Vulnerabilities > CVE-2010-1870 - Unspecified vulnerability in Apache Struts
Summary
The OGNL extensive expression evaluation capability in XWork in Struts 2.0.0 through 2.1.8.1, as used in Atlassian Fisheye, Crucible, and possibly other products, uses a permissive whitelist, which allows remote attackers to modify server-side context objects and bypass the "#" protection mechanism in ParameterInterceptors via the (1) #context, (2) #_memberAccess, (3) #root, (4) #this, (5) #_typeResolver, (6) #_classResolver, (7) #_traceEvaluations, (8) #_lastEvaluation, (9) #_keepLastEvaluation, and possibly other OGNL context variables, a different vulnerability than CVE-2008-6504.
Vulnerable Configurations
D2sec
name 2.2.0 RCE Windows url http://www.d2sec.com/exploits/apache-struts__2.2.0_rce_windows.html name 2.2.0 RCE Linux url http://www.d2sec.com/exploits/apache-struts__2.2.0_rce_linux.html
Exploit-Db
description Struts2/XWork < 2.2.0 Remote Command Execution Vulnerability. CVE-2010-1870. Remote exploits for multiple platform file exploits/multiple/remote/14360.txt id EDB-ID:14360 last seen 2016-02-01 modified 2010-07-14 platform multiple port published 2010-07-14 reporter Meder Kydyraliev source https://www.exploit-db.com/download/14360/ title Struts2/XWork < 2.2.0 - Remote Command Execution Vulnerability type remote description Apache Struts < 2.2.0 Remote Command Execution. CVE-2010-1870. Remote exploits for multiple platform id EDB-ID:17691 last seen 2016-02-02 modified 2011-08-19 published 2011-08-19 reporter metasploit source https://www.exploit-db.com/download/17691/ title Apache Struts < 2.2.0 - Remote Command Execution
Metasploit
| description | This module exploits a remote command execution vulnerability in Apache Struts versions < 2.2.0. This issue is caused by a failure to properly handle unicode characters in OGNL extensive expressions passed to the web server. By sending a specially crafted request to the Struts application it is possible to bypass the "#" restriction on ParameterInterceptors by using OGNL context variables. Bypassing this restriction allows for the execution of arbitrary Java code. |
| id | MSF:EXPLOIT/MULTI/HTTP/STRUTS_CODE_EXEC |
| last seen | 2020-05-26 |
| modified | 2019-08-02 |
| published | 2011-11-28 |
| references | https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2010-1870 |
| reporter | Rapid7 |
| source | https://github.com/rapid7/metasploit-framework/blob/master//modules/exploits/multi/http/struts_code_exec.rb |
| title | Apache Struts Remote Command Execution |
Nessus
