Security News
![S3 Ep125: When security hardware has security holes [Audio + Text]](/static/build/img/news/s3-ep125-when-security-hardware-has-security-holes-audio-text-small.jpg)
Ransomware bust, ransomware warning, and anti-ransomware advice. DOUG. Ransomware, more ransomware, and TPM vulnerabilities.

To up your security risk management game, these industry best practices will help you understand and mitigate risks before they take hold. Your strategy should include the potential risks you've identified for your organization, how likely they are to occur and your response plan in the event of an active threat.

Secondly, introducing the dark web report in the U.S. will aid in better monitoring personal information.Google One has announced that VPN access will be expanded to all its plans, including the Basic plan that starts at $1.99/month.
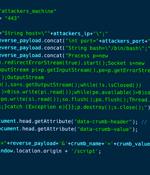
A pair of severe security vulnerabilities have been disclosed in the Jenkins open source automation server that could lead to code execution on targeted systems. The flaws, tracked as CVE-2023-27898 and CVE-2023-27905, impact the Jenkins server and Update Center, and have been collectively christened CorePlague by cloud security firm Aqua.

This can leave gaps in an enterprise's ability to identify devices that are accessing the network and in ensuring that those devices are compliant with security policies. As part of the market's need to gain a clearer, real-time picture of their devices and security posture, Syxsense launched its Enterprise platform last year to address the three key elements of endpoint management and security: vulnerabilities, patch, and compliance.

TPMs are sometimes implemented as a miniature plug-in board that plugs into a designated TPM socket on your computer's motherboard. Hardware TPMs of this sort contain a tiny, dedicated coprocessor with its own secure storage that provides a range of security-related functionality, including hardware random number generation, trusted creation of crytographic keys, and secure digital signatures.

The Environmental Protection Agency is outlining steps public water systems officials need to take to protect drinking water supplies, and mandating cybersecurity assessments in their 'sanitary surveys' of the water systems. Security software maker Tripwire said in a September 2022 report that many of the water systems in the country "Are small, serving low-density communities and functioning on limited budgets. The fragmented nature of water utility coverage coupled with low budgets and limited technological expertise means many systems are outdated and under-protected."

It appears that's not the case in the cyber criminal underground, according to Trend Micro, which recently published a study in which it claims at least 30 percent - if not more - of cyber criminal forum users are women. For its study, Trend Micro looked at five English-language cyber crime forums: Sinister, Cracked, Breached, Hackforums and Raidforum.

"The threat actor was able to capture the employee's master password as it was entered after the employee authenticated with MFA and gained access to the DevOps engineer's LastPass corporate vault," detailed the company´s recent security incident report. LastPass issued recommendations for affected users and businesses in two security bulletins.

"In today's economic reality, security budgets have not necessarily been cut down, but buyers are far more careful in their purchasing decisions and rightfully so. We believe that you cannot secure what you do not know, so knowing should be a basic commodity. Once you understand the magnitude of your SaaS attack layer, you can make an educated decision as to how you are going to solve it. Discovery is the natural and basic first step and it should be accessible to anyone." said Galit Lubetzky Sharon, Wing's Co-Founder and CTO. The company reported that within the first few weeks of launching, over 200 companies enrolled in their self-service free discovery tool, adding to the company's existing customer base. The challenge is that SaaS applications are often onboarded by employees without involving IT or security teams.