8.13") && rpm_check(release:"EL7", cpu:"x86_64", reference:"kernel-uek-doc-3.8.13-118.18.2.el7uek")) flag++; if (rpm_exists(release:"EL7", rpm:"kernel-uek-firmware-3.8.13") && rpm_check(release:"EL7", cpu:"x86_64", reference:"kernel-uek-firmware-3.8.13-118.18.2.el7uek")) flag++; if (flag) { if (report_verbosity > 0) security_hole(port:0, extra:rpm_report_get()); else security_hole(0); exit(0); } else { tested = pkg_tests_get(); if (tested) audit(AUDIT_PACKAGE_NOT_AFFECTED, tested); else audit(AUDIT_PACKAGE_NOT_INSTALLED, "affected kernel"); }NASL family Huawei Local Security Checks NASL id EULEROS_SA-2019-1491.NASL description According to the versions of the kernel packages installed, the EulerOS Virtualization installation on the remote host is affected by the following vulnerabilities : - A use-after-free flaw was found in the way the Linux kernel last seen 2020-03-19 modified 2019-05-13 plugin id 124815 published 2019-05-13 reporter This script is Copyright (C) 2019-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/124815 title EulerOS Virtualization 3.0.1.0 : kernel (EulerOS-SA-2019-1491) code # # (C) Tenable Network Security, Inc. # include("compat.inc"); if (description) { script_id(124815); script_version("1.5"); script_set_attribute(attribute:"plugin_modification_date", value:"2020/03/19"); script_cve_id( "CVE-2016-0728", "CVE-2016-0758", "CVE-2016-0821", "CVE-2016-0823", "CVE-2016-10044", "CVE-2016-10088", "CVE-2016-10200", "CVE-2016-10208", "CVE-2016-10229", "CVE-2016-1575", "CVE-2016-1576", "CVE-2016-2053", "CVE-2016-2069", "CVE-2016-2070", "CVE-2016-2117", "CVE-2016-2184", "CVE-2016-2185", "CVE-2016-2186", "CVE-2016-2187", "CVE-2016-2188", "CVE-2016-2384", "CVE-2016-2543", "CVE-2016-2544" ); script_name(english:"EulerOS Virtualization 3.0.1.0 : kernel (EulerOS-SA-2019-1491)"); script_summary(english:"Checks the rpm output for the updated packages."); script_set_attribute(attribute:"synopsis", value: "The remote EulerOS Virtualization host is missing multiple security updates."); script_set_attribute(attribute:"description", value: "According to the versions of the kernel packages installed, the EulerOS Virtualization installation on the remote host is affected by the following vulnerabilities : - A use-after-free flaw was found in the way the Linux kernel's key management subsystem handled keyring object reference counting in certain error path of the join_session_keyring() function. A local, unprivileged user could use this flaw to escalate their privileges on the system.(CVE-2016-0728) - A flaw was found in the way the Linux kernel's ASN.1 DER decoder processed certain certificate files with tags of indefinite length. A local, unprivileged user could use a specially crafted X.509 certificate DER file to crash the system or, potentially, escalate their privileges on the system.(CVE-2016-0758) - The LIST_POISON feature in include/linux/poison.h in the Linux kernel before 4.3, as used in Android 6.0.1 before 2016-03-01, does not properly consider the relationship to the mmap_min_addr value, which makes it easier for attackers to bypass a poison-pointer protection mechanism by triggering the use of an uninitialized list entry, aka Android internal bug 26186802, a different vulnerability than CVE-2015-3636.(CVE-2016-0821) - The pagemap_open function in fs/proc/task_mmu.c in the Linux kernel before 3.19.3, as used in Android 6.0.1 before 2016-03-01, allows local users to obtain sensitive physical-address information by reading a pagemap file, aka Android internal bug 25739721.(CVE-2016-0823) - The aio_mount function in fs/aio.c in the Linux kernel does not properly restrict execute access, which makes it easier for local users to bypass intended SELinux W^X policy restrictions.(CVE-2016-10044) - It was found that the fix for CVE-2016-9576 was incomplete: the Linux kernel's sg implementation did not properly restrict write operations in situations where the KERNEL_DS option is set. A local attacker to read or write to arbitrary kernel memory locations or cause a denial of service (use-after-free) by leveraging write access to a /dev/sg device.(CVE-2016-10088) - A use-after-free flaw was found in the Linux kernel which enables a race condition in the L2TPv3 IP Encapsulation feature. A local user could use this flaw to escalate their privileges or crash the system.(CVE-2016-10200) - Mounting a crafted EXT4 image read-only leads to an attacker controlled memory corruption and SLAB-Out-of-Bounds reads.(CVE-2016-10208) - The Linux kernel allows remote attackers to execute arbitrary code via UDP traffic that triggers an unsafe second checksum calculation during execution of a recv system call with the MSG_PEEK flag. This may create a kernel panic or memory corruption leading to privilege escalation.(CVE-2016-10229) - The overlayfs implementation in the Linux kernel through 4.5.2 does not properly maintain POSIX ACL xattr data, which allows local users to gain privileges by leveraging a group-writable setgid directory.(CVE-2016-1575) - The overlayfs implementation in the Linux kernel through 4.5.2 does not properly restrict the mount namespace, which allows local users to gain privileges by mounting an overlayfs filesystem on top of a FUSE filesystem, and then executing a crafted setuid program.