NASL family CGI abuses NASL id STRUTS_XWORK_OGNL_CODE_EXECUTION_SAFE.NASL description The remote web application appears to use Struts 2, a web framework that uses XWork. Due to a vulnerability in XWork, it is possible to disable settings designed to prevent remote code execution. A remote attacker can exploit this by submitting an HTTP request containing specially crafted OGNL statements, resulting in the execution of arbitrary Java. Note that versions of Apache Archiva includes Struts and may be affected. last seen 2020-04-30 modified 2010-07-29 plugin id 47900 published 2010-07-29 reporter This script is Copyright (C) 2010-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/47900 title Apache Struts 2 / XWork Remote Code Execution (safe check) code # # (C) Tenable Network Security, Inc. # include("compat.inc"); if (description) { script_id(47900); script_version("1.30"); script_set_attribute(attribute:"plugin_modification_date", value:"2020/04/27"); script_cve_id("CVE-2010-1870"); script_bugtraq_id(41592); script_xref(name:"EDB-ID", value:"14360"); script_xref(name:"EDB-ID", value:"17691"); script_xref(name:"Secunia", value:"40558"); script_xref(name:"Secunia", value:"40575"); script_name(english:"Apache Struts 2 / XWork Remote Code Execution (safe check)"); script_summary(english:"Fingerprints the vulnerability by doing multiple sleeps."); script_set_attribute( attribute:"synopsis", value: "A remote web application uses a framework that is affected by a code execution vulnerability." ); script_set_attribute( attribute:"description", value: "The remote web application appears to use Struts 2, a web framework that uses XWork. Due to a vulnerability in XWork, it is possible to disable settings designed to prevent remote code execution. A remote attacker can exploit this by submitting an HTTP request containing specially crafted OGNL statements, resulting in the execution of arbitrary Java. Note that versions of Apache Archiva includes Struts and may be affected." ); script_set_attribute(attribute:"see_also", value:"http://blog.o0o.nu/2010/07/cve-2010-1870-struts2xwork-remote.html"); script_set_attribute(attribute:"see_also", value:"http://struts.apache.org/docs/s2-005.html"); script_set_attribute(attribute:"see_also", value:"http://archiva.apache.org/docs/1.3.6/release-notes.html"); script_set_attribute( attribute:"solution", value: "Upgrade to Struts 2.2.1 or later. Alternatively, upgrade to Archiva 1.3.6 or later if using that product." ); script_set_cvss_base_vector("CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:C"); script_set_cvss_temporal_vector("CVSS2#E:F/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:F/RL:O/RC:C"); script_set_attribute(attribute:"cvss_score_source", value:"CVE-2010-1870"); script_set_attribute(attribute:"cvss_score_rationale", value:"NVD scores this vulnerability with a score of 5.0 but the Tenable Research Team disagrees with their finding and set it to a 10.0 instead."); script_set_attribute(attribute:"exploitability_ease", value:"No exploit is required"); script_set_attribute(attribute:"exploit_available", value:"false"); script_set_attribute(attribute:"exploit_framework_core", value:"true"); script_set_attribute(attribute:"d2_elliot_name", value:"Apache-Struts < 2.2.0 RCE