Security News

Industrial control system vulnerability disclosures grew a staggering 110% over the last four years, with a 25% increase in the second half of 2021 compared to the previous six months, according to a research released by Claroty. "As more cyber-physical systems become connected, accessibility to these networks from the internet and the cloud requires defenders to have timely, useful vulnerability information to inform risk decisions," said Amir Preminger, VP of research at Claroty.
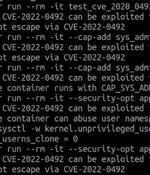
Details have emerged about a now-patched high-severity vulnerability in the Linux kernel that could potentially be abused to escape a container in order to execute arbitrary commands on the container host. The shortcoming resides in a Linux kernel feature called control groups, also referred to as cgroups version 1, which allows processes to be organized into hierarchical groups, effectively making it possible to limit and monitor the usage of resources such as CPU, memory, disk I/O, and network.

Researchers have disclosed details of a now-patched security vulnerability in GitLab, an open-source DevOps software, that could potentially allow a remote, unauthenticated attacker to recover user-related information.Tracked as CVE-2021-4191, the medium-severity flaw affects all versions of GitLab Community Edition and Enterprise Edition starting from 13.0 and all versions starting from 14.4 and prior to 14.8.

TechCrunch is reporting - but not describing in detail - a vulnerability in a series of stalkerware apps that exposes personal information of the victims. The vulnerability isn't in the apps installed on the victims' phones, but in the website the stalker goes to view the information the app collects.

The global security and vulnerability management market is expected to grow from $6.7 billion in 2020 to $15.86 billion by 2030, at a CAGR of 9% during the forecast period 2021-2030, according to The Brainy Insights. An increase in vulnerabilities across the globe, high monetary losses due to the absence of security and vulnerability management solutions, stringent regulatory standards and data privacy compliances, surge in the adoption of IoT and cloud trends, and integration of advanced technologies such as AI and ML with security and vulnerability management solutions are some of the major driving factors contributing to the high growth rate of the security and vulnerability management market.

Adobe on Sunday rolled out patches to contain a critical security vulnerability impacting its Commerce and Magento Open Source products that it said is being actively exploited in the wild. The California-headquartered company also pointed out that the vulnerability is only exploitable by an attacker with administrative privileges.

Apple on Thursday patched a zero-day security vulnerability in its WebKit browser engine, issuing updates for iOS, iPadOS, and macOS. Its Safari browser, based on WebKit, received the security update separately for instances where it is being used with an older version of macOS, like Big Sur. The Apple patch is relevant not just to users of Safari, which relies on WebKit, but to users of any iOS browser, because Apple requires that all iOS browsers use WebKit - a situation currently being considered by antitrust regulators in the US and UK. Alex Russell, a program manager for Microsoft's Edge browser who formerly worked at Google and has long evangelized web technology, echoed past frustration with Apple's insistence that only WebKit is fit for iOS. "Imagine, if you can, a world where installing an alternative browser as your default actually had a chance of protecting you from Apple's shocking underinvestment in security," he lamented via Twitter.

iOS users: Patch now to avoid falling prey to this WebKit vulnerability. iOS users may have noticed an unexpected software update on their devices yesterday, and Apple is urging everyone to install that update immediately to avoid falling prey to a use-after-free vulnerability that could allow an attacker to execute arbitrary code on a victim's device.

The US Cybersecurity and Infrastructure Security Agency has warned admins to patch a set of severe security flaws dubbed ICMAD and impacting SAP business apps using Internet Communication Manager. Yesterday, Onapsis Research Labs who found and reported CVE-2022-22536, one of the three ICMAD bugs and the one rated as a maximum severity issue, also cautioned SAP customers to patch them immediately.

The U.S. Cybersecurity and Infrastructure Security Agency is urging federal agencies to secure their systems against an actively exploited security vulnerability in Windows that could be abused to gain elevated permissions on affected hosts. To that end, the agency has added CVE-2022-21882 to the Known Exploited Vulnerabilities Catalog, necessitating that Federal Civilian Executive Branch agencies patch all systems against this vulnerability by February 18, 2022.