Vulnerabilities > CVE-2014-4688 - Remote Security vulnerability in Pfsense
Attack vector
NETWORK Attack complexity
LOW Privileges required
SINGLE Confidentiality impact
PARTIAL Integrity impact
PARTIAL Availability impact
PARTIAL Summary
pfSense before 2.1.4 allows remote authenticated users to execute arbitrary commands via (1) the hostname value to diag_dns.php in a Create Alias action, (2) the smartmonemail value to diag_smart.php, or (3) the database value to status_rrd_graph_img.php. Per: http://cwe.mitre.org/data/definitions/77.html "CWE-77: Improper Neutralization of Special Elements used in a Command ('Command Injection')"
Vulnerable Configurations
| Part | Description | Count |
|---|---|---|
| Application | 8 |
Exploit-Db
| description | pfSense < 2.1.4 - 'status_rrd_graph_img.php' Command Injection. CVE-2014-4688. Webapps exploit for PHP platform |
| file | exploits/php/webapps/43560.py |
| id | EDB-ID:43560 |
| last seen | 2018-01-24 |
| modified | 2018-01-15 |
| platform | php |
| port | |
| published | 2018-01-15 |
| reporter | Exploit-DB |
| source | https://www.exploit-db.com/download/43560/ |
| title | pfSense < 2.1.4 - 'status_rrd_graph_img.php' Command Injection |
| type | webapps |
Nessus
| NASL family | CGI abuses |
| NASL id | PFSENSE_SA-14_12.NASL |
| description | According to its self-reported version number, the remote pfSense install is prior to 2.1.4. It is, therefore, affected by multiple vulnerabilities. |
| last seen | 2020-06-01 |
| modified | 2020-06-02 |
| plugin id | 106490 |
| published | 2018-01-31 |
| reporter | This script is Copyright (C) 2018-2019 and is owned by Tenable, Inc. or an Affiliate thereof. |
| source | https://www.tenable.com/plugins/nessus/106490 |
| title | pfSense < 2.1.4 Multiple Vulnerabilities (SA-14_08 - SA-14_12) |
| code | |
Packetstorm
| data source | https://packetstormsecurity.com/files/download/145909/pfsenserrd-exec.txt |
| id | PACKETSTORM:145909 |
| last seen | 2018-01-16 |
| published | 2018-01-15 |
| reporter | absolomb |
| source | https://packetstormsecurity.com/files/145909/pfSense-2.1.3-status_rrd_graph_img.php-Command-Injection.html |
| title | pfSense 2.1.3 status_rrd_graph_img.php Command Injection |
Seebug
| bulletinFamily | exploit |
| description | ### 漏洞简介 该漏洞的编号为CVE-2014-4688,存在于PfSense的2.1.3以及更低版本中。该漏洞源于php程序中没有对用户的输入值进行严格的校验,导致用户恶意输入达到命令执行函数时会产生严重后果。其中,diag_dns.php, diag_smart.php, status_rrd_graph_img.php三个脚本文件受到该漏洞的影响。 ### 漏洞分析 在diag_dns.php中,用户提交的host值经过处理后将传到dig变量中执行。攻击者通过构造host值执行任意命令。 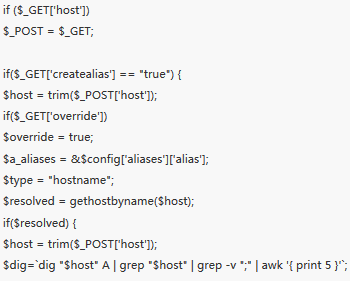 在diag_smart.php中,smartmonemail作为用户的post参数,将会传到shell_exec函数中,同理可以构造smartmonemail执行任意命令。 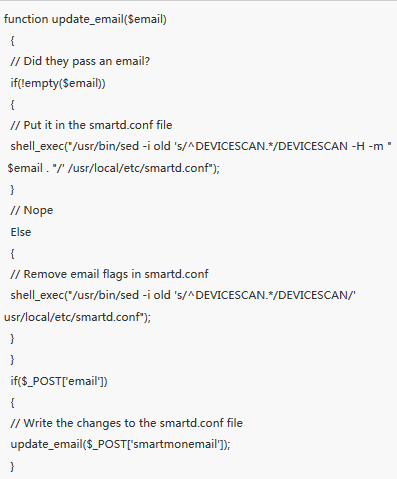 同理,在status_rrd_graph_img.php中,攻击者构造变量database使exec执行任意指令。 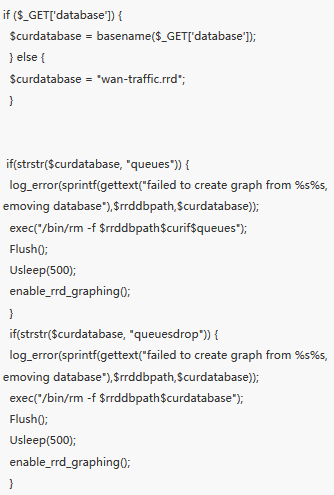 ### 漏洞影响 通过这个漏洞,攻击者可以执行任意指令,致使该款防火墙软件彻底失效。 |
| id | SSV:89663 |
| last seen | 2017-11-19 |
| modified | 2015-10-10 |
| published | 2015-10-10 |
| reporter | 尧之 |
| title | PfSense命令注入漏洞 |