Security News

The Complete Information Security Certification Bundle helps you pick up that vital knowledge. For any business, maintaining information security is not only important for trust - there are many regulations that require it.

Are you looking to take your career in the information security industry to the next level? Look no further than the 2023 Certified Technology Professional Bundle! First, with the increasing reliance on technology and the Internet, information security has become an important issue for individuals and businesses.

Boffins based in China and the UK have devised a telecom network attack that can expose call metadata during VoLTE/VoNR conversations. Researchers Zishuai Cheng and Baojiang Cui, with the Beijing University of Posts and Telecommunications, and Mihai Ordean, Flavio Garcia, and Dominik Rys, with the University of Birmingham, have found a way to access encrypted call metadata - VoLTE activity logs that describe call times, duration, and direction for mobile network conversations.

One popular use of JSON is the JWT system, which isn't pronounced jer-witt, as it is written, but jot, an English word that is sometimes used to refer the little dot we write above above an i or j, and that refers to a tiny but potentially important detail. Loosely speaking, a JWT is a blob of JavaScript that is used by many cloud services as a service access token.

Security veteran Chris Deibler, the new VP of Security at DataGrail, has been brought in to build the company's security team to support its growth. A former Director of Security Engineering at Shopify and Director of Security at Twitch, he knows a thing or two about successfully instituting a security organization within an enterprise, so we decided to pick his brain on the subject.
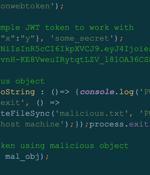
A high-severity security flaw has been disclosed in the open source jsonwebtoken library that, if successfully exploited, could lead to remote code execution on a target server. "By exploiting this vulnerability, attackers could achieve remote code execution on a server verifying a maliciously crafted JSON web token request," Palo Alto Networks Unit 42 researcher Artur Oleyarsh said in a Monday report.

A strong identity governance strategy can address these hurdles, and should be a foundational part of every IT and security initiative. Today, even organizations with the most modern IT frameworks are looking for a way to orchestrate identity management across hybrid-cloud environments.

In this Help Net Security video, Karthik Kannan, CEO at Anvilogic, talks about predictions for the cybersecurity world in 2023 and how to gain security consciousness through cost. The post How to...

Two of the US government's leading security agencies are building a machine learning-based analytics environment to defend against rapidly evolving threats and create more resilient infrastructures for both government entities and private organizations. The Department of Homeland Security - in particular its Science and Technology Directorate research arm - and Cybersecurity and Infrastructure Security Agency picture a multicloud collaborative sandbox that will become a training ground for government boffins to test analytic methods and technologies that rely heavily on artificial intelligence and machine learning techniques.

The MS Exchange exploit chain recently revealed by Crowdstrike researchers is how the Play ransomware gang breached the Rackspace Hosted Exchange email environment, the company confirmed last week. "We will be sharing more detailed information with our customers and peers in the security community so that, collectively, we can all better defend against these types of exploits in the future," Rackspace noted in its final update on the concluded forensic investigation.