Linux"); script_set_attribute(attribute:"exploit_framework_d2_elliot", value:"true"); script_set_attribute(attribute:"metasploit_name", value:'Apache Struts Remote Command Execution'); script_set_attribute(attribute:"exploit_framework_metasploit", value:"true"); script_set_attribute(attribute:"exploit_framework_canvas", value:"true"); script_set_attribute(attribute:"canvas_package", value:'White_Phosphorus'); script_set_attribute(attribute:"vuln_publication_date", value:"2010/07/09"); script_set_attribute(attribute:"patch_publication_date", value:"2010/08/16"); script_set_attribute(attribute:"plugin_publication_date", value:"2010/07/29"); script_set_attribute(attribute:"plugin_type", value:"remote"); script_set_attribute(attribute:"cpe", value:"cpe:/a:apache:struts"); script_end_attributes(); script_category(ACT_ATTACK); script_family(english:"CGI abuses"); script_copyright(english:"This script is Copyright (C) 2010-2020 and is owned by Tenable, Inc. or an Affiliate thereof."); script_dependencies("http_version.nasl", "webmirror.nasl"); script_require_ports("Services/www", 80, 8080); exit(0); } include("audit.inc"); include("global_settings.inc"); include("misc_func.inc"); include("http.inc"); include("webapp_func.inc"); port = get_http_port(default:8080); cgis = get_kb_list('www/' + port + '/cgi'); urls = make_list(); # To identify actions that we can test the exploit on we will look # for files with the .action / .jsp / .do suffix from the KB. if (!isnull(cgis)) { foreach cgi (cgis) { match = pregmatch(pattern:"((^.*)(/.+\.act(ion)?)($|\?|;))", string:cgi); if (match) { urls = make_list(urls, match[0]); if (!thorough_tests) break; } match2 = pregmatch(pattern:"(^.*)(/.+\.jsp)$", string:cgi); if (!isnull(match2)) { urls = make_list(urls, match2[0]); if (!thorough_tests) break; } match3 = pregmatch(pattern:"(^.*)(/.+\.do)$", string:cgi); if (!isnull(match3)) { urls = make_list(urls, match3[0]); if (!thorough_tests) break; } if (cgi =~ "struts2?(-rest)?-showcase") { urls = make_list(urls, cgi); if (!thorough_tests) break; } } } if (thorough_tests) { cgi2 = get_kb_list('www/' + port + '/content/extensions/act*'); if (!isnull(cgi2)) urls = make_list(urls, cgi2); cgi3 = get_kb_list('www/' + port + '/content/extensions/jsp'); if (!isnull(cgi3)) urls = make_list(urls, cgi3); cgi4 = get_kb_list('www/' + port + '/content/extensions/do'); if (!isnull(cgi4)) urls = make_list(urls, cgi4); } # Always check web root urls = make_list(urls, "/"); urls = list_uniq(urls); secs = make_list(5, 10, 20); vuln_actions = make_list(); foreach dir (urls) { # assume the action is vulnerable unless proven otherwise vuln = TRUE; for (i = 0; i < max_index(secs) && vuln; i++) { millis = secs[i] * 1000; ognl = '(\'\\u0023_memberAccess[\\\'allowStaticMethodAccess\\\']\')(meh)=true&' + '(aaa)((\'\\u0023context[\\\'xwork.MethodAccessor.denyMethodExecution\\\']\\u003d\\u0023foo\')(\\u0023foo\\u003dnew%20java.lang.Boolean(%22false%22)))&' + '(asdf)((\'\\u0023thread.sleep(' + millis +')\')(\\u0023thread\\[email protected]@currentThread()))=1'; url = dir + '?' + ognl; http_set_read_timeout(secs[i] * 2); then = unixtime(); res = http_send_recv3( method:'GET', item:url, port:port, exit_on_fail:TRUE ); now = unixtime(); # if it looks like this action isn't vulnerable, move on to checking # the next one if ( now - then < secs[i] || now - then > (secs[i]+5) ) vuln = FALSE; } if (vuln) break; } if (!vuln) exit(0, 'No vulnerable applications were detected on the web server listening on port '+port+'.'); if (report_verbosity > 0) { report = get_vuln_report( header: 'Nessus determined a struts 2 application is vulnerable by\n'+ 'forcing it to sleep() before sending the server\'s response.\n'+ 'This was verified using the following URL :', trailer: 'Please note Nessus stopped after detecting the first vulnerable\n'+ 'application. Others may be vulnerable.', items:url, port:port ); security_hole(port:port, extra:report); } else security_hole(port);NASL family Misc. NASL id STRUTS_2_2_1.NASL description The version of Apache Struts running on the remote host is 2.x prior to 2.2.1. It, therefore, is affected by a possible remote code execution vulnerability when OGNL expressions are evaluated due to improper validation by the ParametersInterceptor class. Note that Nessus has not tested for these issues but has instead relied only on the application last seen 2020-06-01 modified 2020-06-02 plugin id 117363 published 2018-09-10 reporter This script is Copyright (C) 2018-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/117363 title Apache Struts 2.x < 2.2.1 OGNL RCE (S2-005) code # # (C) Tenable Network Security, Inc. # include("compat.inc"); if (description) { script_id(117363); script_version("1.9"); script_cvs_date("Date: 2019/11/05"); script_cve_id("CVE-2010-1870"); script_bugtraq_id(41592); script_name(english:"Apache Struts 2.x < 2.2.1 OGNL RCE (S2-005)"); script_summary(english:"Checks the Struts 2 version."); script_set_attribute(attribute:"synopsis", value: "A web application running on the remote host uses a Java framework that is affected by a possible remote code execution."); script_set_attribute(attribute:"description", value: "The version of Apache Struts running on the remote host is 2.x prior to 2.2.1. It, therefore, is affected by a possible remote code execution vulnerability when OGNL expressions are evaluated due to improper validation by the ParametersInterceptor class. Note that Nessus has not tested for these issues but has instead relied only on the application's self-reported version number."); script_set_attribute(attribute:"see_also", value:"http://blog.o0o.nu/2010/07/cve-2010-1870-struts2xwork-remote.html"); script_set_attribute(attribute:"see_also", value:"https://cwiki.apache.org/confluence/display/WW/S2-005"); script_set_attribute(attribute:"solution", value: "Upgrade to Apache Struts version 2.2.1 or