Vulnerabilities > CVE-2015-7756 - Cryptographic Issues vulnerability in Juniper Screenos
Attack vector
NETWORK Attack complexity
LOW Privileges required
NONE Confidentiality impact
PARTIAL Integrity impact
NONE Availability impact
NONE Summary
The encryption implementation in Juniper ScreenOS 6.2.0r15 through 6.2.0r18, 6.3.0r12 before 6.3.0r12b, 6.3.0r13 before 6.3.0r13b, 6.3.0r14 before 6.3.0r14b, 6.3.0r15 before 6.3.0r15b, 6.3.0r16 before 6.3.0r16b, 6.3.0r17 before 6.3.0r17b, 6.3.0r18 before 6.3.0r18b, 6.3.0r19 before 6.3.0r19b, and 6.3.0r20 before 6.3.0r21 makes it easier for remote attackers to discover the plaintext content of VPN sessions by sniffing the network for ciphertext data and conducting an unspecified decryption attack.
Vulnerable Configurations
| Part | Description | Count |
|---|---|---|
| OS | 12 |
Common Weakness Enumeration (CWE)
Common Attack Pattern Enumeration and Classification (CAPEC)
- Signature Spoofing by Key Recreation An attacker obtains an authoritative or reputable signer's private signature key by exploiting a cryptographic weakness in the signature algorithm or pseudorandom number generation and then uses this key to forge signatures from the original signer to mislead a victim into performing actions that benefit the attacker.
Nessus
| NASL family | Firewalls |
| NASL id | SCREENOS_JSA10713.NASL |
| description | The remote host is running a version of Juniper ScreenOS that is 6.2.x prior to 6.2.0r19 or 6.3.x prior to 6.3.0r21. It is, therefore, affected by multiple vulnerabilities : - A backdoor exists that allows a remote attacker administrative access to the device over SSH or telnet. (CVE-2015-7755) - An unspecified flaw exists that allows a man-in-the-middle attacker to decrypt VPN traffic. (CVE-2015-7756) Note that Nessus has not tested for these issues but has instead relied only on the application |
