Security News

A privilege escalation vulnerability (CVE-2023-30799) could allow attackers to commandeer up to 900,000 MikroTik routers, says VulnCheck researcher Jacob Baines. While exploting it does require...
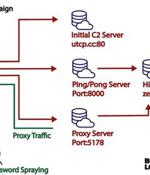
A new malware strain has been found covertly targeting small office/home office routers for more than two years, infiltrating over 70,000 devices and creating a botnet with 40,000 nodes spanning 20 countries. Lumen Black Lotus Labs has dubbed the malware AVrecon, making it the third such strain to focus on SOHO routers after ZuoRAT and HiatusRAT over the past year.

Since at least May 2021, stealthy Linux malware called AVrecon was used to infect over 70,000 Linux-based small office/home office routers to a botnet designed to steal bandwidth and provide a hidden residential proxy service. According to Lumen's Black Lotus Labs threat research team, while the AVrecon remote access trojan compromised over 70,000 devices, only 40,000 were added to the botnet after gaining persistence.

Since at least May 2021, stealthy Linux malware called AVrecon was used to infect over 70,000 Linux-based small office/home office routers to a botnet designed to steal bandwidth and provide a hidden residential proxy service. According to Lumen's Black Lotus Labs threat research team, while the AVrecon remote access trojan compromised over 70,000 devices, only 40,00 were added to the botnet after gaining persistence.

A new malware called Condi has been observed exploiting a security vulnerability in TP-Link Archer AX21 Wi-Fi routers to rope the devices into a distributed denial-of-service botnet. "The Telegram channel was started in May 2022, and the threat actor has been monetizing its botnet by providing DDoS-as-a-service and selling the malware source code," security researchers Joie Salvio and Roy Tay said.

A new DDoS-as-a-Service botnet called "Condi" emerged in May 2023, exploiting a vulnerability in TP-Link Archer AX21 Wi-Fi routers to build an army of bots to conduct attacks. Condi aims to enlist new devices to create a powerful DDoS botnet that can be rented to launch attacks on websites and services.

Annoyingly for ASUS customers, perhaps, two of the now-patched vulnerabilities have been around waiting to be patched for a long time. Why ASUS took so long to patch these particular bugs is not mentioned in the company's official advisory, but handling HTTP "Escape codes" is a fundamental part of any software that listens to and uses web URLs.

Taiwanese company ASUS on Monday released firmware updates to address, among other issues, nine security bugs impacting a wide range of router models. Of the nine security flaws, two are rated Critical and six are rated High in severity.

ASUS has released new firmware with cumulative security updates that address vulnerabilities in multiple router models, warning customers to immediately update their devices or restrict WAN access until they're secured.As the company explains, the newly released firmware contains fixes for nine security flaws, including high and critical ones.
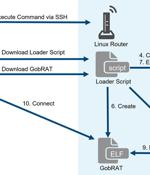
Linux routers in Japan are the target of a new Golang remote access trojan called GobRAT. "Initially, the attacker targets a router whose WEBUI is open to the public, executes scripts possibly by using vulnerabilities, and finally infects the GobRAT," the JPCERT Coordination Center said in a report published today. The compromise of an internet-exposed router is followed by the deployment of a loader script that acts as a conduit for delivering GobRAT, which, when launched, masquerades as the Apache daemon process to evade detection.