(CVE-2016-1576) - A syntax vulnerability was discovered in the kernel's ASN1.1 DER decoder, which could lead to memory corruption or a complete local denial of service through x509 certificate DER files. A local system user could use a specially created key file to trigger BUG_ON() in the public_key_verify_signature() function (crypto/asymmetric_keys/public_key.c), to cause a kernel panic and crash the system.(CVE-2016-2053) - A flaw was discovered in the way the Linux kernel dealt with paging structures. When the kernel invalidated a paging structure that was not in use locally, it could, in principle, race against another CPU that is switching to a process that uses the paging structure in question. A local user could use a thread running with a stale cached virtual-i1/4zphysical translation to potentially escalate their privileges if the translation in question were writable and the physical page got reused for something critical (for example, a page table).(CVE-2016-2069) - A divide-by-zero vulnerability was found in a way the kernel processes TCP connections. The error can occur if a connection starts another cwnd reduction phase by setting tp-i1/4zprior_cwnd to the current cwnd (0) in tcp_init_cwnd_reduction(). A remote, unauthenticated attacker could use this flaw to crash the kernel (denial of service).(CVE-2016-2070) - It was discovered that the atl2_probe() function in the Atheros L2 Ethernet driver in the Linux kernel incorrectly enabled scatter/gather I/O. A remote attacker could use this flaw to obtain potentially sensitive information from the kernel memory.(CVE-2016-2117) - The create_fixed_stream_quirk function in sound/usb/quirks.c in the snd-usb-audio driver in the Linux kernel before 4.5.1 allows physically proximate attackers to cause a denial of service (NULL pointer dereference or double free, and system crash) via a crafted endpoints value in a USB device descriptor.(CVE-2016-2184) - The ati_remote2_probe function in drivers/input/misc/ati_remote2.c in the Linux kernel before 4.5.1 allows physically proximate attackers to cause a denial of service (NULL pointer dereference and system crash) via a crafted endpoints value in a USB device descriptor.(CVE-2016-2185) - The powermate_probe function in drivers/input/misc/powermate.c in the Linux kernel before 4.5.1 allows physically proximate attackers to cause a denial of service (NULL pointer dereference and system crash) via a crafted endpoints value in a USB device descriptor.(CVE-2016-2186) - The gtco_probe function in drivers/input/tablet/gtco.c in the Linux kernel through 4.5.2 allows physically proximate attackers to cause a denial of service (NULL pointer dereference and system crash) via a crafted endpoints value in a USB device descriptor.(CVE-2016-2187) - The iowarrior_probe function in drivers/usb/misc/iowarrior.c in the Linux kernel before 4.5.1 allows physically proximate attackers to cause a denial of service (NULL pointer dereference and system crash) via a crafted endpoints value in a USB device descriptor.(CVE-2016-2188) - A flaw was found in the USB-MIDI Linux kernel driver: a double-free error could be triggered for the 'umidi' object. An attacker with physical access to the system could use this flaw to escalate their privileges.(CVE-2016-2384) - The snd_seq_ioctl_remove_events function in sound/core/seq/seq_clientmgr.c in the Linux kernel before 4.4.1 does not verify FIFO assignment before proceeding with FIFO clearing, which allows local users to cause a denial of service (NULL pointer dereference and OOPS) via a crafted ioctl call.(CVE-2016-2543) - Race condition in the queue_delete function in sound/core/seq/seq_queue.c in the Linux kernel before 4.4.1 allows local users to cause a denial of service (use-after-free and system crash) by making an ioctl call at a certain time.(CVE-2016-2544) Note that Tenable Network Security has extracted the preceding description block directly from the EulerOS security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues."); # https://developer.huaweicloud.com/ict/en/site-euleros/euleros/security-advisories/EulerOS-SA-2019-1491 script_set_attribute(attribute:"see_also", value:"http://www.nessus.org/u?2d818220"); script_set_attribute(attribute:"solution", value: "Update the affected kernel packages."); script_set_cvss_base_vector("CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:C"); script_set_cvss_temporal_vector("CVSS2#E:H/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:H/RL:O/RC:C"); script_set_attribute(attribute:"exploitability_ease", value:"Exploits are