| last seen | 2020-06-01 |
| modified | 2020-06-02 |
| plugin id | 87507 |
| published | 2015-12-18 |
| reporter | This script is Copyright (C) 2015-2018 and is owned by Tenable, Inc. or an Affiliate thereof. |
| source | https://www.tenable.com/plugins/nessus/87507 |
| title | Juniper ScreenOS 6.2.0r15 < 6.2.0r19 / 6.3.0r12 < 6.3.0r21 Multiple Vulnerabilities (JSA10713) |
| code | |
Seebug
| bulletinFamily | exploit |
| description | ``` Author: xiaohu & mt (知道创宇404安全实验室) Date: 2015-12-23 ``` ## 漏洞信息: Juniper 网络公司(瞻博网络)作为全球领先的联网和安全性解决方案供应商,Juniper 网络公司对依赖网络获得战略性收益的客户一直给予密切关注。公司的客户来自全球各行各业,包括主要的网络运营商、企业、政府机构以及研究和教育机构等。Juniper 网络公司推出的一系列联网解决方案,提供所需的安全性和性能来支持全球最大型、最复杂、要求最严格的关键网络。 Juniper 网络公司在上周发表声明,称 NetScreen 与 Juniper SSG 防火墙产品使用的操作系统 Juniper ScreenOS 中发现高危漏洞 CVE-2015-7756。涉及设备 VPN 加密伪随机密钥可被破解的漏洞。 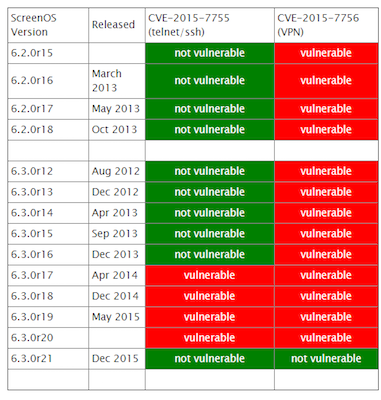 ## 漏洞分析: 首先,需要了解涉及 Juniper 的 VPN加密的几个关键函数,其次相互关系和作用。其调用关系如下表所示: 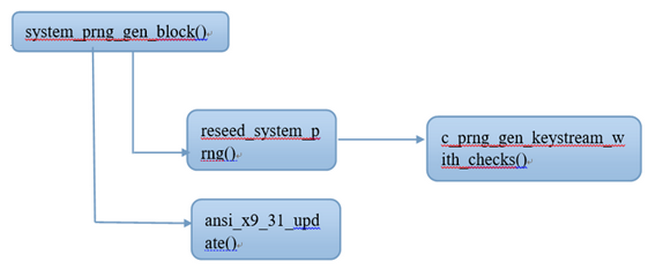 上表中 reseed_system_prng 函数的作用是生成SEED和3DES密钥, 函数 ansi_x9_31_update 作用是迭代混淆。ansi_x9_31_update函数的流程图如下:  如图所示,T 为 8字节随机数,但四个字节固定为 0,所以只有四个字节是随机数。T的生成方式为此时机器的 Timer(计时器读值)。system_prng_gen_block 和 reseed_system_prng 函数绝大部分代码已被逆向出来,其伪代码见附录。至此,基于对上述关键函数的分析,国外大牛 RPW 声称:“暂时没有发现一种切实可行的漏洞利用方法解密Juniper 的 VPN加密,但是会持续关注这个这个漏洞,而且他怀疑他错过一些东西!有时间的话他会用硬件 JTAG 调试器分析”。 在 system_prng_gen_block 伪代码中,有关键的一行并没有得到深入分析。如下:通过这句代码,我们可以根据固件推出在一个随机种子用来初始化的 prngseed。逆向ssg5ssg20.6.3.0r19.0 固件得到伪代码,从中可以找到如下代码片段: 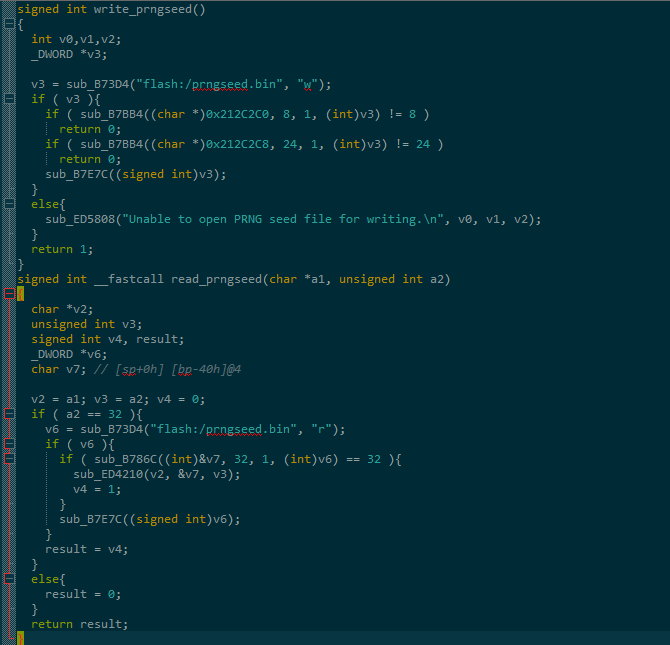 通过上述代码段,可以得到一种可能的 VPN 解密方式:在获取系统控制权或者听过其他漏洞或方法读出 prngseed 的32个字节,暴力破解 T(后4字节伪机数),最后可以实现对 VPN 的解密。另外一种可能,同时如果厂家的 prngseed 的生成机制,被泄漏出来,则 VPN 直接可以被解密。以上为我们的初步分析,我们将进一步对 Juniper 漏洞深入分析。 ## 漏洞影响: 我们从 ZoomEye 平台对全球 ScreenOS 设备分析统计发现,开放了 Telnet 服务的总数高达 34000 台。 