later"); script_set_cvss_base_vector("CVSS2#AV:N/AC:L/Au:N/C:N/I:P/A:N"); script_set_cvss_temporal_vector("CVSS2#E:F/RL:OF/RC:ND"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:L/A:N"); script_set_cvss3_temporal_vector("CVSS:3.0/E:F/RL:O/RC:C"); script_set_attribute(attribute:"cvss_score_source", value:"CVE-2010-1870"); script_set_attribute(attribute:"exploitability_ease", value:"Exploits are available"); script_set_attribute(attribute:"exploit_available", value:"true"); script_set_attribute(attribute:"exploit_framework_core", value:"true"); script_set_attribute(attribute:"d2_elliot_name", value:"Apache-Struts < 2.2.0 RCE Linux"); script_set_attribute(attribute:"exploit_framework_d2_elliot", value:"true"); script_set_attribute(attribute:"metasploit_name", value:'Apache Struts Remote Command Execution'); script_set_attribute(attribute:"exploit_framework_metasploit", value:"true"); script_set_attribute(attribute:"exploit_framework_canvas", value:"true"); script_set_attribute(attribute:"canvas_package", value:'White_Phosphorus'); script_set_attribute(attribute:"agent", value:"all"); script_set_attribute(attribute:"vuln_publication_date", value:"2010/08/15"); script_set_attribute(attribute:"patch_publication_date", value:"2010/08/15"); script_set_attribute(attribute:"plugin_publication_date", value:"2018/09/10"); script_set_attribute(attribute:"potential_vulnerability", value:"true"); script_set_attribute(attribute:"plugin_type", value:"combined"); script_set_attribute(attribute:"cpe", value:"cpe:/a:apache:struts"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_family(english:"Misc."); script_copyright(english:"This script is Copyright (C) 2018-2019 and is owned by Tenable, Inc. or an Affiliate thereof."); script_dependencies("os_fingerprint.nasl", "struts_detect_win.nbin", "struts_detect_nix.nbin", "struts_config_browser_detect.nbin"); script_require_keys("Settings/ParanoidReport"); script_require_ports("installed_sw/Apache Struts", "installed_sw/Struts"); exit(0); } include("vcf.inc"); if (report_paranoia < 2) audit(AUDIT_PARANOID); app_info = vcf::combined_get_app_info(app:"Apache Struts"); vcf::check_granularity(app_info:app_info, sig_segments:3); constraints = [ { "min_version" : "2.0.0", "max_version" : "2.1.8.1", "fixed_version" : "2.2.1" } ]; vcf::check_version_and_report(app_info:app_info, constraints:constraints, severity:SECURITY_WARNING);
Packetstorm
data source https://packetstormsecurity.com/files/download/91774/struts2xwork-exec.txt id PACKETSTORM:91774 last seen 2016-12-05 published 2010-07-14 reporter Meder Kydyraliev source https://packetstormsecurity.com/files/91774/Struts2-XWork-Remote-Command-Execution.html title Struts2/XWork Remote Command Execution data source https://packetstormsecurity.com/files/download/104227/struts_code_exec.rb.txt id PACKETSTORM:104227 last seen 2016-12-05 published 2011-08-19 reporter Meder Kydyraliev source https://packetstormsecurity.com/files/104227/Apache-Struts-2.2.0-Remote-Command-Execution.html title Apache Struts < 2.2.0 Remote Command Execution