available"); script_set_attribute(attribute:"exploit_available", value:"true"); script_set_attribute(attribute:"exploit_framework_core", value:"true"); script_set_attribute(attribute:"exploited_by_malware", value:"true"); script_set_attribute(attribute:"patch_publication_date", value:"2019/05/09"); script_set_attribute(attribute:"plugin_publication_date", value:"2019/05/13"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:huawei:euleros:kernel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:huawei:euleros:kernel-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:huawei:euleros:kernel-headers"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:huawei:euleros:kernel-tools"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:huawei:euleros:kernel-tools-libs"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:huawei:euleros:kernel-tools-libs-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:huawei:euleros:perf"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:huawei:euleros:python-perf"); script_set_attribute(attribute:"cpe", value:"cpe:/o:huawei:euleros:uvp:3.0.1.0"); script_set_attribute(attribute:"generated_plugin", value:"current"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_family(english:"Huawei Local Security Checks"); script_copyright(english:"This script is Copyright (C) 2019-2020 and is owned by Tenable, Inc. or an Affiliate thereof."); script_dependencies("ssh_get_info.nasl"); script_require_keys("Host/local_checks_enabled", "Host/cpu", "Host/EulerOS/release", "Host/EulerOS/rpm-list", "Host/EulerOS/uvp_version"); exit(0); } include("audit.inc"); include("global_settings.inc"); include("rpm.inc"); if (!get_kb_item("Host/local_checks_enabled")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); release = get_kb_item("Host/EulerOS/release"); if (isnull(release) || release !~ "^EulerOS") audit(AUDIT_OS_NOT, "EulerOS"); uvp = get_kb_item("Host/EulerOS/uvp_version"); if (uvp != "3.0.1.0") audit(AUDIT_OS_NOT, "EulerOS Virtualization 3.0.1.0"); if (!get_kb_item("Host/EulerOS/rpm-list")) audit(AUDIT_PACKAGE_LIST_MISSING); cpu = get_kb_item("Host/cpu"); if (isnull(cpu)) audit(AUDIT_UNKNOWN_ARCH); if ("x86_64" >!< cpu && cpu !~ "^i[3-6]86$" && "aarch64" >!< cpu) audit(AUDIT_LOCAL_CHECKS_NOT_IMPLEMENTED, "EulerOS", cpu); if ("x86_64" >!< cpu && cpu !~ "^i[3-6]86$") audit(AUDIT_ARCH_NOT, "i686 / x86_64", cpu); flag = 0; pkgs = ["kernel-3.10.0-862.14.1.6_42", "kernel-devel-3.10.0-862.14.1.6_42", "kernel-headers-3.10.0-862.14.1.6_42", "kernel-tools-3.10.0-862.14.1.6_42", "kernel-tools-libs-3.10.0-862.14.1.6_42", "kernel-tools-libs-devel-3.10.0-862.14.1.6_42", "perf-3.10.0-862.14.1.6_42", "python-perf-3.10.0-862.14.1.6_42"]; foreach (pkg in pkgs) if (rpm_check(release:"EulerOS-2.0", reference:pkg)) flag++; if (flag) { security_report_v4( port : 0, severity : SECURITY_HOLE, extra : rpm_report_get() ); exit(0); } else { tested = pkg_tests_get(); if (tested) audit(AUDIT_PACKAGE_NOT_AFFECTED, tested); else audit(AUDIT_PACKAGE_NOT_INSTALLED, "kernel"); }NASL family Oracle Linux Local Security Checks NASL id ORACLELINUX_ELSA-2017-3567.NASL description Description of changes: [2.6.39-400.295.2.el6uek] - nfsd: stricter decoding of write-like NFSv2/v3 ops (J. Bruce Fields) [Orabug: 25986995] {CVE-2017-7895} [2.6.39-400.295.1.el6uek] - ocfs2/o2net: o2net_listen_data_ready should do nothing if socket state is not TCP_LISTEN (Tariq Saeed) [Orabug: 25510857] - IB/CORE: sync the resouce access in fmr_pool (Wengang Wang) [Orabug: 23750748] - ipv6: Skip XFRM lookup if dst_entry in socket cache is valid (Jakub Sitnicki) [Orabug: 25534688] - uek-rpm: enable CONFIG_KSPLICE. (Jamie Iles) [Orabug: 25549845] - ksplice: add sysctls for determining Ksplice features. (Jamie Iles) [Orabug: 25549845] - signal: protect SIGNAL_UNKILLABLE from unintentional clearing. (Jamie Iles) [Orabug: 25549845] - KVM: x86: fix emulation of last seen 2020-06-01 modified 2020-06-02 plugin id 100235 published 2017-05-17 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/100235 title Oracle Linux 6 : Unbreakable Enterprise kernel (ELSA-2017-3567) code # # (C) Tenable Network Security, Inc. # # The descriptive text and package checks in this plugin were # extracted from Oracle Linux Security Advisory ELSA-2017-3567. # include("compat.inc"); if (description) { script_id(100235); script_version("3.14"); script_cvs_date("Date: 2019/09/27 13:00:38"); script_cve_id("CVE-2013-7446", "CVE-2015-1420", "CVE-2015-4700", "CVE-2015-5257", "CVE-2015-5707", "CVE-2015-6252", "CVE-2015-6937", "CVE-2015-9731", "CVE-2016-10088", "CVE-2016-10142", "CVE-2016-10229", "CVE-2016-2782", "CVE-2016-3140", "CVE-2016-3672", "CVE-2016-4482", "CVE-2016-4485", "CVE-2016-4580", "CVE-2016-7425", "CVE-2016-7910", "CVE-2016-8399", "CVE-2016-8633", "CVE-2016-8645", "CVE-2017-2583", "CVE-2017-2636", "CVE-2017-2647", "CVE-2017-5669", "CVE-2017-5986", "CVE-2017-6074", "CVE-2017-6214", "CVE-2017-6345", "CVE-2017-7184", "CVE-2017-7187", "CVE-2017-7895"); script_name(english:"Oracle Linux 6 : Unbreakable Enterprise kernel (ELSA-2017-3567)"); script_summary(english:"Checks rpm output for the updated packages"); script_set_attribute( attribute:"synopsis", value:"The remote Oracle Linux host is missing one or more security updates." ); script_set_attribute( attribute:"description", value: "Description of changes: [2.6.39-400.295.2.el6uek] - nfsd: stricter decoding of write-like NFSv2/v3 ops (J. Bruce Fields) [Orabug: 25986995] {CVE-2017-7895} [2.6.39-400.295.1.el6uek] - ocfs2/o2net: o2net_listen_data_ready should do nothing if socket state is not TCP_LISTEN (Tariq Saeed) [Orabug: 25510857] - IB/CORE: sync the resouce access in fmr_pool (Wengang Wang) [Orabug: 23750748] - ipv6: Skip XFRM lookup if dst_entry in socket cache is valid (Jakub Sitnicki) [Orabug: 25534688] - uek-rpm: enable CONFIG_KSPLICE. (Jamie