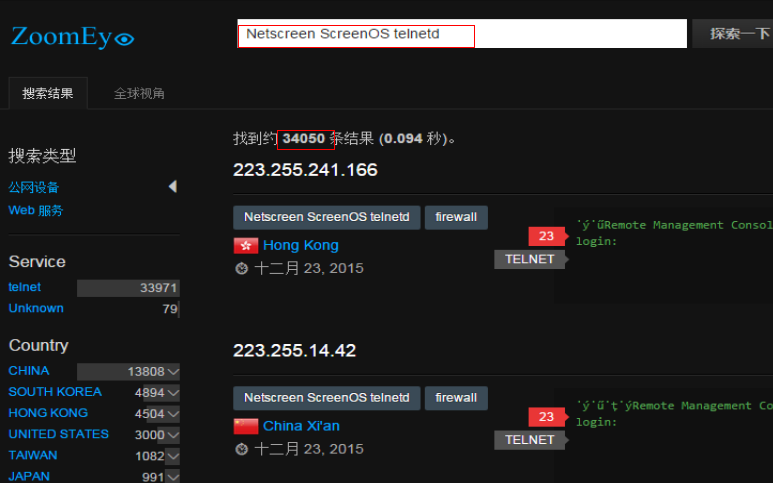 目前知道创宇 Sebug 照妖镜已提供对绕过 ScreenOS 身份认证漏洞在线检测,利用此功能可以针对 ScreenOS 设备进行测试,如果存在漏洞建议立即升级设备固件。Sebug 提供最新漏洞信息、漏洞搜索、漏洞修复、漏洞目录、安全文档、漏洞趋势分析等服务。 ## 解决方案: 目前 Juniper 网络公司已对 ScreenOS 受漏洞影响版本进行了修复。可进入官网下载设备型号相对应的固件版本进行升级。(链接:http://www.juniper.net/support/downloads/screenos.html) 另外需要说明的是,针对使用后门绕过认证,获取设备管理员权限,会被 ScreenOS 日志记录,如果一旦设备被完全控制,日志将变的不可靠,建议立即升级 ScreenOS 设备固件,如果因客观因素无法升级设备固件,应该限制对设备访问的 IP,为了进一步安全考虑,可以增加网络日志服务器,ScreenOS 所有日志发生时自动导入网络日志服务器,相对而言远程存储日志比本地存储日志被窜改的概率将会降低很多。 ## 参考资料 https://community.rapid7.com/community/infosec/blog/2015/12/20/cve-2015-7755-juniper-screenos-authentication-backdoor https://kb.juniper.net/InfoCenter/index?page=content&id=JSA10713&cat=SIRT_1&actp=LIST https://rpw.sh/blog/2015/12/21/the-backdoored-backdoor/ https://github.com/hdm/juniper-cve-2015-7755 http://www.juniper.net/support/downloads/screenos.html |
| id | SSV:90140 |
| last seen | 2017-11-19 |
| modified | 2015-12-21 |
| published | 2015-12-21 |
| reporter | Root |
| title | Juniper Networks(瞻博网络)未授权访问漏洞 |
References
- http://arstechnica.com/security/2015/12/unauthorized-code-in-juniper-firewalls-decrypts-encrypted-vpn-traffic/
- http://kb.juniper.net/InfoCenter/index?page=content&id=JSA10713
- http://www.forbes.com/sites/thomasbrewster/2015/12/18/juniper-says-it-didnt-work-with-government-to-add-unauthorized-code-to-network-gear/
- http://www.kb.cert.org/vuls/id/640184
- http://www.securitytracker.com/id/1034489
- http://www.wired.com/2015/12/juniper-networks-hidden-backdoors-show-the-risk-of-government-backdoors/
- https://adamcaudill.com/2015/12/17/much-ado-about-juniper/
- https://forums.juniper.net/t5/Security-Incident-Response/Important-Announcement-about-ScreenOS/ba-p/285554
- https://github.com/hdm/juniper-cve-2015-7755