Security News

A recently disclosed F5 BIG-IP vulnerability has been used in destructive attacks, attempting to erase a device's file system and make the server unusable. Last week, F5 disclosed a vulnerability tracked as CVE-2022-1388 that allows remote attackers to execute commands on BIG-IP network devices as 'root' without authentication.

Microsoft on Monday disclosed that it mitigated a security flaw affecting Azure Synapse and Azure Data Factory that, if successfully exploited, could result in remote code execution. "The vulnerability was specific to the third-party Open Database Connectivity driver used to connect to Amazon Redshift in Azure Synapse pipelines and Azure Data Factory Integration Runtime and did not impact Azure Synapse as a whole," the company said.
Days after F5 released patches for a critical remote code execution vulnerability affecting its BIG-IP family of products, security researchers are warning that they were able to create an exploit for the shortcoming. The critical security vulnerability impacts the following versions of BIG-IP products -.

Google has released monthly security patches for Android with fixes for 37 flaws across different components, one of which is a fix for an actively exploited Linux kernel vulnerability that came to light earlier this year. Tracked as CVE-2021-22600, the vulnerability is ranked "High" for severity and could be exploited by a local user to escalate privileges or deny service.

QNAP has released several security advisories today, one of them for a critical security issue that allows remote execution of arbitrary commands on vulnerable QVR systems, the company's video surveillance solution hosted on a NAS device. QNAP's advisory explains that the "Vulnerability has been reported to affect QNAP VS Series NVR running QVR. If exploited, this vulnerability allows remote attackers to run arbitrary commands."

Google has released the second part of the May security patch for Android, including a fix for an actively exploited Linux kernel vulnerability. As Android uses a modified Linux kernel, the vulnerability also affects the operating system.

Cloud security and application delivery network provider F5 on Wednesday released patches to contain 43 bugs spanning its products. "This vulnerability may allow an unauthenticated attacker with network access to the BIG-IP system through the management port and/or self IP addresses to execute arbitrary system commands, create or delete files, or disable services," F5 said in an advisory.
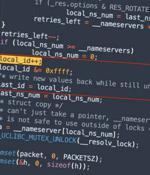
Cybersecurity researchers have disclosed an unpatched security vulnerability that could pose a serious risk to IoT products. The issue, which was originally reported in September 2021, affects the Domain Name System implementation of two popular C libraries called uClibc and uClibc-ng that are used for developing embedded Linux systems.

They're leaving traditional vulnerability management paradigms behind and shifting to the next generation of VPT solutions. It's not news that even the most resource-rich enterprise can't possibly sort through, prioritize and patch every single vulnerability in their ecosystem.

Survey: Recovery from Log4Shell vulnerability is ongoing with 77% of organizations still in patching mode. In March 2022, Valtix worked with an independent research firm to survey 200 cloud security leaders to understand how the vulnerability has influenced security teams.