Iles) [Orabug: 25549845] - ksplice: add sysctls for determining Ksplice features. (Jamie Iles) [Orabug: 25549845] - signal: protect SIGNAL_UNKILLABLE from unintentional clearing. (Jamie Iles) [Orabug: 25549845] - KVM: x86: fix emulation of 'MOV SS, null selector' (Paolo Bonzini) [Orabug: 25719676] {CVE-2017-2583} {CVE-2017-2583} - sctp: avoid BUG_ON on sctp_wait_for_sndbuf (Marcelo Ricardo Leitner) [Orabug: 25719811] {CVE-2017-5986} - tcp: avoid infinite loop in tcp_splice_read() (Eric Dumazet) [Orabug: 25720815] {CVE-2017-6214} - USB: visor: fix null-deref at probe (Johan Hovold) [Orabug: 25796604] {CVE-2016-2782} - ipc/shm: Fix shmat mmap nil-page protection (Davidlohr Bueso) [Orabug: 25797014] {CVE-2017-5669} - vhost: actually track log eventfd file (Marc-André Lureau) [Orabug: 25797056] {CVE-2015-6252} - xfrm_user: validate XFRM_MSG_NEWAE incoming ESN size harder (Andy Whitcroft) [Orabug: 25814664] {CVE-2017-7184} - xfrm_user: validate XFRM_MSG_NEWAE XFRMA_REPLAY_ESN_VAL replay_window (Andy Whitcroft) [Orabug: 25814664] {CVE-2017-7184} - KEYS: Remove key_type::match in favour of overriding default by match_preparse (David Howells) [Orabug: 25823965] {CVE-2017-2647} {CVE-2017-2647} - USB: whiteheat: fix potential null-deref at probe (Johan Hovold) [Orabug: 25825107] {CVE-2015-5257} - RDS: fix race condition when sending a message on unbound socket (Quentin Casasnovas) [Orabug: 25871048] {CVE-2015-6937} {CVE-2015-6937} - udf: Check path length when reading symlink (Jan Kara) [Orabug: 25871104] {CVE-2015-9731} - udf: Treat symlink component of type 2 as / (Jan Kara) [Orabug: 25871104] {CVE-2015-9731} - udp: properly support MSG_PEEK with truncated buffers (Eric Dumazet) [Orabug: 25874741] {CVE-2016-10229} - block: fix use-after-free in seq file (Vegard Nossum) [Orabug: 25877531] {CVE-2016-7910} - RHEL: complement upstream workaround for CVE-2016-10142. (Quentin Casasnovas) [Orabug: 25765786] {CVE-2016-10142} {CVE-2016-10142} - net: ping: check minimum size on ICMP header length (Kees Cook) [Orabug: 25766914] {CVE-2016-8399} - ipv6: stop sending PTB packets for MTU < 1280 (Hagen Paul Pfeifer) [Orabug: 25765786] {CVE-2016-10142} - sg_write()/bsg_write() is not fit to be called under KERNEL_DS (Al Viro) [Orabug: 25765448] {CVE-2016-10088} - scsi: sg: check length passed to SG_NEXT_CMD_LEN (peter chang) [Orabug: 25752011] {CVE-2017-7187} - tty: n_hdlc: get rid of racy n_hdlc.tbuf (Alexander Popov) [Orabug: 25696689] {CVE-2017-2636} - TTY: n_hdlc, fix lockdep false positive (Jiri Slaby) [Orabug: 25696689] {CVE-2017-2636} - drivers/tty/n_hdlc.c: replace kmalloc/memset by kzalloc (Fabian Frederick) [Orabug: 25696689] {CVE-2017-2636} - list: introduce list_first_entry_or_null (Jiri Pirko) [Orabug: 25696689] {CVE-2017-2636} - firewire: net: guard against rx buffer overflows (Stefan Richter) [Orabug: 25451538] {CVE-2016-8633} - x86/mm/32: Enable full randomization on i386 and X86_32 (Hector Marco-Gisbert) [Orabug: 25463929] {CVE-2016-3672} - x86 get_unmapped_area: Access mmap_legacy_base through mm_struct member (Radu Caragea) [Orabug: 25463929] {CVE-2016-3672} - sg_start_req(): make sure that there's not too many elements in iovec (Al Viro) [Orabug: 25490377] {CVE-2015-5707} - tcp: take care of truncations done by sk_filter() (Eric Dumazet) [Orabug: 25507232] {CVE-2016-8645} - rose: limit sk_filter trim to payload (Willem de Bruijn) [Orabug: 25507232] {CVE-2016-8645} - scsi: arcmsr: Buffer overflow in arcmsr_iop_message_xfer() (Dan Carpenter) [Orabug: 25507330] {CVE-2016-7425} - x86: bpf_jit: fix compilation of large bpf programs (Alexei Starovoitov) [Orabug: 25507375] {CVE-2015-4700} - net: fix a kernel infoleak in x25 module (Kangjie Lu) [Orabug: 25512417] {CVE-2016-4580} - USB: digi_acceleport: do sanity checking for the number of ports (Oliver Neukum) [Orabug: 25512472] {CVE-2016-3140} - net/llc: avoid BUG_ON() in skb_orphan() (Eric Dumazet) [Orabug: 25682437] {CVE-2017-6345} - dccp: fix freeing skb too early for IPV6_RECVPKTINFO (Andrey Konovalov) [Orabug: 25598277] {CVE-2017-6074} - vfs: read file_handle only once in handle_to_path (Sasha Levin) [Orabug: 25388709] {CVE-2015-1420} - crypto: algif_hash - Only export and import on sockets with data (Herbert Xu) [Orabug: 25417807] - USB: usbfs: fix potential infoleak in devio (Kangjie Lu) [Orabug: 25462763] {CVE-2016-4482} - net: fix infoleak in llc (Kangjie Lu) [Orabug: 25462811] {CVE-2016-4485} - af_unix: Guard against other == sk in unix_dgram_sendmsg (Rainer Weikusat) [Orabug: 25464000] {CVE-2013-7446} - unix: avoid use-after-free in ep_remove_wait_queue (Rainer Weikusat) [Orabug: 25464000] {CVE-2013-7446}" ); script_set_attribute( attribute:"see_also", value:"https://oss.oracle.com/pipermail/el-errata/2017-May/006913.html" ); script_set_attribute( attribute:"solution", value:"Update the affected unbreakable enterprise kernel packages." ); script_set_cvss_base_vector("CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:C"); script_set_cvss_temporal_vector("CVSS2#E:F/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:F/RL:O/RC:C"); script_set_attribute(attribute:"exploitability_ease", value:"Exploits are