Security News
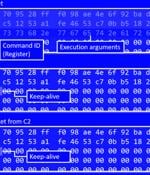
"This family borrows heavily from the original Mirai source code, but what separates it from other IoT malware families is its built-in capability to brute force credentials and gain access to SSH servers instead of Telnet as implemented in Mirai," Fortinet FortiGuard Labs said in a report. The malware, which gets its name from an embedded URL to a YouTube rap music video in an earlier version, is said to have amassed a growing collection of compromised SSH servers, with over 3,500 unique IP addresses used to scan and brute-force their way into the servers.

Meta has released its Q2 2022 adversarial threat report, and among the highlights is the discovery of two cyber-espionage clusters connected to hacker groups known as 'Bitter APT' and APT36 using new Android malware. These cyberspying operatives use social media platforms like Facebook to collect intelligence or to befriend victims using fake personas and then drag them to external platforms to download malware.

A nascent service called Dark Utilities has already attracted 3,000 users for its ability to provide command-and-control services with the goal of commandeering compromised systems. Users are provided an administrative panel to run commands on the machines under their control upon establishing an active C2 channel, effectively granting the attacker full access to the systems.

An unknown threat actor has been targeting Russian entities with a newly discovered remote access trojan called Woody RAT for at least a year as part of a spear-phishing campaign. The advanced custom backdoor is said to be delivered via either of two methods: archive files and Microsoft Office documents leveraging the now-patched "Follina" support diagnostic tool vulnerability in Windows.

A new botnet called 'RapperBot' is being used in attacks since mid-June 2022, focusing on brute-forcing its way into Linux SSH servers to establish a foothold on the device. Over the past 1.5 months since its discovery, the new botnet used over 3,500 unique IPs worldwide to scan and attempt brute-forcing Linux SSH servers.

The U.S. Cybersecurity and Infrastructure Security Agency released a list of the topmost detected malware strains last year in a joint advisory with the Australian Cyber Security Centre. "Most of the top malware strains have been in use for more than five years with their respective code bases evolving into multiple variations," the cybersecurity agencies said.

Other most impersonated legitimate apps by icon include 7-Zip, TeamViewer, CCleaner, Microsoft Edge, Steam, Zoom, and WhatsApp, an analysis from VirusTotal has revealed. "One of the simplest social engineering tricks we've seen involves making a malware sample seem a legitimate program," VirusTotal said in a Tuesday report.

Unknown attackers target Russian entities with newly discovered malware that allows them to control and steal information from compromised devices remotely. According to Malwarebytes, one of the Russian organizations that were attacked using this malware is a government-controlled defense corporation.

A fake website impersonating the official portal for the Atomic wallet, a popular decentralized wallet that also operates as a cryptocurrency exchange portal, is, in reality, distributing copies of the Mars Stealer information-stealing malware. The phony website was disclosed by a malware researcher known as Dee on Monday, but at the time of writing this, it remains online, serving copies of the said malware.

Smart App Control, a Windows 11 security feature that blocks threats at the process level, now comes with support for blocking several file types threat actors have recently adopted to infect targets with malware in phishing attacks. "Windows 11 with smart app control blocks iso and lnk files that have mark of the web just like Macros," David Weston, Microsoft's VP for Enterprise and OS Security, tweeted on Tuesday.