Security News

Thousands of GitHub repositories were forked with their clones altered to include malware, a software engineer discovered today. While cloning open source repositories is a common development practice and even encouraged among developers, this case involves threat actors creating copies of legitimate projects but tainting these with malicious code to target unsuspecting developers with their malicious clones.

Cybercriminals are turning to messaging apps like Telegram and Discord as alternatives to popular underground forums: not only for the private communications and security features but also as avenues for spreading malware. The migration to Telegram and Discord illustrates the dynamic nature of criminal groups and the world in which they operate, according to Garrett Carstens, director of intel collection management at the company.

One of the primary methods used by malware distributors to infect devices is by deceiving people into downloading and running malicious files, and to achieve this deception, malware authors are using a variety of tricks. Some of these tricks include masquerading malware executables as legitimate applications, signing them with valid certificates, or compromising trustworthy sites to use them as distribution points.
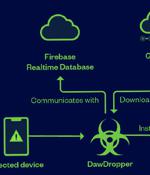
A malicious campaign leveraged seemingly innocuous Android dropper apps on the Google Play Store to compromise users' devices with banking malware. These 17 dropper apps, collectively dubbed DawDropper by Trend Micro, masqueraded as productivity and utility apps such as document scanners, QR code readers, VPN services, and call recorders, among others.

Microsoft has discovered that an access broker it tracks as DEV-0206 uses the Raspberry Robin Windows worm to deploy a malware downloader on networks where it also found evidence of malicious activity matching Evil Corp tactics. "On July 26, 2022, Microsoft researchers discovered the FakeUpdates malware being delivered via existing Raspberry Robin infections," Microsoft revealed Thursday.
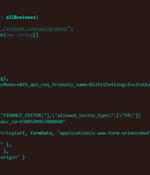
Facebook business and advertising accounts are at the receiving end of an ongoing campaign dubbed Ducktail designed to seize control as part of a financially driven cybercriminal operation. "The malware is designed to steal browser cookies and take advantage of authenticated Facebook sessions to steal information from the victim's Facebook account and ultimately hijack any Facebook Business account that the victim has sufficient access to."

Microsoft has linked a threat group it tracks as Knotweed to a cyber mercenary outfit named DSIRF, targeting European and Central American entities using a malware toolset dubbed Subzero. Using passive DNS data while investigating Knotweed attacks, threat intelligence firm RiskIQ also found that infrastructure actively serving malware since February 2020 linked to DSIRF, including its official website and domains likely used to debug and stage the Subzero malware.

Infostealer malware targets Facebook business accounts to capture sensitive data. A new attack analyzed by cybersecurity provider WithSecure Intelligence targets Facebook business users with the intent of stealing their sensitive data and taking over their accounts.

As many as 30 malicious Android apps with cumulative downloads of nearly 10 million have been found on the Google Play Store distributing adware. While masquerading as innocuous apps, their primary goal is to request permissions to show windows over other apps and run in the background in order to serve intrusive ads.
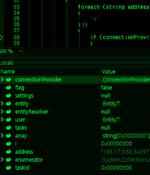
An information-stealing malware called Amadey is being distributed by means of another backdoor called SmokeLoader. The attacks hinge on tricking users into downloading SmokeLoader that masquerades as software cracks, paving the way for the deployment of Amadey, researchers from the AhnLab Security Emergency Response Center said in a report published last week.