available"); script_set_attribute(attribute:"exploit_available", value:"true"); script_set_attribute(attribute:"exploit_framework_core", value:"true"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:oracle:linux:kernel-uek"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:oracle:linux:kernel-uek-debug"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:oracle:linux:kernel-uek-debug-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:oracle:linux:kernel-uek-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:oracle:linux:kernel-uek-doc"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:oracle:linux:kernel-uek-firmware"); script_set_attribute(attribute:"cpe", value:"cpe:/o:oracle:linux:6"); script_set_attribute(attribute:"vuln_publication_date", value:"2015/03/16"); script_set_attribute(attribute:"patch_publication_date", value:"2017/05/16"); script_set_attribute(attribute:"plugin_publication_date", value:"2017/05/17"); script_set_attribute(attribute:"generated_plugin", value:"current"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_copyright(english:"This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof."); script_family(english:"Oracle Linux Local Security Checks"); script_dependencies("ssh_get_info.nasl", "linux_alt_patch_detect.nasl"); script_require_keys("Host/local_checks_enabled", "Host/OracleLinux", "Host/RedHat/release", "Host/RedHat/rpm-list"); exit(0); } include("audit.inc"); include("global_settings.inc"); include("rpm.inc"); include("ksplice.inc"); if (!get_kb_item("Host/local_checks_enabled")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); if (!get_kb_item("Host/OracleLinux")) audit(AUDIT_OS_NOT, "Oracle Linux"); release = get_kb_item("Host/RedHat/release"); if (isnull(release) || !pregmatch(pattern: "Oracle (?:Linux Server|Enterprise Linux)", string:release)) audit(AUDIT_OS_NOT, "Oracle Linux"); os_ver = pregmatch(pattern: "Oracle (?:Linux Server|Enterprise Linux) .*release ([0-9]+(\.[0-9]+)?)", string:release); if (isnull(os_ver)) audit(AUDIT_UNKNOWN_APP_VER, "Oracle Linux"); os_ver = os_ver[1]; if (! preg(pattern:"^6([^0-9]|$)", string:os_ver)) audit(AUDIT_OS_NOT, "Oracle Linux 6", "Oracle Linux " + os_ver); if (!get_kb_item("Host/RedHat/rpm-list")) audit(AUDIT_PACKAGE_LIST_MISSING); cpu = get_kb_item("Host/cpu"); if (isnull(cpu)) audit(AUDIT_UNKNOWN_ARCH); if ("x86_64" >!< cpu && cpu !~ "^i[3-6]86$") audit(AUDIT_LOCAL_CHECKS_NOT_IMPLEMENTED, "Oracle Linux", cpu); if (get_one_kb_item("Host/ksplice/kernel-cves")) { rm_kb_item(name:"Host/uptrack-uname-r"); cve_list = make_list("CVE-2013-7446", "CVE-2015-1420", "CVE-2015-4700", "CVE-2015-5257", "CVE-2015-5707", "CVE-2015-6252", "CVE-2015-6937", "CVE-2015-9731", "CVE-2016-10088", "CVE-2016-10142", "CVE-2016-10229", "CVE-2016-2782", "CVE-2016-3140", "CVE-2016-3672", "CVE-2016-4482", "CVE-2016-4485", "CVE-2016-4580", "CVE-2016-7425", "CVE-2016-7910", "CVE-2016-8399", "CVE-2016-8633", "CVE-2016-8645", "CVE-2017-2583", "CVE-2017-2636", "CVE-2017-2647", "CVE-2017-5669", "CVE-2017-5986", "CVE-2017-6074", "CVE-2017-6214", "CVE-2017-6345", "CVE-2017-7184", "CVE-2017-7187", "CVE-2017-7895"); if (ksplice_cves_check(cve_list)) { audit(AUDIT_PATCH_INSTALLED, "KSplice hotfix for ELSA-2017-3567"); } else { __rpm_report = ksplice_reporting_text(); } } kernel_major_minor = get_kb_item("Host/uname/major_minor"); if (empty_or_null(kernel_major_minor)) exit(1, "Unable to determine kernel major-minor level."); expected_kernel_major_minor = "2.6"; if (kernel_major_minor != expected_kernel_major_minor) audit(AUDIT_OS_NOT, "running kernel level " + expected_kernel_major_minor + ", it is running kernel level " + kernel_major_minor); flag = 0; if (rpm_exists(release:"EL6", rpm:"kernel-uek-2.6.39") && rpm_check(release:"EL6", reference:"kernel-uek-2.6.39-400.295.2.el6uek")) flag++; if (rpm_exists(release:"EL6", rpm:"kernel-uek-debug-2.6.39") && rpm_check(release:"EL6", reference:"kernel-uek-debug-2.6.39-400.295.2.el6uek")) flag++; if (rpm_exists(release:"EL6", rpm:"kernel-uek-debug-devel-2.6.39") && rpm_check(release:"EL6", reference:"kernel-uek-debug-devel-2.6.39-400.295.2.el6uek")) flag++; if (rpm_exists(release:"EL6", rpm:"kernel-uek-devel-2.6.39") && rpm_check(release:"EL6", reference:"kernel-uek-devel-2.6.39-400.295.2.el6uek")) flag++; if (rpm_exists(release:"EL6", rpm:"kernel-uek-doc-2.6.39") && rpm_check(release:"EL6", reference:"kernel-uek-doc-2.6.39-400.295.2.el6uek")) flag++; if (rpm_exists(release:"EL6", rpm:"kernel-uek-firmware-2.6.39") && rpm_check(release:"EL6", reference:"kernel-uek-firmware-2.6.39-400.295.2.el6uek")) flag++; if (flag) { if (report_verbosity > 0) security_hole(port:0, extra:rpm_report_get()); else security_hole(0); exit(0); } else { tested = pkg_tests_get(); if (tested) audit(AUDIT_PACKAGE_NOT_AFFECTED, tested); else audit(AUDIT_PACKAGE_NOT_INSTALLED, "affected kernel"); }NASL family Amazon Linux Local Security Checks NASL id ALA_ALAS-2017-832.NASL description Unsafe second checksum calculation in udp.c : The Linux kernel allows remote attackers to execute arbitrary code via UDP traffic that triggers an unsafe second checksum calculation during execution of a recv system call with the MSG_PEEK flag. This may create a kernel panic or memory corruption leading to privilege escalation. (CVE-2016-10229) last seen 2020-06-01 