Security News
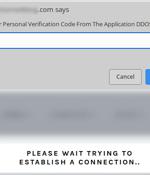
WordPress sites are being hacked to display fraudulent Cloudflare DDoS protection pages that lead to the delivery of malware such as NetSupport RAT and Raccoon Stealer. "A recent surge in JavaScript injections targeting WordPress sites has resulted in fake DDoS prevent prompts which lead victims to download remote access trojan malware," Sucuri's Ben Martin said in a write-up published last week.

Cybersecurity researchers have discovered multiple ongoing malware distribution campaigns that target internet users who seek to download copies of pirated software. In many cases, the malicious executables masquerading as the promised software installers are hosted on file hosting services, so the landing pages redirect victims to other services to download the files.

The operators of the XCSSET macOS malware have upped the stakes by making iterative improvements that add support for macOS Monterey by upgrading its source code components to Python 3. "The malware authors have changed from hiding the primary executable in a fake Xcode.app in the initial versions in 2020 to a fake Mail.app in 2021 and now to a fake Notes.app in 2022," SentinelOne researchers Phil Stokes and Dinesh Devadoss said in a report.

This type of analysis may reveal to malware analysts not only what the malware does, but also its developer's future intentions. All the malware analysis tools listed below can be freely downloaded and used.

Malware peddlers are exploiting users' familiarity with and inherent trust in DDoS protection pages to make them download and run malware on their computer, Sucuri researchers have warned. DDoS protection pages have become so common that users rarely think twice about doing what those pages tell them to do to get website access.

Resecurity, a Los Angeles-based cybersecurity company protecting Fortune 500 worldwide, identified a new RAT advertised in Dark Web and Telegram called Escanor. The threat actors offer Android-based and PC-based versions of RAT, along with HVNC module and exploit builder to weaponize Microsoft Office and Adobe PDF documents to deliver malicious code.

Fortinet announced the latest semiannual FortiGuard Labs Global Threat Landscape Report which revealed that ransomware threat continues to adapt with more variants enabled by Ransomware-as-a-Service. Destructive threat trends continue to evolve, as evidenced by the spread of wiper malware as part of adversary toolkits.
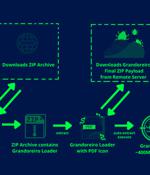
Organizations in the Spanish-speaking nations of Mexico and Spain are in the crosshairs of a new campaign designed to deliver the Grandoreiro banking trojan. "In this campaign, the threat actors impersonate government officials from the Attorney General's Office of Mexico City and from the Public Ministry in the form of spear-phishing emails in order to lure victims to download and execute 'Grandoreiro,' a prolific banking trojan that has been active since at least 2016, and that specifically targets users in Latin America," Zscaler said in a report.

WordPress sites are being hacked to display fake Cloudflare DDoS protection pages to distribute malware that installs the NetSupport RAT and the RaccoonStealer password-stealing Trojan.DDoS protection screens are commonplace on the internet, protecting sites from bots that ping them with bogus requests, aiming to overwhelm them with garbage traffic.

The notorious 'Grandoreiro' banking trojan was spotted in recent attacks targeting employees of a chemicals manufacturer in Spain and workers of automotive and machinery makers in Mexico. It involves the deployment of a Grandoreiro malware variant featuring several new features to evade detection and anti-analysis, as well as a revamped C2 system.