Saint
| bid | 41592 |
| description | Apache Struts2 XWork ParameterInterceptor security bypass |
| osvdb | 66280 |
| title | struts_xwork_parameterinterceptor |
| type | remote |
Seebug
bulletinFamily exploit description ## 漏洞详情 在struts2中,DefaultActionMapper类支持以"action:"、"redirect:"、"redirectAction:"作为导航或是重定向前缀,但是这些前缀后面同时可以跟OGNL表达式,由于struts2没有对这些前缀做过滤,导致利用OGNL表达式调用java静态方法执行任意系统命令。 这里以“redirect:”前缀举例,struts2会将“redirect:”前缀后面的内容设置到redirect.location当中,这里我们一步步跟踪,首先是这个getMapping函数跟入 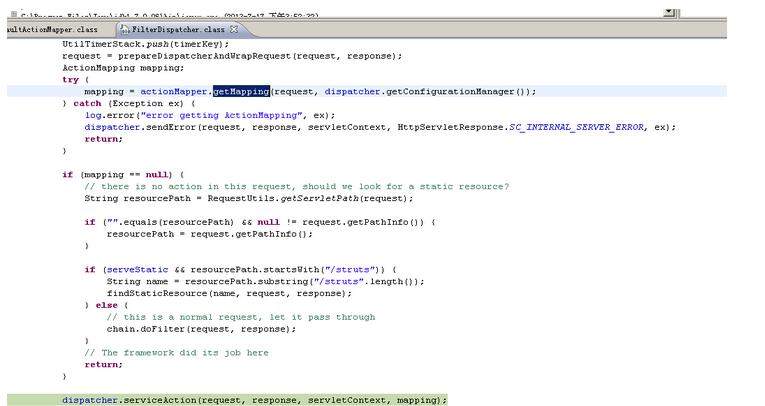 这里一直到这个handleSpecialParameters(),继续跟入 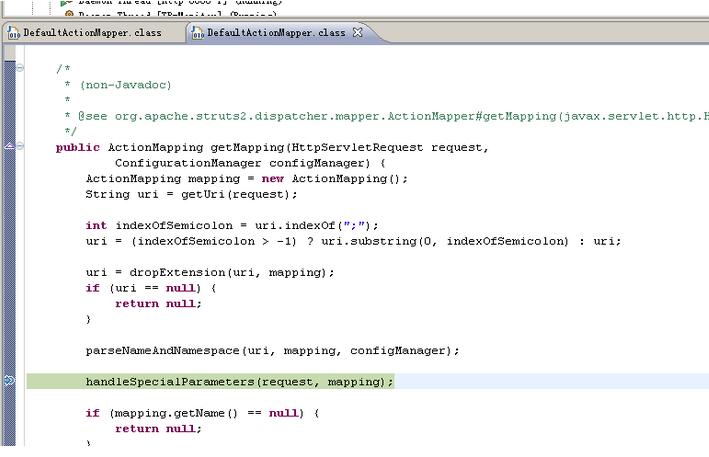 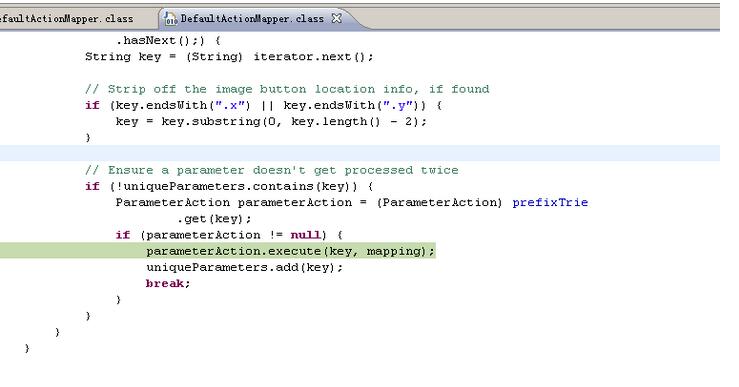 这里真正传入OGNL表达式是在这个parameterAction.execute()中,继续跟入来到DefaultActionMapper.java的代码 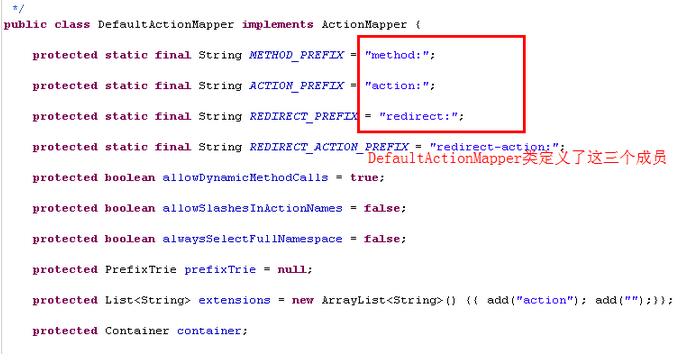 然而上面的过程只是传递OGNL表达式,真正执行是在后面,这里是在FilterDispatcher类中的dispatcher.serviceAction()方法,这里的mapping对象中设置了传入的OGNL 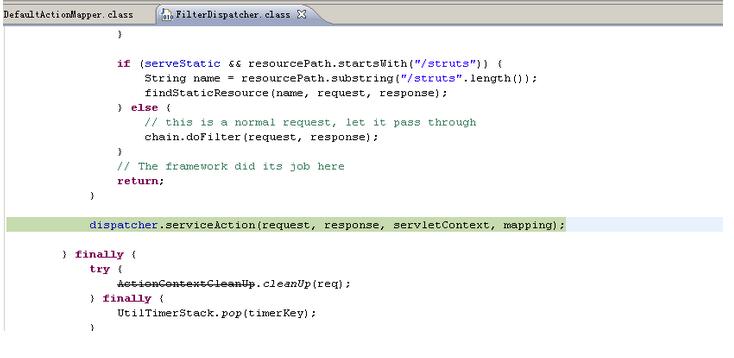 这里跟入方法最终会在TextParseUtil这个类的调用stack.findValue()方法执行OGNL。 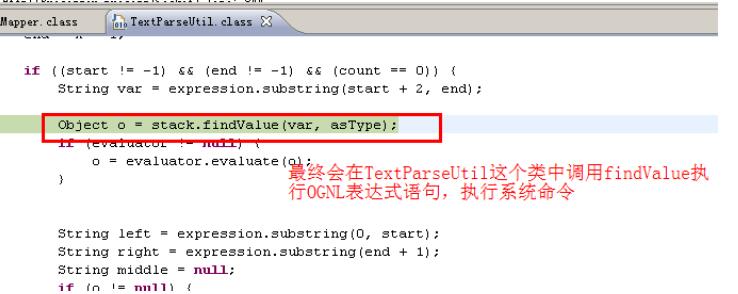 详情来源:http://drops.wooyun.org/papers/902 id SSV:69390 last seen 2017-11-19 modified 2014-07-01 published 2014-07-01 reporter Root source https://www.seebug.org/vuldb/ssvid-69390 title Struts2/XWork < 2.2.0 - Remote Command Execution Vulnerability bulletinFamily exploit description CVE ID: CVE-2010-1870 VMware vCenter Orchestrator是自动管理任务的应用程序。Alive Enterprise是监管进程的应用程序。 VMware vCenter Orchestrator和Alive Enterprise在实现上存在远程代码执行漏洞,两个产品中都嵌入了第三方组件Apache Struts,此组件中的远程代码执行漏洞可允许恶意用户绕过ParametersInterceptor内的'#'-usage保护,使服务器端context对象受控。 VMWare VMware vCenter Orchestrator 4.1 VMWare VMware vCenter Orchestrator 4.0 VMWare Alive Enterprise 7.2 厂商补丁: VMWare ------ 目前厂商已经发布了升级补丁以修复这个安全问题,请到厂商的主页下载: http://www.vmware.com id SSV:20526 last seen 2017-11-19 modified 2011-05-10 published 2011-05-10 reporter Root title VMware vCenter Orchestrator和Alive Enterprise远程代码执行漏洞 bulletinFamily exploit description No description provided by source. id SSV:19954 last seen 2017-11-19 modified 2010-07-15 published 2010-07-15 reporter Root source https://www.seebug.org/vuldb/ssvid-19954 title Struts2/XWork < 2.2.0 Remote Command Execution Vulnerability
References
- http://blog.o0o.nu/2010/07/cve-2010-1870-struts2xwork-remote.html
- http://confluence.atlassian.com/display/FISHEYE/FishEye+Security+Advisory+2010-06-16
- http://packetstormsecurity.com/files/159643/LISTSERV-Maestro-9.0-8-Remote-Code-Execution.html
- http://seclists.org/fulldisclosure/2010/Jul/183
- http://seclists.org/fulldisclosure/2020/Oct/23
- http://secunia.com/advisories/59110
- http://securityreason.com/securityalert/8345
- http://struts.apache.org/2.2.1/docs/s2-005.html
- http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20140709-struts2
- http://www.exploit-db.com/exploits/14360
- http://www.osvdb.org/66280
- http://www.securityfocus.com/bid/41592