modified 2020-06-02 plugin id 100552 published 2017-06-01 reporter This script is Copyright (C) 2017-2018 Tenable Network Security, Inc. source https://www.tenable.com/plugins/nessus/100552 title Amazon Linux AMI : kernel (ALAS-2017-832) code # # (C) Tenable Network Security, Inc. # # The descriptive text and package checks in this plugin were # extracted from Amazon Linux AMI Security Advisory ALAS-2017-832. # include("compat.inc"); if (description) { script_id(100552); script_version("3.3"); script_cvs_date("Date: 2018/04/18 15:09:36"); script_cve_id("CVE-2016-10229"); script_xref(name:"ALAS", value:"2017-832"); script_name(english:"Amazon Linux AMI : kernel (ALAS-2017-832)"); script_summary(english:"Checks rpm output for the updated packages"); script_set_attribute( attribute:"synopsis", value:"The remote Amazon Linux AMI host is missing a security update." ); script_set_attribute( attribute:"description", value: "Unsafe second checksum calculation in udp.c : The Linux kernel allows remote attackers to execute arbitrary code via UDP traffic that triggers an unsafe second checksum calculation during execution of a recv system call with the MSG_PEEK flag. This may create a kernel panic or memory corruption leading to privilege escalation. (CVE-2016-10229)" ); script_set_attribute( attribute:"see_also", value:"https://alas.aws.amazon.com/ALAS-2017-832.html" ); script_set_attribute( attribute:"solution", value:"Run 'yum update kernel' to update your system." ); script_set_cvss_base_vector("CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:kernel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:kernel-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:kernel-debuginfo-common-i686"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:kernel-debuginfo-common-x86_64"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:kernel-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:kernel-doc"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:kernel-headers"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:kernel-tools"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:kernel-tools-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:kernel-tools-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:perf"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:amazon:linux:perf-debuginfo"); script_set_attribute(attribute:"cpe", value:"cpe:/o:amazon:linux"); script_set_attribute(attribute:"patch_publication_date", value:"2017/05/23"); script_set_attribute(attribute:"plugin_publication_date", value:"2017/06/01"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_copyright(english:"This script is Copyright (C) 2017-2018 Tenable Network Security, Inc."); script_family(english:"Amazon Linux Local Security Checks"); script_dependencies("ssh_get_info.nasl"); script_require_keys("Host/local_checks_enabled", "Host/AmazonLinux/release", "Host/AmazonLinux/rpm-list"); exit(0); } include("audit.inc"); include("global_settings.inc"); include("rpm.inc"); if (!get_kb_item("Host/local_checks_enabled")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); release = get_kb_item("Host/AmazonLinux/release"); if (isnull(release) || !strlen(release)) audit(AUDIT_OS_NOT, "Amazon Linux"); os_ver = pregmatch(pattern: "^AL(A|\d)", string:release); if (isnull(os_ver)) audit(AUDIT_UNKNOWN_APP_VER, "Amazon Linux"); os_ver = os_ver[1]; if (os_ver != "A") { if (os_ver == 'A') os_ver = 'AMI'; audit(AUDIT_OS_NOT, "Amazon Linux AMI", "Amazon Linux " + os_ver); } if (!get_kb_item("Host/AmazonLinux/rpm-list")) audit(AUDIT_PACKAGE_LIST_MISSING); flag = 0; if (rpm_check(release:"ALA", reference:"kernel-4.9.17-8.31.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"kernel-debuginfo-4.9.17-8.31.amzn1")) flag++; if (rpm_check(release:"ALA", cpu:"i686", reference:"kernel-debuginfo-common-i686-4.9.17-8.31.amzn1")) flag++; if (rpm_check(release:"ALA", cpu:"x86_64", reference:"kernel-debuginfo-common-x86_64-4.9.17-8.31.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"kernel-devel-4.9.17-8.31.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"kernel-doc-4.9.17-8.31.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"kernel-headers-4.9.17-8.31.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"kernel-tools-4.9.17-8.31.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"kernel-tools-debuginfo-4.9.17-8.31.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"kernel-tools-devel-4.9.17-8.31.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"perf-4.9.17-8.31.amzn1")) flag++; if (rpm_check(release:"ALA", reference:"perf-debuginfo-4.9.17-8.31.amzn1")) flag++; if (flag) { if (report_verbosity > 0) security_hole(port:0, extra:rpm_report_get()); else security_hole(0); exit(0); } else { tested = pkg_tests_get(); if (tested) audit(AUDIT_PACKAGE_NOT_AFFECTED, tested); else audit(AUDIT_PACKAGE_NOT_INSTALLED, "kernel / kernel-debuginfo / kernel-debuginfo-common-i686 / etc"); }NASL family OracleVM Local Security Checks NASL id ORACLEVM_OVMSA-2017-0061.NASL description The remote OracleVM system is missing necessary patches to address critical security updates : - udp: properly support MSG_PEEK with truncated buffers (Eric Dumazet) [Orabug: 25874741] (CVE-2016-10229) - block: