Security News

Well-known cybersecurity researcher Fabian Bräunlein has featured not once but twice before on Naked Security for his work in researching the pros and cons of Apple's AirTag products. Now, Bräunlein is back with another worthwhile warning, this time about the danger of cloud-based security lookup services that give you a free opinion about cybersecurity data you may have collected.

I have been meaning to write about Joe Sullivan, Uber's former Chief Security Officer. He was convicted of crimes related to covering up a cyberattack against Uber.
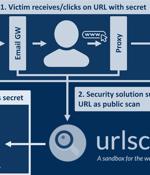
Security researchers are warning of "a trove of sensitive information" leaking through urlscan.io, a website scanner for suspicious and malicious URLs. "Sensitive URLs to shared documents, password reset pages, team invites, payment invoices and more are publicly listed and searchable," Positive Security co-founder, Fabian Bräunlein, said in a report published on November 2, 2022.

Prevention is often seen as the responsibility of the software developer, as they are required to securely develop and deliver code, verify third party components, and harden the build environment. The supplier also holds a critical responsibility in ensuring the security and integrity of our software.

You will also receive a complimentary subscription to TechRepublic's News and Special Offers newsletter and the Top Story of the Day newsletter. You may unsubscribe from these newsletters at any time.

Windows has its own independently developed and maintained encryption library with the wacky name Cryptography API: Next Generation, so in theory you would not expect to have to worry about OpenSSL on Windows at all. Dll in its System folder, which is a filename typically associated with OpenSSL. Intriguingly, that one turns out to be a false alarm, because it was compiled from the LibreSSL code, a similar but alternative cryptographic library from the OpenBSD team that is loosely compatible with OpenSSL, but doesn't have these bugs in it.

Every SaaS app user and login is a potential threat; whether it's bad actors or potential disgruntled former associates, identity management and access control is crucial to prevent unwanted or mistaken entrances to the organization's data and systems. Identity and Access Management solutions administer user identities and control access to enterprise resources and applications.
With high chances of user error, limited security resources, and constantly evolving computing environments, commercial and public organizations need cybersecurity resources to help protect their data and workloads in the cloud. Download this white paper to learn what CIS resources can help secure your cloud environments.

Recent cyberthreats have highlighted security gaps in the software supply chain, and enterprises must take a closer look at their third-party due diligence processes to ensure trust and security. In a recent survey conducted by the Neustar International Security Council, 76% of security and information technology professionals worldwide cited software supply chain risk as a top security priority, and fully 77% attributed the increased rigor of due diligence processes they have in place for external managed service providers to the Log4j vulnerability and other prominent attacks against software and service providers.

Sloppy data security at education tech giant Chegg exposed students and workers' personal information not once but four times in various ways over four years, according to the FTC. In response, the American consumer watchdog today ordered the company to better protect data, including encrypting sensitive information, providing multi-factor authentication to users and employees, limiting the amount of personal information it collects and retains, and training staff on security practices. Per an FTC order [PDF], the tech firm also has to notify "Each individual whose unencrypted Social Security number, financial account information, date of birth, user account credentials, or medical information was exposed" within the next 60 days.