Security News
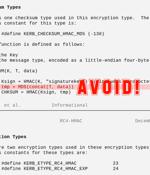
Astonishingly, the CVE-2022-38023 vulnerability existed in the first place because both Windows and Samba still supported a style of integrity protection based on the long-deprecated hashing algorithm MD5. Simply put, network authentication using Microsoft's version of the Kerberos protocol still allowed data to be integrity-protected using flawed cryptography. Assuming a reliable algorithm, with no exploitable weaknesses, you'd expect that a hash with X bits of output would need about 2X-1 tries to find a second input that collided with the hash of an existing file.

Current cybersecurity practices are woefully unprepared to meet the complexities of modern networks. Cloud services, remote users, personally-owned devices, mobile company assets and other forms of tech regularly move from outside the network in, and a once-safe device can't be assumed to be safe again.

The Internet Systems Consortium has released patches to address multiple security vulnerabilities in the Berkeley Internet Name Domain 9 Domain Name System software suite that could lead to a denial-of-service condition. "A remote attacker could exploit these vulnerabilities to potentially cause denial-of-service conditions and system failures," the U.S. Cybersecurity and Infrastructure Security Agency said in an advisory released Friday.

The NSCS has attributed the campaigns to a Russia-based group called SEABORGIUM and the Iran-based TA453 group, also known as APT42. The threat groups target individuals working in academia, defence, government, non-government organisations, and think-tanks.

While many organizations are prioritizing ERP application security, others are instead focusing on and investing heavily in traditional cybersecurity tools that only address more common threats, like ransomware. There are numerous security risks that can leave business-critical applications vulnerable to cybercriminals.

Portainer smooths out the rather steep learning curve of Kubernetes, making it considerably easier for your teams to manage namespaces, networks, pods, ingresses, Helm, ConfigMaps & Secrets, Volumes and even the cluster. My go-to method of deploying Portainer is via a Microk8s cluster, which is the easiest method of getting Kubernetes support rolled into the web-based GUI; however, when deployed in this fashion, Portainer can be accessed either via HTTP or HTTPS and doesn't use SSL certificates.

The dangers of 5G security Networks are only as strong as their weakest link Must-read security coverage. Among other things, 5G constitutes networks linked, often weakly, because each network and device within it may have different security protocols and technology.

More and more security teams are now turning to the emerging category of purpose-built Browser Security Platform as the answer to the browser's security challenges. As this security solution category is still relatively new, there is not yet an established set of browser security best practices, nor common evaluation criteria.

Remote access outfit GoTo has admitted that a threat actor exfiltrated an encryption key that allowed access to "a portion" of encrypted backup files. A third-party cloud storage service GoTo uses for its own products and affiliate company LastPass was attacked in August 2022.

VMware released security patches on Tuesday to address vRealize Log Insight vulnerabilities that could enable attackers to gain remote execution on unpatched appliances. vRealize Log Insight is a log analysis and management tool that helps analyze terabytes of infrastructure and application logs in VMware environments.