fix use-after-free in seq file (Vegard Nossum) [Orabug: 25877531] (CVE-2016-7910) last seen 2020-06-01 modified 2020-06-02 plugin id 99391 published 2017-04-14 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/99391 title OracleVM 3.2 : Unbreakable / etc (OVMSA-2017-0061) NASL family Palo Alto Local Security Checks NASL id PALO_ALTO_PAN-OS_8_0_3.NASL description The version of Palo Alto Networks PAN-OS running on the remote host is 6.1.x prior to 6.1.18, 7.0.x prior to 7.0.17, 7.1.x prior to 7.1.12, or 8.0.x prior to 8.0.3. It is, therefore, affected by multiple vulnerabilities : - A denial of service vulnerability exists in the OpenSSL component that is triggered when handling a large number of consecutive last seen 2020-06-01 modified 2020-06-02 plugin id 101164 published 2017-06-30 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/101164 title Palo Alto Networks PAN-OS 6.1.x < 6.1.18 / 7.0.x < 7.0.17 / 7.1.x < 7.1.12 / 8.0.x < 8.0.3 Multiple Vulnerabilities NASL family OracleVM Local Security Checks NASL id ORACLEVM_OVMSA-2017-0145.NASL description The remote OracleVM system is missing necessary patches to address critical security updates : please see Oracle VM Security Advisory OVMSA-2017-0145 for details. last seen 2020-06-01 modified 2020-06-02 plugin id 102774 published 2017-08-25 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/102774 title OracleVM 3.4 : Unbreakable / etc (OVMSA-2017-0145) (Stack Clash) NASL family OracleVM Local Security Checks NASL id ORACLEVM_OVMSA-2017-0104.NASL description The remote OracleVM system is missing necessary patches to address critical security updates : - ipv6: catch a null skb before using it in a DTRACE (Shannon Nelson) - sparc64: Do not retain old VM_SPARC_ADI flag when protection changes on page (Khalid Aziz) [Orabug: 26038830] - nfsd: stricter decoding of write-like NFSv2/v3 ops (J. Bruce Fields) [Orabug: 25986971] (CVE-2017-7895) - sparc64: Detect DAX ra+pgsz when hvapi minor doesn last seen 2020-06-01 modified 2020-06-02 plugin id 100236 published 2017-05-17 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/100236 title OracleVM 3.4 : Unbreakable / etc (OVMSA-2017-0104) NASL family OracleVM Local Security Checks NASL id ORACLEVM_OVMSA-2018-0015.NASL description The remote OracleVM system is missing necessary patches to address critical security updates : please see Oracle VM Security Advisory OVMSA-2018-0015 for details. last seen 2020-06-01 modified 2020-06-02 plugin id 106469 published 2018-01-30 reporter This script is Copyright (C) 2018-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/106469 title OracleVM 3.4 : Unbreakable / etc (OVMSA-2018-0015) (BlueBorne) (Meltdown) (Spectre) (Stack Clash) NASL family OracleVM Local Security Checks NASL id ORACLEVM_OVMSA-2017-0105.NASL description The remote OracleVM system is missing necessary patches to address critical security updates : - nfsd: stricter decoding of write-like NFSv2/v3 ops (J. Bruce Fields) [Orabug: 25986990] (CVE-2017-7895) - fnic: Update fnic driver version to 1.6.0.24 (John Sobecki) [Orabug: 24448585] - xen-netfront: Rework the fix for Rx stall during OOM and network stress (Dongli Zhang) [Orabug: 25450703] - xen-netfront: Fix Rx stall during network stress and OOM (Dongli Zhang) [Orabug: 25450703] - ipv6: Skip XFRM lookup if dst_entry in socket cache is valid (Jakub Sitnicki) - uek-rpm: enable CONFIG_KSPLICE. (Jamie Iles) [Orabug: 25549809] - ksplice: add sysctls for determining Ksplice features. (Jamie Iles) - signal: protect SIGNAL_UNKILLABLE from unintentional clearing. (Jamie Iles) [Orabug: 25549809] - VSOCK: Fix lockdep issue. (Dongli Zhang) [Orabug: 25559937] - VSOCK: sock_put wasn last seen 2020-06-01 modified 2020-06-02 plugin id 100237 published 2017-05-17 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/100237 title OracleVM 3.3 : Unbreakable / etc (OVMSA-2017-0105) NASL family Huawei Local Security Checks NASL id EULEROS_SA-2019-1503.NASL description According to the versions of the kernel packages installed, the EulerOS Virtualization for ARM 64 installation on the remote host is affected by the following vulnerabilities : - The uas driver in the Linux kernel before 4.13.6 allows local users to cause a denial of service (out-of-bounds read and system crash), or possibly have unspecified other impacts via a crafted USB device, related to drivers/usb/storage/uas-detect.h and drivers/usb/storage/uas.c.(CVE-2017-16530i1/4%0 - The implementation of big key management in security/keys/big_key.c in the Linux kernel before 4.8.7 mishandles unsuccessful crypto registration in conjunction with successful key-type registration, which allows local users to cause a denial of service (NULL pointer dereference and panic) or possibly have unspecified other impact via a crafted application that uses the big_key data type.(CVE-2016-9313i1/4%0 - The Linux kernel allows remote attackers to execute arbitrary code via UDP traffic that triggers an unsafe second checksum calculation during execution of a recv system call with the MSG_PEEK flag. This may create a kernel panic or memory corruption leading to privilege escalation.(CVE-2016-10229i1/4%0 - Buffer overflow in the exitcode_proc_write function in arch/um/kernel/exitcode.c in the Linux kernel before 3.12 allows local users to cause a denial of service or possibly have unspecified other impact by leveraging root privileges for a write operation.(CVE-2013-4512i1/4%0 - It was found that unsharing a mount namespace could allow a user to see data beneath their restricted namespace.(CVE-2014-9717i1/4%0 - A divide-by-zero flaw was discovered in the Linux kernel built with KVM virtualization support(CONFIG_KVM). The flaw occurs in the KVM module last seen 2020-03-19 modified 2019-05-13 plugin id 124826 published 2019-05-13 reporter This script is Copyright (C) 2019-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/124826 title EulerOS Virtualization for ARM 64 3.0.1.0 : kernel (EulerOS-SA-2019-1503) NASL family OracleVM Local Security Checks NASL id ORACLEVM_OVMSA-2017-0106.NASL description The remote OracleVM system is missing necessary patches to address critical security updates : - nfsd: stricter decoding of write-like NFSv2/v3 ops (J. Bruce Fields) [Orabug: 25986995] (CVE-2017-7895) - ocfs2/o2net: o2net_listen_data_ready should do nothing if socket state is not TCP_LISTEN (Tariq Saeed) [Orabug: 25510857] - IB/CORE: sync the resouce access in fmr_pool (Wengang Wang) [Orabug: 23750748] - ipv6: Skip XFRM lookup if dst_entry in socket cache is valid (Jakub Sitnicki) [Orabug: 25534688] - uek-rpm: enable CONFIG_KSPLICE. (Jamie Iles) [Orabug: 25549845] - ksplice: add sysctls for determining Ksplice features. (Jamie Iles) - signal: protect SIGNAL_UNKILLABLE from unintentional clearing. (Jamie Iles) [Orabug: 25549845] - KVM: x86: fix emulation of last seen 2020-06-01 modified 2020-06-02 plugin id 100238 published 2017-05-17 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/100238 title OracleVM 3.2 : Unbreakable / etc (OVMSA-2017-0106) NASL family Oracle Linux Local Security Checks NASL id ORACLELINUX_ELSA-2017-3538.NASL description Description of changes: [2.6.39-400.294.7.el6uek] - udp: properly support MSG_PEEK with truncated buffers (Eric Dumazet) [Orabug: 25874741] {CVE-2016-10229} - block: fix use-after-free in seq file (Vegard Nossum) [Orabug: 25877531] {CVE-2016-7910} last seen 2020-06-01 modified 2020-06-02 plugin id 99388 published 2017-04-14 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/99388 title Oracle Linux 6 : Unbreakable Enterprise kernel (ELSA-2017-3538) NASL family Oracle Linux Local Security Checks NASL id ORACLELINUX_ELSA-2017-3609.NASL description The remote Oracle Linux host is missing a security update for the Unbreakable Enterprise kernel package(s). last seen 2020-06-01 modified 2020-06-02 plugin id 102773 published 2017-08-25 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/102773 title Oracle Linux 6 / 7 : Unbreakable Enterprise kernel (ELSA-2017-3609) (Stack Clash) NASL family SuSE Local Security Checks NASL id SUSE_SU-2017-2920-1.NASL description The SUSE Linux Enterprise 12 GA LTS kernel was updated to receive various security and bugfixes. The following security bugs were fixed : - CVE-2017-15649: net/packet/af_packet.c in the Linux kernel allowed local users to gain privileges via crafted system calls that trigger mishandling of packet_fanout data structures, because of a race condition (involving fanout_add and packet_do_bind) that leads to a use-after-free, a different vulnerability than CVE-2017-6346 (bnc#1064388). - CVE-2015-9004: kernel/events/core.c in the Linux kernel mishandled counter grouping, which allowed local users to gain privileges via a crafted application, related to the perf_pmu_register and perf_event_open functions (bnc#1037306). - CVE-2016-10229: udp.c in the Linux kernel allowed remote attackers to execute arbitrary code via UDP traffic that triggers an unsafe second checksum calculation during execution of a recv system call with the MSG_PEEK flag (bnc#1032268). - CVE-2016-9604: The handling of keyrings starting with last seen 2020-06-01 modified 2020-06-02 plugin id 104374 published 2017-11-03 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/104374 title SUSE SLES12 Security Update : kernel (SUSE-SU-2017:2920-1) (KRACK) (Stack Clash)
Seebug
| bulletinFamily | exploit |
| description | The Linux kernel allows remote attackers to execute arbitrary code via UDP traffic that triggers an unsafe second checksum calculation during execution of a recv system call with the MSG_PEEK flag. This may create a kernel panic or memory corruption leading to privilege escalation. https://git.kernel.org/pub/scm/linux/kernel/git/torvalds/linux.git/commit/?id=197c949e7798fbf28cfadc69d9ca0c2abbf93191 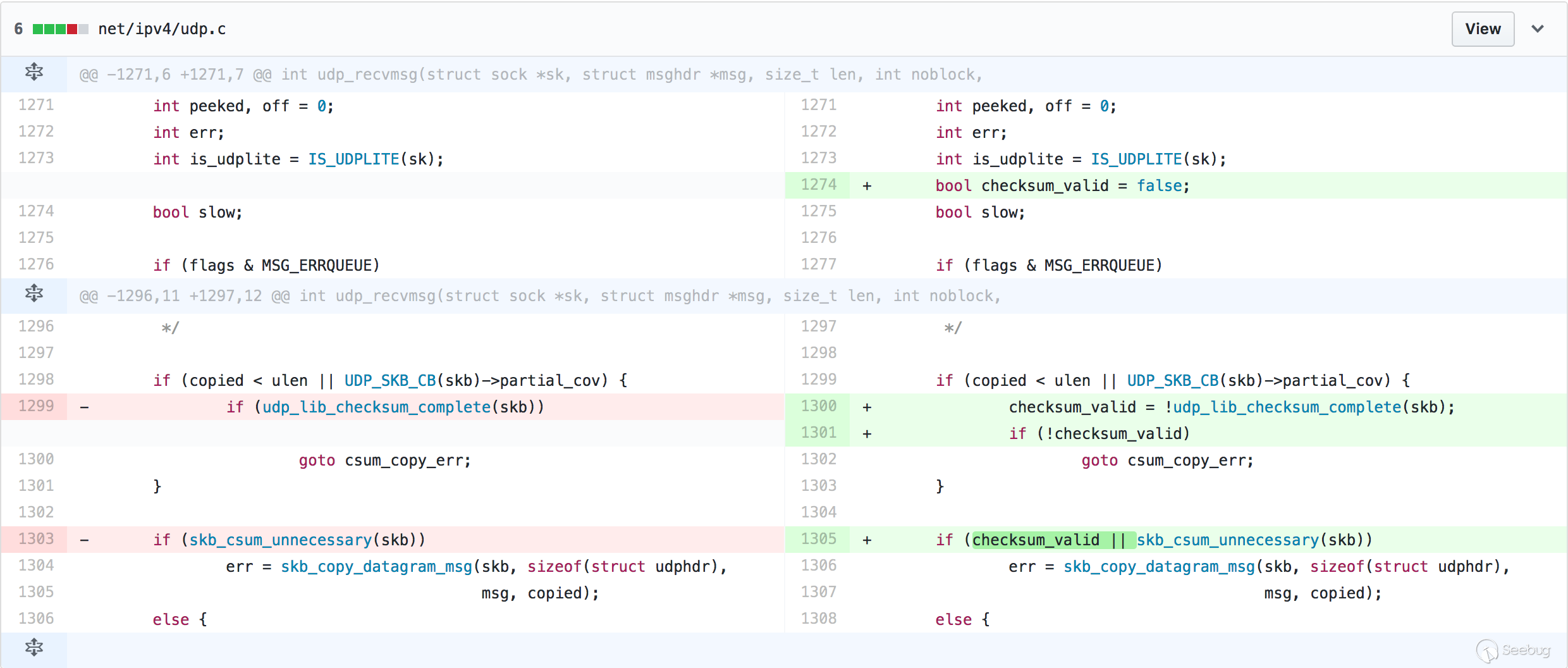 |
| id | SSV:92945 |
| last seen | 2017-11-19 |
| modified | 2017-04-14 |
| published | 2017-04-14 |
| reporter | Root |
| title | Linux kernel 'udp. c' remote code execution vulnerability(CVE-2016-10229) |
References
- https://github.com/torvalds/linux/commit/197c949e7798fbf28cfadc69d9ca0c2abbf93191
- http://source.android.com/security/bulletin/2017-04-01.html
- http://git.kernel.org/cgit/linux/kernel/git/torvalds/linux.git/commit/?id=197c949e7798fbf28cfadc69d9ca0c2abbf93191
- http://www.securityfocus.com/bid/97397
- http://www.securitytracker.com/id/1038201
- https://security.paloaltonetworks.com/CVE-2016-10229